Detailed Secure Network Design and Implementation for B2B Solutions
VerifiedAdded on 2020/03/23
|10
|1928
|234
Project
AI Summary
This project outlines a secure network design for B2B solutions, addressing the expansion of their operations across six buildings with various departments. It begins by defining the project scope and identifying network security threats, categorizing them into active and passive types, and proposing the use of Cisco firewalls to mitigate unauthorized access. The document details the software and hardware requirements, including Cisco routers, switches, firewalls, servers, and access points, along with their specifications and features. The network design is presented, illustrating the interconnection of the buildings using routers, core switches, and switches, ensuring secure wireless connectivity. The project emphasizes the importance of the CIAA model (Confidentiality, Integrity, Availability, and Authorization) and justifies the proposed network solution by employing cryptographic algorithms to maintain data security and ensure authorized access. The conclusion reiterates the design's key aspects, including the use of Cisco devices to reduce operational costs and enhance network security, referencing relevant sources throughout.
network security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Project Scope.................................................................................................................................2
2. Network Security Threats..............................................................................................................2
3. Software and hardware requirement............................................................................................2
4. Network Design.............................................................................................................................5
5. Justification....................................................................................................................................6
6. Conclusion.....................................................................................................................................7
References.............................................................................................................................................8
1
1. Project Scope.................................................................................................................................2
2. Network Security Threats..............................................................................................................2
3. Software and hardware requirement............................................................................................2
4. Network Design.............................................................................................................................5
5. Justification....................................................................................................................................6
6. Conclusion.....................................................................................................................................7
References.............................................................................................................................................8
1

1. Project Scope
The Scope of this project is to create the secure network design for B2B solutions. The B2B
solutions expanding their operations. So, organization team decided to creating the network design.
The B2B solutions has the six building and various departments. It Each building the has the separate
work stations. The Six buildings are finance office, sales office, research office, transport office,
Information technology office and head office. the finance office contains the 100 work stations,
sales office contains the 25 workstations, research office contains the 25 work stations, transport
office contains the 50 work stations, head office contains the 50 work stations and information
technology office contains the 250 work stations. Each building has the single subnet. These are
connected with each other by using the routers. The Proposed network design provides the security
and productivity of the network infrastructure for B2B solutions. The Network security threats are
will be identified. The proposed network infrastructure hardware and software components are will
be addressed and discussed in detail. The justification of proposed network design will be justified by
ensuring the confidentiality, integrity, availability and authorization model in the network.
2. Network Security Threats
The security threats are divided into two categories like active and passive threats. The passive
threats are identified to as eavesdropping and it involves the attempted by hackers to obtain the
information related to communication [1]. It obtained by using the release of message content and
traffic analysis method. The release of message content is used to identified the transmitted the file
may contain sensitive and confidential information. So, it prevents the opponent from the message
or data transmissions. Another method is traffic analysis. It is a kind of attack done on encrypted
messages. The Active threats is including the false stream creation and data stream modification by
using the denial of service and message modification method. The denial of services is one of the
attack and it take the place when the network availability to a resource is blocked by a hacker. The
proposed network design is used to provides the secure network by using the cisco firewalls. The
firewalls are used to blocking the unauthorised access to prevent the sensitive information’s.
3. Software and hardware requirement
The Proposed network design hardware and software requirements are listed in below [2].
2
The Scope of this project is to create the secure network design for B2B solutions. The B2B
solutions expanding their operations. So, organization team decided to creating the network design.
The B2B solutions has the six building and various departments. It Each building the has the separate
work stations. The Six buildings are finance office, sales office, research office, transport office,
Information technology office and head office. the finance office contains the 100 work stations,
sales office contains the 25 workstations, research office contains the 25 work stations, transport
office contains the 50 work stations, head office contains the 50 work stations and information
technology office contains the 250 work stations. Each building has the single subnet. These are
connected with each other by using the routers. The Proposed network design provides the security
and productivity of the network infrastructure for B2B solutions. The Network security threats are
will be identified. The proposed network infrastructure hardware and software components are will
be addressed and discussed in detail. The justification of proposed network design will be justified by
ensuring the confidentiality, integrity, availability and authorization model in the network.
2. Network Security Threats
The security threats are divided into two categories like active and passive threats. The passive
threats are identified to as eavesdropping and it involves the attempted by hackers to obtain the
information related to communication [1]. It obtained by using the release of message content and
traffic analysis method. The release of message content is used to identified the transmitted the file
may contain sensitive and confidential information. So, it prevents the opponent from the message
or data transmissions. Another method is traffic analysis. It is a kind of attack done on encrypted
messages. The Active threats is including the false stream creation and data stream modification by
using the denial of service and message modification method. The denial of services is one of the
attack and it take the place when the network availability to a resource is blocked by a hacker. The
proposed network design is used to provides the secure network by using the cisco firewalls. The
firewalls are used to blocking the unauthorised access to prevent the sensitive information’s.
3. Software and hardware requirement
The Proposed network design hardware and software requirements are listed in below [2].
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Software Requirements
The Software requirements for B2B network infrastructure is shown in below.
Operating System - Windows 7
Memory - 2 GB RAM
Hard Drive - 2.2 GB
Hardware Requirements
The Hardware requirements for B2B network infrastructure is shown in below.
Cisco Routers - Cisco 1900 series Routers
Cisco Switches - Cisco Catalyst 4948 Switch
Cisco Firewall - Cisco ASA 5540 Adaptive Security Appliance
Cisco Server - Cisco UCS C3260 Rack Server
Cisco Core Switches - Cisco Catalyst 6500 Series Switches
Cisco Access point - Cisco Aironet 700 Series Access point
Personal Computers - Dell Computers
Printers - Canon Printers
Specification and Features of Network devices
Cisco 1900 series Routers
The Cisco 1900 series routers are used to provide the secure connectivity.
Cloud manged security and machine learning [3].
It grows the resiliency and density for a scalable network edge.
It provides the high performance.
To enhance the network infrastructure by combining the power of software and hardware.
It delivers the high network functions.
It creates the deliver the new services fast.
Cisco Catalyst 4948 Switch
It provides the high-speed network
low latency
3
The Software requirements for B2B network infrastructure is shown in below.
Operating System - Windows 7
Memory - 2 GB RAM
Hard Drive - 2.2 GB
Hardware Requirements
The Hardware requirements for B2B network infrastructure is shown in below.
Cisco Routers - Cisco 1900 series Routers
Cisco Switches - Cisco Catalyst 4948 Switch
Cisco Firewall - Cisco ASA 5540 Adaptive Security Appliance
Cisco Server - Cisco UCS C3260 Rack Server
Cisco Core Switches - Cisco Catalyst 6500 Series Switches
Cisco Access point - Cisco Aironet 700 Series Access point
Personal Computers - Dell Computers
Printers - Canon Printers
Specification and Features of Network devices
Cisco 1900 series Routers
The Cisco 1900 series routers are used to provide the secure connectivity.
Cloud manged security and machine learning [3].
It grows the resiliency and density for a scalable network edge.
It provides the high performance.
To enhance the network infrastructure by combining the power of software and hardware.
It delivers the high network functions.
It creates the deliver the new services fast.
Cisco Catalyst 4948 Switch
It provides the high-speed network
low latency
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

It delivers the better mobile experience
It easily simplifies the operations
High network connectivity and security
It gives the high network performance.
Power consuming
It supports the multilayer switching
Shared buffer
It provides the end to end service for an organization [4].
Cisco ASA 5540 Adaptive Security Appliance
It is an adaptive and threat focused next generation firewall.
It designed for medium sized organization to provide the threat and advanced malware
protection.
It delivers the integrate threat defence from attackers.
It provides the high performance and availability.
It ensures the business continuity [5].
Cisco UCS C3260 Rack Server
The UCS rack server is used to extend the cisco unified computing to reducing the
organization total costs.
It increasing the organization agility.
It reduces the work load.
It provides the record braking performance.
It reliability to power the most computer and memory intensive.
High storage density [6].
Cisco Catalyst 6500 Series Switches
4
It easily simplifies the operations
High network connectivity and security
It gives the high network performance.
Power consuming
It supports the multilayer switching
Shared buffer
It provides the end to end service for an organization [4].
Cisco ASA 5540 Adaptive Security Appliance
It is an adaptive and threat focused next generation firewall.
It designed for medium sized organization to provide the threat and advanced malware
protection.
It delivers the integrate threat defence from attackers.
It provides the high performance and availability.
It ensures the business continuity [5].
Cisco UCS C3260 Rack Server
The UCS rack server is used to extend the cisco unified computing to reducing the
organization total costs.
It increasing the organization agility.
It reduces the work load.
It provides the record braking performance.
It reliability to power the most computer and memory intensive.
High storage density [6].
Cisco Catalyst 6500 Series Switches
4

It enhances the security.
It improves the reliability
Easily manage the wired and wireless networks.
Easily simplifies the campus network.
High efficiency.
Cisco Aironet 700 Series Access point
It providing the c regulatory domain and internal antenna.
It provides the high-density experience for network [7].
It offers a greater coverage for more capacity and reliability.
4. Network Design
The proposed network infrastructure for B2B solutions is shown in below.
5
It improves the reliability
Easily manage the wired and wireless networks.
Easily simplifies the campus network.
High efficiency.
Cisco Aironet 700 Series Access point
It providing the c regulatory domain and internal antenna.
It provides the high-density experience for network [7].
It offers a greater coverage for more capacity and reliability.
4. Network Design
The proposed network infrastructure for B2B solutions is shown in below.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
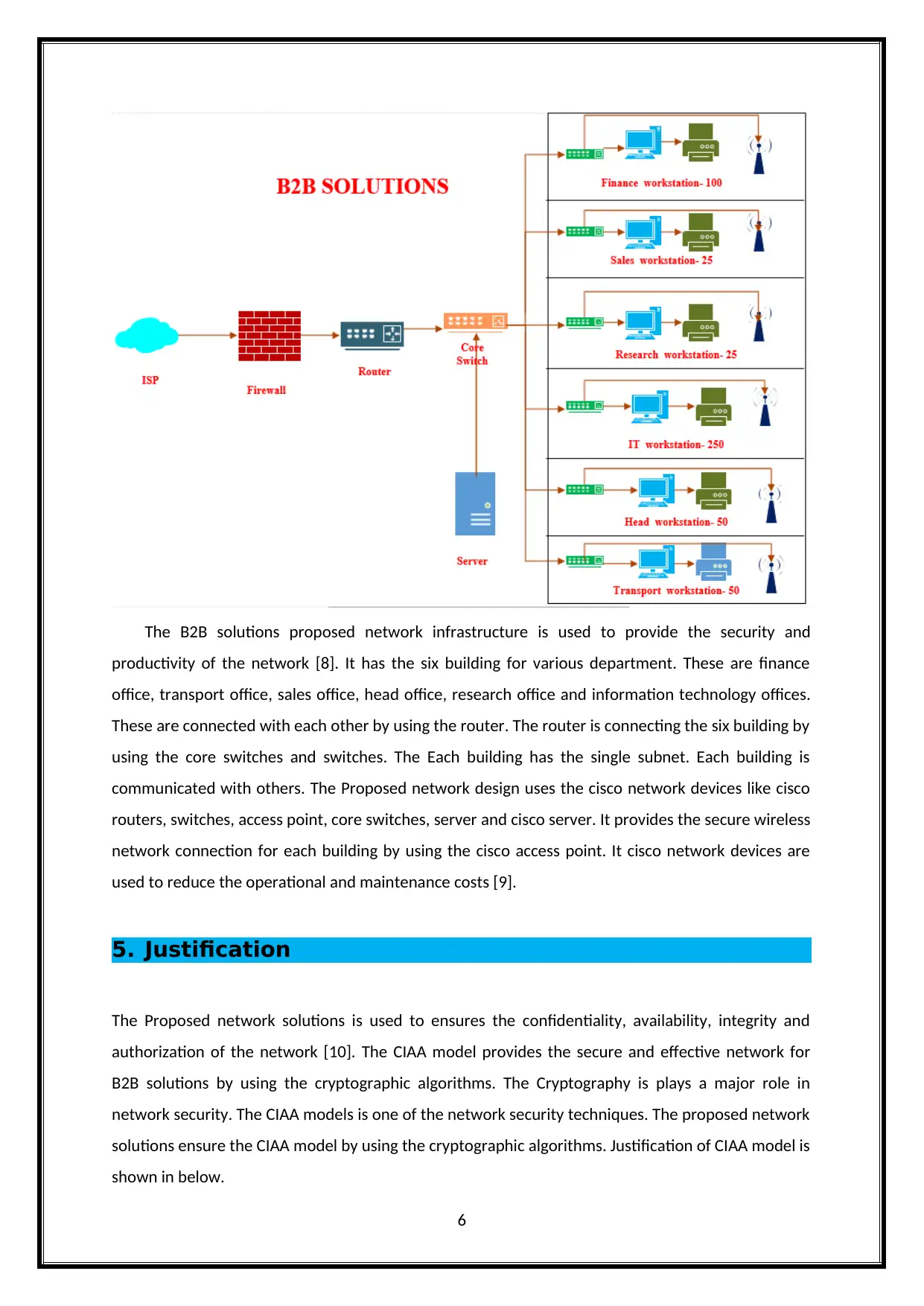
The B2B solutions proposed network infrastructure is used to provide the security and
productivity of the network [8]. It has the six building for various department. These are finance
office, transport office, sales office, head office, research office and information technology offices.
These are connected with each other by using the router. The router is connecting the six building by
using the core switches and switches. The Each building has the single subnet. Each building is
communicated with others. The Proposed network design uses the cisco network devices like cisco
routers, switches, access point, core switches, server and cisco server. It provides the secure wireless
network connection for each building by using the cisco access point. It cisco network devices are
used to reduce the operational and maintenance costs [9].
5. Justification
The Proposed network solutions is used to ensures the confidentiality, availability, integrity and
authorization of the network [10]. The CIAA model provides the secure and effective network for
B2B solutions by using the cryptographic algorithms. The Cryptography is plays a major role in
network security. The CIAA models is one of the network security techniques. The proposed network
solutions ensure the CIAA model by using the cryptographic algorithms. Justification of CIAA model is
shown in below.
6
productivity of the network [8]. It has the six building for various department. These are finance
office, transport office, sales office, head office, research office and information technology offices.
These are connected with each other by using the router. The router is connecting the six building by
using the core switches and switches. The Each building has the single subnet. Each building is
communicated with others. The Proposed network design uses the cisco network devices like cisco
routers, switches, access point, core switches, server and cisco server. It provides the secure wireless
network connection for each building by using the cisco access point. It cisco network devices are
used to reduce the operational and maintenance costs [9].
5. Justification
The Proposed network solutions is used to ensures the confidentiality, availability, integrity and
authorization of the network [10]. The CIAA model provides the secure and effective network for
B2B solutions by using the cryptographic algorithms. The Cryptography is plays a major role in
network security. The CIAA models is one of the network security techniques. The proposed network
solutions ensure the CIAA model by using the cryptographic algorithms. Justification of CIAA model is
shown in below.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Confidentiality
It is used to prevent the sensitive information from unauthorized users. It only allows the
authorised users to accessing the sensitive information. It provides the high data security. It
encrypting the information to protect the sensitive information by using the SSL/TLS security
protocol for communications over the network. It ensures the information confidentiality include
enforcing the file access control and permission to restrict access to information’s [11].
Integrity
The integrity is used to maintains the data consistency, trustworthiness and accuracy through
the network. It ensures that data cannot be modified by unauthorised users. It measures the file
permissions and access control lists. It verifies the data integrity by using the checksums and
cryptographic checksums.
Availability
The availability is used to ensure the authorised users are able to access the information when
needed. It provides the sensitive information for authorised users at the right times. It denying the
unauthorised users are accessing the information. It ensures the data availability by using the
cryptographic algorithms [12].
Authorization
The authorization is used to authenticate the users to accessing the sensitive information. It
allows the authenticated users only accessing the campus information through the network. The
Cryptographic algorithms provide the users authentications to accessing the information. The
cryptographic mechanisms are used to provide secure network and effective network. The CIAA
model is used to maintains the organization security and provide the scalable and reliable network.
6. Conclusion
The B2B solutions decided to create the secure network design because the organization
expanding their operations. The B2b solutions consists of six building and various departments.
These are sales office, finance office, transport office, research office, head office and information
technology office. These are connected with each other by using the cisco routers. Each building has
the single subnet. These are communicated with each other. The proposed network design provides
the security and efficiency of the network. It gives the security by using the cisco firewalls. The
firewall is used to provide the productivity and security for an organization. It uses the cisco network
devices to reduce the maintenance and operational costs. The Network security are identified. The
proposed network design hardware and software requirement are identified and discussed in detail.
7
It is used to prevent the sensitive information from unauthorized users. It only allows the
authorised users to accessing the sensitive information. It provides the high data security. It
encrypting the information to protect the sensitive information by using the SSL/TLS security
protocol for communications over the network. It ensures the information confidentiality include
enforcing the file access control and permission to restrict access to information’s [11].
Integrity
The integrity is used to maintains the data consistency, trustworthiness and accuracy through
the network. It ensures that data cannot be modified by unauthorised users. It measures the file
permissions and access control lists. It verifies the data integrity by using the checksums and
cryptographic checksums.
Availability
The availability is used to ensure the authorised users are able to access the information when
needed. It provides the sensitive information for authorised users at the right times. It denying the
unauthorised users are accessing the information. It ensures the data availability by using the
cryptographic algorithms [12].
Authorization
The authorization is used to authenticate the users to accessing the sensitive information. It
allows the authenticated users only accessing the campus information through the network. The
Cryptographic algorithms provide the users authentications to accessing the information. The
cryptographic mechanisms are used to provide secure network and effective network. The CIAA
model is used to maintains the organization security and provide the scalable and reliable network.
6. Conclusion
The B2B solutions decided to create the secure network design because the organization
expanding their operations. The B2b solutions consists of six building and various departments.
These are sales office, finance office, transport office, research office, head office and information
technology office. These are connected with each other by using the cisco routers. Each building has
the single subnet. These are communicated with each other. The proposed network design provides
the security and efficiency of the network. It gives the security by using the cisco firewalls. The
firewall is used to provide the productivity and security for an organization. It uses the cisco network
devices to reduce the maintenance and operational costs. The Network security are identified. The
proposed network design hardware and software requirement are identified and discussed in detail.
7

The Detailed proposed design is designed and description of design is evaluated. The Justification of
CIAA model is justified.
References
[1]J. Kurose and K. Ross, Computer networking. .
[2]NETworking. [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI, EDB, 2013.
[3]J. Wang, Broadband wireless communications. [Place of publication not identified]: Springer-
Verlag New York, 2013.
[4]W. Osterhage, Wireless security. Enfield, N.H.: Science Publishers, 2012.
[5]D. Forsberg, W. Moeller, V. Niemi and G. Horn, Lte security. Hoboken, N.J.: Wiley, 2014.
[6]"Disadvantages of Wireless Networks | Techwalla.com", Techwalla, 2017. [Online]. Available:
https://www.techwalla.com/articles/disadvantages-of-wireless-networks. [Accessed: 27- Sep-
2017].
[7]T. Alpcan and T. Başar, Network security. Cambridge: Cambridge University Press, 2011.
[8]T. Chia, "Confidentiality, Integrity, Availability: The three components of the CIA Triad « Stack
Exchange Security Blog", Security.blogoverflow.com, 2017. [Online]. Available:
http://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-three-
components-of-the-cia-triad/. [Accessed: 28- Sep- 2017].
[9]"What is confidentiality, integrity, and availability (CIA triad)? - Definition from
WhatIs.com", WhatIs.com, 2017. [Online]. Available:
http://whatis.techtarget.com/definition/Confidentiality-integrity-and-availability-CIA.
[Accessed: 28- Sep- 2017].
[10]"Wireless Networking Security", Cs.bham.ac.uk, 2017. [Online]. Available:
https://www.cs.bham.ac.uk/~mdr/teaching/modules03/security/students/SS7/Wireless
%20Networking%20Security.htm. [Accessed: 28- Sep- 2017].
[11]"What is Network Security? - Palo Alto Networks", Paloaltonetworks.com, 2017. [Online].
Available: https://www.paloaltonetworks.com/cyberpedia/what-is-network-security.
[Accessed: 28- Sep- 2017].
8
CIAA model is justified.
References
[1]J. Kurose and K. Ross, Computer networking. .
[2]NETworking. [Hong Kong]: Regional NET Coordinating Team, NET Section, CDI, EDB, 2013.
[3]J. Wang, Broadband wireless communications. [Place of publication not identified]: Springer-
Verlag New York, 2013.
[4]W. Osterhage, Wireless security. Enfield, N.H.: Science Publishers, 2012.
[5]D. Forsberg, W. Moeller, V. Niemi and G. Horn, Lte security. Hoboken, N.J.: Wiley, 2014.
[6]"Disadvantages of Wireless Networks | Techwalla.com", Techwalla, 2017. [Online]. Available:
https://www.techwalla.com/articles/disadvantages-of-wireless-networks. [Accessed: 27- Sep-
2017].
[7]T. Alpcan and T. Başar, Network security. Cambridge: Cambridge University Press, 2011.
[8]T. Chia, "Confidentiality, Integrity, Availability: The three components of the CIA Triad « Stack
Exchange Security Blog", Security.blogoverflow.com, 2017. [Online]. Available:
http://security.blogoverflow.com/2012/08/confidentiality-integrity-availability-the-three-
components-of-the-cia-triad/. [Accessed: 28- Sep- 2017].
[9]"What is confidentiality, integrity, and availability (CIA triad)? - Definition from
WhatIs.com", WhatIs.com, 2017. [Online]. Available:
http://whatis.techtarget.com/definition/Confidentiality-integrity-and-availability-CIA.
[Accessed: 28- Sep- 2017].
[10]"Wireless Networking Security", Cs.bham.ac.uk, 2017. [Online]. Available:
https://www.cs.bham.ac.uk/~mdr/teaching/modules03/security/students/SS7/Wireless
%20Networking%20Security.htm. [Accessed: 28- Sep- 2017].
[11]"What is Network Security? - Palo Alto Networks", Paloaltonetworks.com, 2017. [Online].
Available: https://www.paloaltonetworks.com/cyberpedia/what-is-network-security.
[Accessed: 28- Sep- 2017].
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
[12]J. Rak, J. Bay, I. Kotenko, L. Popyack, V. Skormin and K. Szczypiorski, Computer network security. .
9
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





