Network Security Design Report: Subnetting, Security, and Hardware
VerifiedAdded on 2020/04/07
|10
|1645
|484
Report
AI Summary
This report details the design of a secure network for a B2B company, addressing the need for subnetting and enhanced security measures. The author, acting as a Network Security Architect and Administrator, outlines a network divided into six subnets: finance, head office, transport, research, sales, and IT. The design includes IP address allocation, subnet masks, and a discussion of potential network risks like data breaches, employee theft, and weak access control. Hardware requirements, including Cisco routers and D-Link switches, are specified. The design emphasizes security through subnetting, encryption, and firewalls. The report concludes by highlighting the importance of network security and the effectiveness of the proposed design in meeting the company's requirements. References to cryptography and network security are provided in the bibliography.

Running head: NETWORK SECURITY
Network Security
Name of the Student:
Name of the University:
Author Note
Network Security
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Network Requirements....................................................................................................................2
Design of the Security Network......................................................................................................4
Description of the Security Network...............................................................................................4
Risks to the network........................................................................................................................5
Hardware Requirements for the network.........................................................................................6
Justification of the network design..................................................................................................7
Conclusion.......................................................................................................................................8
Bibliography....................................................................................................................................9
NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Network Requirements....................................................................................................................2
Design of the Security Network......................................................................................................4
Description of the Security Network...............................................................................................4
Risks to the network........................................................................................................................5
Hardware Requirements for the network.........................................................................................6
Justification of the network design..................................................................................................7
Conclusion.......................................................................................................................................8
Bibliography....................................................................................................................................9

2
NETWORK SECURITY
Introduction
The report contains the information about the network design for the B2B solutions. I am
the Network Security Architect and I have been handed the role of Network Administrator and I
am responsible for designing the network for the company. The company is looking to
implement a subnet solution for the network within the organization that would be dividing the
network into six sub divisions and would also improve the security and the authentication system
within the network.
This report provides the information about the network design of the company and also
the required sub networking of the network into different divisions.
This report consists of the information about the network design and a brief discussion
about the network design is also provided in this report. The justification about the network and
the hardware requirements for the network that is to be constructed for the company is also
provided in this report.
Network Requirements
The B2B Company is looking to improve the security within their network and hence the
network structure for the company is to be relayed. The company has provided information about
the type of network that they are looking to implement for their offices and the different
departments.
The network is required to be sub netted into 6 different sub nets. The different departments
of the company are finance office, the head office, transport office, the research office, the sales
office, the information technology department and the head office. In addition to this, the
NETWORK SECURITY
Introduction
The report contains the information about the network design for the B2B solutions. I am
the Network Security Architect and I have been handed the role of Network Administrator and I
am responsible for designing the network for the company. The company is looking to
implement a subnet solution for the network within the organization that would be dividing the
network into six sub divisions and would also improve the security and the authentication system
within the network.
This report provides the information about the network design of the company and also
the required sub networking of the network into different divisions.
This report consists of the information about the network design and a brief discussion
about the network design is also provided in this report. The justification about the network and
the hardware requirements for the network that is to be constructed for the company is also
provided in this report.
Network Requirements
The B2B Company is looking to improve the security within their network and hence the
network structure for the company is to be relayed. The company has provided information about
the type of network that they are looking to implement for their offices and the different
departments.
The network is required to be sub netted into 6 different sub nets. The different departments
of the company are finance office, the head office, transport office, the research office, the sales
office, the information technology department and the head office. In addition to this, the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK SECURITY
company has provided the further requirements about the network to me as I am the designer of
the network.
The company wants to implement around 500 workstations in their networks. The layout of
the network should be as the mentioned criteria that are stated below.
Finance Office - 100 workstations
Transport Office - 50 workstations
Research Office - 25 workstations
Sales Office - 25 workstations
Information technology - 250 workstations
Head Office - 50 workstations
The company is also looking to implement a proper sub network system within the
organization that would be completely secured logically and also by means encryption
techniques so that proper authentication within the network is maintained.
NETWORK SECURITY
company has provided the further requirements about the network to me as I am the designer of
the network.
The company wants to implement around 500 workstations in their networks. The layout of
the network should be as the mentioned criteria that are stated below.
Finance Office - 100 workstations
Transport Office - 50 workstations
Research Office - 25 workstations
Sales Office - 25 workstations
Information technology - 250 workstations
Head Office - 50 workstations
The company is also looking to implement a proper sub network system within the
organization that would be completely secured logically and also by means encryption
techniques so that proper authentication within the network is maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK SECURITY
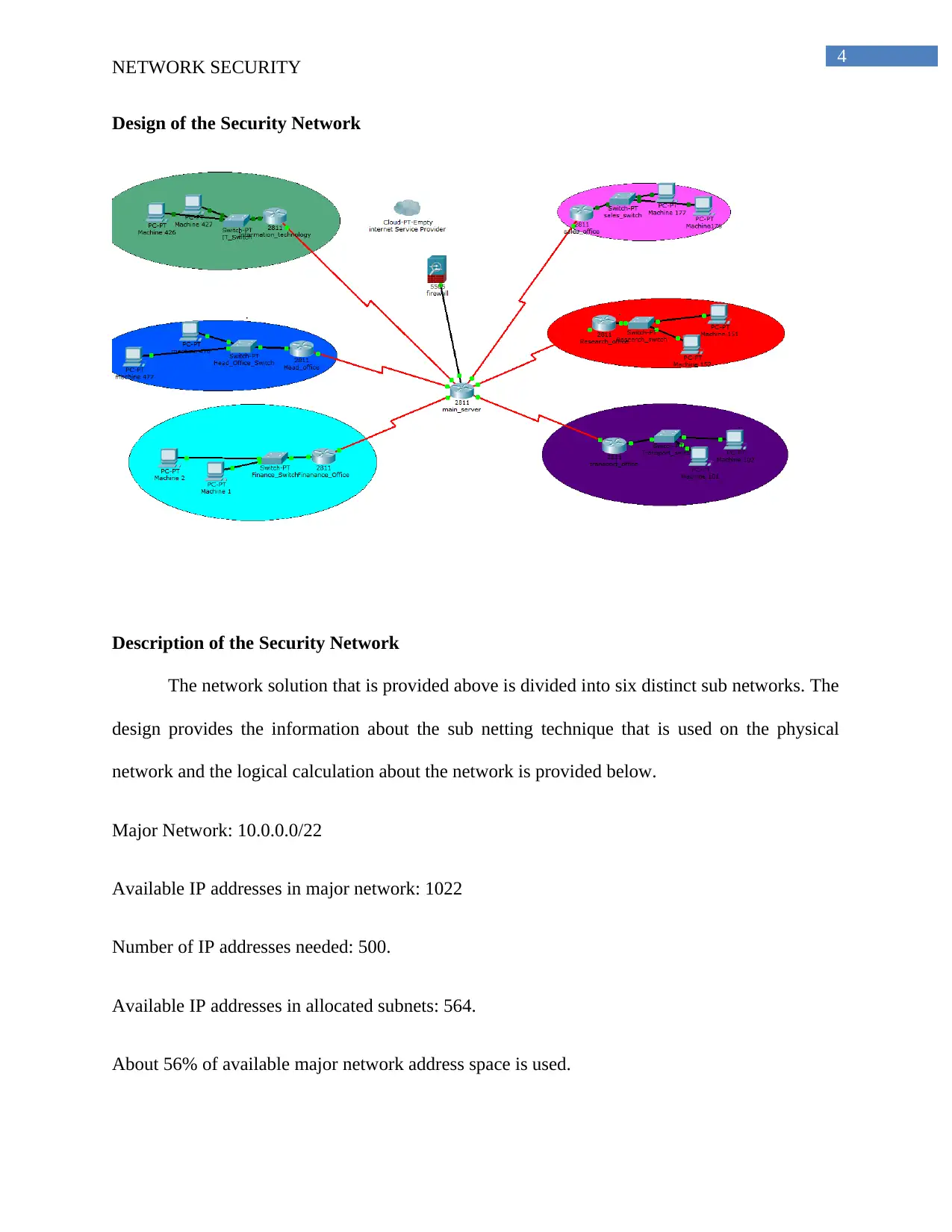
Design of the Security Network
Description of the Security Network
The network solution that is provided above is divided into six distinct sub networks. The
design provides the information about the sub netting technique that is used on the physical
network and the logical calculation about the network is provided below.
Major Network: 10.0.0.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500.
Available IP addresses in allocated subnets: 564.
About 56% of available major network address space is used.
NETWORK SECURITY
Design of the Security Network
Description of the Security Network
The network solution that is provided above is divided into six distinct sub networks. The
design provides the information about the sub netting technique that is used on the physical
network and the logical calculation about the network is provided below.
Major Network: 10.0.0.0/22
Available IP addresses in major network: 1022
Number of IP addresses needed: 500.
Available IP addresses in allocated subnets: 564.
About 56% of available major network address space is used.
5
NETWORK SECURITY
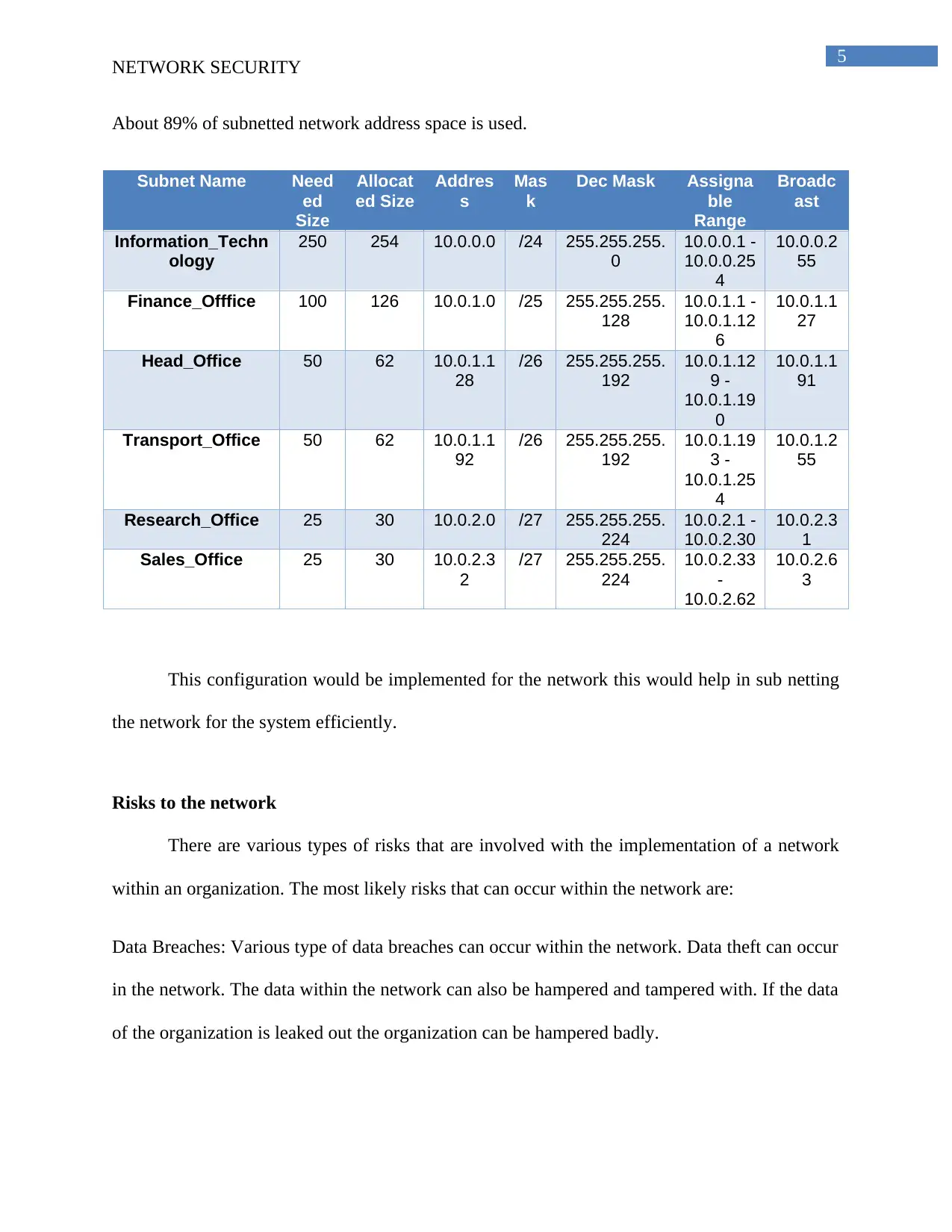
About 89% of subnetted network address space is used.
Subnet Name Need
ed
Size
Allocat
ed Size
Addres
s
Mas
k
Dec Mask Assigna
ble
Range
Broadc
ast
Information_Techn
ology
250 254 10.0.0.0 /24 255.255.255.
0
10.0.0.1 -
10.0.0.25
4
10.0.0.2
55
Finance_Offfice 100 126 10.0.1.0 /25 255.255.255.
128
10.0.1.1 -
10.0.1.12
6
10.0.1.1
27
Head_Office 50 62 10.0.1.1
28
/26 255.255.255.
192
10.0.1.12
9 -
10.0.1.19
0
10.0.1.1
91
Transport_Office 50 62 10.0.1.1
92
/26 255.255.255.
192
10.0.1.19
3 -
10.0.1.25
4
10.0.1.2
55
Research_Office 25 30 10.0.2.0 /27 255.255.255.
224
10.0.2.1 -
10.0.2.30
10.0.2.3
1
Sales_Office 25 30 10.0.2.3
2
/27 255.255.255.
224
10.0.2.33
-
10.0.2.62
10.0.2.6
3
This configuration would be implemented for the network this would help in sub netting
the network for the system efficiently.
Risks to the network
There are various types of risks that are involved with the implementation of a network
within an organization. The most likely risks that can occur within the network are:
Data Breaches: Various type of data breaches can occur within the network. Data theft can occur
in the network. The data within the network can also be hampered and tampered with. If the data
of the organization is leaked out the organization can be hampered badly.
NETWORK SECURITY
About 89% of subnetted network address space is used.
Subnet Name Need
ed
Size
Allocat
ed Size
Addres
s
Mas
k
Dec Mask Assigna
ble
Range
Broadc
ast
Information_Techn
ology
250 254 10.0.0.0 /24 255.255.255.
0
10.0.0.1 -
10.0.0.25
4
10.0.0.2
55
Finance_Offfice 100 126 10.0.1.0 /25 255.255.255.
128
10.0.1.1 -
10.0.1.12
6
10.0.1.1
27
Head_Office 50 62 10.0.1.1
28
/26 255.255.255.
192
10.0.1.12
9 -
10.0.1.19
0
10.0.1.1
91
Transport_Office 50 62 10.0.1.1
92
/26 255.255.255.
192
10.0.1.19
3 -
10.0.1.25
4
10.0.1.2
55
Research_Office 25 30 10.0.2.0 /27 255.255.255.
224
10.0.2.1 -
10.0.2.30
10.0.2.3
1
Sales_Office 25 30 10.0.2.3
2
/27 255.255.255.
224
10.0.2.33
-
10.0.2.62
10.0.2.6
3
This configuration would be implemented for the network this would help in sub netting
the network for the system efficiently.
Risks to the network
There are various types of risks that are involved with the implementation of a network
within an organization. The most likely risks that can occur within the network are:
Data Breaches: Various type of data breaches can occur within the network. Data theft can occur
in the network. The data within the network can also be hampered and tampered with. If the data
of the organization is leaked out the organization can be hampered badly.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SECURITY
Employee Theft: The data from within the organization can also be leaked by an employee of the
organization. The data from the company can acquired and the can be handed over to the rival
organization and also if the attackers gate the access to the network they can very easily perform
the DoS attack on the network.
Weak Access Control: The weak access control within the network would allow easy access to
the attackers and they can perform the man in the middle attacks within the network to obtain
sensitive data from the network and also the security within the network would be hampered.
Privilege Misuse: The network would consist of different levels of authentication and different
staffs of the organization would be assigned different levels of privileges within the network.
Hence, this would provide the staffs within the organization the chance to misuse these
opportunities.
Considering all the risks and the requirements of the company some further assumptions
were made before the designing of the network. It was assumed that the 10.0.0.0/21 subnet
would be used for the network. In addition to this, there can be additional systems installed in the
network and hence, the scope for the installation of the additional machines within the system
was also made.
Hardware Requirements for the network
For the implementation of the network the Cisco SPA122 Small Business ATA with
Router are being used. These are a product of Cisco. The price of each router is about $1000. In
addition to this the connection to the machine can be done with the help of the CAT5 cables. The
network would also require some additional switches to spread the network among the six
NETWORK SECURITY
Employee Theft: The data from within the organization can also be leaked by an employee of the
organization. The data from the company can acquired and the can be handed over to the rival
organization and also if the attackers gate the access to the network they can very easily perform
the DoS attack on the network.
Weak Access Control: The weak access control within the network would allow easy access to
the attackers and they can perform the man in the middle attacks within the network to obtain
sensitive data from the network and also the security within the network would be hampered.
Privilege Misuse: The network would consist of different levels of authentication and different
staffs of the organization would be assigned different levels of privileges within the network.
Hence, this would provide the staffs within the organization the chance to misuse these
opportunities.
Considering all the risks and the requirements of the company some further assumptions
were made before the designing of the network. It was assumed that the 10.0.0.0/21 subnet
would be used for the network. In addition to this, there can be additional systems installed in the
network and hence, the scope for the installation of the additional machines within the system
was also made.
Hardware Requirements for the network
For the implementation of the network the Cisco SPA122 Small Business ATA with
Router are being used. These are a product of Cisco. The price of each router is about $1000. In
addition to this the connection to the machine can be done with the help of the CAT5 cables. The
network would also require some additional switches to spread the network among the six
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK SECURITY
different departments and also within the departments. The D-Link 24 port switches can be used
in the network and cost of these switches is around $150 each.
Justification of the network design
The network that is designed is done as per the instruction of the company and the
requirement criteria provided by them. This design is very useful in proving ample amount of
security to the network and also is very helpful in dividing the network successfully into six
divisions. The network design would be useful in providing the options of authentication for the
systems and this would also effect in avoiding any type of external intrusions for the networking
system. The network would into the following sub divisions as provided below:
Information Technology- 10.0.0.0/24255.255.255.0 10.0.0.1 - 10.0.0.254 10.0.0.255
Finance Office- 10.0.1.0/25 255.255.255.128 10.0.1.1 - 10.0.1.126 10.0.1.127
Head Office- 10.0.1.128/26 255.255.255.192 10.0.1.129 - 10.0.1.190 10.0.1.191
Transport Office- 10.0.1.192/26 255.255.255.192 10.0.1.193 10.0.1.254 10.0.1.255
Research Office- 10.0.2.0/27 255.255.255.224 10.0.2.1 - 10.0.2.30 10.0.2.31
Sales Office- 10.0.2.32/27 255.255.255.224 10.0.2.33 - 10.0.2.62 10.0.2.63
In addition to this, the firewalls are installed into the network for the security of the
network and for protecting the data packets that are flowing within the network. Encryption and
decryption techniques are also incorporated within the network. The network is encrypted with
the 3 DES encryption system.
NETWORK SECURITY
different departments and also within the departments. The D-Link 24 port switches can be used
in the network and cost of these switches is around $150 each.
Justification of the network design
The network that is designed is done as per the instruction of the company and the
requirement criteria provided by them. This design is very useful in proving ample amount of
security to the network and also is very helpful in dividing the network successfully into six
divisions. The network design would be useful in providing the options of authentication for the
systems and this would also effect in avoiding any type of external intrusions for the networking
system. The network would into the following sub divisions as provided below:
Information Technology- 10.0.0.0/24255.255.255.0 10.0.0.1 - 10.0.0.254 10.0.0.255
Finance Office- 10.0.1.0/25 255.255.255.128 10.0.1.1 - 10.0.1.126 10.0.1.127
Head Office- 10.0.1.128/26 255.255.255.192 10.0.1.129 - 10.0.1.190 10.0.1.191
Transport Office- 10.0.1.192/26 255.255.255.192 10.0.1.193 10.0.1.254 10.0.1.255
Research Office- 10.0.2.0/27 255.255.255.224 10.0.2.1 - 10.0.2.30 10.0.2.31
Sales Office- 10.0.2.32/27 255.255.255.224 10.0.2.33 - 10.0.2.62 10.0.2.63
In addition to this, the firewalls are installed into the network for the security of the
network and for protecting the data packets that are flowing within the network. Encryption and
decryption techniques are also incorporated within the network. The network is encrypted with
the 3 DES encryption system.

8
NETWORK SECURITY
Conclusion
For conclusion it can be said that the security in any particular network is very
important. Main concern in our report is regarding the B2B company and the company is looking
to implement a subnetwork for their company. I am the Network Security Architect and I have
been handed the role of Network Administrator and I am responsible for designing the network
for the company. This report provides the information about the network design of the company
and also the required sub networking of the network into different divisions. This report consists
of the information about the network design and a brief discussion about the network design is
also provided in this report. The justification about the network and the hardware requirements
for the network that is to be constructed for the company is also provided in this report.
NETWORK SECURITY
Conclusion
For conclusion it can be said that the security in any particular network is very
important. Main concern in our report is regarding the B2B company and the company is looking
to implement a subnetwork for their company. I am the Network Security Architect and I have
been handed the role of Network Administrator and I am responsible for designing the network
for the company. This report provides the information about the network design of the company
and also the required sub networking of the network into different divisions. This report consists
of the information about the network design and a brief discussion about the network design is
also provided in this report. The justification about the network and the hardware requirements
for the network that is to be constructed for the company is also provided in this report.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK SECURITY
Bibliography
[1] Anandakumar, S., 2015. Image Cryptography Using RSA Algorithm in Network
Security. International Journal of Computer Science & Engineering Technology, 5(9).
[2] Bhatia, P. and Sumbaly, R., 2014. Framework for wireless network security using
quantum cryptography. arXiv preprint arXiv:1412.2495.
[3] Gill, M. and Kakkar, A.G., 2016. Wireless Sensor Network Security Using Certificateless
Cryptography (Doctoral dissertation).
[4] Joshi, M.R. and Karkade, R.A., 2015. Network security with
cryptography. IJCSMC, 4(1), pp.201-204.
[5] Kapoor, V. and Yadav, R., 2016. A Hybrid Cryptography Technique for Improving
Network Security. International Journal of Computer Applications (0975–8887) Volume.
[6] Kumar, A. and Bose, S., 2017. Cryptography and network security. Pearson Education
India.
[7] Manshaei, M.H., Zhu, Q., Alpcan, T., Bacşar, T. and Hubaux, J.P., 2013. Game theory
meets network security and privacy. ACM Computing Surveys (CSUR), 45(3), p.25.
[8] Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles
and practice (Vol. 6). London: Pearson.
[9] Van Tilborg, H.C. and Jajodia, S. eds., 2014. Encyclopedia of cryptography and security.
Springer Science & Business Media.
NETWORK SECURITY
Bibliography
[1] Anandakumar, S., 2015. Image Cryptography Using RSA Algorithm in Network
Security. International Journal of Computer Science & Engineering Technology, 5(9).
[2] Bhatia, P. and Sumbaly, R., 2014. Framework for wireless network security using
quantum cryptography. arXiv preprint arXiv:1412.2495.
[3] Gill, M. and Kakkar, A.G., 2016. Wireless Sensor Network Security Using Certificateless
Cryptography (Doctoral dissertation).
[4] Joshi, M.R. and Karkade, R.A., 2015. Network security with
cryptography. IJCSMC, 4(1), pp.201-204.
[5] Kapoor, V. and Yadav, R., 2016. A Hybrid Cryptography Technique for Improving
Network Security. International Journal of Computer Applications (0975–8887) Volume.
[6] Kumar, A. and Bose, S., 2017. Cryptography and network security. Pearson Education
India.
[7] Manshaei, M.H., Zhu, Q., Alpcan, T., Bacşar, T. and Hubaux, J.P., 2013. Game theory
meets network security and privacy. ACM Computing Surveys (CSUR), 45(3), p.25.
[8] Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles
and practice (Vol. 6). London: Pearson.
[9] Van Tilborg, H.C. and Jajodia, S. eds., 2014. Encyclopedia of cryptography and security.
Springer Science & Business Media.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





