ITECH1102 Networking Assignment: Data Link, Transport, Cloud Computing
VerifiedAdded on 2023/04/25
|15
|3115
|65
Homework Assignment
AI Summary
This assignment provides a comprehensive overview of the Data Link Layer, Transport Layer, and Cloud Computing concepts within the context of the ITECH1102 Networking and Security course. The Data Link Layer section details its function in the OSI model, its sublayers (MAC and LLC), and key functions such as error detection, framing, and media access control. The Transport Layer focuses on its role, the TCP and UDP protocols, and the function of ports. It explains the key functions of the transport layer, including data handling, connection establishment, addressing, packet fragmentation, and flow control. Finally, the cloud computing section introduces cloud computing, its architecture, and various cloud services, explaining the concept of cloud computing as a service delivery model. This assignment is designed to help students understand networking fundamentals, prepare for exams, and enhance their understanding of theoretical concepts.

Data link layer
This is the second layer in the OSI model and governs the transfer of data
between two nodes on same network. The data is transferred on basis of
Physical ID of the devices. As per OSI standard, the layer itself is sandwiched
between Physical layer and Network Layer. Physical layer deals with the
underlying medium of the network. Network layer manages the routing of data
across networks. Data link layer manages data packet between these two
layers.
The data link layer is used for the encoding, unraveling and predictable
relationship of data bits. Data bundles are handled by this layer. The layer itself
is divided into two sublayers. The data link layer's first sublayer is the Media
Access control (MAC) layer. It holds a 48 bit ID which is used for unique
identification of a node with in a network. The MAC layer allows the data link
layer to identify itself on the same network. All data packets routed on
network are directed based on this MAC address.
The data link layer's second sublayer is the logical link control. It manages two
way communication of data stream from higher layers.
Some important functions of Data link layer are given below:
This is the second layer in the OSI model and governs the transfer of data
between two nodes on same network. The data is transferred on basis of
Physical ID of the devices. As per OSI standard, the layer itself is sandwiched
between Physical layer and Network Layer. Physical layer deals with the
underlying medium of the network. Network layer manages the routing of data
across networks. Data link layer manages data packet between these two
layers.
The data link layer is used for the encoding, unraveling and predictable
relationship of data bits. Data bundles are handled by this layer. The layer itself
is divided into two sublayers. The data link layer's first sublayer is the Media
Access control (MAC) layer. It holds a 48 bit ID which is used for unique
identification of a node with in a network. The MAC layer allows the data link
layer to identify itself on the same network. All data packets routed on
network are directed based on this MAC address.
The data link layer's second sublayer is the logical link control. It manages two
way communication of data stream from higher layers.
Some important functions of Data link layer are given below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Maintain bit rate - bits should be passed on at rates not to overwhelm the
receiver. This is done by making use of suitable buffers and use of
acknowledgments between communicating parties.
Data link layer is to pass on the data in and out from network layer. The bit
by bit data received at the input must be framed as a data packet and
transferred to the upper layers.
Data link layer transforms data packet in to data bits. These data bits are
then encoded in physical layer for transmission of the data. Reverse is also
done when getting the data from physical layer. The bit stream is converted
into data packet and forwarded.
Keep track of any errors in bit values by making using of CRC bits in data
packets and perform CRC checks. Due to noise in physical channels, some
bits received might be in error. The various parity and redundancy bits are
used to identify single bit or burst errors. The measures are then taken
accordingly to correct the error or request retransmission of packet.
Link Configuration Control: The layer must also handle the mode of
transmission. Some network media may support full duplex mode, others
may only support half duplex or simplex modes of transmission. Not all
channels full two way communication. This must be taken care of by the
layer and data must only be transmitted when media is available for
transmission.
receiver. This is done by making use of suitable buffers and use of
acknowledgments between communicating parties.
Data link layer is to pass on the data in and out from network layer. The bit
by bit data received at the input must be framed as a data packet and
transferred to the upper layers.
Data link layer transforms data packet in to data bits. These data bits are
then encoded in physical layer for transmission of the data. Reverse is also
done when getting the data from physical layer. The bit stream is converted
into data packet and forwarded.
Keep track of any errors in bit values by making using of CRC bits in data
packets and perform CRC checks. Due to noise in physical channels, some
bits received might be in error. The various parity and redundancy bits are
used to identify single bit or burst errors. The measures are then taken
accordingly to correct the error or request retransmission of packet.
Link Configuration Control: The layer must also handle the mode of
transmission. Some network media may support full duplex mode, others
may only support half duplex or simplex modes of transmission. Not all
channels full two way communication. This must be taken care of by the
layer and data must only be transmitted when media is available for
transmission.

Framing of packet must also be done by the layer adding the MAC address in
the header for other devices to recognize and accept the packet at the
matching node. This might need use of ARP from higher layers to resolve
MAC addresses of receiving stations. This is done by sending broadcast
messages on network and processing an ARP reply received by the node
responsible for providing the MAC id.
Packet Synchronization: The packets must be framed with synchronization
bits on each side to allow the receiving terminals detect start and end of the
packet on media. This is important for physical media to be able to recognize
the frame boundaries.
Packet Identification: Data Link layer also needs to decode the packets
received on its input and match the destination MAC address in the packet
with its own MAC address. The packet should be buffered and processed if
the address matches and forwarded to upper layers for further processing.
Carrier Sense and Media Access: Physical layer only converts the signals into
streams of bits. It makes no decision based on values of those bits. It’s up to
the data link layer to make sense out of it. The layer must decide if the
carrier is occupied or free at any given moment before it starts transmission.
There are two methodologies used for carrier access, one is based on
transmission and waiting for collision to occur called as CSMA/CD (Carrier
sense Multiple Access/ Collision Detection) and other one senses carrier
the header for other devices to recognize and accept the packet at the
matching node. This might need use of ARP from higher layers to resolve
MAC addresses of receiving stations. This is done by sending broadcast
messages on network and processing an ARP reply received by the node
responsible for providing the MAC id.
Packet Synchronization: The packets must be framed with synchronization
bits on each side to allow the receiving terminals detect start and end of the
packet on media. This is important for physical media to be able to recognize
the frame boundaries.
Packet Identification: Data Link layer also needs to decode the packets
received on its input and match the destination MAC address in the packet
with its own MAC address. The packet should be buffered and processed if
the address matches and forwarded to upper layers for further processing.
Carrier Sense and Media Access: Physical layer only converts the signals into
streams of bits. It makes no decision based on values of those bits. It’s up to
the data link layer to make sense out of it. The layer must decide if the
carrier is occupied or free at any given moment before it starts transmission.
There are two methodologies used for carrier access, one is based on
transmission and waiting for collision to occur called as CSMA/CD (Carrier
sense Multiple Access/ Collision Detection) and other one senses carrier
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

before transmission and tries to avoid collision, called as CSMA/CA (Carrier
Sense Multiple Access/Collision Avoidance).
CSMA/CD is usually preferred for Wired Networks, where each node
transmits the data and senses the media at the same time. If there is
transmission by more than one node at the same time, both the nodes cease
to transmit data, wait for random amount of time and transmit again.
CSMA/CA is usually preferred for wireless networks, since two nodes might
not be in range of each other but in range of third device. In such a case
collision will be hard to detect by transmitting stations. So transmitting
stations first send a request to reserve a channel before transmission. Only if
the channel is free, the node starts transmission. And relinquishes the
channel after it is done transmitting.
All these functions are carried out by the data link layer for every single
packet that passes through the layer either upstream or downstream. This
way the layer keeps the node connected in a network.
Sense Multiple Access/Collision Avoidance).
CSMA/CD is usually preferred for Wired Networks, where each node
transmits the data and senses the media at the same time. If there is
transmission by more than one node at the same time, both the nodes cease
to transmit data, wait for random amount of time and transmit again.
CSMA/CA is usually preferred for wireless networks, since two nodes might
not be in range of each other but in range of third device. In such a case
collision will be hard to detect by transmitting stations. So transmitting
stations first send a request to reserve a channel before transmission. Only if
the channel is free, the node starts transmission. And relinquishes the
channel after it is done transmitting.
All these functions are carried out by the data link layer for every single
packet that passes through the layer either upstream or downstream. This
way the layer keeps the node connected in a network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Transport Layer
Transport layer is middle layer of the OSI model. The fourth layer sandwiched
between Network layer on downstream and Session layer on Upstream. The
purpose of the layer is delivery of packets from Host application to client
application. The TCP uses port/ socket number to identify the applications on
each host. This is coordination with session layer allows for distribution of data
packets received at the client end from multiple sources to correct application
at the receiver machine. The Layer has two protocols for data transfer that are
currently in use under TCP/IP model. No protocol as such is specified in the OSI
model.
Ports
The UDP and TCP uses the model of ports for communication. There can be
many services executing on a single host i.e. web browsers, email etc. Every
service that is being executed on the host has a pot assigned. A port is a 16-bit
integer i.e. from 1 to 65535.
Each TCP and UDP link must have a source and a destination port allocated.
Whenever a certain service being executed on a host it starts listens to a port
i.e. it notifies the operating system on the host that it needs to collect data
guided to that specific port.
Transport layer is middle layer of the OSI model. The fourth layer sandwiched
between Network layer on downstream and Session layer on Upstream. The
purpose of the layer is delivery of packets from Host application to client
application. The TCP uses port/ socket number to identify the applications on
each host. This is coordination with session layer allows for distribution of data
packets received at the client end from multiple sources to correct application
at the receiver machine. The Layer has two protocols for data transfer that are
currently in use under TCP/IP model. No protocol as such is specified in the OSI
model.
Ports
The UDP and TCP uses the model of ports for communication. There can be
many services executing on a single host i.e. web browsers, email etc. Every
service that is being executed on the host has a pot assigned. A port is a 16-bit
integer i.e. from 1 to 65535.
Each TCP and UDP link must have a source and a destination port allocated.
Whenever a certain service being executed on a host it starts listens to a port
i.e. it notifies the operating system on the host that it needs to collect data
guided to that specific port.
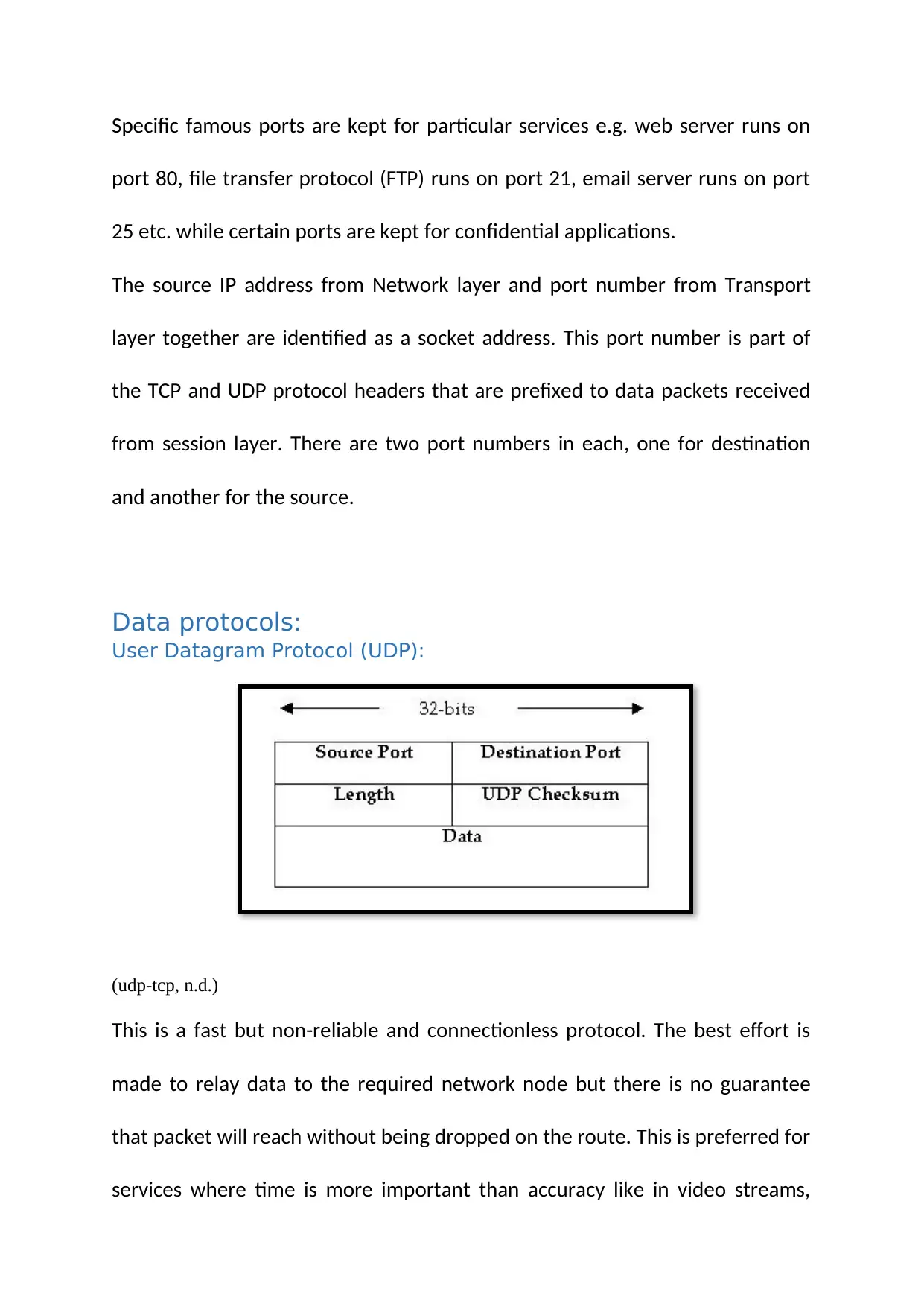
Specific famous ports are kept for particular services e.g. web server runs on
port 80, file transfer protocol (FTP) runs on port 21, email server runs on port
25 etc. while certain ports are kept for confidential applications.
The source IP address from Network layer and port number from Transport
layer together are identified as a socket address. This port number is part of
the TCP and UDP protocol headers that are prefixed to data packets received
from session layer. There are two port numbers in each, one for destination
and another for the source.
Data protocols:
User Datagram Protocol (UDP):
(udp-tcp, n.d.)
This is a fast but non-reliable and connectionless protocol. The best effort is
made to relay data to the required network node but there is no guarantee
that packet will reach without being dropped on the route. This is preferred for
services where time is more important than accuracy like in video streams,
port 80, file transfer protocol (FTP) runs on port 21, email server runs on port
25 etc. while certain ports are kept for confidential applications.
The source IP address from Network layer and port number from Transport
layer together are identified as a socket address. This port number is part of
the TCP and UDP protocol headers that are prefixed to data packets received
from session layer. There are two port numbers in each, one for destination
and another for the source.
Data protocols:
User Datagram Protocol (UDP):
(udp-tcp, n.d.)
This is a fast but non-reliable and connectionless protocol. The best effort is
made to relay data to the required network node but there is no guarantee
that packet will reach without being dropped on the route. This is preferred for
services where time is more important than accuracy like in video streams,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
audio calls etc. There is no means to perform retransmission of lost packets or
track lost packets. The packet header and the original data packet are
encapsulated in an IP Packet and transmitted. If the packet reaches the
destination IP, the port numbers are looked up and data payload is forwarded
to appropriate service.
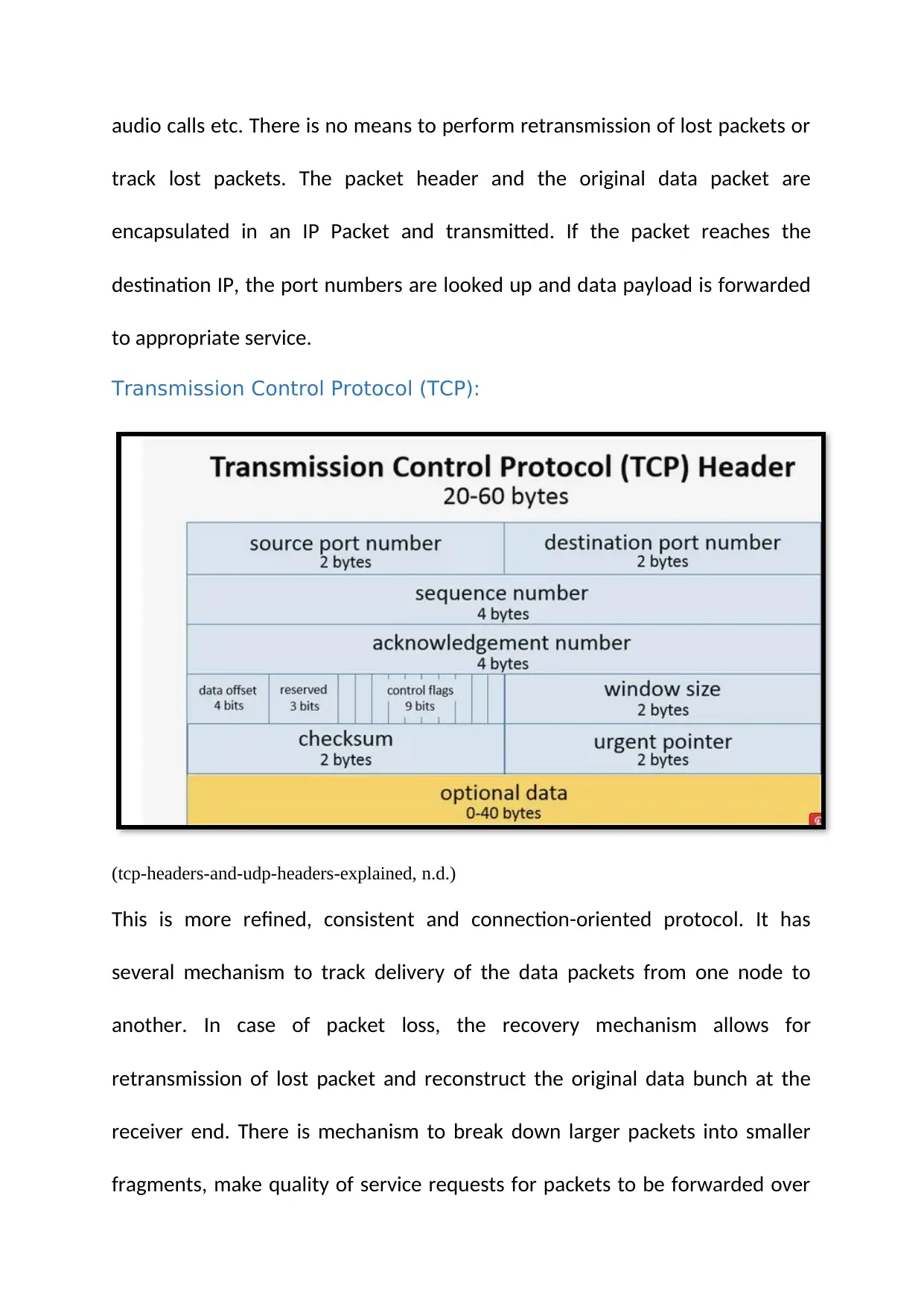
Transmission Control Protocol (TCP):
(tcp-headers-and-udp-headers-explained, n.d.)
This is more refined, consistent and connection-oriented protocol. It has
several mechanism to track delivery of the data packets from one node to
another. In case of packet loss, the recovery mechanism allows for
retransmission of lost packet and reconstruct the original data bunch at the
receiver end. There is mechanism to break down larger packets into smaller
fragments, make quality of service requests for packets to be forwarded over
track lost packets. The packet header and the original data packet are
encapsulated in an IP Packet and transmitted. If the packet reaches the
destination IP, the port numbers are looked up and data payload is forwarded
to appropriate service.
Transmission Control Protocol (TCP):
(tcp-headers-and-udp-headers-explained, n.d.)
This is more refined, consistent and connection-oriented protocol. It has
several mechanism to track delivery of the data packets from one node to
another. In case of packet loss, the recovery mechanism allows for
retransmission of lost packet and reconstruct the original data bunch at the
receiver end. There is mechanism to break down larger packets into smaller
fragments, make quality of service requests for packets to be forwarded over
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
other packets by bypassing the queue. The mechanism is more complex than
UDP and requires more resources over network.
Functions of Transport Layer:
Data Handling and Packaging: Transport Layer also lays out rules by which
applications are able to send data to it from higher layers. This received data
packet is then packaged into TCP or UDP packets to be sent to the destination
node’s Transport Layer. The destination software unpacks the data, removes
the TCP/UDP headers and gives it to the application on the destination
machine
Data Transfer: Conceptually, the responsibility of transmission of entire data
package and its integrity being maintained until it reaches the destination, is
on a transmitting device. Following the division of functions of task among
layers, this is done by having the transport layer responsible for sending the
data packets to the underlying network-layer protocol such that all data can be
received by the other machine truthfully.
Connection Establishment: Transport Layer proposed a set of defined rules
that devices must follow to negotiate and establish a connection with each
other so as to transfer data, in case of TCP protocol. Once connection is
established, TCP supports managing of connections and handling errors in
transmission or reception that may result due to network issues. When both
UDP and requires more resources over network.
Functions of Transport Layer:
Data Handling and Packaging: Transport Layer also lays out rules by which
applications are able to send data to it from higher layers. This received data
packet is then packaged into TCP or UDP packets to be sent to the destination
node’s Transport Layer. The destination software unpacks the data, removes
the TCP/UDP headers and gives it to the application on the destination
machine
Data Transfer: Conceptually, the responsibility of transmission of entire data
package and its integrity being maintained until it reaches the destination, is
on a transmitting device. Following the division of functions of task among
layers, this is done by having the transport layer responsible for sending the
data packets to the underlying network-layer protocol such that all data can be
received by the other machine truthfully.
Connection Establishment: Transport Layer proposed a set of defined rules
that devices must follow to negotiate and establish a connection with each
other so as to transfer data, in case of TCP protocol. Once connection is
established, TCP supports managing of connections and handling errors in
transmission or reception that may result due to network issues. When both

devices are done with data exchange, a special sequence of packets is
exchanged to terminate the connection at both ends.
Addressing/Multiplexing: Transport layer must also provide means to
differentiate between different applications sharing same IP address on a
machine. Therefore, an important function is multiplexing the data received
from higher layers in the stack and package them so they can be sent out using
the underlying network-layer protocol with unique packet identifiers. The
reverse process must be supported when de-multiplexing the received packets
so that they reach their intended application processes.
These features allow for service level packet delivery in a network owing to
correct functioning of Transport layer.
Packet Fragmentation: Transport layer also holds responsibility of
fragmentation of larger data packets into convenient small sizes packets as per
the capacity of the receiver station. This is called fragmentation of the data.
Each fragmented data packet has its own fragmentation bit set and a unique
sequence number. This helps reconstruction of the original data packet at the
receiver’s transport layer. This feature helps transport layer achieve a better
flow control while keeping the connection alive and not timing out.
Flow Control: The transport layer using TCP protocol also helps to do flow
control or data rate control between the two nodes. Each node engaged in
communication advertises its buffer size or receiver’s window size. Only the
exchanged to terminate the connection at both ends.
Addressing/Multiplexing: Transport layer must also provide means to
differentiate between different applications sharing same IP address on a
machine. Therefore, an important function is multiplexing the data received
from higher layers in the stack and package them so they can be sent out using
the underlying network-layer protocol with unique packet identifiers. The
reverse process must be supported when de-multiplexing the received packets
so that they reach their intended application processes.
These features allow for service level packet delivery in a network owing to
correct functioning of Transport layer.
Packet Fragmentation: Transport layer also holds responsibility of
fragmentation of larger data packets into convenient small sizes packets as per
the capacity of the receiver station. This is called fragmentation of the data.
Each fragmented data packet has its own fragmentation bit set and a unique
sequence number. This helps reconstruction of the original data packet at the
receiver’s transport layer. This feature helps transport layer achieve a better
flow control while keeping the connection alive and not timing out.
Flow Control: The transport layer using TCP protocol also helps to do flow
control or data rate control between the two nodes. Each node engaged in
communication advertises its buffer size or receiver’s window size. Only the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

data bytes advertised by the receiver can be transmitted by the sender at a
given time and then it must wait for acknowledgement till next packet can be
sent again.
given time and then it must wait for acknowledgement till next packet can be
sent again.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cloud computing
Cloud Computing is a very vast field. Space it encompasses several
technologies where internet lies at the heart of it. Ability of devices to connect
to each other over a network broadens the scope of things that can be done,
from where they can be done and how they can be done. Mainly the cloud
computing is divided into users and providers. Uses of the people who make
use of services or the Infrastructures or both of them combined in different
combinations. Providers other people make available those services or
Infrastructures to the people asking for it.
In cloud computing resources are located at a location which is not known or
may not be known to the end user, and might even be irrelevant to the user.
The physical devices and software services are hosted and maintained by a
provider over the internet. This abstraction of services is called cloud.
As a minimum the hardware infrastructure is always provided and maintained
by the provider. Over the top of it the provider may agree to provide certain
software or other services like backup and maintenance of the operating
environment depending upon the user’s requirement. Customer benefits by
not having to deal with technical task of maintaining and servicing the
hardware. That allows users to pay for the services only when he is using it
seems them the licensing costs for software and services.
Cloud Computing is a very vast field. Space it encompasses several
technologies where internet lies at the heart of it. Ability of devices to connect
to each other over a network broadens the scope of things that can be done,
from where they can be done and how they can be done. Mainly the cloud
computing is divided into users and providers. Uses of the people who make
use of services or the Infrastructures or both of them combined in different
combinations. Providers other people make available those services or
Infrastructures to the people asking for it.
In cloud computing resources are located at a location which is not known or
may not be known to the end user, and might even be irrelevant to the user.
The physical devices and software services are hosted and maintained by a
provider over the internet. This abstraction of services is called cloud.
As a minimum the hardware infrastructure is always provided and maintained
by the provider. Over the top of it the provider may agree to provide certain
software or other services like backup and maintenance of the operating
environment depending upon the user’s requirement. Customer benefits by
not having to deal with technical task of maintaining and servicing the
hardware. That allows users to pay for the services only when he is using it
seems them the licensing costs for software and services.

The biggest advantage of cloud computing is its flexibility and availability. The
user can always scale the infrastructure as per its current needs and scale
down when the peak is over. The user need not maintain the entire
infrastructure all the time, this gives a big cost saving.
Some users are still not convinced about security of their data being on the
cloud. Many organizations still want to hold data in their own server rather
than hosting it on third party machines. With new advances in networking
Technologies this risk is reducing and more businesses are now relying on
cloud storage for their data warehouses.
Concept of cloud computing is based upon Technology called virtualization
which allows for more than one operating systems to be running on same
hardware machine. The underlying software makes it appear like each guest
operating system is having Direct Access to the hardware and has total control
of it, in reality the hardware is shared among several guest operating systems.
Depending upon type of virtualizations we can have Type 1 bare metal
architecture or type 2 hosted architecture. Under Type 1 Virtualization, the
Hypervisor layer is the main layer and all other operating systems are guests. In
Type -2, the native operating system runs directly on hardware and a
virtualization service runs on top of it. The guests then talk to this layer instead
of host OS.
user can always scale the infrastructure as per its current needs and scale
down when the peak is over. The user need not maintain the entire
infrastructure all the time, this gives a big cost saving.
Some users are still not convinced about security of their data being on the
cloud. Many organizations still want to hold data in their own server rather
than hosting it on third party machines. With new advances in networking
Technologies this risk is reducing and more businesses are now relying on
cloud storage for their data warehouses.
Concept of cloud computing is based upon Technology called virtualization
which allows for more than one operating systems to be running on same
hardware machine. The underlying software makes it appear like each guest
operating system is having Direct Access to the hardware and has total control
of it, in reality the hardware is shared among several guest operating systems.
Depending upon type of virtualizations we can have Type 1 bare metal
architecture or type 2 hosted architecture. Under Type 1 Virtualization, the
Hypervisor layer is the main layer and all other operating systems are guests. In
Type -2, the native operating system runs directly on hardware and a
virtualization service runs on top of it. The guests then talk to this layer instead
of host OS.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




