Folks Company Network Security Solution Report - BIT243, Semester 1
VerifiedAdded on 2023/01/03
|11
|3146
|48
Report
AI Summary
This report presents a comprehensive network security solution for Folks Company, a financial consultancy firm expanding with new branches. The report addresses the company's requirements for high-level security, secure communication, and remote access. It begins with an executive summary, followed by an introduction that emphasizes the importance of network security in today's environment. The report then outlines the company's specific needs, including the need for secure connectivity between the head office in Melbourne and new branches in Sydney and Perth. The solution design section details the proposed star topology, which facilitates easy monitoring and control. It delves into key concepts of OSI security architecture, the implementation of intrusion detection and prevention systems, and processes for security in a trust-based computing environment. The report evaluates the effective use of security techniques like authentication, digital signatures, access control, identity management, and public key cryptography. Finally, the report concludes by summarizing the proposed services and applications, which include secure email, file sharing, remote access, video conferencing, and access to shared applications, ensuring a secure and efficient network infrastructure for Folks Company.

NETWORK SECURITY 1
Network Security
Student Name
Course
Institution
Date
Network Security
Student Name
Course
Institution
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORK SECURITY 2
Executive Summary
This report has been prepared for Folks Company proposing a network security solution that will
meet its network requirements. The company is planning to open two new branches in Sydney
and Perth and the two branches will be connected to the head office in Melbourne. The solution
should be able to ensure high-level security and availability, facilitate secure email
communication, secure sharing of files, video conferencing, remote access, and access hared
applications. The proposed network solution will effectively meet the security requirements of
the company without compromising on the services, performance, and availability. Star topology
will be used to facilitates easy monitoring of its network usage and security from central
command. This report has provided a solution with several network security strategies that can
be adopted.
Executive Summary
This report has been prepared for Folks Company proposing a network security solution that will
meet its network requirements. The company is planning to open two new branches in Sydney
and Perth and the two branches will be connected to the head office in Melbourne. The solution
should be able to ensure high-level security and availability, facilitate secure email
communication, secure sharing of files, video conferencing, remote access, and access hared
applications. The proposed network solution will effectively meet the security requirements of
the company without compromising on the services, performance, and availability. Star topology
will be used to facilitates easy monitoring of its network usage and security from central
command. This report has provided a solution with several network security strategies that can
be adopted.

NETWORK SECURITY 3
Table of Contents
Executive Summary.........................................................................................................................2
Introduction......................................................................................................................................4
Requirements...................................................................................................................................4
Solution Design...............................................................................................................................5
Network Topology.......................................................................................................................5
Solution Description....................................................................................................................6
Key Concepts of OSI Security Architecture............................................................................6
Design and Implement Detection and Prevention Systems.....................................................7
Processes for Security in a Trust-Based Computing Environment.........................................7
Effective Uses of Security Techniques....................................................................................8
Services and Applications............................................................................................................9
Interfaces and Technologies........................................................................................................9
Analysis and Evaluation................................................................................................................10
Conclusion.....................................................................................................................................10
List of References..........................................................................................................................11
Table of Contents
Executive Summary.........................................................................................................................2
Introduction......................................................................................................................................4
Requirements...................................................................................................................................4
Solution Design...............................................................................................................................5
Network Topology.......................................................................................................................5
Solution Description....................................................................................................................6
Key Concepts of OSI Security Architecture............................................................................6
Design and Implement Detection and Prevention Systems.....................................................7
Processes for Security in a Trust-Based Computing Environment.........................................7
Effective Uses of Security Techniques....................................................................................8
Services and Applications............................................................................................................9
Interfaces and Technologies........................................................................................................9
Analysis and Evaluation................................................................................................................10
Conclusion.....................................................................................................................................10
List of References..........................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK SECURITY 4
Introduction
Network security breaches have become more common and rampant across the world. They can
be minor or major but both lead to loss of data which may result in a catastrophe within an
organization (Ciampa, 2012). For the purpose of this paper, network security will be described as
a process of employing the various strategies and mechanisms to protect and secure the network
infrastructure from improper disclosure, misuse, destruction, modification, and unauthorized
access. By implementing the different security mechanism and strategies, users, application, and
computers are allowed to carry out their critical functions within a secure environment. In order
to secure a network, one needs to have a complex combination of various networking
components and software such as anti-virus, firewalls, and routers. In order to have an effective
network security mechanisms, organizations and governments have employed highly-skilled
personnel to design, develop, and implement security plans and regularly monitor the
effectiveness of these plans. Network security is a very important element that every
organization and business whether small or large should pay attention to at every level of
operation. Networks without proper security measures can be exploited easily by hackers and
other cybercriminals with the intention to steal or modify the data (Stewart, 2014). This report
will describe the network security requirements for Folks Company which is a financial
consultancy firm located in Melbourne. The company has grown over the years and has opened
more branches in Sydney and Perth.
Requirements
Folks have opened up new branches in Sydney and Perth and since the company has its data
center in the central office, the company wants to implement a secure network infrastructure that
will enable the pilot offices to connect to the data center in the central office. The company
currently has 52 employees in the main office and the two branches will have a total of 35
employees. The company is expected to grow and is planning that in the next 10 years the
company will have more than 500 employees. The company expects that the proposed network
infrastructure will ensure high-level security and availability, facilitate secure email
communication, secure sharing of files, video conferencing, remote access, and access hared
applications.
Introduction
Network security breaches have become more common and rampant across the world. They can
be minor or major but both lead to loss of data which may result in a catastrophe within an
organization (Ciampa, 2012). For the purpose of this paper, network security will be described as
a process of employing the various strategies and mechanisms to protect and secure the network
infrastructure from improper disclosure, misuse, destruction, modification, and unauthorized
access. By implementing the different security mechanism and strategies, users, application, and
computers are allowed to carry out their critical functions within a secure environment. In order
to secure a network, one needs to have a complex combination of various networking
components and software such as anti-virus, firewalls, and routers. In order to have an effective
network security mechanisms, organizations and governments have employed highly-skilled
personnel to design, develop, and implement security plans and regularly monitor the
effectiveness of these plans. Network security is a very important element that every
organization and business whether small or large should pay attention to at every level of
operation. Networks without proper security measures can be exploited easily by hackers and
other cybercriminals with the intention to steal or modify the data (Stewart, 2014). This report
will describe the network security requirements for Folks Company which is a financial
consultancy firm located in Melbourne. The company has grown over the years and has opened
more branches in Sydney and Perth.
Requirements
Folks have opened up new branches in Sydney and Perth and since the company has its data
center in the central office, the company wants to implement a secure network infrastructure that
will enable the pilot offices to connect to the data center in the central office. The company
currently has 52 employees in the main office and the two branches will have a total of 35
employees. The company is expected to grow and is planning that in the next 10 years the
company will have more than 500 employees. The company expects that the proposed network
infrastructure will ensure high-level security and availability, facilitate secure email
communication, secure sharing of files, video conferencing, remote access, and access hared
applications.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK SECURITY 5
Solution Design
This section will describe the various solution designs and measures that the network designer
will take in order to meet the network requirements set out by Folks Company. This section will
discuss various aspects including network topology, solution description, services and
applications, and interfaces and technologies. Under solution description, the following aspects
will be discussed, key concepts of OSI security architecture, design and implementation of
detection and prevention system, process for security in trust-based computing environment, and
evaluate the effective use of security mechanisms such as public key encryption, identity
management, access controls, authentication, and digital signatures.
Network Topology
The proposed network topology for Folks Company is star topology. Star topology is a type of
networking topology where all the nodes on the network are connected to a central device such
as a switch or a hub. Al the data goes through the central device before being forwarded to the
target device or address. Star topology will facilitate easy monitoring of the device and it will be
easier to detect any unfamiliar traffic or activity (Anada et al., 2017). Due to the centralized
nature of star topology, it will be easier to monitor and control all the network activities.
Enforcing security measure is easy because it is done from a centralized device. However, this
topology has one main setback, that is, if the central device fails, then the entire network is
brought down (Mohammadi, Allahvakil and Khaghani, 2012). Some of the other advantages of
start topology that Folks will benefit from include: easy installation, scalability, easy
management, easy to troubleshoot, and centralization. The diagram below shows the proposed
topology
Solution Design
This section will describe the various solution designs and measures that the network designer
will take in order to meet the network requirements set out by Folks Company. This section will
discuss various aspects including network topology, solution description, services and
applications, and interfaces and technologies. Under solution description, the following aspects
will be discussed, key concepts of OSI security architecture, design and implementation of
detection and prevention system, process for security in trust-based computing environment, and
evaluate the effective use of security mechanisms such as public key encryption, identity
management, access controls, authentication, and digital signatures.
Network Topology
The proposed network topology for Folks Company is star topology. Star topology is a type of
networking topology where all the nodes on the network are connected to a central device such
as a switch or a hub. Al the data goes through the central device before being forwarded to the
target device or address. Star topology will facilitate easy monitoring of the device and it will be
easier to detect any unfamiliar traffic or activity (Anada et al., 2017). Due to the centralized
nature of star topology, it will be easier to monitor and control all the network activities.
Enforcing security measure is easy because it is done from a centralized device. However, this
topology has one main setback, that is, if the central device fails, then the entire network is
brought down (Mohammadi, Allahvakil and Khaghani, 2012). Some of the other advantages of
start topology that Folks will benefit from include: easy installation, scalability, easy
management, easy to troubleshoot, and centralization. The diagram below shows the proposed
topology
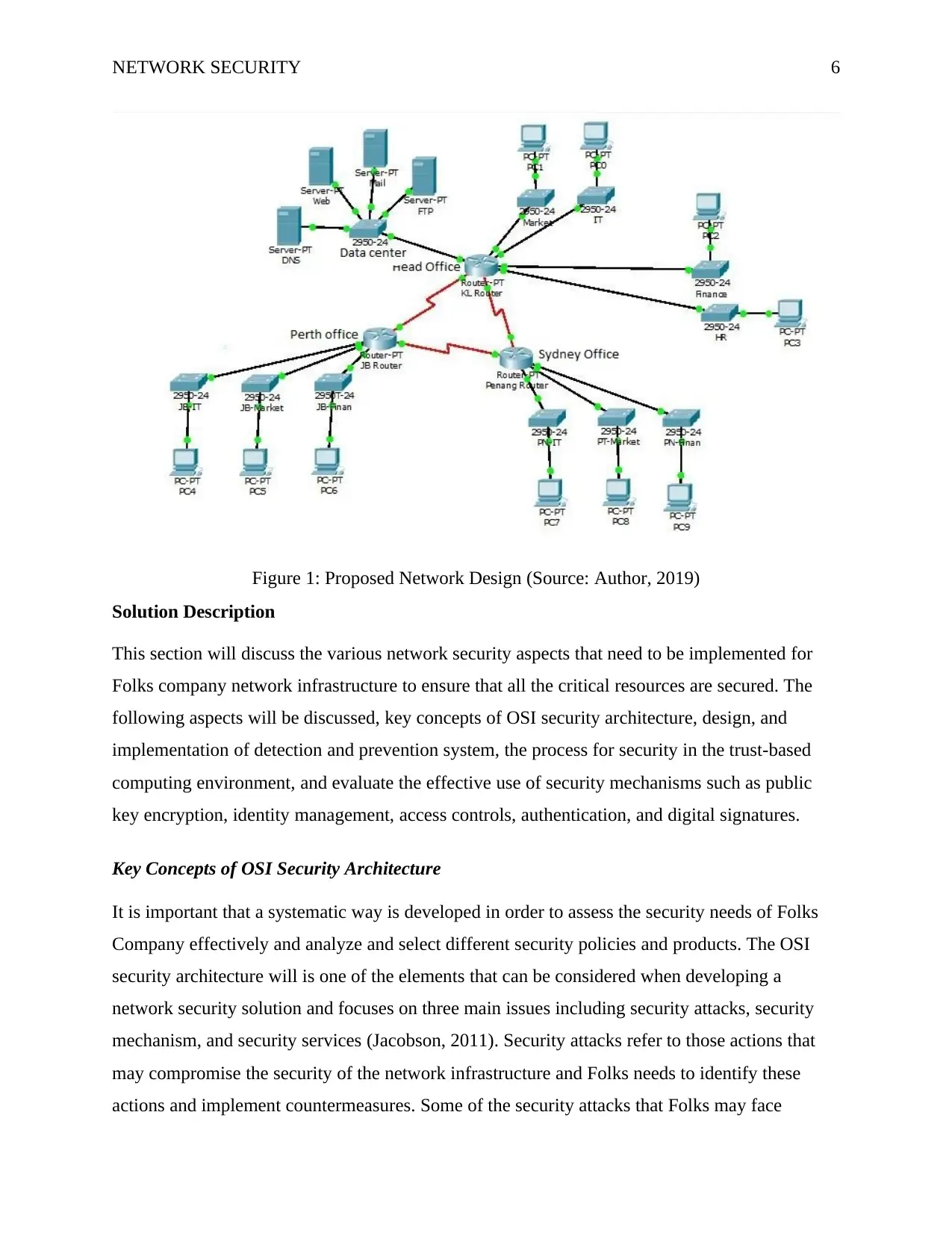
NETWORK SECURITY 6
Figure 1: Proposed Network Design (Source: Author, 2019)
Solution Description
This section will discuss the various network security aspects that need to be implemented for
Folks company network infrastructure to ensure that all the critical resources are secured. The
following aspects will be discussed, key concepts of OSI security architecture, design, and
implementation of detection and prevention system, the process for security in the trust-based
computing environment, and evaluate the effective use of security mechanisms such as public
key encryption, identity management, access controls, authentication, and digital signatures.
Key Concepts of OSI Security Architecture
It is important that a systematic way is developed in order to assess the security needs of Folks
Company effectively and analyze and select different security policies and products. The OSI
security architecture will is one of the elements that can be considered when developing a
network security solution and focuses on three main issues including security attacks, security
mechanism, and security services (Jacobson, 2011). Security attacks refer to those actions that
may compromise the security of the network infrastructure and Folks needs to identify these
actions and implement countermeasures. Some of the security attacks that Folks may face
Figure 1: Proposed Network Design (Source: Author, 2019)
Solution Description
This section will discuss the various network security aspects that need to be implemented for
Folks company network infrastructure to ensure that all the critical resources are secured. The
following aspects will be discussed, key concepts of OSI security architecture, design, and
implementation of detection and prevention system, the process for security in the trust-based
computing environment, and evaluate the effective use of security mechanisms such as public
key encryption, identity management, access controls, authentication, and digital signatures.
Key Concepts of OSI Security Architecture
It is important that a systematic way is developed in order to assess the security needs of Folks
Company effectively and analyze and select different security policies and products. The OSI
security architecture will is one of the elements that can be considered when developing a
network security solution and focuses on three main issues including security attacks, security
mechanism, and security services (Jacobson, 2011). Security attacks refer to those actions that
may compromise the security of the network infrastructure and Folks needs to identify these
actions and implement countermeasures. Some of the security attacks that Folks may face
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK SECURITY 7
include denial-of-service attacks, interruptions, fabrication, modification, interceptions among
others. The proposed solution will assess all the threats and possible attacks and implement the
necessary procedures to address them. Security mechanism will be designed to identify, prevent,
or recover from a security attack including the use of digital signatures, access control,
encipherment, use of antiviruses, firewall among others. Security services refer to services that
are designed to enhance the security of data processing systems and transmission of information
within an organization. These services will be implemented in the Folks Company network to
counter security attacks. A security service can make use of one or more security mechanisms.
Some of the security services include data confidentiality, authentication, data privacy, non-
repudiation, integrity, and access control (Stallings, 2017).
Design and Implement Detection and Prevention Systems
It will be necessary to implement intrusion detection and intrusion prevention system for Folks
company. An intrusion detection system (IDS) will be responsible for detecting any unusual
activity, malicious coding, abnormal traffic, or unusual behavior before they occur (Kizza,
2017). Upon detecting any malicious activity within the network, the IDS will prompt the
intrusion prevention system (IPS) to prevent the activity from occurring or causing damage to the
network. The IPS are also responsible for adding the source address to the blocked list and
logging the attack. IDS and IPS can be implemented in either IPS on a stick, inline, or tap/span
mode. For the purpose of Folks company, IPS on stick deployment model will be employed
because Cisco infrastructure will be used because packets can be forwarded to several IDS/SPS
sensors using Cisco Ethernet Channel Technology. However, one of the best additionally, the
practices that will be adopted is creating several policies for the different resources and functions
(Knapp, 2011). This includes defining policies for a network segment or VLAN interfaces/sub-
interfaces. Additionally, the direction of the traffic will be defined to facilitate the protection of a
targeted section, for instance, incoming traffic from the internet to the DMZ.
Processes for Security in a Trust-Based Computing Environment
There are several processes for security in a trust-based computing environment that has to be
met when setting up the network infrastructure for Folks Company. The network security analyst
include denial-of-service attacks, interruptions, fabrication, modification, interceptions among
others. The proposed solution will assess all the threats and possible attacks and implement the
necessary procedures to address them. Security mechanism will be designed to identify, prevent,
or recover from a security attack including the use of digital signatures, access control,
encipherment, use of antiviruses, firewall among others. Security services refer to services that
are designed to enhance the security of data processing systems and transmission of information
within an organization. These services will be implemented in the Folks Company network to
counter security attacks. A security service can make use of one or more security mechanisms.
Some of the security services include data confidentiality, authentication, data privacy, non-
repudiation, integrity, and access control (Stallings, 2017).
Design and Implement Detection and Prevention Systems
It will be necessary to implement intrusion detection and intrusion prevention system for Folks
company. An intrusion detection system (IDS) will be responsible for detecting any unusual
activity, malicious coding, abnormal traffic, or unusual behavior before they occur (Kizza,
2017). Upon detecting any malicious activity within the network, the IDS will prompt the
intrusion prevention system (IPS) to prevent the activity from occurring or causing damage to the
network. The IPS are also responsible for adding the source address to the blocked list and
logging the attack. IDS and IPS can be implemented in either IPS on a stick, inline, or tap/span
mode. For the purpose of Folks company, IPS on stick deployment model will be employed
because Cisco infrastructure will be used because packets can be forwarded to several IDS/SPS
sensors using Cisco Ethernet Channel Technology. However, one of the best additionally, the
practices that will be adopted is creating several policies for the different resources and functions
(Knapp, 2011). This includes defining policies for a network segment or VLAN interfaces/sub-
interfaces. Additionally, the direction of the traffic will be defined to facilitate the protection of a
targeted section, for instance, incoming traffic from the internet to the DMZ.
Processes for Security in a Trust-Based Computing Environment
There are several processes for security in a trust-based computing environment that has to be
met when setting up the network infrastructure for Folks Company. The network security analyst
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK SECURITY 8
has been facing numerous challenges for using the traditional Centaurus protocol for providing
security in trust-based environments. This protocol cannot apply for the proposed solution
because having a central command point for a single group or building is impossible because it
demands that every user will have specified access right. This is impractical for Folks Company
network infrastructure because of the increasing number of employees/users (Abiona et al.,
2013). As a result, this paper has proposed that Folks should use distributed trust processes such
as dynamic rights and models to meet the requirements of the trust-based computing
environment. Dynamic rights consider trust management as developing trust relationships rather
than its contemporary meaning of reckoning trust. This approach involves assigning security
credentials to users, formulating policies for access control, authentication of the users, and
delegation, providing access control by validating that the credentials of the initiator satisfy the
policies, and enabling entities to modify the rights of access of other entities by deferring or
delegating their rights of access to third parties. In this case, access rights are dynamic and
change depending on revocations and delegations (Meghanathan, 2010). This approach will best
suit Folks Company to ensure that when an employee is not around, another one will take up
his/her roles after being delegated the duties.
Effective Uses of Security Techniques
The proposed network security solution for Folks Company will make use of several security
techniques such as authentication, digital signatures, access control, identity management, public
key cryptography. Digital signatures will be used to validate the integrity and validity of any data
transmitted over the network. Authentication is important in ensuring that the identity of who
they say they are is verified. This will involve the use of usernames and passwords to access the
network resources. For authentication, two-step verification will be employed for Folks
Company. Access control is another security technique that will be employed in the proposed
solution. Access control is an additional feature of authentication that is used to restrict some
segments of the network resources (Sobh and Aly, 2011). For instance, the users in the
procurement department will only access the resources relevant to procurement and will not have
access to other resources of another department. Identity management will be used to identify,
authenticate, and authorize users or group of users to get access to the network resources such as
data and applications by relating user restrictions and rights with developed identities. The main
has been facing numerous challenges for using the traditional Centaurus protocol for providing
security in trust-based environments. This protocol cannot apply for the proposed solution
because having a central command point for a single group or building is impossible because it
demands that every user will have specified access right. This is impractical for Folks Company
network infrastructure because of the increasing number of employees/users (Abiona et al.,
2013). As a result, this paper has proposed that Folks should use distributed trust processes such
as dynamic rights and models to meet the requirements of the trust-based computing
environment. Dynamic rights consider trust management as developing trust relationships rather
than its contemporary meaning of reckoning trust. This approach involves assigning security
credentials to users, formulating policies for access control, authentication of the users, and
delegation, providing access control by validating that the credentials of the initiator satisfy the
policies, and enabling entities to modify the rights of access of other entities by deferring or
delegating their rights of access to third parties. In this case, access rights are dynamic and
change depending on revocations and delegations (Meghanathan, 2010). This approach will best
suit Folks Company to ensure that when an employee is not around, another one will take up
his/her roles after being delegated the duties.
Effective Uses of Security Techniques
The proposed network security solution for Folks Company will make use of several security
techniques such as authentication, digital signatures, access control, identity management, public
key cryptography. Digital signatures will be used to validate the integrity and validity of any data
transmitted over the network. Authentication is important in ensuring that the identity of who
they say they are is verified. This will involve the use of usernames and passwords to access the
network resources. For authentication, two-step verification will be employed for Folks
Company. Access control is another security technique that will be employed in the proposed
solution. Access control is an additional feature of authentication that is used to restrict some
segments of the network resources (Sobh and Aly, 2011). For instance, the users in the
procurement department will only access the resources relevant to procurement and will not have
access to other resources of another department. Identity management will be used to identify,
authenticate, and authorize users or group of users to get access to the network resources such as
data and applications by relating user restrictions and rights with developed identities. The main

NETWORK SECURITY 9
objective of using identity management is to make sure that only users that are authenticated are
allowed to access the specified network resources which they are authorized. Finally, public key
cryptography will be adapted to facilitate the use of public and private keys for encrypting the
data being transmitted over the network. The main benefit why this technique will be used in the
proposed solution is because it does not need any kind of secure channel for initial sharing of
secret keys between the communicating parties (Bellovin, 2011). This is an added advantage to
the company.
Services and Applications
The proposed network solution for Folks Company will ensure that all the requirements both
functional and nonfunctional, have been met. The proposed solution is expected to offer the
followings services and applications:
Allow the users to communicate via email securely
Allow users to securely share the file through a file transfer protocol (both uploading and
downloading)
Allow the users to access the network resources remotely in a secure way through
terminal emulation.
Video conferencing and,
Access shared applications on the application server
Interfaces and Technologies
In the proposed solution, every interface will be connected to a virtual or physical device. By
doing so, it will be easy for the network administrators to monitor and troubleshoot individual
interfaces without having to affect the entire network. Every server in the data center will have
one network interface that is configurable for every ethernet card available. Additionally, the
solution will define the localhost interface or the virtual network interface (loopback) which is
used to connect processes and applications on one workstation to other processes and
applications (Huang, MacCallum and Du, 2010). To enhance the security of the network, one
interface for the company LAN and one to service the internet traffic will be configured.
objective of using identity management is to make sure that only users that are authenticated are
allowed to access the specified network resources which they are authorized. Finally, public key
cryptography will be adapted to facilitate the use of public and private keys for encrypting the
data being transmitted over the network. The main benefit why this technique will be used in the
proposed solution is because it does not need any kind of secure channel for initial sharing of
secret keys between the communicating parties (Bellovin, 2011). This is an added advantage to
the company.
Services and Applications
The proposed network solution for Folks Company will ensure that all the requirements both
functional and nonfunctional, have been met. The proposed solution is expected to offer the
followings services and applications:
Allow the users to communicate via email securely
Allow users to securely share the file through a file transfer protocol (both uploading and
downloading)
Allow the users to access the network resources remotely in a secure way through
terminal emulation.
Video conferencing and,
Access shared applications on the application server
Interfaces and Technologies
In the proposed solution, every interface will be connected to a virtual or physical device. By
doing so, it will be easy for the network administrators to monitor and troubleshoot individual
interfaces without having to affect the entire network. Every server in the data center will have
one network interface that is configurable for every ethernet card available. Additionally, the
solution will define the localhost interface or the virtual network interface (loopback) which is
used to connect processes and applications on one workstation to other processes and
applications (Huang, MacCallum and Du, 2010). To enhance the security of the network, one
interface for the company LAN and one to service the internet traffic will be configured.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORK SECURITY 10
Analysis and Evaluation
The proposed network solution will effectively meet the security requirements of the company
without compromising on the services, performance, and availability. By employing the use of
star topology, the company will be able to monitor its network usage and security from central
command. This makes it easier for the network security analyst to detect or identify any
malicious activity within the network. Additionally, with the help of intrusion detection and
intrusion prevention system, the network security will have an easy time monitoring and
managing the network security and taking necessary action when an issue arises. The various
strategies employed in the proposed solution will be effective enough to serve the needs of the
company. Using security techniques such as digital signatures, authentication, access control,
public key cryptography will go a long way in ensuring the security of the network. This is
because only authenticated and authorized users will be granted access to network resources.
Access control technique comes in handy when restricting access to particular resources to
ensure that only users with rights will be granted access to the resources whose rights are
granted. As mentioned in the earlier sections, access control categorizes users based on the rights
given, for instance, what a sales manager sees upon login is different from what a procumbent
manager sees. As such, based on the earlier specified requirements, it is evident that the proposed
solution has met all of them.
Conclusion
In conclusion, this paper has attempted to provide a network security solution for folks
Company. The company has planned to open up two new branches in Sydney and Perth and
wants the two branches to be connected to the central office securely. This paper has provided a
solution with several network security strategies that can be adopted. By implementing the
different security mechanism and strategies, users, applications, and computers will be able to
carry out their critical functions within a secure environment. In order to secure a network, one
needs to have a complex combination of various networking components and software such as
anti-virus, firewalls, and routers.
Analysis and Evaluation
The proposed network solution will effectively meet the security requirements of the company
without compromising on the services, performance, and availability. By employing the use of
star topology, the company will be able to monitor its network usage and security from central
command. This makes it easier for the network security analyst to detect or identify any
malicious activity within the network. Additionally, with the help of intrusion detection and
intrusion prevention system, the network security will have an easy time monitoring and
managing the network security and taking necessary action when an issue arises. The various
strategies employed in the proposed solution will be effective enough to serve the needs of the
company. Using security techniques such as digital signatures, authentication, access control,
public key cryptography will go a long way in ensuring the security of the network. This is
because only authenticated and authorized users will be granted access to network resources.
Access control technique comes in handy when restricting access to particular resources to
ensure that only users with rights will be granted access to the resources whose rights are
granted. As mentioned in the earlier sections, access control categorizes users based on the rights
given, for instance, what a sales manager sees upon login is different from what a procumbent
manager sees. As such, based on the earlier specified requirements, it is evident that the proposed
solution has met all of them.
Conclusion
In conclusion, this paper has attempted to provide a network security solution for folks
Company. The company has planned to open up two new branches in Sydney and Perth and
wants the two branches to be connected to the central office securely. This paper has provided a
solution with several network security strategies that can be adopted. By implementing the
different security mechanism and strategies, users, applications, and computers will be able to
carry out their critical functions within a secure environment. In order to secure a network, one
needs to have a complex combination of various networking components and software such as
anti-virus, firewalls, and routers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORK SECURITY 11
List of References
Abiona, O., Oluwaranti, A., Oluwatope, A., Bello, S., Onime, C., Sanni, M. and Kehinde, L.
(2013). Wireless Network Security: The Mobile Agent Approach. International Journal of
Communications, Network and System Sciences, 06(10), pp.443-450.
Anada, H., Morozov, K., Suga, Y., Okumura, S. and Sakurai, K. (2017). Secret sharing for
dependability, usability and security of network storage and its mathematical modeling.
Fukuoka: Institute of Mathematics for Industry, Kyushu University.
Bellovin, S. (2011). Applied cryptography and network security. Berlin: Springer.
Ciampa, M. (2012). Security+ guide to network security fundamentals. Boston, MA: Course
Technology, Cengage Learning.
Huang, S., MacCallum, D. and Du, D. (2010). Network security. New York: Springer.
Jacobson, D. (2011). Introduction to Network Security. Hoboken: CRC Press.
Kizza, J. (2017). Guide to Computer Network Security. Cham: Springer International Publishing.
Knapp, E. (2011). Industrial network security. Waltham, MA: Syngress.
Meghanathan, N. (2010). Recent trends in network security and applications. Berlin: Springer.
Mohammadi, S., Allahvakil, V. and Khaghani, M. (2012). Effect of Network Traffic on IPS
Performance. Journal of Information Security, 03(02), pp.162-168.
Sobh, T. and Aly, Y. (2011). Effective and Extensive Virtual Private Network. Journal of
Information Security, 02(01), pp.39-49.
Stallings, W. (2017). Cryptography and Network Security. Harlow, United Kingdom: Pearson
Education Limited.
Stewart, J. (2014). Network security, firewalls, and VPNs, second edition. Burlington, MA: Jones
& Bartlett Learning.
List of References
Abiona, O., Oluwaranti, A., Oluwatope, A., Bello, S., Onime, C., Sanni, M. and Kehinde, L.
(2013). Wireless Network Security: The Mobile Agent Approach. International Journal of
Communications, Network and System Sciences, 06(10), pp.443-450.
Anada, H., Morozov, K., Suga, Y., Okumura, S. and Sakurai, K. (2017). Secret sharing for
dependability, usability and security of network storage and its mathematical modeling.
Fukuoka: Institute of Mathematics for Industry, Kyushu University.
Bellovin, S. (2011). Applied cryptography and network security. Berlin: Springer.
Ciampa, M. (2012). Security+ guide to network security fundamentals. Boston, MA: Course
Technology, Cengage Learning.
Huang, S., MacCallum, D. and Du, D. (2010). Network security. New York: Springer.
Jacobson, D. (2011). Introduction to Network Security. Hoboken: CRC Press.
Kizza, J. (2017). Guide to Computer Network Security. Cham: Springer International Publishing.
Knapp, E. (2011). Industrial network security. Waltham, MA: Syngress.
Meghanathan, N. (2010). Recent trends in network security and applications. Berlin: Springer.
Mohammadi, S., Allahvakil, V. and Khaghani, M. (2012). Effect of Network Traffic on IPS
Performance. Journal of Information Security, 03(02), pp.162-168.
Sobh, T. and Aly, Y. (2011). Effective and Extensive Virtual Private Network. Journal of
Information Security, 02(01), pp.39-49.
Stallings, W. (2017). Cryptography and Network Security. Harlow, United Kingdom: Pearson
Education Limited.
Stewart, J. (2014). Network security, firewalls, and VPNs, second edition. Burlington, MA: Jones
& Bartlett Learning.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





