IAS623 - Network Analysis and Infrastructure Report: DMZ Solutions
VerifiedAdded on 2022/10/04
|14
|2647
|4
Report
AI Summary
This report presents a comprehensive analysis of network infrastructure, starting with a comparison of cloud computing and virtualization, highlighting their benefits and differences. It then evaluates RAID technology, detailing various levels like RAID 0, 1, 5, and 10, and their architectural, operational, and performance characteristics. The report further outlines the similarities and differences between NAS, SAN, and DAS storage solutions, examining their costs, data transmission methods, and storage types, along with their respective advantages and disadvantages. It also identifies and describes different storage protocols, including Fibre Channel, FCoE, SCSI, and NFS, covering their performance considerations and security aspects. Finally, the report concludes with a case study focused on DMZ Solutions, where a NAS storage solution is proposed, along with a network diagram, cost plan, and justification for the chosen architecture, addressing future demands in storage, performance, and security.

Running head: NETWORK ANALYSIS AND INFRASTRUCTURE
Network Analysis and Infrastructure
Name of the Student
Name of the University
Author Note
Network Analysis and Infrastructure
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
NETWORK ANALYSIS AND INFRASTRUCTURE
Part I: Research
Task 1: Difference between Cloud Computing and Virtualization. Highlight the
benefits of each and share the comparison.
To most, virtualization and cloud computing can seem as pretty much the same thing
despite both of them having broader definitions which applies for various system types.
Cloud computing and virtualization both are mostly found to be virtual in that they rely upon
pretty much the same principles and models (Rankothge et al., 2015). This does not
necessarily mean that cloud computing and virtualization are one and the same.
Virtualization refers to the technology using which creation of several simulated
network environments can be allowed as well as duplication of available resources out of a
particular hardware system. Applications known as hypervisors connect directly to hardware
systems (Jin et al., 2015). These allow one in splitting of a system to different, unique and
secure system environments called virtual machines or VMs.
Cloud computing on the other hand refers to the approaches and set of principles
which perform computational, network as well as storage based infrastructural resources,
platforms, applications and services for the users all across the network.
Cloud Computing Virtualization
Serves the purpose of setting up multiple
simulated virtual environments out of the
same system.
Serves the purpose of pooling as also
automating virtual resources for on demand
usage.
Used for delivering resources to certain
users for designated use cases.
Used for delivering variable set of resources
for group of users to perform various
activities.
NETWORK ANALYSIS AND INFRASTRUCTURE
Part I: Research
Task 1: Difference between Cloud Computing and Virtualization. Highlight the
benefits of each and share the comparison.
To most, virtualization and cloud computing can seem as pretty much the same thing
despite both of them having broader definitions which applies for various system types.
Cloud computing and virtualization both are mostly found to be virtual in that they rely upon
pretty much the same principles and models (Rankothge et al., 2015). This does not
necessarily mean that cloud computing and virtualization are one and the same.
Virtualization refers to the technology using which creation of several simulated
network environments can be allowed as well as duplication of available resources out of a
particular hardware system. Applications known as hypervisors connect directly to hardware
systems (Jin et al., 2015). These allow one in splitting of a system to different, unique and
secure system environments called virtual machines or VMs.
Cloud computing on the other hand refers to the approaches and set of principles
which perform computational, network as well as storage based infrastructural resources,
platforms, applications and services for the users all across the network.
Cloud Computing Virtualization
Serves the purpose of setting up multiple
simulated virtual environments out of the
same system.
Serves the purpose of pooling as also
automating virtual resources for on demand
usage.
Used for delivering resources to certain
users for designated use cases.
Used for delivering variable set of resources
for group of users to perform various
activities.
2
NETWORK ANALYSIS AND INFRASTRUCTURE
Comes in image based configuration in
virtual drives.
Comes in template based configuration for
integration with company networks.
Built for long term usage generally years. Built for short term usage generally hours or
months.
Comes with higher capital expenses
(CAPEX) and lower operating expenditure
(OPEX)
Comes in two instances:
Private Cloud: High CAPEX and Low
OPEX
Public Cloud: Low CAPEX and High
OPEX
Virtualization can be scaled up Cloud implementations can be scaled out.
Involves stateful implementations Involves stateless integration
Serves a single user Can serve multiple usrs
Cloud Computing Features
1. Pooling of Resources
2. Easy to Maintain
3. Greater Accessibility of Network
Virtualization Features
1. Tightened Security through use of sandboxed environment
2. Wide range of features in managing execution like sharing, aggregation, emulation,
isolation
3. Highly portable solution
NETWORK ANALYSIS AND INFRASTRUCTURE
Comes in image based configuration in
virtual drives.
Comes in template based configuration for
integration with company networks.
Built for long term usage generally years. Built for short term usage generally hours or
months.
Comes with higher capital expenses
(CAPEX) and lower operating expenditure
(OPEX)
Comes in two instances:
Private Cloud: High CAPEX and Low
OPEX
Public Cloud: Low CAPEX and High
OPEX
Virtualization can be scaled up Cloud implementations can be scaled out.
Involves stateful implementations Involves stateless integration
Serves a single user Can serve multiple usrs
Cloud Computing Features
1. Pooling of Resources
2. Easy to Maintain
3. Greater Accessibility of Network
Virtualization Features
1. Tightened Security through use of sandboxed environment
2. Wide range of features in managing execution like sharing, aggregation, emulation,
isolation
3. Highly portable solution
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 2: Evaluation of RAID technology and its different levels. Reflect the
differences of various RAID levels in term of their: architecture, techniques,
operation, and performance.
RAID offers arrays of storage which the operating system or OS sees as logical hard
disks. The RAID technology employs different techniques like mirroring of disks and disk
striping (Yuan et al., 2017). This mirroring copies similar data to one or more drives based on
the RAID configuration selected. Striping partitions of the storage space of every drive to
units that range from a sector of 512 bytes and all the way to some megabytes. These stripes
of the disks then get interleaved and are addressed accordingly.
RAID levels
RAID 0: In this configuration striping exists redundancy of data is absent. This level of
RAID provides maximum performance without any countermeasures to address faults.
Figure 1: Working principle of RAID 0
(Source: dataplugs.com)
RAID 1: This level performs disk mirroring and the configuration can consist of about two
drives for duplication of storage data. No disk striping occurs here. The read performance
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 2: Evaluation of RAID technology and its different levels. Reflect the
differences of various RAID levels in term of their: architecture, techniques,
operation, and performance.
RAID offers arrays of storage which the operating system or OS sees as logical hard
disks. The RAID technology employs different techniques like mirroring of disks and disk
striping (Yuan et al., 2017). This mirroring copies similar data to one or more drives based on
the RAID configuration selected. Striping partitions of the storage space of every drive to
units that range from a sector of 512 bytes and all the way to some megabytes. These stripes
of the disks then get interleaved and are addressed accordingly.
RAID levels
RAID 0: In this configuration striping exists redundancy of data is absent. This level of
RAID provides maximum performance without any countermeasures to address faults.
Figure 1: Working principle of RAID 0
(Source: dataplugs.com)
RAID 1: This level performs disk mirroring and the configuration can consist of about two
drives for duplication of storage data. No disk striping occurs here. The read performance
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
NETWORK ANALYSIS AND INFRASTRUCTURE
gets improved as any of the two disks are readable simultaneously. Write performance is
similar for single disk storage.
Figure 2: Working principle of RAID 1
(Source: xorcom.com)
RAID 5: This RAID level is built upon block-level disk striping with parity. This parity
information gets striped all across the drives, and allows the array in functioning although
one of the drives end up failing. This architecture of the RAID array allows both read, write
operations which can span several drives. This translates to better performance than what is
observed in a single drive though falls short of RAID 0 performance. RAID 5 requires three
disk drives at the minimum though it is recommended to have five disks for better
performance.
NETWORK ANALYSIS AND INFRASTRUCTURE
gets improved as any of the two disks are readable simultaneously. Write performance is
similar for single disk storage.
Figure 2: Working principle of RAID 1
(Source: xorcom.com)
RAID 5: This RAID level is built upon block-level disk striping with parity. This parity
information gets striped all across the drives, and allows the array in functioning although
one of the drives end up failing. This architecture of the RAID array allows both read, write
operations which can span several drives. This translates to better performance than what is
observed in a single drive though falls short of RAID 0 performance. RAID 5 requires three
disk drives at the minimum though it is recommended to have five disks for better
performance.
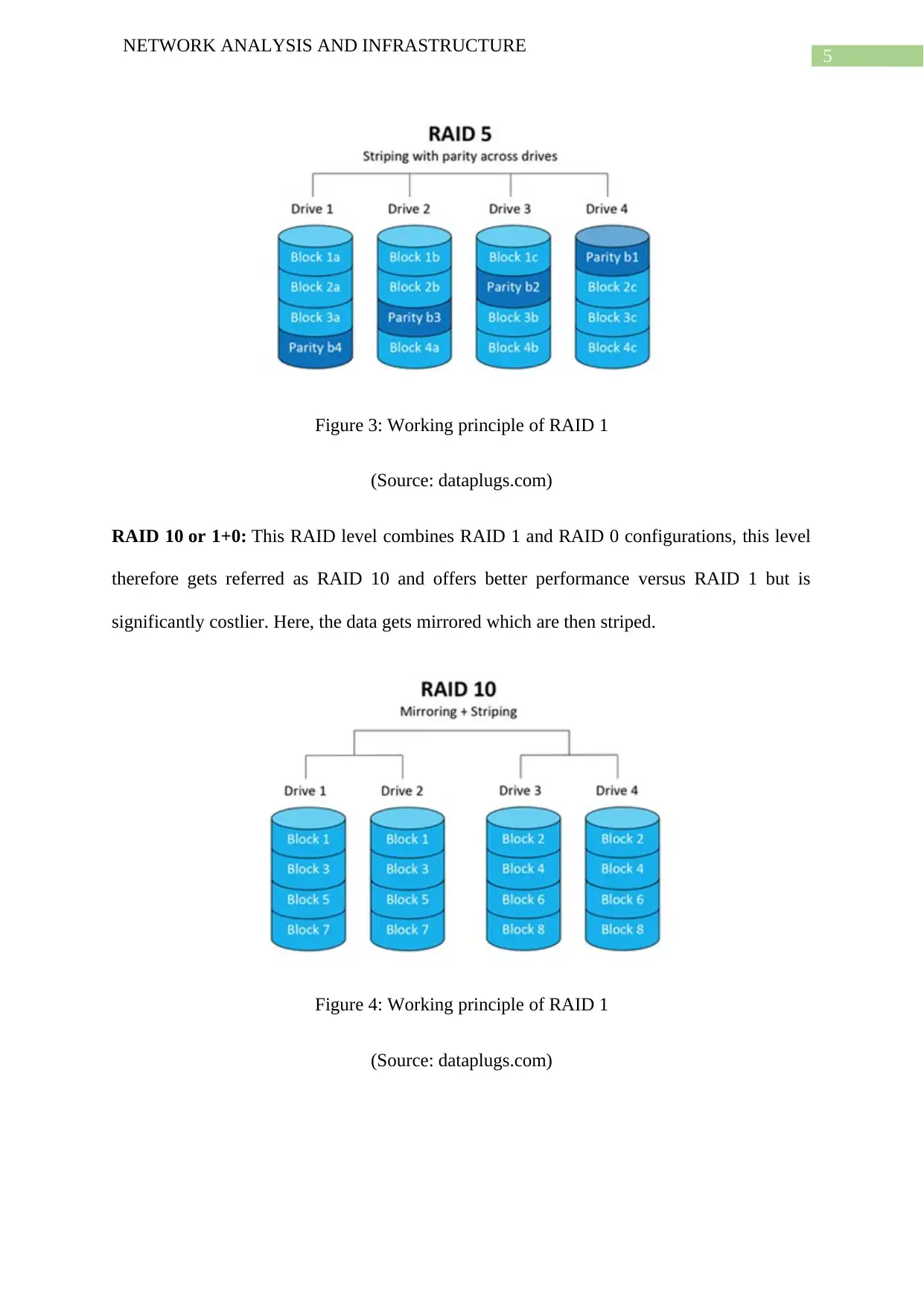
5
NETWORK ANALYSIS AND INFRASTRUCTURE
Figure 3: Working principle of RAID 1
(Source: dataplugs.com)
RAID 10 or 1+0: This RAID level combines RAID 1 and RAID 0 configurations, this level
therefore gets referred as RAID 10 and offers better performance versus RAID 1 but is
significantly costlier. Here, the data gets mirrored which are then striped.
Figure 4: Working principle of RAID 1
(Source: dataplugs.com)
NETWORK ANALYSIS AND INFRASTRUCTURE
Figure 3: Working principle of RAID 1
(Source: dataplugs.com)
RAID 10 or 1+0: This RAID level combines RAID 1 and RAID 0 configurations, this level
therefore gets referred as RAID 10 and offers better performance versus RAID 1 but is
significantly costlier. Here, the data gets mirrored which are then striped.
Figure 4: Working principle of RAID 1
(Source: dataplugs.com)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 3: Outline the similarities and differences of NAS, SAN, and DAS in terms
of their cost, data transmission, and storage type. In addition, identify the
advantages and disadvantages of using one from the other.
NAS refers to file systems delivered over the network (Wei, 2017). This is ready to
get mounted and used.To accomplish this NAS uses technologies like network file system
(NFS), common internet file system (CIFS), Andrew File System (AFS) among others.
Bandwidth is observed to vary from 1 MB/s to 10 GB/s.
NAS Advantages
Single volume can be shared among several clients.
Ensures fault tolerance for the system.
Enables administrators in employing simpler, cost efficient load balancing.
NAS Disadvantages
Limited application support.
Backup solutions are costlier than storage systems.
Disturbances in LAN connections can significantly affect storage access times.
SAN Advantages
Flexible and simple storage administration.
Servers can boot themselves automatically through SAN.
Easy to quickly replace faulty servers.
SAN Disadvantages
Expensive to acquire and implement.
SAN solutions are complicated to manage.
Advanced skills are needed for maintaining SAN.
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 3: Outline the similarities and differences of NAS, SAN, and DAS in terms
of their cost, data transmission, and storage type. In addition, identify the
advantages and disadvantages of using one from the other.
NAS refers to file systems delivered over the network (Wei, 2017). This is ready to
get mounted and used.To accomplish this NAS uses technologies like network file system
(NFS), common internet file system (CIFS), Andrew File System (AFS) among others.
Bandwidth is observed to vary from 1 MB/s to 10 GB/s.
NAS Advantages
Single volume can be shared among several clients.
Ensures fault tolerance for the system.
Enables administrators in employing simpler, cost efficient load balancing.
NAS Disadvantages
Limited application support.
Backup solutions are costlier than storage systems.
Disturbances in LAN connections can significantly affect storage access times.
SAN Advantages
Flexible and simple storage administration.
Servers can boot themselves automatically through SAN.
Easy to quickly replace faulty servers.
SAN Disadvantages
Expensive to acquire and implement.
SAN solutions are complicated to manage.
Advanced skills are needed for maintaining SAN.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORK ANALYSIS AND INFRASTRUCTURE
DAS Advantages
Availability rate is very high.
Access rates are high as well because of no Storage Area Network.
No complications regarding network setup is required.
DAS Disadvantages
Inability to access data by multiple user groups.
Enables single user access at any point of time.
Administering costs are on the higher side.
SAN refers to device blocks that delivers storage over the network (Ono et al., 2015).
Like Direct Attached Storage (DAS) one should still be able to place file systems on them
before being used. Technologies used to accomplish this are Fibre channel, internet Small
Computers Systems Interface (iSCSI), File transfer on EtherCAT (FoE) among others.
Bandwidth is observed to vary from 100 MB/s to 200 MB/s.
DAS is the digital storage mechanism that is attached directly to computers which
access it, as against the storage accessed over computer networks that is network
attached storages. Examples of DAS implementation can include hard drives, optical discs,
solid state drives as also storage present on external drives. Bandwidth is observed to vary
from 40 MB/s to 160 MB/s.
Task 4: Identify and describe the different storage protocols and its advantages
and disadvantages. Your report must include performance considerations and
security aspects of each identified protocols.
Four key storage protocols are:
Fibre Channel (FC)
Fibre Channel over Ethernet (FCoE)
NETWORK ANALYSIS AND INFRASTRUCTURE
DAS Advantages
Availability rate is very high.
Access rates are high as well because of no Storage Area Network.
No complications regarding network setup is required.
DAS Disadvantages
Inability to access data by multiple user groups.
Enables single user access at any point of time.
Administering costs are on the higher side.
SAN refers to device blocks that delivers storage over the network (Ono et al., 2015).
Like Direct Attached Storage (DAS) one should still be able to place file systems on them
before being used. Technologies used to accomplish this are Fibre channel, internet Small
Computers Systems Interface (iSCSI), File transfer on EtherCAT (FoE) among others.
Bandwidth is observed to vary from 100 MB/s to 200 MB/s.
DAS is the digital storage mechanism that is attached directly to computers which
access it, as against the storage accessed over computer networks that is network
attached storages. Examples of DAS implementation can include hard drives, optical discs,
solid state drives as also storage present on external drives. Bandwidth is observed to vary
from 40 MB/s to 160 MB/s.
Task 4: Identify and describe the different storage protocols and its advantages
and disadvantages. Your report must include performance considerations and
security aspects of each identified protocols.
Four key storage protocols are:
Fibre Channel (FC)
Fibre Channel over Ethernet (FCoE)

8
NETWORK ANALYSIS AND INFRASTRUCTURE
Small Computer System Interface (SCSI)
Network File System (NFS)
Advantages of Fibre Channel
Commonly deployable architecture for enterprise storage.
Generally found to be the best storage mechanism owing to higher bandwidth
available.
Block level storage can be used through virtualization applications
Disadvantages
Generally found to be the most expensive storage option
Involves specialized components like switches, HBAs and cables
Less security options available with complex authentication and encryption schemes
Advantages of Fibre Channel over Ethernet (FCoE)
FCoE enables native support for transporting Fibre Channel SAN traffic through
Ethernet networks.
Can be managed with existing management software as also support current functions
of SAN storage.
Is a form of technology which unifies networks of datacentres
Disadvantages
FCoE is not suitable enough for WAN or wide area networks
Is also not suitable for standard Ethernet due to latencies being high
Cost of operating FCoE is relatively higher
Advantages of Small Computer System Interface (SCSI)
Performance is substantially faster than other drives
Concurrent connections to multiple devices can be made through single controller
NETWORK ANALYSIS AND INFRASTRUCTURE
Small Computer System Interface (SCSI)
Network File System (NFS)
Advantages of Fibre Channel
Commonly deployable architecture for enterprise storage.
Generally found to be the best storage mechanism owing to higher bandwidth
available.
Block level storage can be used through virtualization applications
Disadvantages
Generally found to be the most expensive storage option
Involves specialized components like switches, HBAs and cables
Less security options available with complex authentication and encryption schemes
Advantages of Fibre Channel over Ethernet (FCoE)
FCoE enables native support for transporting Fibre Channel SAN traffic through
Ethernet networks.
Can be managed with existing management software as also support current functions
of SAN storage.
Is a form of technology which unifies networks of datacentres
Disadvantages
FCoE is not suitable enough for WAN or wide area networks
Is also not suitable for standard Ethernet due to latencies being high
Cost of operating FCoE is relatively higher
Advantages of Small Computer System Interface (SCSI)
Performance is substantially faster than other drives
Concurrent connections to multiple devices can be made through single controller
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORK ANALYSIS AND INFRASTRUCTURE
Same cable can be used for interfacing different devices.
Disadvantages of Small Computer System Interface (SCSI)
SCSI are much costlier than other storage drives
As every device have unique identities, the interfaces must be configured perfectly
Older models are even more difficult to configure
Advantages of Network File System (NFS)
Operates with stateless servers and clients
Server restarts can be made without affecting users
Distinction between clients and servers happen in the application layer and is more
flexible
Disadvantages of Network File System (NFS)
Uses RPC authentication and can be spoofed easily
File system data gets transmitted as clear text and can get copied
Absence of multi-pathing or failover capabilities
is slow compared to block storage devices
NETWORK ANALYSIS AND INFRASTRUCTURE
Same cable can be used for interfacing different devices.
Disadvantages of Small Computer System Interface (SCSI)
SCSI are much costlier than other storage drives
As every device have unique identities, the interfaces must be configured perfectly
Older models are even more difficult to configure
Advantages of Network File System (NFS)
Operates with stateless servers and clients
Server restarts can be made without affecting users
Distinction between clients and servers happen in the application layer and is more
flexible
Disadvantages of Network File System (NFS)
Uses RPC authentication and can be spoofed easily
File system data gets transmitted as clear text and can get copied
Absence of multi-pathing or failover capabilities
is slow compared to block storage devices
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
NETWORK ANALYSIS AND INFRASTRUCTURE
Part II: Case Study
Task 5: As the Network Engineer of DMZ Solutions, you need to identify
solutions to ensure that DMZ would not experience the problems mentioned on
the scenario. Prove that your solution will cater to future demand in storage,
performance, and security; and, not as a one-stop solution. Prepare a plan that
outlines the storage solution identified and security for the implementation of the
storage solution you have identified. Detail the resources and the time you may
require. In addition, make sensible assumptions concerning the requirements
required for setting up the new network.
To serve the requirements of DMZ Solutions, the NAS storage option needs to be
used. The network of DMZ solutions is to operate with three sets of nodes simultaneously
with at least two servers present in the perimeter network, three of the servers present in the
server cluster as well as the individual devices. This demands storage options for devices of
all the three segments and hence NAS helps simplify the network architecture by only having
the NAS devices connected separately to the main Ethernet switch (Kawatra, 2016). This
makes the network structure modular and thus streamlines data transmission thereby
improving storage and file sharing performance. This modular structure eliminates any
possible inconsistencies and other problems related to the DMZ network. Thee file locking
and queuing along with the virtualization capabilities offered by NAS further strengthen the
security of the network in addition to the firewalls and DMZ network being used.
In the first week the perimeter network will be connected to the network and
validated. In the second week the servers of the internal network will be connected and
validated. The third week will see integration of individual devices. On the fourth week the
NAS device will be connected and configured accordingly.
NETWORK ANALYSIS AND INFRASTRUCTURE
Part II: Case Study
Task 5: As the Network Engineer of DMZ Solutions, you need to identify
solutions to ensure that DMZ would not experience the problems mentioned on
the scenario. Prove that your solution will cater to future demand in storage,
performance, and security; and, not as a one-stop solution. Prepare a plan that
outlines the storage solution identified and security for the implementation of the
storage solution you have identified. Detail the resources and the time you may
require. In addition, make sensible assumptions concerning the requirements
required for setting up the new network.
To serve the requirements of DMZ Solutions, the NAS storage option needs to be
used. The network of DMZ solutions is to operate with three sets of nodes simultaneously
with at least two servers present in the perimeter network, three of the servers present in the
server cluster as well as the individual devices. This demands storage options for devices of
all the three segments and hence NAS helps simplify the network architecture by only having
the NAS devices connected separately to the main Ethernet switch (Kawatra, 2016). This
makes the network structure modular and thus streamlines data transmission thereby
improving storage and file sharing performance. This modular structure eliminates any
possible inconsistencies and other problems related to the DMZ network. Thee file locking
and queuing along with the virtualization capabilities offered by NAS further strengthen the
security of the network in addition to the firewalls and DMZ network being used.
In the first week the perimeter network will be connected to the network and
validated. In the second week the servers of the internal network will be connected and
validated. The third week will see integration of individual devices. On the fourth week the
NAS device will be connected and configured accordingly.
11
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 6: Create network diagram for a storage solution that is suitable to
implement on DMZ’s network according to company requirements. You are
required to explain the network diagram and how it will operate once
implemented.
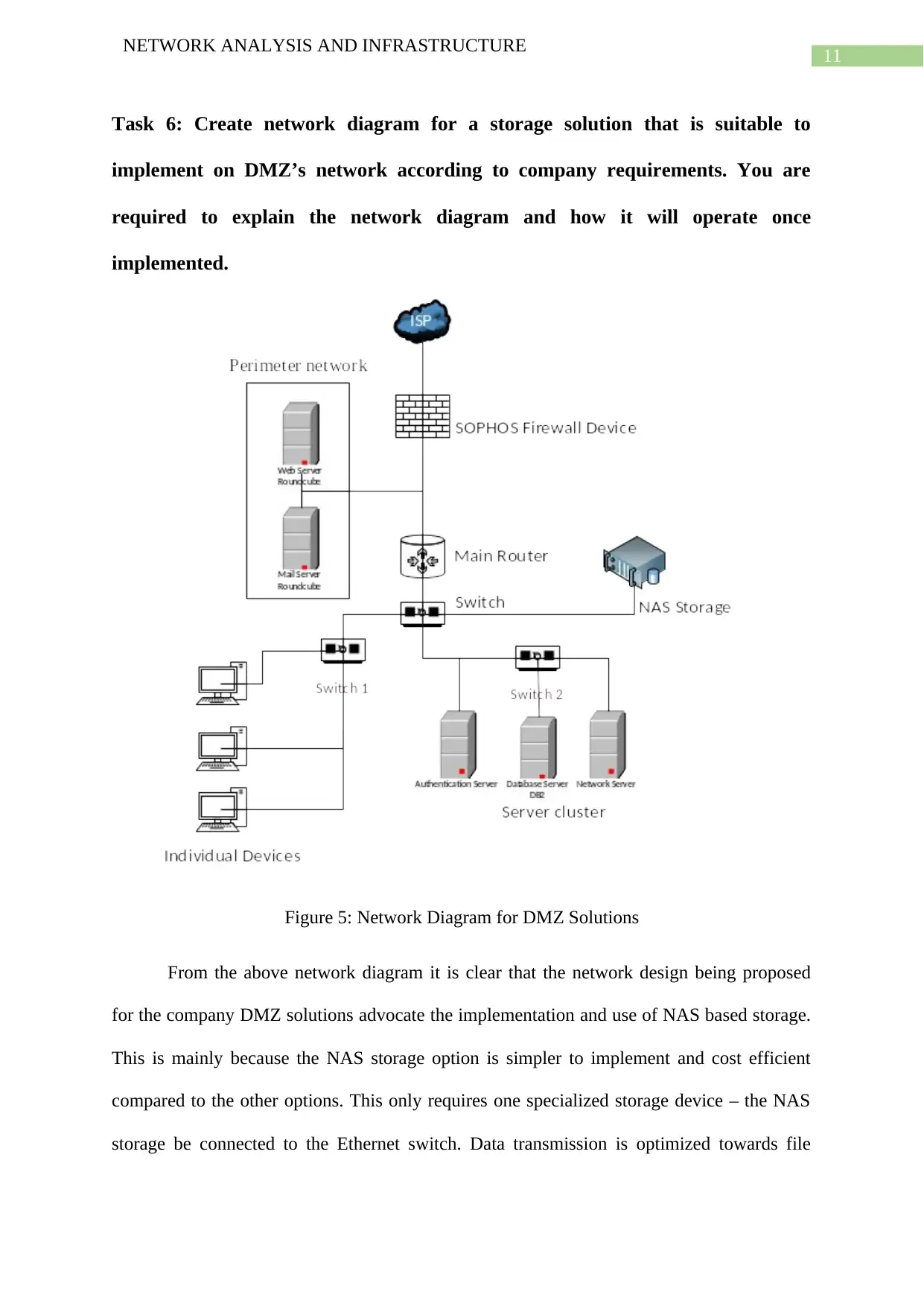
Figure 5: Network Diagram for DMZ Solutions
From the above network diagram it is clear that the network design being proposed
for the company DMZ solutions advocate the implementation and use of NAS based storage.
This is mainly because the NAS storage option is simpler to implement and cost efficient
compared to the other options. This only requires one specialized storage device – the NAS
storage be connected to the Ethernet switch. Data transmission is optimized towards file
NETWORK ANALYSIS AND INFRASTRUCTURE
Task 6: Create network diagram for a storage solution that is suitable to
implement on DMZ’s network according to company requirements. You are
required to explain the network diagram and how it will operate once
implemented.
Figure 5: Network Diagram for DMZ Solutions
From the above network diagram it is clear that the network design being proposed
for the company DMZ solutions advocate the implementation and use of NAS based storage.
This is mainly because the NAS storage option is simpler to implement and cost efficient
compared to the other options. This only requires one specialized storage device – the NAS
storage be connected to the Ethernet switch. Data transmission is optimized towards file
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





