Network Design and Troubleshooting Assignment for Ntek.co.uk
VerifiedAdded on 2023/04/21
|13
|2365
|335
Project
AI Summary
This project presents a network design for ntek.co.uk, a company with four departments, each with specific device and access requirements. The design emphasizes availability, scalability, and security. It includes a network diagram using GPON technology, VLAN implementation for department isolation, and subnetting for IP address allocation. The solution justifies the design choices, detailing the use of GPON technology, devices like Optical Line Terminals (OLTs), and Optical Network Terminals (ONTs). The report also covers network security, detailing security precautions, access control lists (ACLs) to isolate departments, and ACLs for a DMZ. A weekly maintenance schedule based on FCAPS methodology is also included. The project aims to provide a robust and secure network infrastructure for the client.

NETWORK DESIGN AND TROUBLESHOOTING
by (Name)
(Course)
(Tutor)
(University)
(University Location)
(Date)
by (Name)
(Course)
(Tutor)
(University)
(University Location)
(Date)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Abstract
This paper presents principles of network design for a small network. The network
consists of four departments where the first department consisting of forty computers with one
printer. The second department has 21 computers and one dedicated server. The third
department contains eight computers with one printer and one dedicated server and the last
department with eighty one computers, one printer and one dedicated server. In addition, each
department is not supposed to access servers of other departments theirs and the main servers. As
a network engineer, this paper will present a network design for this scenario emphasizing on
availability and scalability. The company is using public IP address 30.40.50.64/28 and a private
IP address 192.168.0.0/24
This paper presents principles of network design for a small network. The network
consists of four departments where the first department consisting of forty computers with one
printer. The second department has 21 computers and one dedicated server. The third
department contains eight computers with one printer and one dedicated server and the last
department with eighty one computers, one printer and one dedicated server. In addition, each
department is not supposed to access servers of other departments theirs and the main servers. As
a network engineer, this paper will present a network design for this scenario emphasizing on
availability and scalability. The company is using public IP address 30.40.50.64/28 and a private
IP address 192.168.0.0/24

Table of Contents
Abstract............................................................................................................................................2
Introduction......................................................................................................................................3
Task one: Network Design..............................................................................................................4
Network diagram and VLAN design...........................................................................................4
Sub-netting...................................................................................................................................4
VLan for each department............................................................................................................5
Task two: Network Design Justification..........................................................................................6
Justification of the use of the network diagram...........................................................................6
Justification of the devices used in the solution...........................................................................7
Justification of the use of GPON technology...............................................................................7
Justification of the maintenance schedule....................................................................................8
Task three: Network security...........................................................................................................9
Security precautions.....................................................................................................................9
Access control list to isolate each department internally...........................................................10
Access control list for DMZ.......................................................................................................11
Conclusion.....................................................................................................................................11
References......................................................................................................................................11
Abstract............................................................................................................................................2
Introduction......................................................................................................................................3
Task one: Network Design..............................................................................................................4
Network diagram and VLAN design...........................................................................................4
Sub-netting...................................................................................................................................4
VLan for each department............................................................................................................5
Task two: Network Design Justification..........................................................................................6
Justification of the use of the network diagram...........................................................................6
Justification of the devices used in the solution...........................................................................7
Justification of the use of GPON technology...............................................................................7
Justification of the maintenance schedule....................................................................................8
Task three: Network security...........................................................................................................9
Security precautions.....................................................................................................................9
Access control list to isolate each department internally...........................................................10
Access control list for DMZ.......................................................................................................11
Conclusion.....................................................................................................................................11
References......................................................................................................................................11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
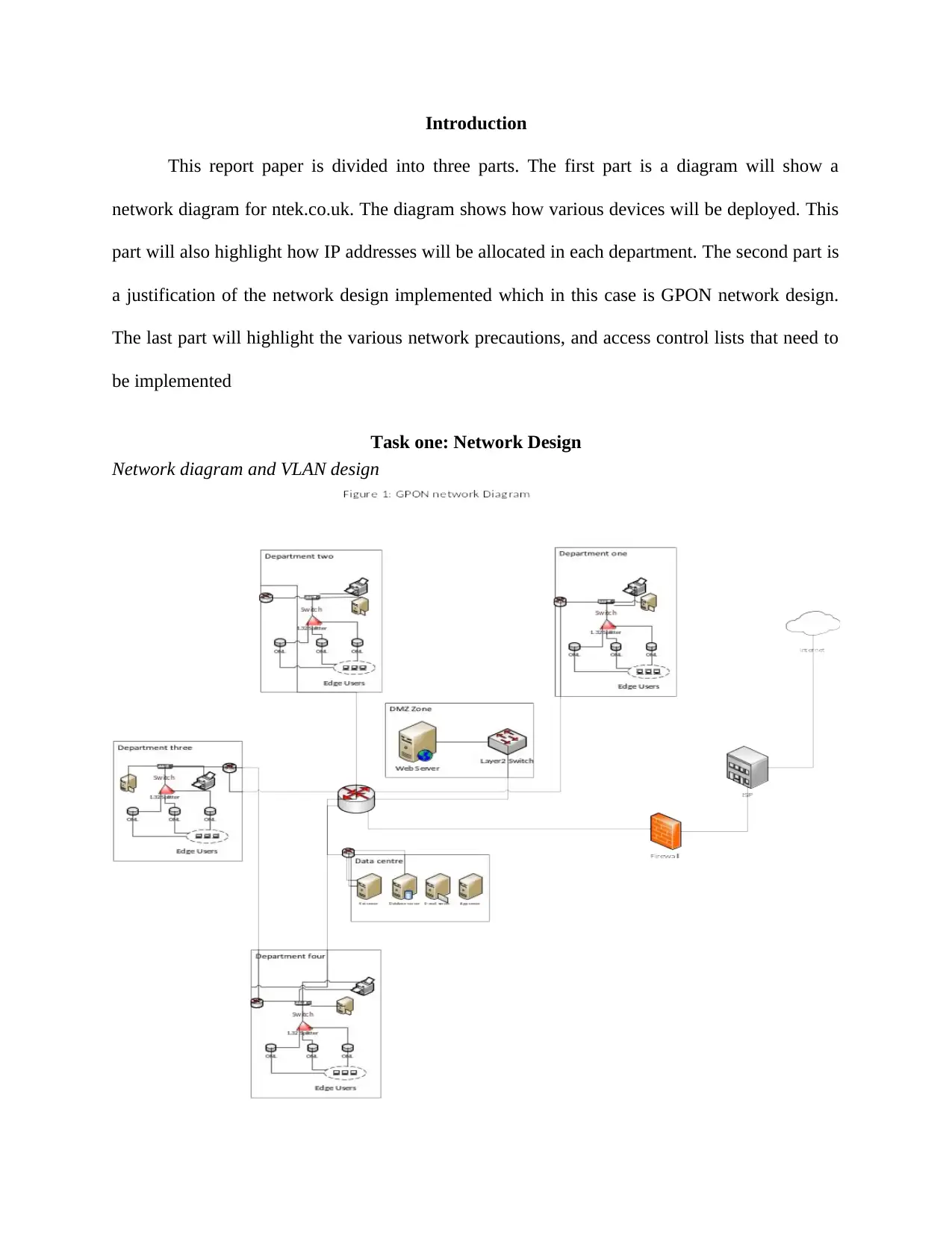
Introduction
This report paper is divided into three parts. The first part is a diagram will show a
network diagram for ntek.co.uk. The diagram shows how various devices will be deployed. This
part will also highlight how IP addresses will be allocated in each department. The second part is
a justification of the network design implemented which in this case is GPON network design.
The last part will highlight the various network precautions, and access control lists that need to
be implemented
Task one: Network Design
Network diagram and VLAN design
This report paper is divided into three parts. The first part is a diagram will show a
network diagram for ntek.co.uk. The diagram shows how various devices will be deployed. This
part will also highlight how IP addresses will be allocated in each department. The second part is
a justification of the network design implemented which in this case is GPON network design.
The last part will highlight the various network precautions, and access control lists that need to
be implemented
Task one: Network Design
Network diagram and VLAN design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
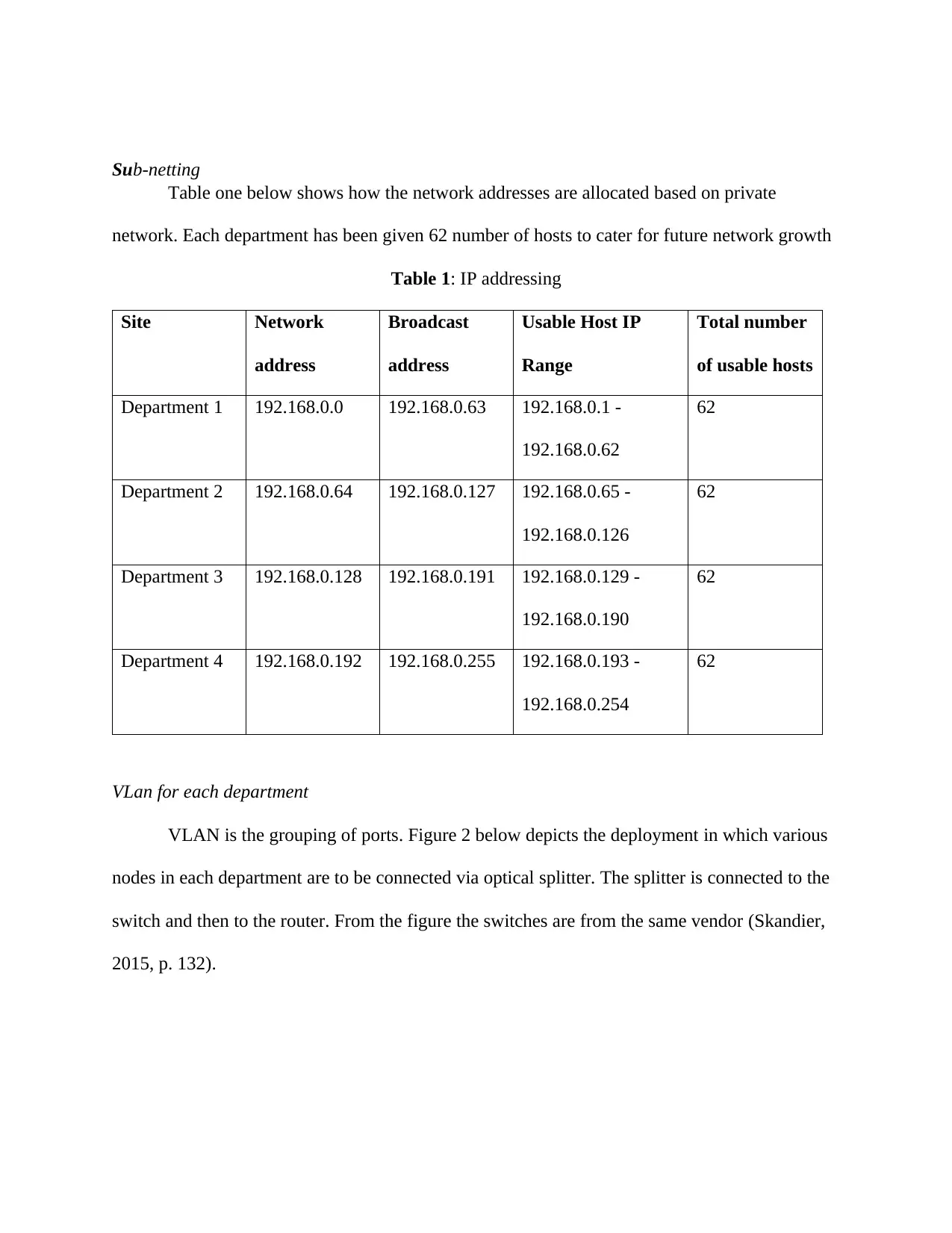
Sub-netting
Table one below shows how the network addresses are allocated based on private
network. Each department has been given 62 number of hosts to cater for future network growth
Table 1: IP addressing
Site Network
address
Broadcast
address
Usable Host IP
Range
Total number
of usable hosts
Department 1 192.168.0.0 192.168.0.63 192.168.0.1 -
192.168.0.62
62
Department 2 192.168.0.64 192.168.0.127 192.168.0.65 -
192.168.0.126
62
Department 3 192.168.0.128 192.168.0.191 192.168.0.129 -
192.168.0.190
62
Department 4 192.168.0.192 192.168.0.255 192.168.0.193 -
192.168.0.254
62
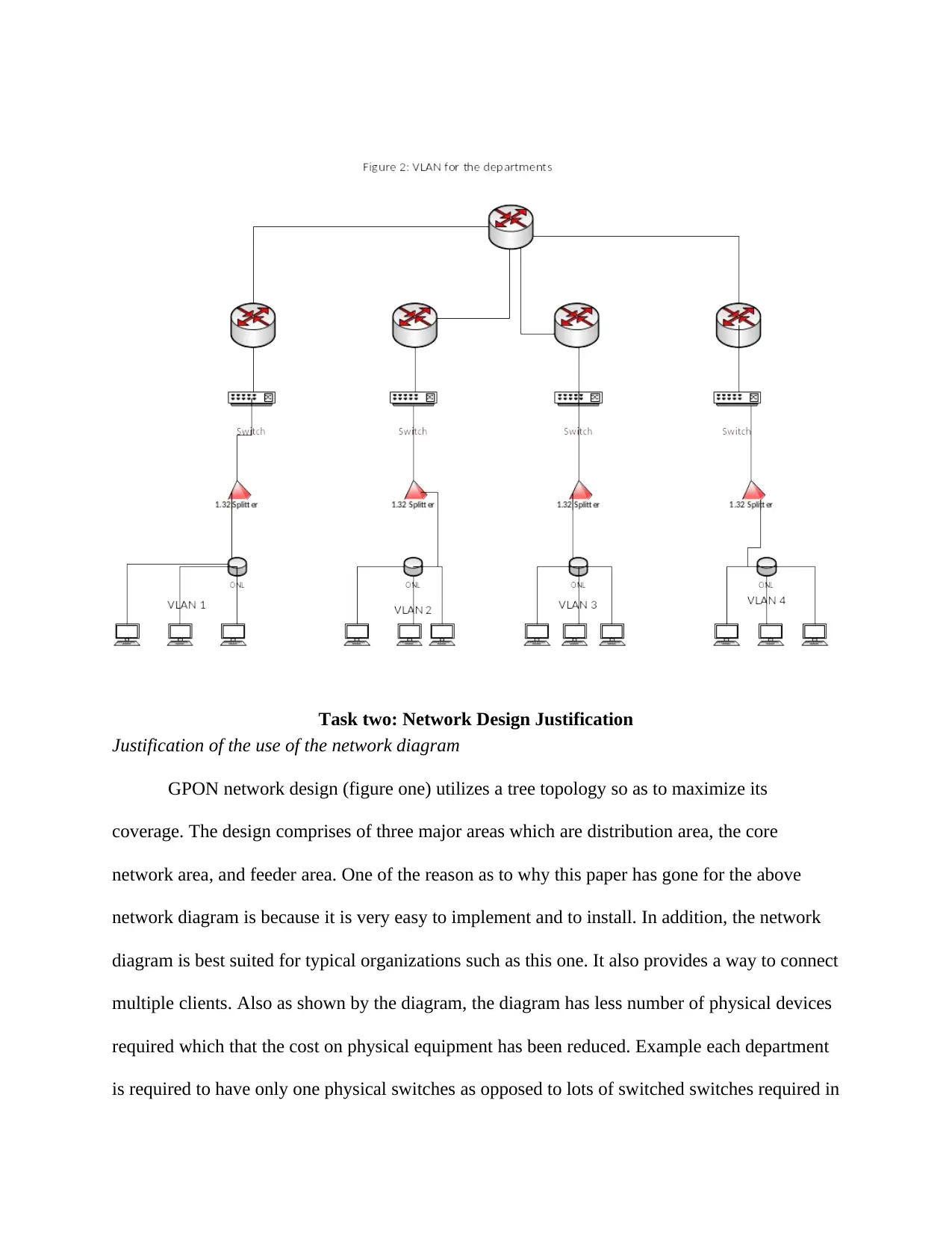
VLan for each department
VLAN is the grouping of ports. Figure 2 below depicts the deployment in which various
nodes in each department are to be connected via optical splitter. The splitter is connected to the
switch and then to the router. From the figure the switches are from the same vendor (Skandier,
2015, p. 132).
Table one below shows how the network addresses are allocated based on private
network. Each department has been given 62 number of hosts to cater for future network growth
Table 1: IP addressing
Site Network
address
Broadcast
address
Usable Host IP
Range
Total number
of usable hosts
Department 1 192.168.0.0 192.168.0.63 192.168.0.1 -
192.168.0.62
62
Department 2 192.168.0.64 192.168.0.127 192.168.0.65 -
192.168.0.126
62
Department 3 192.168.0.128 192.168.0.191 192.168.0.129 -
192.168.0.190
62
Department 4 192.168.0.192 192.168.0.255 192.168.0.193 -
192.168.0.254
62
VLan for each department
VLAN is the grouping of ports. Figure 2 below depicts the deployment in which various
nodes in each department are to be connected via optical splitter. The splitter is connected to the
switch and then to the router. From the figure the switches are from the same vendor (Skandier,
2015, p. 132).
Task two: Network Design Justification
Justification of the use of the network diagram
GPON network design (figure one) utilizes a tree topology so as to maximize its
coverage. The design comprises of three major areas which are distribution area, the core
network area, and feeder area. One of the reason as to why this paper has gone for the above
network diagram is because it is very easy to implement and to install. In addition, the network
diagram is best suited for typical organizations such as this one. It also provides a way to connect
multiple clients. Also as shown by the diagram, the diagram has less number of physical devices
required which that the cost on physical equipment has been reduced. Example each department
is required to have only one physical switches as opposed to lots of switched switches required in
Justification of the use of the network diagram
GPON network design (figure one) utilizes a tree topology so as to maximize its
coverage. The design comprises of three major areas which are distribution area, the core
network area, and feeder area. One of the reason as to why this paper has gone for the above
network diagram is because it is very easy to implement and to install. In addition, the network
diagram is best suited for typical organizations such as this one. It also provides a way to connect
multiple clients. Also as shown by the diagram, the diagram has less number of physical devices
required which that the cost on physical equipment has been reduced. Example each department
is required to have only one physical switches as opposed to lots of switched switches required in
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

other designs this is because an optical splitter has been utilized to split the signal into a number
of different signals. In addition, the network diagram offers a high Bandwidth as compared to
other network diagrams. In addition the network design will offer up-to 2.4 Gps. In addition,
ease of troubleshooting has been considered when designing the network diagram. This has been
captured by using passive components which offers centralized type of management (Mishra,
2018, p. 47)
Justification of the devices used in the solution
GPON technology utilizes devices recommended by ITU-T. These devices represents an
increase in bandwidth as compared to BPON and APON devices. The four main devices utilized
here are optical network terminal, optical line terminal, fiber optical splitters, and the
transmitting media (Donoso, 2016, p. 97).
Optical network terminal is also referred to as the modem and it is used to connect to the
termination point with optical fiber cable. The device connects via a router. The device is used to
convert optical signals so as to deliver to the end devices. Another device utilized here is the
OLT (Optical Line Transmitter); the device serves as a service provider endpoint to the passive
optical network. The device is used to convert the optical signals which are being transmitted
over fiber. The third device utilized here is the fiber cabling. This device is used as transmitting
media. The third device utilized here is the fiber optic splitter which is also known as beam
splitter. With this device, lots of devices can server from a single fiber. Router is another device
utilized here which is used to limit access of services offered in each department (Owusu, et al.,
2017, p. 89).
of different signals. In addition, the network diagram offers a high Bandwidth as compared to
other network diagrams. In addition the network design will offer up-to 2.4 Gps. In addition,
ease of troubleshooting has been considered when designing the network diagram. This has been
captured by using passive components which offers centralized type of management (Mishra,
2018, p. 47)
Justification of the devices used in the solution
GPON technology utilizes devices recommended by ITU-T. These devices represents an
increase in bandwidth as compared to BPON and APON devices. The four main devices utilized
here are optical network terminal, optical line terminal, fiber optical splitters, and the
transmitting media (Donoso, 2016, p. 97).
Optical network terminal is also referred to as the modem and it is used to connect to the
termination point with optical fiber cable. The device connects via a router. The device is used to
convert optical signals so as to deliver to the end devices. Another device utilized here is the
OLT (Optical Line Transmitter); the device serves as a service provider endpoint to the passive
optical network. The device is used to convert the optical signals which are being transmitted
over fiber. The third device utilized here is the fiber cabling. This device is used as transmitting
media. The third device utilized here is the fiber optic splitter which is also known as beam
splitter. With this device, lots of devices can server from a single fiber. Router is another device
utilized here which is used to limit access of services offered in each department (Owusu, et al.,
2017, p. 89).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Justification of the use of GPON technology
As suggested in the earlier in this paper (figure 1), GPON design is the best design for
this case. The technology as highlighted in figure one utilizes Optical Line terminals so as to
convert signals into light. Optical Network terminal is also used to convert light back to standard
Ethernet connection so as to deliver data to end users.
The reason as to why this design utilizes switching from outdated copper infrastructure
meaning that this organization will benefit from greater range. One can transmit data over 10 to
20 kilometers. Second, the design offers a faster speed. It provides high performance bandwidth
of five gigabits per second. In addition, the design offers scalability thus enabling one to provide
seamless path of up to 40 Gbps without upgrading the cabling done. Forth, this type of design
provides stability; the design is very stable and requires very little time when it comes to
maintenance. In addition, the design offers lesspoints of failure which results in higher MTbF
parameters. Fifth, beside this technology being the next generation technologies, it allows an
organization to increase access to network bandwidth at the moment. In addition, the technology
has a longer life span as compared to other technologies (Lacoste, 2014, p. 148).
Justification of the maintenance schedule
Maintenance tasks for this network follows guidelines laid out by IEEE. The first task to
be carried out is failure response; this include tasks such as supporting uses who experience
network problems, troubleshooting link failures . Another task to always be carried out during
network maintenance is testing performance of the network some of these tasks include
performance tuning, resource usage monitoring. Another task to be performed include carrying
out security procedures; this task include carrying out all the security procedures such as
As suggested in the earlier in this paper (figure 1), GPON design is the best design for
this case. The technology as highlighted in figure one utilizes Optical Line terminals so as to
convert signals into light. Optical Network terminal is also used to convert light back to standard
Ethernet connection so as to deliver data to end users.
The reason as to why this design utilizes switching from outdated copper infrastructure
meaning that this organization will benefit from greater range. One can transmit data over 10 to
20 kilometers. Second, the design offers a faster speed. It provides high performance bandwidth
of five gigabits per second. In addition, the design offers scalability thus enabling one to provide
seamless path of up to 40 Gbps without upgrading the cabling done. Forth, this type of design
provides stability; the design is very stable and requires very little time when it comes to
maintenance. In addition, the design offers lesspoints of failure which results in higher MTbF
parameters. Fifth, beside this technology being the next generation technologies, it allows an
organization to increase access to network bandwidth at the moment. In addition, the technology
has a longer life span as compared to other technologies (Lacoste, 2014, p. 148).
Justification of the maintenance schedule
Maintenance tasks for this network follows guidelines laid out by IEEE. The first task to
be carried out is failure response; this include tasks such as supporting uses who experience
network problems, troubleshooting link failures . Another task to always be carried out during
network maintenance is testing performance of the network some of these tasks include
performance tuning, resource usage monitoring. Another task to be performed include carrying
out security procedures; this task include carrying out all the security procedures such as

ensuring that the IPS software is up to date. Server software are up dated regularly. It is
including updating internet anti-virus.
Since the maintenance is to be carried once in a week, it is a structured type of
maintenance. One of the reasons as to why this type of maintenance adopts this type of
maintenance it reduces network downtime, it is cost effective, it offers a higher network security,
and it is aligned with the organization’s objectives. In addition, this type of maintenance is a
proactive one this it reduces the frequency and quantity of problems. Also, long time
maintenance tasks will not be forgotten or neglected.
Network maintenance procedures and tools FCAPs methodology. With fault management
it helps in the discovering some network related issues. Security management ensures
availability, integrity, and confidentiality. It also ensures managing of the overall network
performance. The maintenance model for GPON technology is the FCAPS (Fault, Configuration,
Accounting, Performance, and Security) model (Hutton, 2018, p. 54). Fault is used to detect any
form of problem. One major feature with fault is alarm notification through SMS and email.
Configuration component of FCAPS helps in preparing a set of network devices for operation.
This component provides configuration restore and back-up. Performance component ensures
that the GPON network performs are required or expected. The parameters monitored here
include speed fluctuation and fiber cabling parameters (Blanc & Cotton, 2014, p. 67).
Task three: Network security
Security precautions
After designing any network, an organization should carry out certain precautions to
ensure that the organization network is always protected. First an organization should take
physical precautions i.e. the organization server should be kept in a secure place to avoid any
including updating internet anti-virus.
Since the maintenance is to be carried once in a week, it is a structured type of
maintenance. One of the reasons as to why this type of maintenance adopts this type of
maintenance it reduces network downtime, it is cost effective, it offers a higher network security,
and it is aligned with the organization’s objectives. In addition, this type of maintenance is a
proactive one this it reduces the frequency and quantity of problems. Also, long time
maintenance tasks will not be forgotten or neglected.
Network maintenance procedures and tools FCAPs methodology. With fault management
it helps in the discovering some network related issues. Security management ensures
availability, integrity, and confidentiality. It also ensures managing of the overall network
performance. The maintenance model for GPON technology is the FCAPS (Fault, Configuration,
Accounting, Performance, and Security) model (Hutton, 2018, p. 54). Fault is used to detect any
form of problem. One major feature with fault is alarm notification through SMS and email.
Configuration component of FCAPS helps in preparing a set of network devices for operation.
This component provides configuration restore and back-up. Performance component ensures
that the GPON network performs are required or expected. The parameters monitored here
include speed fluctuation and fiber cabling parameters (Blanc & Cotton, 2014, p. 67).
Task three: Network security
Security precautions
After designing any network, an organization should carry out certain precautions to
ensure that the organization network is always protected. First an organization should take
physical precautions i.e. the organization server should be kept in a secure place to avoid any
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

form of theft. All the server security features must be enabled. In addition the organization
should use both software and hardware firewalls which ought to be located on the organization
broadband router. The organization should guard server passwords and should be changed
regularly. Other warnings includes install anti-virus programs in all organization computers to
ensure protection of user computers. Lastly an organization should be aware of virus warnings
which are known as hoaxes which can erase files (CiscoSystemsInc, 2018, p. 31).
Access control list to isolate each department internally
To start with ACLs are network filters utilized by switches and routers to permit or
restrict data flow from one department to another one. The reason as to why this network design
should utilize Access Control List (ACL) is so as to provide basic level of security for the
organization network. They provide protection to organization systems on higher speed
interfaces. Other reasons are ACLs provide traffic flow by restricting delivery of routing updates.
One of the implementation of ACLS is on router interface in each department. In here the router
will act as a packet filter when it denies or forwards packets as per the filtering rules. This is a
shown by figure two for this case. In here when packets from one department are denied to other
routers in other departments (Blacharski, 2015, p. 42).
The type of access control lists to be utilized to control access of users to other
departments are extended access lists. These type of access control lists is based on the source
address, port number, and the destination address.
Access control list for DMZ
Access control list for DMZ or what is referred to as de-militarized buffer on the
organization network is an additional security to an organization. To implement access control
list for DMZ ought to be done at firewall level. In here the organization need to use a single
should use both software and hardware firewalls which ought to be located on the organization
broadband router. The organization should guard server passwords and should be changed
regularly. Other warnings includes install anti-virus programs in all organization computers to
ensure protection of user computers. Lastly an organization should be aware of virus warnings
which are known as hoaxes which can erase files (CiscoSystemsInc, 2018, p. 31).
Access control list to isolate each department internally
To start with ACLs are network filters utilized by switches and routers to permit or
restrict data flow from one department to another one. The reason as to why this network design
should utilize Access Control List (ACL) is so as to provide basic level of security for the
organization network. They provide protection to organization systems on higher speed
interfaces. Other reasons are ACLs provide traffic flow by restricting delivery of routing updates.
One of the implementation of ACLS is on router interface in each department. In here the router
will act as a packet filter when it denies or forwards packets as per the filtering rules. This is a
shown by figure two for this case. In here when packets from one department are denied to other
routers in other departments (Blacharski, 2015, p. 42).
The type of access control lists to be utilized to control access of users to other
departments are extended access lists. These type of access control lists is based on the source
address, port number, and the destination address.
Access control list for DMZ
Access control list for DMZ or what is referred to as de-militarized buffer on the
organization network is an additional security to an organization. To implement access control
list for DMZ ought to be done at firewall level. In here the organization need to use a single
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

firewall with about three network interfaces which is used ti create network architecture that
contains a DMZ (Odom, 2009, p. 143) .
Conclusion
This paper has gone for GPON network design. This is because it offers triple play
service over IP of video, voice, and data. Other benefits listed in this paper include scalability,
ease of maintenance, and the three network requirements which are availability, confidentiality,
and integrity. Lastly, the paper have listed security precautions which should always considered
to keep this GPON design secure.
References
Blacharski, D., 2015. Network security in a mixed environment by Dan Blacharski. 3rd ed. Foster
City: CA : IDG Books Worldwide Press.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed.
Amsterdam: RTU Publishing House.
contains a DMZ (Odom, 2009, p. 143) .
Conclusion
This paper has gone for GPON network design. This is because it offers triple play
service over IP of video, voice, and data. Other benefits listed in this paper include scalability,
ease of maintenance, and the three network requirements which are availability, confidentiality,
and integrity. Lastly, the paper have listed security precautions which should always considered
to keep this GPON design secure.
References
Blacharski, D., 2015. Network security in a mixed environment by Dan Blacharski. 3rd ed. Foster
City: CA : IDG Books Worldwide Press.
Blanc, R. P. & Cotton, I. W., 2014. Computer networking by Robert P Blanc. 2nd ed.
Amsterdam: RTU Publishing House.

CiscoSystemsInc, 2018. Learn Cisco network administration in a month... by Ben Piper, (IT
consultant). 1st ed. New York: Manning Publications.
Donoso, Y., 2016. Network design for IP convergence by Yezid Donoso. 1st ed. New York: CRC
Press .
Hutton, 2018. Designing Cisco Network Service Architecture 2/e.. 1st ed. New York: Cisco
Press.
Lacoste, R., 2014. ICND1 : VLAN Design Considerations by Raymond Lacoste. 4th ed. New
Hampshire: Skillsoft Corporation Press.
Mishra, A. R., 2018. Fundamentals of network planning and optimisation 2G/3G/4G : evolution
to 5G. 2nd ed. New York: John Wiley & Sons.
Odom, W., 2009. Computer networking first-step by Wendell Odom. 3rd ed. New York: John &
Wiley Press.
Owusu, G., O'Brien, P., McCall, J. & Doherty, N. F., 2017. Transforming field and service
operations : methodologies... by Gilbert Owusu. 1st ed. Chicago: Springer Press.
Skandier, T., 2015. CompTIA Network+ Lab Manual. by Toby Skandier. 1st ed. Chicago: John
Wiley & Sons Press.
consultant). 1st ed. New York: Manning Publications.
Donoso, Y., 2016. Network design for IP convergence by Yezid Donoso. 1st ed. New York: CRC
Press .
Hutton, 2018. Designing Cisco Network Service Architecture 2/e.. 1st ed. New York: Cisco
Press.
Lacoste, R., 2014. ICND1 : VLAN Design Considerations by Raymond Lacoste. 4th ed. New
Hampshire: Skillsoft Corporation Press.
Mishra, A. R., 2018. Fundamentals of network planning and optimisation 2G/3G/4G : evolution
to 5G. 2nd ed. New York: John Wiley & Sons.
Odom, W., 2009. Computer networking first-step by Wendell Odom. 3rd ed. New York: John &
Wiley Press.
Owusu, G., O'Brien, P., McCall, J. & Doherty, N. F., 2017. Transforming field and service
operations : methodologies... by Gilbert Owusu. 1st ed. Chicago: Springer Press.
Skandier, T., 2015. CompTIA Network+ Lab Manual. by Toby Skandier. 1st ed. Chicago: John
Wiley & Sons Press.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 13
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



