Network Security: Threats, Solutions, and Implementation Strategies
VerifiedAdded on 2023/04/03
|17
|3645
|241
Report
AI Summary
This report provides a comprehensive overview of network security, focusing on the importance of securing systems against unauthorized access and risks. It delves into various aspects of network security, including the use of firewalls, intrusion detection systems, and VPNs. The report discusses the different types of firewalls, such as packet filters, stateful inspection firewalls, and circuit-level gateways, along with their respective security threats like IP spoofing and source routing attacks. It also highlights the significance of software tools like antivirus and intrusion detection systems in safeguarding computer systems. The report further emphasizes the importance of proper firewall configuration, addressing issues such as missed security patches and configuration mistakes. Finally, it covers the design and implementation of network security systems, including the use of VPNs to ensure secure connections. This report aims to provide a thorough understanding of network security principles and practices, equipping readers with the knowledge to protect their networks effectively.

TITLE: NETWORK SECURITY
Network Security
Network Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Peixiao, Chopra, Wing, Ganti, Corde, & Patil
2019).
Introduction
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way. Missed Security Patches is problem caused by poor management of the
network firewall software. Attackers always check the possible vulnerabilities and this might be
their gateway. IT and Network experts should always be careful and alert of the firewall tools since
it can cause significant problems. The vendors can assist fix some problems experienced on the
software. Management schedules must be set so as to allow careful monitoring and updating the
network firewalls no matter the situation whether there is attack or not (Yu, Qi, & Li, 2019).
Circuit-Level Gateways is more advanced application gateway and it works at the session layer of
the OSI Model. The significance of this gateway is it acts as the virtual connections between the
internal users and the remote host. It achieve it by creating connection between itself and the remote
host. It also secures and hides the IP addresses of the end users on the packets by removing and
adding its own IP address hence preventing the exposure of the IP addresses of the internal users
from the outside world. This secures so many threads that would have been received if the IP
address is exposed. Firewall is a type of network security system which monitors and controls
network traffic flowing in and out of network according to the network protocols. It acts as a wall
barrier between the internal network and the internet. Firewall can be in form of software or
hardware appliances. Hardware-based act as DHCP server from that network. In most cases experts
prefer software-based firewalls because it secures data from the internet threads. Routers uses
software-based firewalls since the data being transferred from one network to another must pass
internet hence it can also performs routing protocols. Firewalls are mainly used in private networks
to prevent any trouble of unauthorized access which maybe through internet. All the messages
moving in and out of intranet network must me examined and security measures checked by the
firewalls. Secured firewall configurations consist of both hardware and software devices. It is very
important type of security measures in the computer network (Peixiao, Chopra, Wing, Ganti, Corde,
& Patil 2019).
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Peixiao, Chopra, Wing, Ganti, Corde, & Patil
2019).
Introduction
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way. Missed Security Patches is problem caused by poor management of the
network firewall software. Attackers always check the possible vulnerabilities and this might be
their gateway. IT and Network experts should always be careful and alert of the firewall tools since
it can cause significant problems. The vendors can assist fix some problems experienced on the
software. Management schedules must be set so as to allow careful monitoring and updating the
network firewalls no matter the situation whether there is attack or not (Yu, Qi, & Li, 2019).
Circuit-Level Gateways is more advanced application gateway and it works at the session layer of
the OSI Model. The significance of this gateway is it acts as the virtual connections between the
internal users and the remote host. It achieve it by creating connection between itself and the remote
host. It also secures and hides the IP addresses of the end users on the packets by removing and
adding its own IP address hence preventing the exposure of the IP addresses of the internal users
from the outside world. This secures so many threads that would have been received if the IP
address is exposed. Firewall is a type of network security system which monitors and controls
network traffic flowing in and out of network according to the network protocols. It acts as a wall
barrier between the internal network and the internet. Firewall can be in form of software or
hardware appliances. Hardware-based act as DHCP server from that network. In most cases experts
prefer software-based firewalls because it secures data from the internet threads. Routers uses
software-based firewalls since the data being transferred from one network to another must pass
internet hence it can also performs routing protocols. Firewalls are mainly used in private networks
to prevent any trouble of unauthorized access which maybe through internet. All the messages
moving in and out of intranet network must me examined and security measures checked by the
firewalls. Secured firewall configurations consist of both hardware and software devices. It is very
important type of security measures in the computer network (Peixiao, Chopra, Wing, Ganti, Corde,
& Patil 2019).

Network security system threads and requirements
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Yu, Qi, & Li, 2019).
Software tools such as antivirus can be used to detect and remove any malicious software in the
computer systems. Sometimes we might download software in one way or another with or without
knowledge. Therefore, antivirus will help us remove such malicious software build by hackers to
still personal information. This has really help a lot because while busy in computer then you can
mistakenly click download to anything on the screen. Modern antivirus nowadays do much more
than only protection from viruses but also from worms, Trojan-horses, spyware, among other
malicious programs .Caution must be taken to ensure computer data are save (Alm, 2019).
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
network to save IP address blockage in case there is no one to respond to such alerts. It can also
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Yu, Qi, & Li, 2019).
Software tools such as antivirus can be used to detect and remove any malicious software in the
computer systems. Sometimes we might download software in one way or another with or without
knowledge. Therefore, antivirus will help us remove such malicious software build by hackers to
still personal information. This has really help a lot because while busy in computer then you can
mistakenly click download to anything on the screen. Modern antivirus nowadays do much more
than only protection from viruses but also from worms, Trojan-horses, spyware, among other
malicious programs .Caution must be taken to ensure computer data are save (Alm, 2019).
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
network to save IP address blockage in case there is no one to respond to such alerts. It can also
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
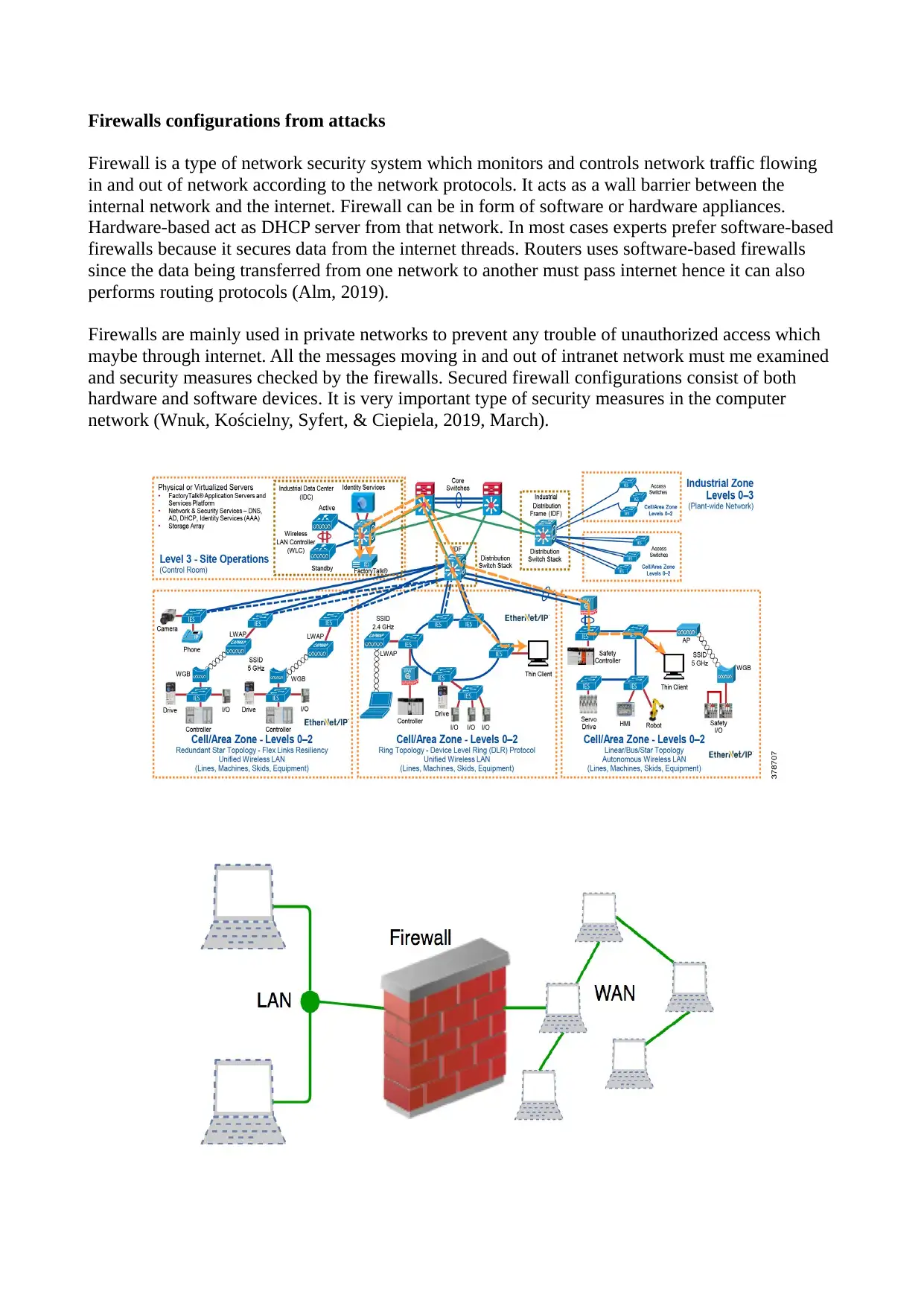
Firewalls configurations from attacks
Firewall is a type of network security system which monitors and controls network traffic flowing
in and out of network according to the network protocols. It acts as a wall barrier between the
internal network and the internet. Firewall can be in form of software or hardware appliances.
Hardware-based act as DHCP server from that network. In most cases experts prefer software-based
firewalls because it secures data from the internet threads. Routers uses software-based firewalls
since the data being transferred from one network to another must pass internet hence it can also
performs routing protocols (Alm, 2019).
Firewalls are mainly used in private networks to prevent any trouble of unauthorized access which
maybe through internet. All the messages moving in and out of intranet network must me examined
and security measures checked by the firewalls. Secured firewall configurations consist of both
hardware and software devices. It is very important type of security measures in the computer
network (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
Firewall is a type of network security system which monitors and controls network traffic flowing
in and out of network according to the network protocols. It acts as a wall barrier between the
internal network and the internet. Firewall can be in form of software or hardware appliances.
Hardware-based act as DHCP server from that network. In most cases experts prefer software-based
firewalls because it secures data from the internet threads. Routers uses software-based firewalls
since the data being transferred from one network to another must pass internet hence it can also
performs routing protocols (Alm, 2019).
Firewalls are mainly used in private networks to prevent any trouble of unauthorized access which
maybe through internet. All the messages moving in and out of intranet network must me examined
and security measures checked by the firewalls. Secured firewall configurations consist of both
hardware and software devices. It is very important type of security measures in the computer
network (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Types of Firewalls
1) Packet Filters
Packet Filters works in network layer of OSI model. It uses set of rules where it will have to decide
whether to forward or discard messages through the network. For instance, it can make a decision of
blocking or disallow all the data transfer from specific IP address or all traffic from UDP protocol.
In other scenarios it may make default decisions of allowing all or discarding all of the packets in
the network (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
Security threats to Packet Filters:
a) IP address spoofing:
In this situation, the malicious attackers sends a packet to the intranet network using the same IP
address as the internal users IP address. Firewalls can overcome this by not allowing any packet
from outside the internal network to be received by internal users from internet (Alm, 2019).
1) Packet Filters
Packet Filters works in network layer of OSI model. It uses set of rules where it will have to decide
whether to forward or discard messages through the network. For instance, it can make a decision of
blocking or disallow all the data transfer from specific IP address or all traffic from UDP protocol.
In other scenarios it may make default decisions of allowing all or discarding all of the packets in
the network (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
Security threats to Packet Filters:
a) IP address spoofing:
In this situation, the malicious attackers sends a packet to the intranet network using the same IP
address as the internal users IP address. Firewalls can overcome this by not allowing any packet
from outside the internal network to be received by internal users from internet (Alm, 2019).
b) Source routing attack:
In this kind of attack, the attacker specifies the route to send the packet with the hope of tricking the
firewall to allow packet transfer. Firewall will overcome this situation by just discarding all the
packets which tries to use source routing options (Peixiao, Chopra, Wing, Ganti, Corde, & Patil
2019).
2) Stateful Inspection Firewalls
It is also referred to as 'Dynamic Packet Filters'. It is always keep it self to active connections and
this will allow them to decide which packet to allow for the transfer. Due to this state of
functioning, it adapts itself current information exchange in the network and starts to work
according to the network function. This is the modern way not like the previous versions of
hardcore and stateless filters (Yu, Qi, & Li, 2019).
In this kind of attack, the attacker specifies the route to send the packet with the hope of tricking the
firewall to allow packet transfer. Firewall will overcome this situation by just discarding all the
packets which tries to use source routing options (Peixiao, Chopra, Wing, Ganti, Corde, & Patil
2019).
2) Stateful Inspection Firewalls
It is also referred to as 'Dynamic Packet Filters'. It is always keep it self to active connections and
this will allow them to decide which packet to allow for the transfer. Due to this state of
functioning, it adapts itself current information exchange in the network and starts to work
according to the network function. This is the modern way not like the previous versions of
hardcore and stateless filters (Yu, Qi, & Li, 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3) Circuit-Level Gateways
This is more advanced application gateway and it works at the session layer of the OSI Model. The
significance of this gateway is it acts as the virtual connections between the internal users and the
remote host. It achieve it by creating connection between itself and the remote host. It also secures
and hides the IP addresses of the end users on the packets by removing and adding its own IP
address hence preventing the exposure of the IP addresses of the internal users from the outside
world. This secures so many threads that would have been received if the IP address is exposed
(Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
4) Missed Security Patches
This problem is caused by poor management of the network firewall software. Attackers always
check the possible vulnerabilities and this might be their gateway. IT and Network experts should
always be careful and alert of the firewall tools since it can cause significant problems. The vendors
can assist fix some problems experienced on the software. Management schedules must be set so as
to allow careful monitoring and updating the network firewalls no matter the situation whether there
is attack or not (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
This is more advanced application gateway and it works at the session layer of the OSI Model. The
significance of this gateway is it acts as the virtual connections between the internal users and the
remote host. It achieve it by creating connection between itself and the remote host. It also secures
and hides the IP addresses of the end users on the packets by removing and adding its own IP
address hence preventing the exposure of the IP addresses of the internal users from the outside
world. This secures so many threads that would have been received if the IP address is exposed
(Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
4) Missed Security Patches
This problem is caused by poor management of the network firewall software. Attackers always
check the possible vulnerabilities and this might be their gateway. IT and Network experts should
always be careful and alert of the firewall tools since it can cause significant problems. The vendors
can assist fix some problems experienced on the software. Management schedules must be set so as
to allow careful monitoring and updating the network firewalls no matter the situation whether there
is attack or not (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
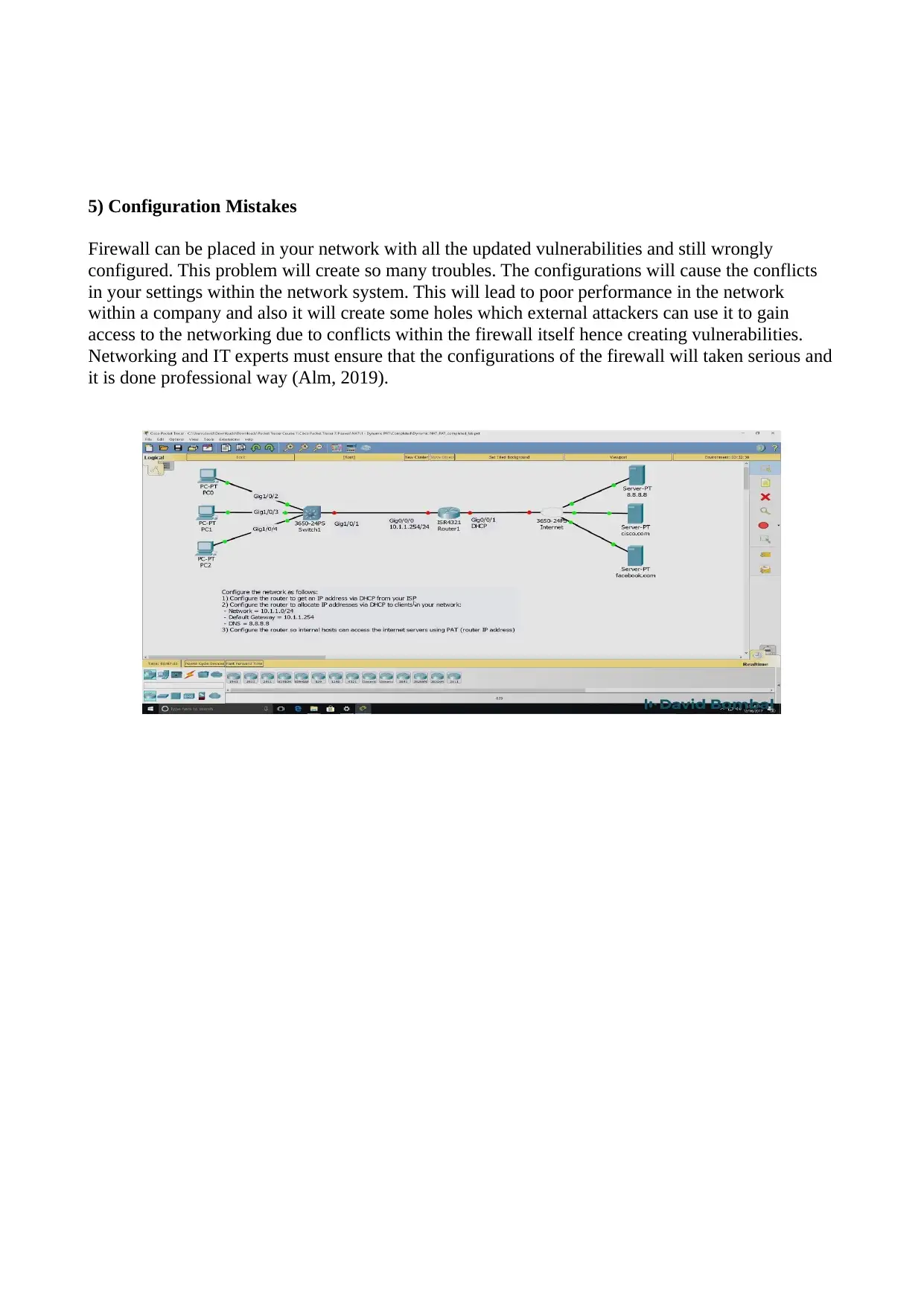
5) Configuration Mistakes
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way (Alm, 2019).
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way (Alm, 2019).

Designing and implementation of network security systems
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Yu, Qi, & Li, 2019).
Designing of network security system
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
network to save IP address blockage in case there is no one to respond to such alerts. It can also
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors. A virtual private network (VPN) is programming that guarantee safety and
encryption of connection in a very less secured network. A VPN functions in a public internet while
it strictly maintain the privacy through procedures. VPN encrypts the data from the sender and also
decrypt to the receiver, the network tunnel which the data is transferred cannot in anyway tamper
the data because encryption is very secured and they are not vulnerable. Also the network addresses
can also be presented by VPN (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
Firewall is a type of network security system which monitors and controls network traffic flowing
in and out of network according to the network protocols. It acts as a wall barrier between the
internal network and the internet. Firewall can be in form of software or hardware appliances.
Hardware-based act as DHCP server from that network. In most cases experts prefer software-based
firewalls because it secures data from the internet threads. Routers uses software-based firewalls
since the data being transferred from one network to another must pass internet hence it can also
performs routing protocols (Alm, 2019).
Software tools such as antivirus can be used to detect and remove any malicious software in the
computer systems. Sometimes we might download software in one way or another with or without
knowledge. Therefore, antivirus will help us remove such malicious software build by hackers to
still personal information. This has really help a lot because while busy in computer then you can
mistakenly click download to anything on the screen. Modern antivirus nowadays do much more
than only protection from viruses but also from worms, Trojan-horses, spyware, among other
malicious programs .Caution must be taken to ensure computer data are save (Laborde, Bulusu,
Wazan, Barrère, & Benzekri, 2019, April).
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
Network security is the safety that is implemented to the systems to prevent them from
unauthorized access and risks. IT and Networking experts must ensure that there networks are very
secured from any external attack. In our daily life's, computers or phones uses network to make
transactions, communicate sensitive information, among other issues. Therefore a very secured
network should be ensured to prevent any data lose or breach in any case. If malicious hackers will
gain access then it will lead to great loses in a business. Security measures in computer networks
should be take to first priority among other securities (Yu, Qi, & Li, 2019).
Designing of network security system
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
network to save IP address blockage in case there is no one to respond to such alerts. It can also
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors. A virtual private network (VPN) is programming that guarantee safety and
encryption of connection in a very less secured network. A VPN functions in a public internet while
it strictly maintain the privacy through procedures. VPN encrypts the data from the sender and also
decrypt to the receiver, the network tunnel which the data is transferred cannot in anyway tamper
the data because encryption is very secured and they are not vulnerable. Also the network addresses
can also be presented by VPN (Peixiao, Chopra, Wing, Ganti, Corde, & Patil 2019).
Firewall is a type of network security system which monitors and controls network traffic flowing
in and out of network according to the network protocols. It acts as a wall barrier between the
internal network and the internet. Firewall can be in form of software or hardware appliances.
Hardware-based act as DHCP server from that network. In most cases experts prefer software-based
firewalls because it secures data from the internet threads. Routers uses software-based firewalls
since the data being transferred from one network to another must pass internet hence it can also
performs routing protocols (Alm, 2019).
Software tools such as antivirus can be used to detect and remove any malicious software in the
computer systems. Sometimes we might download software in one way or another with or without
knowledge. Therefore, antivirus will help us remove such malicious software build by hackers to
still personal information. This has really help a lot because while busy in computer then you can
mistakenly click download to anything on the screen. Modern antivirus nowadays do much more
than only protection from viruses but also from worms, Trojan-horses, spyware, among other
malicious programs .Caution must be taken to ensure computer data are save (Laborde, Bulusu,
Wazan, Barrère, & Benzekri, 2019, April).
Intrusion detection systems are more advanced system software. Their main function is to monitor
and analyze malicious activities taking place in network then gives out the details about such
information by reporting them. They are also able to send any alerts to the experts about any
malicious activities taking place in the network. It can also do the resetting of connections in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
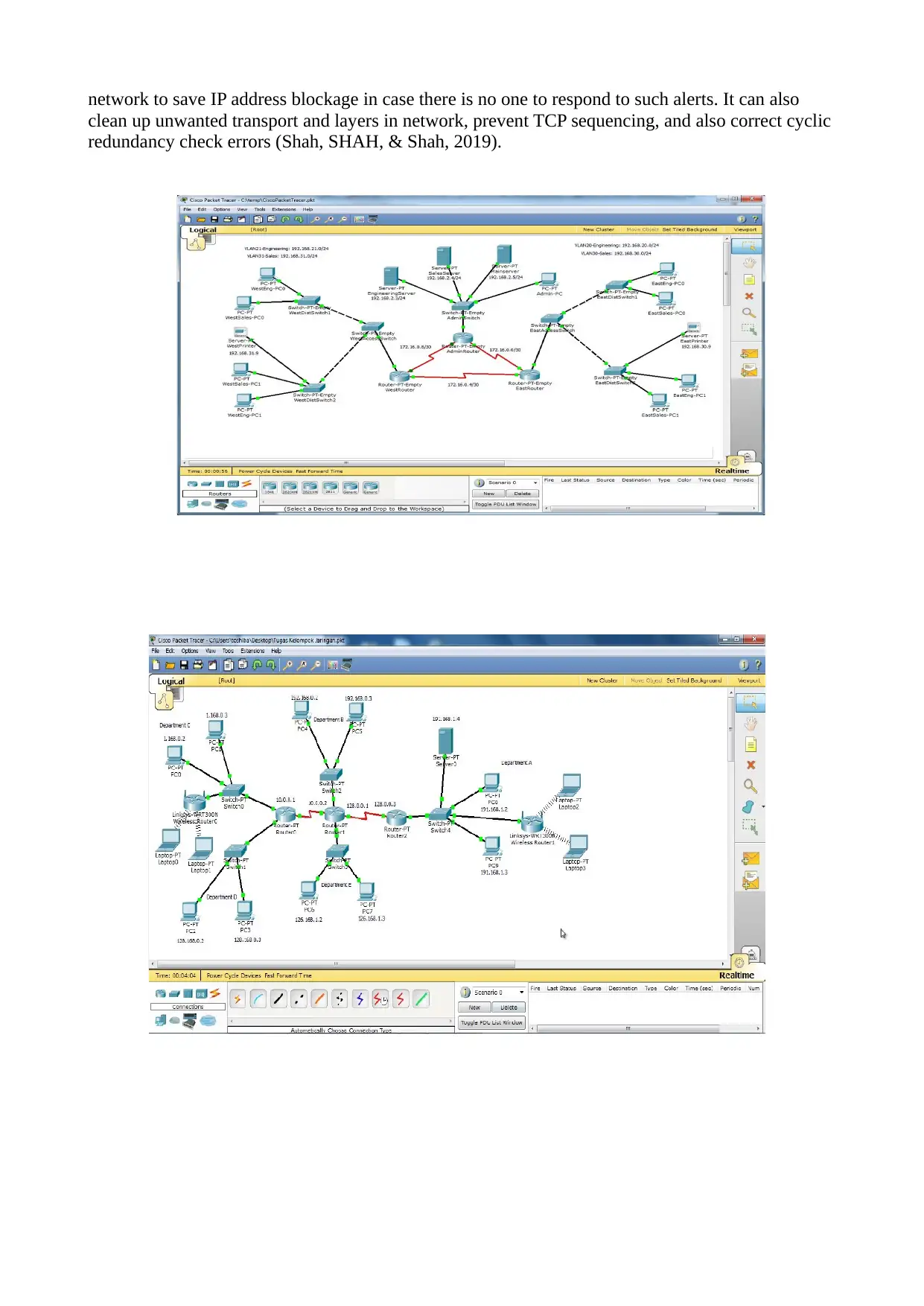
network to save IP address blockage in case there is no one to respond to such alerts. It can also
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors (Shah, SHAH, & Shah, 2019).
clean up unwanted transport and layers in network, prevent TCP sequencing, and also correct cyclic
redundancy check errors (Shah, SHAH, & Shah, 2019).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Implementation of network design
IP address spoofing. In this situation, the malicious attackers sends a packet to the intranet network
using the same IP address as the internal users IP address. Firewalls can overcome this by not
allowing any packet from outside the internal network to be received by internal users from internet.
Source routing attack is a kind of attack where the attacker specifies the route to send the packet
with the hope of tricking the firewall to allow packet transfer. Firewall will overcome this situation
by just discarding all the packets which tries to use source routing options. Stateful Inspection
Firewalls also referred to as 'Dynamic Packet Filters'. It is always keep it self to active connections
and this will allow them to decide which packet to allow for the transfer. Due to this state of
functioning, it adapts itself current information exchange in the network and starts to work
according to the network function. This is the modern way not like the previous versions of
hardcore and stateless filters (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way. Missed Security Patches is problem caused by poor management of the
network firewall software. Attackers always check the possible vulnerabilities and this might be
their gateway. IT and Network experts should always be careful and alert of the firewall tools since
it can cause significant problems. The vendors can assist fix some problems experienced on the
software. Management schedules must be set so as to allow careful monitoring and updating the
network firewalls no matter the situation whether there is attack or not. Circuit-Level Gateways is
more advanced application gateway and it works at the session layer of the OSI Model. The
significance of this gateway is it acts as the virtual connections between the internal users and the
remote host. It achieve it by creating connection between itself and the remote host. It also secures
and hides the IP addresses of the end users on the packets by removing and adding its own IP
address hence preventing the exposure of the IP addresses of the internal users from the outside
world. This secures so many threads that would have been received if the IP address is exposed
(Laborde, Bulusu, Wazan, Barrère, & Benzekri, 2019, April).
IP address spoofing. In this situation, the malicious attackers sends a packet to the intranet network
using the same IP address as the internal users IP address. Firewalls can overcome this by not
allowing any packet from outside the internal network to be received by internal users from internet.
Source routing attack is a kind of attack where the attacker specifies the route to send the packet
with the hope of tricking the firewall to allow packet transfer. Firewall will overcome this situation
by just discarding all the packets which tries to use source routing options. Stateful Inspection
Firewalls also referred to as 'Dynamic Packet Filters'. It is always keep it self to active connections
and this will allow them to decide which packet to allow for the transfer. Due to this state of
functioning, it adapts itself current information exchange in the network and starts to work
according to the network function. This is the modern way not like the previous versions of
hardcore and stateless filters (Wnuk, Kościelny, Syfert, & Ciepiela, 2019, March).
Firewall can be placed in your network with all the updated vulnerabilities and still wrongly
configured. This problem will create so many troubles. The configurations will cause the conflicts
in your settings within the network system. This will lead to poor performance in the network
within a company and also it will create some holes which external attackers can use it to gain
access to the networking due to conflicts within the firewall itself hence creating vulnerabilities.
Networking and IT experts must ensure that the configurations of the firewall will taken serious and
it is done professional way. Missed Security Patches is problem caused by poor management of the
network firewall software. Attackers always check the possible vulnerabilities and this might be
their gateway. IT and Network experts should always be careful and alert of the firewall tools since
it can cause significant problems. The vendors can assist fix some problems experienced on the
software. Management schedules must be set so as to allow careful monitoring and updating the
network firewalls no matter the situation whether there is attack or not. Circuit-Level Gateways is
more advanced application gateway and it works at the session layer of the OSI Model. The
significance of this gateway is it acts as the virtual connections between the internal users and the
remote host. It achieve it by creating connection between itself and the remote host. It also secures
and hides the IP addresses of the end users on the packets by removing and adding its own IP
address hence preventing the exposure of the IP addresses of the internal users from the outside
world. This secures so many threads that would have been received if the IP address is exposed
(Laborde, Bulusu, Wazan, Barrère, & Benzekri, 2019, April).

Implementation of Virtual Private Network (VPN)
A virtual private network (VPN) is programming that guarantee safety and encryption of connection
in a very less secured network. A VPN functions in a public internet while it strictly maintain the
privacy through procedures. VPN encrypts the data from the sender and also decrypt to the receiver,
the network tunnel which the data is transferred cannot in anyway tamper the data because
encryption is very secured and they are not vulnerable. Also the network addresses can also be
presented by VPN (Shah, SHAH, & Shah, 2019)..
1) Remote access VPN
Remote access VPN clients have an access of organization's network through VPN gateway servers.
The gateway servers will only need the authenticated devices in order to allow access of the internal
network for the resources such as intranets, printers, file serves and scanners among others. It
requires IP Security (IPsec) or Secure Sockets Layer(SSL) for connection security (Wnuk,
Kościelny, Syfert, & Ciepiela, 2019, March).
A virtual private network (VPN) is programming that guarantee safety and encryption of connection
in a very less secured network. A VPN functions in a public internet while it strictly maintain the
privacy through procedures. VPN encrypts the data from the sender and also decrypt to the receiver,
the network tunnel which the data is transferred cannot in anyway tamper the data because
encryption is very secured and they are not vulnerable. Also the network addresses can also be
presented by VPN (Shah, SHAH, & Shah, 2019)..
1) Remote access VPN
Remote access VPN clients have an access of organization's network through VPN gateway servers.
The gateway servers will only need the authenticated devices in order to allow access of the internal
network for the resources such as intranets, printers, file serves and scanners among others. It
requires IP Security (IPsec) or Secure Sockets Layer(SSL) for connection security (Wnuk,
Kościelny, Syfert, & Ciepiela, 2019, March).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





