Information Security Project: Blowfish, HTTPS, and Network Firewalls
VerifiedAdded on 2021/06/17
|12
|3009
|22
Project
AI Summary
This project analyzes key aspects of information security, focusing on Blowfish encryption, HTTPS security, and network firewalls. The Blowfish section explains its symmetric block cipher nature, strengths like speed and key generation, and weaknesses like key management complexity. The HTTPS section explores its role in encrypting data, its advantages such as improved security and Google ranking, and disadvantages like resource consumption and latency. It also contrasts HTTPS with HTTP and details server setup. Finally, the project compares network firewalls, including Barracuda NextGen Firewall F10, SonicWall TZ 105, and Cisco ASA 5500-X Series Firewalls, highlighting their features and functionalities in protecting networks. The assignment provides a comprehensive overview of these critical security technologies.

1
Information Security
Name
Course
Professor
School
City
Date
Information Security
Name
Course
Professor
School
City
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
Chapter 5
Case Project 5-3: Blowfish
Blowfish is an encryption technique which is a very strong weapon against hackers as well as the
cyber criminals (Ab Rahman and Choo, 2015). It has been used widely in array of the products
which includes some secure emails encryption tools, backup software and password for the
management tools. It is a keyed symmetric cryptographic block cipher (Ab Rahman and Choo,
2015). It was created by Bruce Schneier in 1993. Given it have been reviewed substantially, it
has gained contentment as a powerful algorithm for encryption. It is license free of charge
actually it is easily available at no cost to almost all the customers (He, Machanavajjhala and
Ding, 2014). It is a symmetric block cipher in which is utilized as the decline in alternative for
the DES or maybe IDEA. The following are the strengths and the weaknesses of the encryption
algorithm.
Strengths and weakness of Blowfish
Strengths
It is an incredibly fast cipher- an encryption tool which has relatively simple structure and it is an
effective (Bulgurcu, Cavusoglu and Benbasat, 2010). It can generate massive vital which alone is
a major advantage to the security. With the increase in the speed of the computer processing, this
tool is able to create much longer key which can be difficult to try to hack the key value.
Blowfish is amongst the fastest block ciphers in the general usage, aside whenever changing the
keys. Each new key might necessitate pre-processing that is comparable to the encrypting in
relation to the 4 kilobytes of the text, which is slow compared to the other block ciphers
Chapter 5
Case Project 5-3: Blowfish
Blowfish is an encryption technique which is a very strong weapon against hackers as well as the
cyber criminals (Ab Rahman and Choo, 2015). It has been used widely in array of the products
which includes some secure emails encryption tools, backup software and password for the
management tools. It is a keyed symmetric cryptographic block cipher (Ab Rahman and Choo,
2015). It was created by Bruce Schneier in 1993. Given it have been reviewed substantially, it
has gained contentment as a powerful algorithm for encryption. It is license free of charge
actually it is easily available at no cost to almost all the customers (He, Machanavajjhala and
Ding, 2014). It is a symmetric block cipher in which is utilized as the decline in alternative for
the DES or maybe IDEA. The following are the strengths and the weaknesses of the encryption
algorithm.
Strengths and weakness of Blowfish
Strengths
It is an incredibly fast cipher- an encryption tool which has relatively simple structure and it is an
effective (Bulgurcu, Cavusoglu and Benbasat, 2010). It can generate massive vital which alone is
a major advantage to the security. With the increase in the speed of the computer processing, this
tool is able to create much longer key which can be difficult to try to hack the key value.
Blowfish is amongst the fastest block ciphers in the general usage, aside whenever changing the
keys. Each new key might necessitate pre-processing that is comparable to the encrypting in
relation to the 4 kilobytes of the text, which is slow compared to the other block ciphers

3
(Bulgurcu, Cavusoglu and Benbasat, 2010). This could prevent various programs, but not a
problem to the others such as SplashID. When it comes to the application, it is a benefit
particularly when password hashing technique has been used in the OpenBSD which utilized
algorithm which has been derived from Blowfish which make usage of slow key schedule (He,
Machanavajjhala and Ding, 2014).
The algorithm is not subject to any particular patents thus it is available for free to any user who
might want to use it (He, Machanavajjhala and Ding, 2014). This is a contribution to its
popularity in cryptographic programs.
Weaknesses
One of the disadvantage to this approach is that is should get key to the different away from the
band in particular not through unsecured channel of transmission. All pairs of end users should
be distinctive, thus as the number of the users improve, the key management evolves into a lot
complicated (Manku and Vasanth , 2015). Blowfish algorithm could not provide an
authentication as well as non repudiation given that two individuals that have key that is similar.
Moreover, it bears weaknesses in regards to the process of decryption over the other algorithms
in regards to the time consumption and serially in throughput.
Another weakness is the fact it should get fundamental key individuals out of band especially
not via unsecured transmission channel (Safa, Von Solms and Furnell, 2016). Each of the pair of
the customers’ needs to be unique, to ensure there is variety of the users’ increases , the
fundamental management turns into a lot complex for example N( N-1 )/2 keys which are
necessary.
How Blowfish it is currently used
(Bulgurcu, Cavusoglu and Benbasat, 2010). This could prevent various programs, but not a
problem to the others such as SplashID. When it comes to the application, it is a benefit
particularly when password hashing technique has been used in the OpenBSD which utilized
algorithm which has been derived from Blowfish which make usage of slow key schedule (He,
Machanavajjhala and Ding, 2014).
The algorithm is not subject to any particular patents thus it is available for free to any user who
might want to use it (He, Machanavajjhala and Ding, 2014). This is a contribution to its
popularity in cryptographic programs.
Weaknesses
One of the disadvantage to this approach is that is should get key to the different away from the
band in particular not through unsecured channel of transmission. All pairs of end users should
be distinctive, thus as the number of the users improve, the key management evolves into a lot
complicated (Manku and Vasanth , 2015). Blowfish algorithm could not provide an
authentication as well as non repudiation given that two individuals that have key that is similar.
Moreover, it bears weaknesses in regards to the process of decryption over the other algorithms
in regards to the time consumption and serially in throughput.
Another weakness is the fact it should get fundamental key individuals out of band especially
not via unsecured transmission channel (Safa, Von Solms and Furnell, 2016). Each of the pair of
the customers’ needs to be unique, to ensure there is variety of the users’ increases , the
fundamental management turns into a lot complex for example N( N-1 )/2 keys which are
necessary.
How Blowfish it is currently used
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
Blowfish is a symmetric key block cipher algorithm; it is used for confidential exchange of the
data such as emails, images and documents. As with all the symmetric algorithms it has a secure
way to exchange on the secret key for the secure communication. Blowfish can be employed as
an alternative for DES or IDEA algorithms. It is a symmetric that is an exclusive key which
utilizes variables length key, from the 32 bits to the 448 bits, which considers it great for both
domestic and exportable use (Catteddu, 2010). This cryptographic approach has become subject
to huge amount of the cryptanalysis. The encryption has certainly not been broken (Naylor,
Finamore, Leontiadis, Grunenberger, Mellia, Munafò, Papagiannaki and Steenkiste, 2014). It is
certainly the fastest block ciphers in the public use, thus making it to become perfect to the
products such as SplashID which functions to the wide variety of the processor which could be
found on the mobile phone and notebook.
Chapter 6
Case Project 6-4: HTTPS
HTTPS is a way to encrypting data which one sends between the browser and the web server
(Catteddu, 2010). This protects on the Websites udders from a kind of attack such as Man in the
middle, where one could steal data that is being sent to the website such as credit card
information or the logins.
What are the advantages of HTTPS?
Improved security: This is the reason as to why Google favors HTTPS since they want to attain
safest web experience to the users (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017).
Google adds criteria to their rankings algorithms when they have proven to offer a better users
Blowfish is a symmetric key block cipher algorithm; it is used for confidential exchange of the
data such as emails, images and documents. As with all the symmetric algorithms it has a secure
way to exchange on the secret key for the secure communication. Blowfish can be employed as
an alternative for DES or IDEA algorithms. It is a symmetric that is an exclusive key which
utilizes variables length key, from the 32 bits to the 448 bits, which considers it great for both
domestic and exportable use (Catteddu, 2010). This cryptographic approach has become subject
to huge amount of the cryptanalysis. The encryption has certainly not been broken (Naylor,
Finamore, Leontiadis, Grunenberger, Mellia, Munafò, Papagiannaki and Steenkiste, 2014). It is
certainly the fastest block ciphers in the public use, thus making it to become perfect to the
products such as SplashID which functions to the wide variety of the processor which could be
found on the mobile phone and notebook.
Chapter 6
Case Project 6-4: HTTPS
HTTPS is a way to encrypting data which one sends between the browser and the web server
(Catteddu, 2010). This protects on the Websites udders from a kind of attack such as Man in the
middle, where one could steal data that is being sent to the website such as credit card
information or the logins.
What are the advantages of HTTPS?
Improved security: This is the reason as to why Google favors HTTPS since they want to attain
safest web experience to the users (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017).
Google adds criteria to their rankings algorithms when they have proven to offer a better users
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
experience. HTTPS could protect the users’ data from the hackers (Felt, Barnes, King, Palmer,
Bentzel and Tabriz, 2017).
Increased Google Rankings: Over forty percent of all the sites on their first page of the Google
are HTTPS, since the organization confirmed that they favor HTTPS sites. They want to ensure
the best experience to their customers, thus, they do not want to send searchers to insecure sites.
Increased conversions: The users might not have technical understanding of connections which
are secure; they do understand that they want a site which is HTTPS if they are providing
personal data (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017).
Increased customer confidence: with the buzz going around in regards to HTTPS, there are many
users who are looking for connections which are secure when they visit a website (Felt, Barnes,
King, Palmer, Bentzel and Tabriz, 2017). A secure connection offers the client peace of mind to
their website so that they could be trusted and information is safe.
What are its disadvantages?
HTTPS utilized a lot of the server Resources: HTTPS requires a lot of processing power as well
as memory for the encryption (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). Some time
ago this could be a problem, unless the site was running on the server from back end.
HTTPS introduces Latencies: There are concerns on how it impacts on the latencies which are
based on the reality (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). The connections take
longer to set up and more roundtrips. HTTPS could cause delays thus; it is worthy to run tests in
order to ensure that SSL are not causing any real world latency.
experience. HTTPS could protect the users’ data from the hackers (Felt, Barnes, King, Palmer,
Bentzel and Tabriz, 2017).
Increased Google Rankings: Over forty percent of all the sites on their first page of the Google
are HTTPS, since the organization confirmed that they favor HTTPS sites. They want to ensure
the best experience to their customers, thus, they do not want to send searchers to insecure sites.
Increased conversions: The users might not have technical understanding of connections which
are secure; they do understand that they want a site which is HTTPS if they are providing
personal data (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017).
Increased customer confidence: with the buzz going around in regards to HTTPS, there are many
users who are looking for connections which are secure when they visit a website (Felt, Barnes,
King, Palmer, Bentzel and Tabriz, 2017). A secure connection offers the client peace of mind to
their website so that they could be trusted and information is safe.
What are its disadvantages?
HTTPS utilized a lot of the server Resources: HTTPS requires a lot of processing power as well
as memory for the encryption (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). Some time
ago this could be a problem, unless the site was running on the server from back end.
HTTPS introduces Latencies: There are concerns on how it impacts on the latencies which are
based on the reality (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). The connections take
longer to set up and more roundtrips. HTTPS could cause delays thus; it is worthy to run tests in
order to ensure that SSL are not causing any real world latency.

6
Proxy caching issues: Over the SSL connections, everything is usually encrypted which includes
the packet headers and the content (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). Any
caching which takes place between the points at which the data has been encrypted and
decrypted is blocked in case the content is encrypted (Ifinedo, 2014).
Mixed modes issues: when browsing the web, sometimes one could receive a warning which
highlights that the site is ostensibly using SSL and it is serving insecure content (Ifinedo, 2014).
This is because they are loading assets from the other sites or services which are not encrypted.
How is it different from HTTP?
HTTPS is regarded as Hypertext Transfer Protocol Secure. This involves the usage of SSL
certificate which represents the secure sockets layer which generates a secure encrypted
connection between the website server and web browser (Catteddu, 2010). The issue with HTTP
data is not encrypted and thus it is possible for the 3rd party to intercept the data which is being
passed between the two systems (Jeong, Seo, Cho, Kim and Park, 2015). Without HTTPS, any
specific data passed is insecure. This will be significant especially for the sites where sensitive
data has been passed across the connectivity for instance ecommerce sites which allow the online
credit card payments or perhaps login areas which necessitates the users to enter their
identification (Catteddu, 2010). HTTPS can make the sites substantially more secure from the
hacker as well as other security breaches. Therefore this is one of the biggest reasons to migrate
from HTTP to HTTPS.
How must the server be set up for HTTPS transactions?
To configure the HTTPS server the SSL guidelines should be allowed to the listening sockets in
server block, and location of server certificate and private key data files must be specified.
Proxy caching issues: Over the SSL connections, everything is usually encrypted which includes
the packet headers and the content (Felt, Barnes, King, Palmer, Bentzel and Tabriz, 2017). Any
caching which takes place between the points at which the data has been encrypted and
decrypted is blocked in case the content is encrypted (Ifinedo, 2014).
Mixed modes issues: when browsing the web, sometimes one could receive a warning which
highlights that the site is ostensibly using SSL and it is serving insecure content (Ifinedo, 2014).
This is because they are loading assets from the other sites or services which are not encrypted.
How is it different from HTTP?
HTTPS is regarded as Hypertext Transfer Protocol Secure. This involves the usage of SSL
certificate which represents the secure sockets layer which generates a secure encrypted
connection between the website server and web browser (Catteddu, 2010). The issue with HTTP
data is not encrypted and thus it is possible for the 3rd party to intercept the data which is being
passed between the two systems (Jeong, Seo, Cho, Kim and Park, 2015). Without HTTPS, any
specific data passed is insecure. This will be significant especially for the sites where sensitive
data has been passed across the connectivity for instance ecommerce sites which allow the online
credit card payments or perhaps login areas which necessitates the users to enter their
identification (Catteddu, 2010). HTTPS can make the sites substantially more secure from the
hacker as well as other security breaches. Therefore this is one of the biggest reasons to migrate
from HTTP to HTTPS.
How must the server be set up for HTTPS transactions?
To configure the HTTPS server the SSL guidelines should be allowed to the listening sockets in
server block, and location of server certificate and private key data files must be specified.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
Figure 1: Configuring HTTPS server
The server certificate is generally a public entity. It can be delivered to each client who links to
server. The private key is secure entity and should be stored to the file with the restricted access
(Jeong, Seo, Cho, Kim and Park, 2015). Nevertheless, it must be comprehensible by nginx’s
master process. Furthermore, the private key needs to be stored to the identical certificate
(Catteddu, 2010). The file access right should be restricted. The directive ssl protocols and ssl
ciphers are then utilized to limit on the connections to combine only the strong versions as well
as ciphers of SSL.
How would it protect you using a public Wi-Fi connection at a local coffee shop?
It is important to connect to the websites through HTTPS, which encrypts anything which
anything which is send and received from websites (McDonald and Sweet, 2015). While a VPN
service usually encrypts everything which is sent, HTTPS usually ensures that communication to
as well as from a given website is secure. To verify that one is connected through HTTPS, it is
important to look at the addresses bar of browsers window.
Should all Web traffic be required to use HTTPS?
Figure 1: Configuring HTTPS server
The server certificate is generally a public entity. It can be delivered to each client who links to
server. The private key is secure entity and should be stored to the file with the restricted access
(Jeong, Seo, Cho, Kim and Park, 2015). Nevertheless, it must be comprehensible by nginx’s
master process. Furthermore, the private key needs to be stored to the identical certificate
(Catteddu, 2010). The file access right should be restricted. The directive ssl protocols and ssl
ciphers are then utilized to limit on the connections to combine only the strong versions as well
as ciphers of SSL.
How would it protect you using a public Wi-Fi connection at a local coffee shop?
It is important to connect to the websites through HTTPS, which encrypts anything which
anything which is send and received from websites (McDonald and Sweet, 2015). While a VPN
service usually encrypts everything which is sent, HTTPS usually ensures that communication to
as well as from a given website is secure. To verify that one is connected through HTTPS, it is
important to look at the addresses bar of browsers window.
Should all Web traffic be required to use HTTPS?
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
Yes they should utilize HTTPS. One of the reasons is because of security. Even on the blogs they
are still have users who are logging into edit and write. No password should ever be passed in the
plain text. SSL is required for the encryption. HTTPS helps to establish a trust to prevent sign on
the site which could cause different risks for the business.
Chapter 7
Case Project 7-4: Network Firewall Comparison
Firewall is software in which blocks suspicious transmission between a program of a computer
and the network. Additionally, a firewall might block Drake software. The firewall usually loads
when one start their computers (Khandelwal, Agarwal and Stoica, 2016). Examples of the
firewalls are; Barracuda NextGen Firewell F10, SonicWall TZ 105, Cisco ASA 5500-X Series
Firewalls.
Barracuda NextGen Firewell F10
It is a family of the hardware as well as virtual appliances which safeguards the network,
enhances on the site to site connectivity and simplifies on the operations of the network. It may
include the subsequent generation firewall technologies that include the layer key application
controls, IPS, Web filtering, network access control and anti-virus. These types of firewalls
monitor the TCP handshaking between packets to be able to guarantee the session is legit. The
traffic is filtered that is depending on the numerous session rules and might be limited to
recognized computer systems. It is able to hide on the networks themselves from the outside, and
this useful to deny any access from the intruders.
SonicWall TZ 105
Yes they should utilize HTTPS. One of the reasons is because of security. Even on the blogs they
are still have users who are logging into edit and write. No password should ever be passed in the
plain text. SSL is required for the encryption. HTTPS helps to establish a trust to prevent sign on
the site which could cause different risks for the business.
Chapter 7
Case Project 7-4: Network Firewall Comparison
Firewall is software in which blocks suspicious transmission between a program of a computer
and the network. Additionally, a firewall might block Drake software. The firewall usually loads
when one start their computers (Khandelwal, Agarwal and Stoica, 2016). Examples of the
firewalls are; Barracuda NextGen Firewell F10, SonicWall TZ 105, Cisco ASA 5500-X Series
Firewalls.
Barracuda NextGen Firewell F10
It is a family of the hardware as well as virtual appliances which safeguards the network,
enhances on the site to site connectivity and simplifies on the operations of the network. It may
include the subsequent generation firewall technologies that include the layer key application
controls, IPS, Web filtering, network access control and anti-virus. These types of firewalls
monitor the TCP handshaking between packets to be able to guarantee the session is legit. The
traffic is filtered that is depending on the numerous session rules and might be limited to
recognized computer systems. It is able to hide on the networks themselves from the outside, and
this useful to deny any access from the intruders.
SonicWall TZ 105

9
This is the many secure and unified Threat Management firewall which is accessible to small
offices , home offices in addition to retail deployments. This technology delivers on the most
effective anti-malware, content/ URL filtering as well as application controls which have
capabilities to the broadest secure mobile platforms that support laptops, smartphones as well as
tablets (Ormazabal, Schulzrinne, Yardeni and Singh, Verizon Patent and Licensing Inc, 2016). It
offers a deep packet inspection to high level performance, thus, eliminating on the bottleneck
which other products introduce, and hence allowing business to realize on increased gains in
productivity.
Cisco ASA 5500-X Series Firewalls
This firewall delivers the network with the visibility one wants, superior threat as well as
advanced malware protection and a greater automation in order to reduce on the costs and the
complexity (Xu, Jiang, Wang, Yuan and Ren, 2014). This firewall assists organization to balance
on the security effectiveness with the productivity. This solution usually provides a combination
to the industry with most deployed state of the art firewall that has comprehensive range to the
next generation network security services.
This is the many secure and unified Threat Management firewall which is accessible to small
offices , home offices in addition to retail deployments. This technology delivers on the most
effective anti-malware, content/ URL filtering as well as application controls which have
capabilities to the broadest secure mobile platforms that support laptops, smartphones as well as
tablets (Ormazabal, Schulzrinne, Yardeni and Singh, Verizon Patent and Licensing Inc, 2016). It
offers a deep packet inspection to high level performance, thus, eliminating on the bottleneck
which other products introduce, and hence allowing business to realize on increased gains in
productivity.
Cisco ASA 5500-X Series Firewalls
This firewall delivers the network with the visibility one wants, superior threat as well as
advanced malware protection and a greater automation in order to reduce on the costs and the
complexity (Xu, Jiang, Wang, Yuan and Ren, 2014). This firewall assists organization to balance
on the security effectiveness with the productivity. This solution usually provides a combination
to the industry with most deployed state of the art firewall that has comprehensive range to the
next generation network security services.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
10
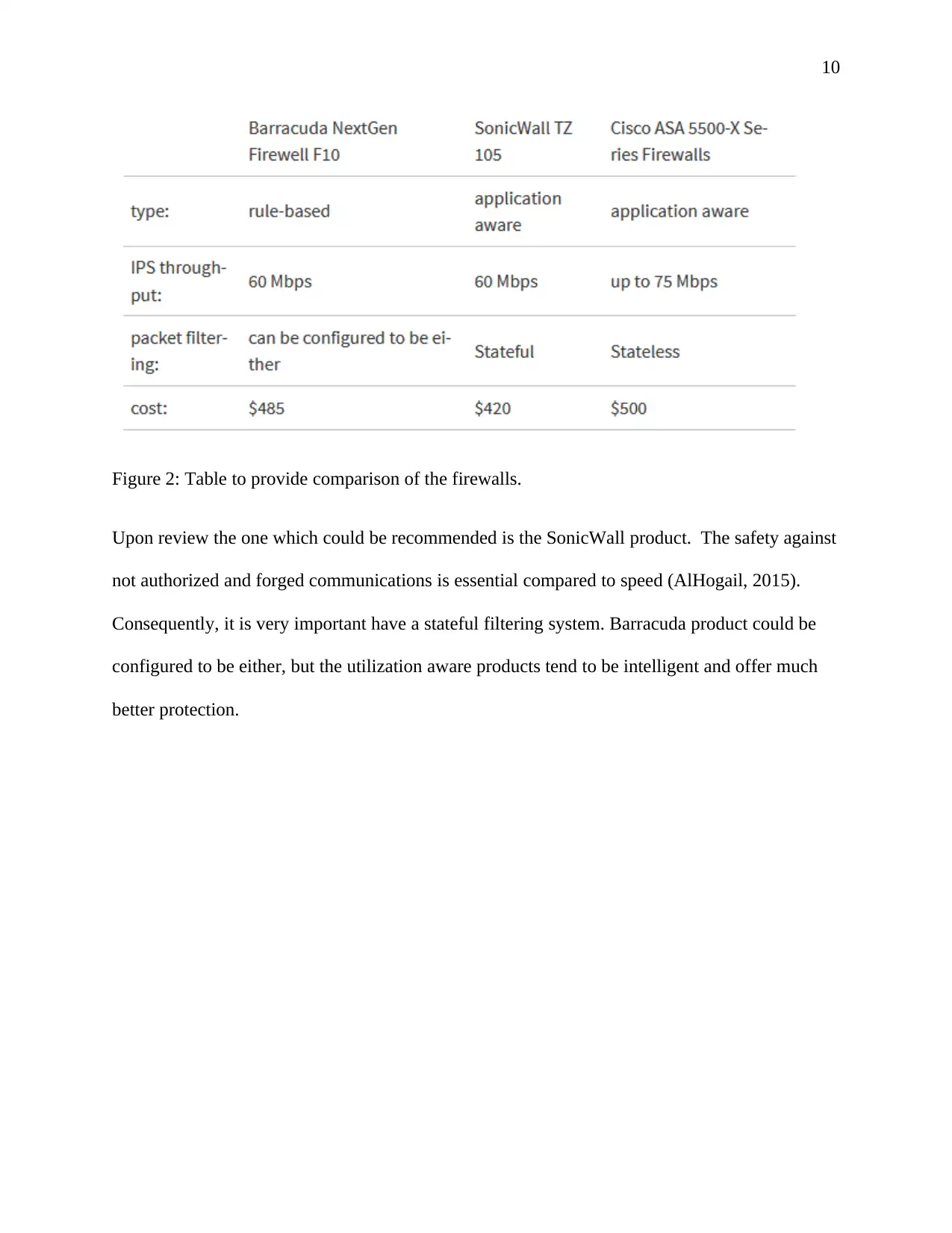
Figure 2: Table to provide comparison of the firewalls.
Upon review the one which could be recommended is the SonicWall product. The safety against
not authorized and forged communications is essential compared to speed (AlHogail, 2015).
Consequently, it is very important have a stateful filtering system. Barracuda product could be
configured to be either, but the utilization aware products tend to be intelligent and offer much
better protection.
Figure 2: Table to provide comparison of the firewalls.
Upon review the one which could be recommended is the SonicWall product. The safety against
not authorized and forged communications is essential compared to speed (AlHogail, 2015).
Consequently, it is very important have a stateful filtering system. Barracuda product could be
configured to be either, but the utilization aware products tend to be intelligent and offer much
better protection.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

11
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident handling
in the cloud. Computers & Security, 49, pp.45-69.
AlHogail, A., 2015. Design and validation of information security culture framework. Computers
in Human Behavior, 49, pp.567-575.
Bulgurcu, B., Cavusoglu, H. and Benbasat, I., 2010. Information security policy compliance: an
empirical study of rationality-based beliefs and information security awareness. MIS quarterly,
34(3), pp.523-548.
Catteddu, D., 2010. Cloud Computing: benefits, risks and recommendations for information
security. In Web application security (pp. 17-17). Springer, Berlin, Heidelberg.
Felt, A.P., Barnes, R., King, A., Palmer, C., Bentzel, C. and Tabriz, P., 2017. Measuring HTTPS
adoption on the web. In 26th USENIX Security Symposium (pp. 1323-1338).
He, X., Machanavajjhala, A. and Ding, B., 2014, June. Blowfish privacy: Tuning privacy-utility
trade-offs using policies. In Proceedings of the 2014 ACM SIGMOD international conference on
Management of data (pp. 1447-1458). ACM.
Jeong, J., Seo, J., Cho, G., Kim, H. and Park, J.S., 2015, March. A framework for security
services based on software-defined networking. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 150-153).
IEEE.
Khandelwal, A., Agarwal, R. and Stoica, I., 2016, March. BlowFish: Dynamic Storage-
Performance Tradeoff in Data Stores. In NSDI (pp. 485-500).
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-79.
Manku, S. and Vasanth, K., 2015. Blowfish encryption algorithm for information security. ARPN
Journal of Engineering and Applied Sciences, 10(10), pp.4717-4719.
McDonald, I. and Sweet, M., 2015. Internet Printing Protocol (IPP) over HTTPS Transport
Binding and the'ipps' URI Scheme.
Naylor, D., Finamore, A., Leontiadis, I., Grunenberger, Y., Mellia, M., Munafò, M.,
Papagiannaki, K. and Steenkiste, P., 2014, December. The cost of the S in HTTPS. In
Proceedings of the 10th ACM International on Conference on emerging Networking Experiments
and Technologies (pp. 133-140). ACM.
References
Ab Rahman, N.H. and Choo, K.K.R., 2015. A survey of information security incident handling
in the cloud. Computers & Security, 49, pp.45-69.
AlHogail, A., 2015. Design and validation of information security culture framework. Computers
in Human Behavior, 49, pp.567-575.
Bulgurcu, B., Cavusoglu, H. and Benbasat, I., 2010. Information security policy compliance: an
empirical study of rationality-based beliefs and information security awareness. MIS quarterly,
34(3), pp.523-548.
Catteddu, D., 2010. Cloud Computing: benefits, risks and recommendations for information
security. In Web application security (pp. 17-17). Springer, Berlin, Heidelberg.
Felt, A.P., Barnes, R., King, A., Palmer, C., Bentzel, C. and Tabriz, P., 2017. Measuring HTTPS
adoption on the web. In 26th USENIX Security Symposium (pp. 1323-1338).
He, X., Machanavajjhala, A. and Ding, B., 2014, June. Blowfish privacy: Tuning privacy-utility
trade-offs using policies. In Proceedings of the 2014 ACM SIGMOD international conference on
Management of data (pp. 1447-1458). ACM.
Jeong, J., Seo, J., Cho, G., Kim, H. and Park, J.S., 2015, March. A framework for security
services based on software-defined networking. In Advanced Information Networking and
Applications Workshops (WAINA), 2015 IEEE 29th International Conference on (pp. 150-153).
IEEE.
Khandelwal, A., Agarwal, R. and Stoica, I., 2016, March. BlowFish: Dynamic Storage-
Performance Tradeoff in Data Stores. In NSDI (pp. 485-500).
Ifinedo, P., 2014. Information systems security policy compliance: An empirical study of the
effects of socialisation, influence, and cognition. Information & Management, 51(1), pp.69-79.
Manku, S. and Vasanth, K., 2015. Blowfish encryption algorithm for information security. ARPN
Journal of Engineering and Applied Sciences, 10(10), pp.4717-4719.
McDonald, I. and Sweet, M., 2015. Internet Printing Protocol (IPP) over HTTPS Transport
Binding and the'ipps' URI Scheme.
Naylor, D., Finamore, A., Leontiadis, I., Grunenberger, Y., Mellia, M., Munafò, M.,
Papagiannaki, K. and Steenkiste, P., 2014, December. The cost of the S in HTTPS. In
Proceedings of the 10th ACM International on Conference on emerging Networking Experiments
and Technologies (pp. 133-140). ACM.

12
Ormazabal, G.S., Schulzrinne, H.G., Yardeni, E. and Singh, K., Verizon Patent and Licensing
Inc, 2016. System and method for testing network firewall using fine granularity measurements.
U.S. Patent 9,374,342.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Xu, L., Jiang, C., Wang, J., Yuan, J. and Ren, Y., 2014. Information security in big data: privacy
and data mining. IEEE Access, 2, pp.1149-1176.
Ormazabal, G.S., Schulzrinne, H.G., Yardeni, E. and Singh, K., Verizon Patent and Licensing
Inc, 2016. System and method for testing network firewall using fine granularity measurements.
U.S. Patent 9,374,342.
Safa, N.S., Von Solms, R. and Furnell, S., 2016. Information security policy compliance model
in organizations. Computers & Security, 56, pp.70-82.
Xu, L., Jiang, C., Wang, J., Yuan, J. and Ren, Y., 2014. Information security in big data: privacy
and data mining. IEEE Access, 2, pp.1149-1176.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
