Network Security: A Detailed Report on Threats and Control Measures
VerifiedAdded on 2023/06/03
|14
|1843
|104
Report
AI Summary
This report provides a detailed analysis of various network security threats and the corresponding controls that organizations should implement. It categorizes threats such as accidental data corruption, loss of intellectual property, software piracy, information theft (by both hackers and employees), website defacement, equipment theft, viruses, privilege elevation, and fire/flood incidents. For each threat category, the report outlines specific controls, classifying them as administrative, product, or physical, and detailing whether they serve to prevent, detect, correct, or compensate for the threat. Controls discussed include antivirus software, data encryption, firewalls, intrusion detection systems, security protocols, and physical security measures. The report also references academic literature to support its analysis and recommendations.

Running head: NETWORK AND SECURITY
Network and Security
Name of the Student
Name of the University
Author’s Note:
Network and Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORK AND SECURITY
Table of Contents
Threats and Controls..................................................................................................................2
Bibliography.............................................................................................................................12
NETWORK AND SECURITY
Table of Contents
Threats and Controls..................................................................................................................2
Bibliography.............................................................................................................................12
2
NETWORK AND SECURITY
Threats and Controls
Threats could be easily categorized and controlled within the organization. The major
controls could be classified as administrative, product and physical and the controls can be
depicted as prevent, detect, correct or compensate.
The proper evaluation of the threat categories are as follows:
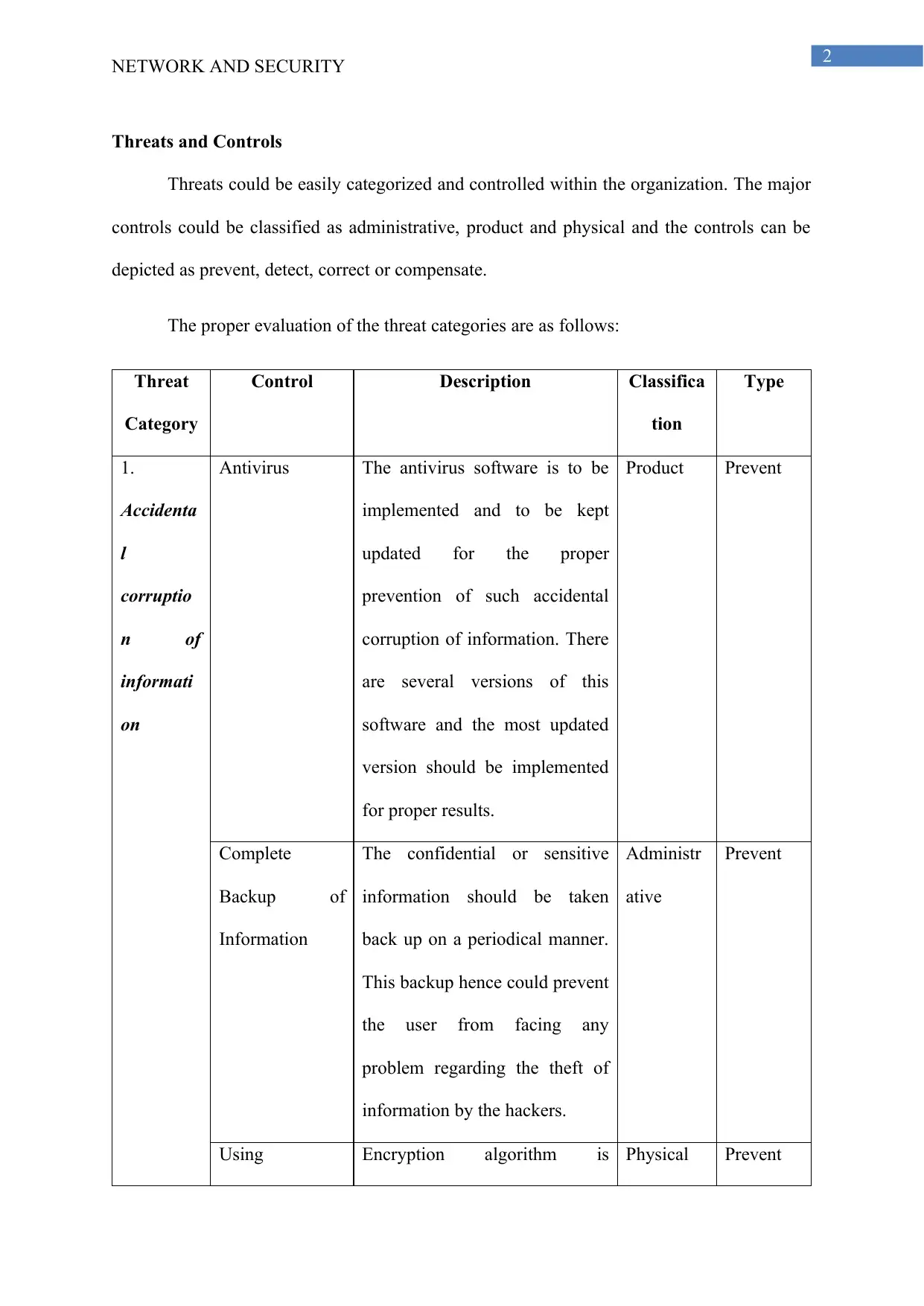
Threat
Category
Control Description Classifica
tion
Type
1.
Accidenta
l
corruptio
n of
informati
on
Antivirus The antivirus software is to be
implemented and to be kept
updated for the proper
prevention of such accidental
corruption of information. There
are several versions of this
software and the most updated
version should be implemented
for proper results.
Product Prevent
Complete
Backup of
Information
The confidential or sensitive
information should be taken
back up on a periodical manner.
This backup hence could prevent
the user from facing any
problem regarding the theft of
information by the hackers.
Administr
ative
Prevent
Using Encryption algorithm is Physical Prevent
NETWORK AND SECURITY
Threats and Controls
Threats could be easily categorized and controlled within the organization. The major
controls could be classified as administrative, product and physical and the controls can be
depicted as prevent, detect, correct or compensate.
The proper evaluation of the threat categories are as follows:
Threat
Category
Control Description Classifica
tion
Type
1.
Accidenta
l
corruptio
n of
informati
on
Antivirus The antivirus software is to be
implemented and to be kept
updated for the proper
prevention of such accidental
corruption of information. There
are several versions of this
software and the most updated
version should be implemented
for proper results.
Product Prevent
Complete
Backup of
Information
The confidential or sensitive
information should be taken
back up on a periodical manner.
This backup hence could prevent
the user from facing any
problem regarding the theft of
information by the hackers.
Administr
ative
Prevent
Using Encryption algorithm is Physical Prevent
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
NETWORK AND SECURITY
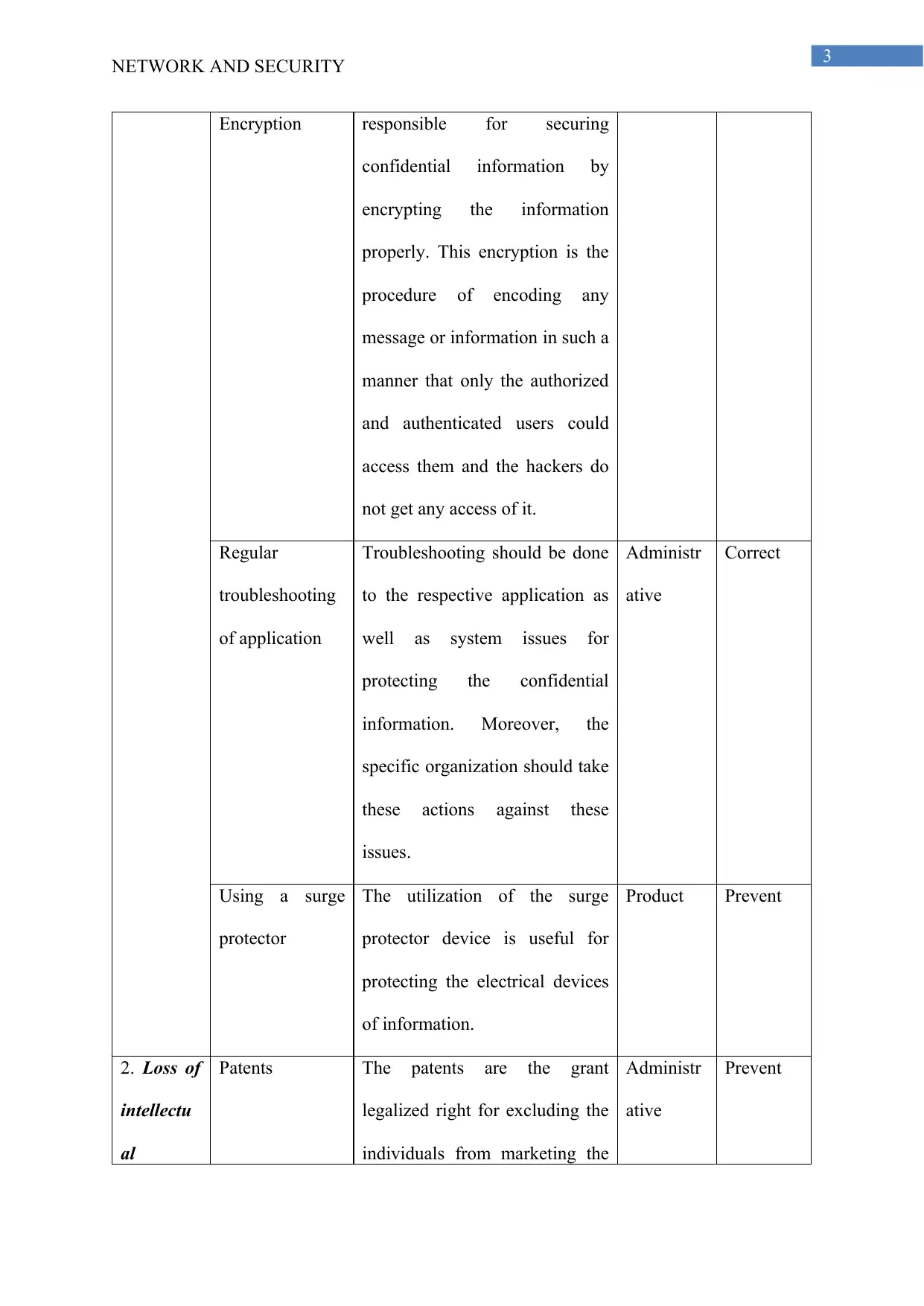
Encryption responsible for securing
confidential information by
encrypting the information
properly. This encryption is the
procedure of encoding any
message or information in such a
manner that only the authorized
and authenticated users could
access them and the hackers do
not get any access of it.
Regular
troubleshooting
of application
Troubleshooting should be done
to the respective application as
well as system issues for
protecting the confidential
information. Moreover, the
specific organization should take
these actions against these
issues.
Administr
ative
Correct
Using a surge
protector
The utilization of the surge
protector device is useful for
protecting the electrical devices
of information.
Product Prevent
2. Loss of
intellectu
al
Patents The patents are the grant
legalized right for excluding the
individuals from marketing the
Administr
ative
Prevent
NETWORK AND SECURITY
Encryption responsible for securing
confidential information by
encrypting the information
properly. This encryption is the
procedure of encoding any
message or information in such a
manner that only the authorized
and authenticated users could
access them and the hackers do
not get any access of it.
Regular
troubleshooting
of application
Troubleshooting should be done
to the respective application as
well as system issues for
protecting the confidential
information. Moreover, the
specific organization should take
these actions against these
issues.
Administr
ative
Correct
Using a surge
protector
The utilization of the surge
protector device is useful for
protecting the electrical devices
of information.
Product Prevent
2. Loss of
intellectu
al
Patents The patents are the grant
legalized right for excluding the
individuals from marketing the
Administr
ative
Prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORK AND SECURITY
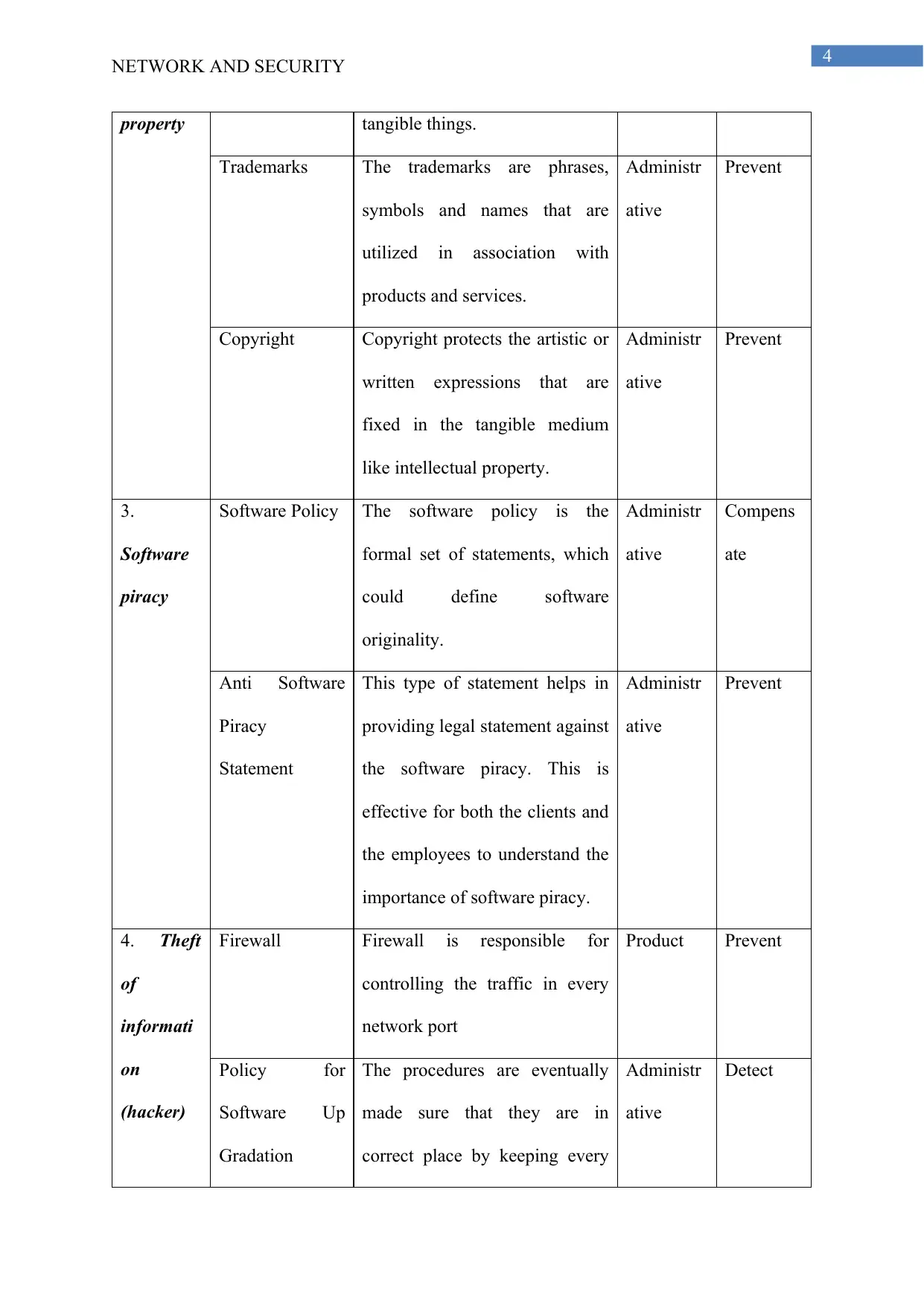
property tangible things.
Trademarks The trademarks are phrases,
symbols and names that are
utilized in association with
products and services.
Administr
ative
Prevent
Copyright Copyright protects the artistic or
written expressions that are
fixed in the tangible medium
like intellectual property.
Administr
ative
Prevent
3.
Software
piracy
Software Policy The software policy is the
formal set of statements, which
could define software
originality.
Administr
ative
Compens
ate
Anti Software
Piracy
Statement
This type of statement helps in
providing legal statement against
the software piracy. This is
effective for both the clients and
the employees to understand the
importance of software piracy.
Administr
ative
Prevent
4. Theft
of
informati
on
(hacker)
Firewall Firewall is responsible for
controlling the traffic in every
network port
Product Prevent
Policy for
Software Up
Gradation
The procedures are eventually
made sure that they are in
correct place by keeping every
Administr
ative
Detect
NETWORK AND SECURITY
property tangible things.
Trademarks The trademarks are phrases,
symbols and names that are
utilized in association with
products and services.
Administr
ative
Prevent
Copyright Copyright protects the artistic or
written expressions that are
fixed in the tangible medium
like intellectual property.
Administr
ative
Prevent
3.
Software
piracy
Software Policy The software policy is the
formal set of statements, which
could define software
originality.
Administr
ative
Compens
ate
Anti Software
Piracy
Statement
This type of statement helps in
providing legal statement against
the software piracy. This is
effective for both the clients and
the employees to understand the
importance of software piracy.
Administr
ative
Prevent
4. Theft
of
informati
on
(hacker)
Firewall Firewall is responsible for
controlling the traffic in every
network port
Product Prevent
Policy for
Software Up
Gradation
The procedures are eventually
made sure that they are in
correct place by keeping every
Administr
ative
Detect
5
NETWORK AND SECURITY
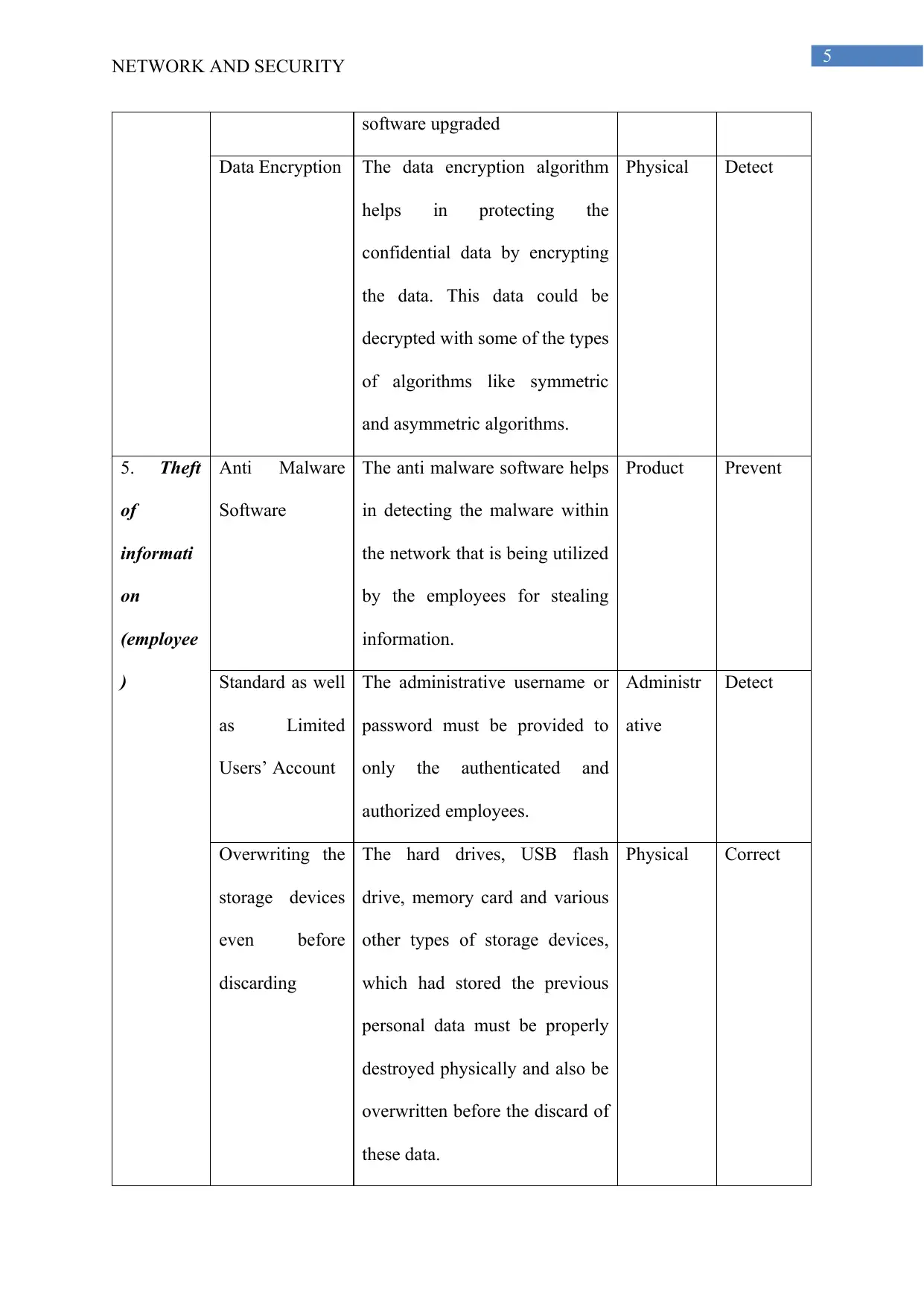
software upgraded
Data Encryption The data encryption algorithm
helps in protecting the
confidential data by encrypting
the data. This data could be
decrypted with some of the types
of algorithms like symmetric
and asymmetric algorithms.
Physical Detect
5. Theft
of
informati
on
(employee
)
Anti Malware
Software
The anti malware software helps
in detecting the malware within
the network that is being utilized
by the employees for stealing
information.
Product Prevent
Standard as well
as Limited
Users’ Account
The administrative username or
password must be provided to
only the authenticated and
authorized employees.
Administr
ative
Detect
Overwriting the
storage devices
even before
discarding
The hard drives, USB flash
drive, memory card and various
other types of storage devices,
which had stored the previous
personal data must be properly
destroyed physically and also be
overwritten before the discard of
these data.
Physical Correct
NETWORK AND SECURITY
software upgraded
Data Encryption The data encryption algorithm
helps in protecting the
confidential data by encrypting
the data. This data could be
decrypted with some of the types
of algorithms like symmetric
and asymmetric algorithms.
Physical Detect
5. Theft
of
informati
on
(employee
)
Anti Malware
Software
The anti malware software helps
in detecting the malware within
the network that is being utilized
by the employees for stealing
information.
Product Prevent
Standard as well
as Limited
Users’ Account
The administrative username or
password must be provided to
only the authenticated and
authorized employees.
Administr
ative
Detect
Overwriting the
storage devices
even before
discarding
The hard drives, USB flash
drive, memory card and various
other types of storage devices,
which had stored the previous
personal data must be properly
destroyed physically and also be
overwritten before the discard of
these data.
Physical Correct
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
NETWORK AND SECURITY
Utilizing the
secured
connectivity for
sending the
sensitive and
confidential
information
The protocols of TLS and SSL
are ensuring that only sensitive
data is being sent in a secured
manner so that the theft of
confidential information by all
the employees is not at all
possible. Hence, the theft of
confidential data could be
stopped with proper
effectiveness.
Physical Prevent
Plan to
responding to
the various
incidents
A specific plan that would be
extremely effective and efficient
for providing proper responses
to the several significant
incidents of information theft by
employees. This type of plan can
also be effective for the
organizational assets.
Administr
ative
Compens
ate
6. Web
site
defaceme
nt
Wachete tool This is one of the most
important and significant tools
that is responsible for the proper
monitoring of various web site
changes. Thus, web site
defacement or the attack on the
web site, which could change
Product Prevent
NETWORK AND SECURITY
Utilizing the
secured
connectivity for
sending the
sensitive and
confidential
information
The protocols of TLS and SSL
are ensuring that only sensitive
data is being sent in a secured
manner so that the theft of
confidential information by all
the employees is not at all
possible. Hence, the theft of
confidential data could be
stopped with proper
effectiveness.
Physical Prevent
Plan to
responding to
the various
incidents
A specific plan that would be
extremely effective and efficient
for providing proper responses
to the several significant
incidents of information theft by
employees. This type of plan can
also be effective for the
organizational assets.
Administr
ative
Compens
ate
6. Web
site
defaceme
nt
Wachete tool This is one of the most
important and significant tools
that is responsible for the proper
monitoring of various web site
changes. Thus, web site
defacement or the attack on the
web site, which could change
Product Prevent
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORK AND SECURITY
the respective visual appearance
of the web site could be
eventually stopped without any
type of issues or problems.
Sucuri Tool The second tool for the proper
control of web site defacement is
the Sucuri tool. This particular
tool helps in the web site
monitoring, which subsequently
protects the web site and also
provides back up as well as
quality performance.
Product Detect
Visualping Another important and
noteworthy tool that helps to
detect, monitor and alter the
various changes in web site is
Visualping. The specific area of
web site, which requires to be
monitored and also could be
done by the proper utilization of
the tool of Visualping.
Product Detect
IPVTec tool The next popular and effective
web site monitoring tool that is
solely responsible for the proper
detection of the web site
Product Detect
NETWORK AND SECURITY
the respective visual appearance
of the web site could be
eventually stopped without any
type of issues or problems.
Sucuri Tool The second tool for the proper
control of web site defacement is
the Sucuri tool. This particular
tool helps in the web site
monitoring, which subsequently
protects the web site and also
provides back up as well as
quality performance.
Product Detect
Visualping Another important and
noteworthy tool that helps to
detect, monitor and alter the
various changes in web site is
Visualping. The specific area of
web site, which requires to be
monitored and also could be
done by the proper utilization of
the tool of Visualping.
Product Detect
IPVTec tool The next popular and effective
web site monitoring tool that is
solely responsible for the proper
detection of the web site
Product Detect
8
NETWORK AND SECURITY
defacement is IPVTec tool.
WebOrion tool This is another important and
significant tool that is being
utilized for the proper detection,
prevention and monitoring of
services, which could offer the
major contents, visual changes
as well as proper monitoring of
integrity.
Product Prevent,
Detect
and
Correct
Fluxguard Fluxguard is yet another
effective and efficient tool for
web site monitoring and that
could easily check and monitor
the defacement of the web site.
The QA automation, visual
regression, application
performance monitoring and
synthetic transactions are
properly checked and monitored
with Fluxguard tool.
Product Prevent
and
Detect
7. Theft
of
equipmen
t
To provide theft
indicator for
every equipment
The theft indicator is the basic
control for mitigating any type
of theft of equipment in an
organization. Hence, this type of
indicator could save the
Physical Detect
NETWORK AND SECURITY
defacement is IPVTec tool.
WebOrion tool This is another important and
significant tool that is being
utilized for the proper detection,
prevention and monitoring of
services, which could offer the
major contents, visual changes
as well as proper monitoring of
integrity.
Product Prevent,
Detect
and
Correct
Fluxguard Fluxguard is yet another
effective and efficient tool for
web site monitoring and that
could easily check and monitor
the defacement of the web site.
The QA automation, visual
regression, application
performance monitoring and
synthetic transactions are
properly checked and monitored
with Fluxguard tool.
Product Prevent
and
Detect
7. Theft
of
equipmen
t
To provide theft
indicator for
every equipment
The theft indicator is the basic
control for mitigating any type
of theft of equipment in an
organization. Hence, this type of
indicator could save the
Physical Detect
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9
NETWORK AND SECURITY
equipment from hackers.
Securing Site of
Equipment
The light pods, locked gates as
well as the onsite security
presence are the most effective
methods of detecting the
hackers.
Administr
ative
Prevent
and detect
Developing
protocols for
equipment
The generators are efficient for
developing protocols for the
equipment of any organization.
Administr
ative
Compens
ate
Utilizing CCTV
cameras
The proper utilization of the
CCTV cameras are effective for
checking and detecting the theft
of equipment. Moreover,
prevention and correction of the
issues are also possible with
these.
Product Prevent,
detect and
compensa
te
8.
Viruses,
worms,
Trojan
horses
Implementation
of Antivirus
software
The viruses, worms and Trojan
horses could be easily prevented
by implementing the software of
antivirus. Proper up gradation is
also required here.
Product Prevent
and
Correct
Implementation
of firewalls
Firewalls are responsible for
proper detection of the viruses,
worms and Trojan horses.
Moreover, it can filter the IP
Product Detect
NETWORK AND SECURITY
equipment from hackers.
Securing Site of
Equipment
The light pods, locked gates as
well as the onsite security
presence are the most effective
methods of detecting the
hackers.
Administr
ative
Prevent
and detect
Developing
protocols for
equipment
The generators are efficient for
developing protocols for the
equipment of any organization.
Administr
ative
Compens
ate
Utilizing CCTV
cameras
The proper utilization of the
CCTV cameras are effective for
checking and detecting the theft
of equipment. Moreover,
prevention and correction of the
issues are also possible with
these.
Product Prevent,
detect and
compensa
te
8.
Viruses,
worms,
Trojan
horses
Implementation
of Antivirus
software
The viruses, worms and Trojan
horses could be easily prevented
by implementing the software of
antivirus. Proper up gradation is
also required here.
Product Prevent
and
Correct
Implementation
of firewalls
Firewalls are responsible for
proper detection of the viruses,
worms and Trojan horses.
Moreover, it can filter the IP
Product Detect
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10
NETWORK AND SECURITY
addresses for accessing network
to prevent such attacks.
Intrusion
Detection
System
The intrusion is easily detected
and prevented with the help of
signature database to identify the
major threats.
Product Detect
9.
Elevation
of
privilege
Decrypter The decrypter helps in
decrypting the encrypted code or
data that is being encrypted by
encryption. Moreover, these are
much cost effective in
comparison to other techniques.
Administr
ative
Correct
API resolver The application platform
interfaces are easily and
promptly resolved with this
product and hence determination
of the working of the shell code
as well as position independent
codes are done properly. Thus,
elevation of privilege is done
easily and promptly.
Product Prevent,
Detect
and
Correct
10. Fire/
Flood
Utilizing the
techniques of
flood resistant as
well as fire
The various techniques
regarding the fire resistant as
well as flood resistant are
properly utilized for the
Physical Compens
ate
NETWORK AND SECURITY
addresses for accessing network
to prevent such attacks.
Intrusion
Detection
System
The intrusion is easily detected
and prevented with the help of
signature database to identify the
major threats.
Product Detect
9.
Elevation
of
privilege
Decrypter The decrypter helps in
decrypting the encrypted code or
data that is being encrypted by
encryption. Moreover, these are
much cost effective in
comparison to other techniques.
Administr
ative
Correct
API resolver The application platform
interfaces are easily and
promptly resolved with this
product and hence determination
of the working of the shell code
as well as position independent
codes are done properly. Thus,
elevation of privilege is done
easily and promptly.
Product Prevent,
Detect
and
Correct
10. Fire/
Flood
Utilizing the
techniques of
flood resistant as
well as fire
The various techniques
regarding the fire resistant as
well as flood resistant are
properly utilized for the
Physical Compens
ate
11
NETWORK AND SECURITY
resistant subsequent prevention from any
type of natural disaster like fire
or flood.
Keeping
organizational
assets in safer
place
The various organizational
assets must be kept in safer
place so that these are easily
protected from fire and flood.
Administr
ative
Prevent
and
Correct
NETWORK AND SECURITY
resistant subsequent prevention from any
type of natural disaster like fire
or flood.
Keeping
organizational
assets in safer
place
The various organizational
assets must be kept in safer
place so that these are easily
protected from fire and flood.
Administr
ative
Prevent
and
Correct
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





