Analyzing Risk Assessment and Disaster Recovery in Network Security
VerifiedAdded on 2023/04/07
|5
|622
|433
Report
AI Summary
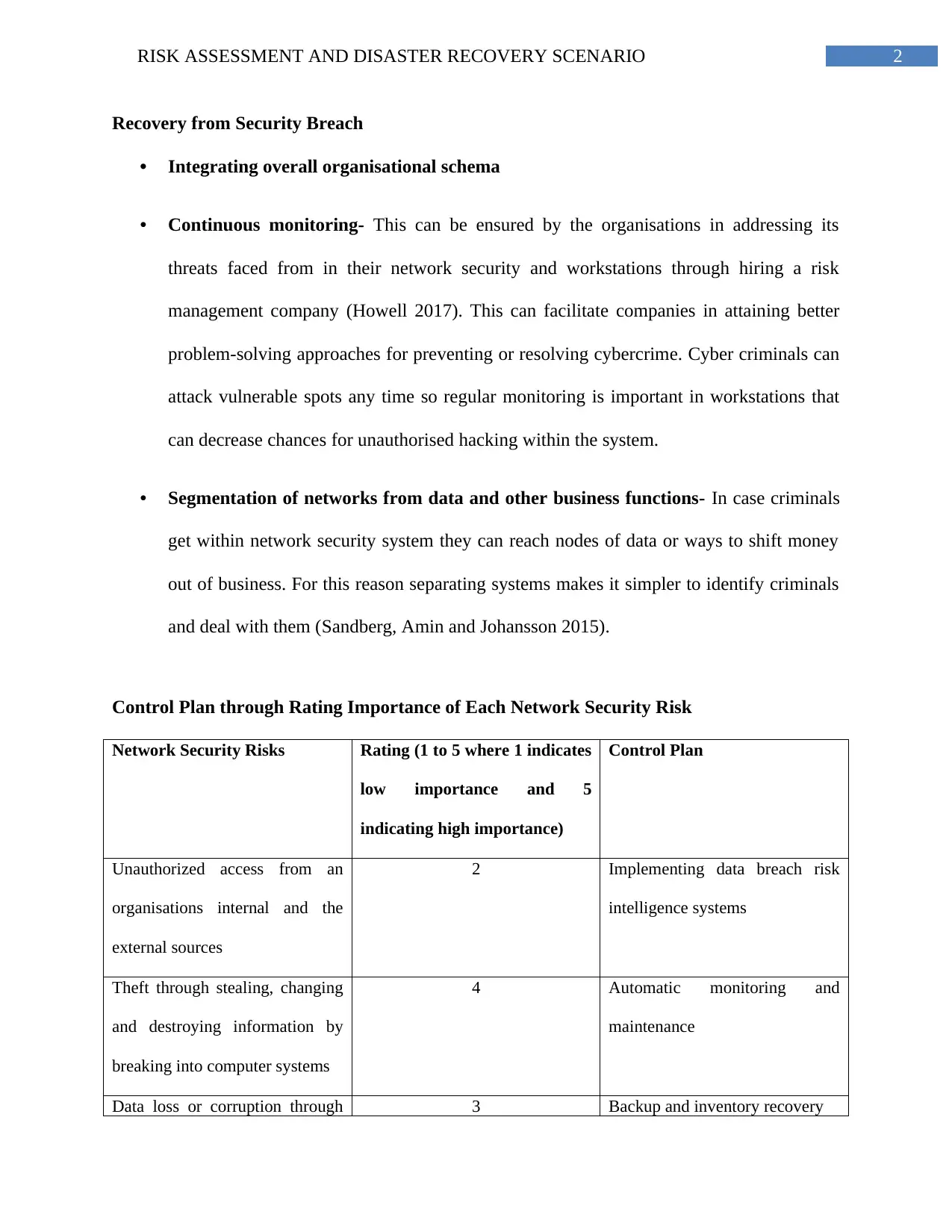
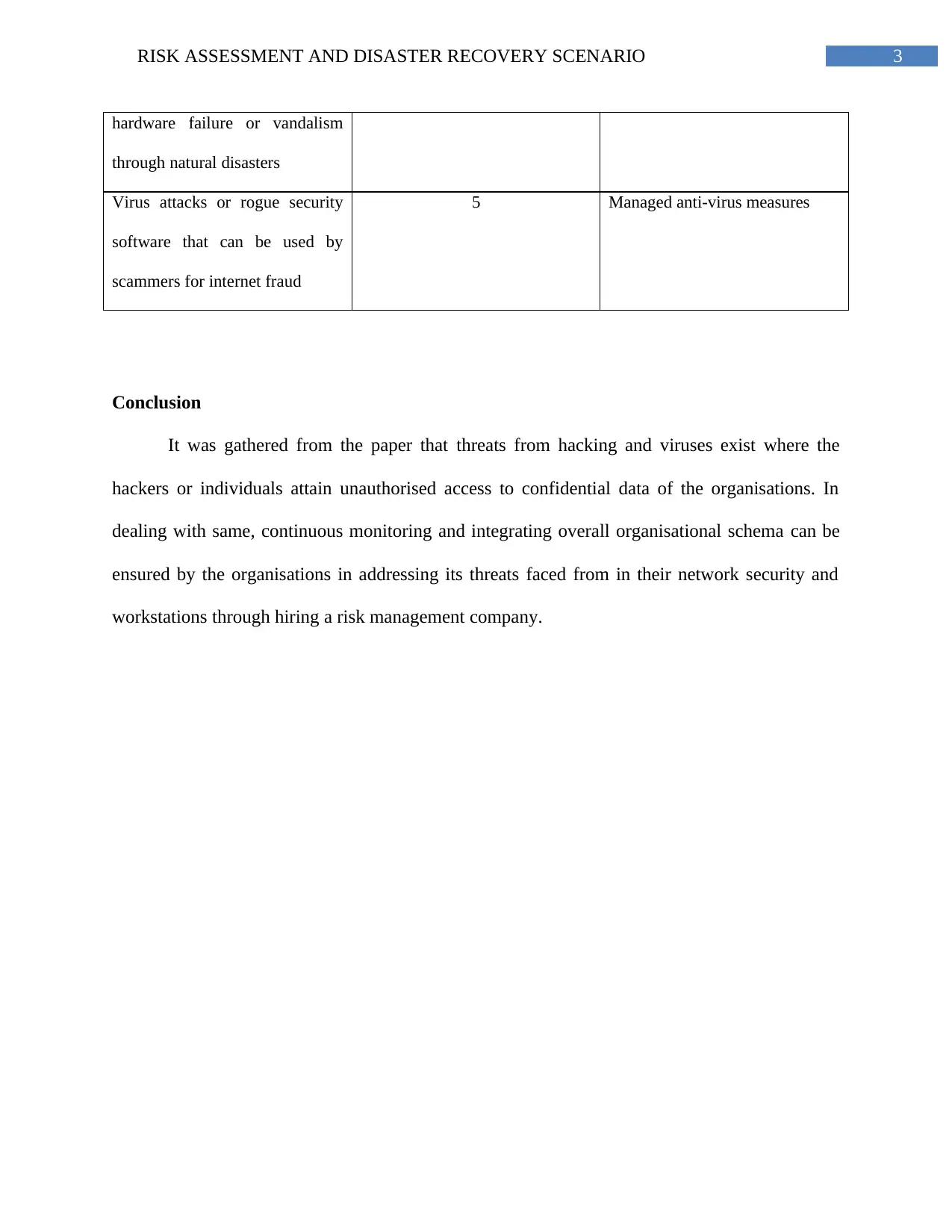
This report provides an analysis of network security threats and proposes a risk assessment and disaster recovery plan. It identifies unstructured threats, internal threats from employees, and external threats from hacking and viruses. The report emphasizes the importance of continuous monitoring, segmentation of networks, and integrating organizational schema to recover from security breaches. A control plan is outlined, rating the importance of various network security risks such as unauthorized access, theft, data loss, and virus attacks, along with corresponding measures like data breach risk intelligence systems, automatic monitoring, backup recovery, and managed anti-virus measures. The study concludes that continuous monitoring and a robust organizational schema, potentially facilitated by a risk management company, are crucial in addressing network security threats.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)