COMP247 Data Communications Assignment 2: Network Redesign Report
VerifiedAdded on 2022/10/31
|5
|1359
|220
Report
AI Summary
This report undertakes a comprehensive analysis of the Soylent Co. network, a financial firm, to identify existing faults and propose an improved network design. The analysis highlights inefficiencies stemming from unplanned network upgrades, resulting in performance issues such as latency and bandwidth limitations, alongside significant security vulnerabilities. The proposed redesign introduces a hierarchical, modular network architecture incorporating VLANs for network segmentation, enhancing both performance and security. The report details the implementation of sub networks, IP addressing, and the use of firewalls to mitigate external threats and control inter-departmental communications. The report provides detailed justifications for all proposed changes, including the use of dedicated sub networks and VLANs. The report concludes with a discussion of security enhancements, addressing the need for controlled access and authentication to prevent unauthorized data access, ensuring a more robust and secure network environment.

Department of Computing
COMP247 Data Communications
Assignment 2, Session 1, 2019
Name: Student Number:
Network Analysis and Design
Introduction
The following report conducts an analysis of the network of financial
firm Soylent and tries to identify faults that exist in the current set up.
Based on this the report is to suggest an improved design along with
appropriate justification. Additionally this report validates the security
parameters of the network to check if effective security measures are in
place. The report starts by describing the faults that exist in the recently
upgraded network after which the redesigned network gets proposed.
All changes made to the redesigned network are then justified [1]. The
network design proposed by the report comprises VLANs requiring sub
networks of the major network and corresponding details regarding IP
addressing. Then the security gets further discussed after which the
report ends with concluding notes.
Soylent Network Evaluation
The financial and insurance firm Soylent has recently
upgraded their network which unfortunately seems to be causing
issues for the firm. As a result the firm require expert assistance in
identifying the faults and rectifying them.
Identification of faults
Upon preliminary inspection it is found that the recently upgraded
network of Soylent has been implemented in a very inefficient and
unplanned manner. The inefficiency results from multiple repeated
branching of the network it gets provided to the different departments
[3]. As a result, performance issues are destined to occur in the
network. These performance issues can include but are not limited to
poor latency, slow response times, network disruptions and slow
COMP247 Data Communications
Assignment 2, Session 1, 2019
Name: Student Number:
Network Analysis and Design
Introduction
The following report conducts an analysis of the network of financial
firm Soylent and tries to identify faults that exist in the current set up.
Based on this the report is to suggest an improved design along with
appropriate justification. Additionally this report validates the security
parameters of the network to check if effective security measures are in
place. The report starts by describing the faults that exist in the recently
upgraded network after which the redesigned network gets proposed.
All changes made to the redesigned network are then justified [1]. The
network design proposed by the report comprises VLANs requiring sub
networks of the major network and corresponding details regarding IP
addressing. Then the security gets further discussed after which the
report ends with concluding notes.
Soylent Network Evaluation
The financial and insurance firm Soylent has recently
upgraded their network which unfortunately seems to be causing
issues for the firm. As a result the firm require expert assistance in
identifying the faults and rectifying them.
Identification of faults
Upon preliminary inspection it is found that the recently upgraded
network of Soylent has been implemented in a very inefficient and
unplanned manner. The inefficiency results from multiple repeated
branching of the network it gets provided to the different departments
[3]. As a result, performance issues are destined to occur in the
network. These performance issues can include but are not limited to
poor latency, slow response times, network disruptions and slow
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
bandwidth. The other most notable flaw in Soylent's current network is
that little to no security measures are present. This makes the network
of Soylent vulnerable to both external and internal information security
threats. The external security threats include threats from malwares,
hackers, denial of service attacks, spam, vulnerability exploits among
others. To prevent these attacks it is strongly recommended that
companies utilize security applications like firewall applications,
antivirus packages and other tools [1]. Internal security threats can
come from organizational members making misuse of excess privileges.
This kind of threats can be mitigated by ensuring query level access to
the members. The web + Email server, engineering file server and HR
file server are critical resources of a company and should not be used
exclusively through any particular department. It is better to maintain a
server farm where these resources are securely administered. Other
areas of inefficiency include the singular network connections from the
ISP for the Web + Email server and the printer of the engineering
department [5]. While a separate network for the server is still
understandable, the connection for the printer is a complete waste.
Subsection two
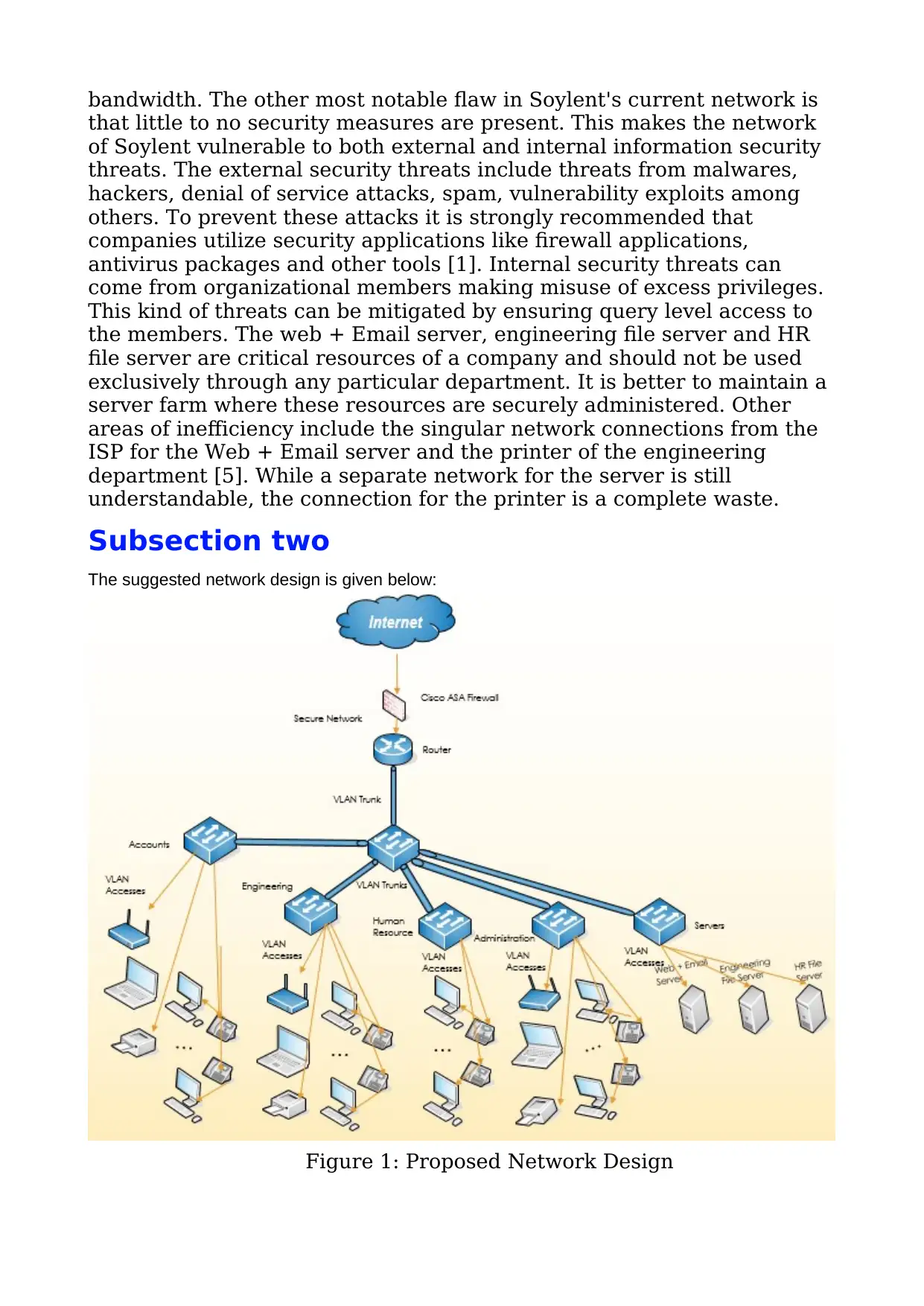
The suggested network design is given below:
Figure 1: Proposed Network Design
that little to no security measures are present. This makes the network
of Soylent vulnerable to both external and internal information security
threats. The external security threats include threats from malwares,
hackers, denial of service attacks, spam, vulnerability exploits among
others. To prevent these attacks it is strongly recommended that
companies utilize security applications like firewall applications,
antivirus packages and other tools [1]. Internal security threats can
come from organizational members making misuse of excess privileges.
This kind of threats can be mitigated by ensuring query level access to
the members. The web + Email server, engineering file server and HR
file server are critical resources of a company and should not be used
exclusively through any particular department. It is better to maintain a
server farm where these resources are securely administered. Other
areas of inefficiency include the singular network connections from the
ISP for the Web + Email server and the printer of the engineering
department [5]. While a separate network for the server is still
understandable, the connection for the printer is a complete waste.
Subsection two
The suggested network design is given below:
Figure 1: Proposed Network Design

The primary change that needs to be brought to the network of
Soylent is of implementing a hierarchical modular network architecture
with the network access being made available to the network devices
through a multilayer switched network consisting of distribution and
access layer switches. Network connections to each department should
be ensured by using dedicated sub networks to improve performance
[2].
These sub networks are to be assigned to the VLANs of the
respective departments. The VLANs will help the firm Soylent segment
their network [4]. These VLANs also help in managing separate rules
and policies for the different VLANs.
The direct links of devices with the immediate access layer switch
is to have the respective interface mode as switchport access [6]. This is
because the switches are to have the specific VLANs of the devices they
provide access to.
The links between the distribution switch and the access switches
need to be in trunk mode since the switches need to enable
communications between the concerned access layer switch with that of
all other switches. This therefore provides a secure framework of inter
departmental communications within the organization.
Security against external threats to the network is ensured
through installing and operating firewall applications and other security
applications. VLANs already offer controlled intercommunications in the
network, firewalls can add further levels of authentication.
Subsection three
The members of engineering department are able to view all
contents of Human Resources specific information on the file server as
the existing network does not have any security mechanisms in place.
Moreover, the issue stems from the fact that the network to the
different branches is made available via the engineering department.
This not only slows down the network performance but makes the
network of subsequent hops visible to the engineering department. This
issue can be easily eliminated by ensuring dedicated sub networks are
set up for the different branches. This can be carried out by adding
routers or implementing VLANs through layer 3 switches [7]. However,
using routers for so many departments can prove very costly. Inter
VLAN routing here helps in making communications between
departments secure and difficult to exploit. Firewalls can also be used to
add authentication and usage policies for devices of individual
departments.
Soylent is of implementing a hierarchical modular network architecture
with the network access being made available to the network devices
through a multilayer switched network consisting of distribution and
access layer switches. Network connections to each department should
be ensured by using dedicated sub networks to improve performance
[2].
These sub networks are to be assigned to the VLANs of the
respective departments. The VLANs will help the firm Soylent segment
their network [4]. These VLANs also help in managing separate rules
and policies for the different VLANs.
The direct links of devices with the immediate access layer switch
is to have the respective interface mode as switchport access [6]. This is
because the switches are to have the specific VLANs of the devices they
provide access to.
The links between the distribution switch and the access switches
need to be in trunk mode since the switches need to enable
communications between the concerned access layer switch with that of
all other switches. This therefore provides a secure framework of inter
departmental communications within the organization.
Security against external threats to the network is ensured
through installing and operating firewall applications and other security
applications. VLANs already offer controlled intercommunications in the
network, firewalls can add further levels of authentication.
Subsection three
The members of engineering department are able to view all
contents of Human Resources specific information on the file server as
the existing network does not have any security mechanisms in place.
Moreover, the issue stems from the fact that the network to the
different branches is made available via the engineering department.
This not only slows down the network performance but makes the
network of subsequent hops visible to the engineering department. This
issue can be easily eliminated by ensuring dedicated sub networks are
set up for the different branches. This can be carried out by adding
routers or implementing VLANs through layer 3 switches [7]. However,
using routers for so many departments can prove very costly. Inter
VLAN routing here helps in making communications between
departments secure and difficult to exploit. Firewalls can also be used to
add authentication and usage policies for devices of individual
departments.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Conclusion
In conclusion, the following report successfully conducts an
analysis of the network of financial firm Soylent and tries to identify
faults that exist in the current set up. Based on this the report is to
suggest an improved design along with appropriate justification.
Additionally this report validates the security parameters of the network
to check if effective security measures are in place. The report starts by
describing the faults that exist in the recently upgraded network after
which the redesigned network gets proposed. All changes made to the
redesigned network are then justified. The network design proposed by
the report comprises VLANs requiring sub networks of the major
network and corresponding details regarding IP addressing. Then the
report ends after discussing security of the network.
In conclusion, the following report successfully conducts an
analysis of the network of financial firm Soylent and tries to identify
faults that exist in the current set up. Based on this the report is to
suggest an improved design along with appropriate justification.
Additionally this report validates the security parameters of the network
to check if effective security measures are in place. The report starts by
describing the faults that exist in the recently upgraded network after
which the redesigned network gets proposed. All changes made to the
redesigned network are then justified. The network design proposed by
the report comprises VLANs requiring sub networks of the major
network and corresponding details regarding IP addressing. Then the
report ends after discussing security of the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
[1] A. Abdelsalam, S. Salsano, F. Clad, P. Camarillo, and C. Filsfils,,
April. SERA: Segment routing aware firewall for service function
chaining scenarios. In 2018 IFIP Networking Conference (IFIP
Networking) and Workshops (pp. 46-54). IEEE. , 2019
[2] D. Komosný, M. Vozňák, and S.U. Rehman, Location accuracy of
commercial IP address geolocation databases. , 2017.
[3] G. Li, H. Zhou, G. Li, and B. Feng, Application-aware and Dynamic
Security Function Chaining for Mobile Networks. J. Internet Serv. Inf.
Secur., 7(4), pp.21-34. , 2017.
[4] M. Koerner, and O. Kao, MAC Based Dynamic VLAN Tagging with
OpenFlow for WLAN Access Networks. Procedia Computer Science, 94,
pp.497-501. , 2016.
[5] M. Trevisan, D. Giordano, I. Drago, M. Mellia, and M. Munafo,
December. Five years at the edge: watching internet from the ISP
network. In Proceedings of the 14th International Conference on
Emerging Networking EXperiments and Technologies (pp. 1-12). ACM. ,
2018,
[6] N.H. Prasad, B.K., Reddy, B. Amarnath, and M. Puthanial, , 2016.
Intervlan Routing and Various Configurations on Vlan in a Network
using Cisco Packet Tracer 6.2. International Journal for Innovative
Research in Science and Technology, 2(11), pp.749-758.
[7] X. Jin, N. Farrington, and J. Rexford, Your data center switch is
trying too hard. In Proceedings of the Symposium on SDN Research (p.
12). ACM. , 2016, March.
[1] A. Abdelsalam, S. Salsano, F. Clad, P. Camarillo, and C. Filsfils,,
April. SERA: Segment routing aware firewall for service function
chaining scenarios. In 2018 IFIP Networking Conference (IFIP
Networking) and Workshops (pp. 46-54). IEEE. , 2019
[2] D. Komosný, M. Vozňák, and S.U. Rehman, Location accuracy of
commercial IP address geolocation databases. , 2017.
[3] G. Li, H. Zhou, G. Li, and B. Feng, Application-aware and Dynamic
Security Function Chaining for Mobile Networks. J. Internet Serv. Inf.
Secur., 7(4), pp.21-34. , 2017.
[4] M. Koerner, and O. Kao, MAC Based Dynamic VLAN Tagging with
OpenFlow for WLAN Access Networks. Procedia Computer Science, 94,
pp.497-501. , 2016.
[5] M. Trevisan, D. Giordano, I. Drago, M. Mellia, and M. Munafo,
December. Five years at the edge: watching internet from the ISP
network. In Proceedings of the 14th International Conference on
Emerging Networking EXperiments and Technologies (pp. 1-12). ACM. ,
2018,
[6] N.H. Prasad, B.K., Reddy, B. Amarnath, and M. Puthanial, , 2016.
Intervlan Routing and Various Configurations on Vlan in a Network
using Cisco Packet Tracer 6.2. International Journal for Innovative
Research in Science and Technology, 2(11), pp.749-758.
[7] X. Jin, N. Farrington, and J. Rexford, Your data center switch is
trying too hard. In Proceedings of the Symposium on SDN Research (p.
12). ACM. , 2016, March.
1 out of 5
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





