University VPN Network Design for Small and Medium Enterprise Report
VerifiedAdded on 2023/04/24
|10
|1995
|203
Report
AI Summary
This report presents a comprehensive VPN network design for a Small and Medium Enterprise (SME). It begins with an introduction outlining the project's scope, which includes secure authentication, VPN type selection, website access, bandwidth efficiency, and cost reduction, while acknowledging limitations such as network security and product compatibility. The report details the requirements, including client VPN software, VPN-supporting routers, firewalls, and a VPN server, with an emphasis on secure channels and physical access restrictions. The solution design covers logical and physical design, network topologies, IP addressing, security features, redundancy, and failover plans, and VPN service implementation. The network topology utilizes public telecommunication networks, encryption, and security procedures. The report also includes detailed IP addressing schemes and security features like firewalls, IDP/IPS systems, antivirus software, and user access policies. Redundancy and failover plans involve redundant links, virtualization, regular backups, and power backup plans. The VPN service implementation section explores remote access, intranet, extranet VPNs, and WAN replacement options. The report concludes by emphasizing the importance of identifying project scopes and limitations, analyzing organizational requirements, and implementing appropriate network topologies, IP addressing, security measures, and redundancy plans.

Running head: VIRTUAL PRIVATE NETWORK
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
VPN Network Design for SME network and VPN services
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction....................................................................................................................................2
Scopes and Limitations...................................................................................................................2
Requirements.................................................................................................................................3
Solution Design...............................................................................................................................3
a. Logical Design.........................................................................................................................3
b. Physical Design.......................................................................................................................4
c. Network Topologies................................................................................................................4
d. IP Addressing..........................................................................................................................4
e. Security features and policies.................................................................................................5
f. Redundancy and failover plans................................................................................................6
g. VPN service implementation...................................................................................................6
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................8
VIRTUAL PRIVATE NETWORK
Table of Contents
Introduction....................................................................................................................................2
Scopes and Limitations...................................................................................................................2
Requirements.................................................................................................................................3
Solution Design...............................................................................................................................3
a. Logical Design.........................................................................................................................3
b. Physical Design.......................................................................................................................4
c. Network Topologies................................................................................................................4
d. IP Addressing..........................................................................................................................4
e. Security features and policies.................................................................................................5
f. Redundancy and failover plans................................................................................................6
g. VPN service implementation...................................................................................................6
Conclusion......................................................................................................................................7
Bibliography....................................................................................................................................8

2
VIRTUAL PRIVATE NETWORK
Introduction
A virtual private network is designed for a small and medium enterprise after the analysis of the
service requirement and the protocols used for the development of a VPN network solution. An analysis
is made on the architecture that should be used for the development of the network and a road map of
the process is interpreted in the report for following it and support the administrator for the
management of the development process of the project. The technologies that can be applied for
increasing the efficiency and scalability of the network framework is analyzed such that it can be
implemented for meeting the long term goals of the organization. The scope and limitation of the
project is analyzed and a solution design is created before starting the project development process
such that the design is evaluated by aligning it with the requirement of the organization.
Scopes and Limitations
The scope of designing the VPN network design are as follows:
Use of secure authentication mechanism and changing password on regular basis for
increasing the security of VPN network
Selection of type of VPN depending on the requirement and structure of the
organization.
Bypassing the filtered and blocked websites and access all the websites and services
Increasing the efficiency of bandwidth and network with the implementation of VPN.
Reducing the cost of maintenance and communication for communicating with the
remote branches
The limitation for designing the VPN network are as follows:
Understanding the installation and configuration of the security issues of the network
for ensuring sufficient protection is implemented for the network
Ensuring reliability and performance for the internet based VPN and application of
sufficient protection for the organizational resources
Compatibility of the different VPN product with the equipment used for the
development of the network
Selection of the router and the transmission link for eliminating the risk of slower VPN
speed and testing it according to the requirement.
VIRTUAL PRIVATE NETWORK
Introduction
A virtual private network is designed for a small and medium enterprise after the analysis of the
service requirement and the protocols used for the development of a VPN network solution. An analysis
is made on the architecture that should be used for the development of the network and a road map of
the process is interpreted in the report for following it and support the administrator for the
management of the development process of the project. The technologies that can be applied for
increasing the efficiency and scalability of the network framework is analyzed such that it can be
implemented for meeting the long term goals of the organization. The scope and limitation of the
project is analyzed and a solution design is created before starting the project development process
such that the design is evaluated by aligning it with the requirement of the organization.
Scopes and Limitations
The scope of designing the VPN network design are as follows:
Use of secure authentication mechanism and changing password on regular basis for
increasing the security of VPN network
Selection of type of VPN depending on the requirement and structure of the
organization.
Bypassing the filtered and blocked websites and access all the websites and services
Increasing the efficiency of bandwidth and network with the implementation of VPN.
Reducing the cost of maintenance and communication for communicating with the
remote branches
The limitation for designing the VPN network are as follows:
Understanding the installation and configuration of the security issues of the network
for ensuring sufficient protection is implemented for the network
Ensuring reliability and performance for the internet based VPN and application of
sufficient protection for the organizational resources
Compatibility of the different VPN product with the equipment used for the
development of the network
Selection of the router and the transmission link for eliminating the risk of slower VPN
speed and testing it according to the requirement.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
VIRTUAL PRIVATE NETWORK
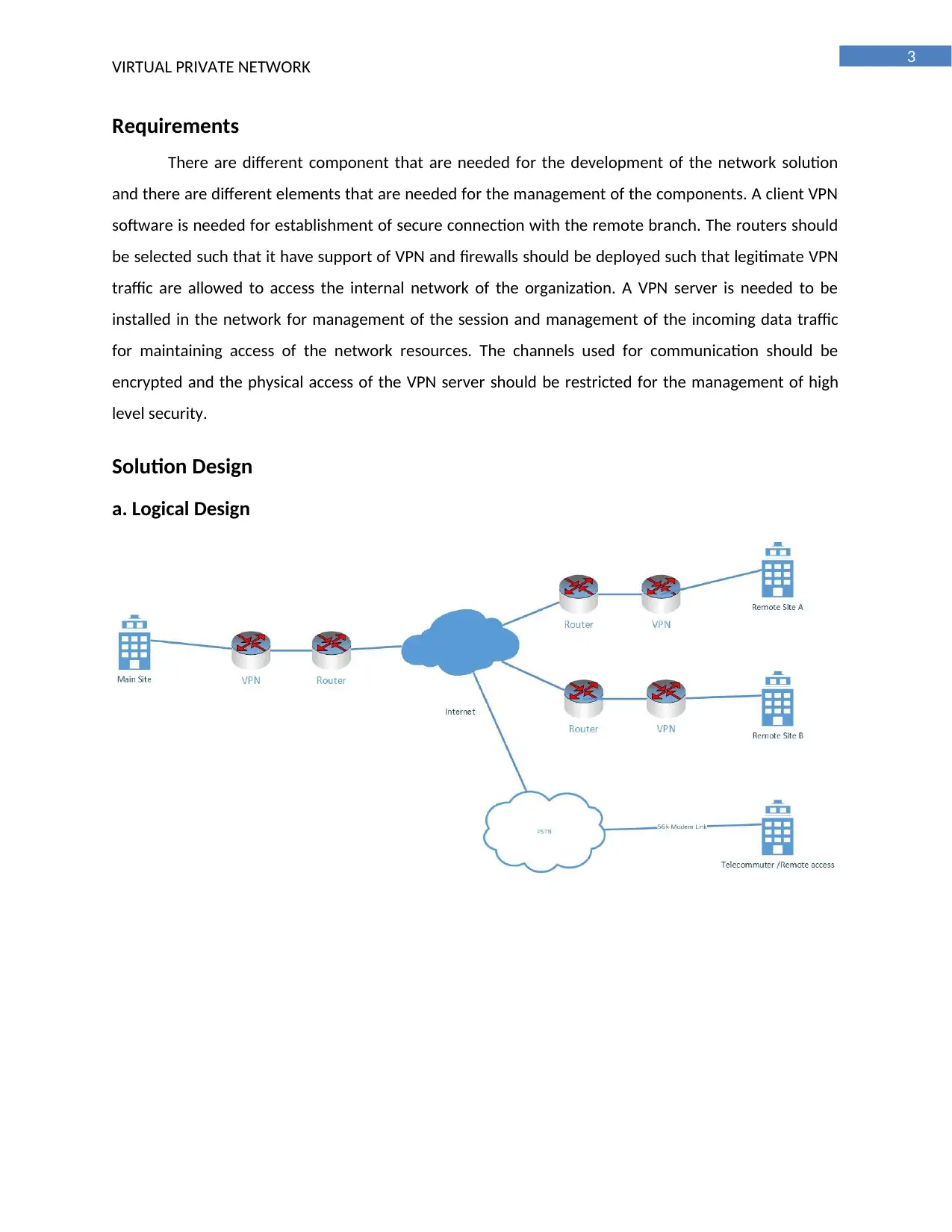
Requirements
There are different component that are needed for the development of the network solution
and there are different elements that are needed for the management of the components. A client VPN
software is needed for establishment of secure connection with the remote branch. The routers should
be selected such that it have support of VPN and firewalls should be deployed such that legitimate VPN
traffic are allowed to access the internal network of the organization. A VPN server is needed to be
installed in the network for management of the session and management of the incoming data traffic
for maintaining access of the network resources. The channels used for communication should be
encrypted and the physical access of the VPN server should be restricted for the management of high
level security.
Solution Design
a. Logical Design
VIRTUAL PRIVATE NETWORK
Requirements
There are different component that are needed for the development of the network solution
and there are different elements that are needed for the management of the components. A client VPN
software is needed for establishment of secure connection with the remote branch. The routers should
be selected such that it have support of VPN and firewalls should be deployed such that legitimate VPN
traffic are allowed to access the internal network of the organization. A VPN server is needed to be
installed in the network for management of the session and management of the incoming data traffic
for maintaining access of the network resources. The channels used for communication should be
encrypted and the physical access of the VPN server should be restricted for the management of high
level security.
Solution Design
a. Logical Design
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
VIRTUAL PRIVATE NETWORK
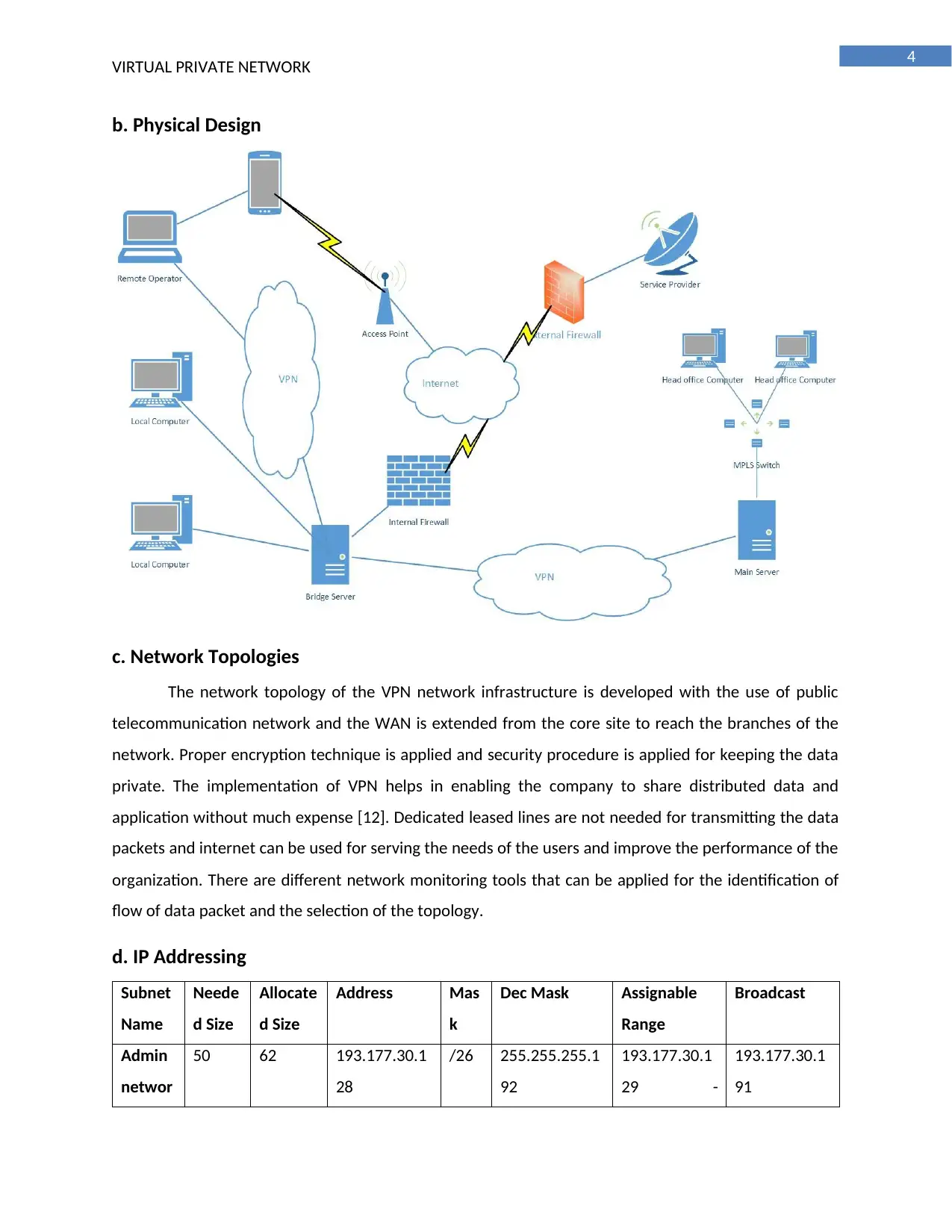
b. Physical Design
c. Network Topologies
The network topology of the VPN network infrastructure is developed with the use of public
telecommunication network and the WAN is extended from the core site to reach the branches of the
network. Proper encryption technique is applied and security procedure is applied for keeping the data
private. The implementation of VPN helps in enabling the company to share distributed data and
application without much expense [12]. Dedicated leased lines are not needed for transmitting the data
packets and internet can be used for serving the needs of the users and improve the performance of the
organization. There are different network monitoring tools that can be applied for the identification of
flow of data packet and the selection of the topology.
d. IP Addressing
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Admin
networ
50 62 193.177.30.1
28
/26 255.255.255.1
92
193.177.30.1
29 -
193.177.30.1
91
VIRTUAL PRIVATE NETWORK
b. Physical Design
c. Network Topologies
The network topology of the VPN network infrastructure is developed with the use of public
telecommunication network and the WAN is extended from the core site to reach the branches of the
network. Proper encryption technique is applied and security procedure is applied for keeping the data
private. The implementation of VPN helps in enabling the company to share distributed data and
application without much expense [12]. Dedicated leased lines are not needed for transmitting the data
packets and internet can be used for serving the needs of the users and improve the performance of the
organization. There are different network monitoring tools that can be applied for the identification of
flow of data packet and the selection of the topology.
d. IP Addressing
Subnet
Name
Neede
d Size
Allocate
d Size
Address Mas
k
Dec Mask Assignable
Range
Broadcast
Admin
networ
50 62 193.177.30.1
28
/26 255.255.255.1
92
193.177.30.1
29 -
193.177.30.1
91
5
VIRTUAL PRIVATE NETWORK
k 193.177.30.1
90
Finance
Networ
k
100 126 193.177.30.0 /25 255.255.255.1
28
193.177.30.1
-
193.177.30.1
26
193.177.30.1
27
Sales
Networ
k
200 254 193.177.28.0 /24 255.255.255.0 193.177.28.1
-
193.177.28.2
54
193.177.28.2
55
Dispatc
h
Networ
k
150 254 193.177.29.0 /24 255.255.255.0 193.177.29.1
-
193.177.29.2
54
193.177.29.2
55
e. Security features and policies
The following are the security implication that can be applied for increasing the security of the
VPN network.
The connection of VPN can be strengthened with the deployment of firewall
An IDP or IPS system can be deployed for monitoring the attack and increasing the
efficiency of the system
The remote client should be installed with Antivirus software for prevention of spread of
virus in the network [6]
The logging of the user into the server should be managed and auditing function should
be implemented for recording the unauthorized attempts and reviewing the
vulnerability of the network.
The network policy should be developed for the deployment of the network framework and
provide guidelines to the user for the appropriate usage of the VPN and distribute it to the responsible
people for controlling and governing the usage of VPN. The user access policy should be developed for
the management of the access rights for the user and providing them to access the necessary resources.
VIRTUAL PRIVATE NETWORK
k 193.177.30.1
90
Finance
Networ
k
100 126 193.177.30.0 /25 255.255.255.1
28
193.177.30.1
-
193.177.30.1
26
193.177.30.1
27
Sales
Networ
k
200 254 193.177.28.0 /24 255.255.255.0 193.177.28.1
-
193.177.28.2
54
193.177.28.2
55
Dispatc
h
Networ
k
150 254 193.177.29.0 /24 255.255.255.0 193.177.29.1
-
193.177.29.2
54
193.177.29.2
55
e. Security features and policies
The following are the security implication that can be applied for increasing the security of the
VPN network.
The connection of VPN can be strengthened with the deployment of firewall
An IDP or IPS system can be deployed for monitoring the attack and increasing the
efficiency of the system
The remote client should be installed with Antivirus software for prevention of spread of
virus in the network [6]
The logging of the user into the server should be managed and auditing function should
be implemented for recording the unauthorized attempts and reviewing the
vulnerability of the network.
The network policy should be developed for the deployment of the network framework and
provide guidelines to the user for the appropriate usage of the VPN and distribute it to the responsible
people for controlling and governing the usage of VPN. The user access policy should be developed for
the management of the access rights for the user and providing them to access the necessary resources.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
VIRTUAL PRIVATE NETWORK
f. Redundancy and failover plans
The servers should be connected via redundant link for the management of the network loads
and reduce the risk of unavailability due to failure of link. The data traffic in the network is needed to be
managed and the servers should have support for virtualization such that it can be used for serving more
number of users [2]. A regular backup of the network should be performed and stored in remote
location such that it can be used for restoring the network in case of disaster and no data is lost. A
power backup plan should also be created such that the situation of power outrages can be handled and
the uptime of the network is increased.
g. VPN service implementation
For the implementation of the VPN service a research is done on the business needs and it is
found that VPN can be deployed for getting various service such as:
Remote access VPN – This is used for connecting a remote user using mobile or home network
to connect with the private network of the organization. The VPN is used for permitting secured,
encrypted connectivity between the private network and remote users.
Intranet VPN – This type of VPN is created for establishing connection between two fixed
location and it can be branch to branch, head office to branch, etc [5]. This protocol is used for joining
multiple remote location and work as a single private network.
Extranet VPN – It is used for connecting the business partner of the organization for example
customer, supplier and allow the user to work with other parties and securely share data in the shared
environment.
WAN replacement – VPN can be used as an alternative to WAN because the maintenance cost
of WAN is much higher specially in case of network dispersed over a larger geographical area. A less cost
is required for VPN because the overhead cost for management of WAN is higher and the scalability is
higher [10]. The reliability and performance of the network can be improved with the implementation of
VPN and creating a tunnel for communication via the internet.
Conclusion
It can be concluded that it is essential to identify the scope and limitation of the project for
identification of errors and resolving it before deployment of the network framework. The requirement
of the organization is needed to be analyzed such that it helps in analyzing the VPN parts and service
VIRTUAL PRIVATE NETWORK
f. Redundancy and failover plans
The servers should be connected via redundant link for the management of the network loads
and reduce the risk of unavailability due to failure of link. The data traffic in the network is needed to be
managed and the servers should have support for virtualization such that it can be used for serving more
number of users [2]. A regular backup of the network should be performed and stored in remote
location such that it can be used for restoring the network in case of disaster and no data is lost. A
power backup plan should also be created such that the situation of power outrages can be handled and
the uptime of the network is increased.
g. VPN service implementation
For the implementation of the VPN service a research is done on the business needs and it is
found that VPN can be deployed for getting various service such as:
Remote access VPN – This is used for connecting a remote user using mobile or home network
to connect with the private network of the organization. The VPN is used for permitting secured,
encrypted connectivity between the private network and remote users.
Intranet VPN – This type of VPN is created for establishing connection between two fixed
location and it can be branch to branch, head office to branch, etc [5]. This protocol is used for joining
multiple remote location and work as a single private network.
Extranet VPN – It is used for connecting the business partner of the organization for example
customer, supplier and allow the user to work with other parties and securely share data in the shared
environment.
WAN replacement – VPN can be used as an alternative to WAN because the maintenance cost
of WAN is much higher specially in case of network dispersed over a larger geographical area. A less cost
is required for VPN because the overhead cost for management of WAN is higher and the scalability is
higher [10]. The reliability and performance of the network can be improved with the implementation of
VPN and creating a tunnel for communication via the internet.
Conclusion
It can be concluded that it is essential to identify the scope and limitation of the project for
identification of errors and resolving it before deployment of the network framework. The requirement
of the organization is needed to be analyzed such that it helps in analyzing the VPN parts and service
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
VIRTUAL PRIVATE NETWORK
essential for the development of the project. The network topology that should be followed for the
development of the network is needed to be identified and an IP addressing plan is created for the
configuration of the network interface of the hardware device essential for the development of the
network framework. AN analysis is made on the security requirement of the organization and a security
feature and policy is applied to the network for increasing the security of the network. A redundancy
and failover plan is created for increasing the availability of the network and provide service to the
users.
VIRTUAL PRIVATE NETWORK
essential for the development of the project. The network topology that should be followed for the
development of the network is needed to be identified and an IP addressing plan is created for the
configuration of the network interface of the hardware device essential for the development of the
network framework. AN analysis is made on the security requirement of the organization and a security
feature and policy is applied to the network for increasing the security of the network. A redundancy
and failover plan is created for increasing the availability of the network and provide service to the
users.

8
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. Aguado, Alejandro, et al. "VPN Service Provisioning via Virtual Router Deployment and Quantum
Key Distribution." 2018 Optical Fiber Communications Conference and Exposition (OFC). IEEE,
2018.
[2]. Aznar, José, et al. "CNSMO: A Network Services Manager/Orchestrator tool for cloud federated
environments." Ad Hoc Networking Workshop (Med-Hoc-Net), 2016 Mediterranean. IEEE, 2016.
[3]. Baranda, Jorge, et al. "Orchestration of end-to-end network services in the 5G-Crosshaul multi-
domain multi-technology transport network." IEEE Communications Magazine 56.7 (2018): 184-
191.
[4]. Baucke, Stephan, et al. "Cloud API support for self-service Virtual Network Function (VNF)
deployment." Network Function Virtualization and Software Defined Network (NFV-SDN), 2015
IEEE Conference on. IEEE, 2015.
[5]. Brown, Gabriel. "Mobile edge computing use cases and deployment options." Juniper White
Paper (2016): 1-10.
[6]. DeLong, Mark R., et al. "Protecting sensitive research data and meeting researchers needs: Duke
University's Protected Network." arXiv preprint arXiv:1710.03317 (2017).
[7]. Hong, Tae Chul, et al. "Network architecture for control and non-payload communication of
UAV." Information and Communication Technology Convergence (ICTC), 2016 International
Conference on. IEEE, 2016.
[8]. Khan, Ateeq, et al. "Variability management in Infrastructure as a Service: Scenarios in cloud
deployment models." Computing, Networking and Communications (ICNC), 2017 International
Conference on. IEEE, 2017.
[9]. Liang, Chengchao, and F. Richard Yu. "Wireless network virtualization: A survey, some research
issues and challenges." IEEE Communications Surveys & Tutorials 17.1 (2015): 358-380.
[10]. Liu, Guojun, et al. "Evolution Models of Power Communication Network Management
Based on IPv6 Network." 2015 International Conference on Industrial Technology and
Management Science. Atlantis Press, 2015.
[11]. Perrig, Adrian, et al. "Deployment and Operation." SCION: A Secure Internet
Architecture. Springer, Cham, 2017. 191-239.
[12]. Shankar, R., and S. Duraisamy. "Different Service Models and Deployment Models of
Cloud Computing: Challenges." (2018).
VIRTUAL PRIVATE NETWORK
Bibliography
[1]. Aguado, Alejandro, et al. "VPN Service Provisioning via Virtual Router Deployment and Quantum
Key Distribution." 2018 Optical Fiber Communications Conference and Exposition (OFC). IEEE,
2018.
[2]. Aznar, José, et al. "CNSMO: A Network Services Manager/Orchestrator tool for cloud federated
environments." Ad Hoc Networking Workshop (Med-Hoc-Net), 2016 Mediterranean. IEEE, 2016.
[3]. Baranda, Jorge, et al. "Orchestration of end-to-end network services in the 5G-Crosshaul multi-
domain multi-technology transport network." IEEE Communications Magazine 56.7 (2018): 184-
191.
[4]. Baucke, Stephan, et al. "Cloud API support for self-service Virtual Network Function (VNF)
deployment." Network Function Virtualization and Software Defined Network (NFV-SDN), 2015
IEEE Conference on. IEEE, 2015.
[5]. Brown, Gabriel. "Mobile edge computing use cases and deployment options." Juniper White
Paper (2016): 1-10.
[6]. DeLong, Mark R., et al. "Protecting sensitive research data and meeting researchers needs: Duke
University's Protected Network." arXiv preprint arXiv:1710.03317 (2017).
[7]. Hong, Tae Chul, et al. "Network architecture for control and non-payload communication of
UAV." Information and Communication Technology Convergence (ICTC), 2016 International
Conference on. IEEE, 2016.
[8]. Khan, Ateeq, et al. "Variability management in Infrastructure as a Service: Scenarios in cloud
deployment models." Computing, Networking and Communications (ICNC), 2017 International
Conference on. IEEE, 2017.
[9]. Liang, Chengchao, and F. Richard Yu. "Wireless network virtualization: A survey, some research
issues and challenges." IEEE Communications Surveys & Tutorials 17.1 (2015): 358-380.
[10]. Liu, Guojun, et al. "Evolution Models of Power Communication Network Management
Based on IPv6 Network." 2015 International Conference on Industrial Technology and
Management Science. Atlantis Press, 2015.
[11]. Perrig, Adrian, et al. "Deployment and Operation." SCION: A Secure Internet
Architecture. Springer, Cham, 2017. 191-239.
[12]. Shankar, R., and S. Duraisamy. "Different Service Models and Deployment Models of
Cloud Computing: Challenges." (2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
VIRTUAL PRIVATE NETWORK
VIRTUAL PRIVATE NETWORK
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




