Network Design, Setup, and Specifications for Priority Advertising
VerifiedAdded on 2022/10/31
|12
|3983
|389
Report
AI Summary
This report presents a network solution designed for Priority Advertising, a marketing and advertising firm. It outlines the project goals, workstation configurations based on workloads, and technical specifications for file and mail servers. The report details the network topology, including the Brisbane CBD office and the Toowoomba office, and explains shared components, internet service installation, subnet classification, and IP addressing. Security concerns and mitigation techniques are also discussed. The report provides a comprehensive overview of the network infrastructure, including the setup of workstations, printers, and wireless access points for each department, ensuring seamless connectivity and data sharing between the Brisbane and Toowoomba branches. The report emphasizes the importance of network topology diagrams, hardware component specifications, and networking equipment in establishing a robust network infrastructure for the organization. This includes the setup of a file server for data backup and storage, and a mail server to manage email communications. The report concludes with an analysis of the network's security concerns and mitigation strategies.

Running head: NETWORK SET UP AND SPECIFICATIONS
Network Set UP and Specifications
Name of the Student
Name of the University
Author Note
Network Set UP and Specifications
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK SET UP AND SPECIFICATIONS
Summary
As per numerous studies in the area of network, the importance of network topology diagrams,
specifications of hardware components and networking equipment in setting up network
infrastructure of organizations have been well established. The report presents one such network
solution for Priority Advertising. First this report talks about the goals of the project that are to be
met by the proposed network. Then it is to prescribe the various configurations of workstations
depending on the workloads they are subjected to. After that the report classifies the technical
specifications of the hardware components of the File and Mail servers in tabular format. Then the
report is to present and discuss the network topology for Priority Advertising followed by detailed
explanations on the shared components and installation of Internet services being acquired. Next
the subnet classification and IP addressing the different subnets and devices are to be made. After
briefly explaining the security concerns with public and private IP addresses and the mitigation
technique, the report is to end with concluding notes.
Summary
As per numerous studies in the area of network, the importance of network topology diagrams,
specifications of hardware components and networking equipment in setting up network
infrastructure of organizations have been well established. The report presents one such network
solution for Priority Advertising. First this report talks about the goals of the project that are to be
met by the proposed network. Then it is to prescribe the various configurations of workstations
depending on the workloads they are subjected to. After that the report classifies the technical
specifications of the hardware components of the File and Mail servers in tabular format. Then the
report is to present and discuss the network topology for Priority Advertising followed by detailed
explanations on the shared components and installation of Internet services being acquired. Next
the subnet classification and IP addressing the different subnets and devices are to be made. After
briefly explaining the security concerns with public and private IP addresses and the mitigation
technique, the report is to end with concluding notes.

2NETWORK SET UP AND SPECIFICATIONS
Table of Contents
Introduction...........................................................................................................................................3
Brief of the Organization.......................................................................................................................3
Project Goals.........................................................................................................................................3
Activity 1................................................................................................................................................4
Computer System for Various Workloads.........................................................................................4
Activity 2................................................................................................................................................5
Server Set Up.....................................................................................................................................5
Activity 3................................................................................................................................................6
Network Design.................................................................................................................................6
Activity 4................................................................................................................................................7
Shared Components..........................................................................................................................7
Activity 5................................................................................................................................................7
Internet Service and Installation.......................................................................................................7
Activity 6................................................................................................................................................7
Subnet Classification and IP Addressing............................................................................................7
Activity 7................................................................................................................................................8
Security Concerns and Mitigation.....................................................................................................8
Conclusion.............................................................................................................................................9
References...........................................................................................................................................10
Table of Contents
Introduction...........................................................................................................................................3
Brief of the Organization.......................................................................................................................3
Project Goals.........................................................................................................................................3
Activity 1................................................................................................................................................4
Computer System for Various Workloads.........................................................................................4
Activity 2................................................................................................................................................5
Server Set Up.....................................................................................................................................5
Activity 3................................................................................................................................................6
Network Design.................................................................................................................................6
Activity 4................................................................................................................................................7
Shared Components..........................................................................................................................7
Activity 5................................................................................................................................................7
Internet Service and Installation.......................................................................................................7
Activity 6................................................................................................................................................7
Subnet Classification and IP Addressing............................................................................................7
Activity 7................................................................................................................................................8
Security Concerns and Mitigation.....................................................................................................8
Conclusion.............................................................................................................................................9
References...........................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORK SET UP AND SPECIFICATIONS
Introduction
The following report tries to highlight the importance of network topology diagrams,
specifications of hardware components and networking equipment in setting up network
infrastructure of business organizations. The report presents one such network solution for the
marketing and advertising firm Priority Advertising. The report begins by talking about the goals of
the networking project that needs to be met by the proposed network. Then it prescribes the
various configurations of workstations based on the workloads that is to be performed by each type
of workstation. Thereafter that the report classifies the technical specifications of the hardware
components for the File and the Email servers in a specification table. Then the report proceeds
further by presenting and discussing the network topology which has been drawn in the network
simulation software Cisco Packet Tracer. The network solution for Priority Advertising gets followed
by detailed explanations on the shared components and installation of Internet services being
acquired. Next the subnet classification and IP addressing the different subnets and devices are to be
made. After briefly explaining the security concerns with public and private IP addresses and the
mitigation technique, the report is to end with concluding notes.
Brief of the Organization
The advertising firm Priority Advertising is a medium sized organization that serves in the
marketing and advertising sector. There activities of the firm include film production, creation of
advertisement media content and high-quality printing of advertisement banners and posters.
Project Goals
The new network is to include a solution for Priority Advertisement so that they can use their newly
set up office at Brisbane CBD.
The new network is to provide connectivity services to the workstations and printers for all the 95
employees that are to work in the location of Brisbane CBD.
The new office that has been set up in the suburbs of Brisbane is five stories tall and is to house a
department in each of these five floors.
The organization has also expanded in other cities like Toowoomba where they need to cater
increasing demands from customers for interactive advertisement content such as video
presentations.
The network therefore must also include the small office that have been leased in Toowoomba
which consists of one department only – the advertisement media department.
The employees of Priority advertising should be able to obtain email services from the web mail as
provided by the ISP both from office and from homes.
The company should additionally be able to internally manage email accounts for their employees
and updates to their mailing domain should not be interrupting the services offered by the company.
The managers as well as the employees must be able to share large volumes of data over the
network at any time of the day which includes film files ranging in sizes from 5GB and up to 20GB.
The organizational members must be able to back up sensitivity and important files in a safe and
secure manner in the office building of Brisbane only.
These files that have been backed up should be accessible to department managers present in each
department of both the branches.
Introduction
The following report tries to highlight the importance of network topology diagrams,
specifications of hardware components and networking equipment in setting up network
infrastructure of business organizations. The report presents one such network solution for the
marketing and advertising firm Priority Advertising. The report begins by talking about the goals of
the networking project that needs to be met by the proposed network. Then it prescribes the
various configurations of workstations based on the workloads that is to be performed by each type
of workstation. Thereafter that the report classifies the technical specifications of the hardware
components for the File and the Email servers in a specification table. Then the report proceeds
further by presenting and discussing the network topology which has been drawn in the network
simulation software Cisco Packet Tracer. The network solution for Priority Advertising gets followed
by detailed explanations on the shared components and installation of Internet services being
acquired. Next the subnet classification and IP addressing the different subnets and devices are to be
made. After briefly explaining the security concerns with public and private IP addresses and the
mitigation technique, the report is to end with concluding notes.
Brief of the Organization
The advertising firm Priority Advertising is a medium sized organization that serves in the
marketing and advertising sector. There activities of the firm include film production, creation of
advertisement media content and high-quality printing of advertisement banners and posters.
Project Goals
The new network is to include a solution for Priority Advertisement so that they can use their newly
set up office at Brisbane CBD.
The new network is to provide connectivity services to the workstations and printers for all the 95
employees that are to work in the location of Brisbane CBD.
The new office that has been set up in the suburbs of Brisbane is five stories tall and is to house a
department in each of these five floors.
The organization has also expanded in other cities like Toowoomba where they need to cater
increasing demands from customers for interactive advertisement content such as video
presentations.
The network therefore must also include the small office that have been leased in Toowoomba
which consists of one department only – the advertisement media department.
The employees of Priority advertising should be able to obtain email services from the web mail as
provided by the ISP both from office and from homes.
The company should additionally be able to internally manage email accounts for their employees
and updates to their mailing domain should not be interrupting the services offered by the company.
The managers as well as the employees must be able to share large volumes of data over the
network at any time of the day which includes film files ranging in sizes from 5GB and up to 20GB.
The organizational members must be able to back up sensitivity and important files in a safe and
secure manner in the office building of Brisbane only.
These files that have been backed up should be accessible to department managers present in each
department of both the branches.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK SET UP AND SPECIFICATIONS
It is required that each of the colour printers which can be used for printing storyboards containing
large amounts of graphics content be accessible to all the members of the organization.
These printers are to include printers for each department in each of the five floors of the Brisbane
office, one in Toowoomba office as also a separate private printer for the administrator at
Toowoomba.
Each of the departments of Priority Advertising include the Advertising media department present at
Toowoomba small office.
The networks of all departments must come with support for wireless network connectivity through
individual WLAN networks set up for each department.
The company is to obtain internet access through the major network 194.32.9.160 from the ISP and
perform IP addressing based on the IPv4 protocol.
Every department of Priority Advertising must have their own networks that are independently
manageable and well segmented from the networks of other departments.
Members from both the branches Brisbane and Toowoomba of the company Priority Advertising
should be able to communicate with one another and should be able to seamlessly connect with the
internally managed servers the respective purposes.
Activity 1
Computer System for Various Workloads
The computer systems that are to be installed for general use should be based on
the following configuration and technical specification:
Processor: Intel Core i5 9600k
RAM (Random Access Memory): 8 GB DDR4 RAM 3000Mhz
Storage Drives: 500 GB Internal Hard Drive (HDD) 7200RPM 64M cache
USB connectivity: 7 USB ports
The workstations that needs to be installed for graphics production should at least match
the following technical specifications:
Processor: Intel Core i7 9700k
RAM: 16 GB DDR4 RAM 3000Mhz
Storage Drives: 64 GB Internal Solid-State Drive (SSD)
1 TB Internal Hard Drive (HDD) 7200RPM 64M cache
Graphics Card: Nvidia Quadro P1000 4GB GDDR5 128bit PCI Express 3.0 x16
USB connectivity: 7 USB ports
The workstations which are going to be needed for film production are recommended to
meet the following requirements and technical specifications:
Processor: Intel Core i9 9900k
RAM: 32 GB DDR4 RAM 3200Mhz
It is required that each of the colour printers which can be used for printing storyboards containing
large amounts of graphics content be accessible to all the members of the organization.
These printers are to include printers for each department in each of the five floors of the Brisbane
office, one in Toowoomba office as also a separate private printer for the administrator at
Toowoomba.
Each of the departments of Priority Advertising include the Advertising media department present at
Toowoomba small office.
The networks of all departments must come with support for wireless network connectivity through
individual WLAN networks set up for each department.
The company is to obtain internet access through the major network 194.32.9.160 from the ISP and
perform IP addressing based on the IPv4 protocol.
Every department of Priority Advertising must have their own networks that are independently
manageable and well segmented from the networks of other departments.
Members from both the branches Brisbane and Toowoomba of the company Priority Advertising
should be able to communicate with one another and should be able to seamlessly connect with the
internally managed servers the respective purposes.
Activity 1
Computer System for Various Workloads
The computer systems that are to be installed for general use should be based on
the following configuration and technical specification:
Processor: Intel Core i5 9600k
RAM (Random Access Memory): 8 GB DDR4 RAM 3000Mhz
Storage Drives: 500 GB Internal Hard Drive (HDD) 7200RPM 64M cache
USB connectivity: 7 USB ports
The workstations that needs to be installed for graphics production should at least match
the following technical specifications:
Processor: Intel Core i7 9700k
RAM: 16 GB DDR4 RAM 3000Mhz
Storage Drives: 64 GB Internal Solid-State Drive (SSD)
1 TB Internal Hard Drive (HDD) 7200RPM 64M cache
Graphics Card: Nvidia Quadro P1000 4GB GDDR5 128bit PCI Express 3.0 x16
USB connectivity: 7 USB ports
The workstations which are going to be needed for film production are recommended to
meet the following requirements and technical specifications:
Processor: Intel Core i9 9900k
RAM: 32 GB DDR4 RAM 3200Mhz
5NETWORK SET UP AND SPECIFICATIONS
Storage Drives: 128 GB Internal Solid-State Drive (SSD)
1 TB Internal Hard Drive (HDD) 7200RPM 64M cache
Graphics Card: Nvidia Quadro RTX 4000 8 GB GDDR6 128bit PCI Express 3.0 x16
USB connectivity: 14 USB ports
Activity 2
Server Set Up
Location:
Component Recommendation
Processor: Intel, Xeon W-3175X,
, 3.10 GHZ, 38.5M cache
Memory: DDR4, 256 GB, 3000 MHz
Hard Drive: SSD, 500GB, HDD, 3TB
CD-ROM/DVD: Read 24x, Read/Write 16x, DVD-ROM < 160 ms,
CD-ROM < 140 ms
USB Ports: 2 USB3.0, 2 USB2.0, Front, 2 USB3.0, 2 USB2.0
Back
Video Card: Nvidia, Quadro P1000, 4GB GDDR5, 128bit PCI
Express 3.0 x16
Sound Card: ASUS, Xonar DG 5.1 Channel
Modem: Linksys Small Business RV042, External, 100
Mbps, 802.11 Standard
Network Card(s): Intel X520-DA2, Ethernet: 5.0 GT/s, Wireless,
PCI Express 2.0
Operating System: Windows, Server 2019, 64-bit
Monitor: 32-inch, 3840 x 2160, 60 Hz
Printer: HP, LaserJet Enterprise 500, Laser, 800 Mhz
Speakers: Creative Labs, Inspire P7800, 7.1
Channel Surround)
Internet Connection: T3 Ethernet
Storage Drives: 128 GB Internal Solid-State Drive (SSD)
1 TB Internal Hard Drive (HDD) 7200RPM 64M cache
Graphics Card: Nvidia Quadro RTX 4000 8 GB GDDR6 128bit PCI Express 3.0 x16
USB connectivity: 14 USB ports
Activity 2
Server Set Up
Location:
Component Recommendation
Processor: Intel, Xeon W-3175X,
, 3.10 GHZ, 38.5M cache
Memory: DDR4, 256 GB, 3000 MHz
Hard Drive: SSD, 500GB, HDD, 3TB
CD-ROM/DVD: Read 24x, Read/Write 16x, DVD-ROM < 160 ms,
CD-ROM < 140 ms
USB Ports: 2 USB3.0, 2 USB2.0, Front, 2 USB3.0, 2 USB2.0
Back
Video Card: Nvidia, Quadro P1000, 4GB GDDR5, 128bit PCI
Express 3.0 x16
Sound Card: ASUS, Xonar DG 5.1 Channel
Modem: Linksys Small Business RV042, External, 100
Mbps, 802.11 Standard
Network Card(s): Intel X520-DA2, Ethernet: 5.0 GT/s, Wireless,
PCI Express 2.0
Operating System: Windows, Server 2019, 64-bit
Monitor: 32-inch, 3840 x 2160, 60 Hz
Printer: HP, LaserJet Enterprise 500, Laser, 800 Mhz
Speakers: Creative Labs, Inspire P7800, 7.1
Channel Surround)
Internet Connection: T3 Ethernet
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6NETWORK SET UP AND SPECIFICATIONS
Activity 3
Network Design
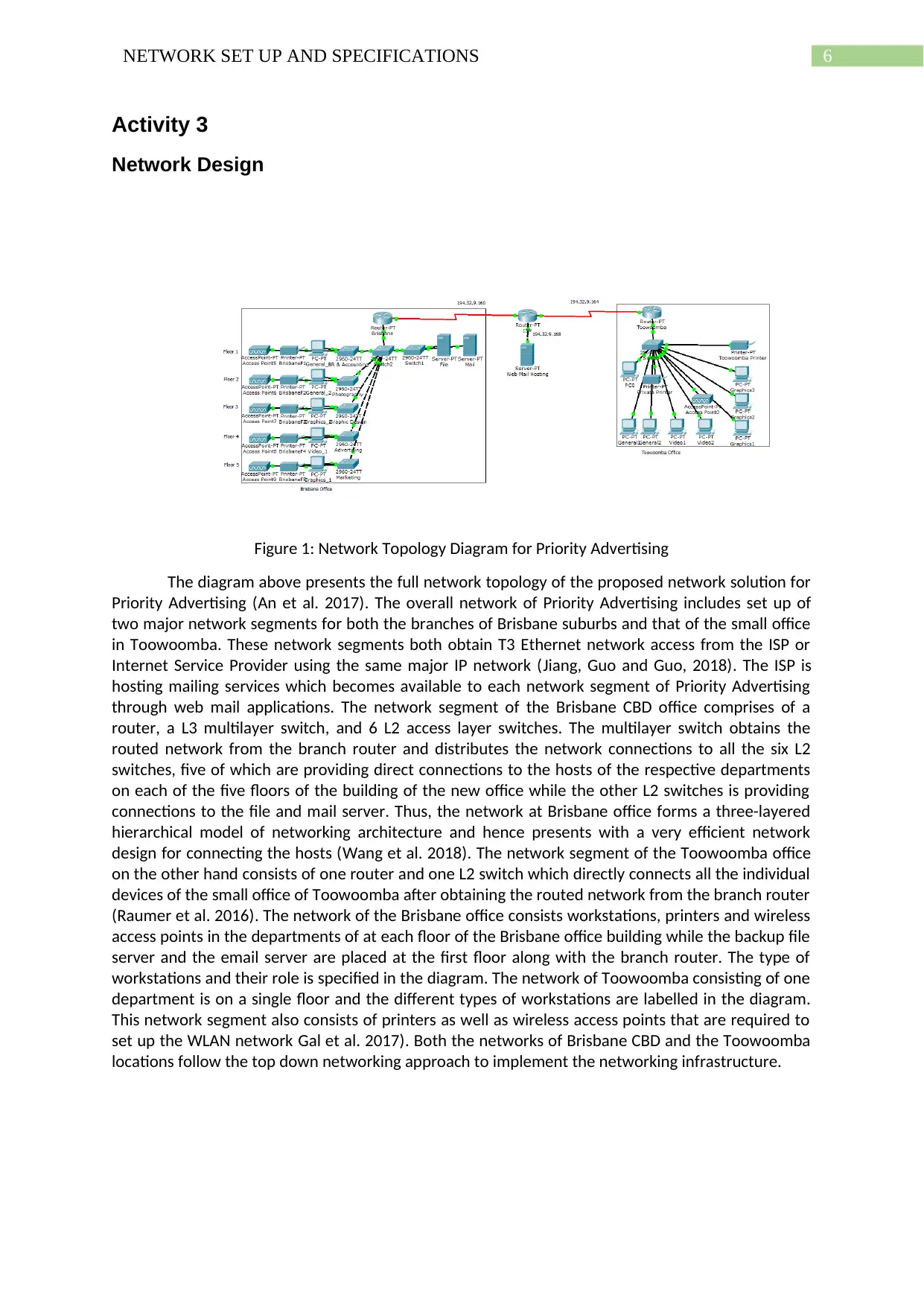
Figure 1: Network Topology Diagram for Priority Advertising
The diagram above presents the full network topology of the proposed network solution for
Priority Advertising (An et al. 2017). The overall network of Priority Advertising includes set up of
two major network segments for both the branches of Brisbane suburbs and that of the small office
in Toowoomba. These network segments both obtain T3 Ethernet network access from the ISP or
Internet Service Provider using the same major IP network (Jiang, Guo and Guo, 2018). The ISP is
hosting mailing services which becomes available to each network segment of Priority Advertising
through web mail applications. The network segment of the Brisbane CBD office comprises of a
router, a L3 multilayer switch, and 6 L2 access layer switches. The multilayer switch obtains the
routed network from the branch router and distributes the network connections to all the six L2
switches, five of which are providing direct connections to the hosts of the respective departments
on each of the five floors of the building of the new office while the other L2 switches is providing
connections to the file and mail server. Thus, the network at Brisbane office forms a three-layered
hierarchical model of networking architecture and hence presents with a very efficient network
design for connecting the hosts (Wang et al. 2018). The network segment of the Toowoomba office
on the other hand consists of one router and one L2 switch which directly connects all the individual
devices of the small office of Toowoomba after obtaining the routed network from the branch router
(Raumer et al. 2016). The network of the Brisbane office consists workstations, printers and wireless
access points in the departments of at each floor of the Brisbane office building while the backup file
server and the email server are placed at the first floor along with the branch router. The type of
workstations and their role is specified in the diagram. The network of Toowoomba consisting of one
department is on a single floor and the different types of workstations are labelled in the diagram.
This network segment also consists of printers as well as wireless access points that are required to
set up the WLAN network Gal et al. 2017). Both the networks of Brisbane CBD and the Toowoomba
locations follow the top down networking approach to implement the networking infrastructure.
Activity 3
Network Design
Figure 1: Network Topology Diagram for Priority Advertising
The diagram above presents the full network topology of the proposed network solution for
Priority Advertising (An et al. 2017). The overall network of Priority Advertising includes set up of
two major network segments for both the branches of Brisbane suburbs and that of the small office
in Toowoomba. These network segments both obtain T3 Ethernet network access from the ISP or
Internet Service Provider using the same major IP network (Jiang, Guo and Guo, 2018). The ISP is
hosting mailing services which becomes available to each network segment of Priority Advertising
through web mail applications. The network segment of the Brisbane CBD office comprises of a
router, a L3 multilayer switch, and 6 L2 access layer switches. The multilayer switch obtains the
routed network from the branch router and distributes the network connections to all the six L2
switches, five of which are providing direct connections to the hosts of the respective departments
on each of the five floors of the building of the new office while the other L2 switches is providing
connections to the file and mail server. Thus, the network at Brisbane office forms a three-layered
hierarchical model of networking architecture and hence presents with a very efficient network
design for connecting the hosts (Wang et al. 2018). The network segment of the Toowoomba office
on the other hand consists of one router and one L2 switch which directly connects all the individual
devices of the small office of Toowoomba after obtaining the routed network from the branch router
(Raumer et al. 2016). The network of the Brisbane office consists workstations, printers and wireless
access points in the departments of at each floor of the Brisbane office building while the backup file
server and the email server are placed at the first floor along with the branch router. The type of
workstations and their role is specified in the diagram. The network of Toowoomba consisting of one
department is on a single floor and the different types of workstations are labelled in the diagram.
This network segment also consists of printers as well as wireless access points that are required to
set up the WLAN network Gal et al. 2017). Both the networks of Brisbane CBD and the Toowoomba
locations follow the top down networking approach to implement the networking infrastructure.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK SET UP AND SPECIFICATIONS
Activity 4
Shared Components
The shared components that have been identified from the overall network of the company
Priority Advertising are the public use printers that have been placed in each of the departments of
both the network segments (Koeller, Lewis and Pooley 2019). Other than these printers, the backup
File server is among the most important shared component that is being shared over the network.
The organizational members are also to enjoy email services that is being provided by the ISP. These
are soon to be managed from within the organization through the Mail Server (Vanwinkle and Kodi
2018). The File server is so store and back up all kinds of relevant information starting from
confidential business data, employee and human resource information, diagnostics and
configuration data of the network as also large volumes of data regarding the graphics and video
production content of final outputs and therefore requires significant storage and processing power
(Monge et al. 2018). The Mail server should also be able to store the mailbox data of all the
members of the company including the media attachments and hence also requires equally
substantial storage as well as compute power. The printers that are being shared are all
multipurpose laserjet color printers that is these printers can also perform the roles of scanners and
copiers while also delivering high quality print outs (Han et al. 2015). The private use printer that is
installed in the room of administrator in the Toowoomba office is specifically for use by the
administrator for safeguarding confidential data. However, access to this printer is only physically
isolated. The network still allows print orders to be sent from other users since the administrator
may be in need of documents from other members.
Activity 5
Internet Service and Installation
The internet services are being provided to the overall network of Priority Advertising
through the Internet Service Provider (Green et al. 2015). The ISP at both the locations of Brisbane
CBD and Toowoomba are directly providing services to the branch routers through their own router.
This is how they are letting both the network segments be connected over the same major network
that has been made available (Han et al. 2015). The type of connection that Priority Advertising is
purchasing from the ISP on a subscription basis is T3 Ethernet network. This means that the
company is regularly receiving over 40 Mbps of network bandwidth. This is the minimum Internet
speed required to allow transfer large files of up to 20 GB in less than an hour. To implement the
network and make sure that it is also reliable at the same time, static IP address was requested from
the ISP for configuring both the routers of branches Brisbane and Toowoomba (Peterside, Zavarsky
and Butakov 2015). These static IP addresses are assigned on the serial ports to set up the wide area
network (WAN) between the two branches via the ISP router. Then network segmentation has been
done so that the subnetworks of each department can be individually managed and can be secured
from security risks by isolation of network segments (Ibrahim 2017). Other than that security in the
overall network has mainly been applied by means of IPsec point to point VPN configured on the
routers manufactured by Cisco (Bensalah, Kamoun and Bahnasse 2017). The connection between
the routers is performed with serial cables, after which the connection between the router and the
switch takes place via straight through Ethernet cables. From one switch to another, connections are
made with crossover Ethernet cables and the end devices are directly connected to switches with
straight through Ethernet cables.
Activity 4
Shared Components
The shared components that have been identified from the overall network of the company
Priority Advertising are the public use printers that have been placed in each of the departments of
both the network segments (Koeller, Lewis and Pooley 2019). Other than these printers, the backup
File server is among the most important shared component that is being shared over the network.
The organizational members are also to enjoy email services that is being provided by the ISP. These
are soon to be managed from within the organization through the Mail Server (Vanwinkle and Kodi
2018). The File server is so store and back up all kinds of relevant information starting from
confidential business data, employee and human resource information, diagnostics and
configuration data of the network as also large volumes of data regarding the graphics and video
production content of final outputs and therefore requires significant storage and processing power
(Monge et al. 2018). The Mail server should also be able to store the mailbox data of all the
members of the company including the media attachments and hence also requires equally
substantial storage as well as compute power. The printers that are being shared are all
multipurpose laserjet color printers that is these printers can also perform the roles of scanners and
copiers while also delivering high quality print outs (Han et al. 2015). The private use printer that is
installed in the room of administrator in the Toowoomba office is specifically for use by the
administrator for safeguarding confidential data. However, access to this printer is only physically
isolated. The network still allows print orders to be sent from other users since the administrator
may be in need of documents from other members.
Activity 5
Internet Service and Installation
The internet services are being provided to the overall network of Priority Advertising
through the Internet Service Provider (Green et al. 2015). The ISP at both the locations of Brisbane
CBD and Toowoomba are directly providing services to the branch routers through their own router.
This is how they are letting both the network segments be connected over the same major network
that has been made available (Han et al. 2015). The type of connection that Priority Advertising is
purchasing from the ISP on a subscription basis is T3 Ethernet network. This means that the
company is regularly receiving over 40 Mbps of network bandwidth. This is the minimum Internet
speed required to allow transfer large files of up to 20 GB in less than an hour. To implement the
network and make sure that it is also reliable at the same time, static IP address was requested from
the ISP for configuring both the routers of branches Brisbane and Toowoomba (Peterside, Zavarsky
and Butakov 2015). These static IP addresses are assigned on the serial ports to set up the wide area
network (WAN) between the two branches via the ISP router. Then network segmentation has been
done so that the subnetworks of each department can be individually managed and can be secured
from security risks by isolation of network segments (Ibrahim 2017). Other than that security in the
overall network has mainly been applied by means of IPsec point to point VPN configured on the
routers manufactured by Cisco (Bensalah, Kamoun and Bahnasse 2017). The connection between
the routers is performed with serial cables, after which the connection between the router and the
switch takes place via straight through Ethernet cables. From one switch to another, connections are
made with crossover Ethernet cables and the end devices are directly connected to switches with
straight through Ethernet cables.
8NETWORK SET UP AND SPECIFICATIONS
Activity 6
Subnet Classification and IP Addressing
Subnet Network
Address
Subnet Mask First Usable
IP Address
Last Usable
IP Address
Broadcast
Address
ISP-Brisbane 194.32.9.16
0
255.255.255.2
52
194.32.9.16
1
194.32.9.162 194.32.9.163
ISP-
Toowoomba
194.32.9.16
4
255.255.255.2
52
194.32.9.16
5
194.32.9.166 194.32.9.167
HR &
Accounting
194.32.10.0 255.255.255.1
28
194.32.10.1 194.32.10.12
6
194.32.10.12
7
Photography 194.32.20.0 255.255.255.1
28
194.32.20.1 194.32.20.12
6
194.32.20.12
7
Graphic
Design
194.32.30.0 255.255.255.1
28
194.32.30.1 194.32.30.12
6
194.32.30.12
7
Advertising 194.32.40.0 255.255.255.1
28
194.32.40.1 194.32.40.12
6
194.32.40.12
7
Marketing 194.32.50.0 255.255.255.1
28
194.32.50.1 194.32.50.12
6
194.32.50.12
7
Servers 194.32.11.0 255.255.255.1
28
194.32.11.1 194.32.11.12
6
194.32.11.12
7
Advertising
Media
(Toowoomb
a)
194.32.60.0 255.255.255.2
40
194.32.60.1 194.32.60.14 194.32.60.15
Device Interface IP Address Subnet Mask Default
Gateway
Brisbane
Router
Serial2/0 194.32.9.162 255.255.255.252 -/-
Toowoomba
Router
Serial2/0 194.32.9.166 255.255.255.252 -/-
ISP Mail Server FastEthernet0 194.32.9.170 255.255.255.252 194.32.9.169
Activity 7
Security Concerns and Mitigation
With the type of connection that has been set up for Priority Advertising, the network can
become vulnerable to external cyber security threats if the IP addresses of the networks of the two
branches get known to the attacker (Vallejo, Feferman and Rothenberg 2018). To mitigate this
problem public IP addresses are assigned to the network users who are connected within the private
LAN by use of the NAT or Network Address Translation process (Meidan et al. 2019). This process is
also at times called SNAT or Secure NAT (Hossain et al. 2016). When configured in routers, the SNAT
router replaces the source IPs with IP addresses configured on it. Since this is not the actual IP
address of the device, it prevents exposure to external threats (Vasilakos et al. 2015). In many
Activity 6
Subnet Classification and IP Addressing
Subnet Network
Address
Subnet Mask First Usable
IP Address
Last Usable
IP Address
Broadcast
Address
ISP-Brisbane 194.32.9.16
0
255.255.255.2
52
194.32.9.16
1
194.32.9.162 194.32.9.163
ISP-
Toowoomba
194.32.9.16
4
255.255.255.2
52
194.32.9.16
5
194.32.9.166 194.32.9.167
HR &
Accounting
194.32.10.0 255.255.255.1
28
194.32.10.1 194.32.10.12
6
194.32.10.12
7
Photography 194.32.20.0 255.255.255.1
28
194.32.20.1 194.32.20.12
6
194.32.20.12
7
Graphic
Design
194.32.30.0 255.255.255.1
28
194.32.30.1 194.32.30.12
6
194.32.30.12
7
Advertising 194.32.40.0 255.255.255.1
28
194.32.40.1 194.32.40.12
6
194.32.40.12
7
Marketing 194.32.50.0 255.255.255.1
28
194.32.50.1 194.32.50.12
6
194.32.50.12
7
Servers 194.32.11.0 255.255.255.1
28
194.32.11.1 194.32.11.12
6
194.32.11.12
7
Advertising
Media
(Toowoomb
a)
194.32.60.0 255.255.255.2
40
194.32.60.1 194.32.60.14 194.32.60.15
Device Interface IP Address Subnet Mask Default
Gateway
Brisbane
Router
Serial2/0 194.32.9.162 255.255.255.252 -/-
Toowoomba
Router
Serial2/0 194.32.9.166 255.255.255.252 -/-
ISP Mail Server FastEthernet0 194.32.9.170 255.255.255.252 194.32.9.169
Activity 7
Security Concerns and Mitigation
With the type of connection that has been set up for Priority Advertising, the network can
become vulnerable to external cyber security threats if the IP addresses of the networks of the two
branches get known to the attacker (Vallejo, Feferman and Rothenberg 2018). To mitigate this
problem public IP addresses are assigned to the network users who are connected within the private
LAN by use of the NAT or Network Address Translation process (Meidan et al. 2019). This process is
also at times called SNAT or Secure NAT (Hossain et al. 2016). When configured in routers, the SNAT
router replaces the source IPs with IP addresses configured on it. Since this is not the actual IP
address of the device, it prevents exposure to external threats (Vasilakos et al. 2015). In many
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORK SET UP AND SPECIFICATIONS
scenarios the network administrators do not define these simple mappings, rather they set up
policies for allowing the gateway device for assigning the mappings depending upon the destination
involved in the communication (Yu et al. 2017). Another method of securing with public and private
IP addresses is by translating the IPv4 address to their respective IPv6 addresses which is not the real
IP however makes the communication compatible with IPv6 based networking environments none
the less.
Conclusion
In conclusion the above report successfully highlights the importance of network topology
diagrams, specifications of hardware components and networking equipment in setting up network
infrastructure of business organizations. The report is observed to present such a network solution
for the marketing and advertising firm Priority Advertising. The report begins by talking about the
goals of the networking project that needs to be met by the proposed network. Then it prescribes
the various configurations of workstations based on the workloads that is to be performed by each
type of workstation. Thereafter that the report classifies the technical specifications of the hardware
components for the File and the Email servers in a specification table. Then the report proceeds
further by presenting and discussing the network topology which has been drawn in the network
simulation software Cisco Packet Tracer. The network solution for Priority Advertising gets followed
by detailed explanations on the shared components and installation of Internet services being
acquired. Next the subnet classification and IP addressing the different subnets and devices are to be
made. After that the report briefly explains the security concerns with public and private IP
addresses and the mitigation technique before coming to an end.
scenarios the network administrators do not define these simple mappings, rather they set up
policies for allowing the gateway device for assigning the mappings depending upon the destination
involved in the communication (Yu et al. 2017). Another method of securing with public and private
IP addresses is by translating the IPv4 address to their respective IPv6 addresses which is not the real
IP however makes the communication compatible with IPv6 based networking environments none
the less.
Conclusion
In conclusion the above report successfully highlights the importance of network topology
diagrams, specifications of hardware components and networking equipment in setting up network
infrastructure of business organizations. The report is observed to present such a network solution
for the marketing and advertising firm Priority Advertising. The report begins by talking about the
goals of the networking project that needs to be met by the proposed network. Then it prescribes
the various configurations of workstations based on the workloads that is to be performed by each
type of workstation. Thereafter that the report classifies the technical specifications of the hardware
components for the File and the Email servers in a specification table. Then the report proceeds
further by presenting and discussing the network topology which has been drawn in the network
simulation software Cisco Packet Tracer. The network solution for Priority Advertising gets followed
by detailed explanations on the shared components and installation of Internet services being
acquired. Next the subnet classification and IP addressing the different subnets and devices are to be
made. After that the report briefly explains the security concerns with public and private IP
addresses and the mitigation technique before coming to an end.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORK SET UP AND SPECIFICATIONS
References
An, K., Chiu, Y.C., Hu, X. and Chen, X., 2017. A network partitioning algorithmic approach for
macroscopic fundamental diagram-based hierarchical traffic network management. IEEE
Transactions on Intelligent Transportation Systems, 19(4), pp.1130-1139.
Bensalah, F., El Kamoun, N. and Bahnasse, A., 2017. Evaluation of tunnel layer impact on VOIP
performances (IP-MPLS-MPLS VPN-MPLS VPN IPsec). International Journal of Computer Science and
Network Security (IJCSNS), 17(3), p.87.
Elbers, W. and Weygaert, R.V.D., 2019. Persistent topology of the reionization bubble network–I.
Formalism and phenomenology. Monthly Notices of the Royal Astronomical Society, 486(2), pp.1523-
1538.
Gal, E., London, M., Globerson, A., Ramaswamy, S., Reimann, M.W., Muller, E., Markram, H. and
Segev, I., 2017. Rich cell-type-specific network topology in neocortical microcircuitry. Nature
neuroscience, 20(7), p.1004.
Green, M., MacFarland, D.C., Smestad, D.R. and Shue, C.A., 2015, October. Characterizing network-
based moving target defenses. In Proceedings of the Second ACM Workshop on Moving Target
Defense (pp. 31-35). ACM.
Han, B., Gopalakrishnan, V., Ji, L. and Lee, S., 2015. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine, 53(2), pp.90-97.
Han, B., Gopalakrishnan, V., Ji, L. and Lee, S., 2015. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine, 53(2), pp.90-97.
Hossain, M.A., Printder, D., Jahan, S. and Hussain, M., 2016. Performance analysis of three transition
mechanisms between IPv6 network and IPv4 network: dual stack tunneling and translation.
International Journal of Computer, 20(1), pp.217-228.
Ibrahim, L., 2017. Virtual Private Network (VPN) Management and IPSec Tunneling Technology.
Middle East, 1.
Jiang, Y., Guo, P. and Guo, M., 2018, December. A Network Topology Discovery Model Based on
OSPF. In 2018 3rd Joint International Information Technology, Mechanical and Electronic Engineering
Conference (JIMEC 2018). Atlantis Press.
Koeller, J., Lewis, M. and Pooley, D., 2019. Using Apache Spark™ for Distributed Computation on a
Network of Workstations. In Proceedings of the International Conference on Parallel and Distributed
Processing Techniques and Applications (PDPTA) (pp. 26-31). The Steering Committee of The World
Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
Meidan, Y., Sachidananda, V., Elovici, Y. and Shabtai, A., 2019. Privacy-Preserving Detection of IoT
Devices Connected Behind a NAT in a Smart Home Setup. arXiv preprint arXiv:1905.13430.
Monge, Z.A., Stanley, M.L., Geib, B.R., Davis, S.W. and Cabeza, R., 2018. Functional networks
underlying item and source memory: shared and distinct network components and age-related
differences. Neurobiology of aging, 69, pp.140-150.
Peterside, G.B., Zavarsky, P. and Butakov, S., 2015, December. Automated security configuration
checklist for a cisco IPsec VPN router using SCAP 1.2. In 2015 10th International Conference for
Internet Technology and Secured Transactions (ICITST) (pp. 355-360). IEEE.
References
An, K., Chiu, Y.C., Hu, X. and Chen, X., 2017. A network partitioning algorithmic approach for
macroscopic fundamental diagram-based hierarchical traffic network management. IEEE
Transactions on Intelligent Transportation Systems, 19(4), pp.1130-1139.
Bensalah, F., El Kamoun, N. and Bahnasse, A., 2017. Evaluation of tunnel layer impact on VOIP
performances (IP-MPLS-MPLS VPN-MPLS VPN IPsec). International Journal of Computer Science and
Network Security (IJCSNS), 17(3), p.87.
Elbers, W. and Weygaert, R.V.D., 2019. Persistent topology of the reionization bubble network–I.
Formalism and phenomenology. Monthly Notices of the Royal Astronomical Society, 486(2), pp.1523-
1538.
Gal, E., London, M., Globerson, A., Ramaswamy, S., Reimann, M.W., Muller, E., Markram, H. and
Segev, I., 2017. Rich cell-type-specific network topology in neocortical microcircuitry. Nature
neuroscience, 20(7), p.1004.
Green, M., MacFarland, D.C., Smestad, D.R. and Shue, C.A., 2015, October. Characterizing network-
based moving target defenses. In Proceedings of the Second ACM Workshop on Moving Target
Defense (pp. 31-35). ACM.
Han, B., Gopalakrishnan, V., Ji, L. and Lee, S., 2015. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine, 53(2), pp.90-97.
Han, B., Gopalakrishnan, V., Ji, L. and Lee, S., 2015. Network function virtualization: Challenges and
opportunities for innovations. IEEE Communications Magazine, 53(2), pp.90-97.
Hossain, M.A., Printder, D., Jahan, S. and Hussain, M., 2016. Performance analysis of three transition
mechanisms between IPv6 network and IPv4 network: dual stack tunneling and translation.
International Journal of Computer, 20(1), pp.217-228.
Ibrahim, L., 2017. Virtual Private Network (VPN) Management and IPSec Tunneling Technology.
Middle East, 1.
Jiang, Y., Guo, P. and Guo, M., 2018, December. A Network Topology Discovery Model Based on
OSPF. In 2018 3rd Joint International Information Technology, Mechanical and Electronic Engineering
Conference (JIMEC 2018). Atlantis Press.
Koeller, J., Lewis, M. and Pooley, D., 2019. Using Apache Spark™ for Distributed Computation on a
Network of Workstations. In Proceedings of the International Conference on Parallel and Distributed
Processing Techniques and Applications (PDPTA) (pp. 26-31). The Steering Committee of The World
Congress in Computer Science, Computer Engineering and Applied Computing (WorldComp).
Meidan, Y., Sachidananda, V., Elovici, Y. and Shabtai, A., 2019. Privacy-Preserving Detection of IoT
Devices Connected Behind a NAT in a Smart Home Setup. arXiv preprint arXiv:1905.13430.
Monge, Z.A., Stanley, M.L., Geib, B.R., Davis, S.W. and Cabeza, R., 2018. Functional networks
underlying item and source memory: shared and distinct network components and age-related
differences. Neurobiology of aging, 69, pp.140-150.
Peterside, G.B., Zavarsky, P. and Butakov, S., 2015, December. Automated security configuration
checklist for a cisco IPsec VPN router using SCAP 1.2. In 2015 10th International Conference for
Internet Technology and Secured Transactions (ICITST) (pp. 355-360). IEEE.

11NETWORK SET UP AND SPECIFICATIONS
Raumer, D., Gallenmüller, S., Emmerich, P., Märdian, L. and Carle, G., 2016, October. Efficient serving
of VPN endpoints on COTS server hardware. In 2016 5th IEEE International Conference on Cloud
Networking (Cloudnet) (pp. 164-169). IEEE.
Vallejo, J.S.M., Feferman, D.L. and Rothenberg, C.E., 2018, July. Network Address Translation using a
Programmable Dataplane Processor. In 17º Workshop em Desempenho de Sistemas Computacionais
e de Comunicação (WPerformance 2018) (Vol. 17, No. 1/2018). SBC.
Vanwinkle, S. and Kodi, A.K., 2018. SHARP: Shared Heterogeneous Architecture with Reconfigurable
Photonic Network-on-Chip. ACM Journal on Emerging Technologies in Computing Systems (JETC),
14(2), p.25.
Vasilakos, A.V., Li, Z., Simon, G. and You, W., 2015. Information centric network: Research challenges
and opportunities. Journal of network and computer applications, 52, pp.1-10.
Wang, Z., Ran, Z., Chen, X., Liang, Y., Ren, Z. and He, Y., 2018. Critical Node Identification for Electric
Power Communication Network Based on Topology and Services Characteristics. In MATEC Web of
Conferences (Vol. 246, p. 03023). EDP Sciences.
Yu, T., Fayaz, S.K., Collins, M.P., Sekar, V. and Seshan, S., 2017, February. PSI: Precise Security
Instrumentation for Enterprise Networks. In NDSS.
Raumer, D., Gallenmüller, S., Emmerich, P., Märdian, L. and Carle, G., 2016, October. Efficient serving
of VPN endpoints on COTS server hardware. In 2016 5th IEEE International Conference on Cloud
Networking (Cloudnet) (pp. 164-169). IEEE.
Vallejo, J.S.M., Feferman, D.L. and Rothenberg, C.E., 2018, July. Network Address Translation using a
Programmable Dataplane Processor. In 17º Workshop em Desempenho de Sistemas Computacionais
e de Comunicação (WPerformance 2018) (Vol. 17, No. 1/2018). SBC.
Vanwinkle, S. and Kodi, A.K., 2018. SHARP: Shared Heterogeneous Architecture with Reconfigurable
Photonic Network-on-Chip. ACM Journal on Emerging Technologies in Computing Systems (JETC),
14(2), p.25.
Vasilakos, A.V., Li, Z., Simon, G. and You, W., 2015. Information centric network: Research challenges
and opportunities. Journal of network and computer applications, 52, pp.1-10.
Wang, Z., Ran, Z., Chen, X., Liang, Y., Ren, Z. and He, Y., 2018. Critical Node Identification for Electric
Power Communication Network Based on Topology and Services Characteristics. In MATEC Web of
Conferences (Vol. 246, p. 03023). EDP Sciences.
Yu, T., Fayaz, S.K., Collins, M.P., Sekar, V. and Seshan, S., 2017, February. PSI: Precise Security
Instrumentation for Enterprise Networks. In NDSS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





