6 Advance Network and Infrastructure Security Case Study for NPB Bank
VerifiedAdded on 2022/12/30
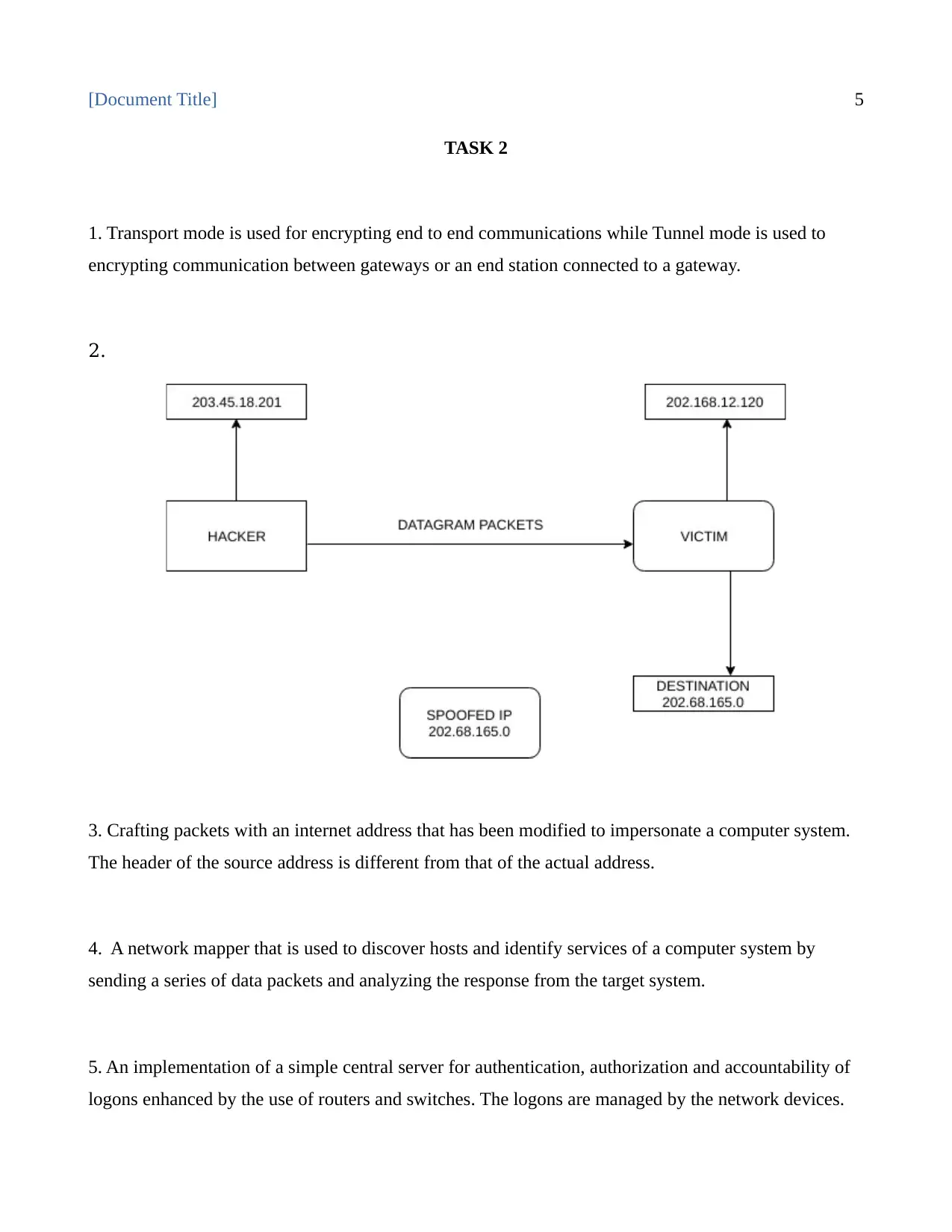
|7
|686
|84
Case Study
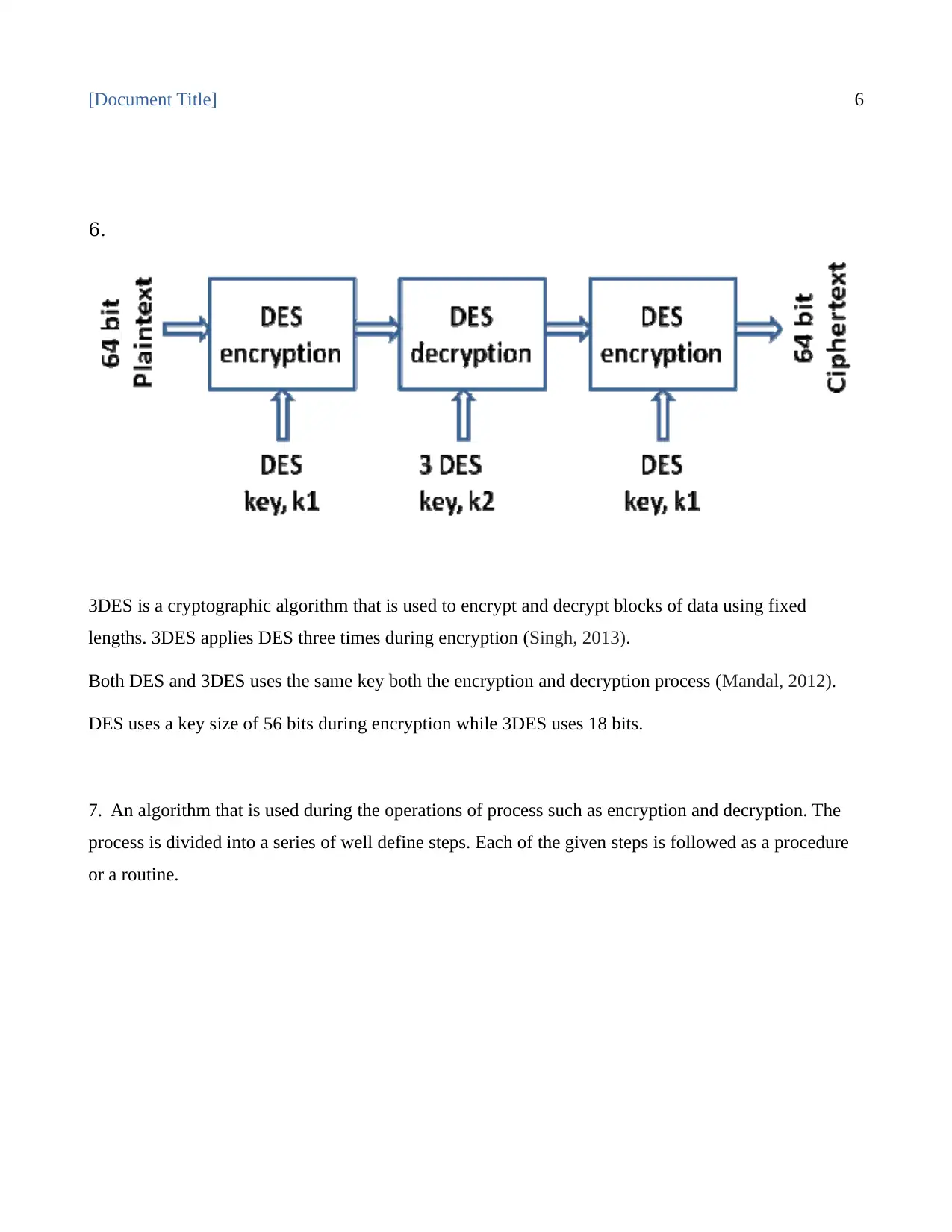
AI Summary
This case study examines the network and infrastructure security of National People's Bank (NPB), a major financial institution in Melbourne. The analysis focuses on vulnerabilities within the bank's online and mobile banking systems, including the use of HTTP protocol, password security, and data storage practices. The assignment explores the need for HTTPS migration, strong hashing algorithms, and normalization of data. It delves into cryptographic methods like AES and RSA, and discusses potential threats such as brute force and dictionary attacks. Furthermore, it addresses risk management strategies, including identifying areas of risk, implementing mitigation techniques, and establishing auditing processes. The study also highlights the importance of user awareness, policy enforcement, and the use of security protocols like IPsec (Transport and Tunnel modes), along with tools like network mappers and authentication servers. Finally, it touches on cryptographic algorithms like 3DES and their role in data encryption, providing a comprehensive overview of the bank's security posture and potential areas for improvement.
1 out of 7








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)