Comprehensive Network Security Assignment Analysis
VerifiedAdded on 2022/08/22
|11
|1870
|16
Homework Assignment
AI Summary
This assignment solution delves into various aspects of network security. It begins by addressing the limitations of Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS), providing examples of Host-based IDS (HIDS) like SolarWinds Security Event Manager and Network-based IDS (NIDS) such as Snort. The solution then examines modern antivirus software, explaining its mechanisms for detecting and preventing malware, including heuristic, specific, and generic detection methods, and discusses the ongoing necessity of antivirus software in today's computing environment. The assignment also explores the pros and cons of homogeneous versus heterogeneous networks, and outlines key training topics for employees regarding cybersecurity, and the importance of WEP, WPA2 and other security measures. Finally, it provides a perspective on budgeting for security systems.

Running head: SECURITY OF NETWORK
SECURITY OF NETWORK
Enter the name of the Student:
Enter the name of the University:
Author note:
SECURITY OF NETWORK
Enter the name of the Student:
Enter the name of the University:
Author note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1SECURITY OF NETWORK
Table of Contents
Question 1:.................................................................................................................................2
Question 2:.................................................................................................................................4
Question 3:.................................................................................................................................5
Question 4:.................................................................................................................................5
Question 5:.................................................................................................................................6
Question 6:.................................................................................................................................7
References..................................................................................................................................8
Table of Contents
Question 1:.................................................................................................................................2
Question 2:.................................................................................................................................4
Question 3:.................................................................................................................................5
Question 4:.................................................................................................................................5
Question 5:.................................................................................................................................6
Question 6:.................................................................................................................................7
References..................................................................................................................................8

2SECURITY OF NETWORK
Question 1:
The problem with relying on IDS/IPS solutions are as follows:
i) Noise can rigorously limit the intrusion detection the effectiveness of system (Nigam,
Minero & Haenggi, 2014).
ii) Bad packets created from the bugs of software.
iii) corrupt the DNS data.
iv) They cannot see into the encrypted packets.
The example of a good host based IDS that is HIDS is SolarWinds Log & Event
Manager. Now it has renamed to Security Event Manager. It contains similar capabilities as
previous along with some new facilities. It is all in one tool kit of SIEM also the pros of
security used to make simpler detecting and examining the issues of security by the data of
event log.
Question 1:
The problem with relying on IDS/IPS solutions are as follows:
i) Noise can rigorously limit the intrusion detection the effectiveness of system (Nigam,
Minero & Haenggi, 2014).
ii) Bad packets created from the bugs of software.
iii) corrupt the DNS data.
iv) They cannot see into the encrypted packets.
The example of a good host based IDS that is HIDS is SolarWinds Log & Event
Manager. Now it has renamed to Security Event Manager. It contains similar capabilities as
previous along with some new facilities. It is all in one tool kit of SIEM also the pros of
security used to make simpler detecting and examining the issues of security by the data of
event log.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
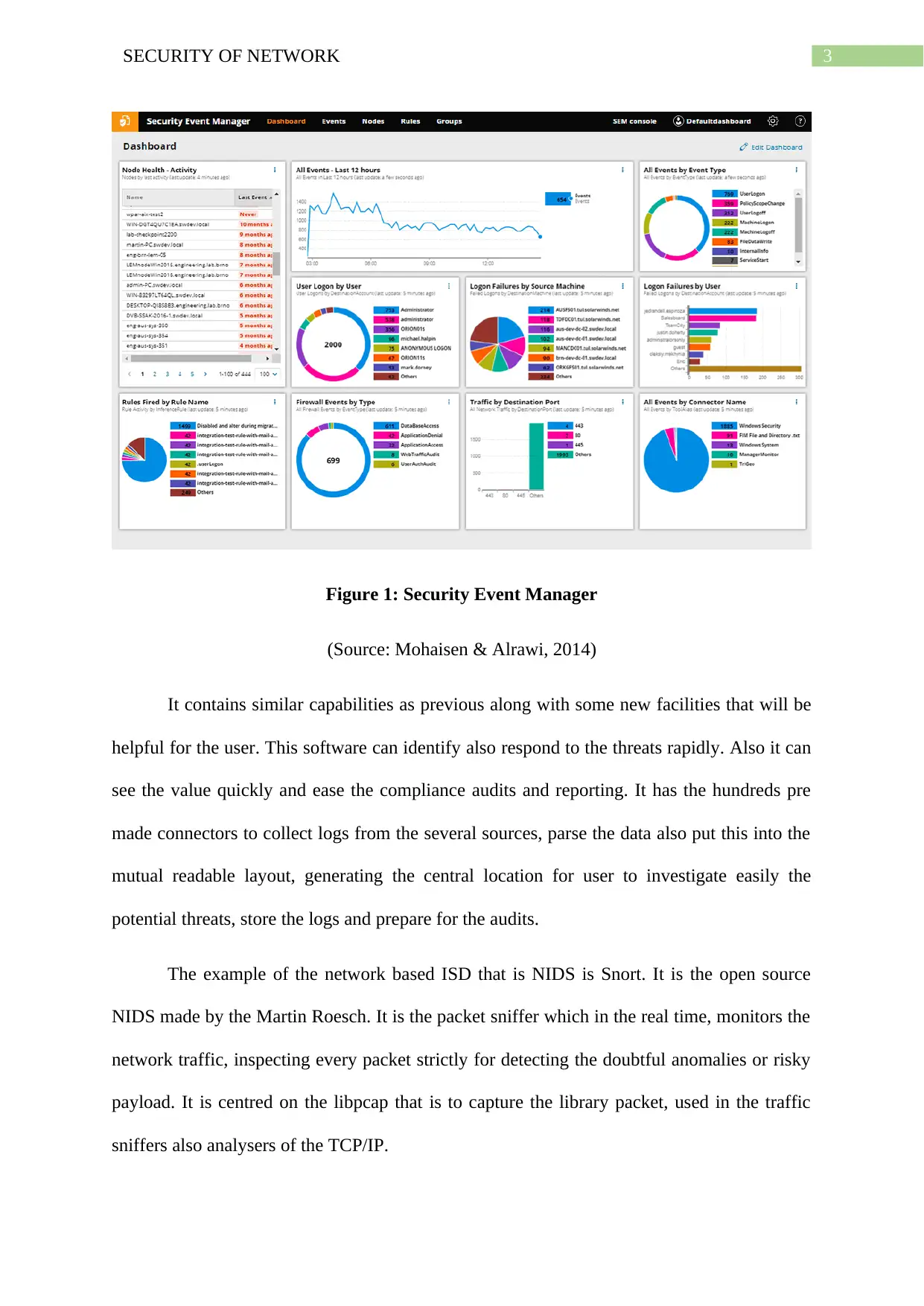
3SECURITY OF NETWORK
Figure 1: Security Event Manager
(Source: Mohaisen & Alrawi, 2014)
It contains similar capabilities as previous along with some new facilities that will be
helpful for the user. This software can identify also respond to the threats rapidly. Also it can
see the value quickly and ease the compliance audits and reporting. It has the hundreds pre
made connectors to collect logs from the several sources, parse the data also put this into the
mutual readable layout, generating the central location for user to investigate easily the
potential threats, store the logs and prepare for the audits.
The example of the network based ISD that is NIDS is Snort. It is the open source
NIDS made by the Martin Roesch. It is the packet sniffer which in the real time, monitors the
network traffic, inspecting every packet strictly for detecting the doubtful anomalies or risky
payload. It is centred on the libpcap that is to capture the library packet, used in the traffic
sniffers also analysers of the TCP/IP.
Figure 1: Security Event Manager
(Source: Mohaisen & Alrawi, 2014)
It contains similar capabilities as previous along with some new facilities that will be
helpful for the user. This software can identify also respond to the threats rapidly. Also it can
see the value quickly and ease the compliance audits and reporting. It has the hundreds pre
made connectors to collect logs from the several sources, parse the data also put this into the
mutual readable layout, generating the central location for user to investigate easily the
potential threats, store the logs and prepare for the audits.
The example of the network based ISD that is NIDS is Snort. It is the open source
NIDS made by the Martin Roesch. It is the packet sniffer which in the real time, monitors the
network traffic, inspecting every packet strictly for detecting the doubtful anomalies or risky
payload. It is centred on the libpcap that is to capture the library packet, used in the traffic
sniffers also analysers of the TCP/IP.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4SECURITY OF NETWORK
Figure 2: Snort
(Source: McMillan et al., 2020)
. It is the packet sniffer which in the real time, monitors the network traffic, inspecting
every packet strictly for detecting the doubtful anomalies or risky payload.
Question 2:
The antivirus software that is known as anti-malware software is designed for
detecting, preventing also taking the action to eliminate the malicious software from the
computer like worms, Trojan horses and viruses.
The software of antivirus first check the computer programs also match them to the
recognized types of the malware. Also it can scan the computer for the behaviours
which may indicate existence of the fresh and unidentified malware (Hock & Kortiš,
2015). This software uses three procedures for scanning detection which are heuristic
Figure 2: Snort
(Source: McMillan et al., 2020)
. It is the packet sniffer which in the real time, monitors the network traffic, inspecting
every packet strictly for detecting the doubtful anomalies or risky payload.
Question 2:
The antivirus software that is known as anti-malware software is designed for
detecting, preventing also taking the action to eliminate the malicious software from the
computer like worms, Trojan horses and viruses.
The software of antivirus first check the computer programs also match them to the
recognized types of the malware. Also it can scan the computer for the behaviours
which may indicate existence of the fresh and unidentified malware (Hock & Kortiš,
2015). This software uses three procedures for scanning detection which are heuristic

5SECURITY OF NETWORK
detection, specific detection and generic detection. The specific detection works by
seeking for identified malware by the distinct set of the characteristics. The procedure
of seeking for the malware which are variants of identified families or the malware
connected by general codebase is known as the generic detection (Virustotal.com.,
2020). And the procedure of heuristic detection scans for the former unfamiliar
viruses by seeking the identified doubtful behaviours or the file structure. It can also
scan the computer for the behaviours which may specify the existence of the new and
unidentified malware.
To do better protect the host machines against the unknown threats, two factors are
present there (Wei et al., 2014). One is install any antivirus software in the host
machines and another is use of the firewall because it recognizes the potential threats
in the traffic of network earlier it can harm the machine.
Now a days all the operating systems have the in-built antivirus software, so user
don’t need to buy any antivirus form the outside. But antivirus is still needful to
protect the computers.
Question 3:
Compare and contrast the pros and cons of deploying the hetero vs. homogenous
networks are as follows:
i) Homogeneous networks are the networks where all nodes have similar function in network
(Nigam, Minero & Haenggi, 2014). On the other hand, heterogeneous networks are the
networks where two or more than two classes of the nodes characterized by both the utility
and function.
ii) The homogeneous networks cost less than the heterogeneous network.
detection, specific detection and generic detection. The specific detection works by
seeking for identified malware by the distinct set of the characteristics. The procedure
of seeking for the malware which are variants of identified families or the malware
connected by general codebase is known as the generic detection (Virustotal.com.,
2020). And the procedure of heuristic detection scans for the former unfamiliar
viruses by seeking the identified doubtful behaviours or the file structure. It can also
scan the computer for the behaviours which may specify the existence of the new and
unidentified malware.
To do better protect the host machines against the unknown threats, two factors are
present there (Wei et al., 2014). One is install any antivirus software in the host
machines and another is use of the firewall because it recognizes the potential threats
in the traffic of network earlier it can harm the machine.
Now a days all the operating systems have the in-built antivirus software, so user
don’t need to buy any antivirus form the outside. But antivirus is still needful to
protect the computers.
Question 3:
Compare and contrast the pros and cons of deploying the hetero vs. homogenous
networks are as follows:
i) Homogeneous networks are the networks where all nodes have similar function in network
(Nigam, Minero & Haenggi, 2014). On the other hand, heterogeneous networks are the
networks where two or more than two classes of the nodes characterized by both the utility
and function.
ii) The homogeneous networks cost less than the heterogeneous network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6SECURITY OF NETWORK
iii) The heterogeneous network offers more protection than the homogeneous network as it
protects by the multiple layers of the security (Mohaisen & Alrawi, 2014).
Question 4:
The list of the most important topics that the chief security officer of the large
company wants to trained his employees:
i) Cyber Secure Business: The program of National Cyber Security Alliances named Cyber
Secure Business is helping the business absorb to be safer also much more secure on online
(Stay Safe Online., 2020). It is the series of in-person, easy to understand and highly
interactive workshops to educate the employees of the business about detecting if something
is going wrong, identifying the assets of the business.
ii) STOP. THINK. CONNECT: It is the worldwide online safety education also the
promotion of awareness for helping all the digital citizens to stay harmless also more
protected online. The NCSA participates STOP. THINK. CONNECT (Stay Safe Online.,
2020). Into the core initiatives also the resources. It offers the resources library containing the
posters, videos, graphics and tip sheets and all these are free for downloading also sharing at
any place such as work, home and in community (Secureworks.com., 2020).
iii) Data Privacy Day: It is the international strength for empowering the characters also
business to respect the privacy, safeguard the data and enable the trust (Stay Safe Online.,
2020). It is signature event in the greater privacy awareness also the effort on education.
Question 5:
To protect the wireless network, WEP wireless security enhancements would
recommend. The WEP is Wired Equivalent Privacy (Gali, Amin Babiker & Mustafa, 2015. It
is the unique encryption protocol that established for the wireless networks. WEP intended to
iii) The heterogeneous network offers more protection than the homogeneous network as it
protects by the multiple layers of the security (Mohaisen & Alrawi, 2014).
Question 4:
The list of the most important topics that the chief security officer of the large
company wants to trained his employees:
i) Cyber Secure Business: The program of National Cyber Security Alliances named Cyber
Secure Business is helping the business absorb to be safer also much more secure on online
(Stay Safe Online., 2020). It is the series of in-person, easy to understand and highly
interactive workshops to educate the employees of the business about detecting if something
is going wrong, identifying the assets of the business.
ii) STOP. THINK. CONNECT: It is the worldwide online safety education also the
promotion of awareness for helping all the digital citizens to stay harmless also more
protected online. The NCSA participates STOP. THINK. CONNECT (Stay Safe Online.,
2020). Into the core initiatives also the resources. It offers the resources library containing the
posters, videos, graphics and tip sheets and all these are free for downloading also sharing at
any place such as work, home and in community (Secureworks.com., 2020).
iii) Data Privacy Day: It is the international strength for empowering the characters also
business to respect the privacy, safeguard the data and enable the trust (Stay Safe Online.,
2020). It is signature event in the greater privacy awareness also the effort on education.
Question 5:
To protect the wireless network, WEP wireless security enhancements would
recommend. The WEP is Wired Equivalent Privacy (Gali, Amin Babiker & Mustafa, 2015. It
is the unique encryption protocol that established for the wireless networks. WEP intended to
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7SECURITY OF NETWORK
deliver related level of the security as the wired networks. However, WEP has several famous
flaws of security is difficult for configuring also is simply broken. This WEP that is Wired
Equivalent Privacy is the security protocol for the wireless local area networks that is
WLANs. It is designed for providing similar level of the security as that of the wired LAN.
This LANs are more protective than the WLANs however the LANs are secured by the
physicality of the structure having some of the network inside the building which can protect
from the unauthorized access.
The other security design elements they can implement to secure as possible so that
work from home can be done are as follows:
i) Keeping the internal and the guest users distinct.
ii) Using the WPA2 that is Wi-Fi protected Access 2.
iii) Secure the access points physically.
iv) Limit the strength of the Wi-Fi signal.
v) Use the detection of the Rough access point.
vi) Use the systems of wireless intrusion prevention.
vii) Practice the management of the mobile device.
viii) Support all the legacy Wi-Fi devices.
Question 6:
On the budget of the $ 10000, it can be enough for the system of lower end security
however if high end software and hardware are required for providing the perimeter security,
there need more money for that.
deliver related level of the security as the wired networks. However, WEP has several famous
flaws of security is difficult for configuring also is simply broken. This WEP that is Wired
Equivalent Privacy is the security protocol for the wireless local area networks that is
WLANs. It is designed for providing similar level of the security as that of the wired LAN.
This LANs are more protective than the WLANs however the LANs are secured by the
physicality of the structure having some of the network inside the building which can protect
from the unauthorized access.
The other security design elements they can implement to secure as possible so that
work from home can be done are as follows:
i) Keeping the internal and the guest users distinct.
ii) Using the WPA2 that is Wi-Fi protected Access 2.
iii) Secure the access points physically.
iv) Limit the strength of the Wi-Fi signal.
v) Use the detection of the Rough access point.
vi) Use the systems of wireless intrusion prevention.
vii) Practice the management of the mobile device.
viii) Support all the legacy Wi-Fi devices.
Question 6:
On the budget of the $ 10000, it can be enough for the system of lower end security
however if high end software and hardware are required for providing the perimeter security,
there need more money for that.

8SECURITY OF NETWORK
The modern IT infrastructure are much more sophisticated also complex than any
other system also the amount of the ground of virtual has grown exponentially. The
consequences of the cyber-attacks continue for growing with the incidents which are digital
now pricing the business of all the sizes on average $ 200000.
The modern IT infrastructure are much more sophisticated also complex than any
other system also the amount of the ground of virtual has grown exponentially. The
consequences of the cyber-attacks continue for growing with the incidents which are digital
now pricing the business of all the sizes on average $ 200000.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9SECURITY OF NETWORK
References
Gali, T. A. B., Amin Babiker, A., & Mustafa, N. (2015). A comparative study between WEP,
WPA and WPA2 security algorithms. International Journal of Science and Research
ISSN, 2319-7064.
Hock, F., & Kortiš, P. (2015, November). Commercial and open-source based Intrusion
Detection System and Intrusion Prevention System (IDS/IPS) design for an IP
networks. In 2015 13th International Conference on Emerging eLearning
Technologies and Applications (ICETA) (pp. 1-4). IEEE.
McMillan, R., McMillan, R., Simonite, T., Matsakis, L., Knight, W., Finley, K., Martineau,
P. and Matsakis, L., 2020. Is Antivirus Software A Waste Of Money?. [online]
WIRED. Available at: <http://www.wired.com/2012/03/antivirus/> [Accessed 18
March 2020].
Mohaisen, A., & Alrawi, O. (2014, July). Av-meter: An evaluation of antivirus scans and
labels. In International conference on detection of intrusions and malware, and
vulnerability assessment (pp. 112-131). Springer, Cham.
Nigam, G., Minero, P., & Haenggi, M. (2014). Coordinated multipoint joint transmission in
heterogeneous networks. IEEE Transactions on Communications, 62(11), 4134-4146.
Secureworks.com. 2020. Managed Security Services, MDR & Security Analytics Software.
[online] Available at: <https://www.secureworks.com/> [Accessed 18 March 2020].
Stay Safe Online. 2020. Get Cybersecurity Safety Resources From The National Cyber
Security Alliance. [online] Available at: <https://staysafeonline.org/> [Accessed 18
March 2020].
References
Gali, T. A. B., Amin Babiker, A., & Mustafa, N. (2015). A comparative study between WEP,
WPA and WPA2 security algorithms. International Journal of Science and Research
ISSN, 2319-7064.
Hock, F., & Kortiš, P. (2015, November). Commercial and open-source based Intrusion
Detection System and Intrusion Prevention System (IDS/IPS) design for an IP
networks. In 2015 13th International Conference on Emerging eLearning
Technologies and Applications (ICETA) (pp. 1-4). IEEE.
McMillan, R., McMillan, R., Simonite, T., Matsakis, L., Knight, W., Finley, K., Martineau,
P. and Matsakis, L., 2020. Is Antivirus Software A Waste Of Money?. [online]
WIRED. Available at: <http://www.wired.com/2012/03/antivirus/> [Accessed 18
March 2020].
Mohaisen, A., & Alrawi, O. (2014, July). Av-meter: An evaluation of antivirus scans and
labels. In International conference on detection of intrusions and malware, and
vulnerability assessment (pp. 112-131). Springer, Cham.
Nigam, G., Minero, P., & Haenggi, M. (2014). Coordinated multipoint joint transmission in
heterogeneous networks. IEEE Transactions on Communications, 62(11), 4134-4146.
Secureworks.com. 2020. Managed Security Services, MDR & Security Analytics Software.
[online] Available at: <https://www.secureworks.com/> [Accessed 18 March 2020].
Stay Safe Online. 2020. Get Cybersecurity Safety Resources From The National Cyber
Security Alliance. [online] Available at: <https://staysafeonline.org/> [Accessed 18
March 2020].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10SECURITY OF NETWORK
Virustotal.com. 2020. Virustotal. [online] Available at:
<https://www.virustotal.com/en/about/> [Accessed 18 March 2020].
Wei, Z., Tang, H., Yu, F. R., Wang, M., & Mason, P. (2014). Security enhancements for
mobile ad hoc networks with trust management using uncertain reasoning. IEEE
Transactions on Vehicular Technology, 63(9), 4647-4658.
Xie, S., & Wang, Y. (2014). Construction of tree network with limited delivery latency in
homogeneous wireless sensor networks. Wireless personal communications, 78(1),
231-246.
Virustotal.com. 2020. Virustotal. [online] Available at:
<https://www.virustotal.com/en/about/> [Accessed 18 March 2020].
Wei, Z., Tang, H., Yu, F. R., Wang, M., & Mason, P. (2014). Security enhancements for
mobile ad hoc networks with trust management using uncertain reasoning. IEEE
Transactions on Vehicular Technology, 63(9), 4647-4658.
Xie, S., & Wang, Y. (2014). Construction of tree network with limited delivery latency in
homogeneous wireless sensor networks. Wireless personal communications, 78(1),
231-246.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





