Network Security Report: Evaluation and Design for Landon Bet
VerifiedAdded on 2023/03/21
|30
|3688
|62
Report
AI Summary
This report presents a comprehensive network security analysis and design for Landon Bet, a small betting company. The project begins with an evaluation of the existing network, assessing physical and logical security aspects, and identifying potential vulnerabilities, including common network attack types such as DoS, DDoS, SYN, IP spoofing, and DNS spoofing attacks. The report then moves on to designing a secure and reliable network infrastructure, detailing the devices, topology (star topology), security measures (firewalls, encryption), and user considerations. This includes the configuration of servers, VLANs, and a DMZ. The implementation phase involves configuring the network design using Cisco Packet Tracer and testing its functionality. Finally, the report addresses network security management, including monitoring, security policies, and recommendations to enhance the network's reliability and security. The report emphasizes the importance of multi-factor authentication, and the role of firewalls, and other security measures. References are included at the end.

University
Semester
Network Security
Student ID
Student Name
Submission Date
1
Semester
Network Security
Student ID
Student Name
Submission Date
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction.........................................................................................................................3
2. Task: 1.................................................................................................................................3
2.1 Physical and Logical Security Evaluation...................................................................3
2.2 Common Types of Network Attacks...........................................................................4
3. Task: 2.................................................................................................................................6
3.1 Designing a Secure and Reliable Network..................................................................6
3.2 Designed Network Design’s Evaluation.....................................................................9
4. Task: 3.................................................................................................................................9
4.1 Network Design Configuration...................................................................................9
4.2 Network Testing........................................................................................................25
5. Task: 4...............................................................................................................................26
5.1 Monitoring System Security......................................................................................27
5.2 Security Policies and Practices..................................................................................27
5.3 Recommendations.....................................................................................................28
6. Conclusion........................................................................................................................29
References................................................................................................................................30
2
1. Introduction.........................................................................................................................3
2. Task: 1.................................................................................................................................3
2.1 Physical and Logical Security Evaluation...................................................................3
2.2 Common Types of Network Attacks...........................................................................4
3. Task: 2.................................................................................................................................6
3.1 Designing a Secure and Reliable Network..................................................................6
3.2 Designed Network Design’s Evaluation.....................................................................9
4. Task: 3.................................................................................................................................9
4.1 Network Design Configuration...................................................................................9
4.2 Network Testing........................................................................................................25
5. Task: 4...............................................................................................................................26
5.1 Monitoring System Security......................................................................................27
5.2 Security Policies and Practices..................................................................................27
5.3 Recommendations.....................................................................................................28
6. Conclusion........................................................................................................................29
References................................................................................................................................30
2

1. Introduction
The main objective of this project is to design a network infrastructure for a Landon
Bet company. This company is a small betting company that specializes in sports Bets and
allows its customers to place bets on various sports activities both in local and online shops
all across the country. This company consists of three departments such as HR/ Admin,
marketing and finance staff. This company has issues in managing network activities and it
recently has suffered from the data breach. So, this project needs to carry out a security audit,
evaluate the londonbet.co.uk network and propose a new network infrastructure for the
company named, Landon Bet.
This project is divided into four tasks. The first task is used for evaluating the existing
network design based on logical and physical security aspects, and also discusses the
potential security impacts of the given network. This report will even discuss the fundamental
network attack types, threats, and all their impacts. The second task is used to design the
network security solutions for London Bet Company. Next, it aims to evaluate the network
design and analyze the feedback with respect to security, manageability, redundancy,
scalability, and availability. The third task is used to implement the network security
solutions by configuring the network design on Cisco packet tracer. Further, it will test the
created network design which includes the servers, VLANs, DMZ, and Technology. The
fourth task is used to manage the network security solution by explaining the security system
monitoring. It also includes system and physical level of security access for the proposed
network review and security policies and practices' analysis work. Then, it provides
recommendations to improve the reliability and security of the proposed network design.
2. Task: 1
In this task, the process of evaluating the existing network design with respect to
logical and physical security that takes place, where the potential security impacts of the
given network will be discussed. The basic network attack types and threats and their impacts
will be discussed as follows:
2.1 Physical and Logical Security Evaluation
In our represented diagram, in the physical design, the problem refers to the position
of each department and it is important to be adapted for the best case for the purpose of
3
The main objective of this project is to design a network infrastructure for a Landon
Bet company. This company is a small betting company that specializes in sports Bets and
allows its customers to place bets on various sports activities both in local and online shops
all across the country. This company consists of three departments such as HR/ Admin,
marketing and finance staff. This company has issues in managing network activities and it
recently has suffered from the data breach. So, this project needs to carry out a security audit,
evaluate the londonbet.co.uk network and propose a new network infrastructure for the
company named, Landon Bet.
This project is divided into four tasks. The first task is used for evaluating the existing
network design based on logical and physical security aspects, and also discusses the
potential security impacts of the given network. This report will even discuss the fundamental
network attack types, threats, and all their impacts. The second task is used to design the
network security solutions for London Bet Company. Next, it aims to evaluate the network
design and analyze the feedback with respect to security, manageability, redundancy,
scalability, and availability. The third task is used to implement the network security
solutions by configuring the network design on Cisco packet tracer. Further, it will test the
created network design which includes the servers, VLANs, DMZ, and Technology. The
fourth task is used to manage the network security solution by explaining the security system
monitoring. It also includes system and physical level of security access for the proposed
network review and security policies and practices' analysis work. Then, it provides
recommendations to improve the reliability and security of the proposed network design.
2. Task: 1
In this task, the process of evaluating the existing network design with respect to
logical and physical security that takes place, where the potential security impacts of the
given network will be discussed. The basic network attack types and threats and their impacts
will be discussed as follows:
2.1 Physical and Logical Security Evaluation
In our represented diagram, in the physical design, the problem refers to the position
of each department and it is important to be adapted for the best case for the purpose of
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

security (Connecting networks companion guide, 2014). I consider that the HR Admin should
be positioned somewhere else and if possible, in the same room for better control and safety.
The position of HR Admin must be in a hard to access position, for an individual who enters
the building. In our case, the HR Admin can be accessed by anyone who enters the building.
The biggest threat here is if a hacker gains access to all data and sells them for personal
purpose.
Logically, the door of reception should be placed next to the entrance and a secured
door should be added to the hall, where we can find both the entrances for HR Admin. If
possible, it can be made as a single room for more space and better capability to manage the
HR Admin, as I consider it as the most important part.
The logical plan consists of security, which is used to comprise the programming shields
for an organization network that includes the user authentication, password verification, and
specialist levels. All these are used to guarantee to approve the clients that can perform the
data access and activities in an organization network. It is a subset of computer security in an
organization.
Elements like Users ID, Authentication and Biometrics are vital for any logical design. In
our diagram, I suggest that HR Admin, Finance and Marketing should have Two-way
authentication and one of them should be biometric, which is a highly secure method.
2.2 Common Types of Network Attacks
Basically, the networks are vulnerable to unauthorized access and it has various types
of network attacks. So, we need to implement the organization network to use proper security
measures and control the organization networks. If you have not implemented the network,
4
be positioned somewhere else and if possible, in the same room for better control and safety.
The position of HR Admin must be in a hard to access position, for an individual who enters
the building. In our case, the HR Admin can be accessed by anyone who enters the building.
The biggest threat here is if a hacker gains access to all data and sells them for personal
purpose.
Logically, the door of reception should be placed next to the entrance and a secured
door should be added to the hall, where we can find both the entrances for HR Admin. If
possible, it can be made as a single room for more space and better capability to manage the
HR Admin, as I consider it as the most important part.
The logical plan consists of security, which is used to comprise the programming shields
for an organization network that includes the user authentication, password verification, and
specialist levels. All these are used to guarantee to approve the clients that can perform the
data access and activities in an organization network. It is a subset of computer security in an
organization.
Elements like Users ID, Authentication and Biometrics are vital for any logical design. In
our diagram, I suggest that HR Admin, Finance and Marketing should have Two-way
authentication and one of them should be biometric, which is a highly secure method.
2.2 Common Types of Network Attacks
Basically, the networks are vulnerable to unauthorized access and it has various types
of network attacks. So, we need to implement the organization network to use proper security
measures and control the organization networks. If you have not implemented the network,
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

there are possibilities of network attacks from outside and inside the organization network.
Here, we will discuss various types of network attacks such as,
Denial of Service (DoS) attack – The Denial of services attack renders a
network, other pieces and hosts the infrastructure unusable by legitimating the
users. The Denial of service attack falls into three categories such as Connection
flooding, bandwidth flooding and vulnerability attack. They are discussed as
follows (Blog.netwrix.com, 2019):
o Connection flooding: In connection flooding, the hackers are establishing
a huge number of Open TCP connections like half open and fully open at
the targeted host. So, the host can become bogged down with bogus
connection, which stops accepting the legitimate connections.
o Bandwidth flooding: In bandwidth flooding, the hackers are sending a
flood of packets to the target host. But, some packets' target access link is
clogged and prevents legitimate packets from reaching the server.
o Vulnerability attack: In the vulnerability attack, it involves sending a few
well-crafted messages to a vulnerable operating system and applications
on target hosts. Therefore, the right sequence of the packets are sent to a
vulnerable operating system or application, the service will be stop and
worse, and the host can crash.
Distributed Denial of Service (DDoS) attack - One of the DoS attacks is DDoS.
It occurs on multiple compromised systems, which is used to target a single
system causing a DoS attack. It is leveraging the botnet with thousands of
comprised hosts that are used for a common occurrence in today's world. It is
harder to defend and detect the DOS attack from a Single host.
SYN attack – In SYN attack, the hackers are exploiting the buffer space used
during the TCP session initialization handshake. This attack causes the target
system to time out while waiting for the response from the attacker’s device that
makes the system crash and becomes unusable when the connection queue fills
up.
IP Address Spoofing Attack - Basically, the Ip spoofing is used by an attacker or
hacker to compromise the system which is used to communicate with a trusted
entity and the known entity. It provides attackers with system access. The hackers
send a packet with the known IP source and the trusted host instead of an IP
5
Here, we will discuss various types of network attacks such as,
Denial of Service (DoS) attack – The Denial of services attack renders a
network, other pieces and hosts the infrastructure unusable by legitimating the
users. The Denial of service attack falls into three categories such as Connection
flooding, bandwidth flooding and vulnerability attack. They are discussed as
follows (Blog.netwrix.com, 2019):
o Connection flooding: In connection flooding, the hackers are establishing
a huge number of Open TCP connections like half open and fully open at
the targeted host. So, the host can become bogged down with bogus
connection, which stops accepting the legitimate connections.
o Bandwidth flooding: In bandwidth flooding, the hackers are sending a
flood of packets to the target host. But, some packets' target access link is
clogged and prevents legitimate packets from reaching the server.
o Vulnerability attack: In the vulnerability attack, it involves sending a few
well-crafted messages to a vulnerable operating system and applications
on target hosts. Therefore, the right sequence of the packets are sent to a
vulnerable operating system or application, the service will be stop and
worse, and the host can crash.
Distributed Denial of Service (DDoS) attack - One of the DoS attacks is DDoS.
It occurs on multiple compromised systems, which is used to target a single
system causing a DoS attack. It is leveraging the botnet with thousands of
comprised hosts that are used for a common occurrence in today's world. It is
harder to defend and detect the DOS attack from a Single host.
SYN attack – In SYN attack, the hackers are exploiting the buffer space used
during the TCP session initialization handshake. This attack causes the target
system to time out while waiting for the response from the attacker’s device that
makes the system crash and becomes unusable when the connection queue fills
up.
IP Address Spoofing Attack - Basically, the Ip spoofing is used by an attacker or
hacker to compromise the system which is used to communicate with a trusted
entity and the known entity. It provides attackers with system access. The hackers
send a packet with the known IP source and the trusted host instead of an IP
5
source address to a target host. The target host might accept the packet and act
upon it.
DNS (Domain Name System) Spoofing Attacks - The domain name system
spoofing attacks or DNS cache poisoning is a form of computer security hacking,
which corrupts the data on domain name system that is introduced into the DNS
resolvers cache and causes the domain name server to return an incorrect IP
address.
3. Task: 2
In this task, we will design the network security solutions for London Bet Company.
Thus, firstly we will design a new reliable and secured network which contains the floor
diagram, topology, devices, security, users, technology and physical security. Next, the
network design is evaluated and the feedbacks are analyzed based on security, manageability,
redundancy, availability, and scalability.
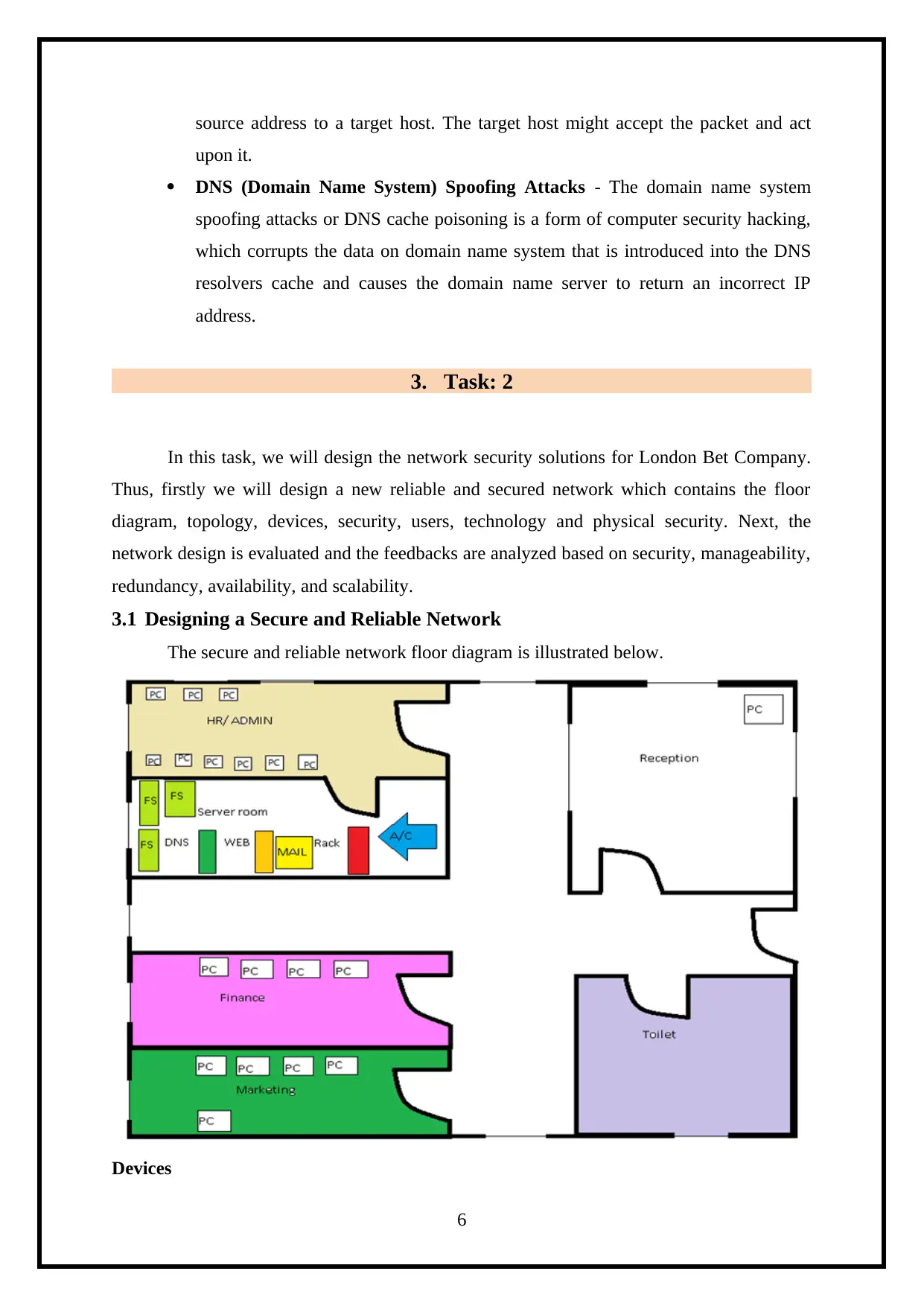
3.1 Designing a Secure and Reliable Network
The secure and reliable network floor diagram is illustrated below.
Devices
6
upon it.
DNS (Domain Name System) Spoofing Attacks - The domain name system
spoofing attacks or DNS cache poisoning is a form of computer security hacking,
which corrupts the data on domain name system that is introduced into the DNS
resolvers cache and causes the domain name server to return an incorrect IP
address.
3. Task: 2
In this task, we will design the network security solutions for London Bet Company.
Thus, firstly we will design a new reliable and secured network which contains the floor
diagram, topology, devices, security, users, technology and physical security. Next, the
network design is evaluated and the feedbacks are analyzed based on security, manageability,
redundancy, availability, and scalability.
3.1 Designing a Secure and Reliable Network
The secure and reliable network floor diagram is illustrated below.
Devices
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
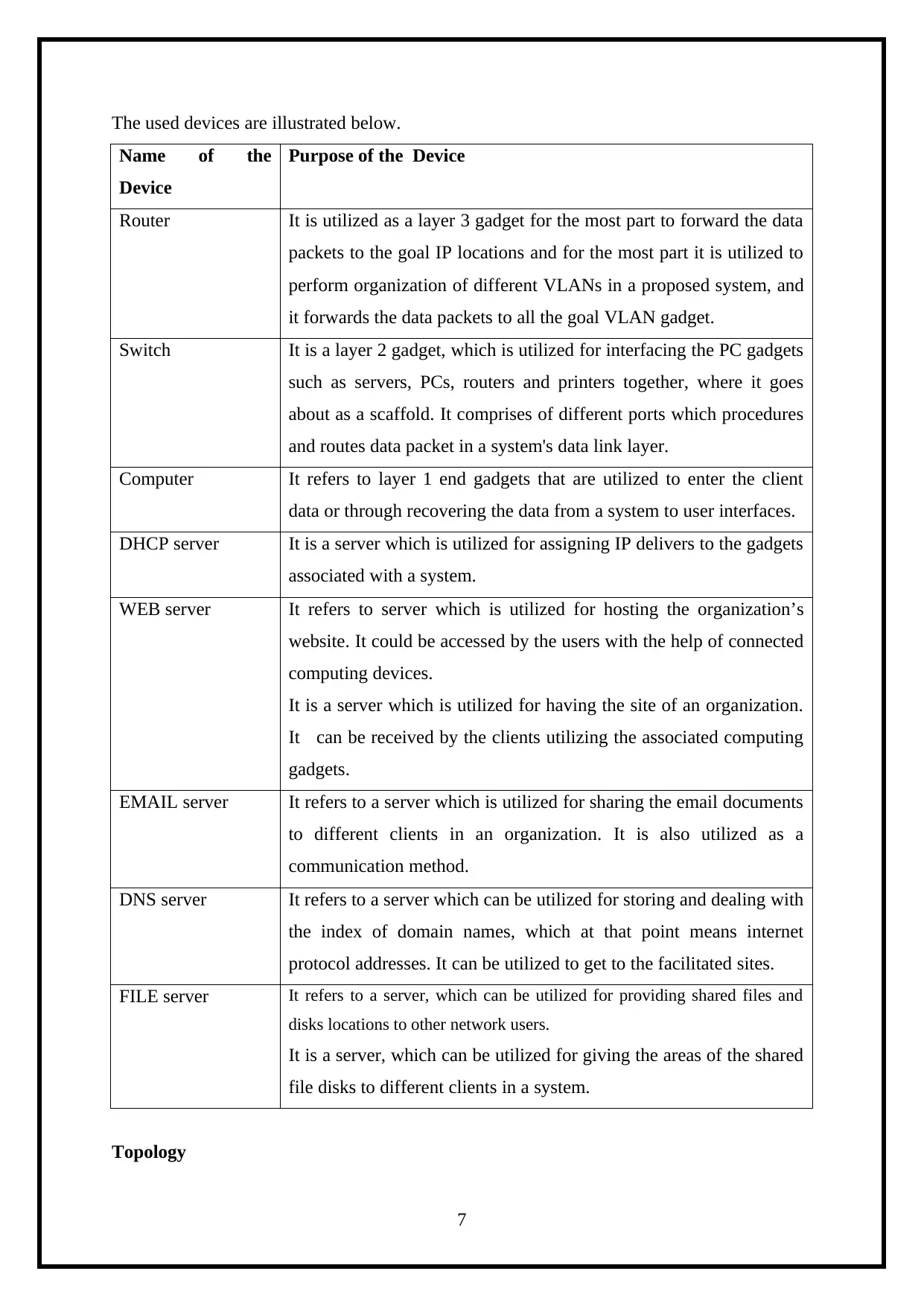
The used devices are illustrated below.
Name of the
Device
Purpose of the Device
Router It is utilized as a layer 3 gadget for the most part to forward the data
packets to the goal IP locations and for the most part it is utilized to
perform organization of different VLANs in a proposed system, and
it forwards the data packets to all the goal VLAN gadget.
Switch It is a layer 2 gadget, which is utilized for interfacing the PC gadgets
such as servers, PCs, routers and printers together, where it goes
about as a scaffold. It comprises of different ports which procedures
and routes data packet in a system's data link layer.
Computer It refers to layer 1 end gadgets that are utilized to enter the client
data or through recovering the data from a system to user interfaces.
DHCP server It is a server which is utilized for assigning IP delivers to the gadgets
associated with a system.
WEB server It refers to server which is utilized for hosting the organization’s
website. It could be accessed by the users with the help of connected
computing devices.
It is a server which is utilized for having the site of an organization.
It can be received by the clients utilizing the associated computing
gadgets.
EMAIL server It refers to a server which is utilized for sharing the email documents
to different clients in an organization. It is also utilized as a
communication method.
DNS server It refers to a server which can be utilized for storing and dealing with
the index of domain names, which at that point means internet
protocol addresses. It can be utilized to get to the facilitated sites.
FILE server It refers to a server, which can be utilized for providing shared files and
disks locations to other network users.
It is a server, which can be utilized for giving the areas of the shared
file disks to different clients in a system.
Topology
7
Name of the
Device
Purpose of the Device
Router It is utilized as a layer 3 gadget for the most part to forward the data
packets to the goal IP locations and for the most part it is utilized to
perform organization of different VLANs in a proposed system, and
it forwards the data packets to all the goal VLAN gadget.
Switch It is a layer 2 gadget, which is utilized for interfacing the PC gadgets
such as servers, PCs, routers and printers together, where it goes
about as a scaffold. It comprises of different ports which procedures
and routes data packet in a system's data link layer.
Computer It refers to layer 1 end gadgets that are utilized to enter the client
data or through recovering the data from a system to user interfaces.
DHCP server It is a server which is utilized for assigning IP delivers to the gadgets
associated with a system.
WEB server It refers to server which is utilized for hosting the organization’s
website. It could be accessed by the users with the help of connected
computing devices.
It is a server which is utilized for having the site of an organization.
It can be received by the clients utilizing the associated computing
gadgets.
EMAIL server It refers to a server which is utilized for sharing the email documents
to different clients in an organization. It is also utilized as a
communication method.
DNS server It refers to a server which can be utilized for storing and dealing with
the index of domain names, which at that point means internet
protocol addresses. It can be utilized to get to the facilitated sites.
FILE server It refers to a server, which can be utilized for providing shared files and
disks locations to other network users.
It is a server, which can be utilized for giving the areas of the shared
file disks to different clients in a system.
Topology
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Topology comes with a good number of benefits when it comes to designing and
executing a network. We need to adapt a better topography, which can fulfil the present
criteria as well as the future requirements:
● The star topology are utilized in the network design, which guaranteed supporting
the network credible in the network’s future growth. It is best for evolving needs and
future reference.
● In a network, utilization of star topology design also supported with availability and
access network services, as the network remains up even when one end node device
fails. Because, it causes no harm to the whole network or other devices..
● The network design comprises of several plans for 4 departments, which have
accomplished the computers and printers, respectively. They are utilized by the
staffs of the organization.
● Network design contains DNS server, which is utilized for storing the domain names
directories.
● The network design contains an installed web server, which is utilized for hosting
the organization’s website system.
● Email is one of the catchy features of topography. The network design contains an
installed Email sever, which is utilized for sharing the mail messages with the
organization’s staff. Email is a special feature through which you can share so many
files and documents without any hassle.
● The network design contains an installed DHCP server, which is utilized to
automatically allocate the IP addresses to different network devices.
● The network design comprised of installed file server, which contains shared
memory to other devices for sharing the files and required applications. It stores a
backup of files for you.
Security
The proposed system structure uses different ways for verifying the system, to guarantee
the nature of administration requirements are meet, and the repetition is likewise executed
and Securing the organization network. There exists different estimates utilized for
8
executing a network. We need to adapt a better topography, which can fulfil the present
criteria as well as the future requirements:
● The star topology are utilized in the network design, which guaranteed supporting
the network credible in the network’s future growth. It is best for evolving needs and
future reference.
● In a network, utilization of star topology design also supported with availability and
access network services, as the network remains up even when one end node device
fails. Because, it causes no harm to the whole network or other devices..
● The network design comprises of several plans for 4 departments, which have
accomplished the computers and printers, respectively. They are utilized by the
staffs of the organization.
● Network design contains DNS server, which is utilized for storing the domain names
directories.
● The network design contains an installed web server, which is utilized for hosting
the organization’s website system.
● Email is one of the catchy features of topography. The network design contains an
installed Email sever, which is utilized for sharing the mail messages with the
organization’s staff. Email is a special feature through which you can share so many
files and documents without any hassle.
● The network design contains an installed DHCP server, which is utilized to
automatically allocate the IP addresses to different network devices.
● The network design comprised of installed file server, which contains shared
memory to other devices for sharing the files and required applications. It stores a
backup of files for you.
Security
The proposed system structure uses different ways for verifying the system, to guarantee
the nature of administration requirements are meet, and the repetition is likewise executed
and Securing the organization network. There exists different estimates utilized for
8

guaranteeing the security of a system which includes- Utilization of firewalls, encoding the
organization organize, and switch firmware redesigning.
Guaranteeing QoS
The executed system had additionally adjusted the nature of administration by
guaranteeing the organization system that is dependably ready for action, consistently.
Users & Scalability
Network design has the capacity of promoting growth, it can even aid the network
devices, then it can even support the availability, and even delivers security as follows:
● Network design could include more switches and the IP address space isn’t
exhausted. Therefore, it supports the future coming evolution demands.
● The network design has the capacity of accepting new and extra devices that are
later automatically allocated as IP addresses by the DHCP server.
● Network design can even aid the availability as it has the capacity of running even in
the case where one or more network devices fail without impacting the whole
network.
3.2 Designed Network Design’s Evaluation
Through this special feature, you can estimate the design particularly and also execute
and design network accordingly as per your desires. This area will have two areas, where the
section one will tell the best way to go about in structure and organizes the whole
organization which is a piece of any system execution. This will incorporate arrangement of
the different switches and changes, how to approach trucking and other innovation related
design, for example, VLANs, VTP, DHCP, and ACLs. Likewise, this area records the system
outline, end gadget design table, and the gadgets setup tables. In conclusion, this segment will
feature how the organization can actualize organize safety efforts to suite the given situation.
To a limited extent two will show and the system adaptability will be tested, which will
incorporate assessment, accessibility, testing, security, security, and survey of significant
zones that demands upgrading (Perez, 2014).
4. Task: 3
9
organization organize, and switch firmware redesigning.
Guaranteeing QoS
The executed system had additionally adjusted the nature of administration by
guaranteeing the organization system that is dependably ready for action, consistently.
Users & Scalability
Network design has the capacity of promoting growth, it can even aid the network
devices, then it can even support the availability, and even delivers security as follows:
● Network design could include more switches and the IP address space isn’t
exhausted. Therefore, it supports the future coming evolution demands.
● The network design has the capacity of accepting new and extra devices that are
later automatically allocated as IP addresses by the DHCP server.
● Network design can even aid the availability as it has the capacity of running even in
the case where one or more network devices fail without impacting the whole
network.
3.2 Designed Network Design’s Evaluation
Through this special feature, you can estimate the design particularly and also execute
and design network accordingly as per your desires. This area will have two areas, where the
section one will tell the best way to go about in structure and organizes the whole
organization which is a piece of any system execution. This will incorporate arrangement of
the different switches and changes, how to approach trucking and other innovation related
design, for example, VLANs, VTP, DHCP, and ACLs. Likewise, this area records the system
outline, end gadget design table, and the gadgets setup tables. In conclusion, this segment will
feature how the organization can actualize organize safety efforts to suite the given situation.
To a limited extent two will show and the system adaptability will be tested, which will
incorporate assessment, accessibility, testing, security, security, and survey of significant
zones that demands upgrading (Perez, 2014).
4. Task: 3
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
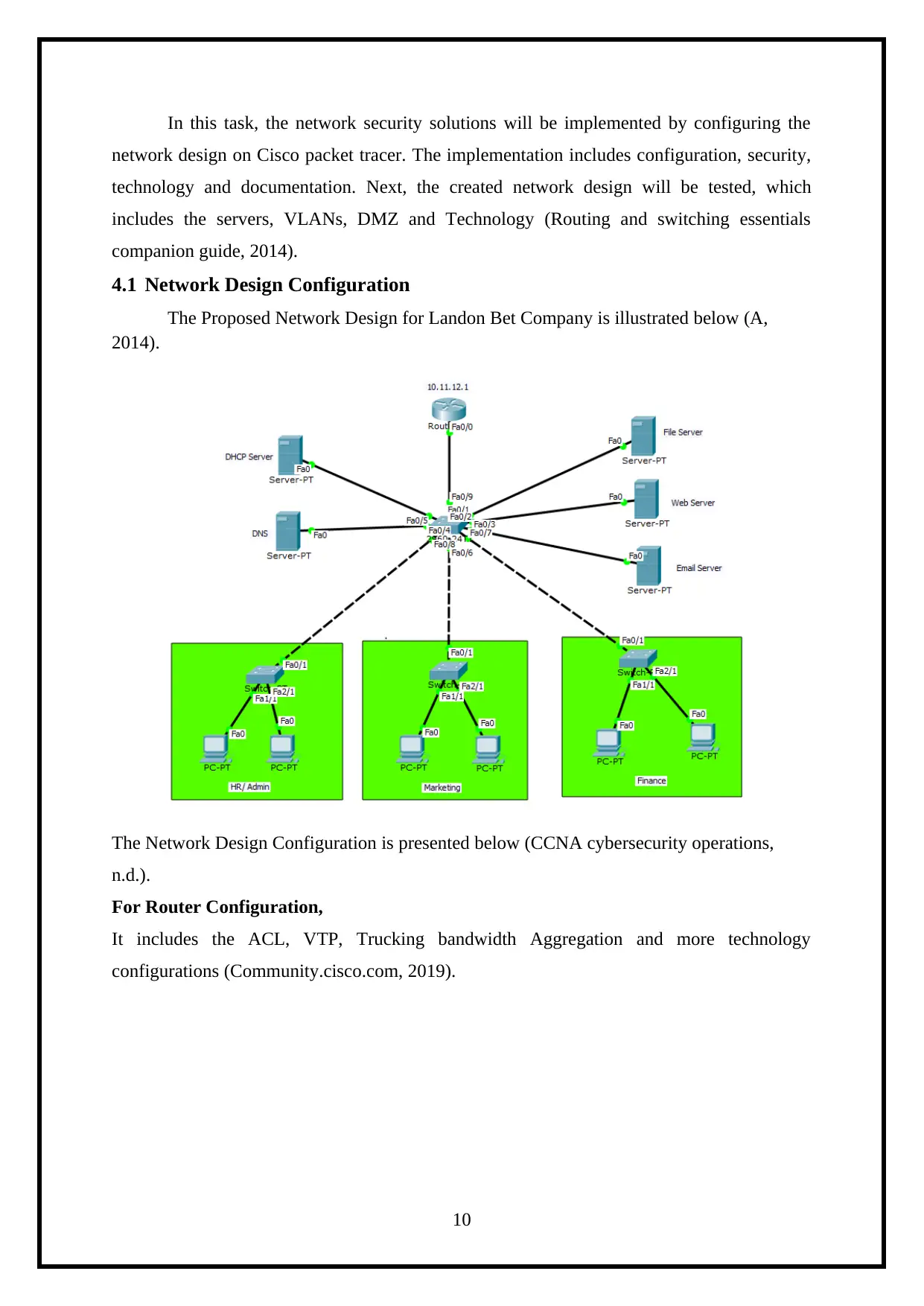
In this task, the network security solutions will be implemented by configuring the
network design on Cisco packet tracer. The implementation includes configuration, security,
technology and documentation. Next, the created network design will be tested, which
includes the servers, VLANs, DMZ and Technology (Routing and switching essentials
companion guide, 2014).
4.1 Network Design Configuration
The Proposed Network Design for Landon Bet Company is illustrated below (A,
2014).
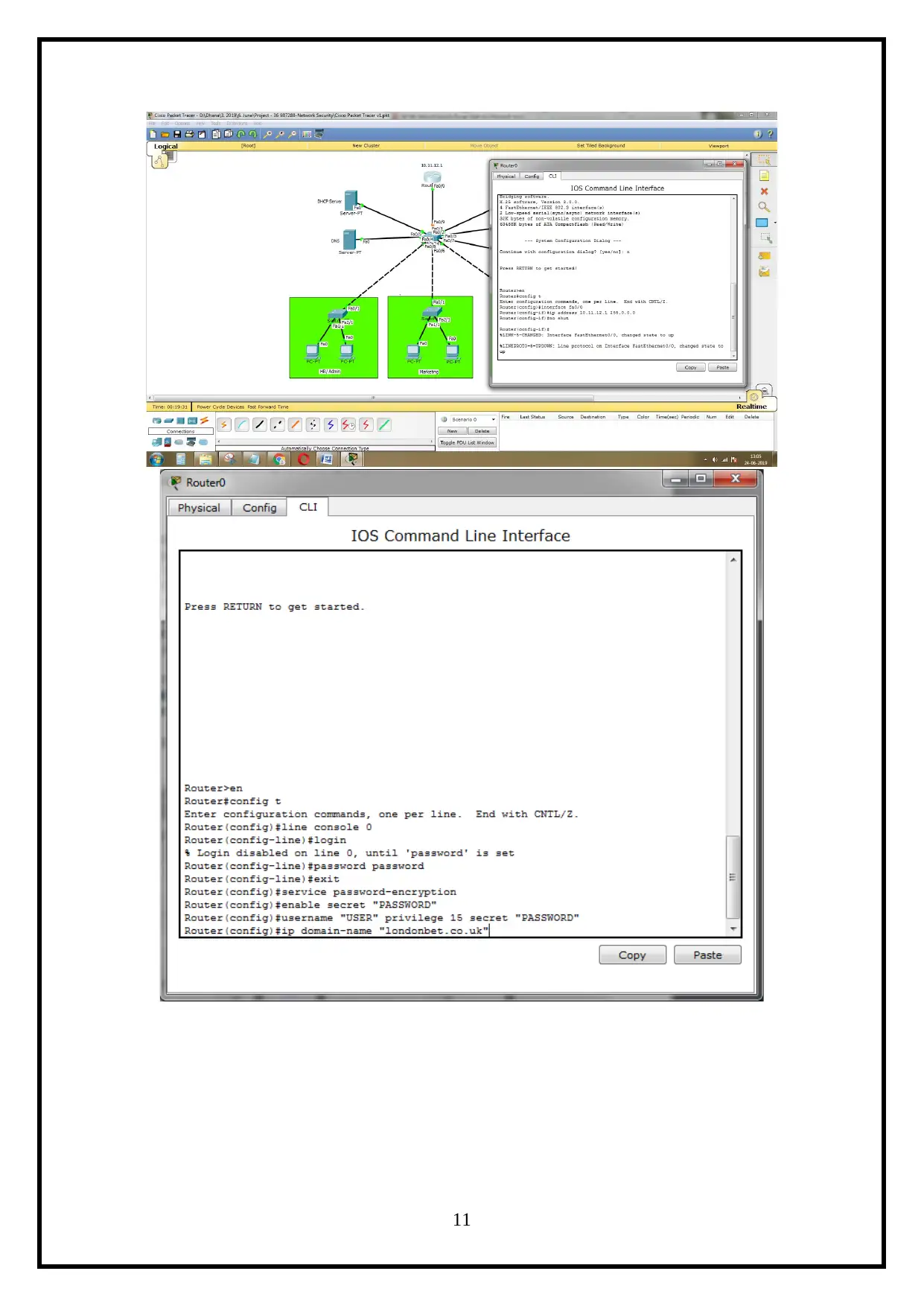
The Network Design Configuration is presented below (CCNA cybersecurity operations,
n.d.).
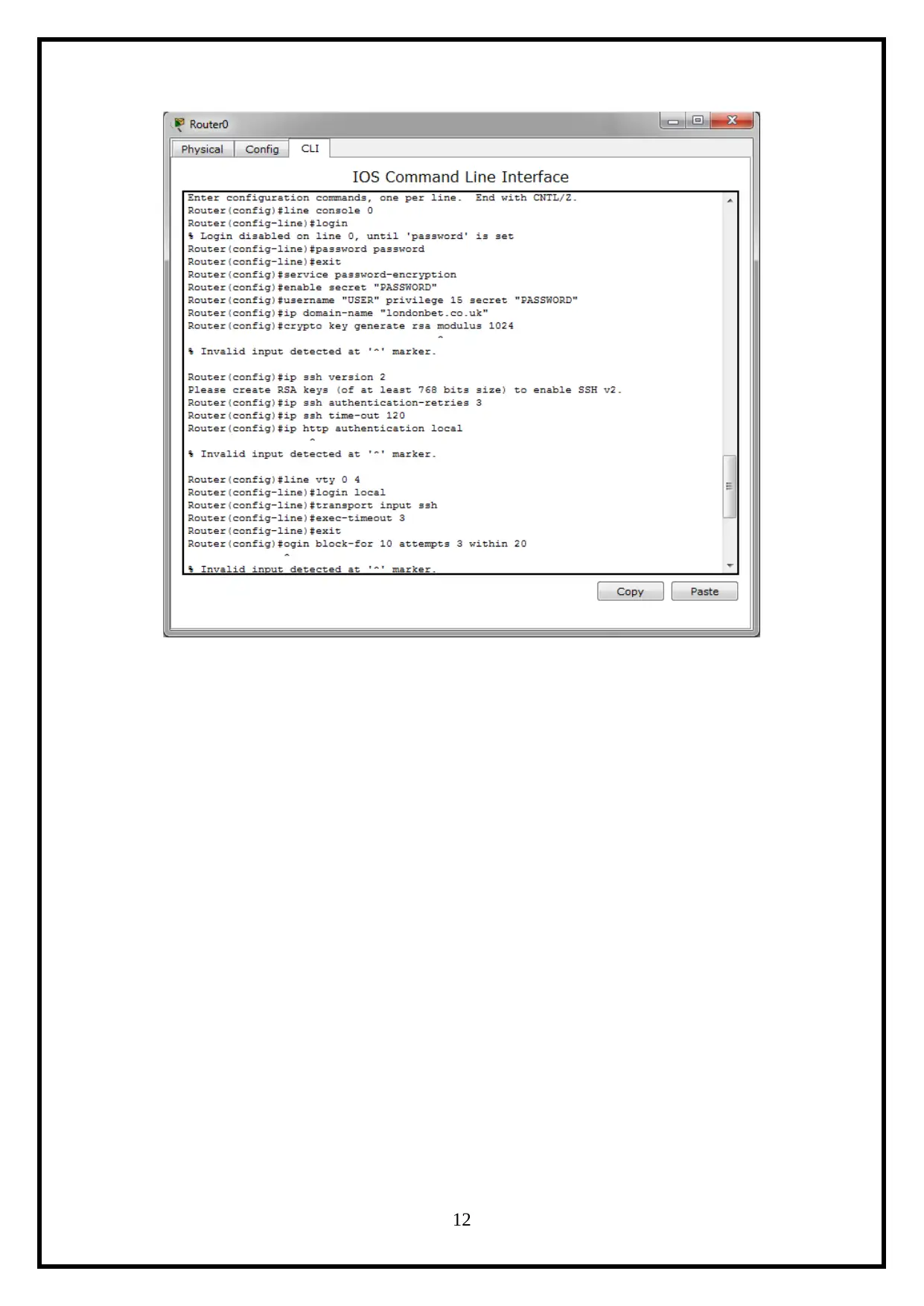
For Router Configuration,
It includes the ACL, VTP, Trucking bandwidth Aggregation and more technology
configurations (Community.cisco.com, 2019).
10
network design on Cisco packet tracer. The implementation includes configuration, security,
technology and documentation. Next, the created network design will be tested, which
includes the servers, VLANs, DMZ and Technology (Routing and switching essentials
companion guide, 2014).
4.1 Network Design Configuration
The Proposed Network Design for Landon Bet Company is illustrated below (A,
2014).
The Network Design Configuration is presented below (CCNA cybersecurity operations,
n.d.).
For Router Configuration,
It includes the ACL, VTP, Trucking bandwidth Aggregation and more technology
configurations (Community.cisco.com, 2019).
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 30
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




