BN203 Network Security Report: Identifying Network Threats T1 2018
VerifiedAdded on 2023/06/11
|8
|1360
|87
Report
AI Summary
This report focuses on identifying network threats using security tools, specifically Nmap and Metasploit. It begins with an introduction to the topic and a literature review discussing various network attacks such as Denial of Service (DoS), social engineering, and malware. The report then details the functionalities and benefits of Nmap and Metasploit as open-source networking tools for vulnerability analysis and security testing. Techniques for threat mitigation, including firewall configuration, network segregation, web application security, patch management, and privilege control, are also discussed. The report concludes by summarizing the use of these tools in identifying and addressing network threats, emphasizing their availability in Kali Linux and the importance of implementing mitigation strategies. Desklib provides a platform for students to access similar solved assignments and past papers for their studies.

Running head: NETWORK SECURITY
NETWORK SECURITY
Name of the Student
Name of the University
Author Note
NETWORK SECURITY
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORK SECURITY
Introduction
The following report reflects on two security tools for checking or analysing various
kinds of threats and providing a list of solution to overcome or mitigate them. Nmap and
Metasploit are considered to be two kind of open source networking tool which is mainly used
for checking various kinds of vulnerabilities which are present in the given network. These tools
are easily available in kali Linux. It is mainly installed in the virtual machine for exploitation of
given or provided network. Various kinds of threats have been easily identified and have been
discussed in brief in the coming pages. These threats have been identified by the help of two
tools that is Nmap and Metasploit.
Literature Review
Introduction
The following report reflects on two security tools for checking or analysing various
kinds of threats and providing a list of solution to overcome or mitigate them. Nmap and
Metasploit are considered to be two kind of open source networking tool which is mainly used
for checking various kinds of vulnerabilities which are present in the given network. These tools
are easily available in kali Linux. It is mainly installed in the virtual machine for exploitation of
given or provided network. Various kinds of threats have been easily identified and have been
discussed in brief in the coming pages. These threats have been identified by the help of two
tools that is Nmap and Metasploit.
Literature Review
2NETWORK SECURITY
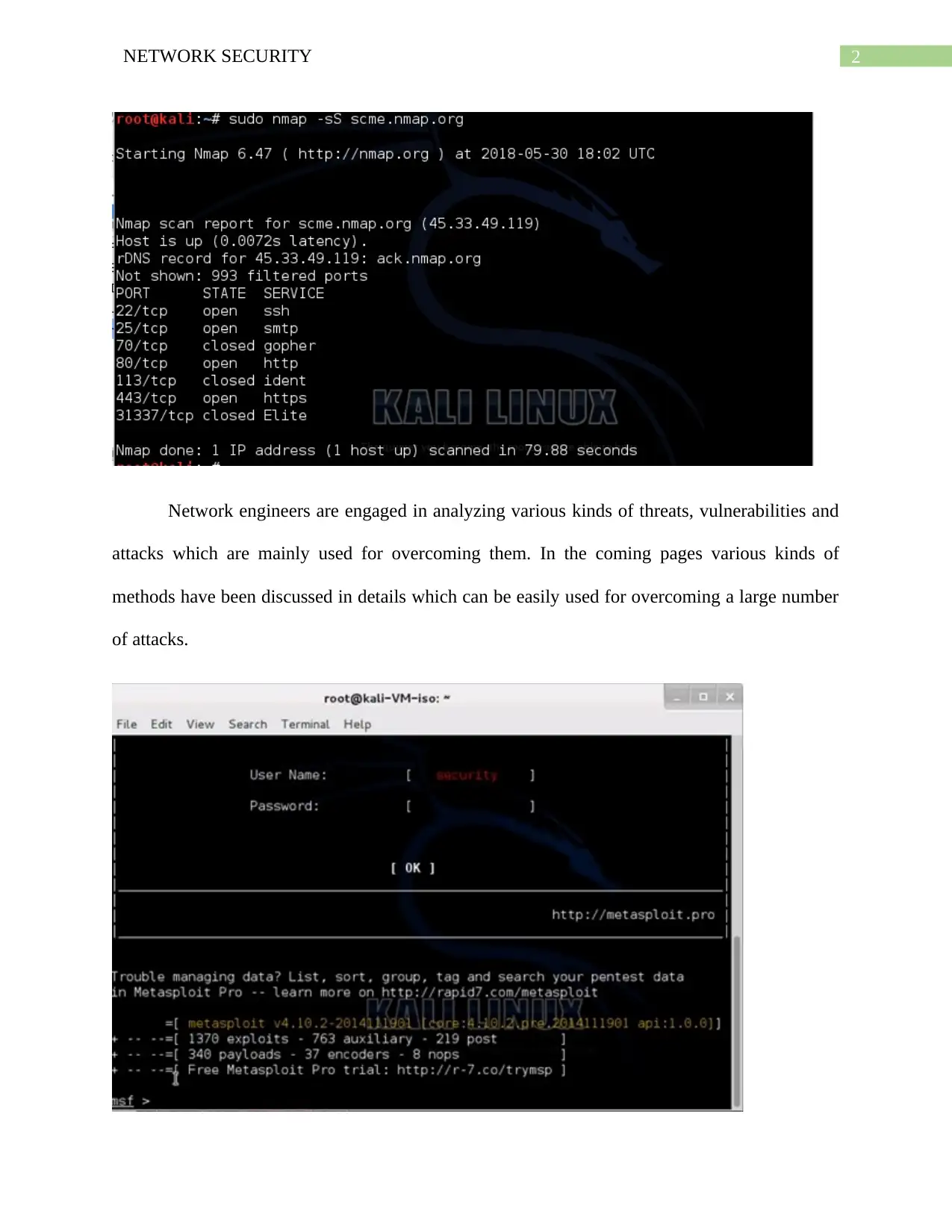
Network engineers are engaged in analyzing various kinds of threats, vulnerabilities and
attacks which are mainly used for overcoming them. In the coming pages various kinds of
methods have been discussed in details which can be easily used for overcoming a large number
of attacks.
Network engineers are engaged in analyzing various kinds of threats, vulnerabilities and
attacks which are mainly used for overcoming them. In the coming pages various kinds of
methods have been discussed in details which can be easily used for overcoming a large number
of attacks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3NETWORK SECURITY
Various kinds of attacks like Denial of service attacks, social engineering and malware has been
discussed in details. A proper kind of DDoS attack occurs when the working ability of the
various kinds of device has been prevented. Any kind of triggering which is done on the given
device can be easily used for overcoming large number of problem and issues. A proper kind of
DoS attack can be easily done by any kind of help from detection of error. A much simple
kind of DoS attack can be easily done with the help of any kind of third party network. It
ultimately focuses various kinds of availability of given network into another kind of given
network capacity. Another common type of attack in a network is all about social engineering.
This kind of attack generally requires a much certain value or level of skills. Social engineering
does not come up with any kind of advantage like social methods that is mainly used for
gathering some kind of important information. Malware is generally termed as malware software
which is considered to be attacks. Malware is mainly inclusive of certain number of things like
adware, Trojan, worm and virus.
Various kinds of attacks like Denial of service attacks, social engineering and malware has been
discussed in details. A proper kind of DDoS attack occurs when the working ability of the
various kinds of device has been prevented. Any kind of triggering which is done on the given
device can be easily used for overcoming large number of problem and issues. A proper kind of
DoS attack can be easily done by any kind of help from detection of error. A much simple
kind of DoS attack can be easily done with the help of any kind of third party network. It
ultimately focuses various kinds of availability of given network into another kind of given
network capacity. Another common type of attack in a network is all about social engineering.
This kind of attack generally requires a much certain value or level of skills. Social engineering
does not come up with any kind of advantage like social methods that is mainly used for
gathering some kind of important information. Malware is generally termed as malware software
which is considered to be attacks. Malware is mainly inclusive of certain number of things like
adware, Trojan, worm and virus.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORK SECURITY
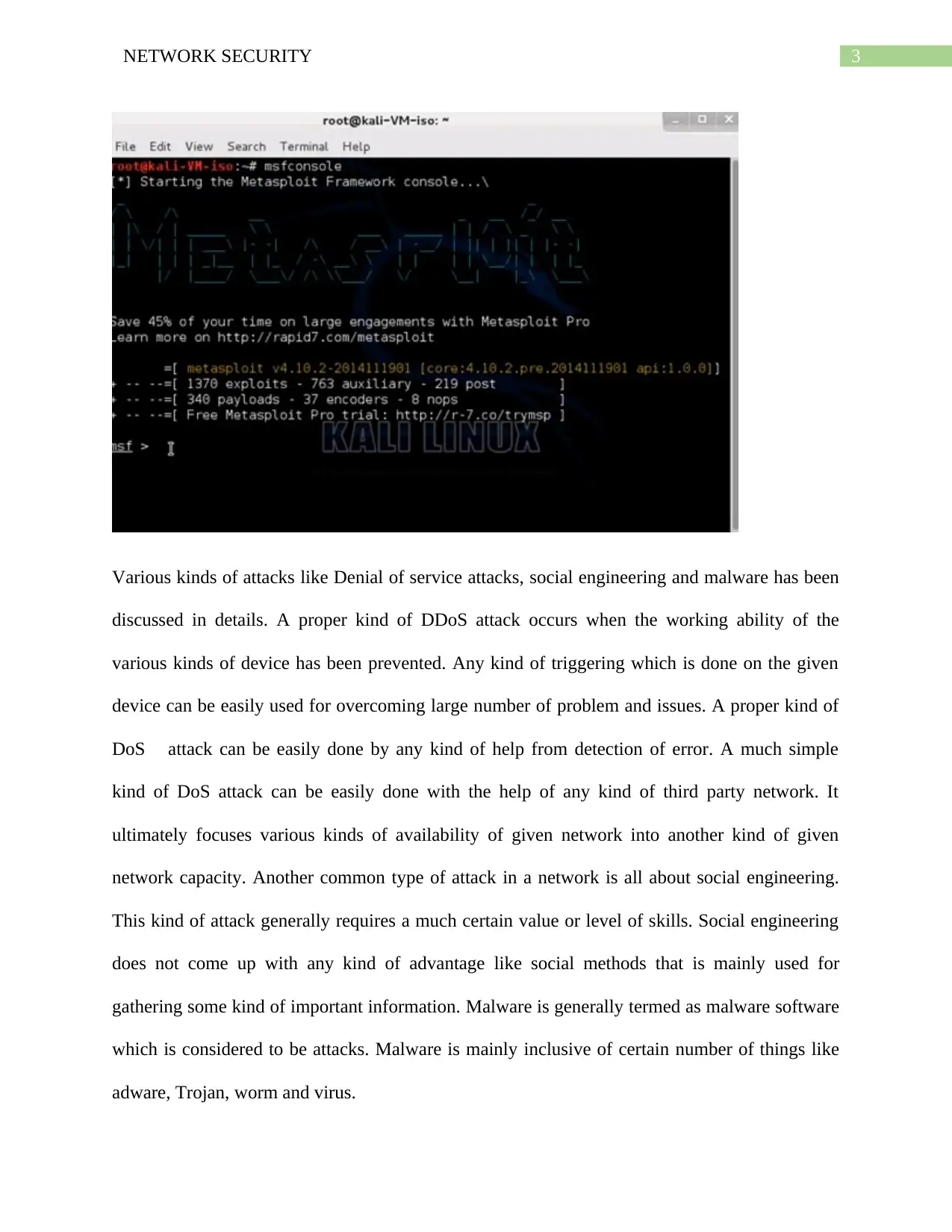
Network security Tools
Nmap is defined as a free and open tool which is used for analyzing different kinds of
threat related to security. Various security administrator round the globe can easily considered to
be helpful in dealing with large number of issues like proper management of services,
management of inventory, proper monitoring of service upgrades. This tool is considered to be
very helpful for IP packets in given novel that is mainly used for analyzing different host
available on the network. This tool is also helpful in checking various kinds of services of
operation for its proper running. Nmap has been designed in such a way that it is very helpful in
analyzing network and other different kinds of tools which are available for any kind of testing.
Nmap networking tool is used in large number of platform of operating system like linux,
windows and lastly Mac OS.
Nmap comes up with large number of benefits like:
Flexible: It supports a large number of advance techniques which is generally used for
mapping out network which is filled with various kinds of things like firewalls, routers and other
kinds of obstacles. This is mainly inclusive of port scanning mechanism that is TCP and UDP,
detection of OS.
Powerful: Nmap is generally prepared by the help of scanning of huge number of
networks which mainly comes up with thousands of machines.
Metasploit is considered to be one of widely used tool which is used in hacking in the
domain of security. It mainly provides a large number of content and infrastructure which is
mainly used for performing a large number of security test. It is considered to be much famous
kind of tool in the domain of security. It can be also stated like a proper kind of tool which is
Network security Tools
Nmap is defined as a free and open tool which is used for analyzing different kinds of
threat related to security. Various security administrator round the globe can easily considered to
be helpful in dealing with large number of issues like proper management of services,
management of inventory, proper monitoring of service upgrades. This tool is considered to be
very helpful for IP packets in given novel that is mainly used for analyzing different host
available on the network. This tool is also helpful in checking various kinds of services of
operation for its proper running. Nmap has been designed in such a way that it is very helpful in
analyzing network and other different kinds of tools which are available for any kind of testing.
Nmap networking tool is used in large number of platform of operating system like linux,
windows and lastly Mac OS.
Nmap comes up with large number of benefits like:
Flexible: It supports a large number of advance techniques which is generally used for
mapping out network which is filled with various kinds of things like firewalls, routers and other
kinds of obstacles. This is mainly inclusive of port scanning mechanism that is TCP and UDP,
detection of OS.
Powerful: Nmap is generally prepared by the help of scanning of huge number of
networks which mainly comes up with thousands of machines.
Metasploit is considered to be one of widely used tool which is used in hacking in the
domain of security. It mainly provides a large number of content and infrastructure which is
mainly used for performing a large number of security test. It is considered to be much famous
kind of tool in the domain of security. It can be also stated like a proper kind of tool which is

5NETWORK SECURITY
used for performing a large number of tests. It can be easily stated to be famous model that is
generally used for various kinds of stages like deployment, exploitation and testing of various
kinds of codes.
Techniques for threat Mitigation
A large number of stages can be easily used for overcoming different problems in a
network like:
Proper configuration of firewall
Segregating network into constituent’s parts
Different web application
Proper management of patch.
Privilege of given network.
Configuration of firewall: Configuration of firewall is all about its proper management.
It generally analyzes different kinds of configuration which is generally considered to be
active in nature.
Web vulnerabilities: Problems and weakness in a given network or web application is
taken to main vendors by which various attacks takes place in an organization.
Management of patch: It is taken to be one of the ways in different kind of method by
which different kind of system and services are mainly patched as per the given
requirement.
used for performing a large number of tests. It can be easily stated to be famous model that is
generally used for various kinds of stages like deployment, exploitation and testing of various
kinds of codes.
Techniques for threat Mitigation
A large number of stages can be easily used for overcoming different problems in a
network like:
Proper configuration of firewall
Segregating network into constituent’s parts
Different web application
Proper management of patch.
Privilege of given network.
Configuration of firewall: Configuration of firewall is all about its proper management.
It generally analyzes different kinds of configuration which is generally considered to be
active in nature.
Web vulnerabilities: Problems and weakness in a given network or web application is
taken to main vendors by which various attacks takes place in an organization.
Management of patch: It is taken to be one of the ways in different kind of method by
which different kind of system and services are mainly patched as per the given
requirement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORK SECURITY
Conclusion
From the above discussion it can be easily stated that report is all about kinds of network
tools which is mainly used for checking various kinds of threats in a network. Various kinds of
identification have been done regarding addressing of various threats. Two type of network tools
that is Nmap and metaspliot has been discussed in brief in the above pages of the report. After
that a list of threat mitigation tools in network has been discussed in details. The tool networking
tools that is Nmap and Metasploit are available in Linux kali. It is installed in any kind of virtual
machine for exploitation of current network. A large number of steps like proper configuration of
firewall, web application has been discussed in details in the above pages of the report.
Conclusion
From the above discussion it can be easily stated that report is all about kinds of network
tools which is mainly used for checking various kinds of threats in a network. Various kinds of
identification have been done regarding addressing of various threats. Two type of network tools
that is Nmap and metaspliot has been discussed in brief in the above pages of the report. After
that a list of threat mitigation tools in network has been discussed in details. The tool networking
tools that is Nmap and Metasploit are available in Linux kali. It is installed in any kind of virtual
machine for exploitation of current network. A large number of steps like proper configuration of
firewall, web application has been discussed in details in the above pages of the report.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORK SECURITY
References
[1] Akhyari, N. and Fahmy, S., 2014. Design of a Network Security Tool Using Open-Source
Applications. Australian Journal of Basic and Applied Sciences, pp.04-06.
[2] Aslan, O. and Samet, R., 2017, September. Mitigating Cyber Security Attacks by being
Aware of Vulnerabilities and Bugs. In 2017 International Conference on Cyberworlds (CW) (pp.
222-225). IEEE.
[3] Patel, S.K. and Sonker, A., 2016. Rule-based network intrusion detection system for port
scanning with efficient port scan detection rules using snort. International Journal of Future
Generation Communication and Networking, 9(6), pp.339-350.
[4] Corbett, C., Basic, T., Lukaseder, T. and Kargl, F., 2017. A Testing Framework Architecture
for Automotive Intrusion Detection Systems. Automotive-Safety & Security 2017-Sicherheit und
Zuverlässigkeit für automobile Informationstechnik.
[5] Patel, K.C. and Sharma, D.P., 2017. A Review paper on pfsense–an Open source firewall
introducing with different capabilities & customization. Vol-3 Issue-2.
[6] Shaw, D., 2015. Nmap Essentials. Packt Publishing Ltd.
[7] Rao, T.D. and Ram, V.S.M.K.S., 2015. Deciphering The Prominent Security Tools Ofkali
Linux. International Journal Of Engineering And Computer Science, 4(01).
[8] Morris, T. and Gao, W., 2014, March. Industrial control system traffic data sets for intrusion
detection research. In International Conference on Critical Infrastructure Protection(pp. 65-78).
Springer, Berlin, Heidelberg.
References
[1] Akhyari, N. and Fahmy, S., 2014. Design of a Network Security Tool Using Open-Source
Applications. Australian Journal of Basic and Applied Sciences, pp.04-06.
[2] Aslan, O. and Samet, R., 2017, September. Mitigating Cyber Security Attacks by being
Aware of Vulnerabilities and Bugs. In 2017 International Conference on Cyberworlds (CW) (pp.
222-225). IEEE.
[3] Patel, S.K. and Sonker, A., 2016. Rule-based network intrusion detection system for port
scanning with efficient port scan detection rules using snort. International Journal of Future
Generation Communication and Networking, 9(6), pp.339-350.
[4] Corbett, C., Basic, T., Lukaseder, T. and Kargl, F., 2017. A Testing Framework Architecture
for Automotive Intrusion Detection Systems. Automotive-Safety & Security 2017-Sicherheit und
Zuverlässigkeit für automobile Informationstechnik.
[5] Patel, K.C. and Sharma, D.P., 2017. A Review paper on pfsense–an Open source firewall
introducing with different capabilities & customization. Vol-3 Issue-2.
[6] Shaw, D., 2015. Nmap Essentials. Packt Publishing Ltd.
[7] Rao, T.D. and Ram, V.S.M.K.S., 2015. Deciphering The Prominent Security Tools Ofkali
Linux. International Journal Of Engineering And Computer Science, 4(01).
[8] Morris, T. and Gao, W., 2014, March. Industrial control system traffic data sets for intrusion
detection research. In International Conference on Critical Infrastructure Protection(pp. 65-78).
Springer, Berlin, Heidelberg.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




