ThinkTank Network System Management Case Study - MN506, MIT, T1 2019
VerifiedAdded on 2023/03/30
|23
|3203
|154
Case Study
AI Summary
This document provides a comprehensive solution to a network system management case study centered around ThinkTank, a small to medium-sized business enterprise based in Sydney. The study addresses the company's need to expand its network infrastructure to accommodate rapid growth and the opening of a new branch in Melbourne. The solution includes a detailed requirement analysis, focusing on scalability, security, and centralized management. It identifies and explains the roles of various servers, such as web servers, file servers, DHCP servers, and DNS servers, necessary for the network's functionality. Furthermore, the document outlines the configuration process, including setting up the domain, assigning IP addresses automatically, and implementing security measures. The solution emphasizes the use of Windows Server and Oracle Virtual Box, along with minimum hardware specifications for successful configuration. This case study offers valuable insights into designing and implementing a robust and scalable network for a growing business.

Network System Management
Case Study of ThinkTank
Student Name
Institutional Affiliation
1 | P a g e
Case Study of ThinkTank
Student Name
Institutional Affiliation
1 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
Networking is one of the major areas a company should consider investing a lot when it comes to
making their objectives achievable and SMART. The idea is understanding how it should be laid
in all aspects. Networking is the interconnection of devices so that they can share the resources
and transmit them from one device to another. The computer networks are being used widely and
thus termed as a basic need for any organization in achieving its objectives.
Network devices are such as the routers, Personal Desktops, mobile and smartphones, and
servers among others [1]. This devices helps in making the communication effective and thus
helping in sharing of all the critical resources. Ideally, for one to understand the network design
of the given company, it is good and necessary for one to perform a thorough analysis with
regards to the company objectives and thus helping in coming up with all the needed
requirements in all aspects. In this report, the major idea is for one to understand what is needed
by ThinkTank. As a company that stores its information in a centralized approach there is a need
for one to identify and analyze the type of server to be used, the role they play in the network and
features and technology they use in realizing to their goals [2]. The report will also give a
detailed explanation of the configuration process of the server.
ThinkTank Case Study
This company by the name ThinkTank is situated in Sydney and is small/medium in size
business enterprise. At the beginning they survived with only 10 pcs but currently they have
developed to more than 50 PCs clearly showing that they have expanded rapidly. They cannot
avoid or evade the charge of expanding their network so that it can cater to all the workstations.
After such rapid growth, the company is having a plan of extending services by opening a new
2 | P a g e
Networking is one of the major areas a company should consider investing a lot when it comes to
making their objectives achievable and SMART. The idea is understanding how it should be laid
in all aspects. Networking is the interconnection of devices so that they can share the resources
and transmit them from one device to another. The computer networks are being used widely and
thus termed as a basic need for any organization in achieving its objectives.
Network devices are such as the routers, Personal Desktops, mobile and smartphones, and
servers among others [1]. This devices helps in making the communication effective and thus
helping in sharing of all the critical resources. Ideally, for one to understand the network design
of the given company, it is good and necessary for one to perform a thorough analysis with
regards to the company objectives and thus helping in coming up with all the needed
requirements in all aspects. In this report, the major idea is for one to understand what is needed
by ThinkTank. As a company that stores its information in a centralized approach there is a need
for one to identify and analyze the type of server to be used, the role they play in the network and
features and technology they use in realizing to their goals [2]. The report will also give a
detailed explanation of the configuration process of the server.
ThinkTank Case Study
This company by the name ThinkTank is situated in Sydney and is small/medium in size
business enterprise. At the beginning they survived with only 10 pcs but currently they have
developed to more than 50 PCs clearly showing that they have expanded rapidly. They cannot
avoid or evade the charge of expanding their network so that it can cater to all the workstations.
After such rapid growth, the company is having a plan of extending services by opening a new
2 | P a g e

branch in Melbourne that will have a direct connection with its headquarter in Sydney. It is
expected to hire the same number of staff as those in the headquarter meaning that their
centralized network will now be managing 100 PCs. In this case, due to the increased number of
workers, there is a need to buy more printers and PCs for the new branch. In this case, they will
have to do centralization, authentication and Data location to ensure that data is stored across all
the branches.
Another requirement is that the company must make sure that they have separate folders on the
network to ensure that the two branches access data without problems. Each department will
need to see their folders and files only. The manager should have access to all folders in the
network.
The problem that ThinkTank is facing is that their data is only stored centrally on two of their
machines in Sydney Branch. The sharing and assigning of IP address manually have been a
problem as most of the staff forget the assigned IP addresses allocated and sometimes this may
lead to duplication of such addresses. There is a need to address the issues of the user not being
able to save anything in the network as the company as they have no access meaning that there is
no accountability that has been put in place. In this case, there is a need to install a server system
that will have features such fault tolerance especially in cases when the business operations run
down and thus making the businesses not to be affected directly. The mentioned problems can be
discussed through the following discussion indicating each step that needs to be followed so that
all the requirements and needs of ThinkTank are met and achieved.
3 | P a g e
expected to hire the same number of staff as those in the headquarter meaning that their
centralized network will now be managing 100 PCs. In this case, due to the increased number of
workers, there is a need to buy more printers and PCs for the new branch. In this case, they will
have to do centralization, authentication and Data location to ensure that data is stored across all
the branches.
Another requirement is that the company must make sure that they have separate folders on the
network to ensure that the two branches access data without problems. Each department will
need to see their folders and files only. The manager should have access to all folders in the
network.
The problem that ThinkTank is facing is that their data is only stored centrally on two of their
machines in Sydney Branch. The sharing and assigning of IP address manually have been a
problem as most of the staff forget the assigned IP addresses allocated and sometimes this may
lead to duplication of such addresses. There is a need to address the issues of the user not being
able to save anything in the network as the company as they have no access meaning that there is
no accountability that has been put in place. In this case, there is a need to install a server system
that will have features such fault tolerance especially in cases when the business operations run
down and thus making the businesses not to be affected directly. The mentioned problems can be
discussed through the following discussion indicating each step that needs to be followed so that
all the requirements and needs of ThinkTank are met and achieved.
3 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Requirement Analysis and Servers
Ideally, to come with a good network design or approach it is wise to consider various factors
with regards to the network infrastructure to be set. This will be significant in helping them to
address the management of the network and the issues which are faced by the executive in such
an environment. The first factor is to know the work plan of the network to be set up [3]. In this
case, one can be able to understand some of the most basic and necessary features that the
network should have so that they can be able to offer provisions of being able to monitor and
manage the network functionalities. Understanding the requirements of the organization will help
one to have an easy time when planning and thus easy implementation. Secondly is that the
network has the ability to avoid all the outages and thus making it be available and reliable all
the time [4]. In this case, this can help in achieving the prediction of the enterprise growth thus
enabling them to be able to prepare for emergency configurations and expansion thus enabling
report integration and techniques and tools that help to plan for the future needs.
Another concept that has been addressed is making the network to have centralized management.
In this case, it will be possible to monitor and control machines connected in the network on one
single platform. Also, through the centralized network management, it will be possible to for one
automatically assign IP Address to the workstations connected in the network via the DHCP
server. The other requirement is making the network scalable [5]. In this case, the network can
be able to support any extension or expansion of the network in case any device is added. When
there is a device added to the network, it is not supposed to interfere with the network
performance. As seen in the case study, ThinkTank is a company that is growing very rapidly
and thus it is not a wonder that they open another branch within the coming years and thus
developing a network that has scalability features will save them in future when such need arises.
4 | P a g e
Ideally, to come with a good network design or approach it is wise to consider various factors
with regards to the network infrastructure to be set. This will be significant in helping them to
address the management of the network and the issues which are faced by the executive in such
an environment. The first factor is to know the work plan of the network to be set up [3]. In this
case, one can be able to understand some of the most basic and necessary features that the
network should have so that they can be able to offer provisions of being able to monitor and
manage the network functionalities. Understanding the requirements of the organization will help
one to have an easy time when planning and thus easy implementation. Secondly is that the
network has the ability to avoid all the outages and thus making it be available and reliable all
the time [4]. In this case, this can help in achieving the prediction of the enterprise growth thus
enabling them to be able to prepare for emergency configurations and expansion thus enabling
report integration and techniques and tools that help to plan for the future needs.
Another concept that has been addressed is making the network to have centralized management.
In this case, it will be possible to monitor and control machines connected in the network on one
single platform. Also, through the centralized network management, it will be possible to for one
automatically assign IP Address to the workstations connected in the network via the DHCP
server. The other requirement is making the network scalable [5]. In this case, the network can
be able to support any extension or expansion of the network in case any device is added. When
there is a device added to the network, it is not supposed to interfere with the network
performance. As seen in the case study, ThinkTank is a company that is growing very rapidly
and thus it is not a wonder that they open another branch within the coming years and thus
developing a network that has scalability features will save them in future when such need arises.
4 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network security usually helps in securing the data in the enterprise and thus it is a major
requirement that should be considered by any organization during such network
implementations. Some of the network requirements are such as the system is able to detect
faults and thus prompting the admin before they happen and thus helping to mitigate such
problems by applying the use of the disaster recovery techniques [6]. Ideally, through good
security, the integrity and usability of the enterprise data will be maintained in all aspects.
Security is very vital and thus a company should include it in both the programs and the
hardware. Security being a very vital component in any network, as an administrator it is good to
understand some of the mechanisms of security that can be implemented during network
designing and implementation.
Developing access control in the network to help in controlling the access of the
enterprise resources. This may help the enterprise to be able to avoid and prevent all the
attackers with an intention to attack the resources of the network without any
authentication or authorization [7].
Installation of antivirus and antimalware programs which can be used to prevent the
spyware and ransomware and other types of attacks to spread over the network.
Another concept or mechanisms is installing the firewalls and intrusion detections that
can help in improving security in the network [8].
Server Identifications and Their Roles.
A server can be considered to be a dedicated component that has power when it comes to
processing and thus its performance is to perform all the functions that they are assigned to. In
this case, there exist various types of servers depending on the functionalities they will play in
the enterprise network implementation [9]. The objectives of ThinkTank indicates using the
5 | P a g e
requirement that should be considered by any organization during such network
implementations. Some of the network requirements are such as the system is able to detect
faults and thus prompting the admin before they happen and thus helping to mitigate such
problems by applying the use of the disaster recovery techniques [6]. Ideally, through good
security, the integrity and usability of the enterprise data will be maintained in all aspects.
Security is very vital and thus a company should include it in both the programs and the
hardware. Security being a very vital component in any network, as an administrator it is good to
understand some of the mechanisms of security that can be implemented during network
designing and implementation.
Developing access control in the network to help in controlling the access of the
enterprise resources. This may help the enterprise to be able to avoid and prevent all the
attackers with an intention to attack the resources of the network without any
authentication or authorization [7].
Installation of antivirus and antimalware programs which can be used to prevent the
spyware and ransomware and other types of attacks to spread over the network.
Another concept or mechanisms is installing the firewalls and intrusion detections that
can help in improving security in the network [8].
Server Identifications and Their Roles.
A server can be considered to be a dedicated component that has power when it comes to
processing and thus its performance is to perform all the functions that they are assigned to. In
this case, there exist various types of servers depending on the functionalities they will play in
the enterprise network implementation [9]. The objectives of ThinkTank indicates using the
5 | P a g e

name in the domain and assigning of IP Addresses manually, this calls for a reason to include
some different servers to help in dealing with such problems. In this case, some of the servers to
be used in the configuration process are such as the file server, web server, DHCP server, DNS
server among others where each server have a specific role in the network.
Server Server Role and Functionality
Web Server This is a server that is used for hosting the enterprise website on their
specific server in their own premises. It is also applied in delivering the
services needed to the users or clients over the internet. It usually
enables HTTP communication in the WWW.
File Server This server has a primary function of allowing access to the shared
disks such as the share files which can only be accessed by only those
with authorization in the network. It is made in a manner that its major
function is to store and retrieve files on the network.
DHCP
Server
This is simply Dynamic Host Control Protocol that is used to
automatically assign all the devices their respective IP addresses
without duplication and thus solving one of the requirements addressed
by ThinkTank in the case study [10]. This server is also important
because it helps in sending the parameters needed for the network
automatically thus enabling them to easily communicate and share files
appropriately over the network.
Print Server The server is usually responsible for the management of the print jobs
over the network. This is because the printer itself cannot be able to
facilitate the print request of a vast amount of data from various
employees.
Other Servers
Mail Server This plays a major role in the management of emails, employee
communicating to their customers among others. This is used for the
storage and sending and receiving of emails across and over the
enterprise network via the Local Areas Network and over the web [11].
6 | P a g e
some different servers to help in dealing with such problems. In this case, some of the servers to
be used in the configuration process are such as the file server, web server, DHCP server, DNS
server among others where each server have a specific role in the network.
Server Server Role and Functionality
Web Server This is a server that is used for hosting the enterprise website on their
specific server in their own premises. It is also applied in delivering the
services needed to the users or clients over the internet. It usually
enables HTTP communication in the WWW.
File Server This server has a primary function of allowing access to the shared
disks such as the share files which can only be accessed by only those
with authorization in the network. It is made in a manner that its major
function is to store and retrieve files on the network.
DHCP
Server
This is simply Dynamic Host Control Protocol that is used to
automatically assign all the devices their respective IP addresses
without duplication and thus solving one of the requirements addressed
by ThinkTank in the case study [10]. This server is also important
because it helps in sending the parameters needed for the network
automatically thus enabling them to easily communicate and share files
appropriately over the network.
Print Server The server is usually responsible for the management of the print jobs
over the network. This is because the printer itself cannot be able to
facilitate the print request of a vast amount of data from various
employees.
Other Servers
Mail Server This plays a major role in the management of emails, employee
communicating to their customers among others. This is used for the
storage and sending and receiving of emails across and over the
enterprise network via the Local Areas Network and over the web [11].
6 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Application
Server
These are servers required by ThinkTank to host the enterprise
applications and the needed and related services.
Proxy
Server
This is a very server especially in terms of security, as it helps in the
filtering of the shared connections and network traffic as it based
between the web browser and web server.
Configuration Process Description
The process for configuring the servers should be made clear in the essence that any person who
accesses the guideline can be able to understand the manual without problems. In order for one
to extremely capture all the details, there is a need to capture ThinkTank objectives and
requirements as stated in the case study. In this case, using the DNS server and the Web Server
the enterprise domain will be set as thinktank.com since it is to be accessed globally. The
network itself should be created in the manner that it is itself an active directory which will have
the root domain as thinktank.com. The other concept is understanding the work of the DNS [12].
DNS server will be fundamental in ensuring that the active directory has been able to establish
all the services which are available on thinktank.com domain indicating the provider of such
services.
Ideally, there will the use of a DHCP server that will be applied to make sure that all the IP
addresses are assigned automatically for the clients. In this concept, the network will be needed
to be in a centralized manner. There will be the use of the Lightweight Directory Access Control
that is needed when one wants to keep track of all the activities that are established over the
network. Notably, the Kerberos will be applied in handling log in that usually facilitate the use of
a single password as well as one username in accessing more than one PC. In building such a
network there is a need to use a windows server and Oracle Virtual Box. The following are
7 | P a g e
Server
These are servers required by ThinkTank to host the enterprise
applications and the needed and related services.
Proxy
Server
This is a very server especially in terms of security, as it helps in the
filtering of the shared connections and network traffic as it based
between the web browser and web server.
Configuration Process Description
The process for configuring the servers should be made clear in the essence that any person who
accesses the guideline can be able to understand the manual without problems. In order for one
to extremely capture all the details, there is a need to capture ThinkTank objectives and
requirements as stated in the case study. In this case, using the DNS server and the Web Server
the enterprise domain will be set as thinktank.com since it is to be accessed globally. The
network itself should be created in the manner that it is itself an active directory which will have
the root domain as thinktank.com. The other concept is understanding the work of the DNS [12].
DNS server will be fundamental in ensuring that the active directory has been able to establish
all the services which are available on thinktank.com domain indicating the provider of such
services.
Ideally, there will the use of a DHCP server that will be applied to make sure that all the IP
addresses are assigned automatically for the clients. In this concept, the network will be needed
to be in a centralized manner. There will be the use of the Lightweight Directory Access Control
that is needed when one wants to keep track of all the activities that are established over the
network. Notably, the Kerberos will be applied in handling log in that usually facilitate the use of
a single password as well as one username in accessing more than one PC. In building such a
network there is a need to use a windows server and Oracle Virtual Box. The following are
7 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

some of the minimum specifications that are mandatory and must be met for this configuration
process to be a success.
40 GB Hard Disk Drive Storage
3GB RAM
2v CPU
The above will help in creating a Host-Only network for the enterprise as shown below in the
given screenshots.
Configuration Screenshots
In this case, one has to install the Oracle VM VirtualBox in the machines depending on the OS
environment is using. In this case, the idea will be majoring in the windows environment.
Figure 1 Oracle VM VirtualBox Manager
To enable the functionality needed by the enterprise, one has to right click on the file after it has
been launched and select the host manager network and continue with the instructions as follows.
8 | P a g e
process to be a success.
40 GB Hard Disk Drive Storage
3GB RAM
2v CPU
The above will help in creating a Host-Only network for the enterprise as shown below in the
given screenshots.
Configuration Screenshots
In this case, one has to install the Oracle VM VirtualBox in the machines depending on the OS
environment is using. In this case, the idea will be majoring in the windows environment.
Figure 1 Oracle VM VirtualBox Manager
To enable the functionality needed by the enterprise, one has to right click on the file after it has
been launched and select the host manager network and continue with the instructions as follows.
8 | P a g e

After selecting the host network manager, click on the create button on the window that opens.
This will help in the creation of network interface that will help to assign the IP address that will
be in line with the enterprise needs.
Figure 2Selecting Properties
In this case, the configured adapter is assigned an IP address of 192.168.99.100 as shown above
in figure two. In this case, one has to click on apply so that the created VM can be modified with
regards to the enterprise network requirements as shown below.
On the Mac address click on advanced. Refresh the mac address for both adapters to be set. Set
up at least two adapters.
Adapter 1
Host only, Vboxnet()
9 | P a g e
This will help in the creation of network interface that will help to assign the IP address that will
be in line with the enterprise needs.
Figure 2Selecting Properties
In this case, the configured adapter is assigned an IP address of 192.168.99.100 as shown above
in figure two. In this case, one has to click on apply so that the created VM can be modified with
regards to the enterprise network requirements as shown below.
On the Mac address click on advanced. Refresh the mac address for both adapters to be set. Set
up at least two adapters.
Adapter 1
Host only, Vboxnet()
9 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
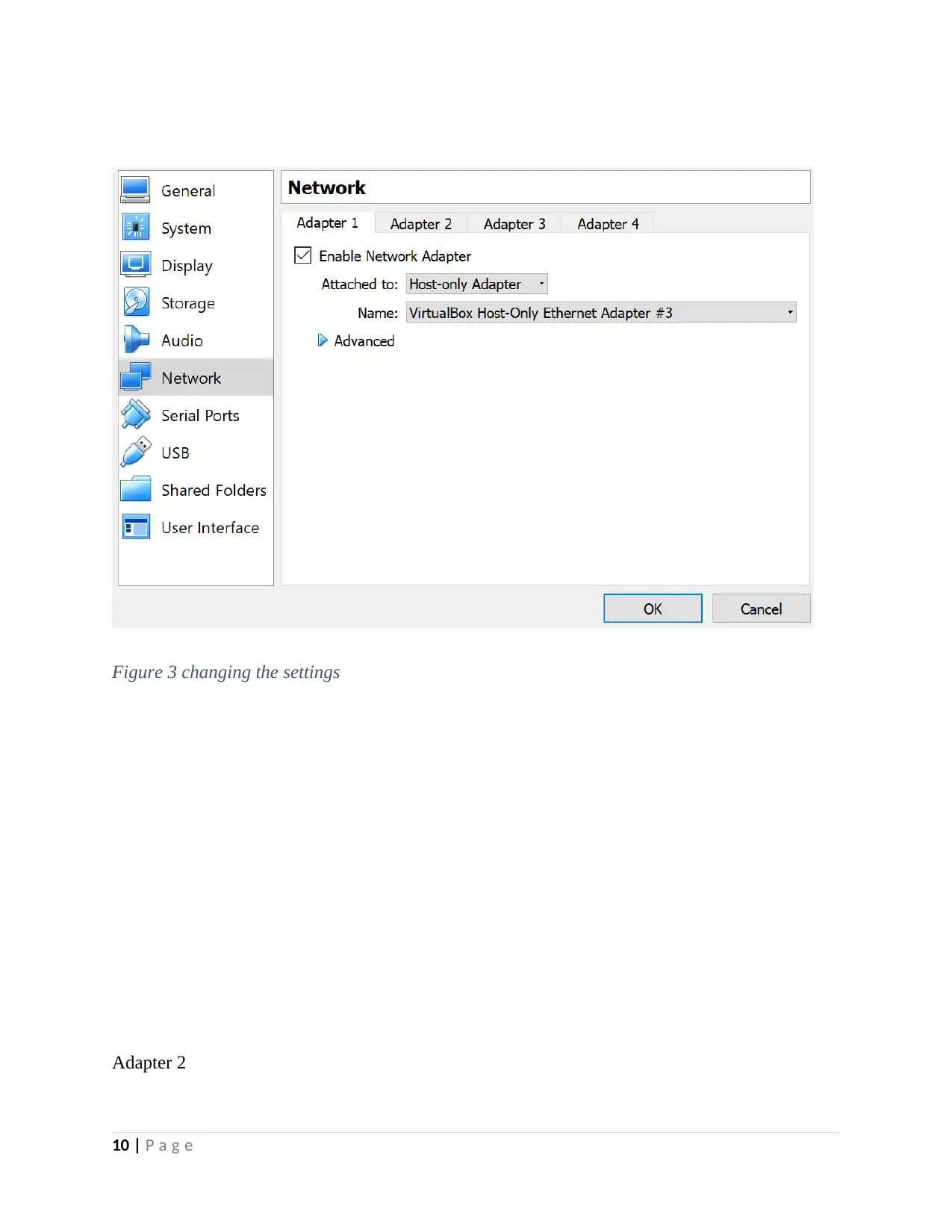
Figure 3 changing the settings
Adapter 2
10 | P a g e
Adapter 2
10 | P a g e
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NAT
Figure 4 NAT configuration
Configuration of the VM
In this case, one has to reboot the virtual machine and login via the console VirtualBox provides.
Open the terminal and execute this command.
11 | P a g e
Figure 4 NAT configuration
Configuration of the VM
In this case, one has to reboot the virtual machine and login via the console VirtualBox provides.
Open the terminal and execute this command.
11 | P a g e

Ideally, the code above will help in providing the adapter name on the virtual machine. In this
case, the adapters were named as eth1 and eth2 respectively where there are 1o and the loopback
interface. The configuration below was applied as shown in the figure below.
Immediately such code is run, it is good to restart the Virtual Machine and the VM will have
been configured as shown below. Once the machine is set the hostname in the host’s file will be
accessed as shown below.
“win => C:\Windows\System32\drivers\etc\hosts, Linux =>”
12 | P a g e
case, the adapters were named as eth1 and eth2 respectively where there are 1o and the loopback
interface. The configuration below was applied as shown in the figure below.
Immediately such code is run, it is good to restart the Virtual Machine and the VM will have
been configured as shown below. Once the machine is set the hostname in the host’s file will be
accessed as shown below.
“win => C:\Windows\System32\drivers\etc\hosts, Linux =>”
12 | P a g e
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





