Analyzing Network Security Threats: Reconnaissance to DoS Attacks
VerifiedAdded on 2020/10/22
|28
|4059
|293
AI Summary
This assignment delves into various aspects of network security, focusing on current threats like reconnaissance attacks in IPv6 networks, techniques for detecting IP spoofing, and strategies to mitigate Distributed Denial-of-Service (DDoS) attacks. It aims to provide a comprehensive understanding of these challenges by reviewing existing literature and analyzing case studies. Students will explore different attack vectors, understand their impact on network infrastructure, and evaluate the effectiveness of current defense mechanisms. The study emphasizes the importance of evolving cybersecurity strategies in response to new threats, with an emphasis on innovative solutions for protecting digital assets. Through this analysis, students are expected to gain a deeper insight into the complexities of maintaining network security in an increasingly interconnected world.

ICT 811
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
TRACE 1.........................................................................................................................................1
HTTP Trace.................................................................................................................................1
Sites visited.................................................................................................................................1
We searched for...........................................................................................................................1
List of IP addresses of sites visited.............................................................................................3
Trace 2.............................................................................................................................................3
HTTPS Trace..............................................................................................................................3
Certificate issuing authority........................................................................................................4
Encryption algorithm..................................................................................................................4
Key and size of key used in encryption......................................................................................4
Expiration date and time on the issued certificate......................................................................4
Complete cipher suite supported by browser..............................................................................4
Cipher suite supported by server.................................................................................................4
Trace 3.............................................................................................................................................5
FTP Trace....................................................................................................................................5
Login name and password used for connecting to FTP server...................................................5
Difference between active and passive FTP...............................................................................5
What files were downloaded. What is their download path and size?......................................11
TRACE 4.......................................................................................................................................11
Trace route tool.........................................................................................................................11
IP addresses observed during trace routing between sender and receiver................................13
Trace 5...........................................................................................................................................13
POP3 Trace...............................................................................................................................13
Login name and password used................................................................................................13
Email details..............................................................................................................................13
TRACES 6, 7, 8 & 9......................................................................................................................16
Networking attacks....................................................................................................................16
Target domain in network attacks:............................................................................................18
REFERENCES .............................................................................................................................20
TRACE 1.........................................................................................................................................1
HTTP Trace.................................................................................................................................1
Sites visited.................................................................................................................................1
We searched for...........................................................................................................................1
List of IP addresses of sites visited.............................................................................................3
Trace 2.............................................................................................................................................3
HTTPS Trace..............................................................................................................................3
Certificate issuing authority........................................................................................................4
Encryption algorithm..................................................................................................................4
Key and size of key used in encryption......................................................................................4
Expiration date and time on the issued certificate......................................................................4
Complete cipher suite supported by browser..............................................................................4
Cipher suite supported by server.................................................................................................4
Trace 3.............................................................................................................................................5
FTP Trace....................................................................................................................................5
Login name and password used for connecting to FTP server...................................................5
Difference between active and passive FTP...............................................................................5
What files were downloaded. What is their download path and size?......................................11
TRACE 4.......................................................................................................................................11
Trace route tool.........................................................................................................................11
IP addresses observed during trace routing between sender and receiver................................13
Trace 5...........................................................................................................................................13
POP3 Trace...............................................................................................................................13
Login name and password used................................................................................................13
Email details..............................................................................................................................13
TRACES 6, 7, 8 & 9......................................................................................................................16
Networking attacks....................................................................................................................16
Target domain in network attacks:............................................................................................18
REFERENCES .............................................................................................................................20
TRACE 1
HTTP Trace
A packet analyser is considered as any software or application that can be used to analyse
the packets over the network (Yan, Gong and Yu, 2017). Along with packets, it can also help in
logging the traffic that is being passed on the network. There are various ways that can be used
to analyse packets but the report involves the application of Wireshark for packet analysing
because there are some specialised features such as providing statistics of packets and also helps
in analysing the traffic over network.
There are a few ways of capturing data and some of these are discussed as under :
Sites visited
URL : www.booktopia.com.au
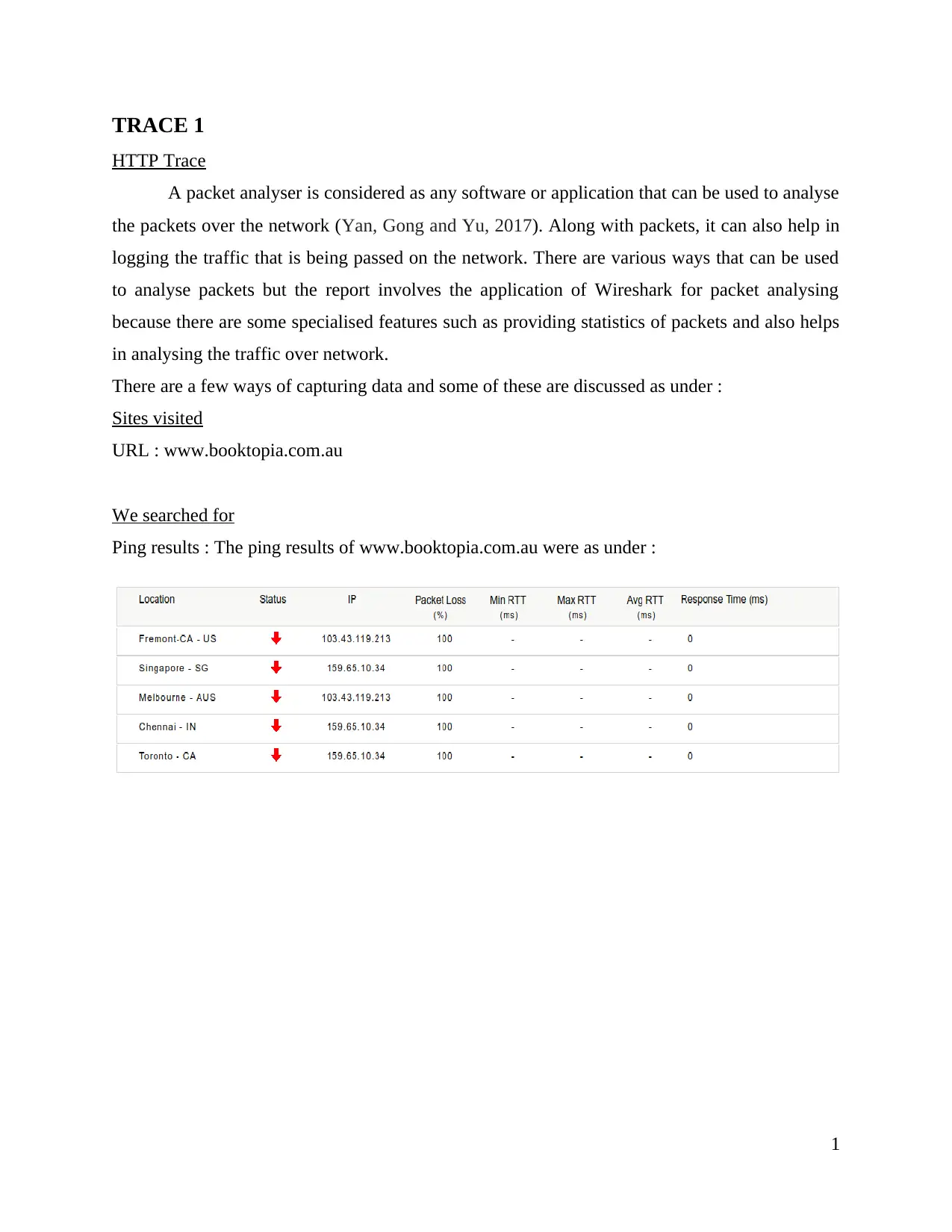
We searched for
Ping results : The ping results of www.booktopia.com.au were as under :
1
HTTP Trace
A packet analyser is considered as any software or application that can be used to analyse
the packets over the network (Yan, Gong and Yu, 2017). Along with packets, it can also help in
logging the traffic that is being passed on the network. There are various ways that can be used
to analyse packets but the report involves the application of Wireshark for packet analysing
because there are some specialised features such as providing statistics of packets and also helps
in analysing the traffic over network.
There are a few ways of capturing data and some of these are discussed as under :
Sites visited
URL : www.booktopia.com.au
We searched for
Ping results : The ping results of www.booktopia.com.au were as under :
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
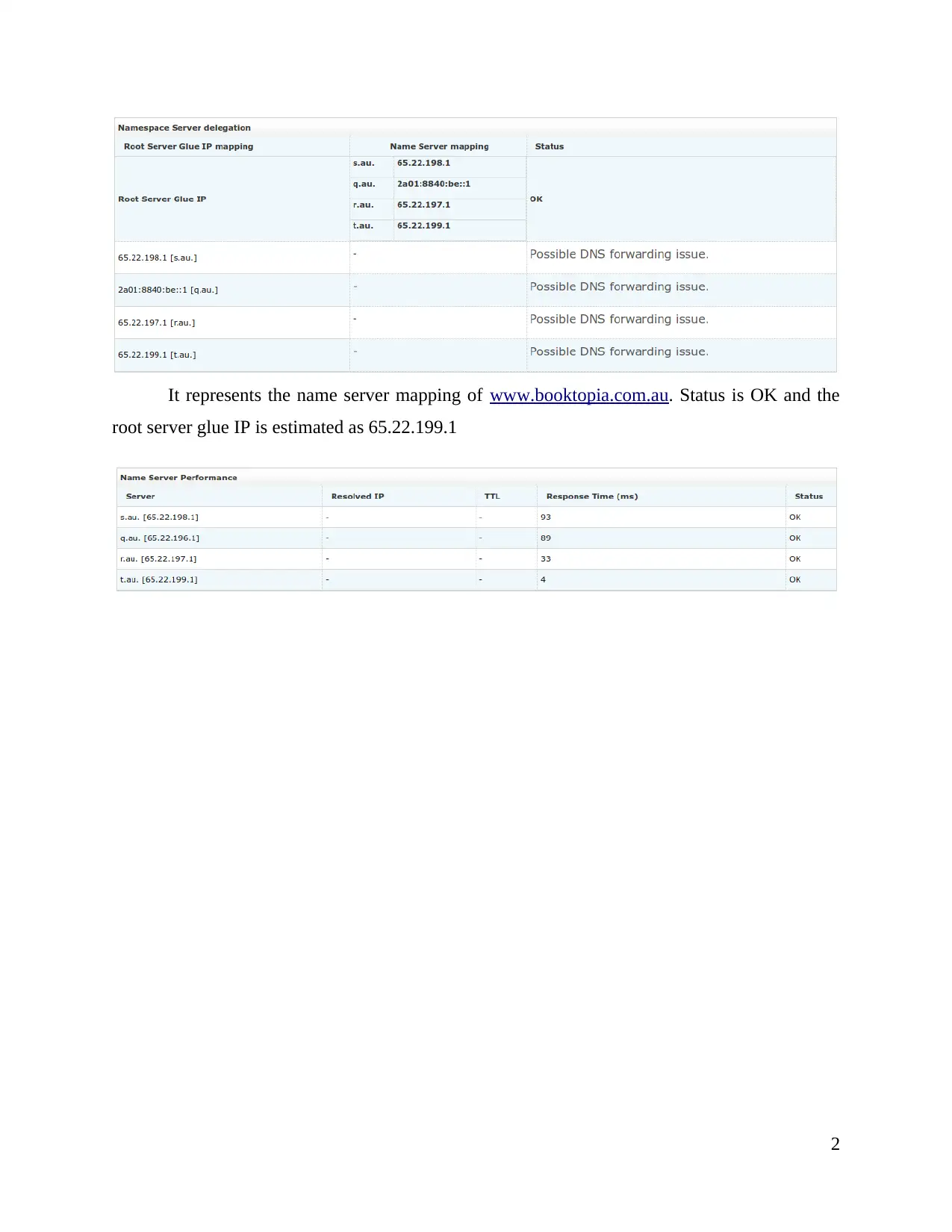
It represents the name server mapping of www.booktopia.com.au. Status is OK and the
root server glue IP is estimated as 65.22.199.1
2
root server glue IP is estimated as 65.22.199.1
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
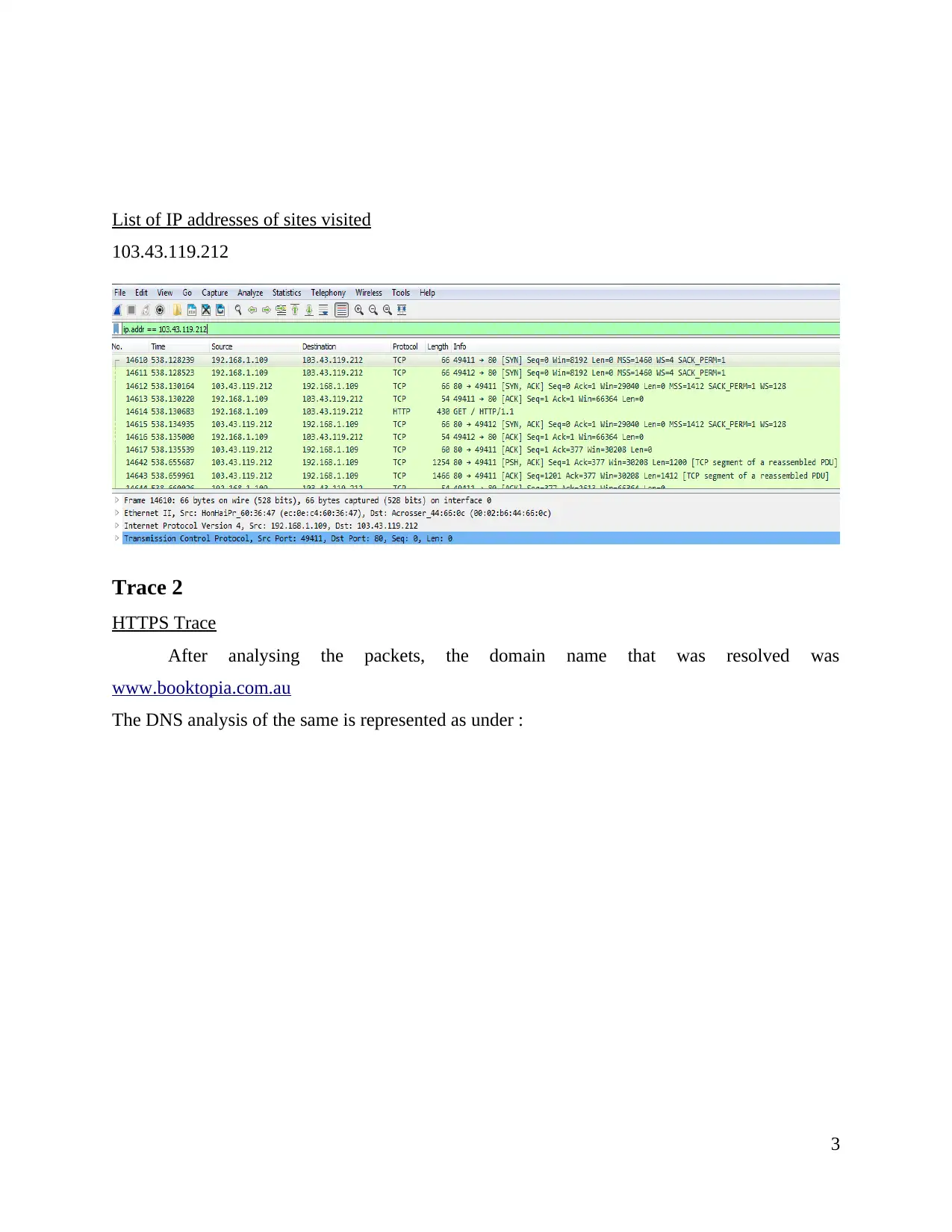
List of IP addresses of sites visited
103.43.119.212
Trace 2
HTTPS Trace
After analysing the packets, the domain name that was resolved was
www.booktopia.com.au
The DNS analysis of the same is represented as under :
3
103.43.119.212
Trace 2
HTTPS Trace
After analysing the packets, the domain name that was resolved was
www.booktopia.com.au
The DNS analysis of the same is represented as under :
3
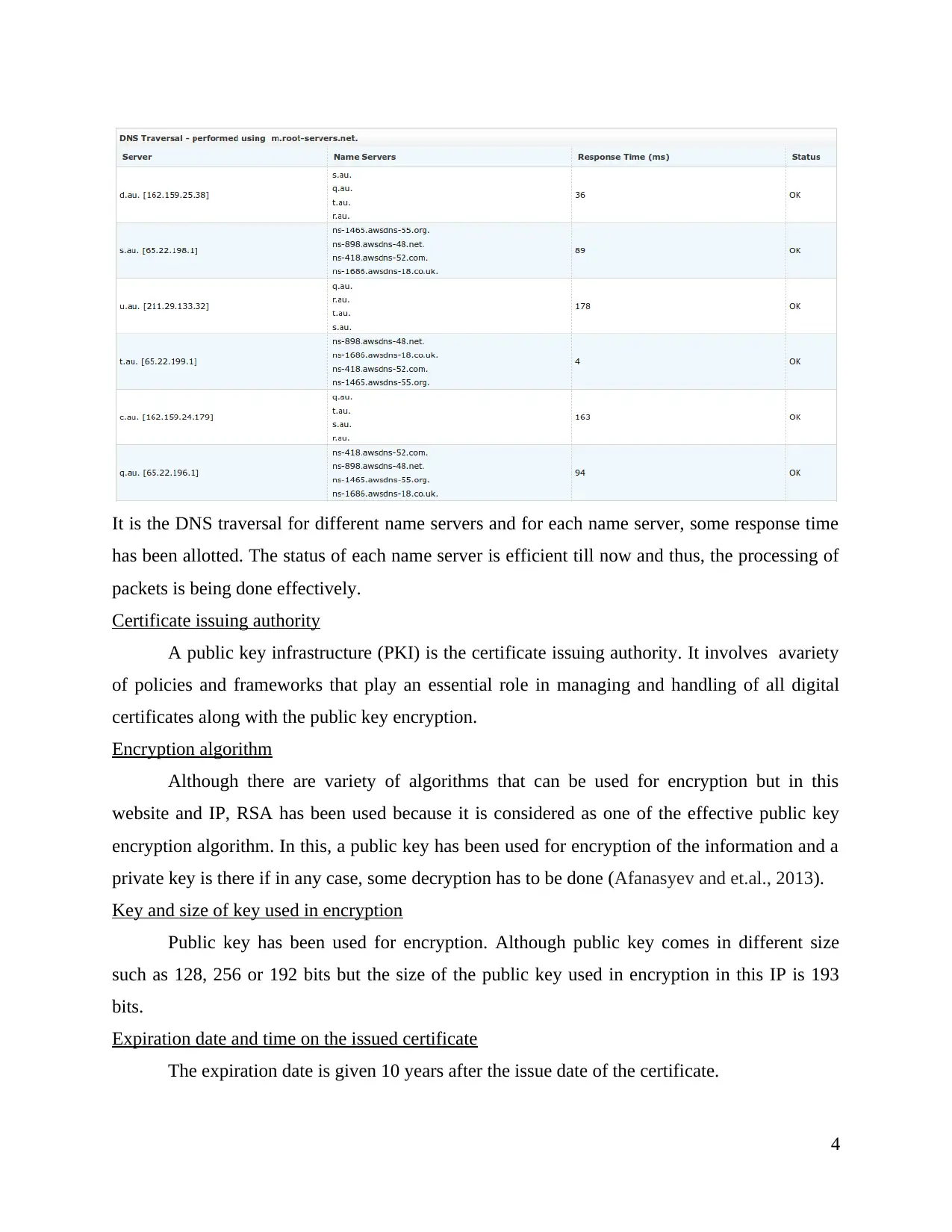
It is the DNS traversal for different name servers and for each name server, some response time
has been allotted. The status of each name server is efficient till now and thus, the processing of
packets is being done effectively.
Certificate issuing authority
A public key infrastructure (PKI) is the certificate issuing authority. It involves avariety
of policies and frameworks that play an essential role in managing and handling of all digital
certificates along with the public key encryption.
Encryption algorithm
Although there are variety of algorithms that can be used for encryption but in this
website and IP, RSA has been used because it is considered as one of the effective public key
encryption algorithm. In this, a public key has been used for encryption of the information and a
private key is there if in any case, some decryption has to be done (Afanasyev and et.al., 2013).
Key and size of key used in encryption
Public key has been used for encryption. Although public key comes in different size
such as 128, 256 or 192 bits but the size of the public key used in encryption in this IP is 193
bits.
Expiration date and time on the issued certificate
The expiration date is given 10 years after the issue date of the certificate.
4
has been allotted. The status of each name server is efficient till now and thus, the processing of
packets is being done effectively.
Certificate issuing authority
A public key infrastructure (PKI) is the certificate issuing authority. It involves avariety
of policies and frameworks that play an essential role in managing and handling of all digital
certificates along with the public key encryption.
Encryption algorithm
Although there are variety of algorithms that can be used for encryption but in this
website and IP, RSA has been used because it is considered as one of the effective public key
encryption algorithm. In this, a public key has been used for encryption of the information and a
private key is there if in any case, some decryption has to be done (Afanasyev and et.al., 2013).
Key and size of key used in encryption
Public key has been used for encryption. Although public key comes in different size
such as 128, 256 or 192 bits but the size of the public key used in encryption in this IP is 193
bits.
Expiration date and time on the issued certificate
The expiration date is given 10 years after the issue date of the certificate.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Complete cipher suite supported by browser
There are enormous number of cipher suites that are supported by browsers but the one
that is being used by this IP address is AES CBC 256 bit. It can also be considered that this is
supported in various browsers as well. Some well known and popular examples of browsers
include Chrome, Mozilla etc. and the cipher suite of this website is compatible in both of these
browsers. So, the customers can easily access the website of www.booktopia.com.au .
Cipher suite supported by server
The transport layer security (TLS) and Secure socket layer (SSL) is considered as the
cipher suites that have been used in www.booktopia.com.au . There are different algorithms
involved in this cipher suite. Some algorithms that have been involved are bulk encryption
algorithm, key exchange algorithm and message authentication code (MAC).
Trace 3
FTP Trace
File transfer protocol is considered as a standard protocol of network that helps in
completing the sharing of files and information between a server and a client. Along with
exchange of information and files between client and server, it also helps in providing an access
to the archive files of the software.
Login name and password used for connecting to FTP server
As it is quite similar to connect to FTP server as it is just like connecting to any website
generally over the internet. So, the login name and password that was used while connecting to
the ftp server like media fire was as under :
IP of www.mediafire.com : 104.19.195.29
Login name :Mymedia123
Password : 12@453**12
Difference between active and passive FTP
The active and passive ftp connections in the trace are represented as below :
5
There are enormous number of cipher suites that are supported by browsers but the one
that is being used by this IP address is AES CBC 256 bit. It can also be considered that this is
supported in various browsers as well. Some well known and popular examples of browsers
include Chrome, Mozilla etc. and the cipher suite of this website is compatible in both of these
browsers. So, the customers can easily access the website of www.booktopia.com.au .
Cipher suite supported by server
The transport layer security (TLS) and Secure socket layer (SSL) is considered as the
cipher suites that have been used in www.booktopia.com.au . There are different algorithms
involved in this cipher suite. Some algorithms that have been involved are bulk encryption
algorithm, key exchange algorithm and message authentication code (MAC).
Trace 3
FTP Trace
File transfer protocol is considered as a standard protocol of network that helps in
completing the sharing of files and information between a server and a client. Along with
exchange of information and files between client and server, it also helps in providing an access
to the archive files of the software.
Login name and password used for connecting to FTP server
As it is quite similar to connect to FTP server as it is just like connecting to any website
generally over the internet. So, the login name and password that was used while connecting to
the ftp server like media fire was as under :
IP of www.mediafire.com : 104.19.195.29
Login name :Mymedia123
Password : 12@453**12
Difference between active and passive FTP
The active and passive ftp connections in the trace are represented as below :
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
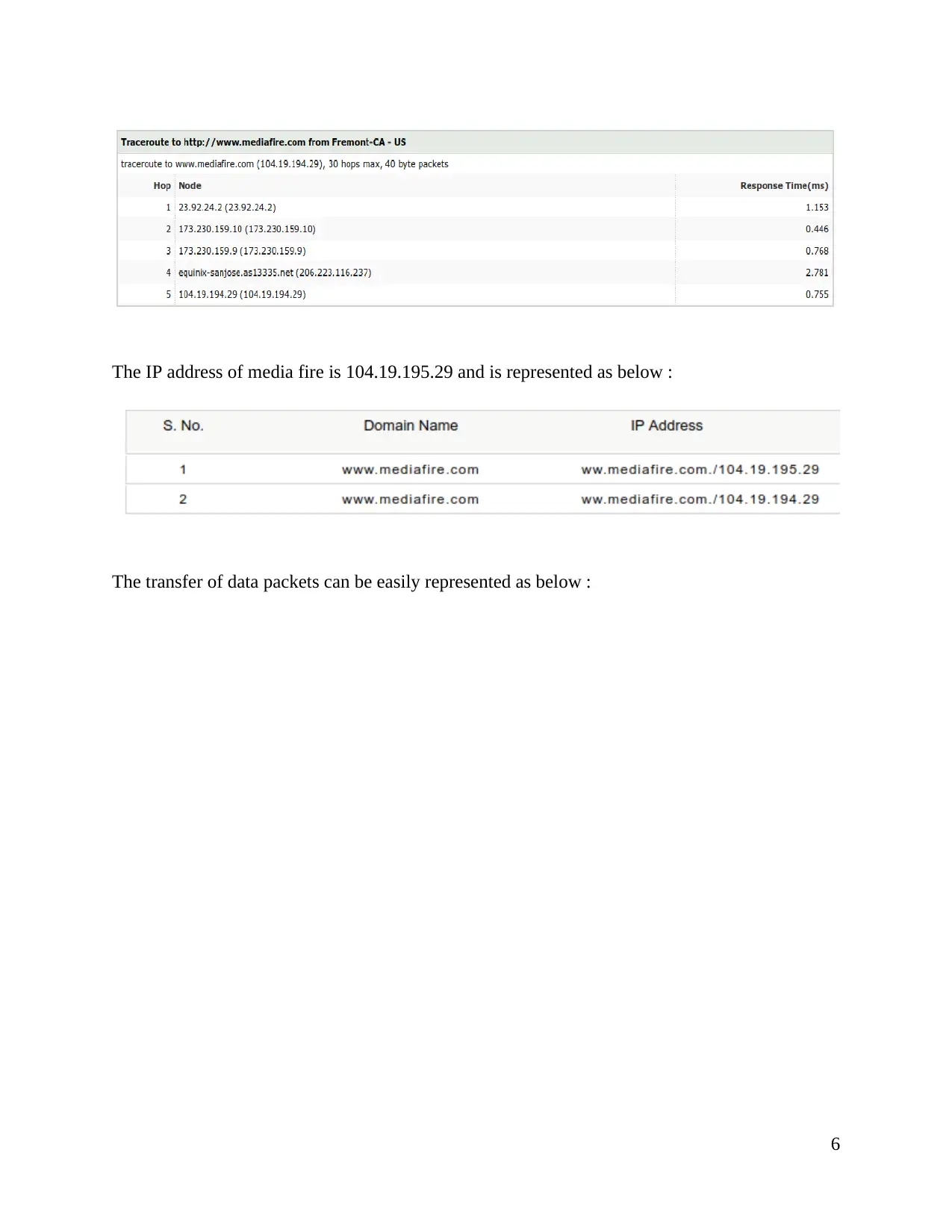
The IP address of media fire is 104.19.195.29 and is represented as below :
The transfer of data packets can be easily represented as below :
6
The transfer of data packets can be easily represented as below :
6
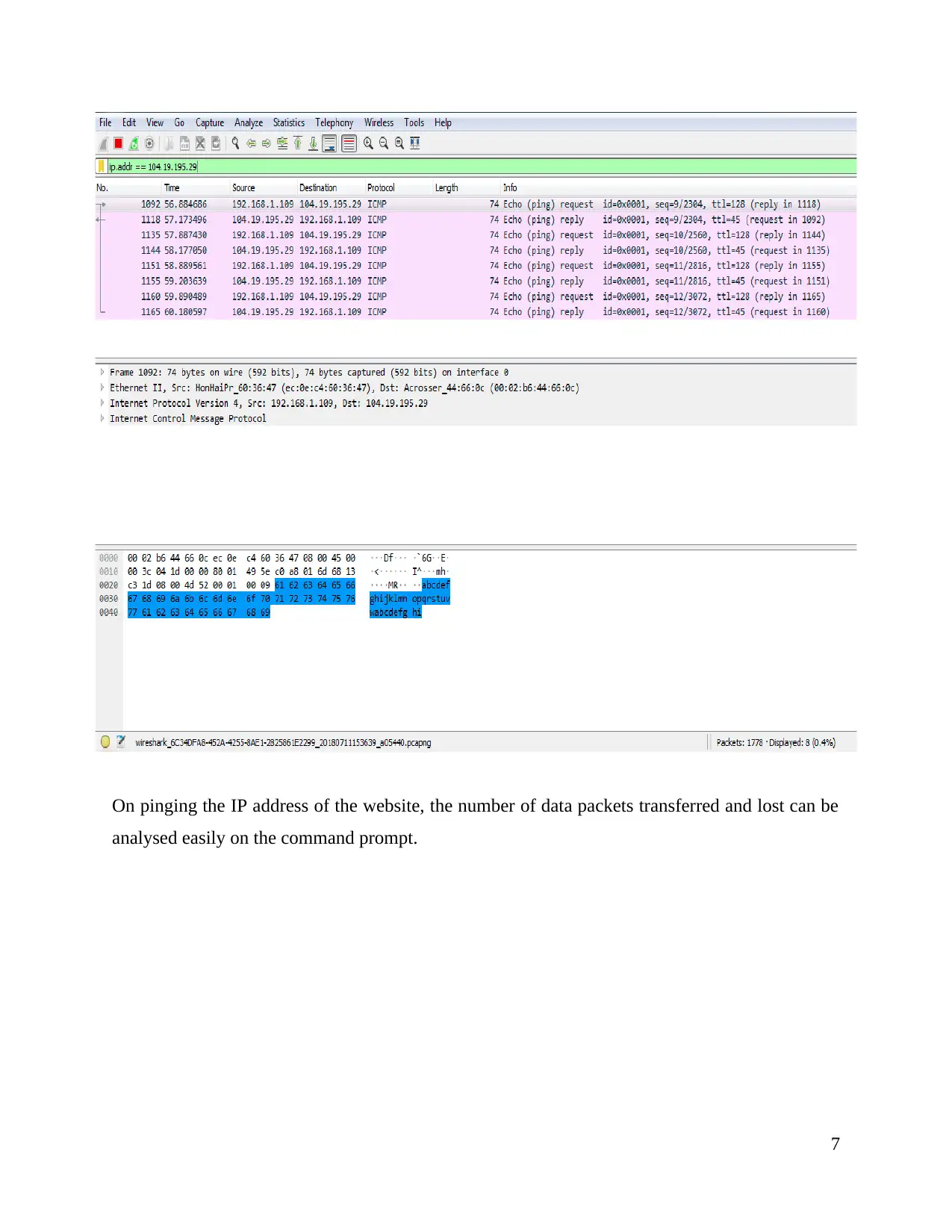
On pinging the IP address of the website, the number of data packets transferred and lost can be
analysed easily on the command prompt.
7
analysed easily on the command prompt.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
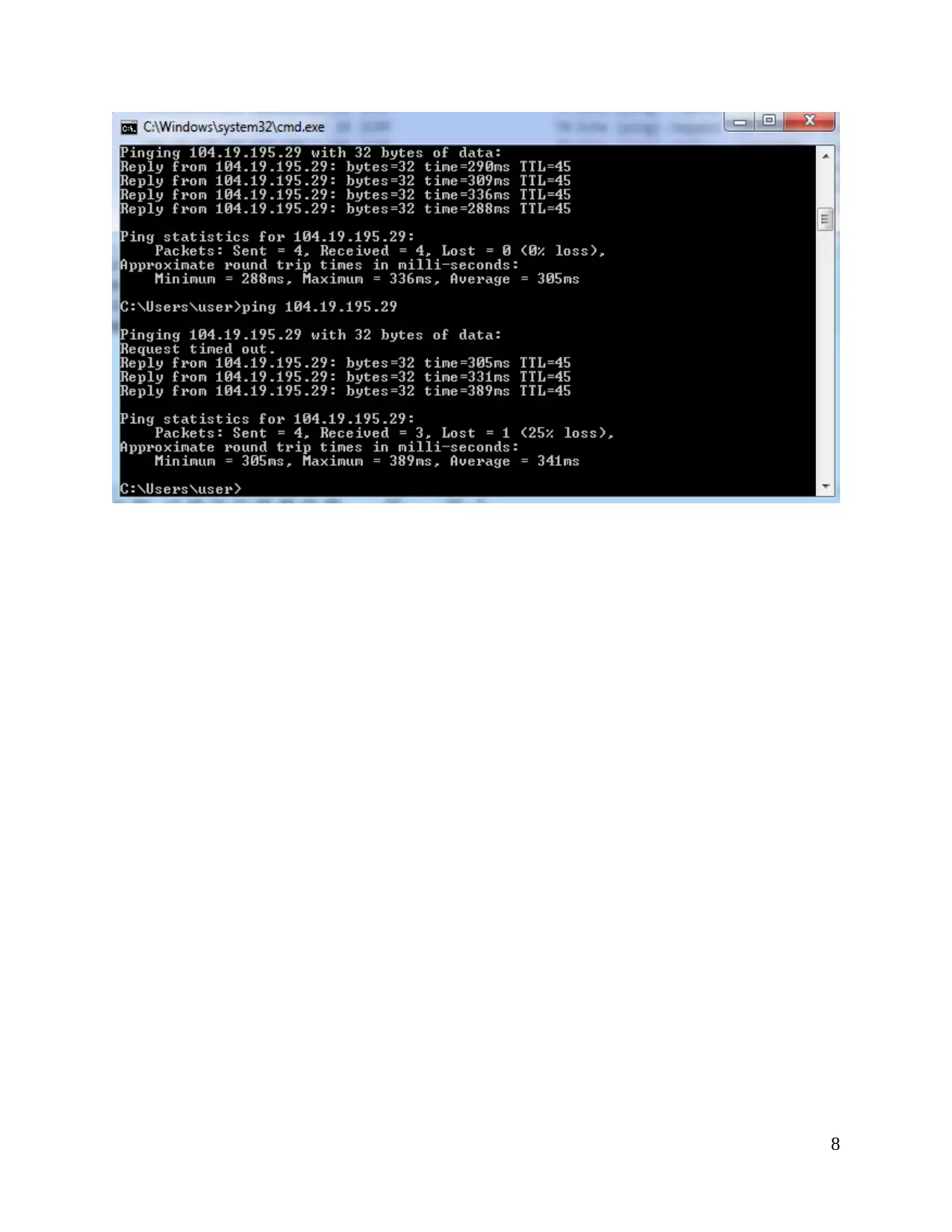
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
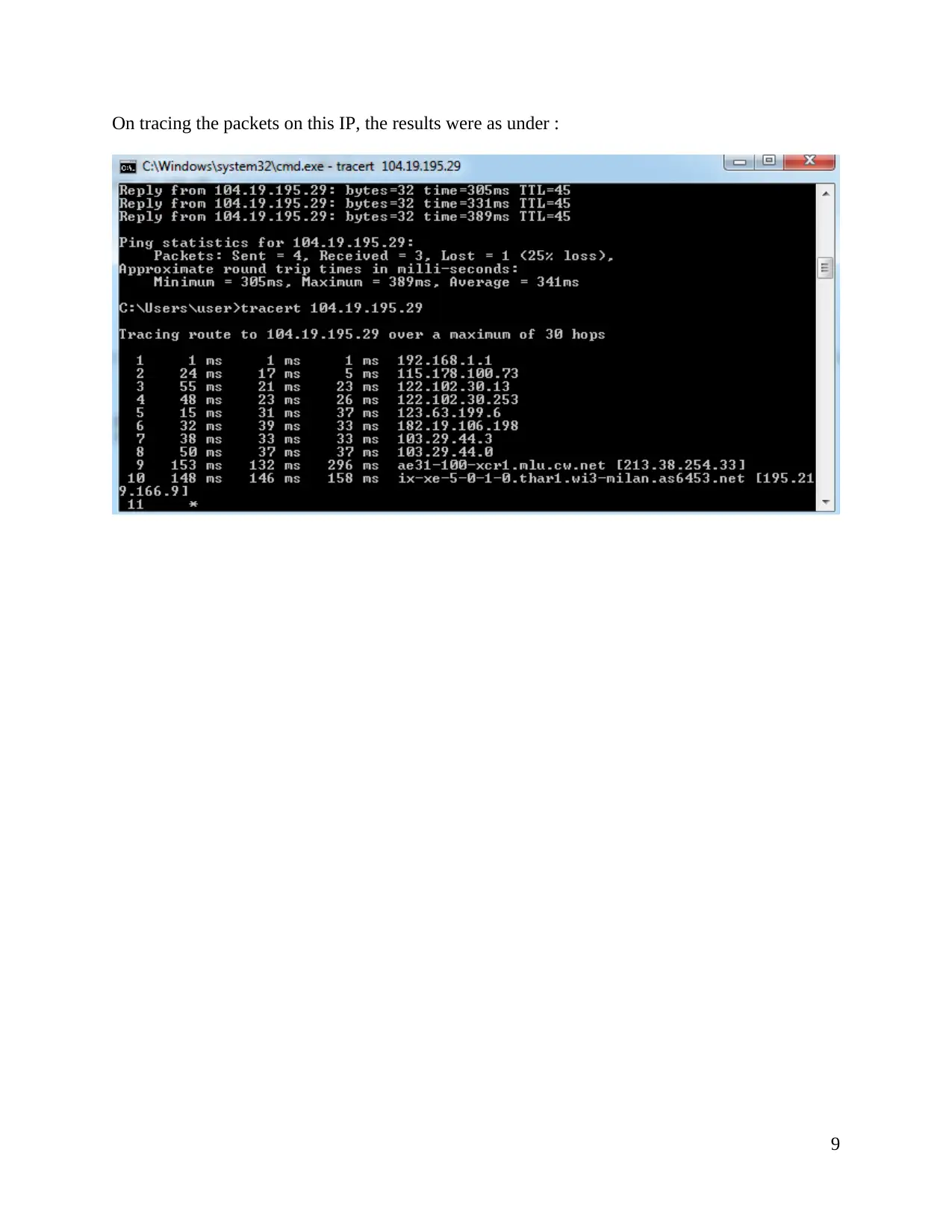
On tracing the packets on this IP, the results were as under :
9
9
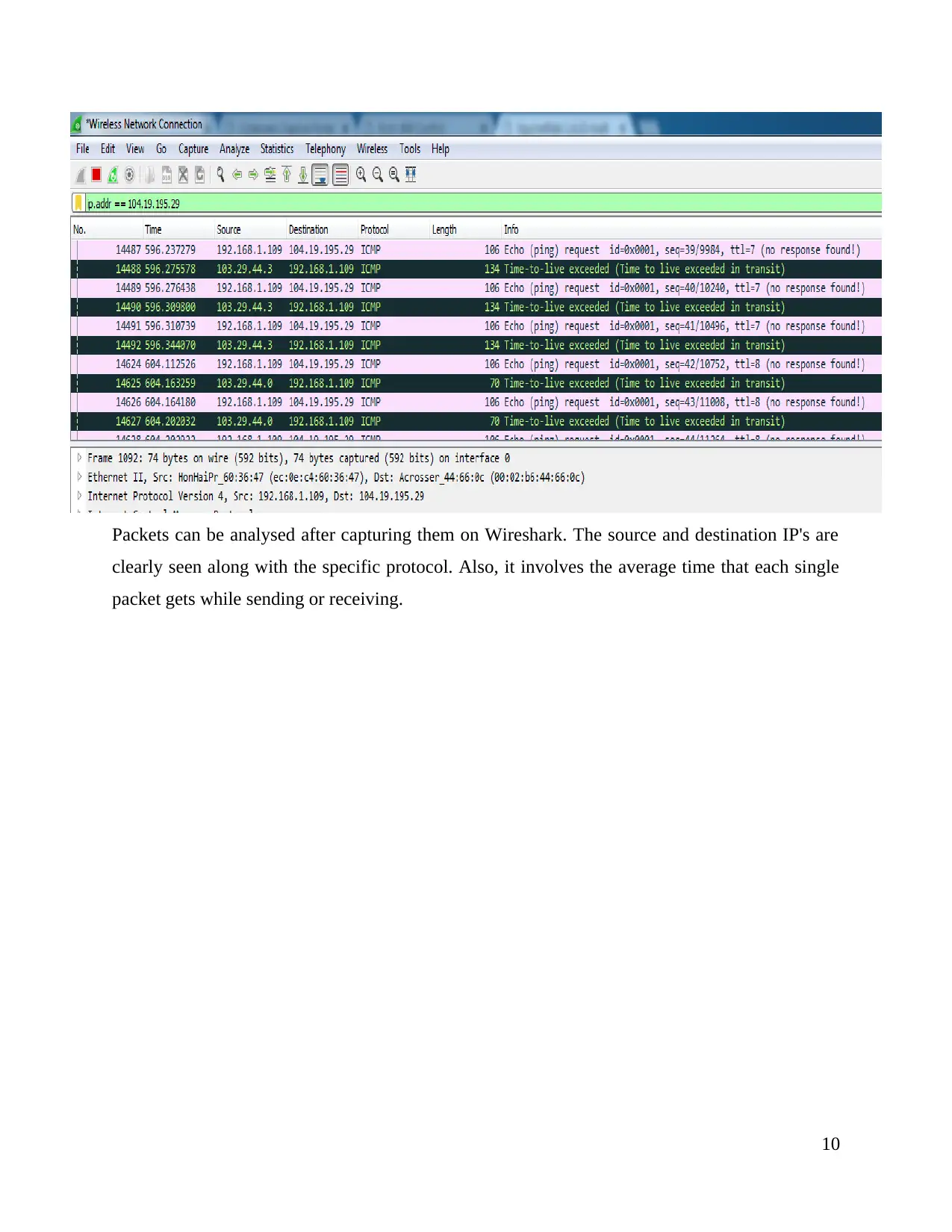
Packets can be analysed after capturing them on Wireshark. The source and destination IP's are
clearly seen along with the specific protocol. Also, it involves the average time that each single
packet gets while sending or receiving.
10
clearly seen along with the specific protocol. Also, it involves the average time that each single
packet gets while sending or receiving.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 28
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





