Network Security: Identifying Threats & Mitigation with Tools
VerifiedAdded on 2023/06/11
|8
|1849
|112
Report
AI Summary
This report explores the identification of network security threats using open-source network monitoring tools, Nmap and Metasploit. It details the process of scanning a local area network for vulnerabilities, discussing the types of threats identified, and outlining mitigation techniques. Nmap is used for port scanning and vulnerability testing, while Metasploit aids in payload identification and security auditing. The report also covers common attack types like Denial of Service (DoS) and Distributed Denial of Service (DDoS), social engineering, and malware, along with strategies for prevention and mitigation. It emphasizes the importance of firewall configuration, network segregation, web application security, system administration, and patch management in maintaining a secure network environment. The conclusion highlights the effectiveness of Nmap and Metasploit in identifying and exploiting system vulnerabilities, offering advanced penetration testing capabilities.

Running head: NETWORK SECURITY
Identifying Network Threats using Network Security Tools
Name of the Student
Name of the University
Author’s Note
Identifying Network Threats using Network Security Tools
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK SECURITY
Table of Contents
Introduction...........................................................................................................................................2
Literature Review..................................................................................................................................2
Network Security Tools..........................................................................................................................4
Threat Mitigation Techniques................................................................................................................5
Conclusion.............................................................................................................................................6
Bibliography...........................................................................................................................................7
NETWORK SECURITY
Table of Contents
Introduction...........................................................................................................................................2
Literature Review..................................................................................................................................2
Network Security Tools..........................................................................................................................4
Threat Mitigation Techniques................................................................................................................5
Conclusion.............................................................................................................................................6
Bibliography...........................................................................................................................................7
2
NETWORK SECURITY
Introduction
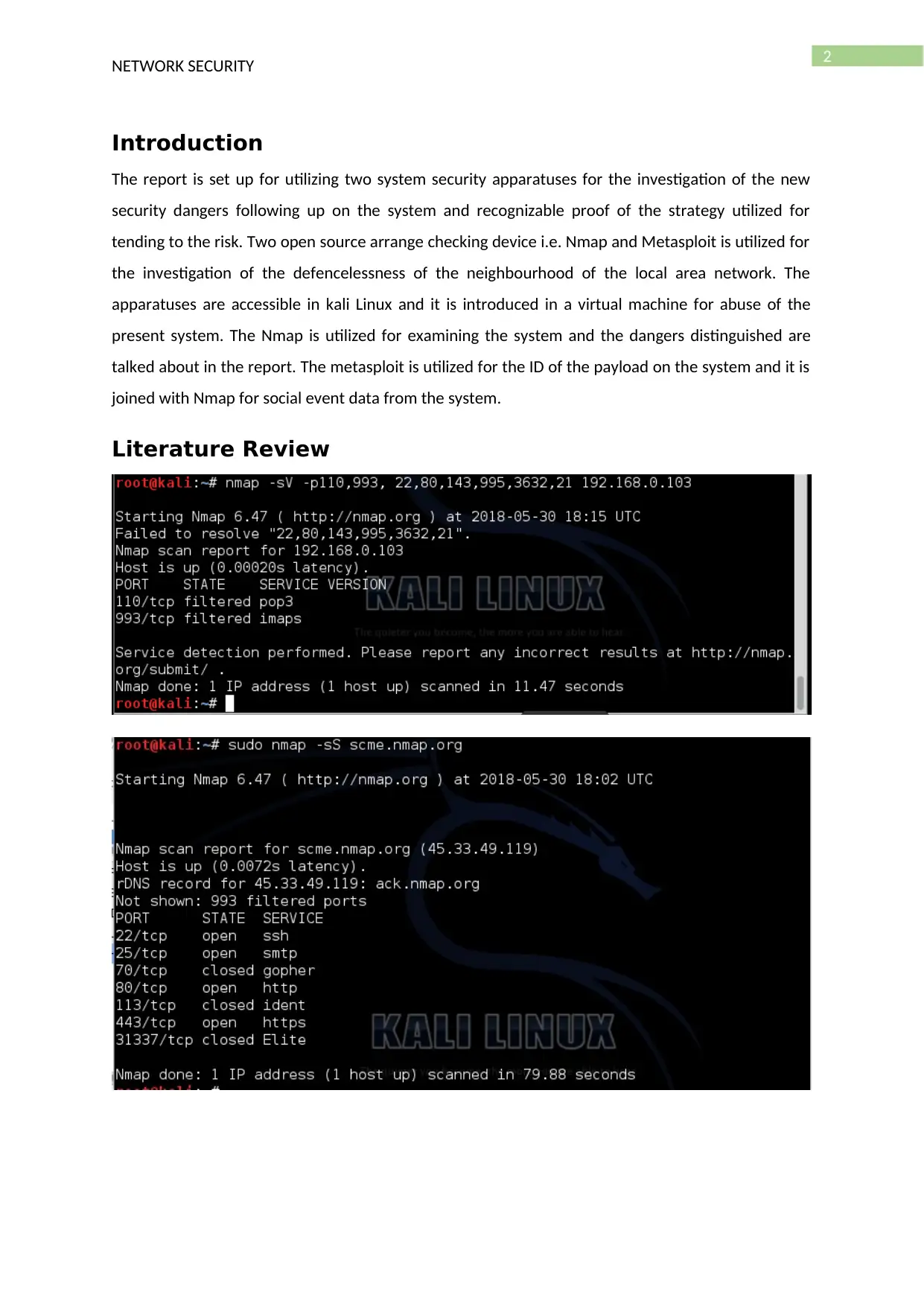
The report is set up for utilizing two system security apparatuses for the investigation of the new
security dangers following up on the system and recognizable proof of the strategy utilized for
tending to the risk. Two open source arrange checking device i.e. Nmap and Metasploit is utilized for
the investigation of the defencelessness of the neighbourhood of the local area network. The
apparatuses are accessible in kali Linux and it is introduced in a virtual machine for abuse of the
present system. The Nmap is utilized for examining the system and the dangers distinguished are
talked about in the report. The metasploit is utilized for the ID of the payload on the system and it is
joined with Nmap for social event data from the system.
Literature Review
NETWORK SECURITY
Introduction
The report is set up for utilizing two system security apparatuses for the investigation of the new
security dangers following up on the system and recognizable proof of the strategy utilized for
tending to the risk. Two open source arrange checking device i.e. Nmap and Metasploit is utilized for
the investigation of the defencelessness of the neighbourhood of the local area network. The
apparatuses are accessible in kali Linux and it is introduced in a virtual machine for abuse of the
present system. The Nmap is utilized for examining the system and the dangers distinguished are
talked about in the report. The metasploit is utilized for the ID of the payload on the system and it is
joined with Nmap for social event data from the system.
Literature Review
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK SECURITY
The nmap is utilized for finding the ports in a framework that are open and utilized for interfering
into the framework utilizing the open port for testing the powerlessness of the framework. The ports
can likewise be utilized for sending offbeat parcel and causing disavowal of administration assault.
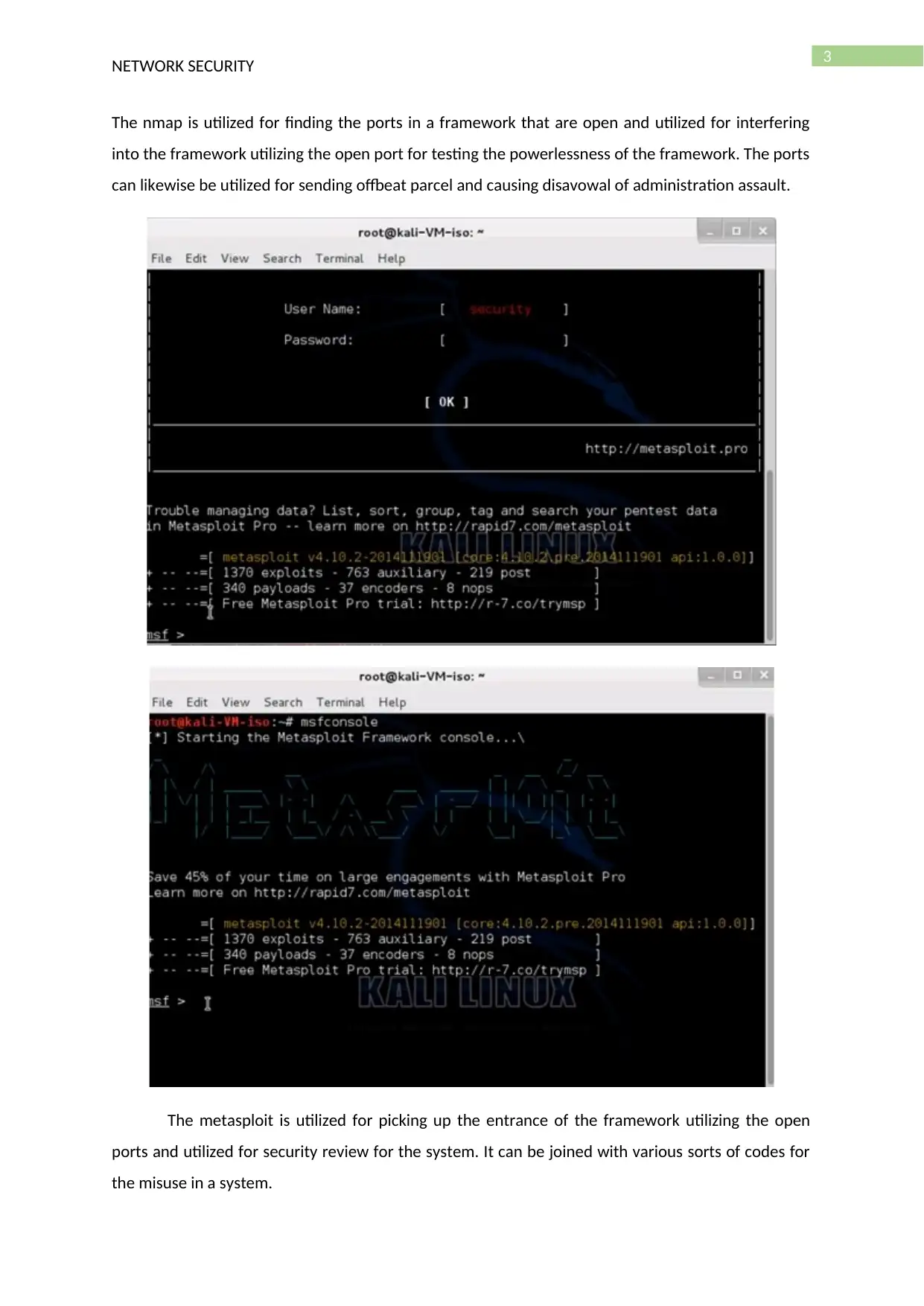
The metasploit is utilized for picking up the entrance of the framework utilizing the open
ports and utilized for security review for the system. It can be joined with various sorts of codes for
the misuse in a system.
NETWORK SECURITY
The nmap is utilized for finding the ports in a framework that are open and utilized for interfering
into the framework utilizing the open port for testing the powerlessness of the framework. The ports
can likewise be utilized for sending offbeat parcel and causing disavowal of administration assault.
The metasploit is utilized for picking up the entrance of the framework utilizing the open
ports and utilized for security review for the system. It can be joined with various sorts of codes for
the misuse in a system.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK SECURITY
System engineers are for the most part required for expectation of different sorts of assaults
and defeating them. There are numerous sorts of strategies which can be utilized for beating the
given assaults like Denial of administration (DoS) or Distributed Denial of Service Attack (DDoS),
social designing and malware. Dos assault is principally thought to be much least demanding to get
it. An effective sort of DoS assault can without much of a stretch occur when the capacity of the
gadget for performing is averted. Techniques which can cause different sorts of condition go which
starts from sending of huge number of movement at the offered gadget to activating of gadget
which can be effectively utilized for buffering. Any sort of activating in the gadget can be utilized for
entering the blunder. A straightforward sort of DDoS can be effectively performed by the assistance
of mistake condition. A basic sort of DDoS assault can be effectively performed by the assistance of
outsider system which center around the accessibility of a given system into another sort of system
limit into another sort of system gadget with less sort of limit. The objective can be effortlessly
observed when the different sorts of assault can be effectively started and certain number of move
made into account. One of the basic sort of assault is social designing. This specific sort of assault
require a specific level of ability which is thought to be of much outstanding quality. Social designing
does not require any sort of innovation. It for the most part takes up the benefit of social strategies
which can be effectively utilized for extraction of any sort of data. Malware is thought to be short
type of pernicious programming. Malware is principally comprehensive of present day sort of
assaults. This is for the most part comprehensive of certain number of techniques like infections,
worm, spyware, Trojan and adware. It chiefly varies in activity when it is joined with different sorts
of task.
Network Security Tools
Nmap is thought to be a free and open source sort of source which is fundamentally utilized
for finding and inspecting of security. Numerous sorts of framework and system manager likewise
thinks that its valuable for managing substantial number of issues like stock of system, legitimate
administration of administration overhaul plans an observing of host or administration uptime.
Nmap makes utilize crude sort of IP parcels in legitimate sort of novel which is basically utilized for
assurance of different sorts of host which are accessible on the system. It is likewise utilized for
dissecting the sort of administration accessible with have offering and sort of working framework
which is running. It was for the most part intended for breaking down the reality for examining
different sorts of systems and legitimate sort of work fine ought to be accessible for it.
NETWORK SECURITY
System engineers are for the most part required for expectation of different sorts of assaults
and defeating them. There are numerous sorts of strategies which can be utilized for beating the
given assaults like Denial of administration (DoS) or Distributed Denial of Service Attack (DDoS),
social designing and malware. Dos assault is principally thought to be much least demanding to get
it. An effective sort of DoS assault can without much of a stretch occur when the capacity of the
gadget for performing is averted. Techniques which can cause different sorts of condition go which
starts from sending of huge number of movement at the offered gadget to activating of gadget
which can be effectively utilized for buffering. Any sort of activating in the gadget can be utilized for
entering the blunder. A straightforward sort of DDoS can be effectively performed by the assistance
of mistake condition. A basic sort of DDoS assault can be effectively performed by the assistance of
outsider system which center around the accessibility of a given system into another sort of system
limit into another sort of system gadget with less sort of limit. The objective can be effortlessly
observed when the different sorts of assault can be effectively started and certain number of move
made into account. One of the basic sort of assault is social designing. This specific sort of assault
require a specific level of ability which is thought to be of much outstanding quality. Social designing
does not require any sort of innovation. It for the most part takes up the benefit of social strategies
which can be effectively utilized for extraction of any sort of data. Malware is thought to be short
type of pernicious programming. Malware is principally comprehensive of present day sort of
assaults. This is for the most part comprehensive of certain number of techniques like infections,
worm, spyware, Trojan and adware. It chiefly varies in activity when it is joined with different sorts
of task.
Network Security Tools
Nmap is thought to be a free and open source sort of source which is fundamentally utilized
for finding and inspecting of security. Numerous sorts of framework and system manager likewise
thinks that its valuable for managing substantial number of issues like stock of system, legitimate
administration of administration overhaul plans an observing of host or administration uptime.
Nmap makes utilize crude sort of IP parcels in legitimate sort of novel which is basically utilized for
assurance of different sorts of host which are accessible on the system. It is likewise utilized for
dissecting the sort of administration accessible with have offering and sort of working framework
which is running. It was for the most part intended for breaking down the reality for examining
different sorts of systems and legitimate sort of work fine ought to be accessible for it.

5
NETWORK SECURITY
Nmap is for the most part utilized for expansive number of stages like Linux, Mac OS and
windows. Aside from the great sort of accessible summon it is essentially comprehensive of cutting
edge sort of GUI and consequence of watcher. It thinks of legitimate sort of adaptable information
exchange method and instruments for troubleshooting. It thinks of different sorts of instruments for
looking at the accessible sort of sweep comes about. A bundle sort of age and apparatus for
responsive examination.
Metaspoilt is an outstanding infiltration test that is principally performed for breaking down
different sorts of vulnerabilities in a given system. It for the most part gives the foundation, content
and different sorts of hardware for performing different sorts of test in organize. It can be expressed
like a broad sort of security evaluating. It thinks of new sorts of security demonstrate that is chiefly
utilized for new sorts of model and substance group which is principally included standard premise.
Metasploit is a popular in the space of security world not long after it was discharged in the time of
2004. It is essentially characterized as a legitimate sort of cutting edge device stage that is
predominantly utilized for creating, testing and abuse of code. It is principally characterized as a
notable model which is primarily utilized for payloads, encoders and misuse which can be effectively
coordinated however much as could be expected which can be effortlessly utilized metasploit
structure which is only an outlet that can be effectively utilized for cut edge for different sorts of
abuse of different sorts of research.
Threat Mitigation Techniques
A substantial number of steps can be taken for conquering different sorts of issues in a system like
Configuration of firewall
Segregation of system
Web application
Be cautious about the benefit of system.
Patch administration
Setup of firewall: It is critical for appropriate administration of design of firewall. It basically
guarantees the way that different sorts of setup must be there in dynamic nature.
System arrangement: Along with checking of different sorts of firewalls it is extremely fundamental
for examining the isolation of things which are working in a powerful route in all the system and
entrance point.
Web vulnerabilities: Weakness and issues in different sorts of web application are thought to be
primary sort of assault merchant by the assistance of vectors by which the association is imperiled.
NETWORK SECURITY
Nmap is for the most part utilized for expansive number of stages like Linux, Mac OS and
windows. Aside from the great sort of accessible summon it is essentially comprehensive of cutting
edge sort of GUI and consequence of watcher. It thinks of legitimate sort of adaptable information
exchange method and instruments for troubleshooting. It thinks of different sorts of instruments for
looking at the accessible sort of sweep comes about. A bundle sort of age and apparatus for
responsive examination.
Metaspoilt is an outstanding infiltration test that is principally performed for breaking down
different sorts of vulnerabilities in a given system. It for the most part gives the foundation, content
and different sorts of hardware for performing different sorts of test in organize. It can be expressed
like a broad sort of security evaluating. It thinks of new sorts of security demonstrate that is chiefly
utilized for new sorts of model and substance group which is principally included standard premise.
Metasploit is a popular in the space of security world not long after it was discharged in the time of
2004. It is essentially characterized as a legitimate sort of cutting edge device stage that is
predominantly utilized for creating, testing and abuse of code. It is principally characterized as a
notable model which is primarily utilized for payloads, encoders and misuse which can be effectively
coordinated however much as could be expected which can be effortlessly utilized metasploit
structure which is only an outlet that can be effectively utilized for cut edge for different sorts of
abuse of different sorts of research.
Threat Mitigation Techniques
A substantial number of steps can be taken for conquering different sorts of issues in a system like
Configuration of firewall
Segregation of system
Web application
Be cautious about the benefit of system.
Patch administration
Setup of firewall: It is critical for appropriate administration of design of firewall. It basically
guarantees the way that different sorts of setup must be there in dynamic nature.
System arrangement: Along with checking of different sorts of firewalls it is extremely fundamental
for examining the isolation of things which are working in a powerful route in all the system and
entrance point.
Web vulnerabilities: Weakness and issues in different sorts of web application are thought to be
primary sort of assault merchant by the assistance of vectors by which the association is imperiled.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK SECURITY
System administration: One of the best that is thought about of security of different sorts of
framework and administrations are fixed according to the prerequisite.
Conclusion
From the above report it can be presumed that utilizing the Nmap and the Metasploit helps in
distinguishing proof of the present weakness of the system and the those two can be utilized as a
decent mix for the abuse of the system. The metasploit can be utilized for avoiding the antivirus
arrangement introduced in the focused on machine and offers propelled entrance testing highlights
for the misuse of the powerlessness in the present system. The nmap is utilized for filtering the
system using crude IP parcel and it can without much of a stretch assemble diverse data from the
system, for example, the adaptation of the working framework, accessible hosts associated in the
system and presence of the firewall, and so forth that are basic for playing out the entrance testing.
NETWORK SECURITY
System administration: One of the best that is thought about of security of different sorts of
framework and administrations are fixed according to the prerequisite.
Conclusion
From the above report it can be presumed that utilizing the Nmap and the Metasploit helps in
distinguishing proof of the present weakness of the system and the those two can be utilized as a
decent mix for the abuse of the system. The metasploit can be utilized for avoiding the antivirus
arrangement introduced in the focused on machine and offers propelled entrance testing highlights
for the misuse of the powerlessness in the present system. The nmap is utilized for filtering the
system using crude IP parcel and it can without much of a stretch assemble diverse data from the
system, for example, the adaptation of the working framework, accessible hosts associated in the
system and presence of the firewall, and so forth that are basic for playing out the entrance testing.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK SECURITY
Bibliography
[1]. Armstrong, M.E., Jones, K.S., Namin, A.S. and Newton, D.C. What Vulnerability Assessment
and Management Cybersecurity Professionals Think Their Future Colleagues Need to Know.
In Proceedings of the 49th ACM Technical Symposium on Computer Science Education (pp.
1082-1082). ACM., 2018, February.
[2]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}., 2017 August.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First
Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September
21–22, 2015 Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Holik, F., Horalek, J., Marik, O., Neradova, S. and Zitta, S. Effective penetration testing with
Metasploit framework and methodologies. In Computational Intelligence and Informatics
(CINTI), 2014 IEEE 15th International Symposium on (pp. 237-242). IEEE., 2014, November.
[5]. Johansen, G., Allen, L., Heriyanto, T. and Ali, S. Kali Linux 2–Assuring Security by Penetration
Testing. Packt Publishing Ltd., 2016.
[6]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[7]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[8]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
NETWORK SECURITY
Bibliography
[1]. Armstrong, M.E., Jones, K.S., Namin, A.S. and Newton, D.C. What Vulnerability Assessment
and Management Cybersecurity Professionals Think Their Future Colleagues Need to Know.
In Proceedings of the 49th ACM Technical Symposium on Computer Science Education (pp.
1082-1082). ACM., 2018, February.
[2]. Atwater, E., Bocovich, C., Hengartner, U. and Goldberg, I. Live Lesson: Netsim: Network
simulation and hacking for high schoolers. In 2017 {USENIX} Workshop on Advances in
Security Education ({ASE} 17). USENIX} Association}., 2017 August.
[3]. Cuppens, F. WirelessHART NetSIM: A WirelessHART SCADA-Based Wireless Sensor Networks
Simulator. In Security of Industrial Control Systems and Cyber Physical Systems: First
Workshop, CyberICS 2015 and First Workshop, WOS-CPS 2015 Vienna, Austria, September
21–22, 2015 Revised Selected Papers (Vol. 9588, p. 63). Springer., 2016, June.
[4]. Holik, F., Horalek, J., Marik, O., Neradova, S. and Zitta, S. Effective penetration testing with
Metasploit framework and methodologies. In Computational Intelligence and Informatics
(CINTI), 2014 IEEE 15th International Symposium on (pp. 237-242). IEEE., 2014, November.
[5]. Johansen, G., Allen, L., Heriyanto, T. and Ali, S. Kali Linux 2–Assuring Security by Penetration
Testing. Packt Publishing Ltd., 2016.
[6]. Nayak, P. and Sinha, P. Analysis of Random Way Point and Random Walk Mobility Model for
Reactive Routing Protocols for MANET Using NetSim Simulator. In Artificial Intelligence,
Modelling and Simulation (AIMS), 2015 3rd International Conference on (pp. 427-432). IEEE.,
2015 December.
[7]. Peng, J., Li, H., Wang, Y. and Chen, J. A web tool for measuring gene semantic similarities by
combining Gene Ontology and gene co-function networks. In Proceedings of the 6th ACM
Conference on Bioinformatics, Computational Biology and Health Informatics (pp. 678-679).
ACM., 2015 September.
[8]. Saifuddin, K.M., Ahmed, A.S., Reza, K.F., Alam, S.S. and Rahman, S. Performance analysis of
cognitive radio: Netsim viewpoint. In Electrical Information and Communication Technology
(EICT), 2017 3rd International Conference on (pp. 1-6). IEEE., 2017 December.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




