Business Network Security Plan: Risk, Policies & Recovery
VerifiedAdded on 2024/05/31
|51
|10015
|210
Report
AI Summary
This document presents a comprehensive network security plan designed for business environments, emphasizing the critical role of network security in safeguarding data and maintaining operational integrity. It begins with an introduction to network security principles, highlighting its importance in protecting against both internal and external threats. The scope of the plan is defined, followed by clearly stated objectives, including resource protection, authentication, authorization, and data integrity. The document outlines key assumptions about potential security breaches and the need for proactive measures. A detailed risk analysis section identifies physical and non-physical assets, assesses potential risks, and summarizes vulnerabilities. Security policies are extensively covered, including acceptable use, email and communications, internet and network access, workstation, antivirus, DMZ, extranet, VPN and remote access, wireless and BYOD, firewall, intrusion detection, vulnerability scanning, internet, IP addressing, physical security, personnel, data, and system/hardware policies. The plan also addresses disaster recovery and business continuity, incorporating business impact analysis, insurance considerations, incident response team setup, physical safeguards, incident response procedures, restoration procedures, and forensics considerations. It concludes with security strategies, recommended controls, a list of residual risks, resource allocation, and a comprehensive list of references. This plan provides a structured approach to network security, aiming to minimize risks and ensure business resilience.

Network Security Plan
1
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction......................................................................................................................................5
Scope................................................................................................................................................6
Objectives........................................................................................................................................7
Assumptions....................................................................................................................................8
Risk Analysis...................................................................................................................................9
Asset Identification......................................................................................................................9
Physical and Non-Physical Assets:-......................................................................................12
Risks...........................................................................................................................................13
Individual Asset Risk Analysis:............................................................................................14
Risk Summary:.......................................................................................................................15
Threats, Challenges and Vulnerabilities....................................................................................16
Threats....................................................................................................................................16
Challenges...............................................................................................................................19
Vulnerabilities........................................................................................................................22
Security Policies............................................................................................................................23
Acceptable Use Policies:............................................................................................................23
Email and Communications Policy:.....................................................................................23
Internet and Network Access Policy:...................................................................................23
Workstation Policy:...............................................................................................................24
Network Security Policies:.........................................................................................................24
Antivirus Policy:.....................................................................................................................24
DMZ Policy:............................................................................................................................24
Extranet Policy:......................................................................................................................24
2
Introduction......................................................................................................................................5
Scope................................................................................................................................................6
Objectives........................................................................................................................................7
Assumptions....................................................................................................................................8
Risk Analysis...................................................................................................................................9
Asset Identification......................................................................................................................9
Physical and Non-Physical Assets:-......................................................................................12
Risks...........................................................................................................................................13
Individual Asset Risk Analysis:............................................................................................14
Risk Summary:.......................................................................................................................15
Threats, Challenges and Vulnerabilities....................................................................................16
Threats....................................................................................................................................16
Challenges...............................................................................................................................19
Vulnerabilities........................................................................................................................22
Security Policies............................................................................................................................23
Acceptable Use Policies:............................................................................................................23
Email and Communications Policy:.....................................................................................23
Internet and Network Access Policy:...................................................................................23
Workstation Policy:...............................................................................................................24
Network Security Policies:.........................................................................................................24
Antivirus Policy:.....................................................................................................................24
DMZ Policy:............................................................................................................................24
Extranet Policy:......................................................................................................................24
2

VPN and Remote Access Policy............................................................................................25
Wireless and BYOD Policy:..................................................................................................25
Firewall Policy:.......................................................................................................................26
Intrusion Detection Policy:....................................................................................................26
Vulnerability Scanning Policy:.............................................................................................26
Internet Policy:.......................................................................................................................27
IP addressed and documentation management policy.......................................................28
Physical Security Policies:.........................................................................................................28
External Protection:...............................................................................................................29
Internal Protection:................................................................................................................29
Personnel Policies:.....................................................................................................................30
Visitors Policy:...........................................................................................................................30
Employee Hiring and Termination Policy:................................................................................30
User training Policy:..................................................................................................................31
Data Policies:.................................................................................................................................32
Information Classification and Sensitivity Policy:....................................................................32
Encryption Policy:......................................................................................................................32
Backup Policy:........................................................................................................................32
Password Management and Complexity Policy:.......................................................................33
System and Hardware Policies:..................................................................................................33
Hardware Lifecycle and Disposal Policy:..................................................................................33
Workstation Policy:....................................................................................................................33
Switch and Router Policy:..........................................................................................................33
Server Security Policy:...............................................................................................................33
Logging Policy:..........................................................................................................................34
3
Wireless and BYOD Policy:..................................................................................................25
Firewall Policy:.......................................................................................................................26
Intrusion Detection Policy:....................................................................................................26
Vulnerability Scanning Policy:.............................................................................................26
Internet Policy:.......................................................................................................................27
IP addressed and documentation management policy.......................................................28
Physical Security Policies:.........................................................................................................28
External Protection:...............................................................................................................29
Internal Protection:................................................................................................................29
Personnel Policies:.....................................................................................................................30
Visitors Policy:...........................................................................................................................30
Employee Hiring and Termination Policy:................................................................................30
User training Policy:..................................................................................................................31
Data Policies:.................................................................................................................................32
Information Classification and Sensitivity Policy:....................................................................32
Encryption Policy:......................................................................................................................32
Backup Policy:........................................................................................................................32
Password Management and Complexity Policy:.......................................................................33
System and Hardware Policies:..................................................................................................33
Hardware Lifecycle and Disposal Policy:..................................................................................33
Workstation Policy:....................................................................................................................33
Switch and Router Policy:..........................................................................................................33
Server Security Policy:...............................................................................................................33
Logging Policy:..........................................................................................................................34
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Disaster Recovery and Business Continuity:.................................................................................35
Business Impact Analysis..........................................................................................................36
Insurance Consideration:............................................................................................................36
Incident Response Team:...........................................................................................................37
Physical Safeguards:..................................................................................................................37
Incident Response Procedures:..................................................................................................37
Restoration Procedures:.............................................................................................................38
Forensics Considerations:..........................................................................................................39
Maintaining the Plan:.................................................................................................................39
Security Strategies and Recommended Controls...........................................................................40
Residual Risks...............................................................................................................................43
List of Residual Risks - that remain after all possible (cost-effective) mitigation or Treatment
of risks........................................................................................................................................43
Resources.......................................................................................................................................47
Conclusion:....................................................................................................................................49
References......................................................................................................................................50
4
Business Impact Analysis..........................................................................................................36
Insurance Consideration:............................................................................................................36
Incident Response Team:...........................................................................................................37
Physical Safeguards:..................................................................................................................37
Incident Response Procedures:..................................................................................................37
Restoration Procedures:.............................................................................................................38
Forensics Considerations:..........................................................................................................39
Maintaining the Plan:.................................................................................................................39
Security Strategies and Recommended Controls...........................................................................40
Residual Risks...............................................................................................................................43
List of Residual Risks - that remain after all possible (cost-effective) mitigation or Treatment
of risks........................................................................................................................................43
Resources.......................................................................................................................................47
Conclusion:....................................................................................................................................49
References......................................................................................................................................50
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Network security plan is important for both home and business field because at both the places
the internet connections are joint so it is just that it could be secure in this report will going to
study about the entire network security plan which is important for a wireless router so that they
can enjoy the network at home. Managing security implies understanding the dangers and
choosing how much risk are satisfactory. Distinctive levels of security are fitting for various
associations. No system is 100 percent secure, so don't go for that level of assurance. On the off
chance that you attempt to stay up-to-date on each new risk and each infection, you'll soon be a
trembling bundle of nervousness and stress.
Network security is important because it stands for a good neighbor policy. It is also important
for time and money policy the reason is it may secure the data from the virus and eliminate any
unwanted things which are not needed in an operating system.
The four fundamental security classes are as per the following:
1. Physical security (counting equipment)
2. Working framework level security
3. Interchanges security
4. Technical security
The popular networks are UUCP it stands for Unix to Unix copy. It can be used in many
networks like PC, apple, macs and many other operating systems. And if we talk about the
security purposes of the networks it is not easily connected to any host it needs user id and
passwords to connect to the network.
And the second one which is popular nowadays is an Internet. The Internet is the world's largest
network. The Internet is very easily connected to every device and the speed of this is also good.
5
Network security plan is important for both home and business field because at both the places
the internet connections are joint so it is just that it could be secure in this report will going to
study about the entire network security plan which is important for a wireless router so that they
can enjoy the network at home. Managing security implies understanding the dangers and
choosing how much risk are satisfactory. Distinctive levels of security are fitting for various
associations. No system is 100 percent secure, so don't go for that level of assurance. On the off
chance that you attempt to stay up-to-date on each new risk and each infection, you'll soon be a
trembling bundle of nervousness and stress.
Network security is important because it stands for a good neighbor policy. It is also important
for time and money policy the reason is it may secure the data from the virus and eliminate any
unwanted things which are not needed in an operating system.
The four fundamental security classes are as per the following:
1. Physical security (counting equipment)
2. Working framework level security
3. Interchanges security
4. Technical security
The popular networks are UUCP it stands for Unix to Unix copy. It can be used in many
networks like PC, apple, macs and many other operating systems. And if we talk about the
security purposes of the networks it is not easily connected to any host it needs user id and
passwords to connect to the network.
And the second one which is popular nowadays is an Internet. The Internet is the world's largest
network. The Internet is very easily connected to every device and the speed of this is also good.
5
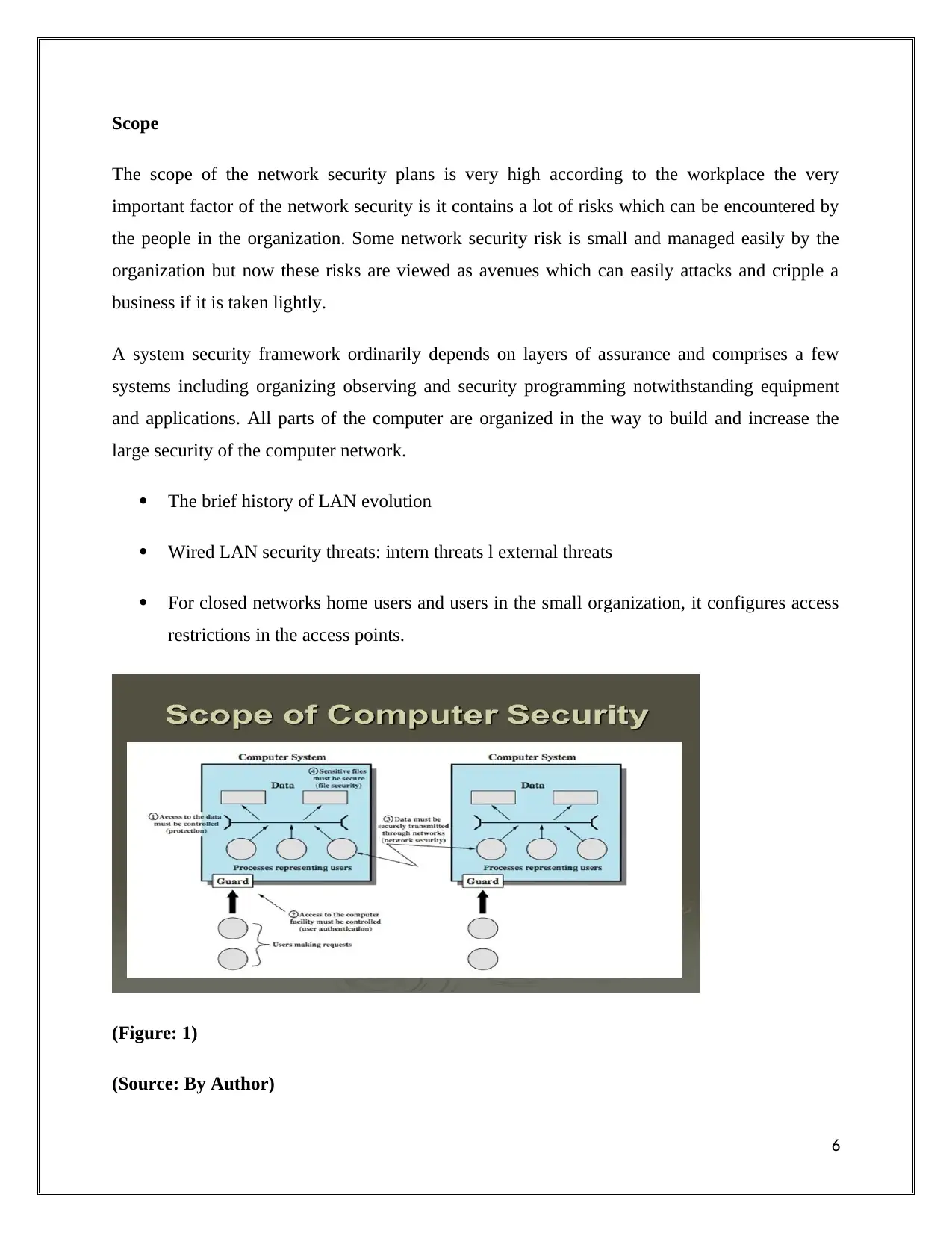
Scope
The scope of the network security plans is very high according to the workplace the very
important factor of the network security is it contains a lot of risks which can be encountered by
the people in the organization. Some network security risk is small and managed easily by the
organization but now these risks are viewed as avenues which can easily attacks and cripple a
business if it is taken lightly.
A system security framework ordinarily depends on layers of assurance and comprises a few
systems including organizing observing and security programming notwithstanding equipment
and applications. All parts of the computer are organized in the way to build and increase the
large security of the computer network.
The brief history of LAN evolution
Wired LAN security threats: intern threats l external threats
For closed networks home users and users in the small organization, it configures access
restrictions in the access points.
(Figure: 1)
(Source: By Author)
6
The scope of the network security plans is very high according to the workplace the very
important factor of the network security is it contains a lot of risks which can be encountered by
the people in the organization. Some network security risk is small and managed easily by the
organization but now these risks are viewed as avenues which can easily attacks and cripple a
business if it is taken lightly.
A system security framework ordinarily depends on layers of assurance and comprises a few
systems including organizing observing and security programming notwithstanding equipment
and applications. All parts of the computer are organized in the way to build and increase the
large security of the computer network.
The brief history of LAN evolution
Wired LAN security threats: intern threats l external threats
For closed networks home users and users in the small organization, it configures access
restrictions in the access points.
(Figure: 1)
(Source: By Author)
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Objectives
When network security is created it definitely has some goals which they have to achieve in the
organization. Some objectives are given below which can be focused on the term network
security is given below:
Resource protection- resource protection have some kind of schemes which only authorized by
the users. Resources which are categorized differently by the users for assessing their system.
Authentication-
Verification of the resources which are involved in human or machines. Authentication is
required in the case of using the networking but there are some security aspects which are
being used in network security. traditionally the systems are used by the user when they
put the correct username and password and in this simple process lots of things are
required like digital certificates, the correct password otherwise it may not get connected.
Authorization-
The assurance that the individual or PC at the opposite end of the session has consent to
do the demand. Approval is the way toward figuring out who or what can get to
framework assets or play out specific exercises on a framework. Commonly, approval is
performed in the setting of verification.
Integrity-
data integrity
a) Shield the information from being sniffed and deciphered, regularly by scrambling it.
b) Guarantee that the transmission has not been changed (information respectability).
c) Demonstrate that the transmission happened (non-repudiation). Later on, you may require
what might as well be called enlisted or affirmed mail.
7
When network security is created it definitely has some goals which they have to achieve in the
organization. Some objectives are given below which can be focused on the term network
security is given below:
Resource protection- resource protection have some kind of schemes which only authorized by
the users. Resources which are categorized differently by the users for assessing their system.
Authentication-
Verification of the resources which are involved in human or machines. Authentication is
required in the case of using the networking but there are some security aspects which are
being used in network security. traditionally the systems are used by the user when they
put the correct username and password and in this simple process lots of things are
required like digital certificates, the correct password otherwise it may not get connected.
Authorization-
The assurance that the individual or PC at the opposite end of the session has consent to
do the demand. Approval is the way toward figuring out who or what can get to
framework assets or play out specific exercises on a framework. Commonly, approval is
performed in the setting of verification.
Integrity-
data integrity
a) Shield the information from being sniffed and deciphered, regularly by scrambling it.
b) Guarantee that the transmission has not been changed (information respectability).
c) Demonstrate that the transmission happened (non-repudiation). Later on, you may require
what might as well be called enlisted or affirmed mail.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Assumptions
Each association with an online presence or an association with the Internet has turned into the
potential focus of interruption and robbery. PC programmers are particularly focusing on law
offices to take licensed innovation information and competitive innovations.
The first assumption is that the To start with, expect that your system is being subjected to visit
astute examining if not focused on assault. Take every single sensible measure to solidify the
system against the progressing endeavors to break in. In the event that an aggressor is effective
in picking up an underlying foothold (e.g., introducing a key-lumberjack on the PC of a
representative), take every single sensible measure to make it harder for the attacker to use that
foothold into an out and out observation of the system, bringing about the area and robbery of
private data.
The second assumption is accepted that your barriers will fall flat and that a gate crasher will
have the capacity to get inside your system to inspect or lay the basis to take and exfiltration
data. Take every sensible measure to attempt to recognize that interruption as ahead of schedule
as conceivable so it can be managed before private data is stolen.
The third assumption is expected that your interruption location measures will neglect to caution
you to the issue before a gate crasher prevails with regards to taking secret data. Have a reaction
design set up so you can respond rapidly and satisfactorily to the information rupture, limit the
harm to your data resources, and limit the danger of blow-back to your business and notoriety.
At last, expect that the absolute worst will happen, that very delicate data will be stolen, and that
you'll have to safeguard yourself against an administration examination or in common
prosecution. Have documentation prepared to demonstrate that you did in certainty take every
single sensible measure to shield yourself and that you responded legitimately when those
safeguards failed.
8
Each association with an online presence or an association with the Internet has turned into the
potential focus of interruption and robbery. PC programmers are particularly focusing on law
offices to take licensed innovation information and competitive innovations.
The first assumption is that the To start with, expect that your system is being subjected to visit
astute examining if not focused on assault. Take every single sensible measure to solidify the
system against the progressing endeavors to break in. In the event that an aggressor is effective
in picking up an underlying foothold (e.g., introducing a key-lumberjack on the PC of a
representative), take every single sensible measure to make it harder for the attacker to use that
foothold into an out and out observation of the system, bringing about the area and robbery of
private data.
The second assumption is accepted that your barriers will fall flat and that a gate crasher will
have the capacity to get inside your system to inspect or lay the basis to take and exfiltration
data. Take every sensible measure to attempt to recognize that interruption as ahead of schedule
as conceivable so it can be managed before private data is stolen.
The third assumption is expected that your interruption location measures will neglect to caution
you to the issue before a gate crasher prevails with regards to taking secret data. Have a reaction
design set up so you can respond rapidly and satisfactorily to the information rupture, limit the
harm to your data resources, and limit the danger of blow-back to your business and notoriety.
At last, expect that the absolute worst will happen, that very delicate data will be stolen, and that
you'll have to safeguard yourself against an administration examination or in common
prosecution. Have documentation prepared to demonstrate that you did in certainty take every
single sensible measure to shield yourself and that you responded legitimately when those
safeguards failed.
8
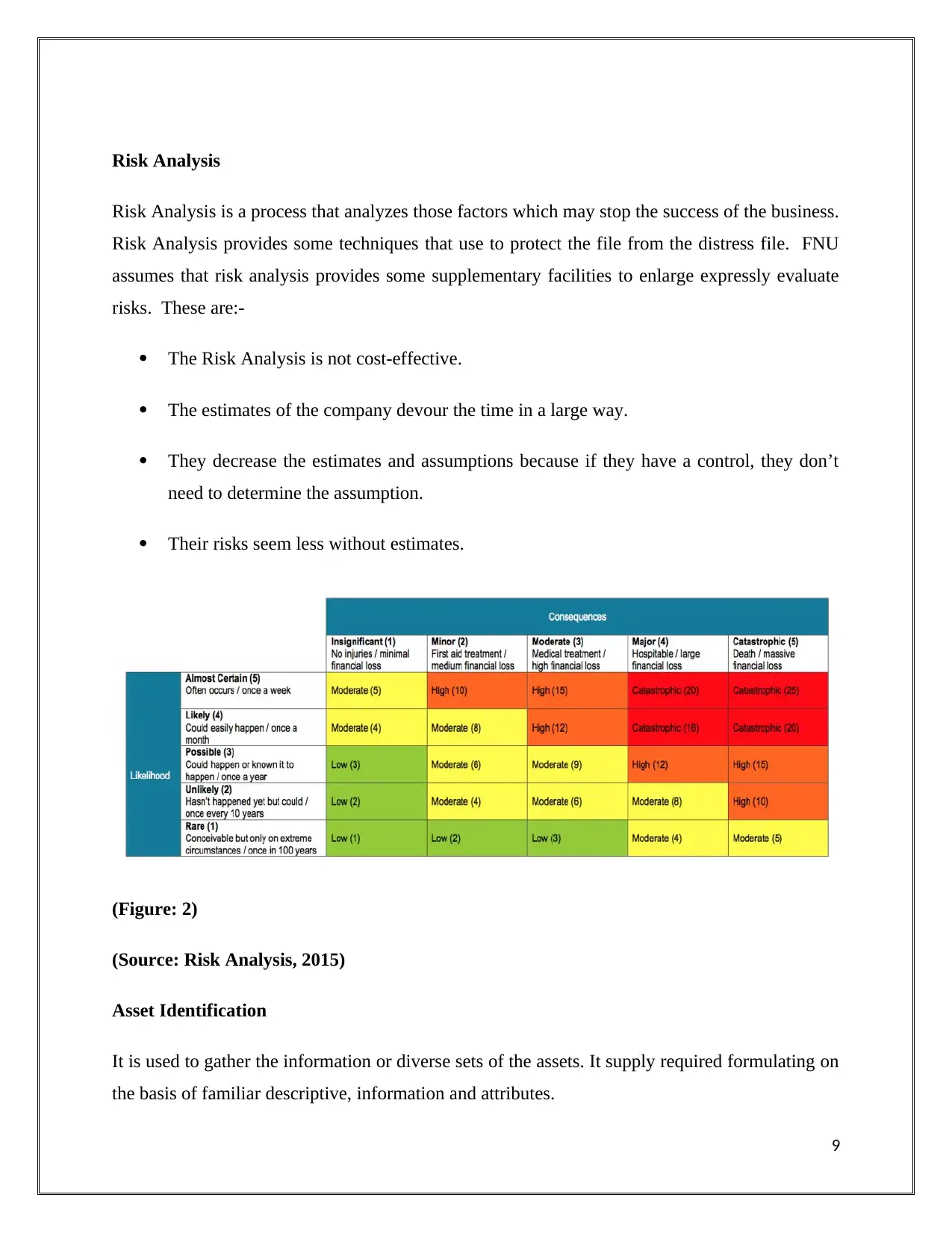
Risk Analysis
Risk Analysis is a process that analyzes those factors which may stop the success of the business.
Risk Analysis provides some techniques that use to protect the file from the distress file. FNU
assumes that risk analysis provides some supplementary facilities to enlarge expressly evaluate
risks. These are:-
The Risk Analysis is not cost-effective.
The estimates of the company devour the time in a large way.
They decrease the estimates and assumptions because if they have a control, they don’t
need to determine the assumption.
Their risks seem less without estimates.
(Figure: 2)
(Source: Risk Analysis, 2015)
Asset Identification
It is used to gather the information or diverse sets of the assets. It supply required formulating on
the basis of familiar descriptive, information and attributes.
9
Risk Analysis is a process that analyzes those factors which may stop the success of the business.
Risk Analysis provides some techniques that use to protect the file from the distress file. FNU
assumes that risk analysis provides some supplementary facilities to enlarge expressly evaluate
risks. These are:-
The Risk Analysis is not cost-effective.
The estimates of the company devour the time in a large way.
They decrease the estimates and assumptions because if they have a control, they don’t
need to determine the assumption.
Their risks seem less without estimates.
(Figure: 2)
(Source: Risk Analysis, 2015)
Asset Identification
It is used to gather the information or diverse sets of the assets. It supply required formulating on
the basis of familiar descriptive, information and attributes.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

There are two types of assets:-
Current assets
Non-current assets
Current assets
It has three sub-classifications. They are following:-
a) Receiving of the Account
b) Get ready for the expenses
c) Having securities of the marketing substances
d) Gathers all the details of the cash transactions.
e) Make the description daily
Non-current assets
Non- current assets has following 3 classifications:-
a) Always be in benevolence
b) Assets should be fixed in the tangible form.
c) Assets may also contain the fixed form of intangible.
When the topic comes about investments, the classification is not applicable. In this situations,
the assets use their types for the higher growth of the company.
These two assets are following:-
Growth Assets
10
Current assets
Non-current assets
Current assets
It has three sub-classifications. They are following:-
a) Receiving of the Account
b) Get ready for the expenses
c) Having securities of the marketing substances
d) Gathers all the details of the cash transactions.
e) Make the description daily
Non-current assets
Non- current assets has following 3 classifications:-
a) Always be in benevolence
b) Assets should be fixed in the tangible form.
c) Assets may also contain the fixed form of intangible.
When the topic comes about investments, the classification is not applicable. In this situations,
the assets use their types for the higher growth of the company.
These two assets are following:-
Growth Assets
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Defensive Assets
Growth Assets
Growth Assets use to produce the capital for the owner or keeper from the
different ways such as the lease, charter, and premium.
From this type of assets, the value of this capital arises in the higher amount and
then they return the earning amount to the keeper.
Sometimes, it faces many challenges. Due to these challenges, they find some
risks. They do not find the valuation.
To evaluate the Growth assets more easily. FNC provides three examples of the
growth assets.
a) Having the details of the property which are rented.
b) They have the same security level
c) They have the complete knowledge of the product such as their furniture,
art, and values etc.
Defensive Assets
These assets provide the capital from the investment to their owner.
They analysis the growth and limit of the investments because their growth only
depends upon the investments.
FNC analysis the defensive assets with their examples for understanding their
growth. They are
a) They firstly secure that there is no debt on the investor because they did
not make a customer who is in debt.
b) They check the details of the saving accounts of their customers.
11
Growth Assets
Growth Assets use to produce the capital for the owner or keeper from the
different ways such as the lease, charter, and premium.
From this type of assets, the value of this capital arises in the higher amount and
then they return the earning amount to the keeper.
Sometimes, it faces many challenges. Due to these challenges, they find some
risks. They do not find the valuation.
To evaluate the Growth assets more easily. FNC provides three examples of the
growth assets.
a) Having the details of the property which are rented.
b) They have the same security level
c) They have the complete knowledge of the product such as their furniture,
art, and values etc.
Defensive Assets
These assets provide the capital from the investment to their owner.
They analysis the growth and limit of the investments because their growth only
depends upon the investments.
FNC analysis the defensive assets with their examples for understanding their
growth. They are
a) They firstly secure that there is no debt on the investor because they did
not make a customer who is in debt.
b) They check the details of the saving accounts of their customers.
11
c) They give the certification to the clients of their deposits.
Physical and Non-Physical Assets:-
“Physical Assets are the combination of the capital, exchanging the worth and trading business.
It is based upon the existence of the stuff. It is mostly used in the business for exchanging the
properties, capital, and stuff etc. It is also known as the "Tangible Assets".
(Figure: 3)
(Source: Maintenance Within Physical Asset Management, 2016)
12
Physical and Non-Physical Assets:-
“Physical Assets are the combination of the capital, exchanging the worth and trading business.
It is based upon the existence of the stuff. It is mostly used in the business for exchanging the
properties, capital, and stuff etc. It is also known as the "Tangible Assets".
(Figure: 3)
(Source: Maintenance Within Physical Asset Management, 2016)
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 51
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




