Comprehensive Network Design Configuration and Security Report for TTF
VerifiedAdded on 2022/11/13
|19
|3997
|243
Report
AI Summary
This report provides a comprehensive analysis and proposed upgrade for the network infrastructure of Talon Textile Fasteners (TTF). It begins with a summary of requirements, including a device needs table, and proposes a network design with a diagram, detailing network configuration and addressing. The report then delves into the Active Directory configuration, outlining user groups, sites, and organizational units. It describes server roles, layouts, and essential project documents like approval sign-off, task lists, and test plans. Further, the report covers server maintenance plans, router specifications, security policies, and concludes with observations. The design incorporates virtual computing environments, security measures like firewalls and ISA Server 2000, and detailed specifications for servers and routers, ensuring a secure and scalable network for TTF's business expansion.

Running head: NETWORK DESIGN CONFIGURATION AND SECURITY
Network Design Configuration and Security
Name of the Student
Name of the University
Author Note
Network Design Configuration and Security
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK DESIGN CONFIGURATION AND SECURITY
Summary
The board members of Talon Textile Fasteners (TTF) have realised that in order to continue
progressing the company needs a major upgrade of their network infrastructure. The report
analyses the network requirements of TTF and proposes the upgraded network design to meet
the various demands of their business expansion. First the report provides a summary of
requirements and presenting the device needs in a tabular format. Then this report jumps to
the network proposal section and suggests the design with the help of a design diagram while
also explaining the network configuration and addressing. Thereafter the various components
of TTF network’s active directory get discussed according to the user groups, the Sites and
the Organizational Units with careful attention given towards role of users as per their
respective domains and organizational units. Then this report describes the server roles and
their layouts along with the necessary project related documents as in user sign off, server
task lists and the server test plan. Following that, the report provides the plans for
maintenance and afterwards lists down the specifications for the routers and servers installed.
Then, after talking about the security policies and measures of the network, the report ends
with observations in the conclusions section.
Summary
The board members of Talon Textile Fasteners (TTF) have realised that in order to continue
progressing the company needs a major upgrade of their network infrastructure. The report
analyses the network requirements of TTF and proposes the upgraded network design to meet
the various demands of their business expansion. First the report provides a summary of
requirements and presenting the device needs in a tabular format. Then this report jumps to
the network proposal section and suggests the design with the help of a design diagram while
also explaining the network configuration and addressing. Thereafter the various components
of TTF network’s active directory get discussed according to the user groups, the Sites and
the Organizational Units with careful attention given towards role of users as per their
respective domains and organizational units. Then this report describes the server roles and
their layouts along with the necessary project related documents as in user sign off, server
task lists and the server test plan. Following that, the report provides the plans for
maintenance and afterwards lists down the specifications for the routers and servers installed.
Then, after talking about the security policies and measures of the network, the report ends
with observations in the conclusions section.

2NETWORK DESIGN CONFIGURATION AND SECURITY
Table of Contents
Introduction................................................................................................................................4
Requirements Summary.............................................................................................................4
Proposed Design of the Network...............................................................................................5
Network Addressing Details..................................................................................................6
Virtual Computing Environment for TTF..................................................................................6
Virtual machines an Operating System..................................................................................6
Configuration.........................................................................................................................7
Security..................................................................................................................................7
Active Directory Configuration.................................................................................................7
AD Site...................................................................................................................................7
AD Organizational Unit.........................................................................................................7
AD Grouping..........................................................................................................................8
Data Entry Officer (Domain User).........................................................................................8
Manufacturing Supervisor (Global Administrator)................................................................8
Sales Manager (Domain User)...............................................................................................8
Operations Manager (Domain User)......................................................................................9
CEO, CFO, CIO (Global User)..............................................................................................9
IT Administrator (Global Administrator)...............................................................................9
Server Specifications..................................................................................................................9
Count and Placement..............................................................................................................9
Server Roles...........................................................................................................................9
Table of Contents
Introduction................................................................................................................................4
Requirements Summary.............................................................................................................4
Proposed Design of the Network...............................................................................................5
Network Addressing Details..................................................................................................6
Virtual Computing Environment for TTF..................................................................................6
Virtual machines an Operating System..................................................................................6
Configuration.........................................................................................................................7
Security..................................................................................................................................7
Active Directory Configuration.................................................................................................7
AD Site...................................................................................................................................7
AD Organizational Unit.........................................................................................................7
AD Grouping..........................................................................................................................8
Data Entry Officer (Domain User).........................................................................................8
Manufacturing Supervisor (Global Administrator)................................................................8
Sales Manager (Domain User)...............................................................................................8
Operations Manager (Domain User)......................................................................................9
CEO, CFO, CIO (Global User)..............................................................................................9
IT Administrator (Global Administrator)...............................................................................9
Server Specifications..................................................................................................................9
Count and Placement..............................................................................................................9
Server Roles...........................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK DESIGN CONFIGURATION AND SECURITY
Approval Sign-off Document...............................................................................................10
Server Task List...................................................................................................................10
Server Test Plan...................................................................................................................11
Server maintenance plan......................................................................................................11
Router Specifications...............................................................................................................12
Security plan and policy...........................................................................................................12
Perimeter Design..................................................................................................................12
Remote Access.....................................................................................................................13
Site to Site Links..................................................................................................................13
Defence in Depth..................................................................................................................13
Security Auditing and Monitoring.......................................................................................14
Threat Identification.............................................................................................................14
Risk Analysis.......................................................................................................................14
Response Procedure.............................................................................................................15
Conclusion................................................................................................................................15
Bibliography.............................................................................................................................16
Approval Sign-off Document...............................................................................................10
Server Task List...................................................................................................................10
Server Test Plan...................................................................................................................11
Server maintenance plan......................................................................................................11
Router Specifications...............................................................................................................12
Security plan and policy...........................................................................................................12
Perimeter Design..................................................................................................................12
Remote Access.....................................................................................................................13
Site to Site Links..................................................................................................................13
Defence in Depth..................................................................................................................13
Security Auditing and Monitoring.......................................................................................14
Threat Identification.............................................................................................................14
Risk Analysis.......................................................................................................................14
Response Procedure.............................................................................................................15
Conclusion................................................................................................................................15
Bibliography.............................................................................................................................16
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK DESIGN CONFIGURATION AND SECURITY
Introduction
To address the issues that Talon Textile Fasteners (TTF) may face from their aging
network, the board members wishes to significantly upgrade their network infrastructure. The
following report analyses the network requirements of TTF and proposes the upgraded
network design to meet the various demands of their business expansion. This report begins
by providing a summary of requirements and presenting the device needs in a tabular format.
Then this report jumps to the network proposal section and suggests the design with the help
of a design diagram. Thereafter the various components of TTF network’s active directory
get discussed according to the user groups, the Sites and the Organizational Units. Then this
report describes the server roles and their layouts along with the necessary project related
documents as in user sign off, server task lists and the server test plan. Following that, the
report provides the plans for maintenance and afterwards lists down the specifications for the
routers and servers installed. Then, after talking about the security policies and measures of
the network, the report ends with observations in concluding notes.
Requirements Summary
Site Server Count Workstation
Count
Number of
Connections
Floor Count
Head office 3 37 40 3
Mt. Burr 2 23 25 2
Pt. Pirie 0 1 1 1
Pt. Adelaide 1 5 6 1
H-Adelaide 2
Adelaide-Burr 2
Introduction
To address the issues that Talon Textile Fasteners (TTF) may face from their aging
network, the board members wishes to significantly upgrade their network infrastructure. The
following report analyses the network requirements of TTF and proposes the upgraded
network design to meet the various demands of their business expansion. This report begins
by providing a summary of requirements and presenting the device needs in a tabular format.
Then this report jumps to the network proposal section and suggests the design with the help
of a design diagram. Thereafter the various components of TTF network’s active directory
get discussed according to the user groups, the Sites and the Organizational Units. Then this
report describes the server roles and their layouts along with the necessary project related
documents as in user sign off, server task lists and the server test plan. Following that, the
report provides the plans for maintenance and afterwards lists down the specifications for the
routers and servers installed. Then, after talking about the security policies and measures of
the network, the report ends with observations in concluding notes.
Requirements Summary
Site Server Count Workstation
Count
Number of
Connections
Floor Count
Head office 3 37 40 3
Mt. Burr 2 23 25 2
Pt. Pirie 0 1 1 1
Pt. Adelaide 1 5 6 1
H-Adelaide 2
Adelaide-Burr 2
5NETWORK DESIGN CONFIGURATION AND SECURITY
Burr-Pirie 2
Pirie-H 2
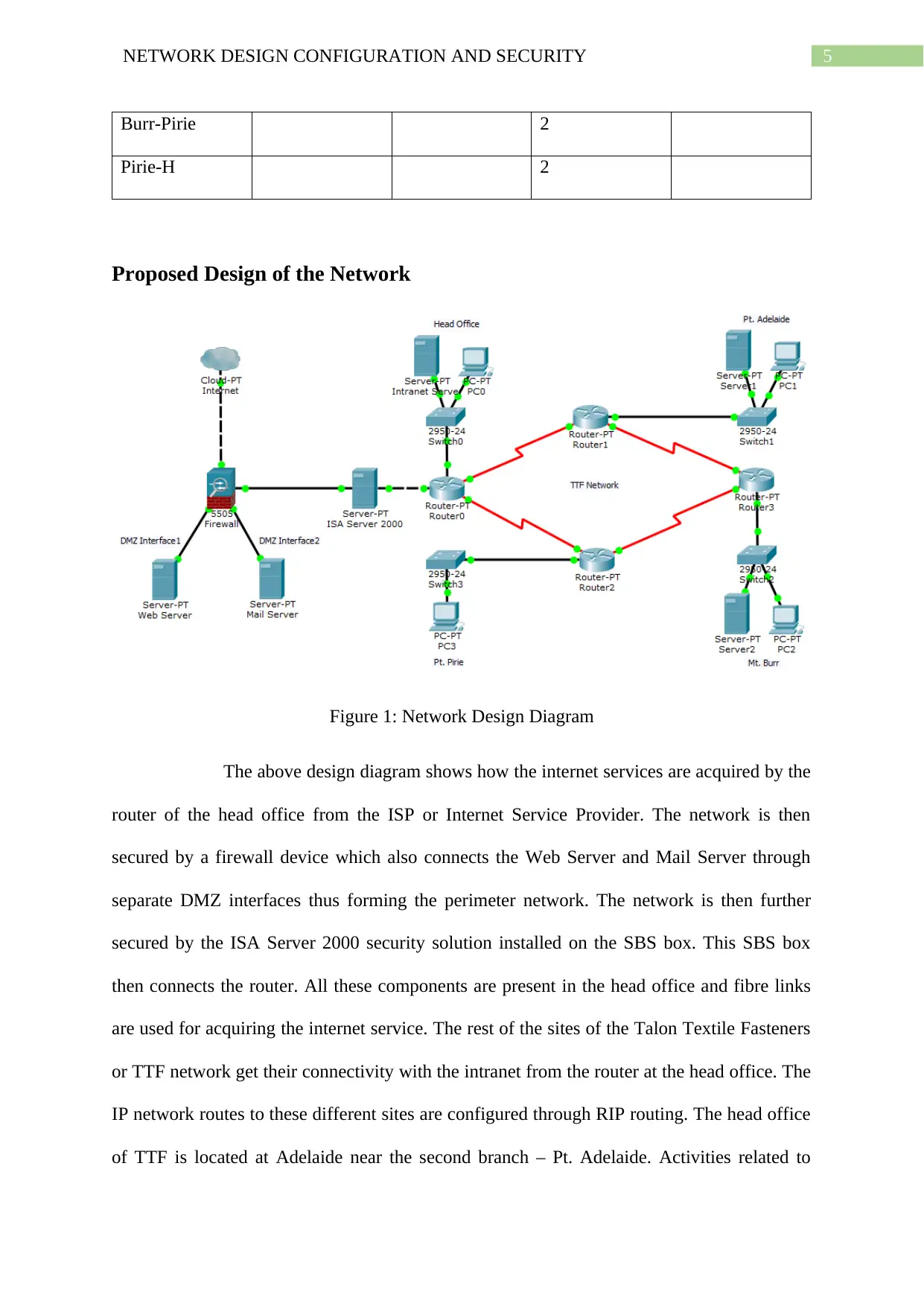
Proposed Design of the Network
Figure 1: Network Design Diagram
The above design diagram shows how the internet services are acquired by the
router of the head office from the ISP or Internet Service Provider. The network is then
secured by a firewall device which also connects the Web Server and Mail Server through
separate DMZ interfaces thus forming the perimeter network. The network is then further
secured by the ISA Server 2000 security solution installed on the SBS box. This SBS box
then connects the router. All these components are present in the head office and fibre links
are used for acquiring the internet service. The rest of the sites of the Talon Textile Fasteners
or TTF network get their connectivity with the intranet from the router at the head office. The
IP network routes to these different sites are configured through RIP routing. The head office
of TTF is located at Adelaide near the second branch – Pt. Adelaide. Activities related to
Burr-Pirie 2
Pirie-H 2
Proposed Design of the Network
Figure 1: Network Design Diagram
The above design diagram shows how the internet services are acquired by the
router of the head office from the ISP or Internet Service Provider. The network is then
secured by a firewall device which also connects the Web Server and Mail Server through
separate DMZ interfaces thus forming the perimeter network. The network is then further
secured by the ISA Server 2000 security solution installed on the SBS box. This SBS box
then connects the router. All these components are present in the head office and fibre links
are used for acquiring the internet service. The rest of the sites of the Talon Textile Fasteners
or TTF network get their connectivity with the intranet from the router at the head office. The
IP network routes to these different sites are configured through RIP routing. The head office
of TTF is located at Adelaide near the second branch – Pt. Adelaide. Activities related to
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK DESIGN CONFIGURATION AND SECURITY
distribution, warehousing, manufacturing and operations are performed at the head office and
when there are excess tasks, they get performed at Pt. Adelaide which comprises of ‘Lines for
All Purposes.’
Network Addressing Details
The networks used for the DMZ interfaces are 172.16.1.0 and 172.16.2.0 while for the routers
four different sites are 192.168.1.0, 192.168.2.0, 192.168.3.0 and 192.168.4.0 respectively.
The devices of the different sites are assigned IP addresses from the networks 192.168.10.0,
192.168.20.0, 192.168.30.0, 192.168.40.0 for the respective networks.
Virtual Computing Environment for TTF
Virtual machines an Operating System
Virtual computing environments allows an organization to utilize the resources
installed in one place from several different locations with the use of virtual machines. These
virtual machines can be third party software applications like virtual box, VMware or even
Microsoft’s own solution called Hyper-V. In TTF network, these applications are installed on
the individual devices of all sites. It allows administrative tasks be performed over the
network from sites where no servers are present like Pt. Pyrie. This can be done by setting up
a virtual machine session using one of the above mentioned applications and on this session
installing server grade operating systems like small business server, windows server 2012.
Thus the system then fulfils the role of another server and helps TTF updating their databases
and changing user privileges when needed. The privileges of users and domains are
configured through active directory which is only available in windows server 2012, since
virtual sessions can be suspended and new sessions with different operating system can be
created, no additional systems are required.
distribution, warehousing, manufacturing and operations are performed at the head office and
when there are excess tasks, they get performed at Pt. Adelaide which comprises of ‘Lines for
All Purposes.’
Network Addressing Details
The networks used for the DMZ interfaces are 172.16.1.0 and 172.16.2.0 while for the routers
four different sites are 192.168.1.0, 192.168.2.0, 192.168.3.0 and 192.168.4.0 respectively.
The devices of the different sites are assigned IP addresses from the networks 192.168.10.0,
192.168.20.0, 192.168.30.0, 192.168.40.0 for the respective networks.
Virtual Computing Environment for TTF
Virtual machines an Operating System
Virtual computing environments allows an organization to utilize the resources
installed in one place from several different locations with the use of virtual machines. These
virtual machines can be third party software applications like virtual box, VMware or even
Microsoft’s own solution called Hyper-V. In TTF network, these applications are installed on
the individual devices of all sites. It allows administrative tasks be performed over the
network from sites where no servers are present like Pt. Pyrie. This can be done by setting up
a virtual machine session using one of the above mentioned applications and on this session
installing server grade operating systems like small business server, windows server 2012.
Thus the system then fulfils the role of another server and helps TTF updating their databases
and changing user privileges when needed. The privileges of users and domains are
configured through active directory which is only available in windows server 2012, since
virtual sessions can be suspended and new sessions with different operating system can be
created, no additional systems are required.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK DESIGN CONFIGURATION AND SECURITY
Configuration
To deploy virtualization features for all the devices, it needs to be ensured that every
device of the network comprises of processors capable of hardware assisted virtualization like
Intel Virtualization Technology (IVT) found in Intel core processors. The devices needs to
allocate separate amount of RAM for the virtualized sessions and hence need to have enough
RAM to operate at least two operating systems simultaneously.
Security
Every users conducting virtualized sessions needs set up strong passwords for their
account. These accounts in turn needs to be managed by network administrators thus
preventing misuse of critical resources. Additionally, virtual machines let the DMZ segment
of the network be configured and managed by network administrators from the ISA 2000
platform so that they do not have to repeatedly switch systems in the perimeter network.
Active Directory Configuration
AD Site
The head office of the company is present in Adelaide as well as the site of Pt.
Adelaide. The rest of the sites involve the sites Mt. Burr and Pt. Pirie. From this, it can be
understood that in TTF’s active directory there are four separate domains – a specific domain
for every site.
AD Organizational Unit
The various organizational units of TTF are found to be the following:
Operations Unit
Sales unit
Finance Unit
Configuration
To deploy virtualization features for all the devices, it needs to be ensured that every
device of the network comprises of processors capable of hardware assisted virtualization like
Intel Virtualization Technology (IVT) found in Intel core processors. The devices needs to
allocate separate amount of RAM for the virtualized sessions and hence need to have enough
RAM to operate at least two operating systems simultaneously.
Security
Every users conducting virtualized sessions needs set up strong passwords for their
account. These accounts in turn needs to be managed by network administrators thus
preventing misuse of critical resources. Additionally, virtual machines let the DMZ segment
of the network be configured and managed by network administrators from the ISA 2000
platform so that they do not have to repeatedly switch systems in the perimeter network.
Active Directory Configuration
AD Site
The head office of the company is present in Adelaide as well as the site of Pt.
Adelaide. The rest of the sites involve the sites Mt. Burr and Pt. Pirie. From this, it can be
understood that in TTF’s active directory there are four separate domains – a specific domain
for every site.
AD Organizational Unit
The various organizational units of TTF are found to be the following:
Operations Unit
Sales unit
Finance Unit

8NETWORK DESIGN CONFIGURATION AND SECURITY
Information Technology Unit
Among the four above mentioned organizational units, the operations unit exist in all the
four sites and out of these sites majority of these operational activities are executed by the
head office and Pt. Adelaide. From this it can be understood that there exists more than one
organizational units other sites have more than one organizational unit in the domains of the
other sites.
AD Grouping
The various groupings that the various user types need to be mapped for maintaining
the different stakeholders are discussed below:
Data Entry Officer (Domain User)
These users perform the data entry tasks for which a single domain is enough for
these staff. Also, they do not need to visit the different sites of the company and hence are
mapped as Domain user.
Manufacturing Supervisor (Global Administrator)
Similar to operations, manufacturing too is gets performed in several sites and
therefore the manufacturing supervisors have the need of visiting the four different sites to
check the ongoing work with the systems and therefore needs access to multiple domains. As
a result, this type of users gets mapped as Global administrator.
Sales Manager (Domain User)
The organizational unit of Sales also are in no need of access to multiple sites and
hence sales managers are tasked with supervising activities at their respective sites thus only
needing accesses to a single domain. Therefore, this type of users gets mapped as Domain
user.
Information Technology Unit
Among the four above mentioned organizational units, the operations unit exist in all the
four sites and out of these sites majority of these operational activities are executed by the
head office and Pt. Adelaide. From this it can be understood that there exists more than one
organizational units other sites have more than one organizational unit in the domains of the
other sites.
AD Grouping
The various groupings that the various user types need to be mapped for maintaining
the different stakeholders are discussed below:
Data Entry Officer (Domain User)
These users perform the data entry tasks for which a single domain is enough for
these staff. Also, they do not need to visit the different sites of the company and hence are
mapped as Domain user.
Manufacturing Supervisor (Global Administrator)
Similar to operations, manufacturing too is gets performed in several sites and
therefore the manufacturing supervisors have the need of visiting the four different sites to
check the ongoing work with the systems and therefore needs access to multiple domains. As
a result, this type of users gets mapped as Global administrator.
Sales Manager (Domain User)
The organizational unit of Sales also are in no need of access to multiple sites and
hence sales managers are tasked with supervising activities at their respective sites thus only
needing accesses to a single domain. Therefore, this type of users gets mapped as Domain
user.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK DESIGN CONFIGURATION AND SECURITY
Operations Manager (Domain User)
Though operations get performed on all the sites, operations managers similar to the
sales managers have been tasked with supervising activities of their respective sites and
hence all they require is single domain access. Therefore, they are mapped as Domain user.
CEO, CFO, CIO (Global User)
These people belong to the C-level or the C-suite members of the company and have
to frequently travel to the different sites of the company as well as outside and therefore need
to have global access. Hence these users are mapped as Global Users.
IT Administrator (Global Administrator)
These IT administrators being responsible carrying out maintenances for ensuring the
uptime of the network and therefore needs access to all parts of the company network in all
sites. Therefore, they need global access and hence are mapped as Global administrators.
Server Specifications
Count and Placement
The network of TTF comprises of 6 servers, among which 3 are present in the head
office, 2 located at Mt. Burr and another in Pt. Adelaide. All 3 servers of sites other than the
head office deal with network specific tasks.
Server Roles
These servers play the key role of facilitating communication lines within the network
among the head office and other sites like with Pt Adelaide for manufacturing, warehousing,
distribution, and operations specific tasks. Servers of the head office are used for hosting the
mailing domain and database needs.
Operations Manager (Domain User)
Though operations get performed on all the sites, operations managers similar to the
sales managers have been tasked with supervising activities of their respective sites and
hence all they require is single domain access. Therefore, they are mapped as Domain user.
CEO, CFO, CIO (Global User)
These people belong to the C-level or the C-suite members of the company and have
to frequently travel to the different sites of the company as well as outside and therefore need
to have global access. Hence these users are mapped as Global Users.
IT Administrator (Global Administrator)
These IT administrators being responsible carrying out maintenances for ensuring the
uptime of the network and therefore needs access to all parts of the company network in all
sites. Therefore, they need global access and hence are mapped as Global administrators.
Server Specifications
Count and Placement
The network of TTF comprises of 6 servers, among which 3 are present in the head
office, 2 located at Mt. Burr and another in Pt. Adelaide. All 3 servers of sites other than the
head office deal with network specific tasks.
Server Roles
These servers play the key role of facilitating communication lines within the network
among the head office and other sites like with Pt Adelaide for manufacturing, warehousing,
distribution, and operations specific tasks. Servers of the head office are used for hosting the
mailing domain and database needs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10NETWORK DESIGN CONFIGURATION AND SECURITY
Approval Sign-off Document
Name of Approver Decision Reason for Rejection Date
Network Architect Approved
Rejected
n/a 22.07.20
19
Project Manager Approved
Rejected
n/a 22.07.20
19
Business Analyst Approved
Rejected
n/a 22.07.20
19
Sponsors Approved
Rejected
n/a 22.07.20
19
Client Representative Approved
Rejected
22.07.20
19
Server Task List
Sl No. Date Activity/Task Priorities Status
S01 21.07.2019 Operations High In Progress
S02 21.07.2019 Manufacturing High Not yet begun
S03 21.07.2019 Sales Medium Delayed
S04 21.07.2019 Operations Medium Delayed
S05 21.07.2019 Finance High Delayed
Approval Sign-off Document
Name of Approver Decision Reason for Rejection Date
Network Architect Approved
Rejected
n/a 22.07.20
19
Project Manager Approved
Rejected
n/a 22.07.20
19
Business Analyst Approved
Rejected
n/a 22.07.20
19
Sponsors Approved
Rejected
n/a 22.07.20
19
Client Representative Approved
Rejected
22.07.20
19
Server Task List
Sl No. Date Activity/Task Priorities Status
S01 21.07.2019 Operations High In Progress
S02 21.07.2019 Manufacturing High Not yet begun
S03 21.07.2019 Sales Medium Delayed
S04 21.07.2019 Operations Medium Delayed
S05 21.07.2019 Finance High Delayed
11NETWORK DESIGN CONFIGURATION AND SECURITY
Server Test Plan
ID TC_R1
Description Ensure all data is consistent among all
servers
Precondition Target server is configured, turned on and
an existing server added the server
Action Server which added the new server ensures
data between the servers are similar
Expected Result Target server has similar data which is
consistent with all other servers
Failure Condition 1. Target server does not have all data
2. Data in Target server is not the same
Server maintenance plan
The maintenance process for the servers can include the following activities:
Verifying and validating server log files
Assessment of storage drive performance
Examining access privileges
Monitoring temperature and other critical measurements of network equipment
Examining of security features
Analysing server logs for security alerts like evidence of hacking attempts
Updating security applications with patches and definitions of all network devices
Installation of updates as in - service packs, hotfixes and the like
Server Test Plan
ID TC_R1
Description Ensure all data is consistent among all
servers
Precondition Target server is configured, turned on and
an existing server added the server
Action Server which added the new server ensures
data between the servers are similar
Expected Result Target server has similar data which is
consistent with all other servers
Failure Condition 1. Target server does not have all data
2. Data in Target server is not the same
Server maintenance plan
The maintenance process for the servers can include the following activities:
Verifying and validating server log files
Assessment of storage drive performance
Examining access privileges
Monitoring temperature and other critical measurements of network equipment
Examining of security features
Analysing server logs for security alerts like evidence of hacking attempts
Updating security applications with patches and definitions of all network devices
Installation of updates as in - service packs, hotfixes and the like
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





