Network Implementation and Security Planning for Business - Report
VerifiedAdded on 2023/04/17
|9
|1352
|248
Report
AI Summary
This report addresses network implementation and security planning for a business, focusing on the needs of a client named Bill. It begins with an Excel task, detailing formulas for calculating daily and weekly expenses. The core of the report compares different LAN topologies, including bus, ring, and star topologies, evaluating their advantages and disadvantages. The report suggests the best topology for Bill's needs, emphasizing the importance of switches for optimal performance. It then delves into network safety and security, covering essential practices like auditing and mapping, keeping the network up-to-date, physical security, MAC address filtering, and the use of antivirus software. The report concludes by emphasizing the importance of a layered approach to network security to protect against various threats. The report provides a comprehensive overview of network planning and security, offering practical recommendations for securing a business network.

Running head: NETWORK IMPLEMENTATION AND SECURITY PLANNING
Network Implementation and Security Planning
Name of the Organization
Name of the University
Author’s note:
Network Implementation and Security Planning
Name of the Organization
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK IMPLEMENTATION AND SECURITY PLANNING
Table of Contents
Excel Task:......................................................................................................................................2
New Network Proposal:...................................................................................................................2
Network Safety and Security:..........................................................................................................5
References:......................................................................................................................................7
Table of Contents
Excel Task:......................................................................................................................................2
New Network Proposal:...................................................................................................................2
Network Safety and Security:..........................................................................................................5
References:......................................................................................................................................7
2NETWORK IMPLEMENTATION AND SECURITY PLANNING
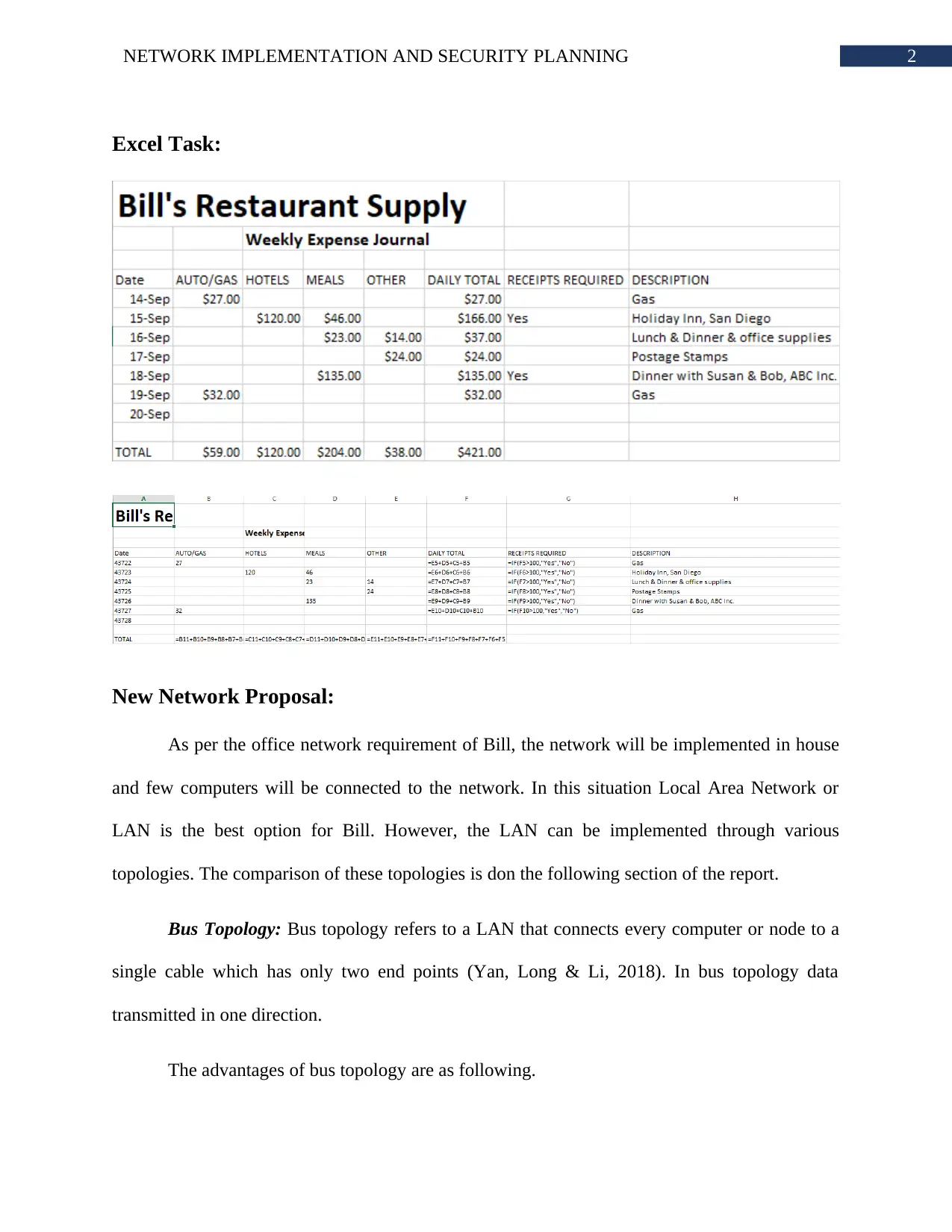
Excel Task:
New Network Proposal:
As per the office network requirement of Bill, the network will be implemented in house
and few computers will be connected to the network. In this situation Local Area Network or
LAN is the best option for Bill. However, the LAN can be implemented through various
topologies. The comparison of these topologies is don the following section of the report.
Bus Topology: Bus topology refers to a LAN that connects every computer or node to a
single cable which has only two end points (Yan, Long & Li, 2018). In bus topology data
transmitted in one direction.
The advantages of bus topology are as following.
Excel Task:
New Network Proposal:
As per the office network requirement of Bill, the network will be implemented in house
and few computers will be connected to the network. In this situation Local Area Network or
LAN is the best option for Bill. However, the LAN can be implemented through various
topologies. The comparison of these topologies is don the following section of the report.
Bus Topology: Bus topology refers to a LAN that connects every computer or node to a
single cable which has only two end points (Yan, Long & Li, 2018). In bus topology data
transmitted in one direction.
The advantages of bus topology are as following.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK IMPLEMENTATION AND SECURITY PLANNING
i. This topology can be implemented in low cost
ii. The number of cable required is less than any other topology
iii. The Bus topology is preferred for small network
iv. The bus topology is easy to understand and upgrade
The disadvantages of bus topology are as following.
i. The availability of the network strongly dependent on the cable
ii. This topology uses HUB, therefore network traffic is not monitored by any device
iii. This topology is far slower than ring topology
Ring Topology: This topology is named after the connection between each computer. In
this topology, the computers are connected to each other. The first computer is connected to at
least one computer and other computers are connected to adjacent computers. In Ring topology,
the transmission is generally done in unidirectional way however, transmission can be made
bidirectional (Dorta et al., 2016). The bidirectional topology is named as Dual Ring Topology. In
Ring Topology, the data transmission is done sequential way that is bit by bit. Each data is
transmitted through intermediate computers until the destination computer is reached.
The advantages of the Ring topology are as following.
i. Neither high traffic nor additional of extra computers affects the transmission
network
ii. The nodes in the network that has tokens can transmit data over the network
iii. The topology is easy to install and upgrade
Disadvantages of Ring topology.
i. This topology can be implemented in low cost
ii. The number of cable required is less than any other topology
iii. The Bus topology is preferred for small network
iv. The bus topology is easy to understand and upgrade
The disadvantages of bus topology are as following.
i. The availability of the network strongly dependent on the cable
ii. This topology uses HUB, therefore network traffic is not monitored by any device
iii. This topology is far slower than ring topology
Ring Topology: This topology is named after the connection between each computer. In
this topology, the computers are connected to each other. The first computer is connected to at
least one computer and other computers are connected to adjacent computers. In Ring topology,
the transmission is generally done in unidirectional way however, transmission can be made
bidirectional (Dorta et al., 2016). The bidirectional topology is named as Dual Ring Topology. In
Ring Topology, the data transmission is done sequential way that is bit by bit. Each data is
transmitted through intermediate computers until the destination computer is reached.
The advantages of the Ring topology are as following.
i. Neither high traffic nor additional of extra computers affects the transmission
network
ii. The nodes in the network that has tokens can transmit data over the network
iii. The topology is easy to install and upgrade
Disadvantages of Ring topology.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK IMPLEMENTATION AND SECURITY PLANNING
i. In ring topology, the trouble shooting can be difficult
ii. The network activity can be disrupted by deleting or adding nodes
iii. If one computer connection is lost then whole or partial network can be delinked
Star Topology: In star topology, each computer in the network is connected to a single
hub/switch through cables or wireless connection. The hub/switch works as the central node in
the network and control the traffic flow. Each node in the star topology can have dedicated
hub/switch connection (Balabanov, Zankinski & Barova, 2016). The hub/switch behave like a
data flow in the network. The network can utilize optical fiber, twisted pair, coaxial cable or
wireless connection.
Advantages of Star topology are as following.
i. The performance of the network becomes high and network traffic becomes very
less
ii. The switch/hub can be updated very easily
iii. The troubleshoot of network is very easy
iv. The topology is extremely easy to configure and modify
v. Can be expanded easily
vi. Only one node connection is affected due to cable damage
The disadvantages of Star topology are as following.
i. The installation price is high than ring and bus
ii. The network maintenance will be high
iii. The whole network depends on the switch/hub
iv. The network performance is based on the quality and capacity of switch/hub
i. In ring topology, the trouble shooting can be difficult
ii. The network activity can be disrupted by deleting or adding nodes
iii. If one computer connection is lost then whole or partial network can be delinked
Star Topology: In star topology, each computer in the network is connected to a single
hub/switch through cables or wireless connection. The hub/switch works as the central node in
the network and control the traffic flow. Each node in the star topology can have dedicated
hub/switch connection (Balabanov, Zankinski & Barova, 2016). The hub/switch behave like a
data flow in the network. The network can utilize optical fiber, twisted pair, coaxial cable or
wireless connection.
Advantages of Star topology are as following.
i. The performance of the network becomes high and network traffic becomes very
less
ii. The switch/hub can be updated very easily
iii. The troubleshoot of network is very easy
iv. The topology is extremely easy to configure and modify
v. Can be expanded easily
vi. Only one node connection is affected due to cable damage
The disadvantages of Star topology are as following.
i. The installation price is high than ring and bus
ii. The network maintenance will be high
iii. The whole network depends on the switch/hub
iv. The network performance is based on the quality and capacity of switch/hub

5NETWORK IMPLEMENTATION AND SECURITY PLANNING
Suggestion: Any of the above discussed network topologies can be used by Bill to
implement a Local Area Network. The Bus topology would not be a good choice as each packet
will travel through all the computers and the network performance will be low. This same
situation will be experienced if Ring topology is used. However, the network performance would
depend on the distance between destination computer and first computer. The whole scenario of
network traffic will change if Star topology is used. It is essential to remember that Bill must use
switch to enhance the traffic performance. Otherwise, the star topology will act like a bus
topology. Each computer will be connected to the central switch and switch to router and router
to ISP or Internet Service Provider. The switches has integrated circuit that can store the MAC
addresses of connected computers. This MAC address list will be used by the Switch for
controlling the traffic.
Network Safety and Security:
Perform Auditing and Mapping: The mapping of the network should be done every
week. Bill must have clear understanding reading the infrastructure of the network. Taken as an
example, Bill must know about the firewall, router, switch, connection type, ISP services, ports
connected to computers and more (Snapp et al., 2017). Network auditing and mapping will
reveal the network security loopholes which is very essential for continuously improve network
security.
Keeping Network Up-to-Date: Once the auditing and mapping process will be done, Bill
must dive deeper into network security. Checking software updates and firmware of all the
networking devices is essential to implement network security (Perlman, Kaufman & Speciner,
2016). Bill must login to each network devices such as router, switch, firewall and few more to
ensure that default password is changed to a strong and secure password.
Suggestion: Any of the above discussed network topologies can be used by Bill to
implement a Local Area Network. The Bus topology would not be a good choice as each packet
will travel through all the computers and the network performance will be low. This same
situation will be experienced if Ring topology is used. However, the network performance would
depend on the distance between destination computer and first computer. The whole scenario of
network traffic will change if Star topology is used. It is essential to remember that Bill must use
switch to enhance the traffic performance. Otherwise, the star topology will act like a bus
topology. Each computer will be connected to the central switch and switch to router and router
to ISP or Internet Service Provider. The switches has integrated circuit that can store the MAC
addresses of connected computers. This MAC address list will be used by the Switch for
controlling the traffic.
Network Safety and Security:
Perform Auditing and Mapping: The mapping of the network should be done every
week. Bill must have clear understanding reading the infrastructure of the network. Taken as an
example, Bill must know about the firewall, router, switch, connection type, ISP services, ports
connected to computers and more (Snapp et al., 2017). Network auditing and mapping will
reveal the network security loopholes which is very essential for continuously improve network
security.
Keeping Network Up-to-Date: Once the auditing and mapping process will be done, Bill
must dive deeper into network security. Checking software updates and firmware of all the
networking devices is essential to implement network security (Perlman, Kaufman & Speciner,
2016). Bill must login to each network devices such as router, switch, firewall and few more to
ensure that default password is changed to a strong and secure password.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK IMPLEMENTATION AND SECURITY PLANNING
Securing Network Physically: The physical security of a network is equally significant
as cyber security. The physical security will make the network secure against local threats. Bill
must have a good security plan for preventing unauthorized people to enter into the room (Khan
& Sarfaraz, 2018). Bill must make sure that cables used in the network should be managed
properly and does not preserve too much extra length.
MAC Address Filtering: The easy and quick authentication issues can be considered as
the security concern of wired network. An unauthorized user can plug in to the network device
can connect to network (Martin et al., 2017). A good hacker can easily bypass MAC address
filtering. The MAC Address filtering, thus, cannot prevent a good hacking attempt but it can
restrict the users to exploit security loopholes in the network.
Antivirus: This piece of software can easily prevent any virus or spam to affect the
computers connected to the internet (Lee, & Kim, 2017). Bill must update the software on daily
basis as new viruses are created each day.
Securing Network Physically: The physical security of a network is equally significant
as cyber security. The physical security will make the network secure against local threats. Bill
must have a good security plan for preventing unauthorized people to enter into the room (Khan
& Sarfaraz, 2018). Bill must make sure that cables used in the network should be managed
properly and does not preserve too much extra length.
MAC Address Filtering: The easy and quick authentication issues can be considered as
the security concern of wired network. An unauthorized user can plug in to the network device
can connect to network (Martin et al., 2017). A good hacker can easily bypass MAC address
filtering. The MAC Address filtering, thus, cannot prevent a good hacking attempt but it can
restrict the users to exploit security loopholes in the network.
Antivirus: This piece of software can easily prevent any virus or spam to affect the
computers connected to the internet (Lee, & Kim, 2017). Bill must update the software on daily
basis as new viruses are created each day.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK IMPLEMENTATION AND SECURITY PLANNING
References:
Balabanov, T., Zankinski, I., & Barova, M. (2016). Strategy for individuals distribution by
incident nodes participation in star topology of distributed evolutionary
algorithms. Cybernetics and Information Technologies, 16(1), 80-88.
Dorta, T., Zapata, M., Madrenas, J., & Sánchez, G. (2016). AER-SRT: Scalable spike
distribution by means of synchronous serial ring topology address event
representation. Neurocomputing, 171, 1684-1690.
Khan, A., & Sarfaraz, A. (2018). Practical guidelines for securing wireless local area networks
(WLANs). International Journal of Security and Its Applications, 12(3), 19-28.
Lee, J. H., & Kim, H. (2017). Security and privacy challenges in the internet of things [security
and privacy matters]. IEEE Consumer Electronics Magazine, 6(3), 134-136.
Martin, J., Mayberry, T., Donahue, C., Foppe, L., Brown, L., Riggins, C., ... & Brown, D.
(2017). A study of MAC address randomization in mobile devices and when it
fails. Proceedings on Privacy Enhancing Technologies, 2017(4), 365-383.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Yan, B. Y., Long, X., & Li, M. (2018). Temporal Boundary Analysis on Startup Algorithm for
Time-Triggered Architecture with Bus Topology. In 2018 2nd International Conference
References:
Balabanov, T., Zankinski, I., & Barova, M. (2016). Strategy for individuals distribution by
incident nodes participation in star topology of distributed evolutionary
algorithms. Cybernetics and Information Technologies, 16(1), 80-88.
Dorta, T., Zapata, M., Madrenas, J., & Sánchez, G. (2016). AER-SRT: Scalable spike
distribution by means of synchronous serial ring topology address event
representation. Neurocomputing, 171, 1684-1690.
Khan, A., & Sarfaraz, A. (2018). Practical guidelines for securing wireless local area networks
(WLANs). International Journal of Security and Its Applications, 12(3), 19-28.
Lee, J. H., & Kim, H. (2017). Security and privacy challenges in the internet of things [security
and privacy matters]. IEEE Consumer Electronics Magazine, 6(3), 134-136.
Martin, J., Mayberry, T., Donahue, C., Foppe, L., Brown, L., Riggins, C., ... & Brown, D.
(2017). A study of MAC address randomization in mobile devices and when it
fails. Proceedings on Privacy Enhancing Technologies, 2017(4), 365-383.
Perlman, R., Kaufman, C., & Speciner, M. (2016). Network security: private communication in a
public world. Pearson Education India.
Snapp, S. R., Brentano, J., Dias, G., Goan, T. L., Heberlein, L. T., Ho, C. L., & Levitt, K. N.
(2017). DIDS (distributed intrusion detection system)-motivation, architecture, and an
early prototype.
Yan, B. Y., Long, X., & Li, M. (2018). Temporal Boundary Analysis on Startup Algorithm for
Time-Triggered Architecture with Bus Topology. In 2018 2nd International Conference

8NETWORK IMPLEMENTATION AND SECURITY PLANNING
on Advances in Energy, Environment and Chemical Science (AEECS 2018). Atlantis
Press.
on Advances in Energy, Environment and Chemical Science (AEECS 2018). Atlantis
Press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





