A Study of Network Technologies: NAS, SAN, NBN, Tor, and Cryptojacking
VerifiedAdded on 2023/04/04
|13
|3929
|146
Homework Assignment
AI Summary
This assignment provides summaries of various network technologies. It covers Storage Area Networks (SAN), explaining their high-speed, block-level access to storage drives and their use of Fiber Channel technology. It also discusses Network File Systems (NFS), which allow remote hosts to mount file systems over a network. Furthermore, the assignment summarizes the National Broadband Network (NBN) in Australia, detailing its various delivery technologies like Fiber to the Premises (FTTP). It explores Tor, a technology for anonymizing online activity by routing traffic through multiple servers. Finally, the assignment discusses cryptojacking, a form of malware that steals computer resources for cryptocurrency mining, and the importance of network redundancy to cope with link or equipment failure. Desklib offers more solved assignments and study tools for students.
Week 1
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or
Storage Area Network (SAN) technologies. Find and summarise ONE resource that
describes EITHER NAS or SAN storage technologies. The resource, and your
summary, must focus on either NAS or SAN, NOT BOTH.
Title and Reference: What Is a Storage Area Network?
Snia.org. (2019). What Is a Storage Area Network? | SNIA. [online] Available at:
https://www.snia.org/education/storage_networking_primer/san/what_san [Accessed
25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
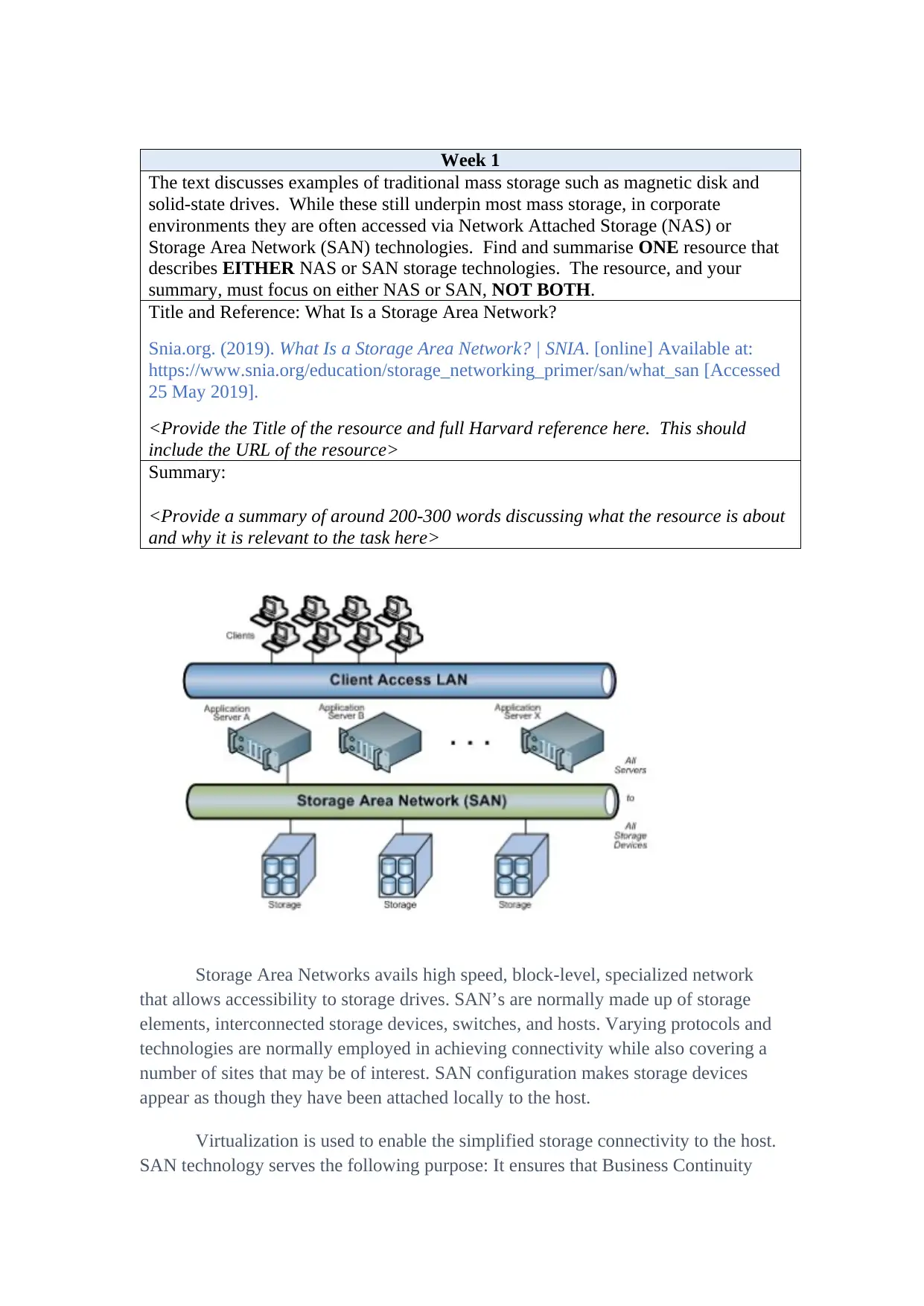
Storage Area Networks avails high speed, block-level, specialized network
that allows accessibility to storage drives. SAN’s are normally made up of storage
elements, interconnected storage devices, switches, and hosts. Varying protocols and
technologies are normally employed in achieving connectivity while also covering a
number of sites that may be of interest. SAN configuration makes storage devices
appear as though they have been attached locally to the host.
Virtualization is used to enable the simplified storage connectivity to the host.
SAN technology serves the following purpose: It ensures that Business Continuity
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or
Storage Area Network (SAN) technologies. Find and summarise ONE resource that
describes EITHER NAS or SAN storage technologies. The resource, and your
summary, must focus on either NAS or SAN, NOT BOTH.
Title and Reference: What Is a Storage Area Network?
Snia.org. (2019). What Is a Storage Area Network? | SNIA. [online] Available at:
https://www.snia.org/education/storage_networking_primer/san/what_san [Accessed
25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Storage Area Networks avails high speed, block-level, specialized network
that allows accessibility to storage drives. SAN’s are normally made up of storage
elements, interconnected storage devices, switches, and hosts. Varying protocols and
technologies are normally employed in achieving connectivity while also covering a
number of sites that may be of interest. SAN configuration makes storage devices
appear as though they have been attached locally to the host.
Virtualization is used to enable the simplified storage connectivity to the host.
SAN technology serves the following purpose: It ensures that Business Continuity
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Management can be sustained in an enterprise, it ensures that storage is fully and
efficiently utilized while upholding the important aspects of security and protection of
data, it boosts performance of applications, and also ensures that availability of
applications is improved. Fiber Channel (FC) Technology is primarily used in SAN
technology and the Fiber Channel Protocol (FCP) for mainframes and open systems is
utilized in this case. More importantly, the Fiber Channel over Ethernet (FCoE)
allows FC traffic to be moved over the already set up ethernet infrastructure that
supports high speed connectivity, while converging IP Protocols and Storage within a
single cable. Technologies such as Small Computing Interface (SCSI) are normally
utilized in SME’s since this offers a cheaper option unlike InfiniBand, and FC, which
are usually used to establish environments that offer highspeed capability.
Week 2
Operating systems use file managers to interact with mass storage devices. However,
the way in which data is stored and retrieved is dictated by the file system. There are
many types of file systems used by modern operating systems. Find and summarise
ONE resource that describes ONE such file system that is NOT FAT, FAT32 or
ExFAT. The resource, and your summary, must focus on A SINGLE file system.
Title and Reference: NTFS
Network File System (NFS)
Web.mit.edu. (2019). Chapter 18. Network File System (NFS). [online] Available at:
https://web.mit.edu/rhel-doc/5/RHEL-5-manual/Deployment_Guide-en-US/ch-
nfs.html [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
A network file system makes it possible for mounting of file systems via a
network by remote hosts. Also, NFS allows the remote hosts to interact with the
mounted file systems as if they have been locally mounted. The primary importance
of this is that it allows IT technician to put together resources on servers that are
centralized quite efficiently. At the moment, three versions of NFS are available for
use. They include, NFSv2, which happens to be very common and greatly supported
by many systems. NFSv3 have a huge number of features such as Safe Async Writes,
advanced Error handling capabilities, and 64bit file handling capability.
There is also NFSv4 which is able to work efficiently on the internet and
through firewalls. This version doesn’t need ACLs, portmapper, and makes use on the
efficiently utilized while upholding the important aspects of security and protection of
data, it boosts performance of applications, and also ensures that availability of
applications is improved. Fiber Channel (FC) Technology is primarily used in SAN
technology and the Fiber Channel Protocol (FCP) for mainframes and open systems is
utilized in this case. More importantly, the Fiber Channel over Ethernet (FCoE)
allows FC traffic to be moved over the already set up ethernet infrastructure that
supports high speed connectivity, while converging IP Protocols and Storage within a
single cable. Technologies such as Small Computing Interface (SCSI) are normally
utilized in SME’s since this offers a cheaper option unlike InfiniBand, and FC, which
are usually used to establish environments that offer highspeed capability.
Week 2
Operating systems use file managers to interact with mass storage devices. However,
the way in which data is stored and retrieved is dictated by the file system. There are
many types of file systems used by modern operating systems. Find and summarise
ONE resource that describes ONE such file system that is NOT FAT, FAT32 or
ExFAT. The resource, and your summary, must focus on A SINGLE file system.
Title and Reference: NTFS
Network File System (NFS)
Web.mit.edu. (2019). Chapter 18. Network File System (NFS). [online] Available at:
https://web.mit.edu/rhel-doc/5/RHEL-5-manual/Deployment_Guide-en-US/ch-
nfs.html [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
A network file system makes it possible for mounting of file systems via a
network by remote hosts. Also, NFS allows the remote hosts to interact with the
mounted file systems as if they have been locally mounted. The primary importance
of this is that it allows IT technician to put together resources on servers that are
centralized quite efficiently. At the moment, three versions of NFS are available for
use. They include, NFSv2, which happens to be very common and greatly supported
by many systems. NFSv3 have a huge number of features such as Safe Async Writes,
advanced Error handling capabilities, and 64bit file handling capability.
There is also NFSv4 which is able to work efficiently on the internet and
through firewalls. This version doesn’t need ACLs, portmapper, and makes use on the

most important operations. All the versions of the NFS can employ Transmission
Control Protocol (TCP) that runs via an Internet Protocol Network. This is a critical
component of NFSv4. On the other hand, NFSv3 and NFSv2 can optionally employ
User Datagram Protocol (UDP) that uses the IP network as its main platform in order
to avail a network connection that is stateless between the server and client.
Week 3
The National Broadband Network (NBN) is currently being rolled-out across
Australia and there is a mix of technologies that are being used to deliver Internet
services (for example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find
and summarise ONE resource that describes ONE of these delivery technologies.
The resource, and your summary, must focus on A SINGLE technology.
Title and Reference: How does the nbn™ work?
Mate. (2019). How does the nbn™ work?. [online] Available at:
https://www.letsbemates.com.au/how-does-the-nbn-work/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
The National Broadband Network is considered to be Australia’s digital
future. The NBN is a project established by Australis national Data Network and it
allows users to gain access to high-speed broadband connectivity both at work and
home. The nbnTM is primarily owned by the government and operates as a wholesale
availability system that allows service producers to gain connectivity, and in turn they
are able to offer connectivity to the small clients. The nbnTM seeks to overrule the
former internet, phone, and data networks, and its advantage is that it enables users to
gain extremely high-speed connectivity to entire populations.
The NBN incorporate four primary technologies, which are; satellite, Optica
Fiber, Fixed Wireless, and Pay TV cable. Using this technology, NBN is able to
support the following types of connectivity: Fiber to the Node (FTTN), Fiber to the
Premises (FTTP), and Fiber to the Building. Fiber to the Premises is the most
common, and it’s basically a fiber optic that goes through homes then ends at the
Network Termination Device (NTD). Using the NTD, homes are able to subscribe to
services to more than four data providers while having two phone services. FTTP can
be availed through laying new cables or with connecting new fiber cables to the
already established telephone network.
Week 4
Control Protocol (TCP) that runs via an Internet Protocol Network. This is a critical
component of NFSv4. On the other hand, NFSv3 and NFSv2 can optionally employ
User Datagram Protocol (UDP) that uses the IP network as its main platform in order
to avail a network connection that is stateless between the server and client.
Week 3
The National Broadband Network (NBN) is currently being rolled-out across
Australia and there is a mix of technologies that are being used to deliver Internet
services (for example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find
and summarise ONE resource that describes ONE of these delivery technologies.
The resource, and your summary, must focus on A SINGLE technology.
Title and Reference: How does the nbn™ work?
Mate. (2019). How does the nbn™ work?. [online] Available at:
https://www.letsbemates.com.au/how-does-the-nbn-work/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
The National Broadband Network is considered to be Australia’s digital
future. The NBN is a project established by Australis national Data Network and it
allows users to gain access to high-speed broadband connectivity both at work and
home. The nbnTM is primarily owned by the government and operates as a wholesale
availability system that allows service producers to gain connectivity, and in turn they
are able to offer connectivity to the small clients. The nbnTM seeks to overrule the
former internet, phone, and data networks, and its advantage is that it enables users to
gain extremely high-speed connectivity to entire populations.
The NBN incorporate four primary technologies, which are; satellite, Optica
Fiber, Fixed Wireless, and Pay TV cable. Using this technology, NBN is able to
support the following types of connectivity: Fiber to the Node (FTTN), Fiber to the
Premises (FTTP), and Fiber to the Building. Fiber to the Premises is the most
common, and it’s basically a fiber optic that goes through homes then ends at the
Network Termination Device (NTD). Using the NTD, homes are able to subscribe to
services to more than four data providers while having two phone services. FTTP can
be availed through laying new cables or with connecting new fiber cables to the
already established telephone network.
Week 4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or hide
online their online activities. Find and summarise ONE resource that describes what
Tor is and how it works. The resource, and your summary, must focus purely on Tor.
Title and Reference: What is the Tor Browser? How it works and how it can help
you protect your identity online
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
The Tor technology enables users to disguise their identity while on the
network, thereby, allowing a person to move traffic anonymously across multiple
servers. The tor network encrypts the traffic that is being transferred so that the
destination cannot be tracked. Trying to analyse the destination only shows network
nodes rather than the exact computer that has made a request. Tor was developed to
allows people to remain anonymous while on the internet, and this was undertaken by
the US navy when they undertook to establish a ring of network servers all over the
globe. However, the network is currently used for non profit purposes and provides a
platform for researching how online privacy tools can be developed.
In order to surf the tor network, one has to use the tor browser as it uses the
technology in the network to anonymize traffic. The downside of using the tor
network to surf is the fact that is tend to be a little bit slower than the clear internet, at
the same time, various web service providers block Tor users. Tor network is made up
of a three-layer proxy, and this is what allows network traffic to be anonymized. In
the Tor network, Connections are made randomly to an entry node that is publicly
listed. The node will then bounce all traffic that goes through it to a middle relay that
is also randomly selected. Finally, the traffic is spit out of the network using a
randomly selected exit node.
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or hide
online their online activities. Find and summarise ONE resource that describes what
Tor is and how it works. The resource, and your summary, must focus purely on Tor.
Title and Reference: What is the Tor Browser? How it works and how it can help
you protect your identity online
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
The Tor technology enables users to disguise their identity while on the
network, thereby, allowing a person to move traffic anonymously across multiple
servers. The tor network encrypts the traffic that is being transferred so that the
destination cannot be tracked. Trying to analyse the destination only shows network
nodes rather than the exact computer that has made a request. Tor was developed to
allows people to remain anonymous while on the internet, and this was undertaken by
the US navy when they undertook to establish a ring of network servers all over the
globe. However, the network is currently used for non profit purposes and provides a
platform for researching how online privacy tools can be developed.
In order to surf the tor network, one has to use the tor browser as it uses the
technology in the network to anonymize traffic. The downside of using the tor
network to surf is the fact that is tend to be a little bit slower than the clear internet, at
the same time, various web service providers block Tor users. Tor network is made up
of a three-layer proxy, and this is what allows network traffic to be anonymized. In
the Tor network, Connections are made randomly to an entry node that is publicly
listed. The node will then bounce all traffic that goes through it to a middle relay that
is also randomly selected. Finally, the traffic is spit out of the network using a
randomly selected exit node.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 5
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
What is Cryptojacking? How it Works And How You Can Prevent It
Weiss, T. (2019). What is Cryptojacking? How it Works And How You Can Prevent
It. [online] ChainBits. Available at:
https://www.chainbits.com/cryptocurrencies/what-is-cryptojacking/ [Accessed 25
May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Cryptpojacking is basically malicious crypto mining, and it is a developing
threat to legitimate crypto miners. This vice has surpassed the number of malware
attacks that get to be perpetrated every year. The hack vice involves stealing of a
computers central processing unit (CPU) and all the resources on a supposed miner’s
system so that they are redirected to serve the illegal crypto mining activity. This is
not perpetrated on a single computer, but thousands of systems, laptops, desktops, and
windows servers. In some cases, mobile devices are also hacked for this purpose.
Cyber criminals find ways of using other people’s systems to avail the mining powers
as they don’t have the financial capability of purchasing expensive systems needed to
undertake legitimate mining. More so, they mine anonymous coins like Monero or
ZCash as this makes it quite hard to track (Weiss, 2019).
Cryptpojacking affects systems by increasing the utilization of resources
hence making electric bills to spike much higher. Cryptpojacking works using two
primary methods, which are; malware scripts and In-Browser JavaScript code. The
Malware is normally installed through a download link, which enables the malware to
be installed into the user’s system. The other option involves embedding the malware
script into a browser and when any system that browses that website, it automatically
becomes infected. Preventing Cryptpojacking is however quite hard and most
antivirus solutions fail to offer protection against this vice. However, a user can
protect themselves using an ad-blocker in whichever system they use, installing
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
What is Cryptojacking? How it Works And How You Can Prevent It
Weiss, T. (2019). What is Cryptojacking? How it Works And How You Can Prevent
It. [online] ChainBits. Available at:
https://www.chainbits.com/cryptocurrencies/what-is-cryptojacking/ [Accessed 25
May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Cryptpojacking is basically malicious crypto mining, and it is a developing
threat to legitimate crypto miners. This vice has surpassed the number of malware
attacks that get to be perpetrated every year. The hack vice involves stealing of a
computers central processing unit (CPU) and all the resources on a supposed miner’s
system so that they are redirected to serve the illegal crypto mining activity. This is
not perpetrated on a single computer, but thousands of systems, laptops, desktops, and
windows servers. In some cases, mobile devices are also hacked for this purpose.
Cyber criminals find ways of using other people’s systems to avail the mining powers
as they don’t have the financial capability of purchasing expensive systems needed to
undertake legitimate mining. More so, they mine anonymous coins like Monero or
ZCash as this makes it quite hard to track (Weiss, 2019).
Cryptpojacking affects systems by increasing the utilization of resources
hence making electric bills to spike much higher. Cryptpojacking works using two
primary methods, which are; malware scripts and In-Browser JavaScript code. The
Malware is normally installed through a download link, which enables the malware to
be installed into the user’s system. The other option involves embedding the malware
script into a browser and when any system that browses that website, it automatically
becomes infected. Preventing Cryptpojacking is however quite hard and most
antivirus solutions fail to offer protection against this vice. However, a user can
protect themselves using an ad-blocker in whichever system they use, installing

plugins such as miner block or No Coin. Finally, a lasting solution could involve
installing malware solution that protects the entire system.
Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link
failure. Note that the failure must relate to a link that connects countries and/or
continents.
Title and Reference:
Redundancy in Cabling: A Must-Have for Any Network
Connector and Cable Assembly Supplier. (2019). Redundancy in Cabling: A Must-
Have for Any Network System. [online] Available at:
https://www.connectorsupplier.com/redundancy-cabling-a-must-have-for-any-
network/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Cabling redundancy is nowadays a standard for data centres and network
management unlike in the past where it was considered to be too much of a forward-
thinking approach. Redundancy has become a primary approach because of the
following reasons.
It offers security.
Redundancy ensures safety of transmitting data in the event that there is fibre
option cable failure. This helps to sustain the operability of an entire system
irrespective of whether there is a downtime. Any data centre and network manager’s
primary objective is to avoid as much as possible the existence of total downtime
especially in this era of extreme competition where clients expect unrivalled
performance at all times. Enduring downtime is entirely dependent on the value that is
attached to an enterprise network, and how important it is to fulfilling second to
second/ day-to-day operations. Also, to what level does revenue generation of an
organization depend on the network. In this digital age, this latter point is normally
100%. Therefore, a downtime isn’t something that can be tolerated.
installing malware solution that protects the entire system.
Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link
failure. Note that the failure must relate to a link that connects countries and/or
continents.
Title and Reference:
Redundancy in Cabling: A Must-Have for Any Network
Connector and Cable Assembly Supplier. (2019). Redundancy in Cabling: A Must-
Have for Any Network System. [online] Available at:
https://www.connectorsupplier.com/redundancy-cabling-a-must-have-for-any-
network/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Cabling redundancy is nowadays a standard for data centres and network
management unlike in the past where it was considered to be too much of a forward-
thinking approach. Redundancy has become a primary approach because of the
following reasons.
It offers security.
Redundancy ensures safety of transmitting data in the event that there is fibre
option cable failure. This helps to sustain the operability of an entire system
irrespective of whether there is a downtime. Any data centre and network manager’s
primary objective is to avoid as much as possible the existence of total downtime
especially in this era of extreme competition where clients expect unrivalled
performance at all times. Enduring downtime is entirely dependent on the value that is
attached to an enterprise network, and how important it is to fulfilling second to
second/ day-to-day operations. Also, to what level does revenue generation of an
organization depend on the network. In this digital age, this latter point is normally
100%. Therefore, a downtime isn’t something that can be tolerated.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
A Two-Way Street
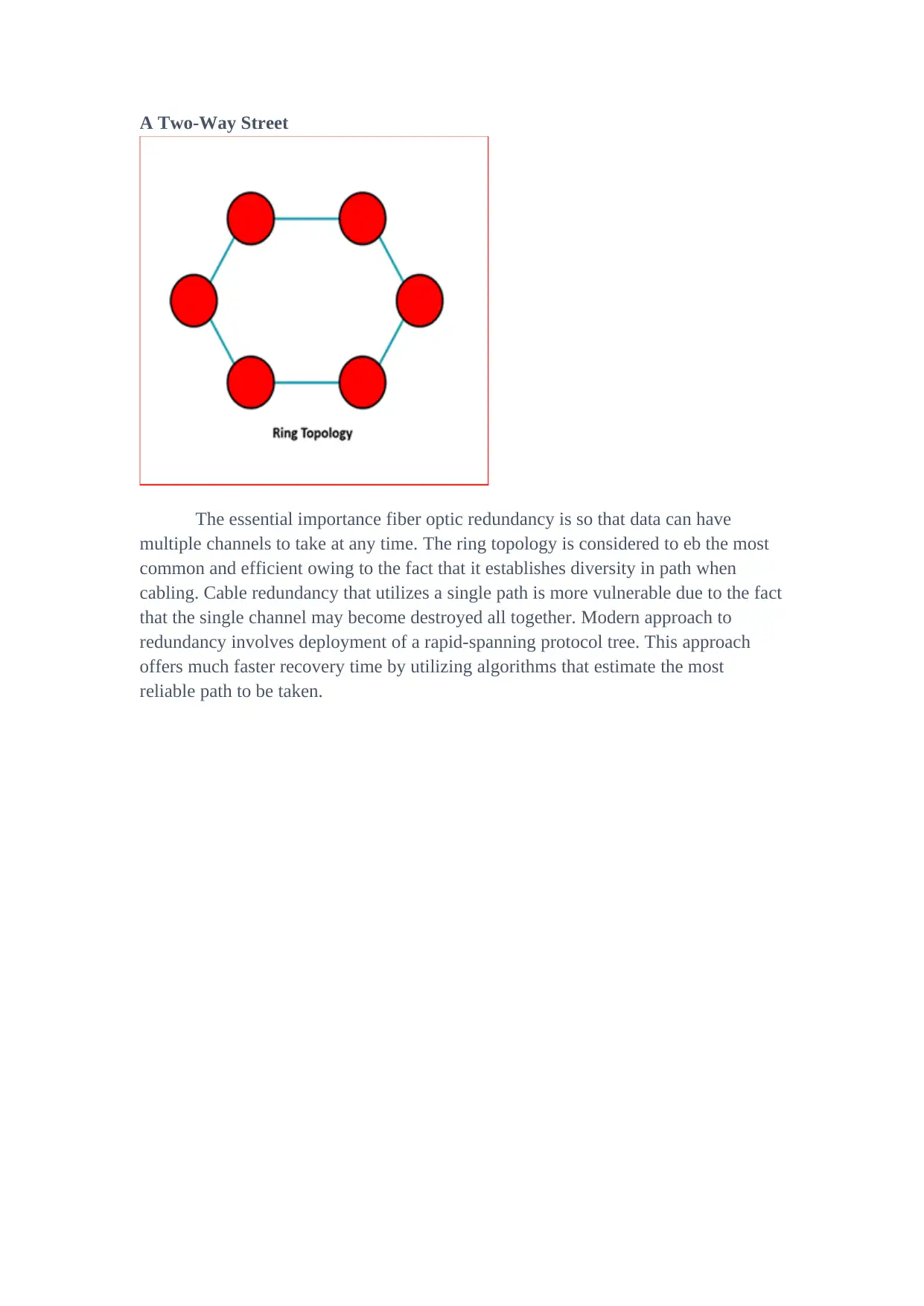
The essential importance fiber optic redundancy is so that data can have
multiple channels to take at any time. The ring topology is considered to eb the most
common and efficient owing to the fact that it establishes diversity in path when
cabling. Cable redundancy that utilizes a single path is more vulnerable due to the fact
that the single channel may become destroyed all together. Modern approach to
redundancy involves deployment of a rapid-spanning protocol tree. This approach
offers much faster recovery time by utilizing algorithms that estimate the most
reliable path to be taken.
The essential importance fiber optic redundancy is so that data can have
multiple channels to take at any time. The ring topology is considered to eb the most
common and efficient owing to the fact that it establishes diversity in path when
cabling. Cable redundancy that utilizes a single path is more vulnerable due to the fact
that the single channel may become destroyed all together. Modern approach to
redundancy involves deployment of a rapid-spanning protocol tree. This approach
offers much faster recovery time by utilizing algorithms that estimate the most
reliable path to be taken.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 7
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this time,
ES/ERPs have evolved and continue to change in response to new demands and
emerging technologies. Find and summarise ONE resource that discusses emerging or
future trends for ES/ERPs. The resource should be recent (published since the
beginning of 2017) and it and your summary should clearly identify how ES/ERPs
are, or are about to, change.
Title and Reference: Future Trends in ERP Systems
Sam, G. (2019). Future Trends in ERP Systems. [online] Medium. Available at:
https://medium.com/@gracesam989/future-trends-in-erp-systems-42b0fe582b83
[Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
In this era, most businesses that have passed the start-up phase will most likely
implement an Enterprise Resource Planning Software. This system has become one of the most
deepened upon IT system over the years by businesses and has evolved a lot since it was
incepted. Now that technology is evolving quite fast, ERP solutions is bound to experience a
huge change, and various trends are bound to be established in regards to the change that is
rapidly occurring in the current market place. The first trend revolves around Cloud Deployment,
and its where ERP solutions are rapidly adopting cloud solutions. This has helped to greatly
reduce heavy depended on IT resources and capital expenditure.
This also helps to sustain flexibility and better maintenance approaches can be adopted.
Most importantly, disaster recovery approaches have become more streamlined while security of
the systems has been made much better unlike in the past. With respect to change in these
aspects, ERP solutions are bound to rapidly be taken up by small enterprises and it will no longer
be big enterprise affair. This is because the implementation ERP systems is bound to encounter
lower costs, making it available for all types of businesses. Increased security will ensure that
ERP systems are able to tightly control the sharing of data as the need of shared data and IoT
continues to grow much further.
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this time,
ES/ERPs have evolved and continue to change in response to new demands and
emerging technologies. Find and summarise ONE resource that discusses emerging or
future trends for ES/ERPs. The resource should be recent (published since the
beginning of 2017) and it and your summary should clearly identify how ES/ERPs
are, or are about to, change.
Title and Reference: Future Trends in ERP Systems
Sam, G. (2019). Future Trends in ERP Systems. [online] Medium. Available at:
https://medium.com/@gracesam989/future-trends-in-erp-systems-42b0fe582b83
[Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
In this era, most businesses that have passed the start-up phase will most likely
implement an Enterprise Resource Planning Software. This system has become one of the most
deepened upon IT system over the years by businesses and has evolved a lot since it was
incepted. Now that technology is evolving quite fast, ERP solutions is bound to experience a
huge change, and various trends are bound to be established in regards to the change that is
rapidly occurring in the current market place. The first trend revolves around Cloud Deployment,
and its where ERP solutions are rapidly adopting cloud solutions. This has helped to greatly
reduce heavy depended on IT resources and capital expenditure.
This also helps to sustain flexibility and better maintenance approaches can be adopted.
Most importantly, disaster recovery approaches have become more streamlined while security of
the systems has been made much better unlike in the past. With respect to change in these
aspects, ERP solutions are bound to rapidly be taken up by small enterprises and it will no longer
be big enterprise affair. This is because the implementation ERP systems is bound to encounter
lower costs, making it available for all types of businesses. Increased security will ensure that
ERP systems are able to tightly control the sharing of data as the need of shared data and IoT
continues to grow much further.

Week 8
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private information
is illegally obtained or disclosed. Find and summarise ONE resource that describes
ONE example of a data breach that has occurred since the beginning of 2017. The
resource, and your summary, should focus purely on A SINGLE EXAMPLE of a
data breach.
Title and Reference: Equifax Data Breach
Center, E. (2019). EPIC - Equifax Data Breach. [online] Epic.org. Available at:
https://epic.org/privacy/data-breach/equifax/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Equifax is among the biggest client credit reporting organizations in the US and the
breach on the company’s systems occurred in the period around July 2017. The breach on the
company’s system led to the loss of data for 150million person in America. The data breach
targeted data relating to phone numbers, home addresses, social security numbers, dates of birth,
drivers licence number etc. Additionally, credit card numbers than 209 000 clients ended up
being breached. The breach is considered to one of the most severed one to occur in the past
decade primarily due to the sensitivity of data that was contained in the systems. As credit
Reporting agency, Equifax undertakes the collection of people’s data from bank so as to keep a
track record of their loan history so that is can be easy for lenders to determine the credit
worthiness of a person.
The breach targeted data from the dispute web portal rather than the core of Equifax
client reporting database. The breach was caused by a vulnerability known as Apache Struts
CVE-2017-5638. The Apache Struts is a framework that is commonly used by Apache Software
foundation to create Java Web Applications. A patch had been released by the foundation on
March 7 2017, but upon scanning of the system by Equifax, the patch wasn’t made since no
threat was found to exist. However, in July 29 2017, suspicious activity was discovered in the
dispute web portal the web application was consequently taken down. Investigations by
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private information
is illegally obtained or disclosed. Find and summarise ONE resource that describes
ONE example of a data breach that has occurred since the beginning of 2017. The
resource, and your summary, should focus purely on A SINGLE EXAMPLE of a
data breach.
Title and Reference: Equifax Data Breach
Center, E. (2019). EPIC - Equifax Data Breach. [online] Epic.org. Available at:
https://epic.org/privacy/data-breach/equifax/ [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Equifax is among the biggest client credit reporting organizations in the US and the
breach on the company’s systems occurred in the period around July 2017. The breach on the
company’s system led to the loss of data for 150million person in America. The data breach
targeted data relating to phone numbers, home addresses, social security numbers, dates of birth,
drivers licence number etc. Additionally, credit card numbers than 209 000 clients ended up
being breached. The breach is considered to one of the most severed one to occur in the past
decade primarily due to the sensitivity of data that was contained in the systems. As credit
Reporting agency, Equifax undertakes the collection of people’s data from bank so as to keep a
track record of their loan history so that is can be easy for lenders to determine the credit
worthiness of a person.
The breach targeted data from the dispute web portal rather than the core of Equifax
client reporting database. The breach was caused by a vulnerability known as Apache Struts
CVE-2017-5638. The Apache Struts is a framework that is commonly used by Apache Software
foundation to create Java Web Applications. A patch had been released by the foundation on
March 7 2017, but upon scanning of the system by Equifax, the patch wasn’t made since no
threat was found to exist. However, in July 29 2017, suspicious activity was discovered in the
dispute web portal the web application was consequently taken down. Investigations by
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Mandiant Security revealed that the data of more than 145 million clients in UK, Canada and Us
had been affected.
Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference: Scrum
Cohn, M. (2019). Scrum Methodology and Project Management. [online] Mountain
Goat Software. Available at: https://www.mountaingoatsoftware.com/agile/scrum
[Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Scrum forms part of the agile development process. The Agile approach for development
was established as a response for the failures exhibited by many of the development approach
that were used in the past, especially waterfall. Scrum tends to be greatly related with lean
approach of development. Scrum is normally viewed as a framework rather than a methodology.
Scrum relies on the precepts of sprints. Scrum is based on the principles of cross functional and
self-organizing teams. In this case, there is no overall leader, rather, everything in the project is
decided by the team. Sprint meetings are normally undertaken on the basis of what is highly
desired by everyone.
Cross-functional implies that every team member is needed to take up a feature and drive
it until it reaches the implementation stage. The functionality of Scrum team members is
supported by two primary roles. These include the ScrumMaster Product Owner. The Scrum
Master sums up as the coach for the entire team and ensure that members can perform maximally
while the Product Owner is basically the system user, business, or client, that outlines how a
product will be developed correctly (Cohn, 2019). The scrum framework suggests that products
are developed in stages of sprints so as to keep up with guidelines of agile development. The
sprints are mostly timed to no more than one month. Meeting’s should be planned at the start of
each sprint and then team members should be allowed to select items that they can deliver on by
had been affected.
Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference: Scrum
Cohn, M. (2019). Scrum Methodology and Project Management. [online] Mountain
Goat Software. Available at: https://www.mountaingoatsoftware.com/agile/scrum
[Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Scrum forms part of the agile development process. The Agile approach for development
was established as a response for the failures exhibited by many of the development approach
that were used in the past, especially waterfall. Scrum tends to be greatly related with lean
approach of development. Scrum is normally viewed as a framework rather than a methodology.
Scrum relies on the precepts of sprints. Scrum is based on the principles of cross functional and
self-organizing teams. In this case, there is no overall leader, rather, everything in the project is
decided by the team. Sprint meetings are normally undertaken on the basis of what is highly
desired by everyone.
Cross-functional implies that every team member is needed to take up a feature and drive
it until it reaches the implementation stage. The functionality of Scrum team members is
supported by two primary roles. These include the ScrumMaster Product Owner. The Scrum
Master sums up as the coach for the entire team and ensure that members can perform maximally
while the Product Owner is basically the system user, business, or client, that outlines how a
product will be developed correctly (Cohn, 2019). The scrum framework suggests that products
are developed in stages of sprints so as to keep up with guidelines of agile development. The
sprints are mostly timed to no more than one month. Meeting’s should be planned at the start of
each sprint and then team members should be allowed to select items that they can deliver on by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

the time the next sprint is held. Team members will then have to outline tasks that have been
undertaken at each stage of the sprint. Scrum framework uses daily scrums to synchronize tasks
accomplished by each team member as discussions are held on the purpose of each sprint.
Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance is
and what activities it entails. The resource, and your summary, should focus purely on
project governance.
Title and Reference: Why is Project Governance Critical to Project Success?
Invensislearning.com. (2019). Why is project governance critical to project success? |
Invensis Learning. [online] Available at:
https://www.invensislearning.com/resources/pmp/why-is-project-governance-critical-
to-project-success [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Project governance is a primary oversight function that is normally established in line
with the governance model that has been taken up in an organization. This function encompasses
all stages of a project’s life cycle. Project governance allows the project manager to have access
to models for decision making, a team that is well structured, tools for controlling and managing
the entire project, and all process that are undertaken in the organization. Where risky.
Complicated project is being undertaken, project governance serves as an essential tool since it
communicates, documents, and defines consistencies around the project, thereby, providing a
well detailed method of controlling the whole project to fruition.
Project governance provides a well-defined framework that allows the project manager to
make apt decisions about different components of the project, while defining roles, liabilities,
responsibilities, and accomplishments. Establishing project governance is not an easy task as it
requires a huge investment to be made at the onset of a project. The other challenging part is
identifying its importance int eh entire project, and this can be summarized by the following four
primary points.
undertaken at each stage of the sprint. Scrum framework uses daily scrums to synchronize tasks
accomplished by each team member as discussions are held on the purpose of each sprint.
Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance is
and what activities it entails. The resource, and your summary, should focus purely on
project governance.
Title and Reference: Why is Project Governance Critical to Project Success?
Invensislearning.com. (2019). Why is project governance critical to project success? |
Invensis Learning. [online] Available at:
https://www.invensislearning.com/resources/pmp/why-is-project-governance-critical-
to-project-success [Accessed 25 May 2019].
<Provide the Title of the resource and full Harvard reference here. This should
include the URL of the resource>
Summary:
<Provide a summary of around 200-300 words discussing what the resource is about
and why it is relevant to the task here>
Project governance is a primary oversight function that is normally established in line
with the governance model that has been taken up in an organization. This function encompasses
all stages of a project’s life cycle. Project governance allows the project manager to have access
to models for decision making, a team that is well structured, tools for controlling and managing
the entire project, and all process that are undertaken in the organization. Where risky.
Complicated project is being undertaken, project governance serves as an essential tool since it
communicates, documents, and defines consistencies around the project, thereby, providing a
well detailed method of controlling the whole project to fruition.
Project governance provides a well-defined framework that allows the project manager to
make apt decisions about different components of the project, while defining roles, liabilities,
responsibilities, and accomplishments. Establishing project governance is not an easy task as it
requires a huge investment to be made at the onset of a project. The other challenging part is
identifying its importance int eh entire project, and this can be summarized by the following four
primary points.

It stipulates the responsibilities, roles, and associations among various stakeholders in the
project.
It provides the project with a single source for accountability.
Project governance establishes proper communication from the onset thereby allowing
information to be evenly distributed.
Most importantly, it provides a point of making resolutions and general management.
Lacking project governance can run aground even the best outlined projects. As much as it is
essential to incorporate innovativeness and technical insight into the project, the essentiality f
project governance cannot be undermined.
project.
It provides the project with a single source for accountability.
Project governance establishes proper communication from the onset thereby allowing
information to be evenly distributed.
Most importantly, it provides a point of making resolutions and general management.
Lacking project governance can run aground even the best outlined projects. As much as it is
essential to incorporate innovativeness and technical insight into the project, the essentiality f
project governance cannot be undermined.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




