BN203 Network Security Assignment: Identifying Network Threats
VerifiedAdded on 2023/06/04
|9
|1788
|54
Report
AI Summary
This report details the identification of network threats using Nmap and Metasploit, focusing on a VNC server penetration test. The introduction highlights the increasing importance of network security due to the proliferation of internet-connected devices and the potential for cyber intrusions. The report explains the functionalities of Nmap for network scanning and Metasploit for exploiting vulnerabilities. A literature review summarizes existing research on vulnerability assessment, penetration testing methodologies, and the use of tools like Nmap and Metasploit. The penetration test involves using Nmap to discover a VNC server running on port 5900 and subsequently employing Metasploit to exploit a weak password. The report then outlines various mitigation techniques to reduce the risk associated with VNC vulnerabilities, such as changing default ports, disabling unused features, using firewalls, and running malware detection software. The conclusion emphasizes the effectiveness of Nmap and Metasploit for vulnerability testing, while also stressing the importance of obtaining proper authorization before conducting such tests.

IDENTIFICATION OF THREATS USING NMAP AND METASPLOIT NETWORK
SECURITY TOOLS
Student
Tutor
Institutional Affiliation
Date
SECURITY TOOLS
Student
Tutor
Institutional Affiliation
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Identification of Threats using Nmap and Metasploit Network Security Tools
Introduction
In many eyes, the home intrusion has always been physical break-ins. However, the
trending fashion of having many internet connected devices in our homes have precipitated
another type of intrusion. This intrusion involves one whose target is the home network and
where the internet-connected devices are potentially open to compromise, this might lead to
devastating consequences and loses if the system is attacked by the intruders (cybercriminals).
Following this rationale, there is a need for a defensive mechanism to prevent these intruders
from gaining access into the home system.
As a prominent technique for assessing system security, a system penetration method is a
method that attempts to break into the target system legally using tools and technologies that are
similar to the techniques used by the cybercriminals. For the purpose of this assignment, two
tools were selected based on the empirical research to assess the vulnerability of a home system.
The following tools were utilized in the network assessment:
Nmap
Nmap, Network Nmap, is a useful tool in penetration testing for a general purpose
network scanning. It refers to a host and a network scanner which scans open, filtered or closed
ports, it also has the ability to make OS assumption through packet signature [5]. The Nmap tool
was used in detecting the victim machines, it utilizes the open ports, versions, and OS to exploit
the network vulnerability in the victimized machines. The Nmap tool is compatible with varieties
of the operating system including Linux, Windows, Mac OS X among other several platforms. It
Introduction
In many eyes, the home intrusion has always been physical break-ins. However, the
trending fashion of having many internet connected devices in our homes have precipitated
another type of intrusion. This intrusion involves one whose target is the home network and
where the internet-connected devices are potentially open to compromise, this might lead to
devastating consequences and loses if the system is attacked by the intruders (cybercriminals).
Following this rationale, there is a need for a defensive mechanism to prevent these intruders
from gaining access into the home system.
As a prominent technique for assessing system security, a system penetration method is a
method that attempts to break into the target system legally using tools and technologies that are
similar to the techniques used by the cybercriminals. For the purpose of this assignment, two
tools were selected based on the empirical research to assess the vulnerability of a home system.
The following tools were utilized in the network assessment:
Nmap
Nmap, Network Nmap, is a useful tool in penetration testing for a general purpose
network scanning. It refers to a host and a network scanner which scans open, filtered or closed
ports, it also has the ability to make OS assumption through packet signature [5]. The Nmap tool
was used in detecting the victim machines, it utilizes the open ports, versions, and OS to exploit
the network vulnerability in the victimized machines. The Nmap tool is compatible with varieties
of the operating system including Linux, Windows, Mac OS X among other several platforms. It

has the capability of scanning open ports using various standardized TCP packet options with
numerous options of command lines [1].
Metasploit
Metasploit framework, on the other hand, was used to exploit development, penetration
testing and almost everything that may be needed by a pen tester. Metasploit involved various
key steps to exploit the system network comprising selection and configuration of the target
exploit, validation to find out whether the selected system is vulnerable to the exploit, selection
and configuration of payloads to be used in the exploit, selection and configuration of the
encoding schema in order to ensure that the payload can easily avoid the intrusion detection
system and execute the exploit finally [6].
Both Nmap and Metasploit combined together made a good team of tools which
contributed a great deal during the home system network assessment [9]. Nmap provided the
information regarding the victim machines with potential vulnerabilities in order to make
payloads using Metasploit.
Literature review
Shah, [8] illustrate vulnerability assessment and penetration testing VAPT for cyber
defense. The author expounds that this approach helps in finding the vulnerabilities in advance
before a cyber-attack take place for preventing an information system from being compromised
by the cyber-criminals. The VAPT consist of a step by step process with nine phases. Shah
proves through her vulnerability assessment results that VAPT is a fundamental technique for the
technology of cyber defense [8]. Plus, VAPT, as proposed by the author, allows a system
numerous options of command lines [1].
Metasploit
Metasploit framework, on the other hand, was used to exploit development, penetration
testing and almost everything that may be needed by a pen tester. Metasploit involved various
key steps to exploit the system network comprising selection and configuration of the target
exploit, validation to find out whether the selected system is vulnerable to the exploit, selection
and configuration of payloads to be used in the exploit, selection and configuration of the
encoding schema in order to ensure that the payload can easily avoid the intrusion detection
system and execute the exploit finally [6].
Both Nmap and Metasploit combined together made a good team of tools which
contributed a great deal during the home system network assessment [9]. Nmap provided the
information regarding the victim machines with potential vulnerabilities in order to make
payloads using Metasploit.
Literature review
Shah, [8] illustrate vulnerability assessment and penetration testing VAPT for cyber
defense. The author expounds that this approach helps in finding the vulnerabilities in advance
before a cyber-attack take place for preventing an information system from being compromised
by the cyber-criminals. The VAPT consist of a step by step process with nine phases. Shah
proves through her vulnerability assessment results that VAPT is a fundamental technique for the
technology of cyber defense [8]. Plus, VAPT, as proposed by the author, allows a system
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

administrator to keep sensitive information and resources from being compromised by the
attackers; the technique helps in reinforcing the cybersecurity.
Goel and Mehtre [3] presents an overview of penetration testing. The authors discuss the
methodology for carrying out penetration testing. According to the authors, the penetration
testing methodology constitutes three phases which include penetration test penetration, the
actual test, and test analysis. The following are involved in the test phase according to the
authors: a gathering of information, analysis of vulnerabilities and vulnerability exploit [3]. The
authors further illustrate how to apply the methodology with different tools including Nmap and
Metasploit among others in a penetration test using various examples.
[2], on the other hand, investigates different tools for penetration test using Kali Linux.
The authors provide a helpful overview of how to carry out different penetration test in
virtualized tools, private network, and system. Their implementation also utilized Metasploit in
making payloads among other tools that a pen tester may need [2]. The findings show that the
proposed technique for penetration test VAPT could be utilized successfully to overcome the
issues concerning cyber-attack.
Greenwald and Shanle [4], on their side, propose an approach which is consist of an
automatic penetration test plan that can be executed from a remote location without any prior
knowledge regarding the target system [4]. The authors further come up with a technique that
helps in generating and executing the test plans remotely, this technique puts into considers the
ambiguity of utilizing the remote tools both to provide pent testing action and to gain the
necessary knowledge regarding systems [4].
Penetration Test
attackers; the technique helps in reinforcing the cybersecurity.
Goel and Mehtre [3] presents an overview of penetration testing. The authors discuss the
methodology for carrying out penetration testing. According to the authors, the penetration
testing methodology constitutes three phases which include penetration test penetration, the
actual test, and test analysis. The following are involved in the test phase according to the
authors: a gathering of information, analysis of vulnerabilities and vulnerability exploit [3]. The
authors further illustrate how to apply the methodology with different tools including Nmap and
Metasploit among others in a penetration test using various examples.
[2], on the other hand, investigates different tools for penetration test using Kali Linux.
The authors provide a helpful overview of how to carry out different penetration test in
virtualized tools, private network, and system. Their implementation also utilized Metasploit in
making payloads among other tools that a pen tester may need [2]. The findings show that the
proposed technique for penetration test VAPT could be utilized successfully to overcome the
issues concerning cyber-attack.
Greenwald and Shanle [4], on their side, propose an approach which is consist of an
automatic penetration test plan that can be executed from a remote location without any prior
knowledge regarding the target system [4]. The authors further come up with a technique that
helps in generating and executing the test plans remotely, this technique puts into considers the
ambiguity of utilizing the remote tools both to provide pent testing action and to gain the
necessary knowledge regarding systems [4].
Penetration Test
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
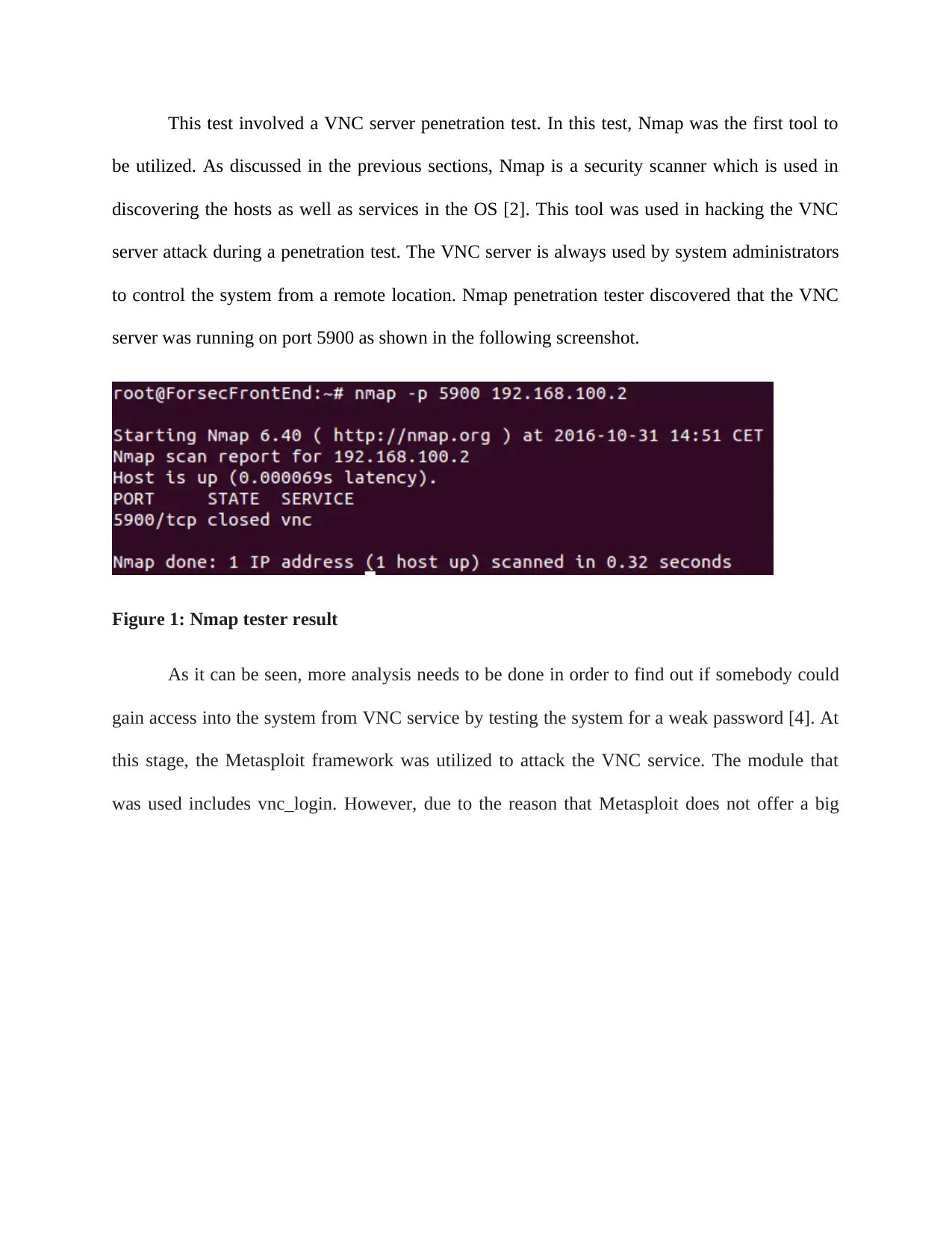
This test involved a VNC server penetration test. In this test, Nmap was the first tool to
be utilized. As discussed in the previous sections, Nmap is a security scanner which is used in
discovering the hosts as well as services in the OS [2]. This tool was used in hacking the VNC
server attack during a penetration test. The VNC server is always used by system administrators
to control the system from a remote location. Nmap penetration tester discovered that the VNC
server was running on port 5900 as shown in the following screenshot.
Figure 1: Nmap tester result
As it can be seen, more analysis needs to be done in order to find out if somebody could
gain access into the system from VNC service by testing the system for a weak password [4]. At
this stage, the Metasploit framework was utilized to attack the VNC service. The module that
was used includes vnc_login. However, due to the reason that Metasploit does not offer a big
be utilized. As discussed in the previous sections, Nmap is a security scanner which is used in
discovering the hosts as well as services in the OS [2]. This tool was used in hacking the VNC
server attack during a penetration test. The VNC server is always used by system administrators
to control the system from a remote location. Nmap penetration tester discovered that the VNC
server was running on port 5900 as shown in the following screenshot.
Figure 1: Nmap tester result
As it can be seen, more analysis needs to be done in order to find out if somebody could
gain access into the system from VNC service by testing the system for a weak password [4]. At
this stage, the Metasploit framework was utilized to attack the VNC service. The module that
was used includes vnc_login. However, due to the reason that Metasploit does not offer a big

word list, a different module list was used to increase the efficiency of the test [1].
Figure 2: VNC scanner
From the diagram above, it can be seen that the password “admin” was retrieved by
Metasploit, the VNC viewer was then used to authenticate the remote host [2].
VNC vulnerability mitigation technique
This threat can get lessened through various ways including the following: first, the
default ports should be changed and use a username and a password containing many special or
weird characters in order to reduce the automated attacks [7]. All VNC listener ports along with
any feature which is not useful should be disabled. It would be safe to block the ports which are
not needed with a firewall to minimize to mitigate the risk. Another important strategy is by
isolating the use of malware detective machine [10]. The VNC server should be run in a virtual
machine where the folders can be limited to the specified users only. Also, when installing
applications it is important that the only ones that would be used remotely are installed to
mitigate the VNC vulnerability. A noteworthy strategy for mitigating VNC vulnerability risk is
to always keep the malware detecting software running [7]. This will limit the attack vectors
Figure 2: VNC scanner
From the diagram above, it can be seen that the password “admin” was retrieved by
Metasploit, the VNC viewer was then used to authenticate the remote host [2].
VNC vulnerability mitigation technique
This threat can get lessened through various ways including the following: first, the
default ports should be changed and use a username and a password containing many special or
weird characters in order to reduce the automated attacks [7]. All VNC listener ports along with
any feature which is not useful should be disabled. It would be safe to block the ports which are
not needed with a firewall to minimize to mitigate the risk. Another important strategy is by
isolating the use of malware detective machine [10]. The VNC server should be run in a virtual
machine where the folders can be limited to the specified users only. Also, when installing
applications it is important that the only ones that would be used remotely are installed to
mitigate the VNC vulnerability. A noteworthy strategy for mitigating VNC vulnerability risk is
to always keep the malware detecting software running [7]. This will limit the attack vectors
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

which might utilize VNC server for escalation; the remote access to a system normally give
cybercriminals more even without breaking into the VNC alone.
Conclusion
At a glance, this report utilized various penetration testing tools including Nmap which
helped in scanning the VNC ports, a Metasploit was also used in finding the vulnerabilities and
weakness in the VNC server system. We also discussed the strategies for mitigating the
vulnerability. The system evaluation demonstrated that Nmap and Metasploit tools are effective
tools and can be used for testing vulnerabilities associated with the VNC server. However, for
one to use this approach, it is important that he or she seek permission from relevant individuals.
cybercriminals more even without breaking into the VNC alone.
Conclusion
At a glance, this report utilized various penetration testing tools including Nmap which
helped in scanning the VNC ports, a Metasploit was also used in finding the vulnerabilities and
weakness in the VNC server system. We also discussed the strategies for mitigating the
vulnerability. The system evaluation demonstrated that Nmap and Metasploit tools are effective
tools and can be used for testing vulnerabilities associated with the VNC server. However, for
one to use this approach, it is important that he or she seek permission from relevant individuals.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
[1] C.M., Leung. “Visual security is feeble for anti-phishing.” In Anti-counterfeiting, Security,
and Identification in Communication, 2009. ASID 2009. 3rd International Conference on
2009 Aug 20 (pp. 118-123). IEEE.
[2] J., Muniz. “Web Penetration Testing with Kali Linux.” Packet Publishing Ltd; 2013 Sep 25.
[3] J.N., Goel, B.M., Mehtre. “Vulnerability assessment & penetration testing as a cyber-defense
technology.” Procedia Computer Science. January 2015.
[4] L., Greenwald, R., Shanley, “Automated planning for remote penetration testing.”
InMILCOM 2009-2009 IEEE Military Communications Conference 2009 Oct 18 (pp. 1-7).
IEEE.
[5] N., Jain, Miao R, “Detecting attacks on data centers.” Microsoft Technology Licensing LLC,
assignee. United States patent application US 14/450,954. 2016 Feb 4.
[6] P., Čisar, S.M., Cisar, I., Fürstner. “Security Assessment with Kali Linux.” Bánki
Közlemények (Bánki Reports). 2018 Jan 28; 1(1):49-52.
[7] S., Mittal, “A survey of soft-error mitigation techniques for non-volatile memories.”
Computers. 2017 Feb 13; 6(1):8.
[8] S., Shah. “Vulnerability assessment and penetration testing (VAPT) techniques for cyber
defense.” IET-NCACNS’SGGS, Nanded. 2013.
[1] C.M., Leung. “Visual security is feeble for anti-phishing.” In Anti-counterfeiting, Security,
and Identification in Communication, 2009. ASID 2009. 3rd International Conference on
2009 Aug 20 (pp. 118-123). IEEE.
[2] J., Muniz. “Web Penetration Testing with Kali Linux.” Packet Publishing Ltd; 2013 Sep 25.
[3] J.N., Goel, B.M., Mehtre. “Vulnerability assessment & penetration testing as a cyber-defense
technology.” Procedia Computer Science. January 2015.
[4] L., Greenwald, R., Shanley, “Automated planning for remote penetration testing.”
InMILCOM 2009-2009 IEEE Military Communications Conference 2009 Oct 18 (pp. 1-7).
IEEE.
[5] N., Jain, Miao R, “Detecting attacks on data centers.” Microsoft Technology Licensing LLC,
assignee. United States patent application US 14/450,954. 2016 Feb 4.
[6] P., Čisar, S.M., Cisar, I., Fürstner. “Security Assessment with Kali Linux.” Bánki
Közlemények (Bánki Reports). 2018 Jan 28; 1(1):49-52.
[7] S., Mittal, “A survey of soft-error mitigation techniques for non-volatile memories.”
Computers. 2017 Feb 13; 6(1):8.
[8] S., Shah. “Vulnerability assessment and penetration testing (VAPT) techniques for cyber
defense.” IET-NCACNS’SGGS, Nanded. 2013.

[9] Y., Malhotra. “Bridging networks, systems and controls frameworks for cyber-security
curriculums and standards development.”
[10] Y., Seralathan, T.T., Oh, S., Jadhav, J., Myers, J.P., Jeong, Y.H., Kim, J.N., Kim. “IoT
security vulnerability: A case study of a Web camera.” In Advanced Communication
Technology (ICACT), 2018 20th International Conference on 2018 Feb 11 (pp. 172-177).
IEEE.
curriculums and standards development.”
[10] Y., Seralathan, T.T., Oh, S., Jadhav, J., Myers, J.P., Jeong, Y.H., Kim, J.N., Kim. “IoT
security vulnerability: A case study of a Web camera.” In Advanced Communication
Technology (ICACT), 2018 20th International Conference on 2018 Feb 11 (pp. 172-177).
IEEE.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





