Network Security Report: Threat Classification and Controls
VerifiedAdded on 2021/09/19
|8
|1020
|164
Report
AI Summary
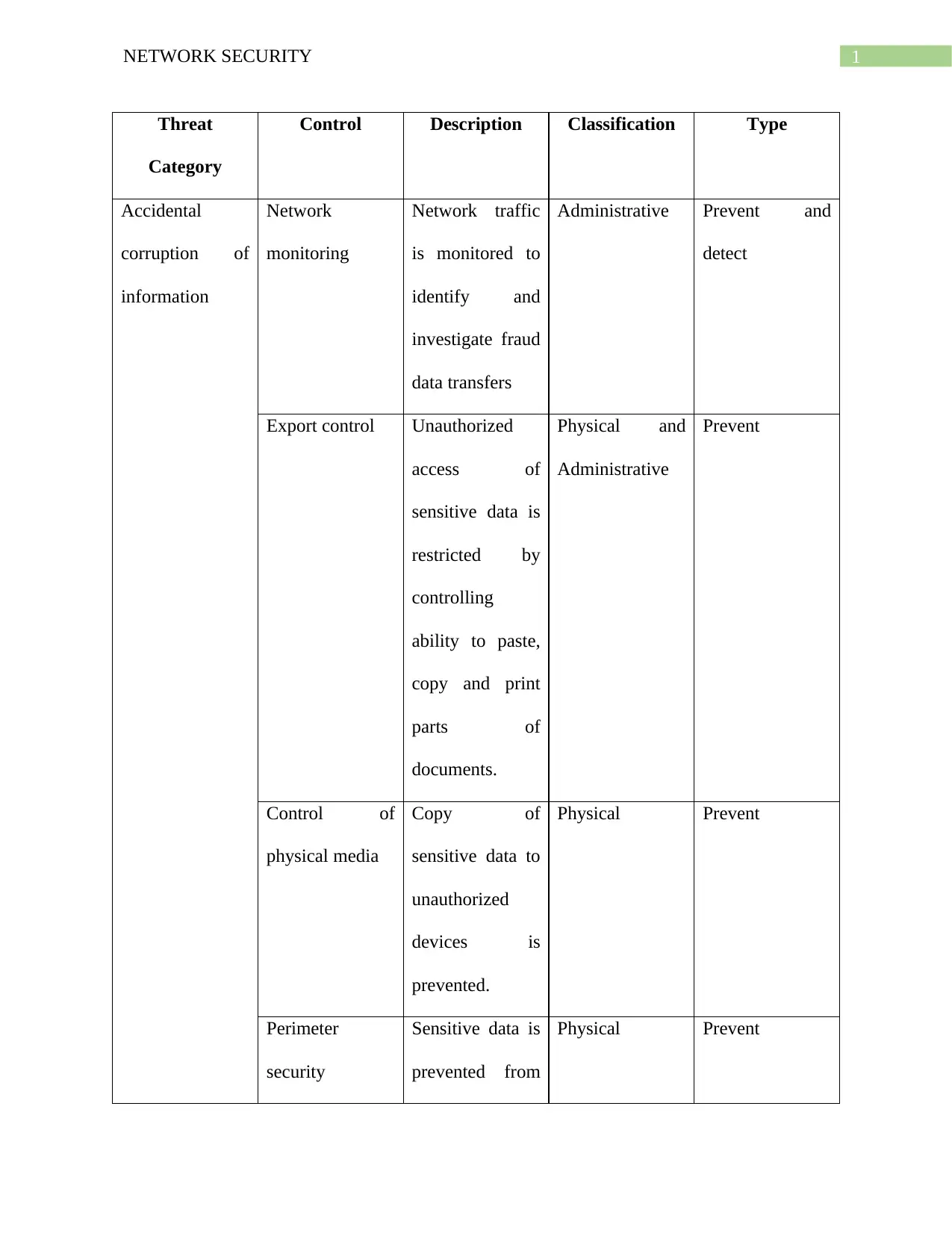
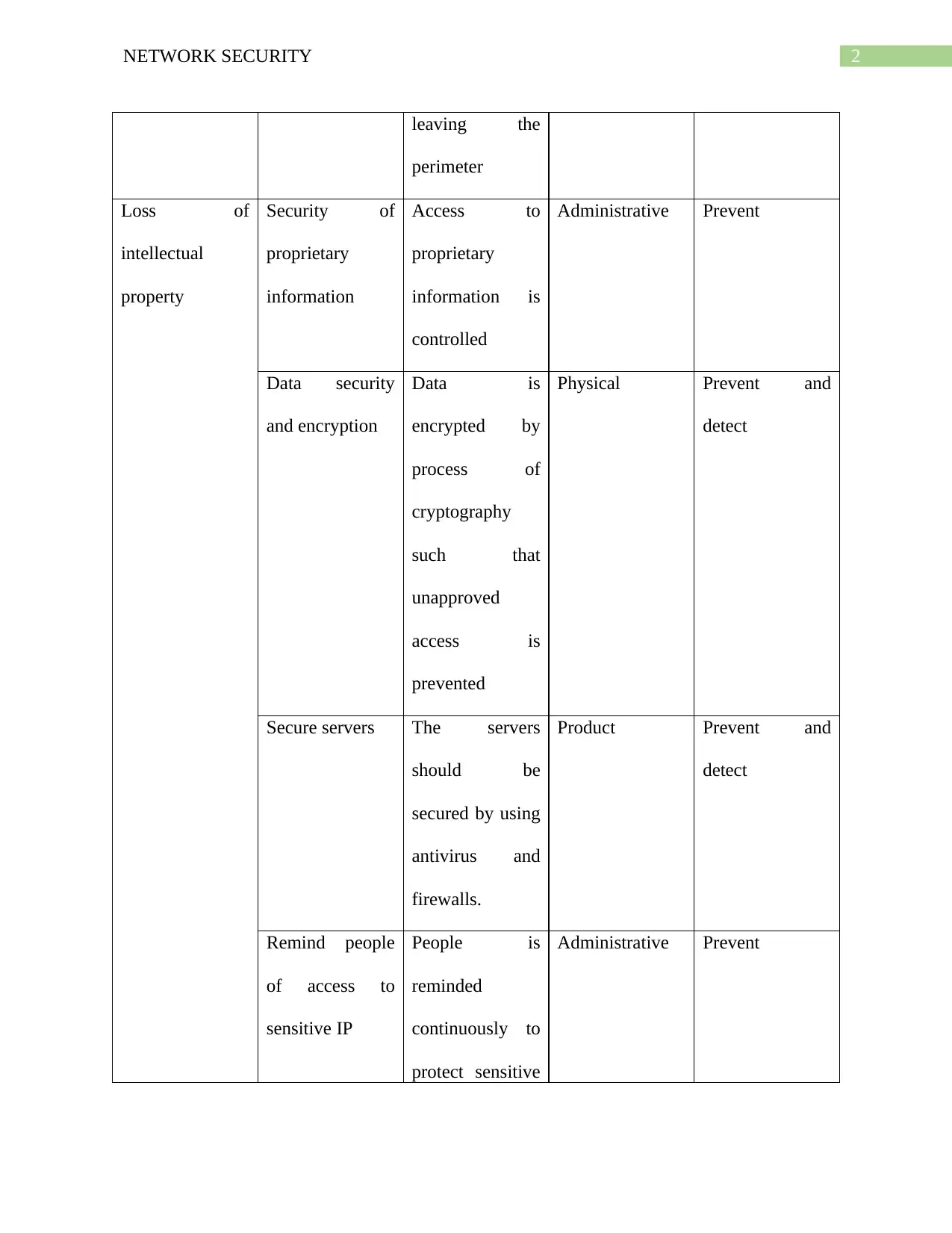
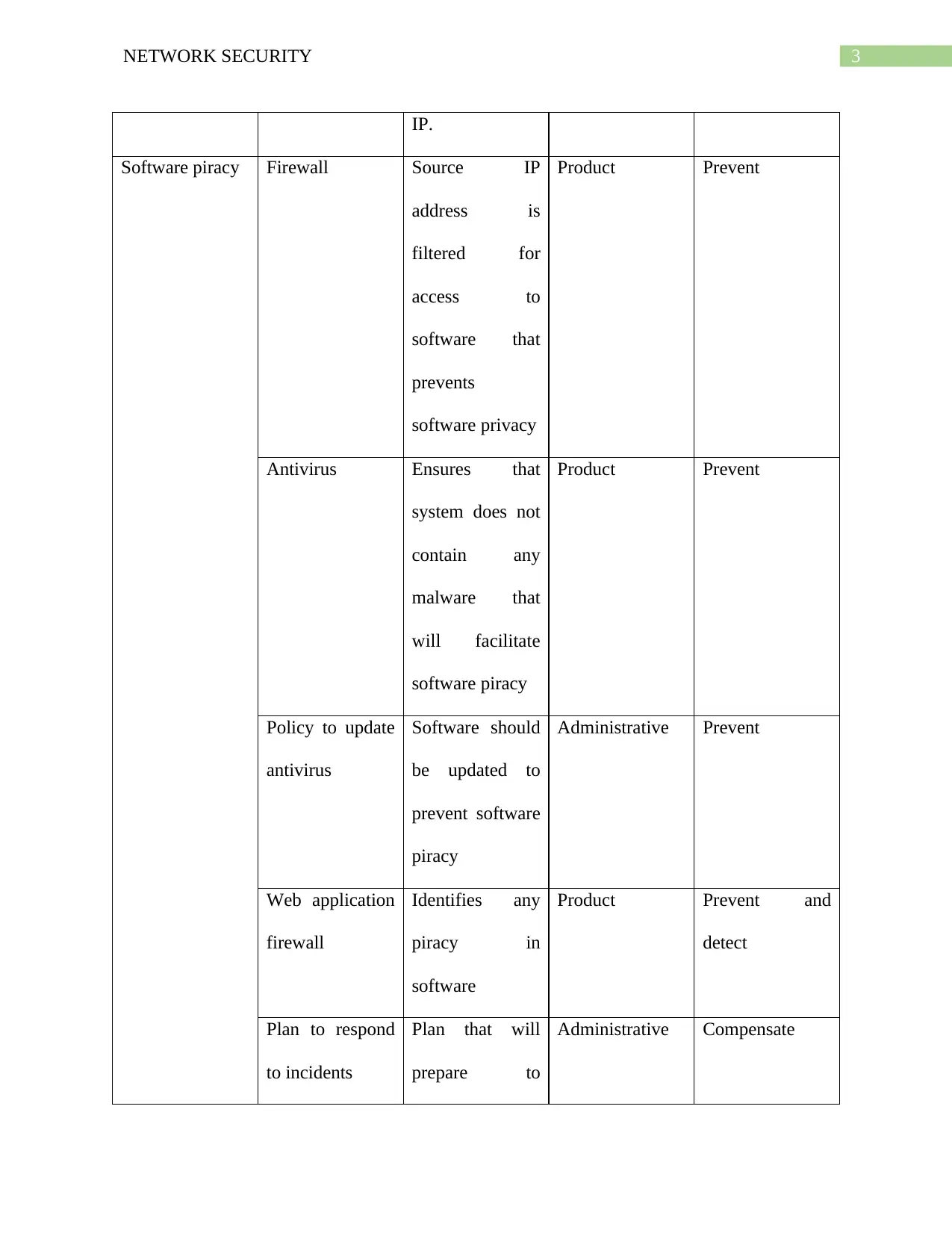
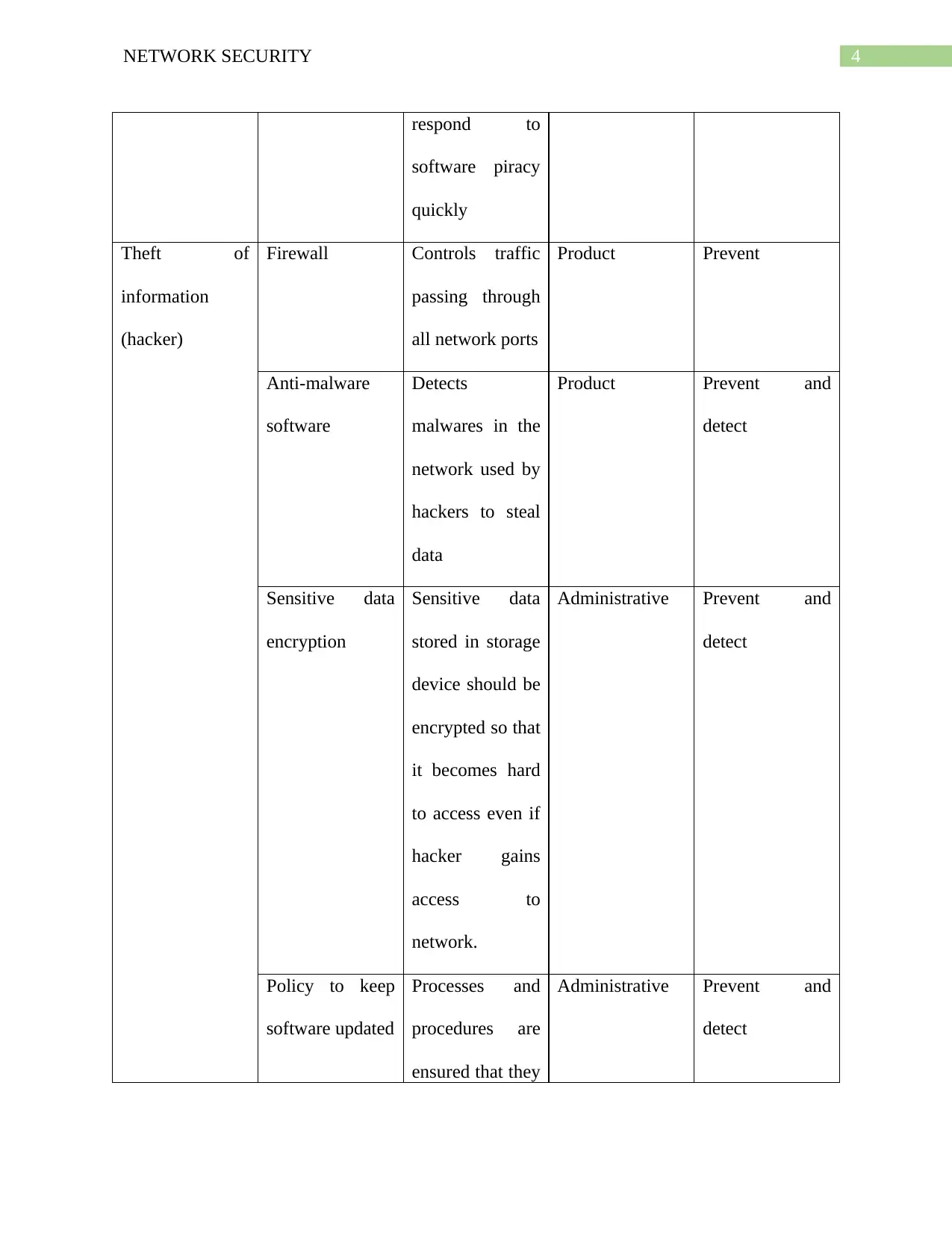
This report provides a detailed analysis of various network security threats and the corresponding control measures. It categorizes threats such as accidental information corruption, unauthorized data access, and theft of information, classifying them based on their nature and potential impact. The report then outlines specific control descriptions, including network monitoring, access restrictions, data encryption, firewall configurations, and the use of antivirus and anti-malware software. These controls are classified into types like administrative, physical, and product-based measures. The report also covers topics like web application firewalls, intrusion detection systems, and incident response plans. Furthermore, the report highlights the importance of keeping software updated, securing servers, and implementing policies to prevent software piracy and equipment theft. The document concludes by emphasizing the significance of employee training, secure connections, and website monitoring tools to maintain robust network security. References to support the analysis are also provided.
1 out of 8








![[object Object]](/_next/static/media/star-bottom.7253800d.svg)