Network Security Project: Securing a CentOS and Apache Web Server
VerifiedAdded on 2023/06/03
|11
|1250
|259
Report
AI Summary
This report details a network security project focused on securing a CentOS Linux server running an Apache 2.0 web server. The project begins with an introduction to the scenario of a company, SportClothes-IT-All, facing potential network attacks due to junior network administrator knowledge gaps. The report includes a network diagram and discusses the implementation of ModSecurity to mitigate SQL injection and cross-site scripting vulnerabilities. It identifies and addresses various threats to both the CentOS server and the Apache web server, including malicious threats, data breaches, DDoS attacks, clickjacking, brute force attacks, and others. The report outlines specific security measures and tools, such as antivirus software, data encryption, firewalls, and the implementation of QOS modules. It also provides a summary of device configurations and a testing plan, highlighting the use of a testing machine to assess the effectiveness of the implemented security measures. The report concludes with a list of references used in the project.

Masters of Network System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1. Introduction
The company uses a web server Apache 2.0 in the CentOS Linux server. This web server
displays the web contents of the organization. In this, junior network administrator trainee is
don’t have that much knowledge about the network and server security. Then, later it was found
that some trusted IP address did the TCP scans in the network. This is known later to the
company team and they suspect that there is a chance of attacking the company network. In order
to overcome from that attack, the company’s network admin needs to implement and properly
use the security tools to prevent the server and network from the attacks and malicious activities.
The SQL injection and cross-site scripting in the web server are overcome by using the tool Mod
Security. Then, the threats regarding the centOS server need to find and also needs to produce
the proper solutions for the possible threats. Then, the possibility of threats may occur in the
Apache web server also needs to find and the solutions should provide to the threats. This report
contains six threats regarding both Apache web server and CentOS Linux server1. Then, the
threats may occur on the network needs to find and the proper methods and steps need to be
taken to overcome those threats in the network. There are four threats in the network are
considered in this report. Then, at last, one machine needs to be designed for the testing purpose
to check the security design in the network.
'How To Install Linux, Apache, Mysql, PHP (LAMP) Stack On Centos 6 | Digitalocean' (Digitalocean.com, 2018)
<https://www.digitalocean.com/community/tutorials/how-to-install-linux-apache-mysql-php-lamp-stack-on-centos-
6> accessed 17 October 2018.1
1
The company uses a web server Apache 2.0 in the CentOS Linux server. This web server
displays the web contents of the organization. In this, junior network administrator trainee is
don’t have that much knowledge about the network and server security. Then, later it was found
that some trusted IP address did the TCP scans in the network. This is known later to the
company team and they suspect that there is a chance of attacking the company network. In order
to overcome from that attack, the company’s network admin needs to implement and properly
use the security tools to prevent the server and network from the attacks and malicious activities.
The SQL injection and cross-site scripting in the web server are overcome by using the tool Mod
Security. Then, the threats regarding the centOS server need to find and also needs to produce
the proper solutions for the possible threats. Then, the possibility of threats may occur in the
Apache web server also needs to find and the solutions should provide to the threats. This report
contains six threats regarding both Apache web server and CentOS Linux server1. Then, the
threats may occur on the network needs to find and the proper methods and steps need to be
taken to overcome those threats in the network. There are four threats in the network are
considered in this report. Then, at last, one machine needs to be designed for the testing purpose
to check the security design in the network.
'How To Install Linux, Apache, Mysql, PHP (LAMP) Stack On Centos 6 | Digitalocean' (Digitalocean.com, 2018)
<https://www.digitalocean.com/community/tutorials/how-to-install-linux-apache-mysql-php-lamp-stack-on-centos-
6> accessed 17 October 2018.1
1
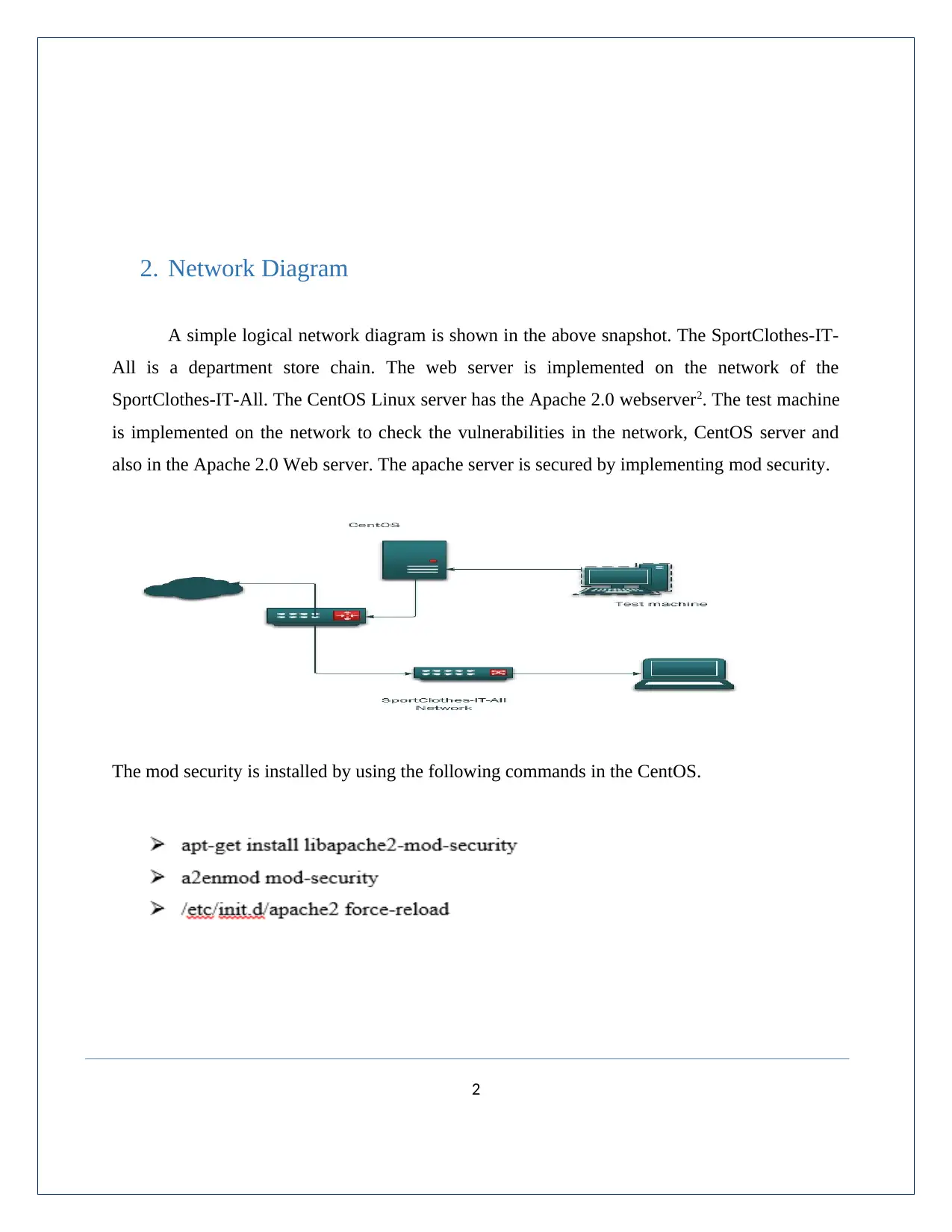
2. Network Diagram
A simple logical network diagram is shown in the above snapshot. The SportClothes-IT-
All is a department store chain. The web server is implemented on the network of the
SportClothes-IT-All. The CentOS Linux server has the Apache 2.0 webserver2. The test machine
is implemented on the network to check the vulnerabilities in the network, CentOS server and
also in the Apache 2.0 Web server. The apache server is secured by implementing mod security.
The mod security is installed by using the following commands in the CentOS.
2
A simple logical network diagram is shown in the above snapshot. The SportClothes-IT-
All is a department store chain. The web server is implemented on the network of the
SportClothes-IT-All. The CentOS Linux server has the Apache 2.0 webserver2. The test machine
is implemented on the network to check the vulnerabilities in the network, CentOS server and
also in the Apache 2.0 Web server. The apache server is secured by implementing mod security.
The mod security is installed by using the following commands in the CentOS.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Philip Hunter, 'Network Security Architecture Without Perimeters' (2002) 2002 Network Security.2
All mod-security rules are inserted in global Apache configuration. For configuring this first
open the apache2 configuration file by using this command of /etc/apache2/apache2.conf. After
that, restart the Apche2 server by the following command /etc/init.d/apache2 restart.
3. Design Discussion
The CentOS server is used in the network design to provide required services to the
network of the SportClothes-IT-All. The Web server of Apache 2.o is used to provide web
services to the SportClothes-IT-All networks. The test machine used in the network is used to
check the vulnerabilities of the network, Apache2 server and also the CentOS server. The cloud
is representing the WAN network. By using this, the online shopping is implemented in the
SportClothes-IT-All network. The vulnerabilities in the CentOS, Apache2 and the network is
identified in order to secure the SportClothes-IT-All network.
The network related threats are listed below
Threats Solution
Malicious threat Install antivirus software to the system
Eavesdropping Use encrypted data using data conversation.
3
All mod-security rules are inserted in global Apache configuration. For configuring this first
open the apache2 configuration file by using this command of /etc/apache2/apache2.conf. After
that, restart the Apche2 server by the following command /etc/init.d/apache2 restart.
3. Design Discussion
The CentOS server is used in the network design to provide required services to the
network of the SportClothes-IT-All. The Web server of Apache 2.o is used to provide web
services to the SportClothes-IT-All networks. The test machine used in the network is used to
check the vulnerabilities of the network, Apache2 server and also the CentOS server. The cloud
is representing the WAN network. By using this, the online shopping is implemented in the
SportClothes-IT-All network. The vulnerabilities in the CentOS, Apache2 and the network is
identified in order to secure the SportClothes-IT-All network.
The network related threats are listed below
Threats Solution
Malicious threat Install antivirus software to the system
Eavesdropping Use encrypted data using data conversation.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Data breaches Encrypt the sensitive information.
D-DOS attack Use firewall for controlling packet traffic
The Apache2 server3 related threats are listed below.
Name Security measure
DDos Limited the number of HTTP requests accepted from
clients.
TimeOut should be set short as the web server needs
extra time to perform certain web requirements.
Clickjacking Implement X-FRAME-OPTIONS in HTTP headers.
There are three settings in the X-FRAME-OPTIONS
such as sameorgin, deny and allow-from uri.
Sameorigin : It display the page itself in a frame on
same orgin.
Deny: prevent the page display in the frame.
Allow-from uri: It allow the page to display only on the
indicated orgin.
SlowLoris Implement Qos module
Brute force attack Encrypt and decrypt the password.
4
D-DOS attack Use firewall for controlling packet traffic
The Apache2 server3 related threats are listed below.
Name Security measure
DDos Limited the number of HTTP requests accepted from
clients.
TimeOut should be set short as the web server needs
extra time to perform certain web requirements.
Clickjacking Implement X-FRAME-OPTIONS in HTTP headers.
There are three settings in the X-FRAME-OPTIONS
such as sameorgin, deny and allow-from uri.
Sameorigin : It display the page itself in a frame on
same orgin.
Deny: prevent the page display in the frame.
Allow-from uri: It allow the page to display only on the
indicated orgin.
SlowLoris Implement Qos module
Brute force attack Encrypt and decrypt the password.
4

M. Masoudifar, 'The Relation Between Apache II And Apache III Scores With Duration Of Mechanical
Ventilation And ICU Stay' (2008) 33 Regional Anesthesia and Pain Medicine.3
Threats related to CentOS are given below.
Ghost attack-> reboot and update all of your Linux servers and FQDN variable not exit the
determined number of characters.
Ddos -> Limit the incoming IP address to SSHD from only know hosts
SlowLoris-> Implement the QOS module to stop slowloris attacks.
Brute Force attack -> configure CentOS to drop packets from anyone but a trusted ip address.
Set password authentication.
Dictionay attack-> encrypt and decrypt the password. Disable all of the other checks it
performs, such as minimum password length and character complexity.
5
Ventilation And ICU Stay' (2008) 33 Regional Anesthesia and Pain Medicine.3
Threats related to CentOS are given below.
Ghost attack-> reboot and update all of your Linux servers and FQDN variable not exit the
determined number of characters.
Ddos -> Limit the incoming IP address to SSHD from only know hosts
SlowLoris-> Implement the QOS module to stop slowloris attacks.
Brute Force attack -> configure CentOS to drop packets from anyone but a trusted ip address.
Set password authentication.
Dictionay attack-> encrypt and decrypt the password. Disable all of the other checks it
performs, such as minimum password length and character complexity.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4. Summary of Device configuration
Threats Action/Tools for
Mitigation
Device
Configured
Commands
Spectrum and
meltdown
Vulnerabilities
The Spectre and
Meltdown Checker
Script is used to
check if the
CentOS is
vulnerable to
Spectre and
Meltdown
Update Kernal
CentOS4 $ sudo sh spectre-meltdown-checker.sh
$ sudo yum update
Unused Services and
Open Ports
Service command
is used to stop
unused services
CentOS $ sudo service nmbd stop
nmbd stop/waiting
$ sudo service smbd stop
smbd stop/waiting
service mysqld stop
'What Is Centos ? - Centos Blog' (CentOS Blog, 2018) <https://www.centosblog.com/what-is-centos/> accessed 17
October 2018.4
6
Threats Action/Tools for
Mitigation
Device
Configured
Commands
Spectrum and
meltdown
Vulnerabilities
The Spectre and
Meltdown Checker
Script is used to
check if the
CentOS is
vulnerable to
Spectre and
Meltdown
Update Kernal
CentOS4 $ sudo sh spectre-meltdown-checker.sh
$ sudo yum update
Unused Services and
Open Ports
Service command
is used to stop
unused services
CentOS $ sudo service nmbd stop
nmbd stop/waiting
$ sudo service smbd stop
smbd stop/waiting
service mysqld stop
'What Is Centos ? - Centos Blog' (CentOS Blog, 2018) <https://www.centosblog.com/what-is-centos/> accessed 17
October 2018.4
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

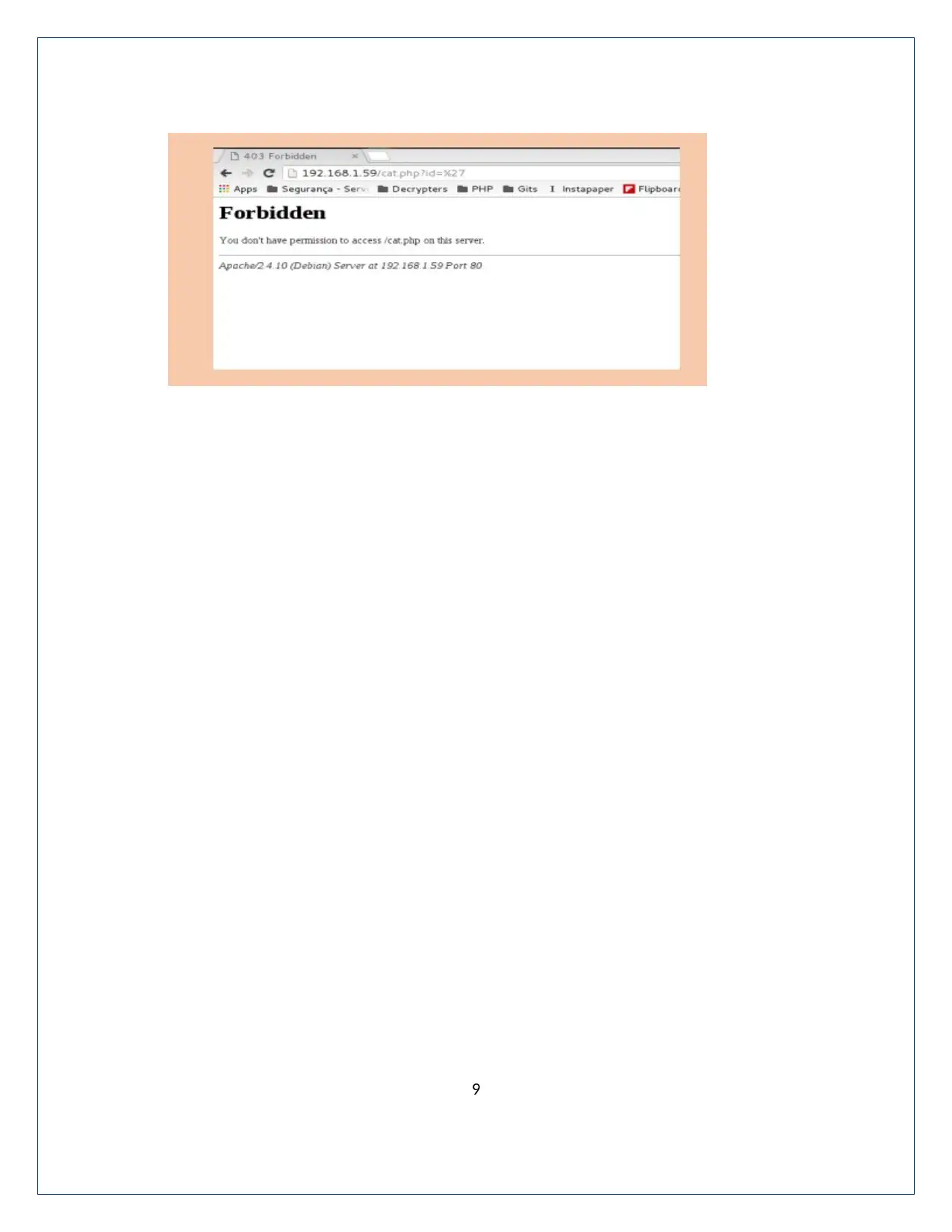
5. Testing Plan
There is no firewall6 in the network. So, there is a chance to happen attacks. There are so
many unused services and ports. They must be stopped. The CentOS also has some
vulnerabilities like spectrum and meltdown vulnerabilities. The mitigation tools and actions are
taken place to avoid vulnerabilities. The network is tested by using testing machine.
The commands used to Prevent SQL Injection5 and XSS using Blocking Rules by ModSecurity
'SQL Injection' (W3schools.com, 2018) <https://www.w3schools.com/sql/sql_injection.asp> accessed 17
October 2018.5
Products Services, 'Next-Generation Firewalls (NGFW)' (Cisco, 2018)
<https://www.cisco.com/c/en/us/products/security/firewalls/index.html> accessed 17 October 2018.6
7
There is no firewall6 in the network. So, there is a chance to happen attacks. There are so
many unused services and ports. They must be stopped. The CentOS also has some
vulnerabilities like spectrum and meltdown vulnerabilities. The mitigation tools and actions are
taken place to avoid vulnerabilities. The network is tested by using testing machine.
The commands used to Prevent SQL Injection5 and XSS using Blocking Rules by ModSecurity
'SQL Injection' (W3schools.com, 2018) <https://www.w3schools.com/sql/sql_injection.asp> accessed 17
October 2018.5
Products Services, 'Next-Generation Firewalls (NGFW)' (Cisco, 2018)
<https://www.cisco.com/c/en/us/products/security/firewalls/index.html> accessed 17 October 2018.6
7

8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

6. References
'How To Install Linux, Apache, Mysql, PHP (LAMP) Stack On Centos 6 | Digitalocean'
(Digitalocean.com, 2018) <https://www.digitalocean.com/community/tutorials/how-to-
install-linux-apache-mysql-php-lamp-stack-on-centos-6> accessed 17 October 2018
Hunter P, 'Network Security Architecture Without Perimeters' (2002) 2002 Network Security
Masoudifar M, 'The Relation Between Apache II And Apache III Scores With Duration Of
Mechanical Ventilation And ICU Stay' (2008) 33 Regional Anesthesia and Pain Medicine
Services P, 'Next-Generation Firewalls (NGFW)' (Cisco, 2018)
<https://www.cisco.com/c/en/us/products/security/firewalls/index.html> accessed 17
October 2018
'SQL Injection' (W3schools.com, 2018) <https://www.w3schools.com/sql/sql_injection.asp>
accessed 17 October 2018
'What Is Centos ? - Centos Blog' (CentOS Blog, 2018) <https://www.centosblog.com/what-is-
centos/> accessed 17 October 2018
10
'How To Install Linux, Apache, Mysql, PHP (LAMP) Stack On Centos 6 | Digitalocean'
(Digitalocean.com, 2018) <https://www.digitalocean.com/community/tutorials/how-to-
install-linux-apache-mysql-php-lamp-stack-on-centos-6> accessed 17 October 2018
Hunter P, 'Network Security Architecture Without Perimeters' (2002) 2002 Network Security
Masoudifar M, 'The Relation Between Apache II And Apache III Scores With Duration Of
Mechanical Ventilation And ICU Stay' (2008) 33 Regional Anesthesia and Pain Medicine
Services P, 'Next-Generation Firewalls (NGFW)' (Cisco, 2018)
<https://www.cisco.com/c/en/us/products/security/firewalls/index.html> accessed 17
October 2018
'SQL Injection' (W3schools.com, 2018) <https://www.w3schools.com/sql/sql_injection.asp>
accessed 17 October 2018
'What Is Centos ? - Centos Blog' (CentOS Blog, 2018) <https://www.centosblog.com/what-is-
centos/> accessed 17 October 2018
10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





