Network Intrusion Detection System Report and Analysis for Security
VerifiedAdded on 2020/05/16
|6
|496
|124
Report
AI Summary
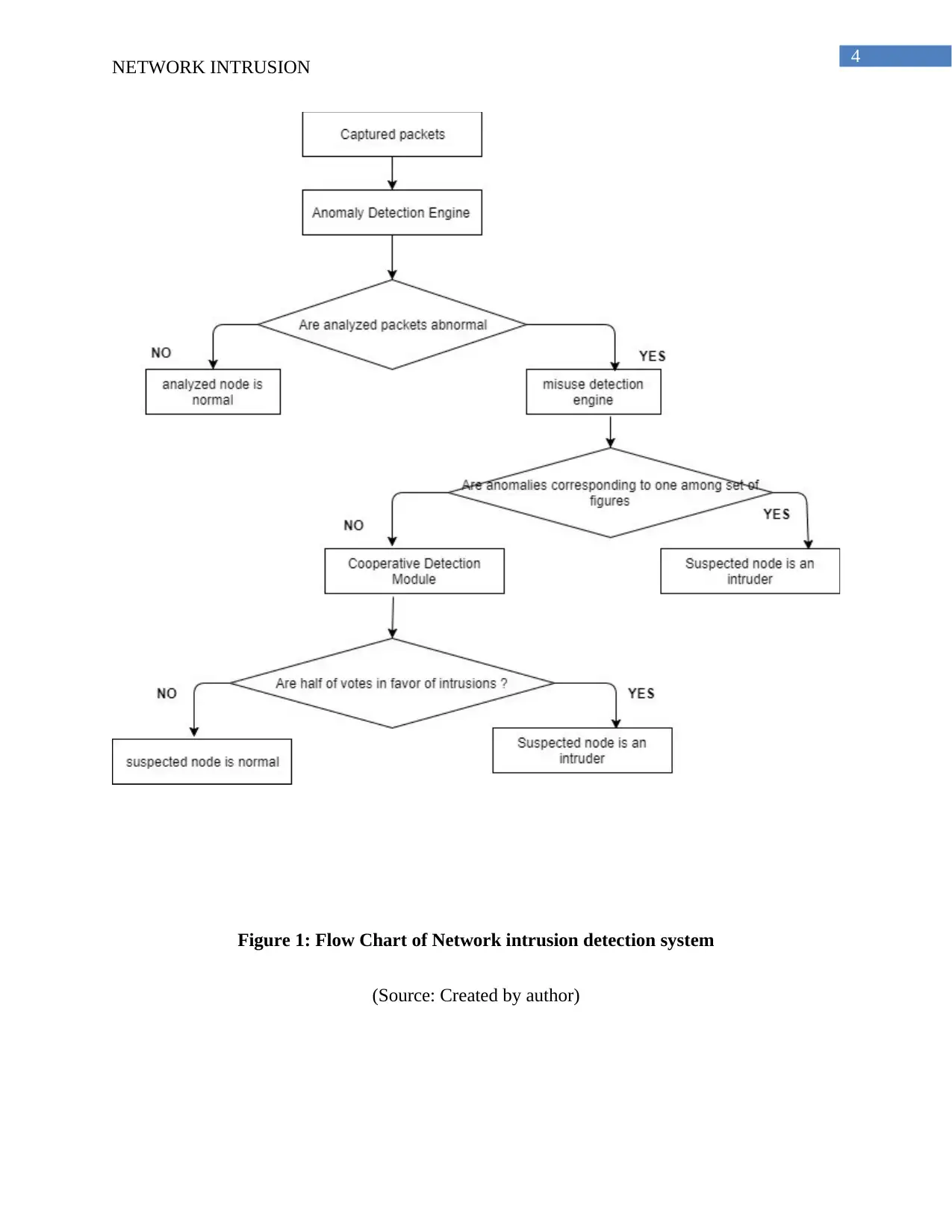
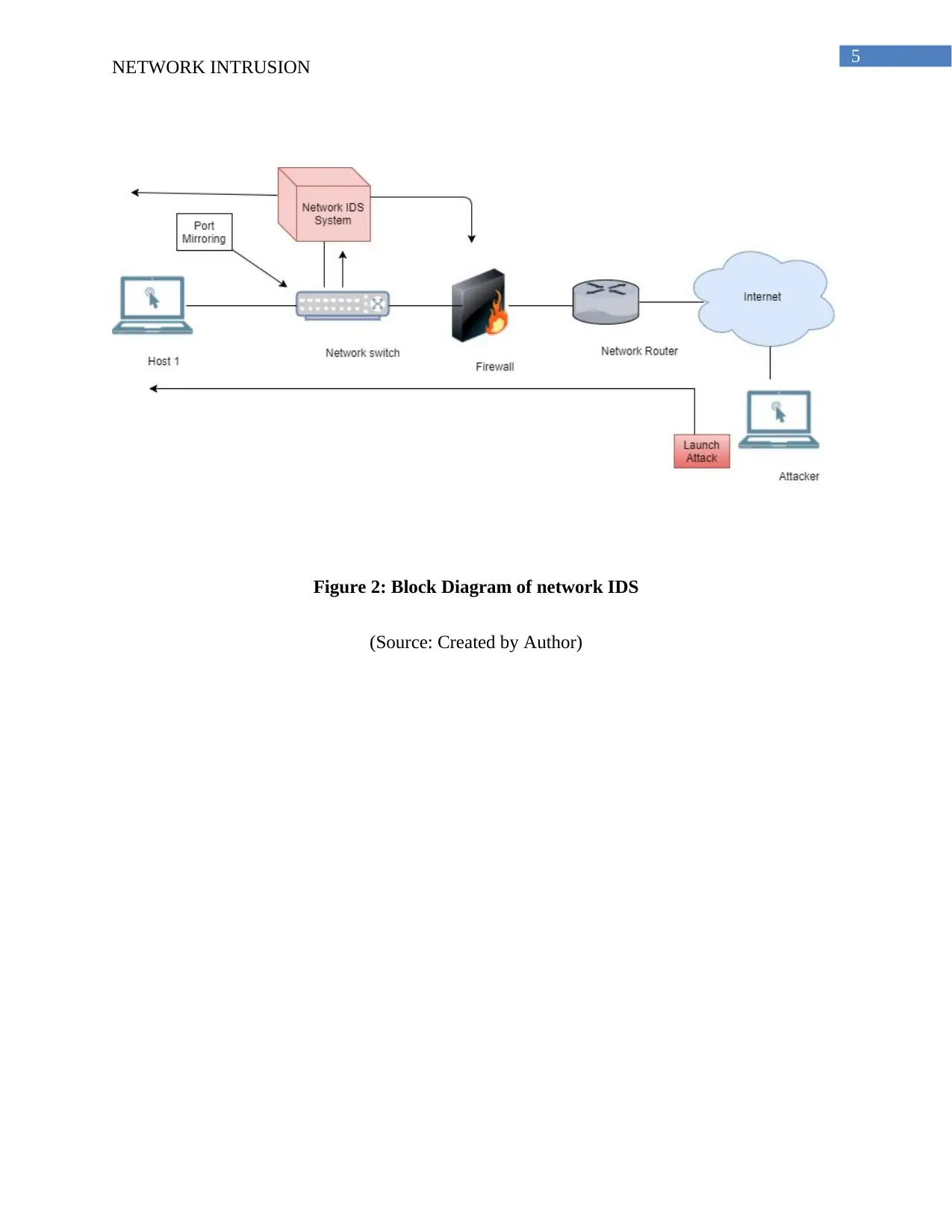
This report provides an overview of Network Intrusion Detection Systems (IDS). It discusses the role of IDS in network security, highlighting the use of algorithms like decision trees, one-class support vector machines, and hybrid intrusion detection methods. The report explains the entropy calculation used in decision trees and the SVM algorithm. It also mentions the use of MATLAB for algorithm testing and the importance of multi-core parallel systems. The report includes a flowchart and block diagram illustrating the IDS process and references relevant research. This report is designed to help understand the principles and applications of intrusion detection techniques for maintaining network security and protecting against various cyber threats.
1 out of 6











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)