Network Solution Design: Flee Technology Company Project
VerifiedAdded on 2021/02/21
|12
|3508
|68
Project
AI Summary
This assignment provides a comprehensive network solution design for Flee Technology, a small-medium enterprise (SME) in the Internet of Things (IoT) business. It begins with an introduction to networks and the rationale for choosing Flee Technology, followed by detailed network requirements, including bandwidth, connectivity, interfaces, servers, routers, and firewalls. The solution is presented in two phases, with network topology diagrams illustrating both Phase 1 (basic connectivity) and Phase 2 (enhanced security and redundancy). The assignment outlines the network's design, including core and access switches, and describes the services and applications offered, such as FTP, email programs, file sharing, email services, internet access, and printing services. The design prioritizes network security through firewalls, encryption, and antivirus measures. The conclusion emphasizes the importance of a robust network infrastructure for modern businesses, particularly those in the technology sector, and provides references to relevant literature.

NETWORK
COMPREHENSION
COMPREHENSION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
REQUIREMENTS..........................................................................................................................1
SOLUTION DESIGNED................................................................................................................3
Network Topology.......................................................................................................................4
Solution Description....................................................................................................................5
Services and Applications............................................................................................................6
Interfaces and Technologies........................................................................................................7
ANALYSIS AND EVOLUTION....................................................................................................8
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10
INTRODUCTION...........................................................................................................................1
REQUIREMENTS..........................................................................................................................1
SOLUTION DESIGNED................................................................................................................3
Network Topology.......................................................................................................................4
Solution Description....................................................................................................................5
Services and Applications............................................................................................................6
Interfaces and Technologies........................................................................................................7
ANALYSIS AND EVOLUTION....................................................................................................8
CONCLUSION................................................................................................................................9
REFERENCES..............................................................................................................................10

INTRODUCTION
Network can be defined as a group which helps in connecting two or more computers or
system or devices together (Kobo, Abu-Mahfouz and Hancke, 2017). It not only helps in
connecting two or more devices together but also helps in exchanging data between devices
using connection between nodes. There are various kinds of network that are available that can
be used to connect two or more than two devices together like LAN, MAN, WAN and many
more. Each of them are used as per the network requirements of the system, devices or
organization. The main aim of this assignment is to propose and design a network solution for a
small medium enterprise. This assignment will further include requirements of the network that
will be used to propose a solution, high level design solution.
Organization Chosen:
A small Flee technology company of internet of things business has been chosen. This
business has been chosen because organizations in this business are required to have a strong and
secure network in order to maintain their data or information and communication connection as
well. This company is an information technology company that focuses on connecting people
through space technology. They sell various kinds of network portal to the companies. Flee is a
small-scale business with less than 50 employees and is located in Beverley, SA Australia. They
provide services like Internet of things, satellite communication etc.
REQUIREMENTS
There are various components or things that are required to propose a solution so that proper
service can be delivered according to the network capacity (Agrawal and et.al., 2017). These
requirements will focus on all the end to end connections, technologies that will be used in
designing a solution, protocols, security aspects and many more. These requirements will
include: Network and service requirements, security requirements, wireless network
requirements. Below explained are the general terminologies that are mostly used in network
designing.
Bandwidth: bandwidth is a maximum rate at which data is transferred between devices across a
given path. These bandwidths are extremely important whenever network design comes into
picture and is used in wireless/wired communication, digital communication etc. there are three
types of bandwidth that are commonly used: network bandwidth, digital bandwidth and data
bandwidth.
1
Network can be defined as a group which helps in connecting two or more computers or
system or devices together (Kobo, Abu-Mahfouz and Hancke, 2017). It not only helps in
connecting two or more devices together but also helps in exchanging data between devices
using connection between nodes. There are various kinds of network that are available that can
be used to connect two or more than two devices together like LAN, MAN, WAN and many
more. Each of them are used as per the network requirements of the system, devices or
organization. The main aim of this assignment is to propose and design a network solution for a
small medium enterprise. This assignment will further include requirements of the network that
will be used to propose a solution, high level design solution.
Organization Chosen:
A small Flee technology company of internet of things business has been chosen. This
business has been chosen because organizations in this business are required to have a strong and
secure network in order to maintain their data or information and communication connection as
well. This company is an information technology company that focuses on connecting people
through space technology. They sell various kinds of network portal to the companies. Flee is a
small-scale business with less than 50 employees and is located in Beverley, SA Australia. They
provide services like Internet of things, satellite communication etc.
REQUIREMENTS
There are various components or things that are required to propose a solution so that proper
service can be delivered according to the network capacity (Agrawal and et.al., 2017). These
requirements will focus on all the end to end connections, technologies that will be used in
designing a solution, protocols, security aspects and many more. These requirements will
include: Network and service requirements, security requirements, wireless network
requirements. Below explained are the general terminologies that are mostly used in network
designing.
Bandwidth: bandwidth is a maximum rate at which data is transferred between devices across a
given path. These bandwidths are extremely important whenever network design comes into
picture and is used in wireless/wired communication, digital communication etc. there are three
types of bandwidth that are commonly used: network bandwidth, digital bandwidth and data
bandwidth.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Connection: Connectivity is another important requirement of the network. In order to access
network, it is important to have connectivity within the network. Old network used to use
ethernet cables for direct physical connectivity but today most of the times wireless bridge setups
are used for connectivity that helps in connecting to its core switches (Gao and et.al., 2016). But
for wired connection ethernet cables are used.
Interface: Interface is a kind of interconnection point between devices and network. These
interfaces are used to provide redundancy between switches, routers, aggregation switches etc.
All network interfaces have some kind of network address which further consist of node
identifier, node ID, port number. Basic function of these interfaces is connecting, disconnecting
and message passing.
Server: Server is a kind of computer system which is used as a central repository of various
programs, data that are mainly shared by users present in the network. There is no need to buy a
new system for server, old unused systems can also be used as network servers for the systems
but it should have huge storage space so that all kind of data can be stored within it without any
errors or issues.
Router: Router is another most commonly used network device with is mainly used to forward
any kind of data packets between systems that are connected to each other within a network
(Shangin and Pardalos, 2016). A router is located at gateway of the network and is connected to
two or more than two devices are connected to a network. It can also be said that routers are used
to perform traffic directing function on the internet. There are various kinds of routers like
virtual, core, edge, wired or wireless routers.
Firewall: Another important element which is required to be used when designing a network is a
Firewall. It is a kind of a system which is mainly used to prevent unauthorized access from a
network. It can be used in both the forms i.e. in the form of hardware and software or in both the
forms.
Devices: there are various kinds of devices are used within a network design such as secure
network devices, access network devices, computer systems connecting devices and many more.
Different types of devices are used for different purposes
Core Switches: Core switches are high capacity switches that are placed at the backbone of the
network. These switches serve as a gateway for internet or WAN. In simple words its work is to
move a packet from point A to point B as fast as possible.
2
network, it is important to have connectivity within the network. Old network used to use
ethernet cables for direct physical connectivity but today most of the times wireless bridge setups
are used for connectivity that helps in connecting to its core switches (Gao and et.al., 2016). But
for wired connection ethernet cables are used.
Interface: Interface is a kind of interconnection point between devices and network. These
interfaces are used to provide redundancy between switches, routers, aggregation switches etc.
All network interfaces have some kind of network address which further consist of node
identifier, node ID, port number. Basic function of these interfaces is connecting, disconnecting
and message passing.
Server: Server is a kind of computer system which is used as a central repository of various
programs, data that are mainly shared by users present in the network. There is no need to buy a
new system for server, old unused systems can also be used as network servers for the systems
but it should have huge storage space so that all kind of data can be stored within it without any
errors or issues.
Router: Router is another most commonly used network device with is mainly used to forward
any kind of data packets between systems that are connected to each other within a network
(Shangin and Pardalos, 2016). A router is located at gateway of the network and is connected to
two or more than two devices are connected to a network. It can also be said that routers are used
to perform traffic directing function on the internet. There are various kinds of routers like
virtual, core, edge, wired or wireless routers.
Firewall: Another important element which is required to be used when designing a network is a
Firewall. It is a kind of a system which is mainly used to prevent unauthorized access from a
network. It can be used in both the forms i.e. in the form of hardware and software or in both the
forms.
Devices: there are various kinds of devices are used within a network design such as secure
network devices, access network devices, computer systems connecting devices and many more.
Different types of devices are used for different purposes
Core Switches: Core switches are high capacity switches that are placed at the backbone of the
network. These switches serve as a gateway for internet or WAN. In simple words its work is to
move a packet from point A to point B as fast as possible.
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Access switches: Access switches are those switches that directly interacts with the user as these
switches connects majority of devices to a network (Pérez and et.al., 2017). So, it can be said that
these switches are responsible for connecting devices to network it also helps in providing
connections to users through ethernet ports of their devices. without any issue or error.
Wireless Access points: it is a device which helps in connecting wireless devices to the network
using Wi-Fi or by using any other related standards. It is mostly connected to a switch or router
that is being used currently. Wireless LAN helps in setting or providing Wi-Fi access to wireless
device users.
Network and service requirements
Introduction of 1 GBPS ports for core switches
Network should be accessible through internet
Quality of service should be based on media or service nature
Security requirements
Firewall should be introduced in order to protect the network.
Network boundaries shall be defined so that all the network connections can be filtered and
communication traffic can be identified by type, source, destination identifier.
LAN should be encrypted for all connections.
All the connections present in the network that carried sensitive information like user id or
passwords etc. should be encrypted or digitally certified.
All the PCs should have their own Anti-virus and other than this a new Anti-Virus should
also be provided by the server so that internal network security can be increased.
Wireless network requirements
Wireless access is required so that users will be able to access internet from point A to point
B.
There is no need of wireless access controller
Wireless Access should be able to cover both the buildings areas.
SOLUTION DESIGNED
There are two phases through which network designing can be completed. Phase 1 network
topology diagram is designed in order to introduce network capabilities with minimum required
investment whereas phase 2 network designed with more security, more efficient, fast network
with better connectivity.
3
switches connects majority of devices to a network (Pérez and et.al., 2017). So, it can be said that
these switches are responsible for connecting devices to network it also helps in providing
connections to users through ethernet ports of their devices. without any issue or error.
Wireless Access points: it is a device which helps in connecting wireless devices to the network
using Wi-Fi or by using any other related standards. It is mostly connected to a switch or router
that is being used currently. Wireless LAN helps in setting or providing Wi-Fi access to wireless
device users.
Network and service requirements
Introduction of 1 GBPS ports for core switches
Network should be accessible through internet
Quality of service should be based on media or service nature
Security requirements
Firewall should be introduced in order to protect the network.
Network boundaries shall be defined so that all the network connections can be filtered and
communication traffic can be identified by type, source, destination identifier.
LAN should be encrypted for all connections.
All the connections present in the network that carried sensitive information like user id or
passwords etc. should be encrypted or digitally certified.
All the PCs should have their own Anti-virus and other than this a new Anti-Virus should
also be provided by the server so that internal network security can be increased.
Wireless network requirements
Wireless access is required so that users will be able to access internet from point A to point
B.
There is no need of wireless access controller
Wireless Access should be able to cover both the buildings areas.
SOLUTION DESIGNED
There are two phases through which network designing can be completed. Phase 1 network
topology diagram is designed in order to introduce network capabilities with minimum required
investment whereas phase 2 network designed with more security, more efficient, fast network
with better connectivity.
3

Network Topology
Network topology can be defined as a topological structure of a network that can be
described both physically and logically (Abdelwahab and et.al., 2016). It can also be defined as
arrangement of all the elements present in the communication network. All the connection
between devices are moulded as lines or links between all the present nodes. There are mainly
two types of topologies physical and logical network topology. Physical topology focuses on
physical layout of the connected nodes or devices. Whereas logical topology focuses on data
transfer pattern between network nodes.
Network topology phase 1
It is a simple network diagram with a secure network designed with a firewall. Currently
there is no connection installed between old and new building. This existing network does not
even have a router to provide redundancy. There is a requirement of few things to be installed
such as a router, point to point wireless interface, additional firewall and switches. Phase one
diagram will provide connectivity with less security and reduced efficiency. Below diagram
shows network topology phase 1 diagram.
Figure 1 network topology phase 1
Network topology phase 2
In phase 2 design a network cluster has been made in order to implement redundancy, a
greater number of firewall and core switches has also been used so that better redundancy and
connectivity can be provided. In this diagram a point to point wireless interface has also been
introduced in order to improve connectivity between old and new building. Wireless interface
4
Network topology can be defined as a topological structure of a network that can be
described both physically and logically (Abdelwahab and et.al., 2016). It can also be defined as
arrangement of all the elements present in the communication network. All the connection
between devices are moulded as lines or links between all the present nodes. There are mainly
two types of topologies physical and logical network topology. Physical topology focuses on
physical layout of the connected nodes or devices. Whereas logical topology focuses on data
transfer pattern between network nodes.
Network topology phase 1
It is a simple network diagram with a secure network designed with a firewall. Currently
there is no connection installed between old and new building. This existing network does not
even have a router to provide redundancy. There is a requirement of few things to be installed
such as a router, point to point wireless interface, additional firewall and switches. Phase one
diagram will provide connectivity with less security and reduced efficiency. Below diagram
shows network topology phase 1 diagram.
Figure 1 network topology phase 1
Network topology phase 2
In phase 2 design a network cluster has been made in order to implement redundancy, a
greater number of firewall and core switches has also been used so that better redundancy and
connectivity can be provided. In this diagram a point to point wireless interface has also been
introduced in order to improve connectivity between old and new building. Wireless interface
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
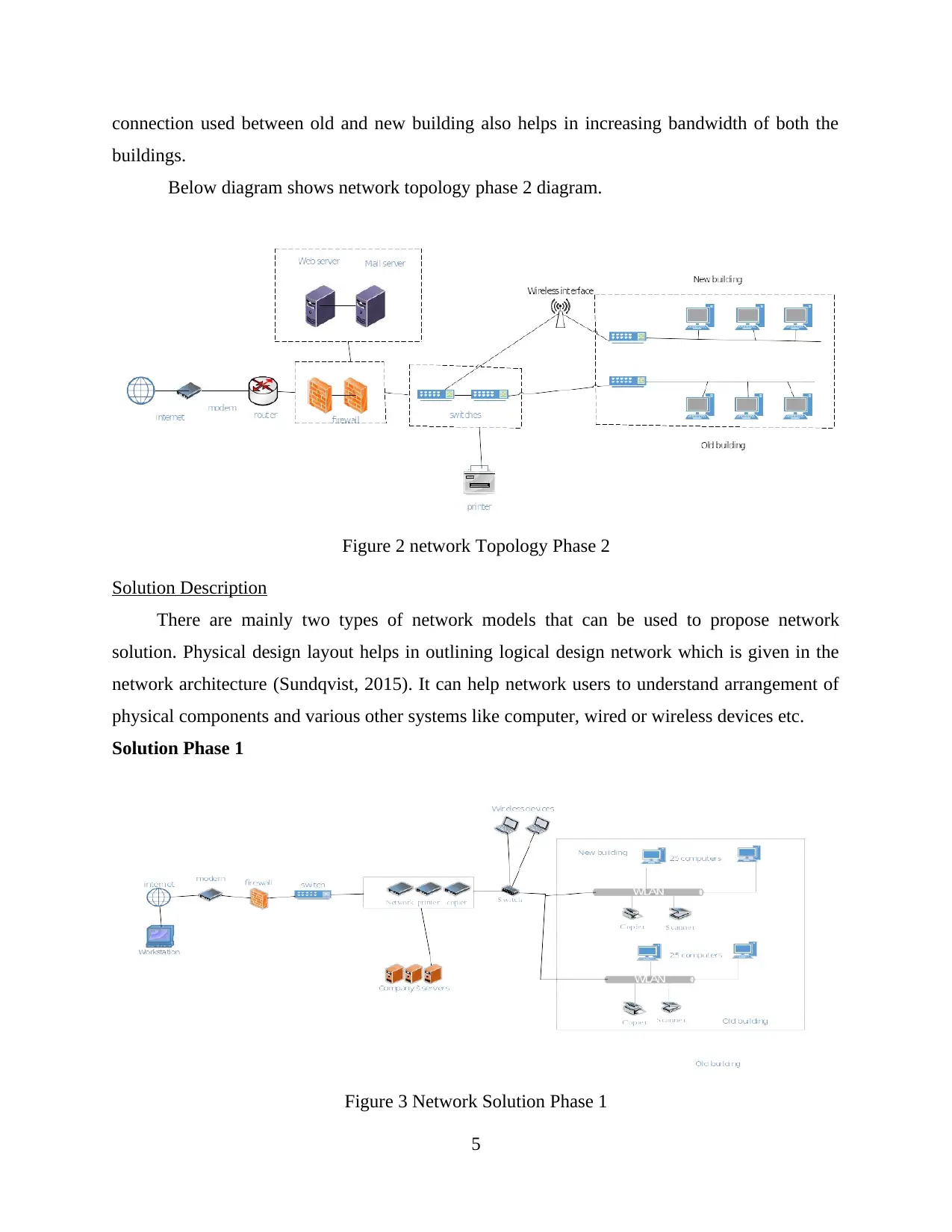
connection used between old and new building also helps in increasing bandwidth of both the
buildings.
Below diagram shows network topology phase 2 diagram.
Figure 2 network Topology Phase 2
Solution Description
There are mainly two types of network models that can be used to propose network
solution. Physical design layout helps in outlining logical design network which is given in the
network architecture (Sundqvist, 2015). It can help network users to understand arrangement of
physical components and various other systems like computer, wired or wireless devices etc.
Solution Phase 1
Figure 3 Network Solution Phase 1
5
buildings.
Below diagram shows network topology phase 2 diagram.
Figure 2 network Topology Phase 2
Solution Description
There are mainly two types of network models that can be used to propose network
solution. Physical design layout helps in outlining logical design network which is given in the
network architecture (Sundqvist, 2015). It can help network users to understand arrangement of
physical components and various other systems like computer, wired or wireless devices etc.
Solution Phase 1
Figure 3 Network Solution Phase 1
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
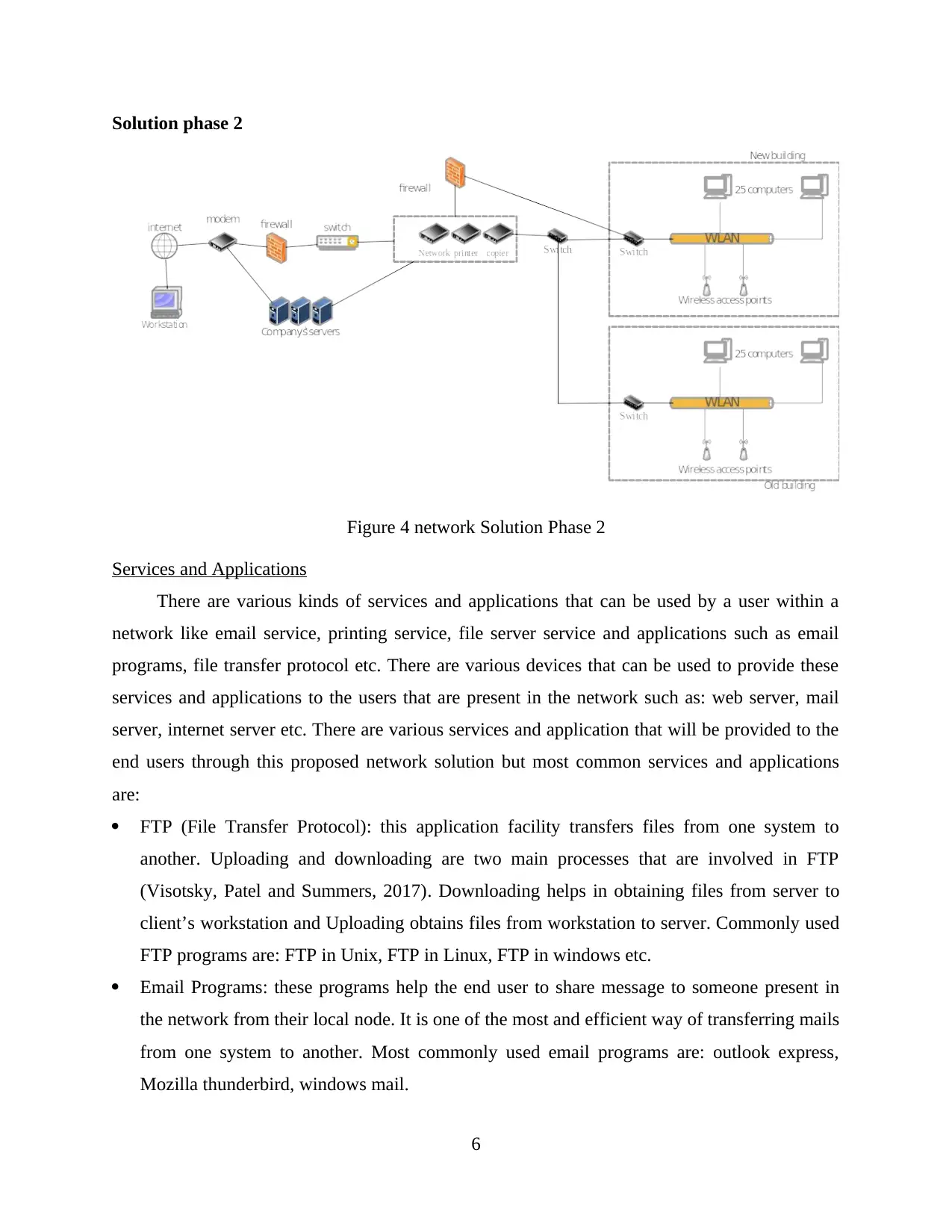
Solution phase 2
Figure 4 network Solution Phase 2
Services and Applications
There are various kinds of services and applications that can be used by a user within a
network like email service, printing service, file server service and applications such as email
programs, file transfer protocol etc. There are various devices that can be used to provide these
services and applications to the users that are present in the network such as: web server, mail
server, internet server etc. There are various services and application that will be provided to the
end users through this proposed network solution but most common services and applications
are:
FTP (File Transfer Protocol): this application facility transfers files from one system to
another. Uploading and downloading are two main processes that are involved in FTP
(Visotsky, Patel and Summers, 2017). Downloading helps in obtaining files from server to
client’s workstation and Uploading obtains files from workstation to server. Commonly used
FTP programs are: FTP in Unix, FTP in Linux, FTP in windows etc.
Email Programs: these programs help the end user to share message to someone present in
the network from their local node. It is one of the most and efficient way of transferring mails
from one system to another. Most commonly used email programs are: outlook express,
Mozilla thunderbird, windows mail.
6
Figure 4 network Solution Phase 2
Services and Applications
There are various kinds of services and applications that can be used by a user within a
network like email service, printing service, file server service and applications such as email
programs, file transfer protocol etc. There are various devices that can be used to provide these
services and applications to the users that are present in the network such as: web server, mail
server, internet server etc. There are various services and application that will be provided to the
end users through this proposed network solution but most common services and applications
are:
FTP (File Transfer Protocol): this application facility transfers files from one system to
another. Uploading and downloading are two main processes that are involved in FTP
(Visotsky, Patel and Summers, 2017). Downloading helps in obtaining files from server to
client’s workstation and Uploading obtains files from workstation to server. Commonly used
FTP programs are: FTP in Unix, FTP in Linux, FTP in windows etc.
Email Programs: these programs help the end user to share message to someone present in
the network from their local node. It is one of the most and efficient way of transferring mails
from one system to another. Most commonly used email programs are: outlook express,
Mozilla thunderbird, windows mail.
6

File sharing: File sharing is a service through which access to digital media can be provided
or distributed like multimedia, electronic books etc. File sharing can be achieved in many
ways and can be done through centralized servers on network, manual sharing using
removable media, world wide web based hyperlinked documents and many more.
Email service: It is a service through which emails can be exchanged between people using
electronic devices. It is one of the most efficient way in which emails can be transferred by
the users that are present in the same network. Many times, many computer network email
services require both sender and recipient both present in the same network and active at the
same time. For this network there is only one requirement i.e. both the sender and recipient
are required to be present in the same network.
Internet service: it is one of the most common and useful service will be provided by the
network to their users. It is a service win which users can search information on the present
network. It can help the users of the network to network upload or download any information
which is present in the network.
Printing service: Printing service is also one of the most common service which is provided
to the network users. In this Print service is provided to users where they can print any
information which is present in the network. Print servers present in the network accept print
job from the network users and print documents in the most appropriate manner.
Interfaces and Technologies
Network technologies can be defined as technologies that helps in connecting two or more
than two devices together so that they can communicate information with each other. These
connections can either be simple dial up connections or complex internet themselves. There are
various kinds of network connections that can be used in connecting two or more devices
together (Maitland and Bharania, 2017). Whereas interfaces are a type of hardware of software
interfaces that are present between two pieces of equipment or protocol layers in a computer
network. Network interfaces have a unique network address which consist of port number, node
identifier and a unique node ID. Technologies and interfaces used in this proposed solution are:
LAN: LAN can be defined as a group of network devices that allows communication
between connected devices. An organization’s private owner has complete ownership of the
local area network rather than the public network. As compared to WAN, LAN has a bit of
propagation delay. It is mostly used in small areas such as: Schools, Hospitals, Colleges etc.
7
or distributed like multimedia, electronic books etc. File sharing can be achieved in many
ways and can be done through centralized servers on network, manual sharing using
removable media, world wide web based hyperlinked documents and many more.
Email service: It is a service through which emails can be exchanged between people using
electronic devices. It is one of the most efficient way in which emails can be transferred by
the users that are present in the same network. Many times, many computer network email
services require both sender and recipient both present in the same network and active at the
same time. For this network there is only one requirement i.e. both the sender and recipient
are required to be present in the same network.
Internet service: it is one of the most common and useful service will be provided by the
network to their users. It is a service win which users can search information on the present
network. It can help the users of the network to network upload or download any information
which is present in the network.
Printing service: Printing service is also one of the most common service which is provided
to the network users. In this Print service is provided to users where they can print any
information which is present in the network. Print servers present in the network accept print
job from the network users and print documents in the most appropriate manner.
Interfaces and Technologies
Network technologies can be defined as technologies that helps in connecting two or more
than two devices together so that they can communicate information with each other. These
connections can either be simple dial up connections or complex internet themselves. There are
various kinds of network connections that can be used in connecting two or more devices
together (Maitland and Bharania, 2017). Whereas interfaces are a type of hardware of software
interfaces that are present between two pieces of equipment or protocol layers in a computer
network. Network interfaces have a unique network address which consist of port number, node
identifier and a unique node ID. Technologies and interfaces used in this proposed solution are:
LAN: LAN can be defined as a group of network devices that allows communication
between connected devices. An organization’s private owner has complete ownership of the
local area network rather than the public network. As compared to WAN, LAN has a bit of
propagation delay. It is mostly used in small areas such as: Schools, Hospitals, Colleges etc.
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

WAN: Wide are network covers more are as compared to LAN like country, continent etc. it
is quite expensive and is not owned by a single organization so for this satellite medium is
used to connect devices together. WAN has the capability to connect various LAN together
and can provide high speed to all the devices as compared to LAN. Due to this it is quite
expensive as compared to LAN.
ANALYSIS AND EVOLUTION
According to the network design configuration a basic configuration has been made in which
completely compatible with the network system. According to this configuration all the devices
connected to the network can access point to point wireless access point and can send or receive
any kind of data. Each of them has a unique identification number printed on it. The above
solution proposed is designed in such a manner that it handles all the requirements and functions
of the network in an easy and efficient manner. All the network requirements have been clearly
shown and explained in the above network design proposed solution. Modem router, core
switches, firewall
Compliance can be defined as a set of standards that helps in defining the overall security of
the network at its planning stage (Hynds, Nasr and O'Dwyer, 2019). It is important for all
organizations to adhere these compliances in order or maintain network security. It also helps the
users to understand what is the right thing to do in order to maintain network security. There are
various kinds of compliances that can be used by small or medium sized organizations. Each and
every network proposed solution should have their defined compliances as per the requirement
of the organization vendors of the network should indicate or propose these compliances in three
forms: first is comply, second is partially comply and third is no comply. These compliances
play a vital role in understanding the main reason behind the project and what level of security is
required by the organization and for small or medium sized organization it is extremely
important to be understood and complied.
Requirement Statements Comply/No Comply/Partially
Comply
The solution needs to introduce at least 1 GBPS ports for
core switches
Comply
8
is quite expensive and is not owned by a single organization so for this satellite medium is
used to connect devices together. WAN has the capability to connect various LAN together
and can provide high speed to all the devices as compared to LAN. Due to this it is quite
expensive as compared to LAN.
ANALYSIS AND EVOLUTION
According to the network design configuration a basic configuration has been made in which
completely compatible with the network system. According to this configuration all the devices
connected to the network can access point to point wireless access point and can send or receive
any kind of data. Each of them has a unique identification number printed on it. The above
solution proposed is designed in such a manner that it handles all the requirements and functions
of the network in an easy and efficient manner. All the network requirements have been clearly
shown and explained in the above network design proposed solution. Modem router, core
switches, firewall
Compliance can be defined as a set of standards that helps in defining the overall security of
the network at its planning stage (Hynds, Nasr and O'Dwyer, 2019). It is important for all
organizations to adhere these compliances in order or maintain network security. It also helps the
users to understand what is the right thing to do in order to maintain network security. There are
various kinds of compliances that can be used by small or medium sized organizations. Each and
every network proposed solution should have their defined compliances as per the requirement
of the organization vendors of the network should indicate or propose these compliances in three
forms: first is comply, second is partially comply and third is no comply. These compliances
play a vital role in understanding the main reason behind the project and what level of security is
required by the organization and for small or medium sized organization it is extremely
important to be understood and complied.
Requirement Statements Comply/No Comply/Partially
Comply
The solution needs to introduce at least 1 GBPS ports for
core switches
Comply
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network should be accessible through internet Comply
Quality of service should be based on media or service nature Partially Comply
Firewall should be introduced in order to protect the network Comply
Network boundaries shall be defined so that all the network
connections can be filtered and communication traffic can be
identified by type, source, destination identifier
Comply
LAN should be encrypted for all connections Comply
All the connections present in the network that carried
sensitive information like user id or passwords etc. should be
encrypted or digitally certified
Comply
All the PCs should have their own Anti-virus and other than
this a new Anti-Virus should also be provided by the server
so that internal network security can be increased
Partially Comply
Wireless access is required so that users will be able to
access internet from point A to point B
Partially Comply
There is no need of wireless access controller Comply
Wireless Access should be able to cover both the buildings
areas
Comply
In the above mentions Requirement statement and comply table all the requirements of the
network have been mentioned and which requirement is required to be complied, which required
to be partially complied and which not required to be complied are mentioned in a clear and
specific manner. These defined compliances will help in designing a network diagram
accordingly where all the above requirements are being fulfilled.
CONCLUSION
From the above assignment it has been summarized that there are various kinds of
requirements that are required to be fulfilled whenever network design solutions are required to
be proposed. The above assignment has successful described network topology designs of both
phase 1 and phase 2. Other than this according to the network requirements a proper network
solution for both the phases has also been proposed in an efficient manner. Above assignment
also helps in describing all Services, Applications provided by the network and all the interfaces
and Technologies used by the network.
9
Quality of service should be based on media or service nature Partially Comply
Firewall should be introduced in order to protect the network Comply
Network boundaries shall be defined so that all the network
connections can be filtered and communication traffic can be
identified by type, source, destination identifier
Comply
LAN should be encrypted for all connections Comply
All the connections present in the network that carried
sensitive information like user id or passwords etc. should be
encrypted or digitally certified
Comply
All the PCs should have their own Anti-virus and other than
this a new Anti-Virus should also be provided by the server
so that internal network security can be increased
Partially Comply
Wireless access is required so that users will be able to
access internet from point A to point B
Partially Comply
There is no need of wireless access controller Comply
Wireless Access should be able to cover both the buildings
areas
Comply
In the above mentions Requirement statement and comply table all the requirements of the
network have been mentioned and which requirement is required to be complied, which required
to be partially complied and which not required to be complied are mentioned in a clear and
specific manner. These defined compliances will help in designing a network diagram
accordingly where all the above requirements are being fulfilled.
CONCLUSION
From the above assignment it has been summarized that there are various kinds of
requirements that are required to be fulfilled whenever network design solutions are required to
be proposed. The above assignment has successful described network topology designs of both
phase 1 and phase 2. Other than this according to the network requirements a proper network
solution for both the phases has also been proposed in an efficient manner. Above assignment
also helps in describing all Services, Applications provided by the network and all the interfaces
and Technologies used by the network.
9

REFERENCES
Books and Journals
Kobo, H.I., Abu-Mahfouz, A.M. and Hancke, G.P., 2017. A survey on software-defined wireless
sensor networks: Challenges and design requirements. IEEE access. 5. pp.1872-1899.
Agrawal, A., and et.al., 2017, July. Fast Exact Algorithms for Survivable Network Design with
Uniform Requirements. In Workshop on Algorithms and Data Structures (pp. 25-36).
Springer, Cham.
Gao, P.X., and et.al., 2016. Network requirements for resource disaggregation. In 12th
{USENIX} Symposium on Operating Systems Design and Implementation ({OSDI} 16)
(pp. 249-264).
Shangin, R.E. and Pardalos, P., 2016. Heuristics for the network design problem with connectiv-
ity requirements. Journal of Combinatorial Optimization. 31(4). pp.1461-1478.
Pérez, A.T.E., and et.al., 2017. Key challenges and requirements for sustainable and industrial-
ized biorefinery supply chain design and management: a bibliographic analysis. Renew-
able and Sustainable Energy Reviews. 69. pp.350-359.
Abdelwahab, S., and et.al., 2016. Network function virtualization in 5G. IEEE Communications
Magazine. 54(4). pp.84-91.
Sundqvist, L., 2015. Cellular controlled drone experiment: Evaluation of network requirements.
Visotsky, D., Patel, A. and Summers, J., 2017. Using design requirements for environmental as-
sessment of products: a historical based method. Procedia CIRP. 61. pp.69-74.
Maitland, C. and Bharania, R., 2017. Balancing Security and Other Requirements in Hastily
Formed Networks: The Case of the Syrian Refugee Response. Available at SSRN
2944147.
Hynds, P.D., Nasr, A.E. and O'Dwyer, J., 2019. Evaluation of hydrometric network efficacy and
user requirements in the Republic of Ireland via expert opinion and statistical analysis.
Journal of Hydrology. 574. pp.851-861.
10
Books and Journals
Kobo, H.I., Abu-Mahfouz, A.M. and Hancke, G.P., 2017. A survey on software-defined wireless
sensor networks: Challenges and design requirements. IEEE access. 5. pp.1872-1899.
Agrawal, A., and et.al., 2017, July. Fast Exact Algorithms for Survivable Network Design with
Uniform Requirements. In Workshop on Algorithms and Data Structures (pp. 25-36).
Springer, Cham.
Gao, P.X., and et.al., 2016. Network requirements for resource disaggregation. In 12th
{USENIX} Symposium on Operating Systems Design and Implementation ({OSDI} 16)
(pp. 249-264).
Shangin, R.E. and Pardalos, P., 2016. Heuristics for the network design problem with connectiv-
ity requirements. Journal of Combinatorial Optimization. 31(4). pp.1461-1478.
Pérez, A.T.E., and et.al., 2017. Key challenges and requirements for sustainable and industrial-
ized biorefinery supply chain design and management: a bibliographic analysis. Renew-
able and Sustainable Energy Reviews. 69. pp.350-359.
Abdelwahab, S., and et.al., 2016. Network function virtualization in 5G. IEEE Communications
Magazine. 54(4). pp.84-91.
Sundqvist, L., 2015. Cellular controlled drone experiment: Evaluation of network requirements.
Visotsky, D., Patel, A. and Summers, J., 2017. Using design requirements for environmental as-
sessment of products: a historical based method. Procedia CIRP. 61. pp.69-74.
Maitland, C. and Bharania, R., 2017. Balancing Security and Other Requirements in Hastily
Formed Networks: The Case of the Syrian Refugee Response. Available at SSRN
2944147.
Hynds, P.D., Nasr, A.E. and O'Dwyer, J., 2019. Evaluation of hydrometric network efficacy and
user requirements in the Republic of Ireland via expert opinion and statistical analysis.
Journal of Hydrology. 574. pp.851-861.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




