Developing a Network Security, Backup, and Recovery Plan for FSM
VerifiedAdded on 2023/06/03
|3
|793
|79
Homework Assignment
AI Summary
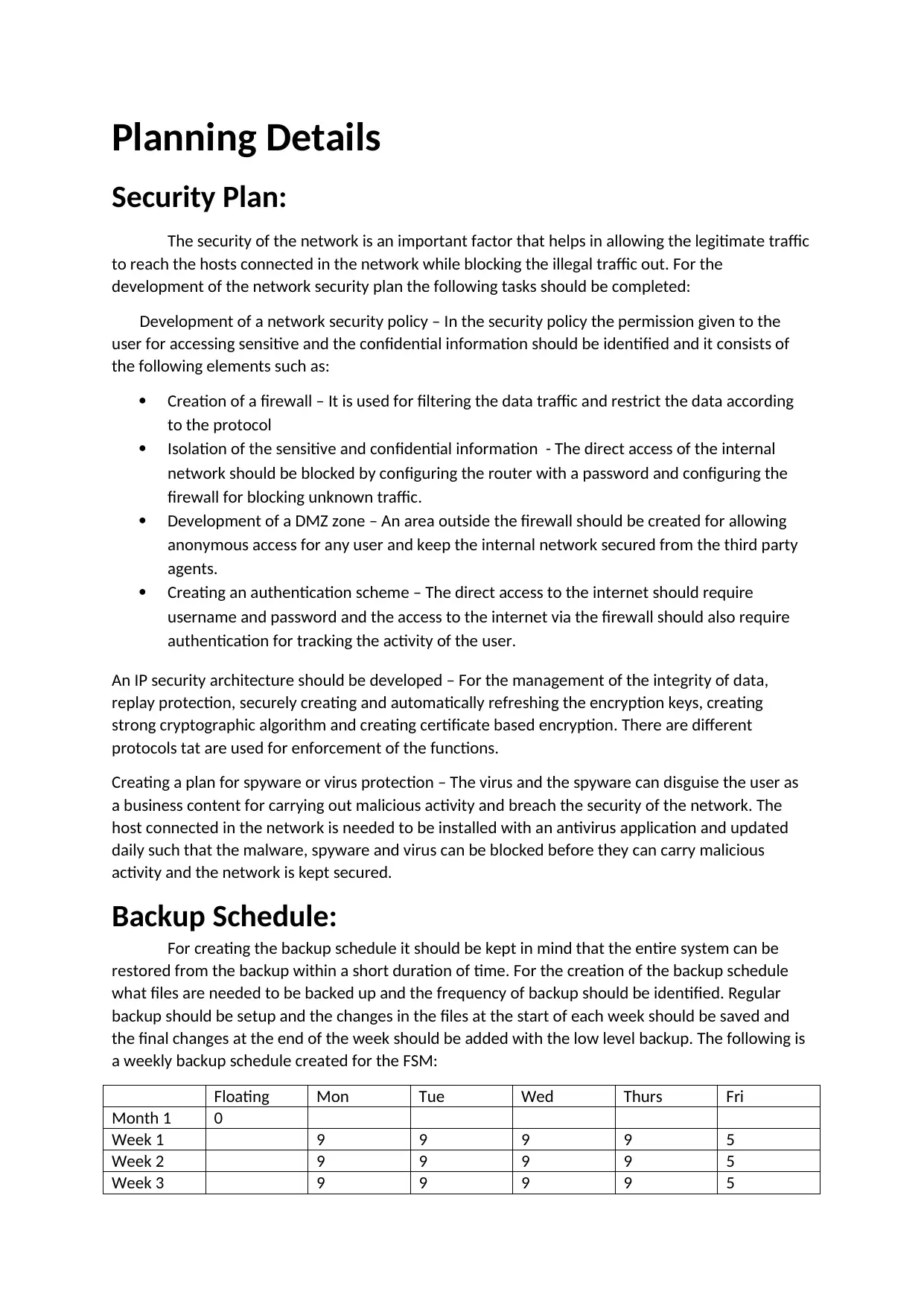
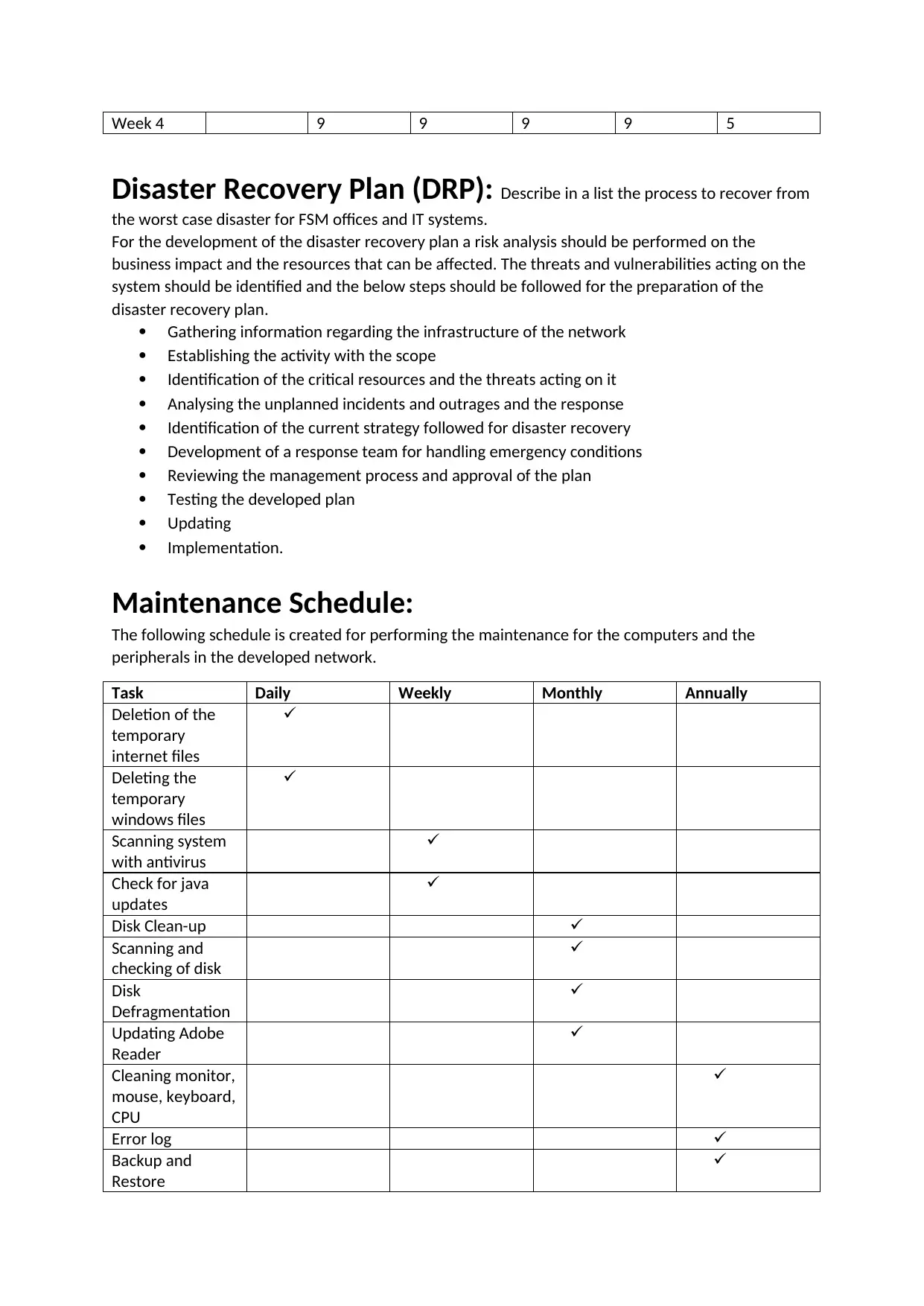
This assignment details a comprehensive network security plan, backup schedule, disaster recovery plan, and maintenance schedule. The security plan covers the creation of a firewall, isolation of sensitive information, development of a DMZ zone, creating an authentication scheme, development of an IP security architecture, and a plan for spyware and virus protection. The backup schedule outlines a weekly backup strategy. The disaster recovery plan includes steps for recovering from worst-case scenarios, encompassing risk analysis, threat identification, and establishing a response team. A maintenance schedule is also provided, detailing daily, weekly, monthly, and annual tasks for computers and peripherals, ensuring data integrity and network performance. This assignment is designed to provide a robust framework for network management and security.
1 out of 3








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)