Network Security: Kerberos Authentication, Architecture, and Use
VerifiedAdded on 2020/02/18
|10
|2029
|38
Report
AI Summary
This report provides a detailed overview of Kerberos, a network authentication protocol utilizing secret key cryptography. It explores the problems addressed by Kerberos, its user authentication process, and the underlying architecture, including the Key Distribution Center (KDC) and Ticket-Granting Ticket (TGT). The report differentiates between Kerberos versions 4 and 5, highlighting key changes and improvements. Furthermore, it discusses the organizational applications of Kerberos, particularly in environments like Microsoft Active Directory. The report concludes with a list of relevant references, offering additional resources for further study on network security and authentication protocols.

Running head: NETWORK SECURITY
Network Security
Student Name
Student ID
University Name
Author’s Note
Network Security
Student Name
Student ID
University Name
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK SECURITY
Table of Contents
Introduction......................................................................................................................................2
Problems with Kerberos..................................................................................................................2
Karberos User Authentication.........................................................................................................3
Kerberos Architecture......................................................................................................................4
Difference between Kerberos 4 and 5.............................................................................................6
Organisational use of Kerberos.......................................................................................................8
References........................................................................................................................................9
Table of Contents
Introduction......................................................................................................................................2
Problems with Kerberos..................................................................................................................2
Karberos User Authentication.........................................................................................................3
Kerberos Architecture......................................................................................................................4
Difference between Kerberos 4 and 5.............................................................................................6
Organisational use of Kerberos.......................................................................................................8
References........................................................................................................................................9

2NETWORK SECURITY
Introduction
Kerberos is a system convention that utilizations mystery key cryptography to confirm
customer service applications. Kerberos asks for an encoded ticket utilising reinforced server
arrangement to utilise administrations. A verification framework created at the Massachusetts
Institute of Technology (MIT). Kerberos is intended to empower two gatherings to trade private
data over an open system. It works by allotting an extraordinary key, called a ticket, to every
client that logs on to the system. The ticket is then implanted in messages to distinguish the
sender of the message.
Problems with Kerberos
Kerberos is intended to give reliable confirmation to customer/server applications by
utilising mystery key cryptography. A free usage of it has been influenced accessible by the
Massachusetts To organisation of Technology (MIT), in spite of the fact that Kerberos is
available in numerous business items as well. Kerberos is utilised of course in Windows
organises and gives shared validation and authorization to customers and servers. It doesn't
require the utilisation of a secret word or a 'hash on the wire'; rather it depends on a put stock in
the outsider for dealing with. MIT itself indicates that Kerberos was made by as an answer for
arranging security issues. This modern convention's cryptography should guarantee that a
customer can demonstrate its personality to a server (and the other way around) over an
uncertain system association. With a specific end goal to take after this story, we have to
characterize a modest bunch of key acronyms:
Introduction
Kerberos is a system convention that utilizations mystery key cryptography to confirm
customer service applications. Kerberos asks for an encoded ticket utilising reinforced server
arrangement to utilise administrations. A verification framework created at the Massachusetts
Institute of Technology (MIT). Kerberos is intended to empower two gatherings to trade private
data over an open system. It works by allotting an extraordinary key, called a ticket, to every
client that logs on to the system. The ticket is then implanted in messages to distinguish the
sender of the message.
Problems with Kerberos
Kerberos is intended to give reliable confirmation to customer/server applications by
utilising mystery key cryptography. A free usage of it has been influenced accessible by the
Massachusetts To organisation of Technology (MIT), in spite of the fact that Kerberos is
available in numerous business items as well. Kerberos is utilised of course in Windows
organises and gives shared validation and authorization to customers and servers. It doesn't
require the utilisation of a secret word or a 'hash on the wire'; rather it depends on a put stock in
the outsider for dealing with. MIT itself indicates that Kerberos was made by as an answer for
arranging security issues. This modern convention's cryptography should guarantee that a
customer can demonstrate its personality to a server (and the other way around) over an
uncertain system association. With a specific end goal to take after this story, we have to
characterize a modest bunch of key acronyms:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK SECURITY
KDC (Key Distribution Center) – a focal element in charge of all verification
assignments.
Ticket-Granting Ticket (TGT) – a ticket is conceded by the Authentication Server (AS)
for a client after starting verification and is important to ask for benefit tickets.
Karberos User Authentication
Kerberos varies from username/secret key confirmation techniques. Rather than
validating every client to each system benefit, Kerberos utilises symmetric encryption and a
trusted outsider (a KDC), to confirm clients to a suite of system administrations. At the point
when a client verifies to the KDC, the KDC sends a ticket particular to that session back to the
client's machine, and any Kerberos-mindful administrations search for the ticket on the client's
machine as opposed to requiring the client to confirm utilising a secret key.
At the point when a client on a Kerberos-mindful system sign in to their workstation,
they're essential is sent to the KDC as a component of a demand for a TGT from the
Authentication Server. This asks for can be sent by the sign in a program with the goal that it is
straightforward to the client, or can be sent by the init program after the client sign in. The KDC
at that point checks for the primary in its database. If the primary is discovered, the KDC makes
a TGT, which is scrambled utilizing the client's vital and come back to that client. The login or
knit program on the customer at that point decodes the TGT utilizing the client's vital, which it
registers from the client's watchword. The client's key is utilized just on the customer machine
and is not transmitted over the system.
KDC (Key Distribution Center) – a focal element in charge of all verification
assignments.
Ticket-Granting Ticket (TGT) – a ticket is conceded by the Authentication Server (AS)
for a client after starting verification and is important to ask for benefit tickets.
Karberos User Authentication
Kerberos varies from username/secret key confirmation techniques. Rather than
validating every client to each system benefit, Kerberos utilises symmetric encryption and a
trusted outsider (a KDC), to confirm clients to a suite of system administrations. At the point
when a client verifies to the KDC, the KDC sends a ticket particular to that session back to the
client's machine, and any Kerberos-mindful administrations search for the ticket on the client's
machine as opposed to requiring the client to confirm utilising a secret key.
At the point when a client on a Kerberos-mindful system sign in to their workstation,
they're essential is sent to the KDC as a component of a demand for a TGT from the
Authentication Server. This asks for can be sent by the sign in a program with the goal that it is
straightforward to the client, or can be sent by the init program after the client sign in. The KDC
at that point checks for the primary in its database. If the primary is discovered, the KDC makes
a TGT, which is scrambled utilizing the client's vital and come back to that client. The login or
knit program on the customer at that point decodes the TGT utilizing the client's vital, which it
registers from the client's watchword. The client's key is utilized just on the customer machine
and is not transmitted over the system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORK SECURITY
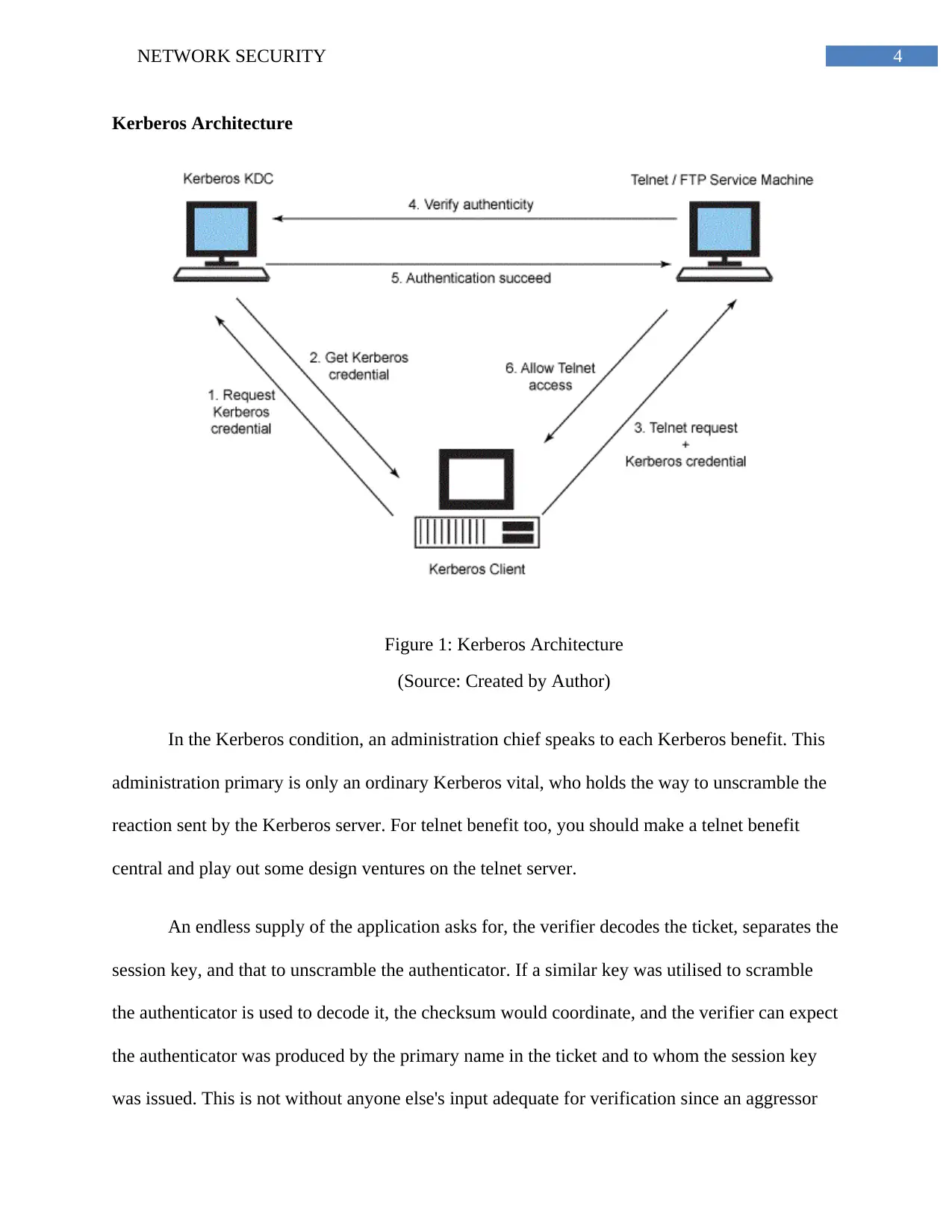
Kerberos Architecture
Figure 1: Kerberos Architecture
(Source: Created by Author)
In the Kerberos condition, an administration chief speaks to each Kerberos benefit. This
administration primary is only an ordinary Kerberos vital, who holds the way to unscramble the
reaction sent by the Kerberos server. For telnet benefit too, you should make a telnet benefit
central and play out some design ventures on the telnet server.
An endless supply of the application asks for, the verifier decodes the ticket, separates the
session key, and that to unscramble the authenticator. If a similar key was utilised to scramble
the authenticator is used to decode it, the checksum would coordinate, and the verifier can expect
the authenticator was produced by the primary name in the ticket and to whom the session key
was issued. This is not without anyone else's input adequate for verification since an aggressor
Kerberos Architecture
Figure 1: Kerberos Architecture
(Source: Created by Author)
In the Kerberos condition, an administration chief speaks to each Kerberos benefit. This
administration primary is only an ordinary Kerberos vital, who holds the way to unscramble the
reaction sent by the Kerberos server. For telnet benefit too, you should make a telnet benefit
central and play out some design ventures on the telnet server.
An endless supply of the application asks for, the verifier decodes the ticket, separates the
session key, and that to unscramble the authenticator. If a similar key was utilised to scramble
the authenticator is used to decode it, the checksum would coordinate, and the verifier can expect
the authenticator was produced by the primary name in the ticket and to whom the session key
was issued. This is not without anyone else's input adequate for verification since an aggressor

5NETWORK SECURITY
can capture an authenticator and replay it later to mimic the client. Thus the verifier also checks
the timestamp to ensure that the authenticator is new. On the off chance that the timestamp is
within a predetermined window (ordinarily 5 minutes) based on the present time on the verifier,
and if the timestamp has not been seen on different demands inside that window, the verifier
acknowledges the demand as genuine. An exchange of the advantages and disadvantages to the
utilization of timestamps in confirmation conventions can be found in.
Now the character of the customer has been checked by the server. For a few applications
the customer likewise needs to make certain of the server's character. If such common validation
is required, the server creates an application reaction by removing the customer's chance from
the authenticator and returns it to the customer together with other data, all scrambled utilizing
the session key. The customer requires a different ticket and session key for every verifier with
which it imparts. At the point when a customer wishes to make a relationship with a specific
verifier, the customer utilizes the validation demand and reaction, messages 1 and two from
figure 1, to get a ticket and session key from the verification server. In demand, the customer
sends the verification server its guaranteed character, the name of the verifier, an asked for
termination time for the ticket, and an arbitrary number that will be utilized to coordinate the
confirmation reaction with the demand. Together, the verification demand and reaction and the
application demand and reaction include the fundamental Kerberos confirmation convention.
can capture an authenticator and replay it later to mimic the client. Thus the verifier also checks
the timestamp to ensure that the authenticator is new. On the off chance that the timestamp is
within a predetermined window (ordinarily 5 minutes) based on the present time on the verifier,
and if the timestamp has not been seen on different demands inside that window, the verifier
acknowledges the demand as genuine. An exchange of the advantages and disadvantages to the
utilization of timestamps in confirmation conventions can be found in.
Now the character of the customer has been checked by the server. For a few applications
the customer likewise needs to make certain of the server's character. If such common validation
is required, the server creates an application reaction by removing the customer's chance from
the authenticator and returns it to the customer together with other data, all scrambled utilizing
the session key. The customer requires a different ticket and session key for every verifier with
which it imparts. At the point when a customer wishes to make a relationship with a specific
verifier, the customer utilizes the validation demand and reaction, messages 1 and two from
figure 1, to get a ticket and session key from the verification server. In demand, the customer
sends the verification server its guaranteed character, the name of the verifier, an asked for
termination time for the ticket, and an arbitrary number that will be utilized to coordinate the
confirmation reaction with the demand. Together, the verification demand and reaction and the
application demand and reaction include the fundamental Kerberos confirmation convention.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK SECURITY
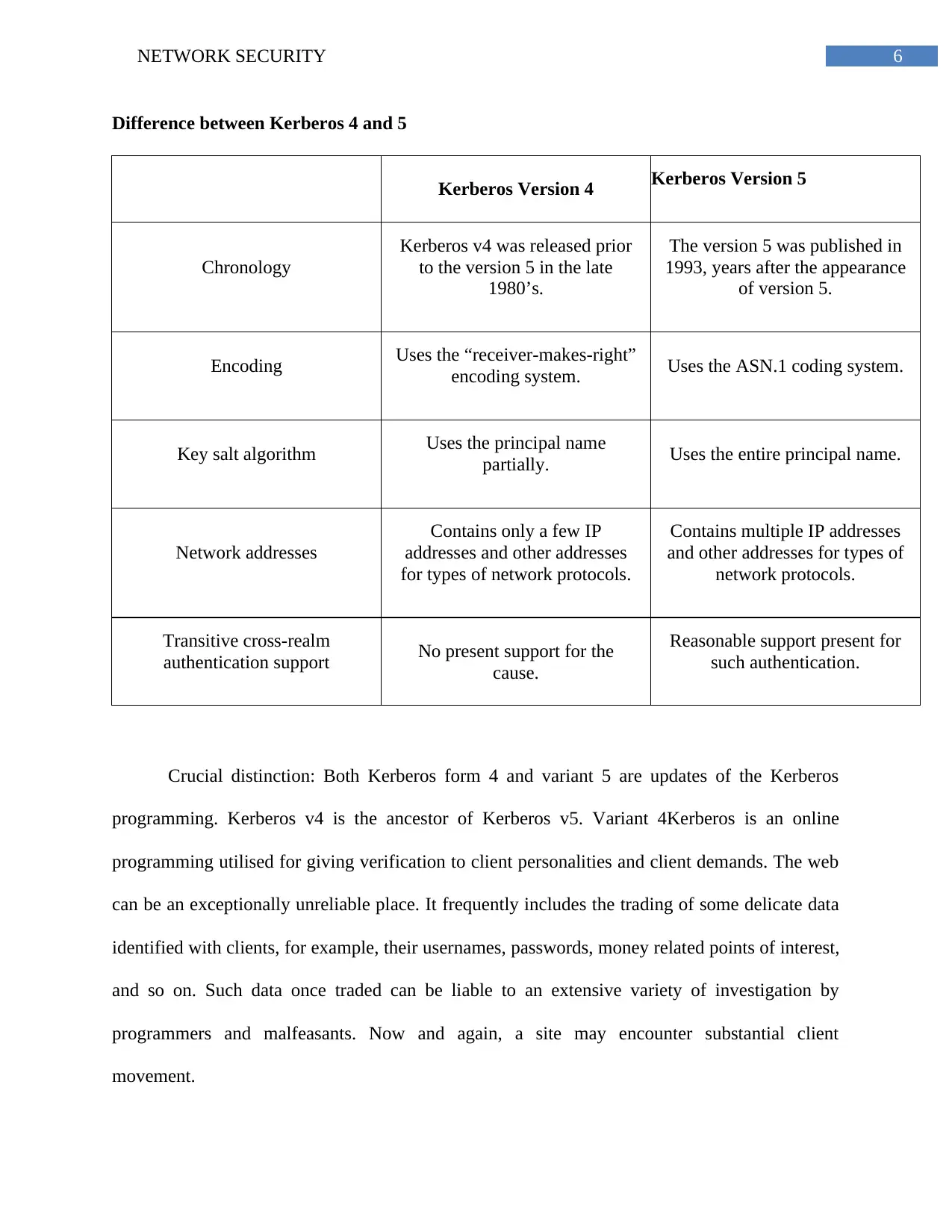
Difference between Kerberos 4 and 5
Kerberos Version 4 Kerberos Version 5
Chronology
Kerberos v4 was released prior
to the version 5 in the late
1980’s.
The version 5 was published in
1993, years after the appearance
of version 5.
Encoding Uses the “receiver-makes-right”
encoding system. Uses the ASN.1 coding system.
Key salt algorithm Uses the principal name
partially. Uses the entire principal name.
Network addresses
Contains only a few IP
addresses and other addresses
for types of network protocols.
Contains multiple IP addresses
and other addresses for types of
network protocols.
Transitive cross-realm
authentication support No present support for the
cause.
Reasonable support present for
such authentication.
Crucial distinction: Both Kerberos form 4 and variant 5 are updates of the Kerberos
programming. Kerberos v4 is the ancestor of Kerberos v5. Variant 4Kerberos is an online
programming utilised for giving verification to client personalities and client demands. The web
can be an exceptionally unreliable place. It frequently includes the trading of some delicate data
identified with clients, for example, their usernames, passwords, money related points of interest,
and so on. Such data once traded can be liable to an extensive variety of investigation by
programmers and malfeasants. Now and again, a site may encounter substantial client
movement.
Difference between Kerberos 4 and 5
Kerberos Version 4 Kerberos Version 5
Chronology
Kerberos v4 was released prior
to the version 5 in the late
1980’s.
The version 5 was published in
1993, years after the appearance
of version 5.
Encoding Uses the “receiver-makes-right”
encoding system. Uses the ASN.1 coding system.
Key salt algorithm Uses the principal name
partially. Uses the entire principal name.
Network addresses
Contains only a few IP
addresses and other addresses
for types of network protocols.
Contains multiple IP addresses
and other addresses for types of
network protocols.
Transitive cross-realm
authentication support No present support for the
cause.
Reasonable support present for
such authentication.
Crucial distinction: Both Kerberos form 4 and variant 5 are updates of the Kerberos
programming. Kerberos v4 is the ancestor of Kerberos v5. Variant 4Kerberos is an online
programming utilised for giving verification to client personalities and client demands. The web
can be an exceptionally unreliable place. It frequently includes the trading of some delicate data
identified with clients, for example, their usernames, passwords, money related points of interest,
and so on. Such data once traded can be liable to an extensive variety of investigation by
programmers and malfeasants. Now and again, a site may encounter substantial client
movement.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK SECURITY
For dispensing with such annoyance, the Kerberos programming was produced.
"Kerberos" is gotten from Greek folklore, where it remains for the name of the three-headed
canine that monitored the entryways of Hades. Kerberos was first created and put being used at
the Massachusetts Institute of Technology (MIT). The initial three variants of this product
worked inside the MIT grounds itself. Until the late 1980's that Kerberos was made accessible to
the majority and the web through the arrival of its variant four programming. Fundamentally
produced for MIT's one of a kind Project Athena, Kerberos was predominantly composed by
Steve Miller and Clifford Neuman. Adaptation 5The working of Kerberos depends on the
verification server (AS). This kind of server is fundamental for giving clients 'tickets', which
approve their solicitations.
If a client demands an instalment benefit, the validation server would naturally create a
specific session key and ID, utilising which the client puts in his/her points of interest and gets
the administration. This is the place Kerberos comes into the photo. These passwords and other
data are in an uncovered shape on the wire. With the assistance of Kerberos programming,
indispensable information like this is scrambled and ensured consistently at each phase of the
exchange. In the wake of distributing the adaptation 4 in the fag end of the 1980's, Clifford
Neuman teamed up with John Kohl, to introduce Kerberos rendition 5, which was a refresh of
the Kerberos variant 4. The adaptation four had encountered numerous constraints and security
issues because of the headway of innovation around it. Therefore, the variant 4 ended up plainly
out of date and must be supplanted by RFC 1510, or the Kerberos adaptation 5, in the year 1993.
For dispensing with such annoyance, the Kerberos programming was produced.
"Kerberos" is gotten from Greek folklore, where it remains for the name of the three-headed
canine that monitored the entryways of Hades. Kerberos was first created and put being used at
the Massachusetts Institute of Technology (MIT). The initial three variants of this product
worked inside the MIT grounds itself. Until the late 1980's that Kerberos was made accessible to
the majority and the web through the arrival of its variant four programming. Fundamentally
produced for MIT's one of a kind Project Athena, Kerberos was predominantly composed by
Steve Miller and Clifford Neuman. Adaptation 5The working of Kerberos depends on the
verification server (AS). This kind of server is fundamental for giving clients 'tickets', which
approve their solicitations.
If a client demands an instalment benefit, the validation server would naturally create a
specific session key and ID, utilising which the client puts in his/her points of interest and gets
the administration. This is the place Kerberos comes into the photo. These passwords and other
data are in an uncovered shape on the wire. With the assistance of Kerberos programming,
indispensable information like this is scrambled and ensured consistently at each phase of the
exchange. In the wake of distributing the adaptation 4 in the fag end of the 1980's, Clifford
Neuman teamed up with John Kohl, to introduce Kerberos rendition 5, which was a refresh of
the Kerberos variant 4. The adaptation four had encountered numerous constraints and security
issues because of the headway of innovation around it. Therefore, the variant 4 ended up plainly
out of date and must be supplanted by RFC 1510, or the Kerberos adaptation 5, in the year 1993.

8NETWORK SECURITY
Organisational use of Kerberos
Many individuals are wilfully ignorant of Kerberos. Such a life is one to treasure. A
considerable lot of these individuals, do, notwithstanding, sign in to an undertaking system by a
method for Microsoft Active Directory. "Promotion" is a Kerberos Controller. Kerberos
Explained If an association utilizes Active Directory to oversee clients, they are running
Kerberos, so have the fundamental foundation expected to validate clients and administrations
inside a Hadoop group. Clients ought to have the capacity to submit employments as themselves,
collaborating with "Kerberized" Hadoop administrations. Setting up Hadoop to work with Active
Directory is past the extent of this book. If you don't mind counsel the references in the book
reference, as well as any merchant particular documentation.
Organisational use of Kerberos
Many individuals are wilfully ignorant of Kerberos. Such a life is one to treasure. A
considerable lot of these individuals, do, notwithstanding, sign in to an undertaking system by a
method for Microsoft Active Directory. "Promotion" is a Kerberos Controller. Kerberos
Explained If an association utilizes Active Directory to oversee clients, they are running
Kerberos, so have the fundamental foundation expected to validate clients and administrations
inside a Hadoop group. Clients ought to have the capacity to submit employments as themselves,
collaborating with "Kerberized" Hadoop administrations. Setting up Hadoop to work with Active
Directory is past the extent of this book. If you don't mind counsel the references in the book
reference, as well as any merchant particular documentation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK SECURITY
References
Beberlein, L.T., Dias, G., Levitt, K.N., Mukherjee, B. and Wood, J., 2017. Network attacks and
an Ethernet-based network security monitor.
Chen, G., Gong, Y., Xiao, P. and Chambers, J.A., 2015. Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
pp.574-583.
Kahate, A., 2013. Cryptography and network security. Tata McGraw-Hill Education.
Liang, X. and Xiao, Y., 2013. Game theory for network security. IEEE Communications Surveys
& Tutorials, 15(1), pp.472-486.
Manshaei, M.H., Zhu, Q., Alpcan, T., Bacşar, T. and Hubaux, J.P., 2013. Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), p.25.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.
Tokuyoshi, B., 2013. The security implications of BYOD. Network Security, 2013(4), pp.12-13.
References
Beberlein, L.T., Dias, G., Levitt, K.N., Mukherjee, B. and Wood, J., 2017. Network attacks and
an Ethernet-based network security monitor.
Chen, G., Gong, Y., Xiao, P. and Chambers, J.A., 2015. Physical layer network security in the
full-duplex relay system. IEEE transactions on information forensics and security, 10(3),
pp.574-583.
Kahate, A., 2013. Cryptography and network security. Tata McGraw-Hill Education.
Liang, X. and Xiao, Y., 2013. Game theory for network security. IEEE Communications Surveys
& Tutorials, 15(1), pp.472-486.
Manshaei, M.H., Zhu, Q., Alpcan, T., Bacşar, T. and Hubaux, J.P., 2013. Game theory meets
network security and privacy. ACM Computing Surveys (CSUR), 45(3), p.25.
Perlman, R., Kaufman, C. and Speciner, M., 2016. Network security: private communication in a
public world. Pearson Education India.
Stallings, W. and Tahiliani, M.P., 2014. Cryptography and network security: principles and
practice (Vol. 6). London: Pearson.
Tokuyoshi, B., 2013. The security implications of BYOD. Network Security, 2013(4), pp.12-13.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




