Detailed Report on Network Security Issues and a Security Model
VerifiedAdded on 2023/06/12
|12
|664
|108
Report
AI Summary
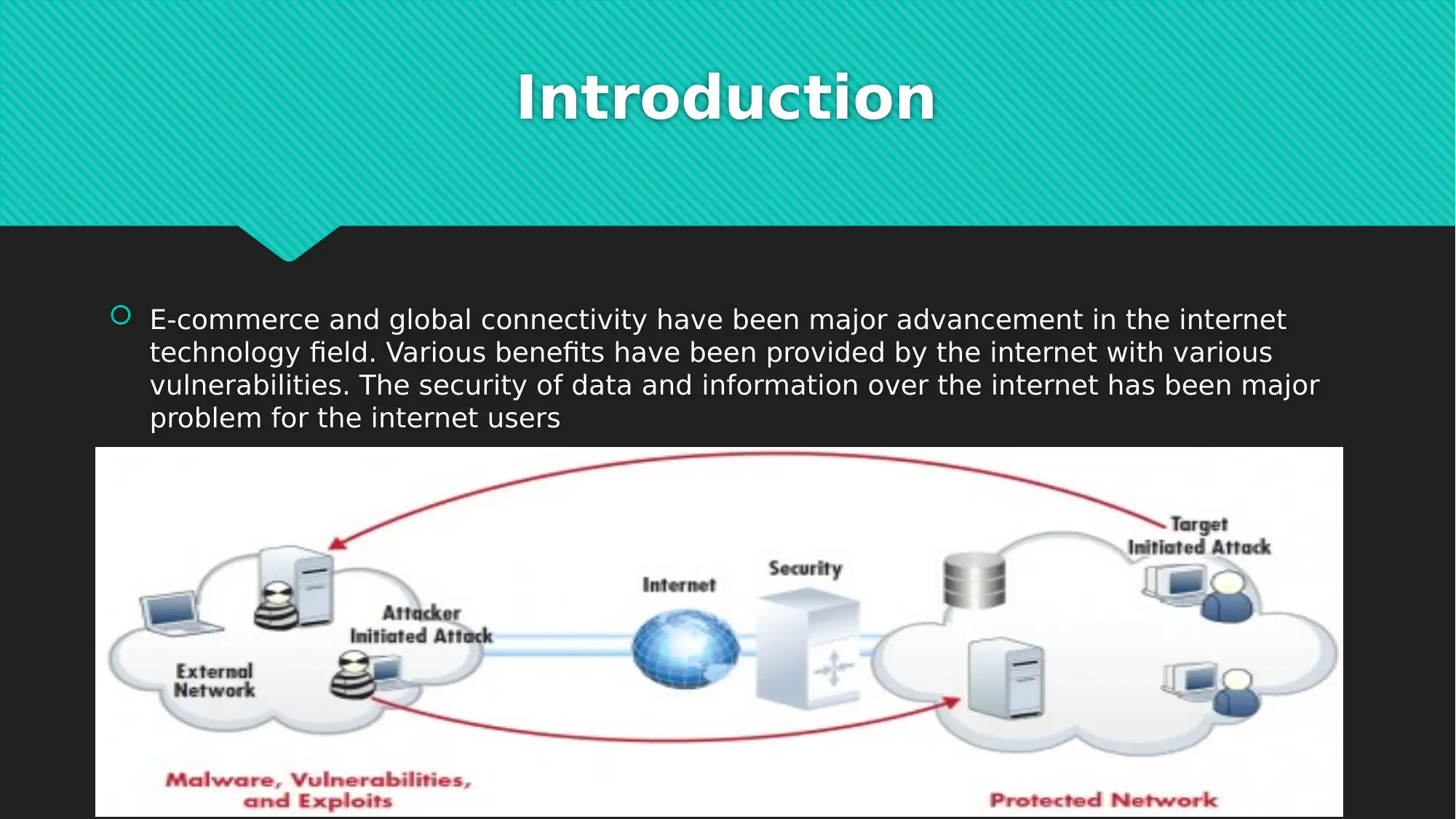
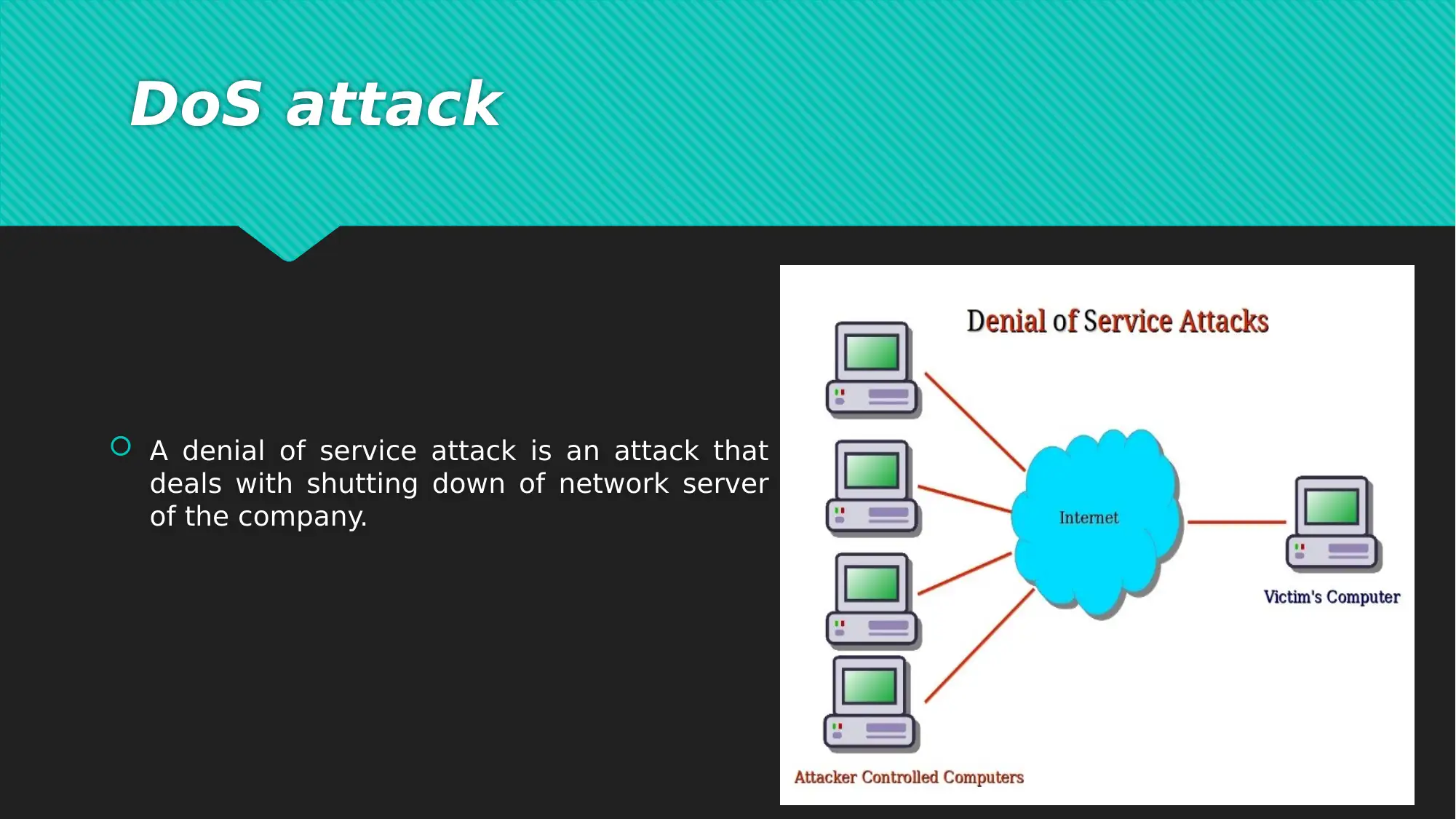
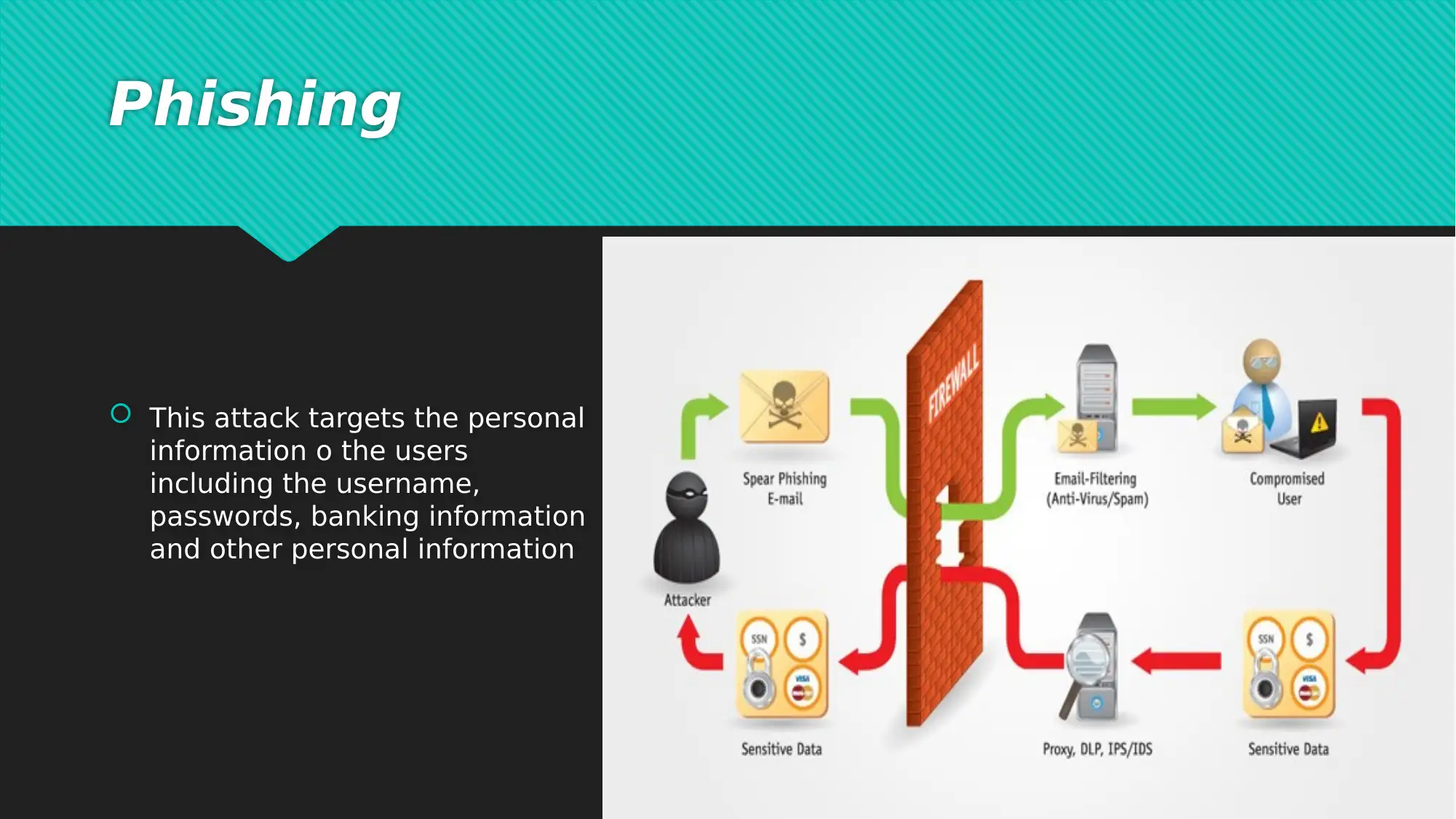
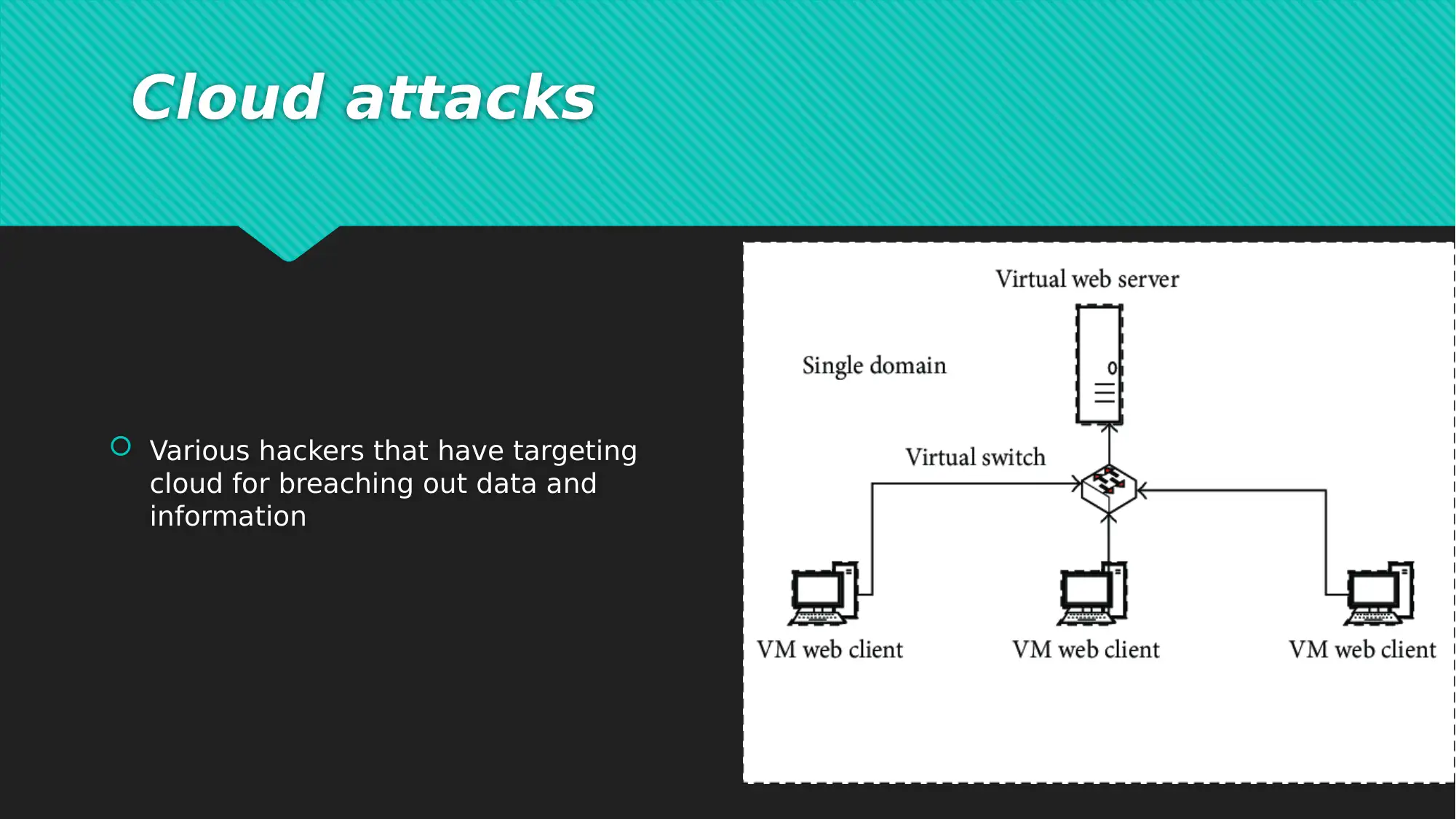
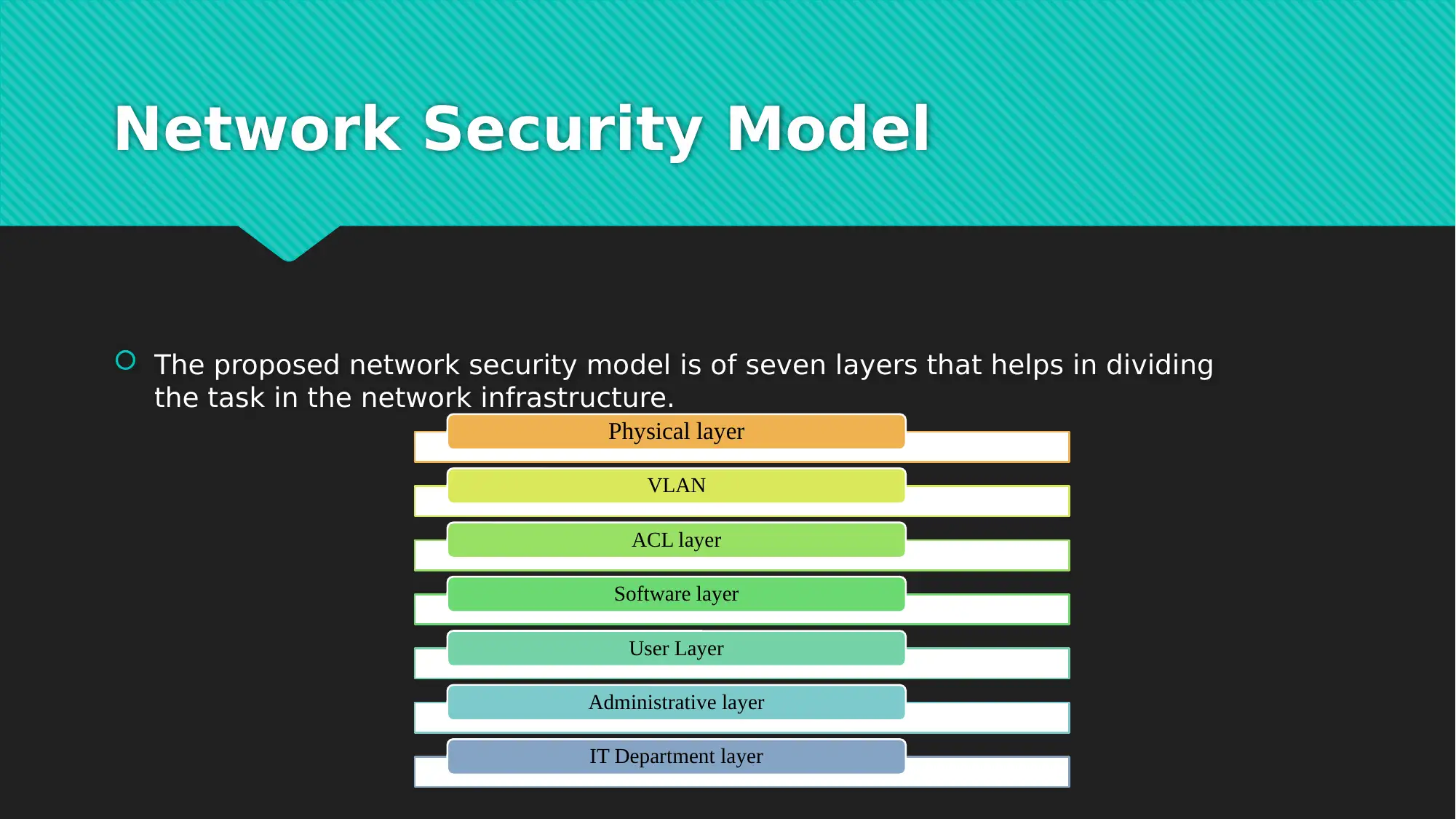
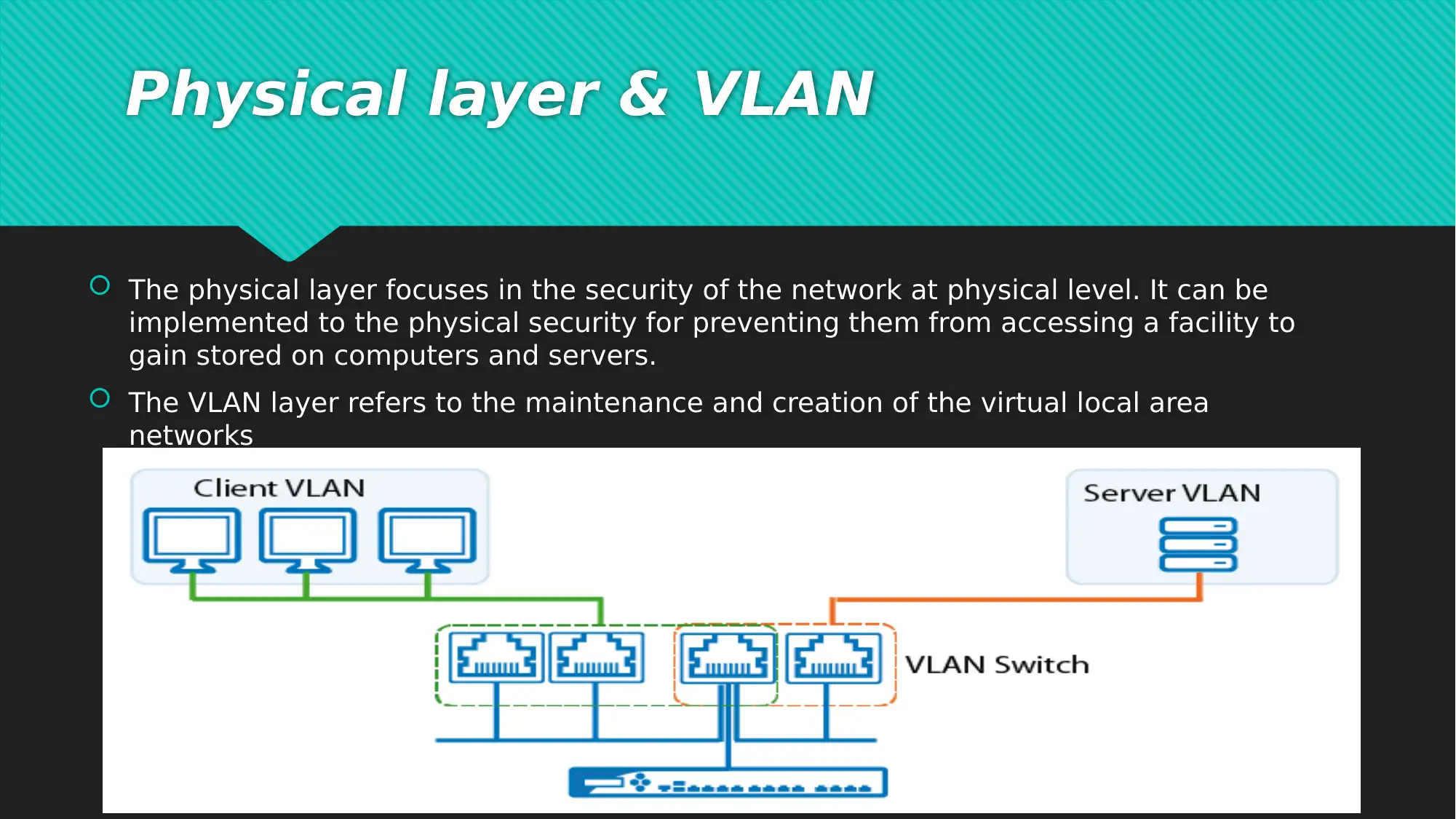
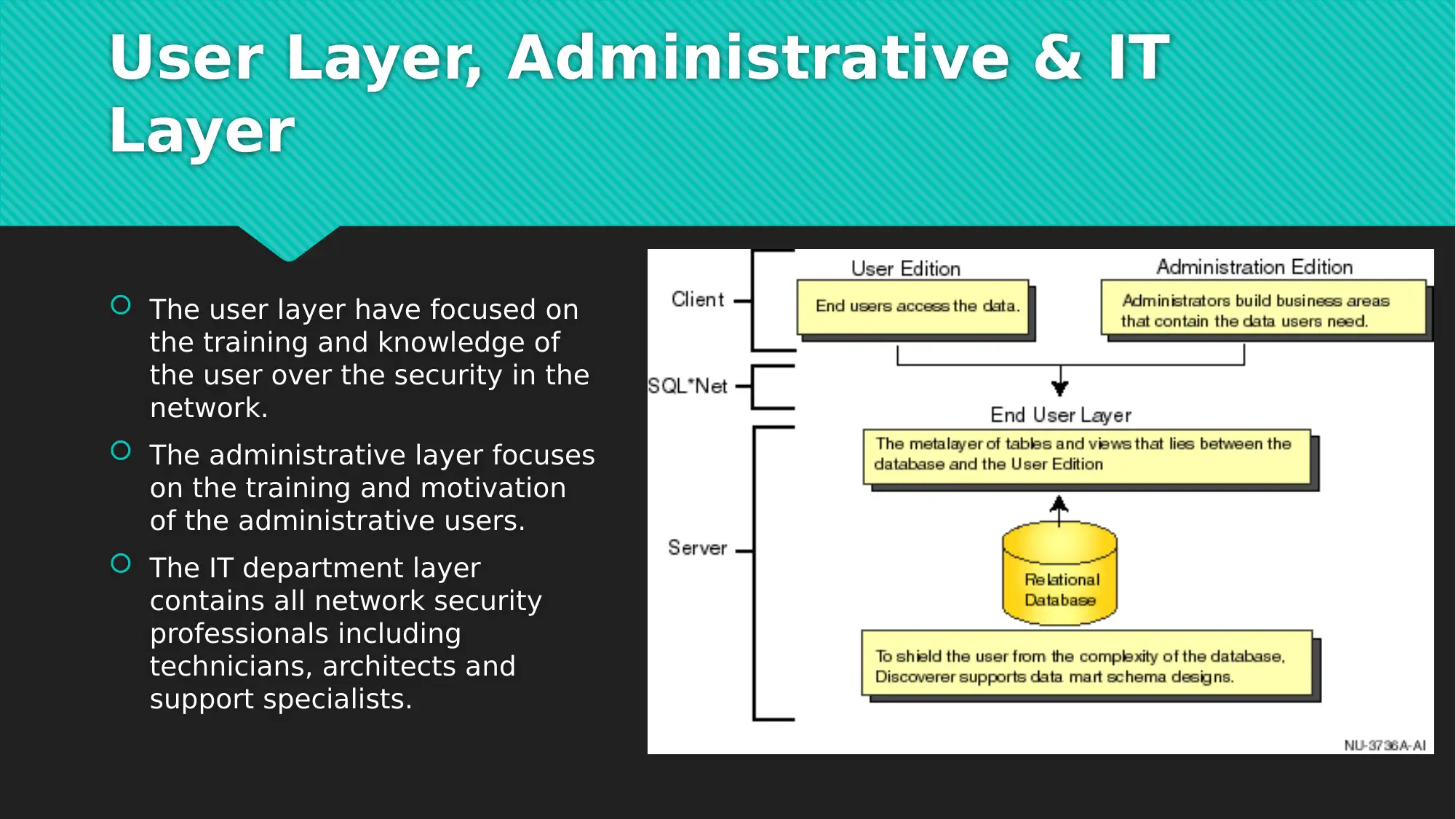
This report examines critical network security issues prevalent in today's interconnected digital landscape, focusing on the vulnerabilities introduced by e-commerce and global connectivity. It highlights common cyber-attacks such as Denial of Service (DoS) attacks, phishing, and cloud-based breaches, which pose significant threats to data and financial security for both users and organizations. To mitigate these risks, the report introduces a comprehensive seven-layer network security model, which divides security tasks across the physical, VLAN, ACL, software, user, administrative, and IT department layers. Each layer addresses specific aspects of network security, from physical access control and virtual network maintenance to software updates, user training, and specialized IT expertise. The report concludes by emphasizing the importance of addressing network security issues to prevent data and financial losses, advocating for continuous vigilance and proactive security measures in the face of evolving cyber threats. The document includes references to support its findings and recommendations. Desklib offers a variety of resources including solved assignments and past papers to support students.
1 out of 12











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)