COIT 20246 Assignment: In-depth Analysis of Network Security Topics
VerifiedAdded on 2023/03/31
|12
|3639
|164
Homework Assignment
AI Summary
This assignment comprises ten weekly tasks exploring various aspects of network technologies and security. Each task requires summarizing a resource on topics such as Network Attached Storage (NAS), Storage Area Network (SAN), New Technology File System (NTFS), Fiber to the Node (FTTN), Tor browser, cryptojacking, and fiber optic cable failures. The summaries, approximately 200-300 words each, detail the resource's focus, key information, and usefulness. The assignment emphasizes the importance of citing and referencing materials using the Harvard format and using the student's own words. The tasks cover a wide range of subjects related to computer networks, storage solutions, file systems, internet infrastructure, security threats, and network resilience. The resources provide an in-depth understanding of the technologies and their practical implications, covering topics from physical infrastructure to cybersecurity.
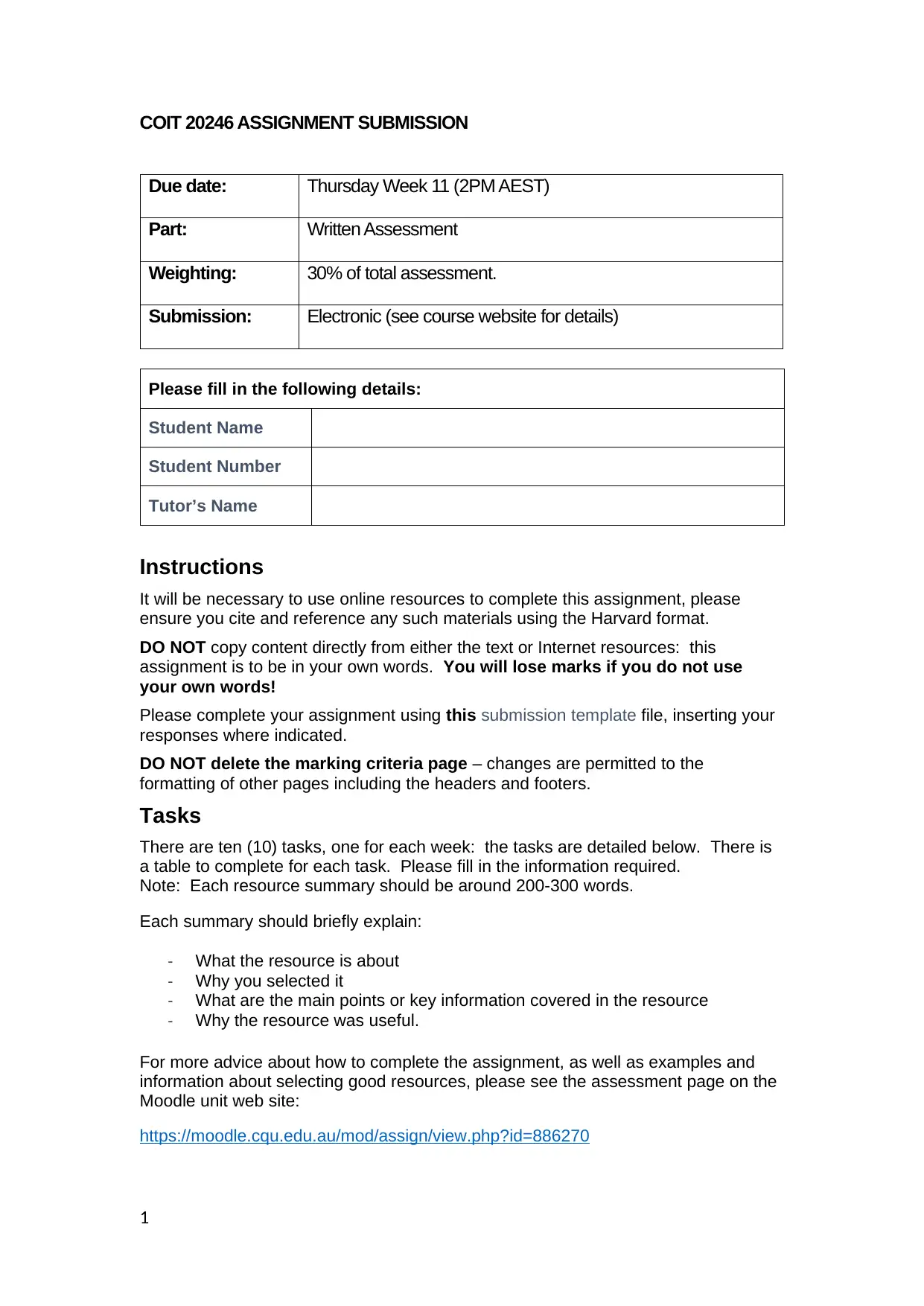
COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 1
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or Storage
Area Network (SAN) technologies. Find and summarise ONE resource that describes
EITHER NAS or SAN storage technologies. The resource, and your summary, must
focus on either NAS or SAN, NOT BOTH.
Title and Reference:
Chosen topic: Network Attached Storage (NAS)
Bednarz, A. (2019). What is a SAN and how does it differ from NAS?. [online] Network
World. Available at: https://www.networkworld.com/article/3256312/what-is-a-san-and-
how-does-it-differ-from-nas.html [Accessed 29 May 2019].
https://www.networkworld.com/article/3256312/what-is-a-san-and-how-does-it-differ-
from-nas.html
Summary:
This resource provides a detailed description of Storage Area Network (SAN) which
helps in providing block level network access to storage. The resource also helps in
understanding that there are different components of SAN such as storage elements,
storage devices, switches and hosts. The resources also helps in understanding the
wide range of topologies, protocols and technologies. The resources also provides in-
depth discussion about the usage of the SAN and most of the associated switches. The
reason behind selecting this resource is it provides a detailed explanation of the use of
this service in commercial establishment. This resource also helps in understanding the
wide range of protocols which are considered in SAN such as the Fibre Channel, Hyper
SCSI and the Ethernet. The working principles of SAN is the key point of this SAN. The
other key information which was mentioned in this resources is the association of the
SAN fabric with SAN. The association with the Fibre Channel switching technology with
SAN is written in this paper in a detailed manner. The resource was very much useful
to understand the tape libraries and disk based services. It can be said that SAN is very
much beneficial to understand how each server associated with SAN gets access to
the shared devices. The role of the SAN volume controller was also stated in the paper
in a professional manner.
2
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or Storage
Area Network (SAN) technologies. Find and summarise ONE resource that describes
EITHER NAS or SAN storage technologies. The resource, and your summary, must
focus on either NAS or SAN, NOT BOTH.
Title and Reference:
Chosen topic: Network Attached Storage (NAS)
Bednarz, A. (2019). What is a SAN and how does it differ from NAS?. [online] Network
World. Available at: https://www.networkworld.com/article/3256312/what-is-a-san-and-
how-does-it-differ-from-nas.html [Accessed 29 May 2019].
https://www.networkworld.com/article/3256312/what-is-a-san-and-how-does-it-differ-
from-nas.html
Summary:
This resource provides a detailed description of Storage Area Network (SAN) which
helps in providing block level network access to storage. The resource also helps in
understanding that there are different components of SAN such as storage elements,
storage devices, switches and hosts. The resources also helps in understanding the
wide range of topologies, protocols and technologies. The resources also provides in-
depth discussion about the usage of the SAN and most of the associated switches. The
reason behind selecting this resource is it provides a detailed explanation of the use of
this service in commercial establishment. This resource also helps in understanding the
wide range of protocols which are considered in SAN such as the Fibre Channel, Hyper
SCSI and the Ethernet. The working principles of SAN is the key point of this SAN. The
other key information which was mentioned in this resources is the association of the
SAN fabric with SAN. The association with the Fibre Channel switching technology with
SAN is written in this paper in a detailed manner. The resource was very much useful
to understand the tape libraries and disk based services. It can be said that SAN is very
much beneficial to understand how each server associated with SAN gets access to
the shared devices. The role of the SAN volume controller was also stated in the paper
in a professional manner.
2

Week 2
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference:
Chosen topic: New Technology File System
TechRepublic. (2019). News, Tips, and Advice for Technology Professionals -
TechRepublic. [online] Available at: https://www.techrepublic.com/article/file-
systems-101-ntfs/ [Accessed 29 May 2019].
https://www.techrepublic.com/article/file-systems-101-ntfs/
Summary:
This resource is about the New Technology File System which are increasingly used
in storing and retrieving of the files on a hard disk. The use of NTFS is very much
useful to keep the track of the file clusters. It can be said that the information about a
file cluster can be retrieved in a useful manner using a NTFS. The main reason
behind selecting this resources is it helps in identifying the advanced specifications of
the NTFS. The resources also stated that more than 16 billion bytes in size can also
be accessed from NTFS. The main point of discussion of this paper is it helps
identifying the file compression ability of NTFS. The resources also stated that long
file names are supported by NTFS. The resources was also very much useful to
understand the data security provided by NTFS on both the fixed as well as the
removable disks. The main point of discussion of this resource is the detailed
description of the Master File Table (MFT). This resource helps in understanding the
usefulness of the NTFS in terms of efficiency and storage. The other key information
of this resource is it helps in identifying different qualities of NTFS such as scalability
issues, journaling issues, transactions, and encryption techniques, reparse points
and interoperability. The resources was very much important to understand each of
the internal as well as the external features of NTFS such as ability of managing
metafiles and file compression abilities of NFTS.
3
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference:
Chosen topic: New Technology File System
TechRepublic. (2019). News, Tips, and Advice for Technology Professionals -
TechRepublic. [online] Available at: https://www.techrepublic.com/article/file-
systems-101-ntfs/ [Accessed 29 May 2019].
https://www.techrepublic.com/article/file-systems-101-ntfs/
Summary:
This resource is about the New Technology File System which are increasingly used
in storing and retrieving of the files on a hard disk. The use of NTFS is very much
useful to keep the track of the file clusters. It can be said that the information about a
file cluster can be retrieved in a useful manner using a NTFS. The main reason
behind selecting this resources is it helps in identifying the advanced specifications of
the NTFS. The resources also stated that more than 16 billion bytes in size can also
be accessed from NTFS. The main point of discussion of this paper is it helps
identifying the file compression ability of NTFS. The resources also stated that long
file names are supported by NTFS. The resources was also very much useful to
understand the data security provided by NTFS on both the fixed as well as the
removable disks. The main point of discussion of this resource is the detailed
description of the Master File Table (MFT). This resource helps in understanding the
usefulness of the NTFS in terms of efficiency and storage. The other key information
of this resource is it helps in identifying different qualities of NTFS such as scalability
issues, journaling issues, transactions, and encryption techniques, reparse points
and interoperability. The resources was very much important to understand each of
the internal as well as the external features of NTFS such as ability of managing
metafiles and file compression abilities of NFTS.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 3
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference:
Code, Security and Server Stuff. (2019). Telstra promised Fibre to the house (FTTP)
when I had FTTN and this is what happened.. [online] Available at:
https://fearby.com/article/telstra-promised-fibre-to-the-house-when-i-had-fttn-and-
this-is-what-happened/ [Accessed 29 May 2019].
https://fearby.com/article/telstra-promised-fibre-to-the-house-when-i-had-fttn-and-
this-is-what-happened/
Summary:
Chosen topic: FTTN
This resources is about the usefulness of FTTN which are widely used in most of the
global commercial establishments such as Telstra can be understood from this
resource. The resource can be very much useful to understand the usability of FTTN.
The usefulness of the FTTN by the consumers of Telstra Corporation was discussed
in this resource in an organized manner. The reliability of the FTN was discussed in a
detailed manner in this resource. The limitation of the FTTN was discussed in this
resource as well. This resources was very much useful to understand and identify the
advantages as well as the limitation of FTTN. The key point of discussion of this
resources is the download speed of FTTN. Based on the discussion of this paper it
can be said that the download speed of FTTM is decreasing each day. The main
point of discussion of this paper is the detailed conversation between a consumers of
Telstra with an operator of Telstar.
The other key information which can be identified from this resources is the
advantages as well as the benefits of using FTTN. The resources highlight that the
upload speed of FTTN is 400Mbps and the download speed of FTTN is 1000 Mbps.
The resources were very much useful to understand that the installation of the FTTN
usually takes day to one week time.
4
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference:
Code, Security and Server Stuff. (2019). Telstra promised Fibre to the house (FTTP)
when I had FTTN and this is what happened.. [online] Available at:
https://fearby.com/article/telstra-promised-fibre-to-the-house-when-i-had-fttn-and-
this-is-what-happened/ [Accessed 29 May 2019].
https://fearby.com/article/telstra-promised-fibre-to-the-house-when-i-had-fttn-and-
this-is-what-happened/
Summary:
Chosen topic: FTTN
This resources is about the usefulness of FTTN which are widely used in most of the
global commercial establishments such as Telstra can be understood from this
resource. The resource can be very much useful to understand the usability of FTTN.
The usefulness of the FTTN by the consumers of Telstra Corporation was discussed
in this resource in an organized manner. The reliability of the FTN was discussed in a
detailed manner in this resource. The limitation of the FTTN was discussed in this
resource as well. This resources was very much useful to understand and identify the
advantages as well as the limitation of FTTN. The key point of discussion of this
resources is the download speed of FTTN. Based on the discussion of this paper it
can be said that the download speed of FTTM is decreasing each day. The main
point of discussion of this paper is the detailed conversation between a consumers of
Telstra with an operator of Telstar.
The other key information which can be identified from this resources is the
advantages as well as the benefits of using FTTN. The resources highlight that the
upload speed of FTTN is 400Mbps and the download speed of FTTN is 1000 Mbps.
The resources were very much useful to understand that the installation of the FTTN
usually takes day to one week time.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 4
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference:
Chosen topic: Tor Browser
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 29 May 2019].
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html
Summary:
This resources sated the detailed description of the Tor browser which is increasingly
used in most of the commercial establishments as well as in our society. This
resources provided an in-depth discussion about the use of the Tor browser. This
resource also helps in identifying that Tor can be used in most of the different
categories of operating system which are used in the recent times such as Microsoft
Windows and Apple Mac. Most of the privacy concerns of the tor browsers is stated
in this resource which is the main reason behind selecting this resource. Tor browser
can be defined as the anonymity network which can be used by the users to avoid
the complexities of other operating systems such as Google Chrome and Microsoft
Windows. There are different types of alternatives of the Tor browser such as
Freenet, Freepto, Tails and Sub graph Operating System. The main point discussion
of this resource is it helps in the identification of the stored cookies in this system.
The other main point of discussion of this resources is that it helps in hiding the IP
address which cannot be done in the other operating systems. This resource was
selected in order to understand the that user activity of the Tor browser can be
monitored and tracked which cannot be done in other browsers such as Google
Chrome.
5
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference:
Chosen topic: Tor Browser
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 29 May 2019].
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html
Summary:
This resources sated the detailed description of the Tor browser which is increasingly
used in most of the commercial establishments as well as in our society. This
resources provided an in-depth discussion about the use of the Tor browser. This
resource also helps in identifying that Tor can be used in most of the different
categories of operating system which are used in the recent times such as Microsoft
Windows and Apple Mac. Most of the privacy concerns of the tor browsers is stated
in this resource which is the main reason behind selecting this resource. Tor browser
can be defined as the anonymity network which can be used by the users to avoid
the complexities of other operating systems such as Google Chrome and Microsoft
Windows. There are different types of alternatives of the Tor browser such as
Freenet, Freepto, Tails and Sub graph Operating System. The main point discussion
of this resource is it helps in the identification of the stored cookies in this system.
The other main point of discussion of this resources is that it helps in hiding the IP
address which cannot be done in the other operating systems. This resource was
selected in order to understand the that user activity of the Tor browser can be
monitored and tracked which cannot be done in other browsers such as Google
Chrome.
5

Week 5
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
Chosen topic: Crypto-jacking
Nadeau, M. (2019). What is cryptojacking? How to prevent, detect, and recover from
it. [online] CSO Online. Available at:
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html [Accessed 29 May 2019].
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html
Summary:
This resources was selected as it provided a detailed description of the crypto-
jacking which is increasingly used in most of the commercial establishment as well
as in our society. This resource helps in identifying that crypto-jacking procedure is
mostly used by social engineers all around the world to load the cryto-mining code on
the victims computers. The main reason behind the selection of this resources is the
detailed description of the injection of the crypto-mining codes on the victims
computer. The use of the Smominru crypto mining botnet can be understood from
this resource as well. This resource was very much useful to understand that crypto
jacking can be very much useful to understand the advanced technologies used by
the social engineers in most of the recent cyber security attacks. Real world crypto-
jacking was also discussed in this resource as well. The main reason behind the
selection of this resource is the detailed implementation of the crypto jacking
procedure. The other key point of this resources is the real world examples of crypto-
jacking such as the use of crypto-mining in GitHub data breach. The resource as
very much useful to understand that the devices of the social engineers can be also
affected during the crypto-jacking procedure.
6
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
Chosen topic: Crypto-jacking
Nadeau, M. (2019). What is cryptojacking? How to prevent, detect, and recover from
it. [online] CSO Online. Available at:
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html [Accessed 29 May 2019].
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html
Summary:
This resources was selected as it provided a detailed description of the crypto-
jacking which is increasingly used in most of the commercial establishment as well
as in our society. This resource helps in identifying that crypto-jacking procedure is
mostly used by social engineers all around the world to load the cryto-mining code on
the victims computers. The main reason behind the selection of this resources is the
detailed description of the injection of the crypto-mining codes on the victims
computer. The use of the Smominru crypto mining botnet can be understood from
this resource as well. This resource was very much useful to understand that crypto
jacking can be very much useful to understand the advanced technologies used by
the social engineers in most of the recent cyber security attacks. Real world crypto-
jacking was also discussed in this resource as well. The main reason behind the
selection of this resource is the detailed implementation of the crypto jacking
procedure. The other key point of this resources is the real world examples of crypto-
jacking such as the use of crypto-mining in GitHub data breach. The resource as
very much useful to understand that the devices of the social engineers can be also
affected during the crypto-jacking procedure.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference:
Chosen topic: Internet-cable-cut
Johnson, B. (2019). Internet connection cut between Europe, Asia and Africa.
[online] the Guardian. Available at:
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut [Accessed 27
May 2019].
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut
Summary:
This resource is about the major incident which had an undesirable impact in our
society. This resource described about the major internet blackout which affected
countries from Asia, Africa and Europe. The prime reason behind the selection of this
resources is the detailed description of this accident. The resources highlighted that
more than 75 million internet users were affected due to a cable cut which might
have occurred between Egypt and Italy. Based on the investigative sources it can be
said that the damage done to cable can be due to the undersea earthquakes as well
as from the anchor of the ships. The main point of discussion of this resources is the
impact of this cable cut, where thousands of people could not access to the internet
facilities even after having numerous wireless technologies as well as internet
connections. The undersea cable which was damaged had an undesirable impact on
both the societies of the affected countries as well as for the commercial
establishments. The entire internet traffic of the infected country was effected due to
the damage done to the undersea cable. This incident also affected the entire global
internet connectivity. Thus, this resource can be very much useful to understand the
impact of a damage done to the undersea cables.
7
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference:
Chosen topic: Internet-cable-cut
Johnson, B. (2019). Internet connection cut between Europe, Asia and Africa.
[online] the Guardian. Available at:
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut [Accessed 27
May 2019].
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut
Summary:
This resource is about the major incident which had an undesirable impact in our
society. This resource described about the major internet blackout which affected
countries from Asia, Africa and Europe. The prime reason behind the selection of this
resources is the detailed description of this accident. The resources highlighted that
more than 75 million internet users were affected due to a cable cut which might
have occurred between Egypt and Italy. Based on the investigative sources it can be
said that the damage done to cable can be due to the undersea earthquakes as well
as from the anchor of the ships. The main point of discussion of this resources is the
impact of this cable cut, where thousands of people could not access to the internet
facilities even after having numerous wireless technologies as well as internet
connections. The undersea cable which was damaged had an undesirable impact on
both the societies of the affected countries as well as for the commercial
establishments. The entire internet traffic of the infected country was effected due to
the damage done to the undersea cable. This incident also affected the entire global
internet connectivity. Thus, this resource can be very much useful to understand the
impact of a damage done to the undersea cables.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 7
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference:
Chosen topic: Enterprise Resource Planning
YourStory.com. (2019). Top ERP Trends of 2019 to Help you out in your Business.
[online] Available at: https://yourstory.com/mystory/top-erp-trends-of-2019-to-help-
you-out-in-your-bus-f581diot7c [Accessed 29 May 2019].
https://yourstory.com/mystory/top-erp-trends-of-2019-to-help-you-out-in-your-bus-
f581diot7c
Summary:
This resource provided a detailed description of the top ERP trends of 2019. The
advanced specification of the ERP is described in a detailed way in this resource.
This resource was very much convenient to understand the mobile accessibility of
the ERP systems. The resources stated that the improved accessibility of the RP
devices can be very much beneficial for the ERP system to address the security
vulnerabilities of the ERP systems. The importance of the security measures which
are going to be adopted by most of the ERP systems can be identified from this
resources which is the main reason behind the election of this resource. This
resource also helps in understanding that the ERP customer can be significantly
improved due to the recent modifications which are already done to the ERP systems
in the last 5 years. Real time response capability of the ERP systems are very much
important to understand the drastic change in the ERP architecture in the last 5
years. This resource also explained the importance of the human capabilities which
are expected from the users of the ERP systems. The key which is covered in this
resource is the detailed description of the future consideration of the ERP systems.
The resource was very much useful to have an idea about the top ERP trends.
8
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference:
Chosen topic: Enterprise Resource Planning
YourStory.com. (2019). Top ERP Trends of 2019 to Help you out in your Business.
[online] Available at: https://yourstory.com/mystory/top-erp-trends-of-2019-to-help-
you-out-in-your-bus-f581diot7c [Accessed 29 May 2019].
https://yourstory.com/mystory/top-erp-trends-of-2019-to-help-you-out-in-your-bus-
f581diot7c
Summary:
This resource provided a detailed description of the top ERP trends of 2019. The
advanced specification of the ERP is described in a detailed way in this resource.
This resource was very much convenient to understand the mobile accessibility of
the ERP systems. The resources stated that the improved accessibility of the RP
devices can be very much beneficial for the ERP system to address the security
vulnerabilities of the ERP systems. The importance of the security measures which
are going to be adopted by most of the ERP systems can be identified from this
resources which is the main reason behind the election of this resource. This
resource also helps in understanding that the ERP customer can be significantly
improved due to the recent modifications which are already done to the ERP systems
in the last 5 years. Real time response capability of the ERP systems are very much
important to understand the drastic change in the ERP architecture in the last 5
years. This resource also explained the importance of the human capabilities which
are expected from the users of the ERP systems. The key which is covered in this
resource is the detailed description of the future consideration of the ERP systems.
The resource was very much useful to have an idea about the top ERP trends.
8

Week 8
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference:
Chosen topic: British Airways hacking
Burgess, M. (2019). The British Airways hack is impressively bad. [online]
Wired.co.uk. Available at: https://www.wired.co.uk/article/hacks-data-breaches-in-
2018 [Accessed 29 May 2019].
https://www.wired.co.uk/article/hacks-data-breaches-in-2018
Summary:
This resource is very much useful to understand the hacking procedure of the British
Airways. This data breaching incident occurred from 21st August 21 to 5th September
during these time the social engineers were inside the IT infrastructure of the British
Airways. The main reason behind the selection of this resource is the detailed
description of the data which were compromise during this security attack. This
resource highlighted that the personal information of the consumers of this
corporation as well as the financial details of the clients of this airport corporation
were compromised during this hacking procedure. The most significant point of this
resource is the detailed explanation of the names, email ID, personnel telephone
numbers, residential address, credit card information which were stolen from the
consumers of this airport. The other key information of the paper is the payment
issue of the consumers of this airport corporation. This resources successfully
describes that more than 380000 transactions of this airport corporation were
affected during this data breaching incident. This data breaching had an undesirable
impact of both the business sales as well as the reputation of the British Airways.
This resource was very much useful to understand the impact of a data breaching
incident in the British Airways.
9
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference:
Chosen topic: British Airways hacking
Burgess, M. (2019). The British Airways hack is impressively bad. [online]
Wired.co.uk. Available at: https://www.wired.co.uk/article/hacks-data-breaches-in-
2018 [Accessed 29 May 2019].
https://www.wired.co.uk/article/hacks-data-breaches-in-2018
Summary:
This resource is very much useful to understand the hacking procedure of the British
Airways. This data breaching incident occurred from 21st August 21 to 5th September
during these time the social engineers were inside the IT infrastructure of the British
Airways. The main reason behind the selection of this resource is the detailed
description of the data which were compromise during this security attack. This
resource highlighted that the personal information of the consumers of this
corporation as well as the financial details of the clients of this airport corporation
were compromised during this hacking procedure. The most significant point of this
resource is the detailed explanation of the names, email ID, personnel telephone
numbers, residential address, credit card information which were stolen from the
consumers of this airport. The other key information of the paper is the payment
issue of the consumers of this airport corporation. This resources successfully
describes that more than 380000 transactions of this airport corporation were
affected during this data breaching incident. This data breaching had an undesirable
impact of both the business sales as well as the reputation of the British Airways.
This resource was very much useful to understand the impact of a data breaching
incident in the British Airways.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference:
Chosen topic: Agile project management
The Digital Project Manager. (2019). The Best Articles About Agile Project
Management. [online] Available at: https://thedigitalprojectmanager.com/project-
management-topics/agile-pm/ [Accessed 29 May 2019].
https://thedigitalprojectmanager.com/project-management-topics/agile-pm/
Summary:
This resources provided a detailed explanation of the Agile project management
approach. Detailed description of the agile project management approach was stated
in the paper in an organised manner. This resource can be very much important to
manage each phase of a product development project. This resource also stated
about the usability and the effectiveness of the agile project management. The key
point of discussion of this resource is the 12 principles of agile such as technical
excellence and transparency, satisfaction of this customer, welcome the new
change, deliver frequently, building projects, face to face time and the measurement
of the progress. The four different categories of agile value is the main point of
discussion of this resource. This resources can be very much beneficial for the
project managers of product development projects as it can help them to manage
each of the stakeholders associated with a project. The other key information of this
resource is the usability of the agile methodology. The resources also helped in
understanding few benefits of agile project management methodology as well the
enhanced visibility of the projects. This resource is also very much useful to
understand the limitation of the agile project management methodology in terms of
less predictability, more commitment required from the project team members and
project scheduling.
10
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference:
Chosen topic: Agile project management
The Digital Project Manager. (2019). The Best Articles About Agile Project
Management. [online] Available at: https://thedigitalprojectmanager.com/project-
management-topics/agile-pm/ [Accessed 29 May 2019].
https://thedigitalprojectmanager.com/project-management-topics/agile-pm/
Summary:
This resources provided a detailed explanation of the Agile project management
approach. Detailed description of the agile project management approach was stated
in the paper in an organised manner. This resource can be very much important to
manage each phase of a product development project. This resource also stated
about the usability and the effectiveness of the agile project management. The key
point of discussion of this resource is the 12 principles of agile such as technical
excellence and transparency, satisfaction of this customer, welcome the new
change, deliver frequently, building projects, face to face time and the measurement
of the progress. The four different categories of agile value is the main point of
discussion of this resource. This resources can be very much beneficial for the
project managers of product development projects as it can help them to manage
each of the stakeholders associated with a project. The other key information of this
resource is the usability of the agile methodology. The resources also helped in
understanding few benefits of agile project management methodology as well the
enhanced visibility of the projects. This resource is also very much useful to
understand the limitation of the agile project management methodology in terms of
less predictability, more commitment required from the project team members and
project scheduling.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference:
Chosen topic: Project governance
Weinzimer, P. (2019). How to Succeed at Project Governance. [online] CIO.
Available at: https://www.cio.com/article/2693222/how-to-succeed-at-project-
governance.html [Accessed 29 May 2019].
https://www.cio.com/article/2693222/how-to-succeed-at-project-governance.html
Summary:
This resources was very much important to understand project governance in an
organized manner. The resource highlighted that project governance plan can be
very much important to manage complex project. This resource also provided
information about the use of project governance in most of the global IT
establishments. The main reason behind selecting this resource is the reliability of
the data. This resource have numerous sections and each of the section is very
much important to understand different aspect of project governance such as the
limitations as well as the implementation of the project management strategies. The
key information of this resource is the risk management ability of project governance.
The robust process associated with most of the project governance can also be
identified from this resource. The main point of discussion of this resources is the
advantages of project governance such as the problem solving ability and the
disadvantages in terms of the more financial backup required for the implementation
of project governance. This resource was also very much useful to understand the
benefits well as the drawback of project governance in a detailed manner so that
accountability of the stakeholders and transparency of the business is maintained on
a long term basis.
11
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference:
Chosen topic: Project governance
Weinzimer, P. (2019). How to Succeed at Project Governance. [online] CIO.
Available at: https://www.cio.com/article/2693222/how-to-succeed-at-project-
governance.html [Accessed 29 May 2019].
https://www.cio.com/article/2693222/how-to-succeed-at-project-governance.html
Summary:
This resources was very much important to understand project governance in an
organized manner. The resource highlighted that project governance plan can be
very much important to manage complex project. This resource also provided
information about the use of project governance in most of the global IT
establishments. The main reason behind selecting this resource is the reliability of
the data. This resource have numerous sections and each of the section is very
much important to understand different aspect of project governance such as the
limitations as well as the implementation of the project management strategies. The
key information of this resource is the risk management ability of project governance.
The robust process associated with most of the project governance can also be
identified from this resource. The main point of discussion of this resources is the
advantages of project governance such as the problem solving ability and the
disadvantages in terms of the more financial backup required for the implementation
of project governance. This resource was also very much useful to understand the
benefits well as the drawback of project governance in a detailed manner so that
accountability of the stakeholders and transparency of the business is maintained on
a long term basis.
11
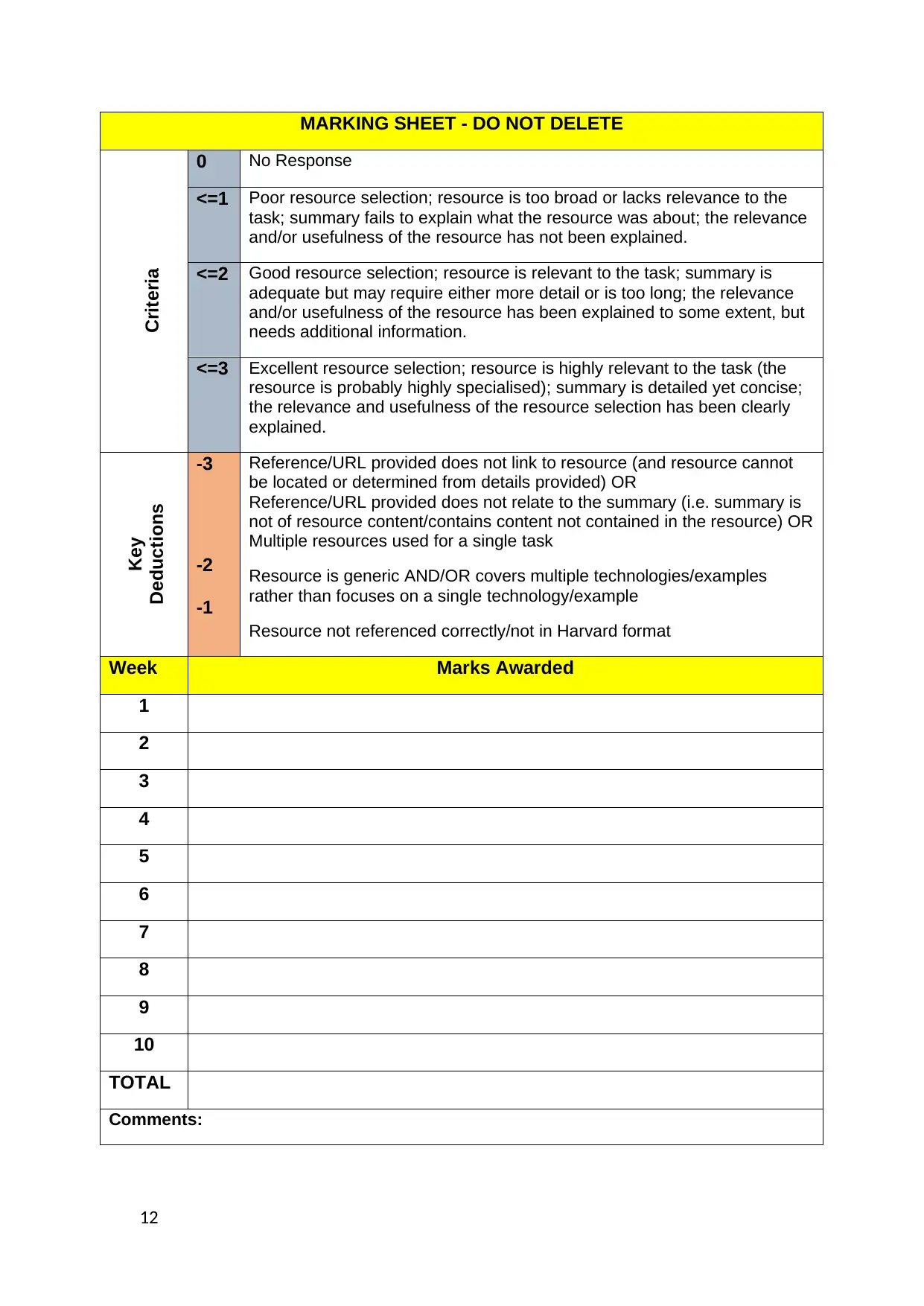
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
12
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


