Network Threats Presentation: Cyber Security and Mitigation Strategies
VerifiedAdded on 2022/10/10
|4
|577
|75
Presentation
AI Summary
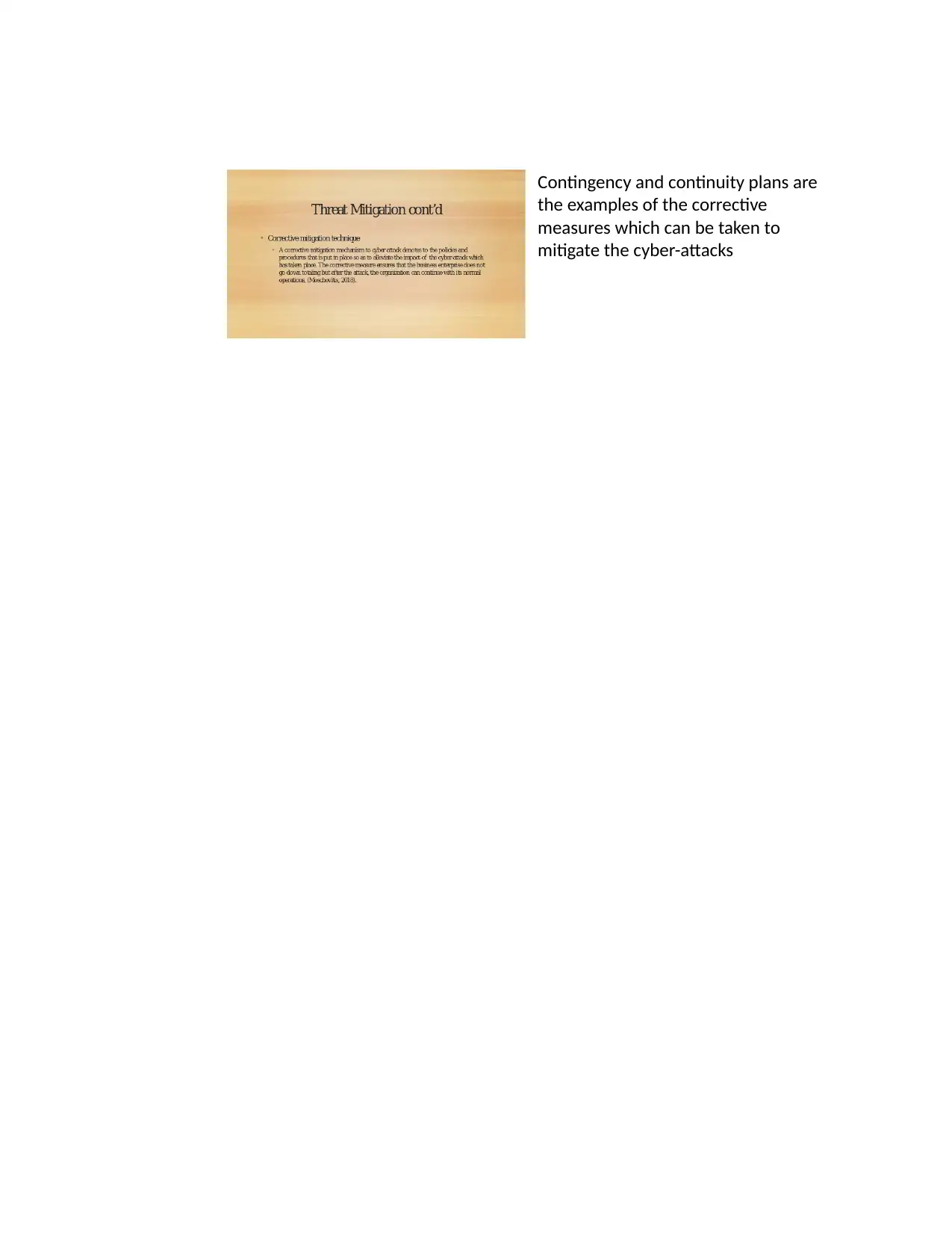
This presentation provides an overview of network threats, categorizing them as internal and external. It identifies various threats, including rogue security software, phishing attacks, and Denial of Service (DoS) and Distributed Denial of Service (DDoS) attacks. The presentation explains how these threats work and their potential impact. It also covers mitigation strategies, including preventive controls like firewalls, encryption, and antivirus software; detective measures such as security log monitoring; and corrective measures like contingency and continuity plans. The presentation aims to inform the audience about the nature of network threats and the various methods used to defend against them.
1 out of 4









![[object Object]](/_next/static/media/star-bottom.7253800d.svg)