COIT20262 Advanced Network Security: Encryption, Digital Signatures
VerifiedAdded on 2023/06/13
|10
|1732
|292
Report
AI Summary
This report delves into advanced network security concepts, beginning with an explanation of symmetric key encryption and its implementation using ciphers like AES. It further differentiates between full disk encryption and file-based encryption, weighing the trade-offs and security ramifications of each approach, especially in the context of cloud backups. The report elucidates the workings of digital signatures, highlighting their role in secure data transfer and cost reduction, alongside key management strategies for AES-256 and PKI. Additionally, it addresses the motivations of malicious users and provides real-world examples of Trojan distribution, emphasizing the importance of secure software handling and malware detection. Recommendations are provided for both software developers and end-users to enhance security practices. Desklib offers a wealth of similar solved assignments and past papers to aid students in their studies.

Running head: ADVANCED NETWORK SECURITY
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Advanced Network Security
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
ADVANCED NETWORK SECURITY
Table of Contents
Question 3..................................................................................................................................2
a) Explanation about working of symmetric key encryption file...........................................2
b) Explanation of full disk encryption, file based encryption and trade-off between two
approaches..............................................................................................................................2
c) Security ramification..........................................................................................................3
d) Working of digital signature and the problems that they solve.........................................3
e) Explanation of the keys and recommendation on managing, sharing as well as changing
keys........................................................................................................................................4
Question 4..................................................................................................................................5
a) Motivation of malicious users............................................................................................5
b) Distribution of Trojan........................................................................................................5
c) Hashes, digests or Signatures.............................................................................................5
d) Recommendation for software developer..........................................................................6
e) Recommendations for users...............................................................................................6
Bibliography...............................................................................................................................7
ADVANCED NETWORK SECURITY
Table of Contents
Question 3..................................................................................................................................2
a) Explanation about working of symmetric key encryption file...........................................2
b) Explanation of full disk encryption, file based encryption and trade-off between two
approaches..............................................................................................................................2
c) Security ramification..........................................................................................................3
d) Working of digital signature and the problems that they solve.........................................3
e) Explanation of the keys and recommendation on managing, sharing as well as changing
keys........................................................................................................................................4
Question 4..................................................................................................................................5
a) Motivation of malicious users............................................................................................5
b) Distribution of Trojan........................................................................................................5
c) Hashes, digests or Signatures.............................................................................................5
d) Recommendation for software developer..........................................................................6
e) Recommendations for users...............................................................................................6
Bibliography...............................................................................................................................7
2
ADVANCED NETWORK SECURITY
Question 3
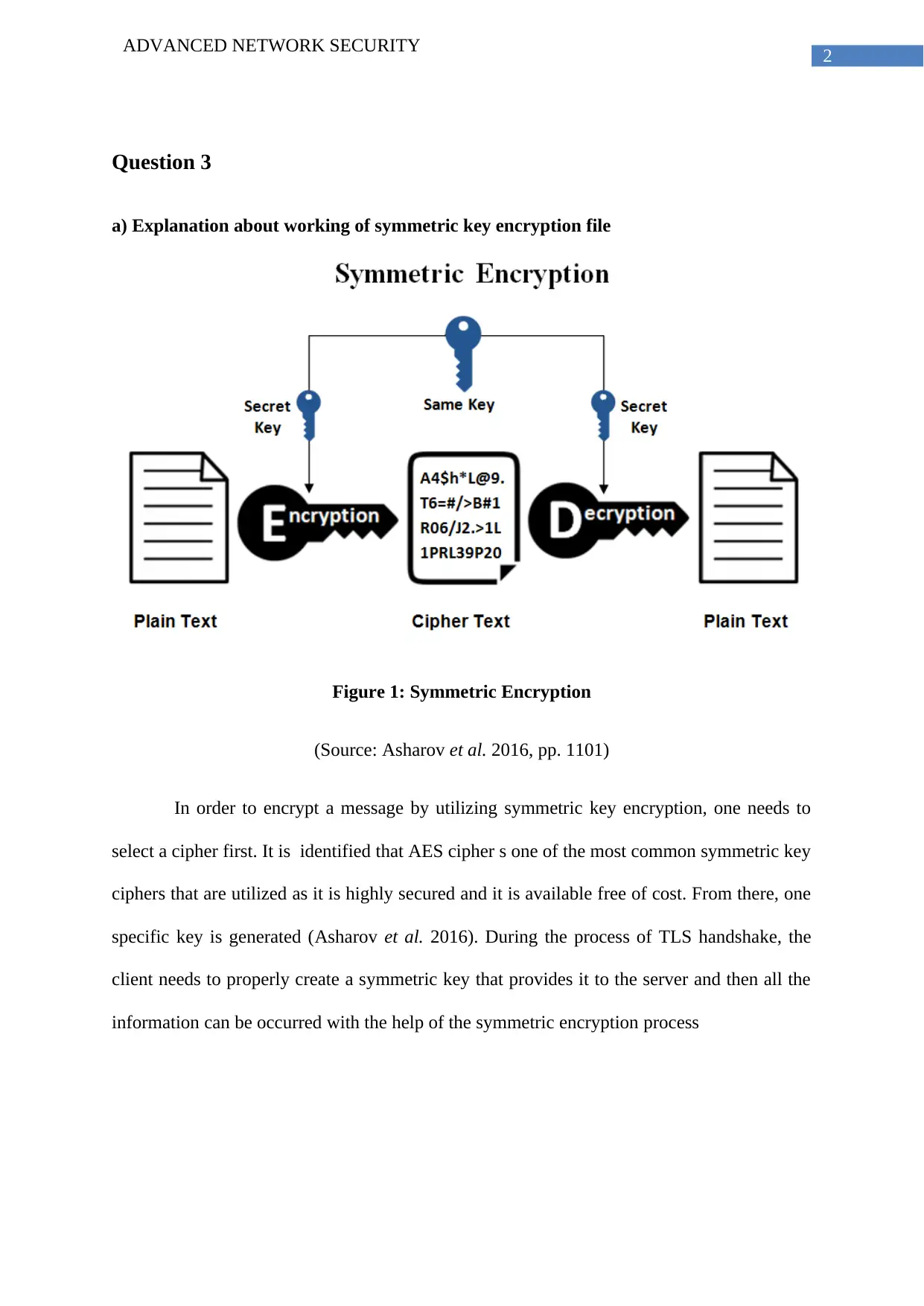
a) Explanation about working of symmetric key encryption file
Figure 1: Symmetric Encryption
(Source: Asharov et al. 2016, pp. 1101)
In order to encrypt a message by utilizing symmetric key encryption, one needs to
select a cipher first. It is identified that AES cipher s one of the most common symmetric key
ciphers that are utilized as it is highly secured and it is available free of cost. From there, one
specific key is generated (Asharov et al. 2016). During the process of TLS handshake, the
client needs to properly create a symmetric key that provides it to the server and then all the
information can be occurred with the help of the symmetric encryption process
ADVANCED NETWORK SECURITY
Question 3
a) Explanation about working of symmetric key encryption file
Figure 1: Symmetric Encryption
(Source: Asharov et al. 2016, pp. 1101)
In order to encrypt a message by utilizing symmetric key encryption, one needs to
select a cipher first. It is identified that AES cipher s one of the most common symmetric key
ciphers that are utilized as it is highly secured and it is available free of cost. From there, one
specific key is generated (Asharov et al. 2016). During the process of TLS handshake, the
client needs to properly create a symmetric key that provides it to the server and then all the
information can be occurred with the help of the symmetric encryption process
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
ADVANCED NETWORK SECURITY
b) Explanation of full disk encryption, file based encryption and trade-off between two
approaches
Full disk encryption
Full disk encryption is considered as one type of encryption that generally occurs at
hardware level. It generally works automatically in order to convert data on a hard drive in
such a form that the individual who does not have proper key for doing conversion cannot be
able to understand (Garg et al. 2016). It is found that without appropriate authentication key
the data cannot be accessed even if the hard drive is removed. In this type of encryption,
when the computer is powered on then there is no protection against the various unauthorized
users.
File based encryption
In file-based encryption, all the files are encrypted by utilizing the same procedure
like full disk encryption but in addition to this, it mainly consist of one of the special
functionality according to which only a specific user can be able to access the data (Garg et
al. 2016). It is identified that this type of encryption process mainly occurs during offline
operation. It also helps in providing proper access control mechanism.
Best selected approach between both
It is identified that file encryption procedure is one of the best solution for the
organization that generally deals with the client. This is because every time they are dealing
with the customers they have access the file server in order to get data and information. File
level encryption generally assists in providing proper access control encryption functionality
that is considered quite advantageous for the organizations.
ADVANCED NETWORK SECURITY
b) Explanation of full disk encryption, file based encryption and trade-off between two
approaches
Full disk encryption
Full disk encryption is considered as one type of encryption that generally occurs at
hardware level. It generally works automatically in order to convert data on a hard drive in
such a form that the individual who does not have proper key for doing conversion cannot be
able to understand (Garg et al. 2016). It is found that without appropriate authentication key
the data cannot be accessed even if the hard drive is removed. In this type of encryption,
when the computer is powered on then there is no protection against the various unauthorized
users.
File based encryption
In file-based encryption, all the files are encrypted by utilizing the same procedure
like full disk encryption but in addition to this, it mainly consist of one of the special
functionality according to which only a specific user can be able to access the data (Garg et
al. 2016). It is identified that this type of encryption process mainly occurs during offline
operation. It also helps in providing proper access control mechanism.
Best selected approach between both
It is identified that file encryption procedure is one of the best solution for the
organization that generally deals with the client. This is because every time they are dealing
with the customers they have access the file server in order to get data and information. File
level encryption generally assists in providing proper access control encryption functionality
that is considered quite advantageous for the organizations.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
ADVANCED NETWORK SECURITY
c) Security ramification
It is found that backing up file server to the cloud can create number of security
ramifications within the company. One such security ramification that can occur is due to
retrieval of data as well as information from the cloud. During the process of data retrieval
from the cloud, there are chances of security ramification.
d) Working of digital signature and the problems that they solve
Digital signatures are unique to the signers as handwritten signatures. It is identified
that digital signatures solution providers generally follows a specific protocol that is known
as PKI. The PKI generally needs a provider in order to utilize proper mathematical algorithm
that generally helps in generating two numbers that is one private key and other is public key
(Donaldson et al. 2016). When a signer enters within a document the signature is mainly
generated with the help of the private key that is totally secured from the signer. The
mathematical algorithm that is present generally works a cipher in order to create appropriate
data matching. The resulting data that is encrypted is the digital signature. The signatures are
generally marked with time that the entire document was signed and if the document changes,
the digital signature is considered invalidated.
ADVANCED NETWORK SECURITY
c) Security ramification
It is found that backing up file server to the cloud can create number of security
ramifications within the company. One such security ramification that can occur is due to
retrieval of data as well as information from the cloud. During the process of data retrieval
from the cloud, there are chances of security ramification.
d) Working of digital signature and the problems that they solve
Digital signatures are unique to the signers as handwritten signatures. It is identified
that digital signatures solution providers generally follows a specific protocol that is known
as PKI. The PKI generally needs a provider in order to utilize proper mathematical algorithm
that generally helps in generating two numbers that is one private key and other is public key
(Donaldson et al. 2016). When a signer enters within a document the signature is mainly
generated with the help of the private key that is totally secured from the signer. The
mathematical algorithm that is present generally works a cipher in order to create appropriate
data matching. The resulting data that is encrypted is the digital signature. The signatures are
generally marked with time that the entire document was signed and if the document changes,
the digital signature is considered invalidated.

5
ADVANCED NETWORK SECURITY
Figure 2: Digital signature working
(Source: Markowsky 2015, pp.410)
Digital signature mainly helps the organization in transferring both information as
well as data with the help of internet. It also helps the organization in reducing the utilization
of paper and assists in saving both time and money.
e) Explanation of the keys and recommendation on managing, sharing as well as
changing keys
It is found that the company will generally utilize AES-256 for the file servers and
PKI for the digital signatures.
It is identified that automated key management can be utilized in any of the condition
that is elaborated below:
A party requires to handle n^2 static keys where n is considered large
Any of the stream cipher lie AES-CTR [NIST], AES-CTR [NIST] or RC4 [TK], can
be utilized
An initiation vector can be used again especially in hidden IV. It is found that pseudo
random explicit IV or random is not considered as a problem unless there is high
probability of repetition
Large amount of data required encryption in a very much short time that causes
regular change in context to short session key.
ADVANCED NETWORK SECURITY
Figure 2: Digital signature working
(Source: Markowsky 2015, pp.410)
Digital signature mainly helps the organization in transferring both information as
well as data with the help of internet. It also helps the organization in reducing the utilization
of paper and assists in saving both time and money.
e) Explanation of the keys and recommendation on managing, sharing as well as
changing keys
It is found that the company will generally utilize AES-256 for the file servers and
PKI for the digital signatures.
It is identified that automated key management can be utilized in any of the condition
that is elaborated below:
A party requires to handle n^2 static keys where n is considered large
Any of the stream cipher lie AES-CTR [NIST], AES-CTR [NIST] or RC4 [TK], can
be utilized
An initiation vector can be used again especially in hidden IV. It is found that pseudo
random explicit IV or random is not considered as a problem unless there is high
probability of repetition
Large amount of data required encryption in a very much short time that causes
regular change in context to short session key.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
ADVANCED NETWORK SECURITY
Question 4
a) Motivation of malicious users
The main motivation of the malicious users is to access data for stealing it. The
attackers can delete, modify or block the data of the users (Yang, He and Shi 2017).
b) Distribution of Trojan
Example 1: Google play store distributes Trojan horse
On 1st April 2016, the research team at Russian Security added Trojan and it is found
by the malware experts that Trojan is mainly available for 104 android application for
download within the play store, which mainly affected 3.2 million users.
Example 2: Trojan (Coldroot RAT) found in Github
A remote access Trojan that was uploaded by Github freely, it affected Linux, Mac
and windows users. It was available for almost 2 years on Github and firstly detected on fake
audio driver of Apple in 2016.
c) Hashes, digests or Signatures
Hashes or Signatures technique is defined as a process that helps in producing a
secure of data that will be helpful in downloading data as well as information securely. The
digest is fund as a size of numeric presentation of various data that is mainly computed by
utilizing hash function after utilizing the procedure of encryption for forming signatures. I is
suggested to key the main private key properly because if the main key is lost then the data
cannot be accessed.
d) Recommendation for software developer
The recommendations for the software developer include:
ADVANCED NETWORK SECURITY
Question 4
a) Motivation of malicious users
The main motivation of the malicious users is to access data for stealing it. The
attackers can delete, modify or block the data of the users (Yang, He and Shi 2017).
b) Distribution of Trojan
Example 1: Google play store distributes Trojan horse
On 1st April 2016, the research team at Russian Security added Trojan and it is found
by the malware experts that Trojan is mainly available for 104 android application for
download within the play store, which mainly affected 3.2 million users.
Example 2: Trojan (Coldroot RAT) found in Github
A remote access Trojan that was uploaded by Github freely, it affected Linux, Mac
and windows users. It was available for almost 2 years on Github and firstly detected on fake
audio driver of Apple in 2016.
c) Hashes, digests or Signatures
Hashes or Signatures technique is defined as a process that helps in producing a
secure of data that will be helpful in downloading data as well as information securely. The
digest is fund as a size of numeric presentation of various data that is mainly computed by
utilizing hash function after utilizing the procedure of encryption for forming signatures. I is
suggested to key the main private key properly because if the main key is lost then the data
cannot be accessed.
d) Recommendation for software developer
The recommendations for the software developer include:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ADVANCED NETWORK SECURITY
The software developer must encrypt the software
The software developer must compress the distributed software.
e) Recommendations for users
The recommendations that are provided to the users include:
Utilization of secure process: It is very much important for the users to utilize
proper as well as secure procedure for downloading software
Utilization of malware detection system: It is necessary to utilize malware detection
system in order to protect data from malware
Review of website: The first priority of the users is to review the website properly
before downloading the software.
ADVANCED NETWORK SECURITY
The software developer must encrypt the software
The software developer must compress the distributed software.
e) Recommendations for users
The recommendations that are provided to the users include:
Utilization of secure process: It is very much important for the users to utilize
proper as well as secure procedure for downloading software
Utilization of malware detection system: It is necessary to utilize malware detection
system in order to protect data from malware
Review of website: The first priority of the users is to review the website properly
before downloading the software.

8
ADVANCED NETWORK SECURITY
Bibliography
Asharov, G., Naor, M., Segev, G. and Shahaf, I., 2016, June. Searchable symmetric
encryption: Optimal locality in linear space via two-dimensional balanced allocations.
In Proceedings of the forty-eighth annual ACM symposium on Theory of Computing (pp.
1101-1114). ACM.
Donaldson, R.J., Collins, R.J., Kleczkowska, K., Amiri, R., Wallden, P., Dunjko, V., Jeffers,
J., Andersson, E. and Buller, G.S., 2016. Experimental demonstration of kilometer-range
quantum digital signatures. Physical Review A, 93(1), p.012329.
Garg, S., Gentry, C., Halevi, S., Raykova, M., Sahai, A. and Waters, B., 2016. Candidate
indistinguishability obfuscation and functional encryption for all circuits. SIAM Journal on
Computing, 45(3), pp.882-929.
Hassan, N.H. and Ismail, Z., 2015. A Conceptual Model Towards Information Security
Culture in Health Informatics. In The Malaysia-Japan Model on Technology Partnership (pp.
187-196). Springer, Tokyo.
Jain, N., Stiller, B., Khan, I., Makarov, V., Marquardt, C. and Leuchs, G., 2015. Risk analysis
of Trojan-horse attacks on practical quantum key distribution systems. IEEE Journal of
Selected Topics in Quantum Electronics, 21(3), pp.168-177.
Markowsky, G., 2015, September. The problem of interceptor top level domains.
In Intelligent Data Acquisition and Advanced Computing Systems: Technology and
Applications (IDAACS), 2015 IEEE 8th International Conference on (Vol. 1, pp. 424-428).
IEEE.
ADVANCED NETWORK SECURITY
Bibliography
Asharov, G., Naor, M., Segev, G. and Shahaf, I., 2016, June. Searchable symmetric
encryption: Optimal locality in linear space via two-dimensional balanced allocations.
In Proceedings of the forty-eighth annual ACM symposium on Theory of Computing (pp.
1101-1114). ACM.
Donaldson, R.J., Collins, R.J., Kleczkowska, K., Amiri, R., Wallden, P., Dunjko, V., Jeffers,
J., Andersson, E. and Buller, G.S., 2016. Experimental demonstration of kilometer-range
quantum digital signatures. Physical Review A, 93(1), p.012329.
Garg, S., Gentry, C., Halevi, S., Raykova, M., Sahai, A. and Waters, B., 2016. Candidate
indistinguishability obfuscation and functional encryption for all circuits. SIAM Journal on
Computing, 45(3), pp.882-929.
Hassan, N.H. and Ismail, Z., 2015. A Conceptual Model Towards Information Security
Culture in Health Informatics. In The Malaysia-Japan Model on Technology Partnership (pp.
187-196). Springer, Tokyo.
Jain, N., Stiller, B., Khan, I., Makarov, V., Marquardt, C. and Leuchs, G., 2015. Risk analysis
of Trojan-horse attacks on practical quantum key distribution systems. IEEE Journal of
Selected Topics in Quantum Electronics, 21(3), pp.168-177.
Markowsky, G., 2015, September. The problem of interceptor top level domains.
In Intelligent Data Acquisition and Advanced Computing Systems: Technology and
Applications (IDAACS), 2015 IEEE 8th International Conference on (Vol. 1, pp. 424-428).
IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
ADVANCED NETWORK SECURITY
Yang, G., He, S. and Shi, Z., 2017. Leveraging crowdsourcing for efficient malicious users
detection in large-scale social networks. IEEE Internet of Things Journal, 4(2), pp.330-339.
ADVANCED NETWORK SECURITY
Yang, G., He, S. and Shi, Z., 2017. Leveraging crowdsourcing for efficient malicious users
detection in large-scale social networks. IEEE Internet of Things Journal, 4(2), pp.330-339.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


