Network Security: Implementing Security Technology Controls Project
VerifiedAdded on 2023/06/11
|9
|797
|371
Project
AI Summary
This network security project focuses on implementing security technology controls to enhance an organization's security posture. The project assesses existing network security plans and proposes upgrades, specifically using firewall controls for improved security and reliability. It details the objectives of firewall control, resources used (routers, switches, proxy servers, etc.), and the development techniques, including circuit-level gateways and proxy servers. The project also includes a system description, block diagram, and step-by-step configuration of Windows Firewall. A test plan verifies the firewall's effectiveness in blocking harmful information. The conclusion highlights the successful implementation and analysis of firewall controls to provide a robust security plan. Desklib provides students access to similar solved assignments.

NETWORK SECURITY PROJECT-SECURITY TECHNOLOGY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1 Introduction..............................................................................................................................3
2 Controls....................................................................................................................................3
2.1 Objective of Control..........................................................................................................3
2.2 Resources Used.................................................................................................................3
2.3 Developing the Control.....................................................................................................4
2.4 System Description...........................................................................................................4
2.5 Block Diagram..................................................................................................................4
2.6 System Configuration.......................................................................................................5
2.7 Test plan............................................................................................................................7
3 Conclusion................................................................................................................................8
References........................................................................................................................................9
2
1 Introduction..............................................................................................................................3
2 Controls....................................................................................................................................3
2.1 Objective of Control..........................................................................................................3
2.2 Resources Used.................................................................................................................3
2.3 Developing the Control.....................................................................................................4
2.4 System Description...........................................................................................................4
2.5 Block Diagram..................................................................................................................4
2.6 System Configuration.......................................................................................................5
2.7 Test plan............................................................................................................................7
3 Conclusion................................................................................................................................8
References........................................................................................................................................9
2

1 Introduction
This project is implemented the security technology controls and its strategies to provide
the effective security plan for an organization. The organization uses the network security plan
and it does not provide the security. So, the organization is decided to upgrade the security plan
to provide the high security and reliability for an organization. The proposed network security
plan uses the firewall control to provide the effective security for an organization. Here, we will
analysis the firewall controls and it strategies and implementation. These are needs to be
discussed in detail.
2 Controls
The organization proposed security plan use the firewall controls. The firewall is most
popular security tool and it used to provide the high security for an organization. The medium
sized organizations are mostly use the firewall controls to secure an organization.
2.1 Objective of Control
The firewall control is used to provide the network security and it designed to protect the
usability and integrity of the organization data and its networks. The firewall also effectively
manages the network access to provide the secure network for an organization. It targets variety
of threats from spreading and entering on the network. The firewall controls is used to implement
the security control and policies. It put up a barrier between the trusted internal network and un-
trusted outside network such as internet. It defines the rules to allow or block the network traffic.
The Cisco firewall is used to provide the unified threat management devices and thread focused
next generation firewalls.
2.2 Resources Used
The firewall control resources are listed below.
Routers
Switches
Proxy Server
TCP and UDP ports
Intrusion Detection System
Internet connection sharing and gateway
3
This project is implemented the security technology controls and its strategies to provide
the effective security plan for an organization. The organization uses the network security plan
and it does not provide the security. So, the organization is decided to upgrade the security plan
to provide the high security and reliability for an organization. The proposed network security
plan uses the firewall control to provide the effective security for an organization. Here, we will
analysis the firewall controls and it strategies and implementation. These are needs to be
discussed in detail.
2 Controls
The organization proposed security plan use the firewall controls. The firewall is most
popular security tool and it used to provide the high security for an organization. The medium
sized organizations are mostly use the firewall controls to secure an organization.
2.1 Objective of Control
The firewall control is used to provide the network security and it designed to protect the
usability and integrity of the organization data and its networks. The firewall also effectively
manages the network access to provide the secure network for an organization. It targets variety
of threats from spreading and entering on the network. The firewall controls is used to implement
the security control and policies. It put up a barrier between the trusted internal network and un-
trusted outside network such as internet. It defines the rules to allow or block the network traffic.
The Cisco firewall is used to provide the unified threat management devices and thread focused
next generation firewalls.
2.2 Resources Used
The firewall control resources are listed below.
Routers
Switches
Proxy Server
TCP and UDP ports
Intrusion Detection System
Internet connection sharing and gateway
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
2.3 Developing the Control
The development of the firewall control is used to protect the organization networks by filters
the all information coming through the internet to network or computer system. The firewall
control development uses the following techniques to prevent the potentially harmful
information. These are,
Circuit level gateway
Application Gateway
Proxy server
Packet filter
2.4 System Description
The firewall control is used to prevent the unauthorized access from private network. IT
can be implemented as both software and hardware. It frequently used to prevent the
unauthorized internet users from accessing the private networks connect to the internet. It is ideal
configuration for both hardware and software. It has the limiting access to the computer system
and network.
2.5 Block Diagram
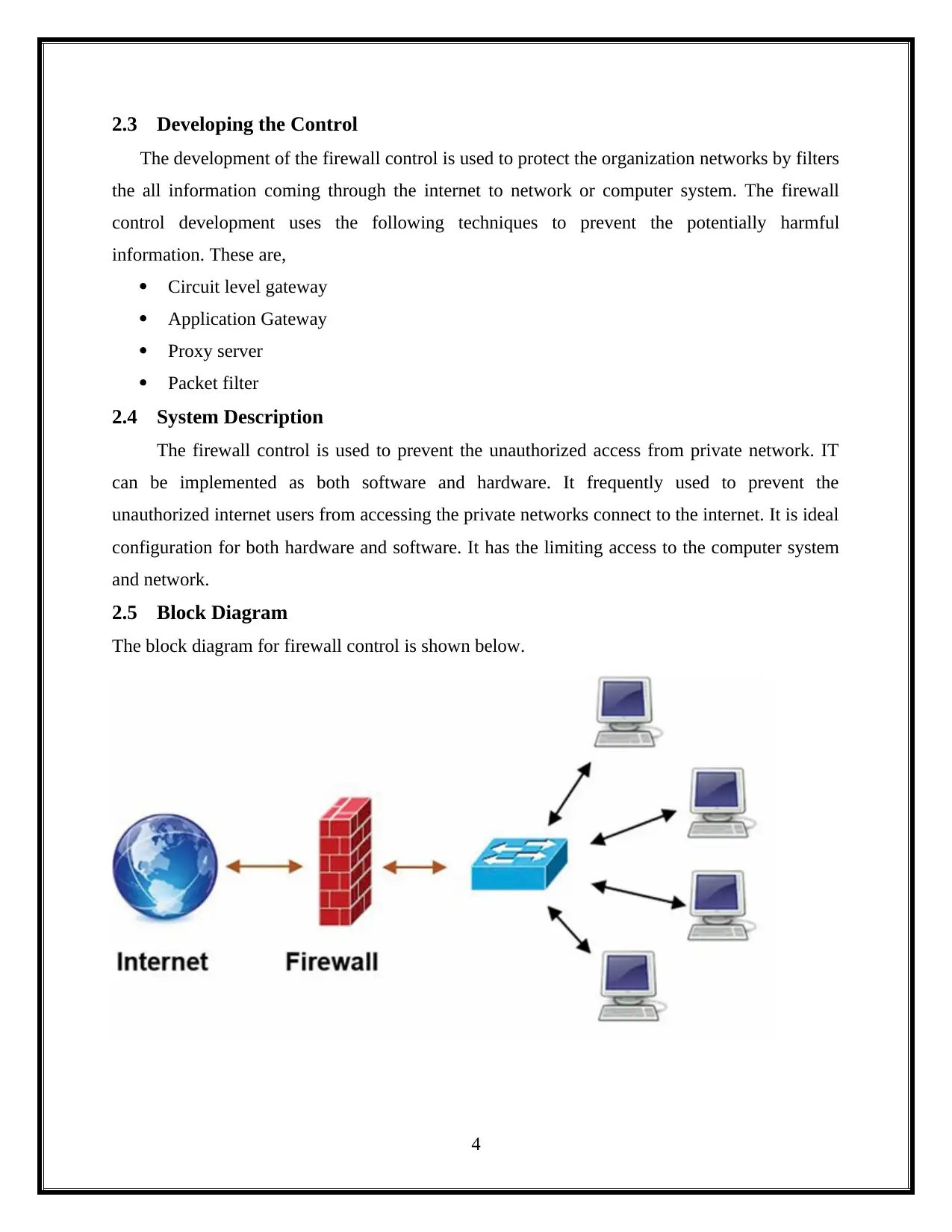
The block diagram for firewall control is shown below.
4
The development of the firewall control is used to protect the organization networks by filters
the all information coming through the internet to network or computer system. The firewall
control development uses the following techniques to prevent the potentially harmful
information. These are,
Circuit level gateway
Application Gateway
Proxy server
Packet filter
2.4 System Description
The firewall control is used to prevent the unauthorized access from private network. IT
can be implemented as both software and hardware. It frequently used to prevent the
unauthorized internet users from accessing the private networks connect to the internet. It is ideal
configuration for both hardware and software. It has the limiting access to the computer system
and network.
2.5 Block Diagram
The block diagram for firewall control is shown below.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2.6 System Configuration
Configure the window firewall on the computer system by following the below steps.
Click the start and choose the control panel. It is shown below.
In control panel, select the security center. It is shown below.
5
Configure the window firewall on the computer system by following the below steps.
Click the start and choose the control panel. It is shown below.
In control panel, select the security center. It is shown below.
5
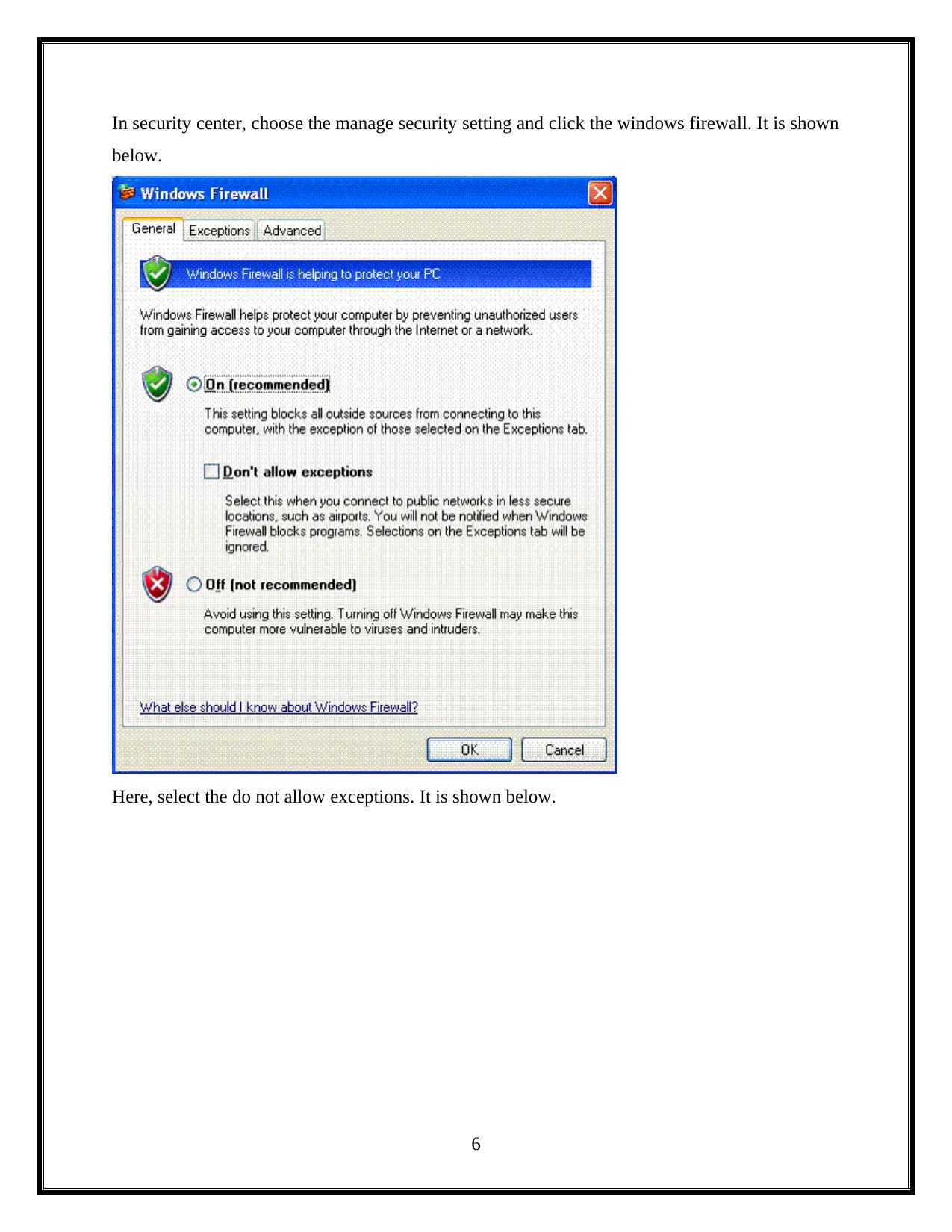
In security center, choose the manage security setting and click the windows firewall. It is shown
below.
Here, select the do not allow exceptions. It is shown below.
6
below.
Here, select the do not allow exceptions. It is shown below.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
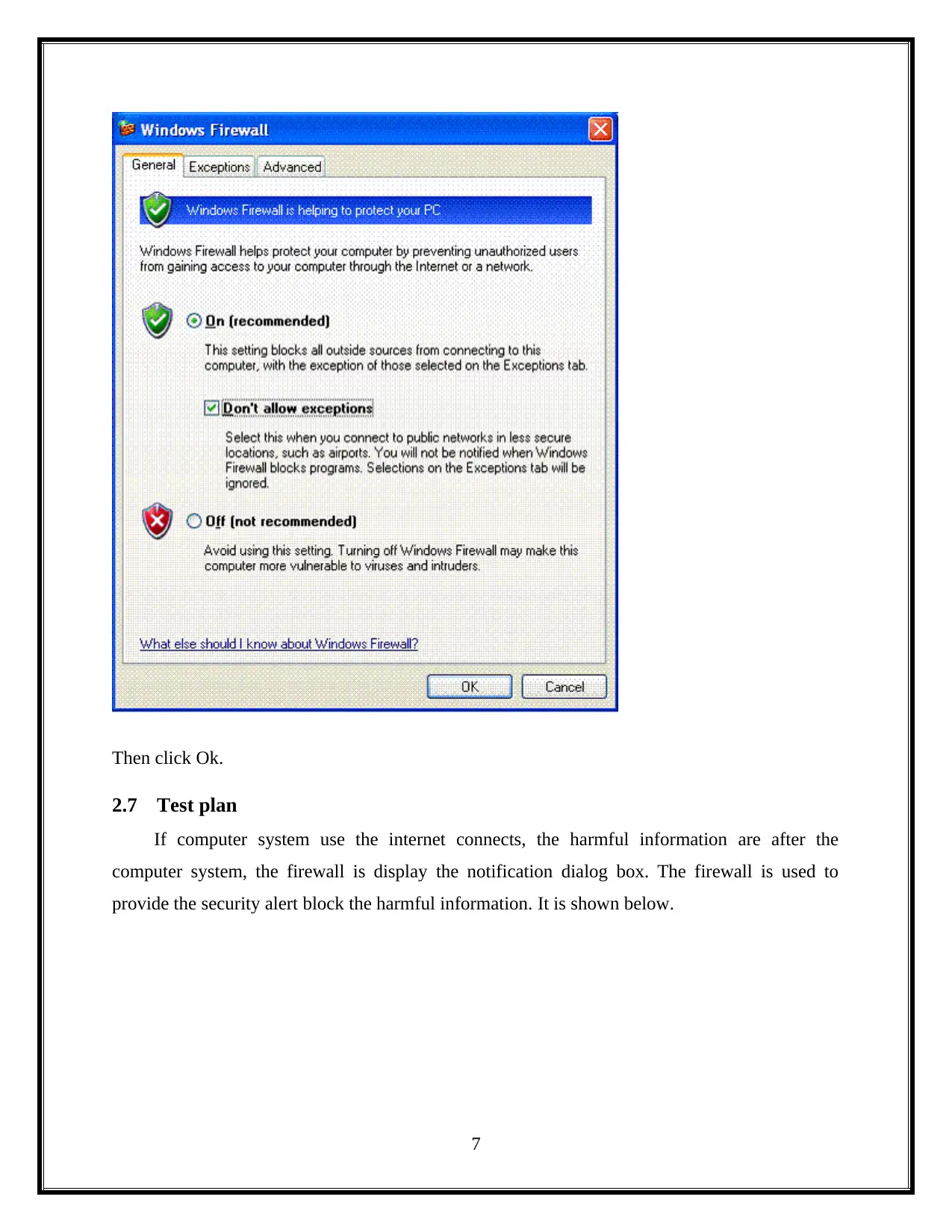
Then click Ok.
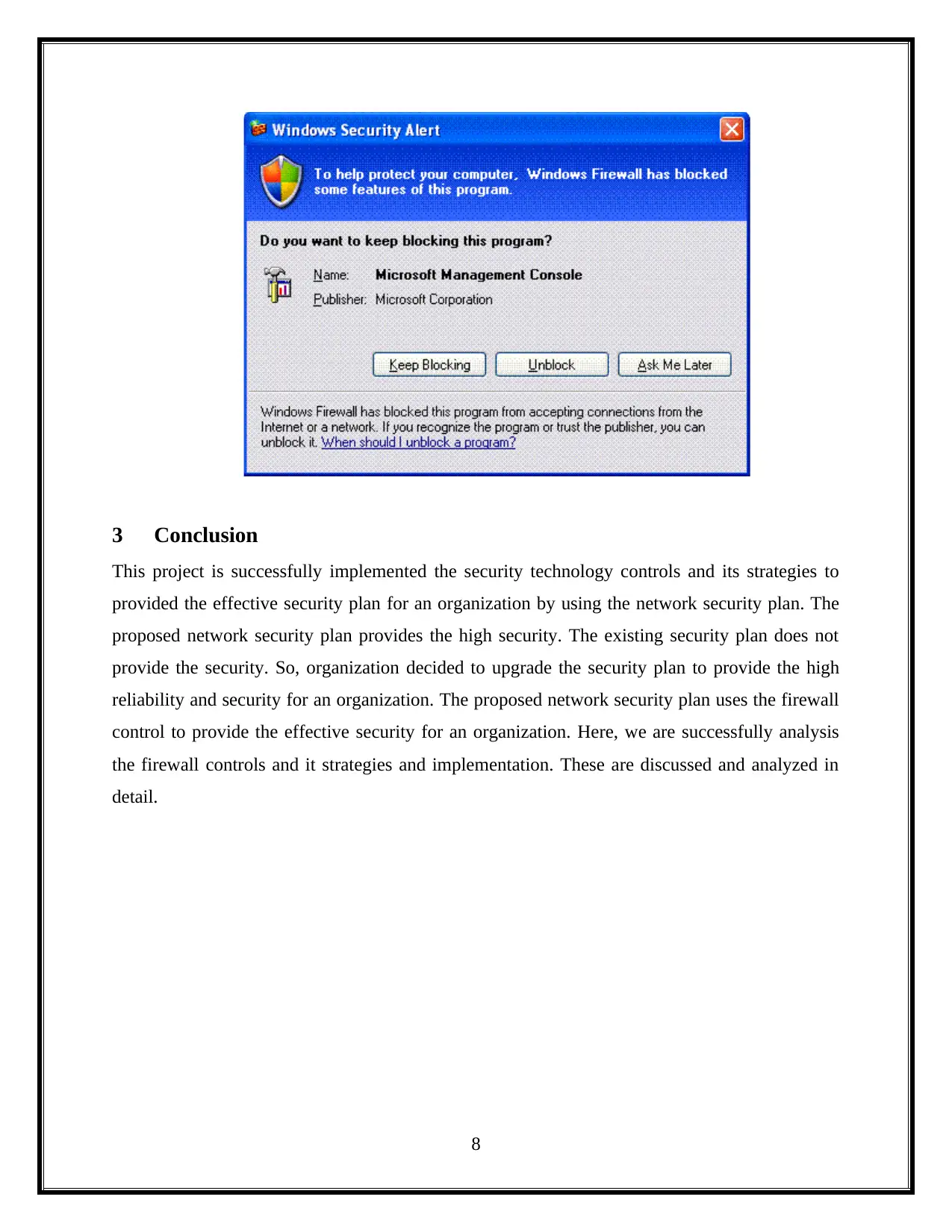
2.7 Test plan
If computer system use the internet connects, the harmful information are after the
computer system, the firewall is display the notification dialog box. The firewall is used to
provide the security alert block the harmful information. It is shown below.
7
2.7 Test plan
If computer system use the internet connects, the harmful information are after the
computer system, the firewall is display the notification dialog box. The firewall is used to
provide the security alert block the harmful information. It is shown below.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3 Conclusion
This project is successfully implemented the security technology controls and its strategies to
provided the effective security plan for an organization by using the network security plan. The
proposed network security plan provides the high security. The existing security plan does not
provide the security. So, organization decided to upgrade the security plan to provide the high
reliability and security for an organization. The proposed network security plan uses the firewall
control to provide the effective security for an organization. Here, we are successfully analysis
the firewall controls and it strategies and implementation. These are discussed and analyzed in
detail.
8
This project is successfully implemented the security technology controls and its strategies to
provided the effective security plan for an organization by using the network security plan. The
proposed network security plan provides the high security. The existing security plan does not
provide the security. So, organization decided to upgrade the security plan to provide the high
reliability and security for an organization. The proposed network security plan uses the firewall
control to provide the effective security for an organization. Here, we are successfully analysis
the firewall controls and it strategies and implementation. These are discussed and analyzed in
detail.
8

References
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
Lin, D., Tsudik, G. and Wang, X. (2011). Cryptology and network security. Berlin: Springer.
9
Hallberg, B. (2013). Networking. New York: McGraw-Hill Publishing.
Lin, D., Tsudik, G. and Wang, X. (2011). Cryptology and network security. Berlin: Springer.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





