COIT 20246 Assignment: Analysis of Network Technologies and Security
VerifiedAdded on 2022/11/13
|12
|3946
|103
Homework Assignment
AI Summary
This COIT 20246 assignment delves into various aspects of network technologies and security. The assignment requires students to research and summarize resources on topics including Network Attached Storage (NAS) and Storage Area Network (SAN) technologies, focusing on their functionalities and advantages. It also covers file systems, specifically NTFS, exploring its features and efficiency compared to other file systems. Furthermore, the assignment examines NBN delivery technologies, focusing on Fibre to the Node (FTTN), and the Tor browser, discussing its functionalities and security measures. Students are also tasked with understanding cryptojacking, its mechanisms, and preventative measures, along with the impact of link failures in network infrastructure, using a real-world example of a cable cut. The assignment emphasizes the importance of understanding various network technologies and their associated security concerns and implications. Students were instructed to provide summaries for each week's task with specific details, including the resource's main points, usefulness, and their selection rationale, all while adhering to proper citation and referencing guidelines.

COIT 20246 ASSIGNMENT SUBMISSION
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Due date: Thursday Week 11 (2PM AEST)
Part: Written Assessment
Weighting: 30% of total assessment.
Submission: Electronic (see course website for details)
Please fill in the following details:
Student Name
Student Number
Tutor’s Name
Instructions
It will be necessary to use online resources to complete this assignment, please
ensure you cite and reference any such materials using the Harvard format.
DO NOT copy content directly from either the text or Internet resources: this
assignment is to be in your own words. You will lose marks if you do not use
your own words!
Please complete your assignment using this submission template file, inserting your
responses where indicated.
DO NOT delete the marking criteria page – changes are permitted to the
formatting of other pages including the headers and footers.
Tasks
There are ten (10) tasks, one for each week: the tasks are detailed below. There is
a table to complete for each task. Please fill in the information required.
Note: Each resource summary should be around 200-300 words.
Each summary should briefly explain:
- What the resource is about
- Why you selected it
- What are the main points or key information covered in the resource
- Why the resource was useful.
For more advice about how to complete the assignment, as well as examples and
information about selecting good resources, please see the assessment page on the
Moodle unit web site:
https://moodle.cqu.edu.au/mod/assign/view.php?id=886270
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 1
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or Storage
Area Network (SAN) technologies. Find and summarise ONE resource that describes
EITHER NAS or SAN storage technologies. The resource, and your summary, must
focus on either NAS or SAN, NOT BOTH.
Title and Reference:
Anon, (2019). [online] Available at: https://www.computereconomics.com/article.cfm?
id=1283 [Accessed 27 May 2019].
https://www.computereconomics.com/article.cfm?id=1283
Summary:
This resource was very much helpful to understand the concept of Storage Area
Network (SAN) is a detailed manner. SAN can be defined as the type of high speed
network which can be very much helpful to provide block level network access to
storage. This resource is selected because it provides a detailed description of the
advantages provided by SAN. The application availability of networking devices can be
solved using SAN. The application performance can also be improved using the
storage utilization and effectiveness. Business Continuity Management (BCM) activities
can also be improved using SAN. SAN can be widely used in other technologies as
well, such as the Fibre Channel (FC) technology. The main point of discussing of this
paper is the detailed usability of SAN. SAN is a collection of storage elements, storage
devices, host and switches which are interconnected with each other using a wide
range of topologies, technologies and protocols. SAN can be controlled using the SAN
switches. It can be said that most of the SAN stitches is Ethernet based. There are
different categories of SAN which are available such as converged SAN, unified SAN
and virtual SAN. This resource was very much helpful to understand the connection
between SAN and client access LAN.
2
The text discusses examples of traditional mass storage such as magnetic disk and
solid-state drives. While these still underpin most mass storage, in corporate
environments they are often accessed via Network Attached Storage (NAS) or Storage
Area Network (SAN) technologies. Find and summarise ONE resource that describes
EITHER NAS or SAN storage technologies. The resource, and your summary, must
focus on either NAS or SAN, NOT BOTH.
Title and Reference:
Anon, (2019). [online] Available at: https://www.computereconomics.com/article.cfm?
id=1283 [Accessed 27 May 2019].
https://www.computereconomics.com/article.cfm?id=1283
Summary:
This resource was very much helpful to understand the concept of Storage Area
Network (SAN) is a detailed manner. SAN can be defined as the type of high speed
network which can be very much helpful to provide block level network access to
storage. This resource is selected because it provides a detailed description of the
advantages provided by SAN. The application availability of networking devices can be
solved using SAN. The application performance can also be improved using the
storage utilization and effectiveness. Business Continuity Management (BCM) activities
can also be improved using SAN. SAN can be widely used in other technologies as
well, such as the Fibre Channel (FC) technology. The main point of discussing of this
paper is the detailed usability of SAN. SAN is a collection of storage elements, storage
devices, host and switches which are interconnected with each other using a wide
range of topologies, technologies and protocols. SAN can be controlled using the SAN
switches. It can be said that most of the SAN stitches is Ethernet based. There are
different categories of SAN which are available such as converged SAN, unified SAN
and virtual SAN. This resource was very much helpful to understand the connection
between SAN and client access LAN.
2

Week 2
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference:
TechRepublic. (2019). News, Tips, and Advice for Technology Professionals -
TechRepublic. [online] Available at: https://www.techrepublic.com/article/file-
systems-101-ntfs/ [Accessed 27 May 2019].
https://www.techrepublic.com/article/file-systems-101-ntfs/
Summary:
This resource highlights the effectiveness and usability of the New Technology File
System (NTFS). NTFS technology is much more advanced and error free as
compared with the other similar technologies. Detailed description of the NTFS
technology is the main reason behind choosing this technology. One of the prime
features of this technology is that it can be used in a b-tree directory scheme,
tracking of the file cluster can be done using the NTFS technology. The main points if
this paper is the usability of this technology as it can be very much useful to support
larger files which are used in most of the global commercial establishments. The key
information of this resource is the ability of the NTFS technology as it supports both
short as well as long file names. The backup facility of NTFS technology was also
highlighted in this resource in an organized manner. The resources also help in
understanding the usability and the security of NTFS technology. The efficiency of
NTFS is way better than FAT32 or ExFAT. NTFS technology can be very much
useful to provide data security as it can transparently encrypt files. The resource was
very much useful to understand the transparent file compression service of the NTFS
technology.
3
Operating systems use file managers to interact with mass storage devices.
However, the way in which data is stored and retrieved is dictated by the file system.
There are many types of file systems used by modern operating systems. Find and
summarise ONE resource that describes ONE such file system that is NOT FAT,
FAT32 or ExFAT. The resource, and your summary, must focus on A SINGLE file
system.
Title and Reference:
TechRepublic. (2019). News, Tips, and Advice for Technology Professionals -
TechRepublic. [online] Available at: https://www.techrepublic.com/article/file-
systems-101-ntfs/ [Accessed 27 May 2019].
https://www.techrepublic.com/article/file-systems-101-ntfs/
Summary:
This resource highlights the effectiveness and usability of the New Technology File
System (NTFS). NTFS technology is much more advanced and error free as
compared with the other similar technologies. Detailed description of the NTFS
technology is the main reason behind choosing this technology. One of the prime
features of this technology is that it can be used in a b-tree directory scheme,
tracking of the file cluster can be done using the NTFS technology. The main points if
this paper is the usability of this technology as it can be very much useful to support
larger files which are used in most of the global commercial establishments. The key
information of this resource is the ability of the NTFS technology as it supports both
short as well as long file names. The backup facility of NTFS technology was also
highlighted in this resource in an organized manner. The resources also help in
understanding the usability and the security of NTFS technology. The efficiency of
NTFS is way better than FAT32 or ExFAT. NTFS technology can be very much
useful to provide data security as it can transparently encrypt files. The resource was
very much useful to understand the transparent file compression service of the NTFS
technology.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 3
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference:
Whistleout.com.au. (2019). NBN Fibre to the Node: Everything you need to know.
[online] Available at: https://www.whistleout.com.au/Broadband/Guides/nbn-fttn-
everything-you-need-to-know [Accessed 27 May 2019].
https://www.whistleout.com.au/Broadband/Guides/nbn-fttn-everything-you-need-to-
know
Summary:
This resource is very much important to understand FTTN technology which are extensively
used in the telecommunication services. This technology is widely used in Australia's National
Broadband Network rollout. The speed of this technology is much more than other similar
technologies such as the HFC and FTTC. The use of this technology is increasing every day
in both commercial establishments as well as in our society. This resource is very much
useful to understand the advantages as well as the disadvantages of FTTN technology.
Based on the discussion on the paper, it can be said that the fixed range of service provided
by this technology is one of the main constraints of this technology. One of the main benefits
of the paper is that it helps in identifying most of the advantages of this technology in terms of
its increased speed. The cost of the FTTN technology is always dynamic in nature, which is
the key point of discussion of this paper. This resource is very much helpful to understand the
expectation of the consumers of this technology. The resource also helps in identifying that
each of the customers of this technology must be within one mile radius.
4
The National Broadband Network (NBN) is currently being rolled-out across Australia
and there is a mix of technologies that are being used to deliver Internet services (for
example, FTTN, FTTC, FTTP, HFC, fixed wireless and satellite). Find and
summarise ONE resource that describes ONE of these delivery technologies. The
resource, and your summary, must focus on A SINGLE technology.
Title and Reference:
Whistleout.com.au. (2019). NBN Fibre to the Node: Everything you need to know.
[online] Available at: https://www.whistleout.com.au/Broadband/Guides/nbn-fttn-
everything-you-need-to-know [Accessed 27 May 2019].
https://www.whistleout.com.au/Broadband/Guides/nbn-fttn-everything-you-need-to-
know
Summary:
This resource is very much important to understand FTTN technology which are extensively
used in the telecommunication services. This technology is widely used in Australia's National
Broadband Network rollout. The speed of this technology is much more than other similar
technologies such as the HFC and FTTC. The use of this technology is increasing every day
in both commercial establishments as well as in our society. This resource is very much
useful to understand the advantages as well as the disadvantages of FTTN technology.
Based on the discussion on the paper, it can be said that the fixed range of service provided
by this technology is one of the main constraints of this technology. One of the main benefits
of the paper is that it helps in identifying most of the advantages of this technology in terms of
its increased speed. The cost of the FTTN technology is always dynamic in nature, which is
the key point of discussion of this paper. This resource is very much helpful to understand the
expectation of the consumers of this technology. The resource also helps in identifying that
each of the customers of this technology must be within one mile radius.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 4
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference:
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 27 May 2019].
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html
Summary:
This resource is very much important to understand the specification of the Tor
browser which is increasingly used in our society as well as in commercial
establishment all over the world. Tor browser can be used in different operating
systems such as Microsoft Windows, Apple MAC OS. The security measures of the
tor browser is stated in the paper in a detailed manner, which is the main reason of
selecting this paper. The blocker facility of the Tor blockers is much impressive as it
helps to improve the security as well as the privacy of the users of this Tor browser.
The main point of discussion of this paper is the usefulness of this browser. This
browser is also very much useful to access the .onion websites which is exclusively
used in the Tor network. This research is very much useful to understand the various
categories of subsets associated with this browser such as the Tor network and the
Tor messenger. This resource was very much helpful to understand the limitations
associated with this technology as it restricts the user to access of the torrent
websites. This resource is very much useful to understand the bandwidth issue of the
Tor browser as well.
5
The Internet is made up of many interconnected servers and networks. Users are
increasingly aware and concerned that their Internet communications can be
intercepted and monitored. Tor is one technology that allows users to obscure or
hide online their online activities. Find and summarise ONE resource that describes
what Tor is and how it works. The resource, and your summary, must focus purely on
Tor.
Title and Reference:
Porup, J. (2019). What is the Tor Browser? How it works and how protects your
identity. [online] CSO Online. Available at:
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html [Accessed 27 May 2019].
https://www.csoonline.com/article/3287653/what-is-the-tor-browser-how-it-works-
and-how-it-can-help-you-protect-your-identity-online.html
Summary:
This resource is very much important to understand the specification of the Tor
browser which is increasingly used in our society as well as in commercial
establishment all over the world. Tor browser can be used in different operating
systems such as Microsoft Windows, Apple MAC OS. The security measures of the
tor browser is stated in the paper in a detailed manner, which is the main reason of
selecting this paper. The blocker facility of the Tor blockers is much impressive as it
helps to improve the security as well as the privacy of the users of this Tor browser.
The main point of discussion of this paper is the usefulness of this browser. This
browser is also very much useful to access the .onion websites which is exclusively
used in the Tor network. This research is very much useful to understand the various
categories of subsets associated with this browser such as the Tor network and the
Tor messenger. This resource was very much helpful to understand the limitations
associated with this technology as it restricts the user to access of the torrent
websites. This resource is very much useful to understand the bandwidth issue of the
Tor browser as well.
5

Week 5
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
Nadeau, M. (2019). What is cryptojacking? How to prevent, detect, and recover from
it. [online] CSO Online. Available at:
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html [Accessed 27 May 2019].
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html
Summary:
This resource is very much useful to understand the concept of crypto jacking
procedure, which is extensively used by most of the social engineers all around the
world. Crypto jacking can be defined as the use of the computing device which are
used for the malware activities. The resource is very much important to understand
the incorporation of the bit coins in the crypto-jacking procedure. The computing
resources of the users can be identified using the crypto-jacking procedure.
Computer botnets are increasingly used in crypto-jacking. The use of the script
codes in crypto jacking can also be identified from this resource which is the main
reason behind the selection of this resource. The selection of this resource is very
much justified as it helps in the identification of the security concerns of crypto
jacking. The main points of discussion of this paper is the detailed description of the
crypto mining botnets which has to be managed by technical IT experts. The key
point of discussion of this paper is that it helps in identifying the exact impact of
crypto jacking. The CPU processing resources are directly compromised during the
crypto jacking procedure. The resources was very much useful to understand that
the crypto-jacking procedure is very much vulnerable to the social engineers as well
as it can damage the devices used by the social engineers during crypto-jacking.
6
An emerging form of malware is cryptojacking (also known as malicious
cryptomining). Find and summarise ONE resource that describes what cryptojacking
is and how it works. The resource, and your summary, should focus purely on
cryptojacking and NO OTHER form(s) of malware.
Title and Reference:
Nadeau, M. (2019). What is cryptojacking? How to prevent, detect, and recover from
it. [online] CSO Online. Available at:
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html [Accessed 27 May 2019].
https://www.csoonline.com/article/3253572/what-is-cryptojacking-how-to-prevent-
detect-and-recover-from-it.html
Summary:
This resource is very much useful to understand the concept of crypto jacking
procedure, which is extensively used by most of the social engineers all around the
world. Crypto jacking can be defined as the use of the computing device which are
used for the malware activities. The resource is very much important to understand
the incorporation of the bit coins in the crypto-jacking procedure. The computing
resources of the users can be identified using the crypto-jacking procedure.
Computer botnets are increasingly used in crypto-jacking. The use of the script
codes in crypto jacking can also be identified from this resource which is the main
reason behind the selection of this resource. The selection of this resource is very
much justified as it helps in the identification of the security concerns of crypto
jacking. The main points of discussion of this paper is the detailed description of the
crypto mining botnets which has to be managed by technical IT experts. The key
point of discussion of this paper is that it helps in identifying the exact impact of
crypto jacking. The CPU processing resources are directly compromised during the
crypto jacking procedure. The resources was very much useful to understand that
the crypto-jacking procedure is very much vulnerable to the social engineers as well
as it can damage the devices used by the social engineers during crypto-jacking.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 6
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference:
Johnson, B. (2019). Internet connection cut between Europe, Asia and Africa.
[online] the Guardian. Available at:
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut [Accessed 27
May 2019].
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut
Summary:
This resource helps in the identification of an incident where optical cable
connections were disrupted between numerous countries. This resource helps in
identifying the impact of an internet blackout between countries such as Africa,
Europe and Asia. This resource helps in understanding the damage done in the
undersea cable, which links Europe, Africa and Asia. The entire internet traffic of
these regions was affected due to this attack.
The main reason behind selecting this paper is it helps in understanding the damage
done during this cable failure. The resources states that the main damage was done
to the cable which runs between Italy and Egypt. This resources also stated that this
major accident occurred due to either earthquake or from the anchor of a ship. The
main point of focus of this resources is the description of the impact of this cable cut,
it was assumed that more than 75 million users across the affected areas could not
access to the internet for several days due to this accident. The other key information
of this paper is it help in the identification of the situation where people are suffering
from internet issues in-spite of having the access of the wireless internet connections
and satellite connections. Thus, this resource was very much useful to understand
the impact of a cable being cut which connected numerous countries as well as
continents.
7
Redundancy is a critical aspect of network design, implemented in order to cope link
or equipment failure. One frequent cause of failure is damage to fibre optic cables
that connect countries and/or continents. Find and summarise ONE resource that
describes ONE example of such a cable being cut or damaged. The resource, and
your summary, should describe the impacts of A SINGLE EXAMPLE of a link failure.
Note that the failure must relate to a link that connects countries and/or continents.
Title and Reference:
Johnson, B. (2019). Internet connection cut between Europe, Asia and Africa.
[online] the Guardian. Available at:
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut [Accessed 27
May 2019].
https://www.theguardian.com/world/2008/dec/21/internet-cable-cut
Summary:
This resource helps in the identification of an incident where optical cable
connections were disrupted between numerous countries. This resource helps in
identifying the impact of an internet blackout between countries such as Africa,
Europe and Asia. This resource helps in understanding the damage done in the
undersea cable, which links Europe, Africa and Asia. The entire internet traffic of
these regions was affected due to this attack.
The main reason behind selecting this paper is it helps in understanding the damage
done during this cable failure. The resources states that the main damage was done
to the cable which runs between Italy and Egypt. This resources also stated that this
major accident occurred due to either earthquake or from the anchor of a ship. The
main point of focus of this resources is the description of the impact of this cable cut,
it was assumed that more than 75 million users across the affected areas could not
access to the internet for several days due to this accident. The other key information
of this paper is it help in the identification of the situation where people are suffering
from internet issues in-spite of having the access of the wireless internet connections
and satellite connections. Thus, this resource was very much useful to understand
the impact of a cable being cut which connected numerous countries as well as
continents.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 7
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference:
Harpham, B. (2019). 6 ERP trends for 2018. [online] CIO. Available at:
https://www.cio.com/article/3285653/6-erp-trends-for-2018.html [Accessed 27 May
2019].
https://www.cio.com/article/3285653/6-erp-trends-for-2018.html
Summary:
Published on 3rd July 2018, this resources helps in the identification of the future
trends of the Enterprise resource planning. This resource can be very much useful
for the readers of this document to understand the 6 important trends of 2018. Top
future trends of the ERP system is the main point of discussion of this resource. The
resource stated that the ERP system will be playing a huge in most of the manually
processing payments. Most of the fraudulent activities will now be tracked by the
latest ERP systems. The security concerns of the payment system will be also be
minimised in the ERP systems.
The compatibility issues of the ERP with Excel will also be reduced in the coming
years. The issues during the enactment of the ERP in global establishments will also
be addressed in the coming years. This paper was selected to understand the future
trends of the ERP systems. The most key information of this resource is it helps to
understand the incorporation of numerous technologies such as Augmented Reality
and Artificial Intelligence in the ERP systems. Thus, this resource is was very much
useful to understand the future trends of ERP system from different perspectives.
8
Since the 1990s, Enterprise Systems (also known as Enterprise Resource Planning
systems) have become critical to the operation modern organisations. Over this
time, ES/ERPs have evolved and continue to change in response to new demands
and emerging technologies. Find and summarise ONE resource that discusses
emerging or future trends for ES/ERPs. The resource should be recent (published
since the beginning of 2017) and it and your summary should clearly identify how
ES/ERPs are, or are about to, change.
Title and Reference:
Harpham, B. (2019). 6 ERP trends for 2018. [online] CIO. Available at:
https://www.cio.com/article/3285653/6-erp-trends-for-2018.html [Accessed 27 May
2019].
https://www.cio.com/article/3285653/6-erp-trends-for-2018.html
Summary:
Published on 3rd July 2018, this resources helps in the identification of the future
trends of the Enterprise resource planning. This resource can be very much useful
for the readers of this document to understand the 6 important trends of 2018. Top
future trends of the ERP system is the main point of discussion of this resource. The
resource stated that the ERP system will be playing a huge in most of the manually
processing payments. Most of the fraudulent activities will now be tracked by the
latest ERP systems. The security concerns of the payment system will be also be
minimised in the ERP systems.
The compatibility issues of the ERP with Excel will also be reduced in the coming
years. The issues during the enactment of the ERP in global establishments will also
be addressed in the coming years. This paper was selected to understand the future
trends of the ERP systems. The most key information of this resource is it helps to
understand the incorporation of numerous technologies such as Augmented Reality
and Artificial Intelligence in the ERP systems. Thus, this resource is was very much
useful to understand the future trends of ERP system from different perspectives.
8

Week 8
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference:
U.S. (2019). Cathay Pacific faces probe over massive data breach. [online] Available
at: https://www.reuters.com/article/us-cathaypacific-cyber/cathay-pacific-faces-probe-
over-massive-data-breach-idUSKCN1NB0JY [Accessed 27 May 2019].
https://www.reuters.com/article/us-cathaypacific-cyber/cathay-pacific-faces-probe-
over-massive-data-breach-idUSKCN1NB0JY
Summary:
The resource is about the famous data breaching incident of 2008, where
confidential information of 9.4 million passengers of the Hong Kong Airport were
compromised by the social engineers. This resource was selected as this data
breach incident was identified after seven months. The resource helps in
understanding the impact of this security breach, as a result, this Airport Corporation
faces huge criticism. The prime point of discussing of this paper is it helps in
understanding that security measures which has to be maintained in most of the
corporate establishment where data is considered as an asset. The resources stated
that personal data of more than 860000 passport numbers were compromised during
this data breach event. This resource also identified the movement of more than
427725 flights for a period of seven months. Most of the business data from the
cargo planes were altered by the social engineers during this data breaching attack.
The main points of the paper is the security measures taken by the Airport authority
so that they can deal with the future data breaching activities such as this one. This
resource was very much useful to understand the security measures which are
needed to be taken by the investigative departments after a data breaching attack.
9
Databases, mass data storage and interrogation technologies underpin virtually all
Information Systems and applications. However, the same tools also make it easier
for data breaches to occur in government departments or private
companies/organisations. In simple terms, a data breach is where private
information is illegally obtained or disclosed. Find and summarise ONE resource that
describes ONE example of a data breach that has occurred since the beginning of
2017. The resource, and your summary, should focus purely on A SINGLE
EXAMPLE of a data breach.
Title and Reference:
U.S. (2019). Cathay Pacific faces probe over massive data breach. [online] Available
at: https://www.reuters.com/article/us-cathaypacific-cyber/cathay-pacific-faces-probe-
over-massive-data-breach-idUSKCN1NB0JY [Accessed 27 May 2019].
https://www.reuters.com/article/us-cathaypacific-cyber/cathay-pacific-faces-probe-
over-massive-data-breach-idUSKCN1NB0JY
Summary:
The resource is about the famous data breaching incident of 2008, where
confidential information of 9.4 million passengers of the Hong Kong Airport were
compromised by the social engineers. This resource was selected as this data
breach incident was identified after seven months. The resource helps in
understanding the impact of this security breach, as a result, this Airport Corporation
faces huge criticism. The prime point of discussing of this paper is it helps in
understanding that security measures which has to be maintained in most of the
corporate establishment where data is considered as an asset. The resources stated
that personal data of more than 860000 passport numbers were compromised during
this data breach event. This resource also identified the movement of more than
427725 flights for a period of seven months. Most of the business data from the
cargo planes were altered by the social engineers during this data breaching attack.
The main points of the paper is the security measures taken by the Airport authority
so that they can deal with the future data breaching activities such as this one. This
resource was very much useful to understand the security measures which are
needed to be taken by the investigative departments after a data breaching attack.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Week 9
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference:
Simplilearn.com. (2019). Scrum Project Management Pros and Cons | CSM Training.
[online] Available at: https://www.simplilearn.com/scrum-project-management-article
[Accessed 27 May 2019].
https://www.simplilearn.com/scrum-project-management-article
Summary:
The key features as well as the key attributes of the Scrum framework which are
increasingly used in most of the complex product development projects. The
resources provided a detailed description of the advantages of the Scrum framework.
The most significant benefits of the Scrum framework is that it saves time and money
as compared with the other similar frameworks. Both the moving as well as the non-
moving objects of this project can be quantified using the Scrum methodology. The
visibility and transparency of the project is improved if the stakeholders of the project
uses this framework. This resource is selected because it provides the practical
implementation procedure of the scrum framework in complicated product
development projects. The main points of discussion of this paper is that it considers
the opinion of both the internal as well as the external stakeholders of the project.
The other key information which was provided in the paper is the individual effort
needed from each of the team members of a project. Commitment level of the project
members are very much required in the scrum methodology. Thus, this resource was
very much useful to understand the benefits of using the Scrum methodology in
product development projects.
10
Agile development is an iterative and incremental approach to delivering systems - it
is particularly useful where the requirements are unclear or evolving. Scrum is a
framework for undertaking agile development. Find and summarise ONE resource
that describes Scrum. The resource, and your summary, should focus purely on
Scrum and discuss some of its key features and attributes.
Title and Reference:
Simplilearn.com. (2019). Scrum Project Management Pros and Cons | CSM Training.
[online] Available at: https://www.simplilearn.com/scrum-project-management-article
[Accessed 27 May 2019].
https://www.simplilearn.com/scrum-project-management-article
Summary:
The key features as well as the key attributes of the Scrum framework which are
increasingly used in most of the complex product development projects. The
resources provided a detailed description of the advantages of the Scrum framework.
The most significant benefits of the Scrum framework is that it saves time and money
as compared with the other similar frameworks. Both the moving as well as the non-
moving objects of this project can be quantified using the Scrum methodology. The
visibility and transparency of the project is improved if the stakeholders of the project
uses this framework. This resource is selected because it provides the practical
implementation procedure of the scrum framework in complicated product
development projects. The main points of discussion of this paper is that it considers
the opinion of both the internal as well as the external stakeholders of the project.
The other key information which was provided in the paper is the individual effort
needed from each of the team members of a project. Commitment level of the project
members are very much required in the scrum methodology. Thus, this resource was
very much useful to understand the benefits of using the Scrum methodology in
product development projects.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Week 10
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference:
Pmi.org. (2019). Governance rules! The principles of effective project governance.
[online] Available at: https://www.pmi.org/learning/library/project-governance-
principles-corporate-perspective-6528 [Accessed 27 May 2019].
https://www.pmi.org/learning/library/project-governance-principles-corporate-
perspective-6528
Summary:
This resource provided in depth discussion about the activities of project governance.
The resource helps in understanding the role of project governance in complicated
projects. The resource highlighted that the performance of any commercial
establishment can depend huge on the project governance plan. The decision
making activities of complicated projects are done using this project governance
plans. The main reason behind selecting this paper is the reliability of the source of
the paper. This resource was published in the year 2010 from the Project
Management Institute. The main point of discussion of this paper is characteristics of
good project governance which are the accountability of the stakeholders,
transparency in the business procedure, efficiency and responsiveness of the
stakeholders, equal participation of each of the stakeholders. The important areas
which have to be focused during the use of project governance such as the clear
defined role and responsibilities can also be identified from the paper as well. The
resources help in understanding that the risk management of project can be done in
an organized manner using project governance plans. The resource also stated that
project governance is directly associated with corporate governance and delivery
capability of the project. Thus, this resource was very much useful to understand how
project governance can be implemented in a corporate establishment.
11
The textbook discusses activities associated with project management. However, it
could be argued that project governance is equally important, especially in very large
projects. Find and summarise ONE resource that describes what project governance
is and what activities it entails. The resource, and your summary, should focus purely
on project governance.
Title and Reference:
Pmi.org. (2019). Governance rules! The principles of effective project governance.
[online] Available at: https://www.pmi.org/learning/library/project-governance-
principles-corporate-perspective-6528 [Accessed 27 May 2019].
https://www.pmi.org/learning/library/project-governance-principles-corporate-
perspective-6528
Summary:
This resource provided in depth discussion about the activities of project governance.
The resource helps in understanding the role of project governance in complicated
projects. The resource highlighted that the performance of any commercial
establishment can depend huge on the project governance plan. The decision
making activities of complicated projects are done using this project governance
plans. The main reason behind selecting this paper is the reliability of the source of
the paper. This resource was published in the year 2010 from the Project
Management Institute. The main point of discussion of this paper is characteristics of
good project governance which are the accountability of the stakeholders,
transparency in the business procedure, efficiency and responsiveness of the
stakeholders, equal participation of each of the stakeholders. The important areas
which have to be focused during the use of project governance such as the clear
defined role and responsibilities can also be identified from the paper as well. The
resources help in understanding that the risk management of project can be done in
an organized manner using project governance plans. The resource also stated that
project governance is directly associated with corporate governance and delivery
capability of the project. Thus, this resource was very much useful to understand how
project governance can be implemented in a corporate establishment.
11
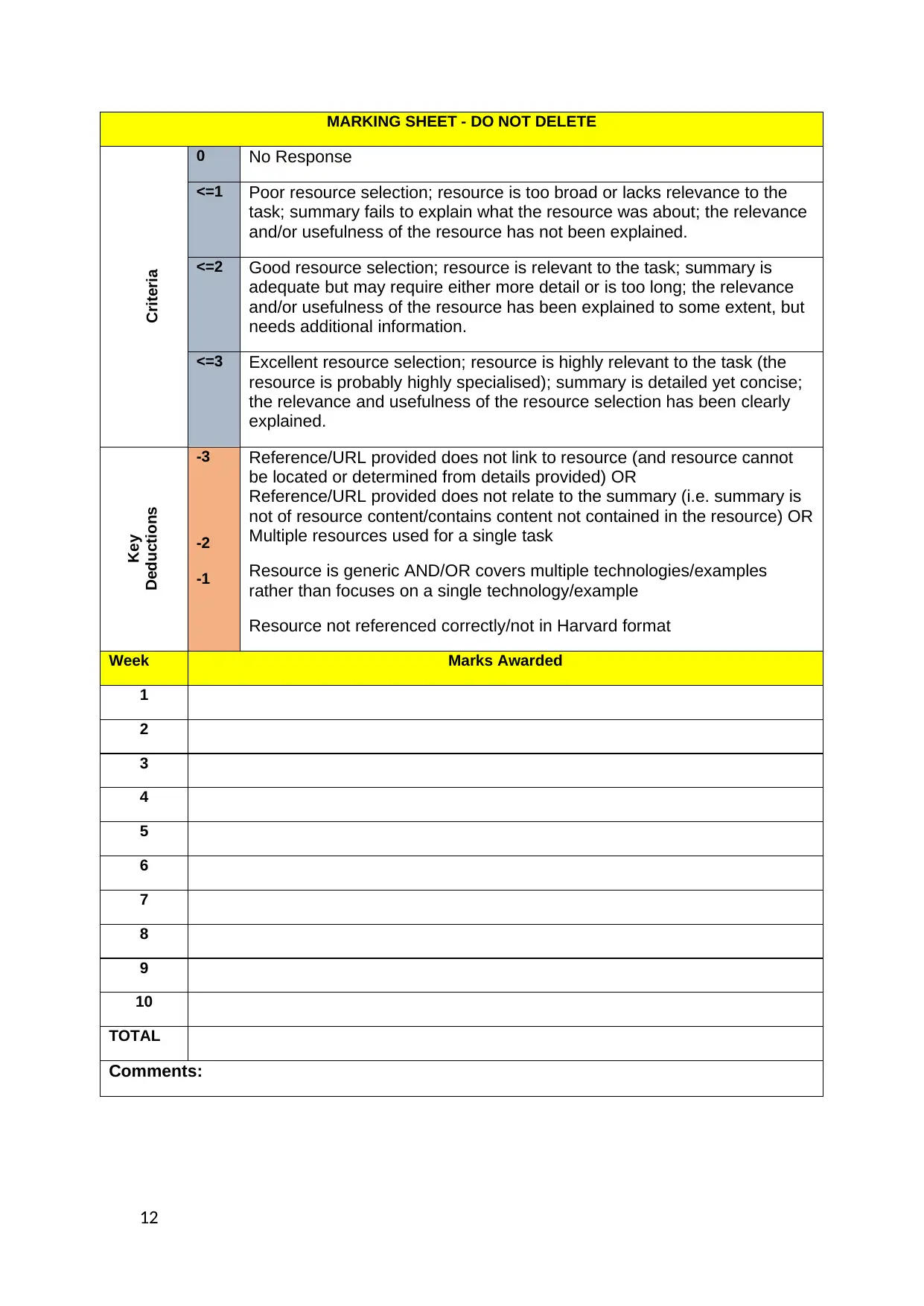
MARKING SHEET - DO NOT DELETE
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
12
Criteria
0 No Response
<=1 Poor resource selection; resource is too broad or lacks relevance to the
task; summary fails to explain what the resource was about; the relevance
and/or usefulness of the resource has not been explained.
<=2 Good resource selection; resource is relevant to the task; summary is
adequate but may require either more detail or is too long; the relevance
and/or usefulness of the resource has been explained to some extent, but
needs additional information.
<=3 Excellent resource selection; resource is highly relevant to the task (the
resource is probably highly specialised); summary is detailed yet concise;
the relevance and usefulness of the resource selection has been clearly
explained.
Key
Deductions
-3
-2
-1
Reference/URL provided does not link to resource (and resource cannot
be located or determined from details provided) OR
Reference/URL provided does not relate to the summary (i.e. summary is
not of resource content/contains content not contained in the resource) OR
Multiple resources used for a single task
Resource is generic AND/OR covers multiple technologies/examples
rather than focuses on a single technology/example
Resource not referenced correctly/not in Harvard format
Week Marks Awarded
1
2
3
4
5
6
7
8
9
10
TOTAL
Comments:
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



