Advanced Networking: CDN and CPDoS, Analysis and Mitigation Strategies
VerifiedAdded on 2022/08/20
|10
|2494
|11
Report
AI Summary
This report provides a comprehensive overview of Content Delivery Networks (CDNs) and Cache Poisoning Denial of Service (CPDoS) attacks. It begins by explaining the fundamental principles of CDNs, including their architecture, functionality, and role in optimizing content delivery. The report then delves into the nature of CPDoS attacks, detailing their various types, such as HTTP Header Oversize, HTTP Meta Character, and HTTP Method Override, and how they exploit vulnerabilities in CDN caching mechanisms. The discussion further explores the impact of these attacks on website accessibility and performance. The report also offers a range of mitigation strategies, including caching according to HTTP standards, using appropriate error codes, disabling error page caching, deploying Web Application Firewalls, and securing DNS servers. The report emphasizes the importance of these countermeasures, highlighting the potential exposure of websites to CPDoS attacks and concluding with a discussion on the overall effectiveness and significance of CDNs in the digital landscape.

Running head: NETWORKING
NETWORKING
Name of the Student:
Name of the University:
Author’s Note:
NETWORKING
Name of the Student:
Name of the University:
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING
Introduction:-
CDN is the transparent pillar of the Internet in control of content distribution. Whether
the user distinguishes it or not, everyone interrelates with CDNs regularly. CDN is a physically
circulated network of data centres and proxy servers. The objective is to deliver high
accessibility and performance by allocating the facility spatially virtual to end-users. In this
report are describing the basic principle of CDN and also define the ideal concept and future
implementation of CPDoS.
Discussion:-
CDN:-
Principle of CDN:-
It is a server network connected to distribute content as swiftly, economically, reliably,
and steadily as possible. To progress connectivity and speed, a CDN will locate servers at the
exchange points between several networks (Herbaut et al. 2016). These exchange points are the
prime locations where several Internet suppliers attach to run each other access to traffic
initiating on their several systems. By taking a link to these extraordinary speeds and highly
centralized locations, a CDN supplier can decrease costs and transfer times in massive data
delivery speed.
The quick expansion of the Internet, to publics' life and work, has brought excessive
convenience, the Internet service feature and access to the speediness of stronger desires.
However, the growing bandwidth, the user's quantity is also enhancing, by the Web server
transmission and load distance and other features, slow reaction or frequent nagging and
Introduction:-
CDN is the transparent pillar of the Internet in control of content distribution. Whether
the user distinguishes it or not, everyone interrelates with CDNs regularly. CDN is a physically
circulated network of data centres and proxy servers. The objective is to deliver high
accessibility and performance by allocating the facility spatially virtual to end-users. In this
report are describing the basic principle of CDN and also define the ideal concept and future
implementation of CPDoS.
Discussion:-
CDN:-
Principle of CDN:-
It is a server network connected to distribute content as swiftly, economically, reliably,
and steadily as possible. To progress connectivity and speed, a CDN will locate servers at the
exchange points between several networks (Herbaut et al. 2016). These exchange points are the
prime locations where several Internet suppliers attach to run each other access to traffic
initiating on their several systems. By taking a link to these extraordinary speeds and highly
centralized locations, a CDN supplier can decrease costs and transfer times in massive data
delivery speed.
The quick expansion of the Internet, to publics' life and work, has brought excessive
convenience, the Internet service feature and access to the speediness of stronger desires.
However, the growing bandwidth, the user's quantity is also enhancing, by the Web server
transmission and load distance and other features, slow reaction or frequent nagging and

2NETWORKING
complaining (Mu and Zhao 2015). The explanation is to use caching skill to make the Web
service information flow near to the network broadcast, and it is an existing technology to
improve the network data transmission, to find high-speed involvement and quality declaration.
Usually speaking, communicating data over the Internet is quicker when the data source
and receiver are nearer together. One method to carry source data and receivers closer together is
by caching copies of the source documents in positions that are closer to the receivers (Ibn-
Khedher et al. 2017). When an operator wants the data, recovering it from the neighbouring
location will be earlier than retrieving it from the source, which might theoretically be much
further away. This preparation is usually recognized as edge caching and is the part of the CDN.
Edge servers are proxy supplies that work in a method related to the browser caches.
When an appeal comes into an edge server, it initially identifies the cache to understand if the
content is existing. The content is assisted openly from the edge server.
The content is not in the cache, or the cache entry has passed on, then the edge server creates
an appeal to the source server to improve the information (Zhang et al. 2014). The source server
is the basis of fact for content. It is skilful of serving all of the material that is accessible on the
complaining (Mu and Zhao 2015). The explanation is to use caching skill to make the Web
service information flow near to the network broadcast, and it is an existing technology to
improve the network data transmission, to find high-speed involvement and quality declaration.
Usually speaking, communicating data over the Internet is quicker when the data source
and receiver are nearer together. One method to carry source data and receivers closer together is
by caching copies of the source documents in positions that are closer to the receivers (Ibn-
Khedher et al. 2017). When an operator wants the data, recovering it from the neighbouring
location will be earlier than retrieving it from the source, which might theoretically be much
further away. This preparation is usually recognized as edge caching and is the part of the CDN.
Edge servers are proxy supplies that work in a method related to the browser caches.
When an appeal comes into an edge server, it initially identifies the cache to understand if the
content is existing. The content is assisted openly from the edge server.
The content is not in the cache, or the cache entry has passed on, then the edge server creates
an appeal to the source server to improve the information (Zhang et al. 2014). The source server
is the basis of fact for content. It is skilful of serving all of the material that is accessible on the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORKING
CDN. When the edge server accepts the answer from the source server, it keeps the content in
the cache based on the HTTP headers of the reply. This network follow some steps like that-
An operator requests content from a network application.
The appeal for the content is interrupted by the CDN and transmitted to the neighbouring
PoP.
Suppose these has the content in its cache, the CDN supplies the content. These are
named a cache HIT. If the content is not cached, the appeal if promoted to the source
server, these are called a cache MISS.
In the occasion of a cache HIT, the CDN makes a response with the demanded content.
The response is established by the network application and the content loads much faster
than it would if the source server brought it.
Example:-
Many CDN suppliers also deliver auto-optimization structures that resize images
spontaneously and keeps them for when they are wanted in the upcoming. For instance, any user
website creates use of header pictures that’s 3MB, and a user needs for user content on a 450px-
widescreen (Medagliani et al. 2017). A CDN can directly repeat the user content and display one
that’s 450PX-wide and 30KB-large. Unnecessary to say, CDNs also acted best for supportive
user mobile visitors. CDNs also can regulate spammers, distrustful IP addresses, and also several
classes of crawlers and the actions they expect to do.
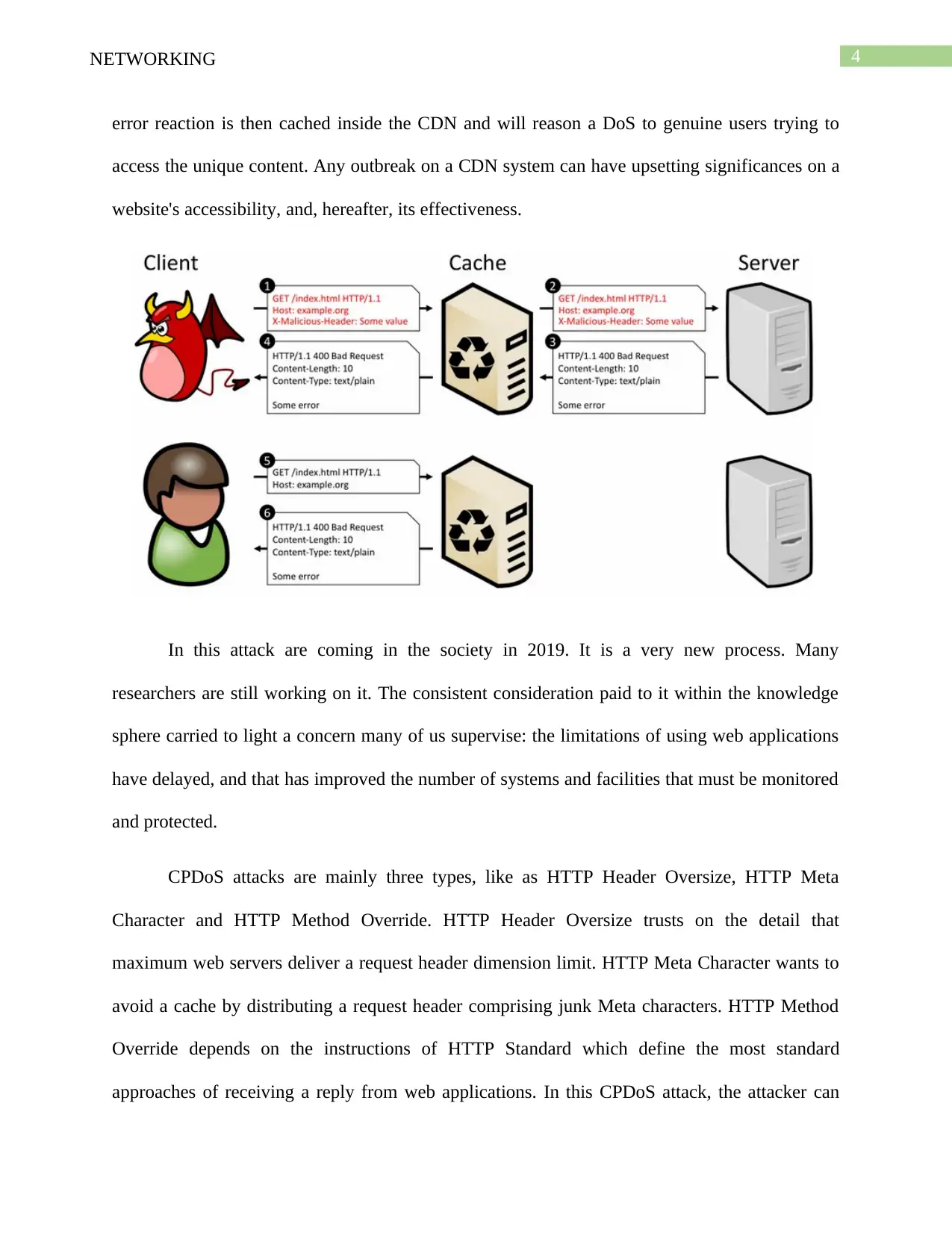
CPDoS:-
It is an innovative class of web cache locating attacks. It works by making a distorted
HTTP request that permits over a CDN to make a fault response from the target's server. The
CDN. When the edge server accepts the answer from the source server, it keeps the content in
the cache based on the HTTP headers of the reply. This network follow some steps like that-
An operator requests content from a network application.
The appeal for the content is interrupted by the CDN and transmitted to the neighbouring
PoP.
Suppose these has the content in its cache, the CDN supplies the content. These are
named a cache HIT. If the content is not cached, the appeal if promoted to the source
server, these are called a cache MISS.
In the occasion of a cache HIT, the CDN makes a response with the demanded content.
The response is established by the network application and the content loads much faster
than it would if the source server brought it.
Example:-
Many CDN suppliers also deliver auto-optimization structures that resize images
spontaneously and keeps them for when they are wanted in the upcoming. For instance, any user
website creates use of header pictures that’s 3MB, and a user needs for user content on a 450px-
widescreen (Medagliani et al. 2017). A CDN can directly repeat the user content and display one
that’s 450PX-wide and 30KB-large. Unnecessary to say, CDNs also acted best for supportive
user mobile visitors. CDNs also can regulate spammers, distrustful IP addresses, and also several
classes of crawlers and the actions they expect to do.
CPDoS:-
It is an innovative class of web cache locating attacks. It works by making a distorted
HTTP request that permits over a CDN to make a fault response from the target's server. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORKING
error reaction is then cached inside the CDN and will reason a DoS to genuine users trying to
access the unique content. Any outbreak on a CDN system can have upsetting significances on a
website's accessibility, and, hereafter, its effectiveness.
In this attack are coming in the society in 2019. It is a very new process. Many
researchers are still working on it. The consistent consideration paid to it within the knowledge
sphere carried to light a concern many of us supervise: the limitations of using web applications
have delayed, and that has improved the number of systems and facilities that must be monitored
and protected.
CPDoS attacks are mainly three types, like as HTTP Header Oversize, HTTP Meta
Character and HTTP Method Override. HTTP Header Oversize trusts on the detail that
maximum web servers deliver a request header dimension limit. HTTP Meta Character wants to
avoid a cache by distributing a request header comprising junk Meta characters. HTTP Method
Override depends on the instructions of HTTP Standard which define the most standard
approaches of receiving a reply from web applications. In this CPDoS attack, the attacker can
error reaction is then cached inside the CDN and will reason a DoS to genuine users trying to
access the unique content. Any outbreak on a CDN system can have upsetting significances on a
website's accessibility, and, hereafter, its effectiveness.
In this attack are coming in the society in 2019. It is a very new process. Many
researchers are still working on it. The consistent consideration paid to it within the knowledge
sphere carried to light a concern many of us supervise: the limitations of using web applications
have delayed, and that has improved the number of systems and facilities that must be monitored
and protected.
CPDoS attacks are mainly three types, like as HTTP Header Oversize, HTTP Meta
Character and HTTP Method Override. HTTP Header Oversize trusts on the detail that
maximum web servers deliver a request header dimension limit. HTTP Meta Character wants to
avoid a cache by distributing a request header comprising junk Meta characters. HTTP Method
Override depends on the instructions of HTTP Standard which define the most standard
approaches of receiving a reply from web applications. In this CPDoS attack, the attacker can

5NETWORKING
start the attack by transferring an HTTP invitation with a malevolent header directing an exact
victim domain. The demand will get treated by transitional cache and remains invisible.
Solution:-
One of the principal motives for CPDoS attacks stands in the detail that a susceptible
cache illegally stores responses comprising error codes like as "400 Bad Request” by default. It
is not permissible conferring to the HTTP structure. The web caching structure only permits to
cache the fault codes “404 Not Found”, “405 Method Not Allowed”, “410 Gone” and “501 Not
Implemented”. Henceforth, caching mistake pages according to the guidelines of the HTTP
structure is the initial step to evade CPDoS outbreaks. Content suppliers must also apply the
suitable status code for the consistent error situation.
For example, “400 Bad Request” which is implemented by several HTTP executions for
stating a large header is not the appropriate standing code (Nguyen, Lacono and Federrath 2019).
IIS even performs “404 Not Found” when an exact header is surpassed. The correct error code
for an oversize request header is “431 Request Header” Fields Too Big. According to modern
research study, this error statement is not caching by any web caching structures.
Another active countermeasure beside CPDoS attacks is to reject error contacts from
caching. One method is to improve the header Cache-Control: no keep to every error page. The
other choice is to immobilize error page caching in the cache formation. CDNs like Cloud Front
or Akamai deliver configuration surroundings to do so (Brown and Willink 2018). A Web
Application Firewalls can also be positioned to moderate CPDoS outbreaks. Though, WAFs
must be placed in front of the cache to block hateful content before they touch the source server.
WAFs that are locating in forward-facing of the source server can be misused to provoke faulty
pages that develop cached either.
start the attack by transferring an HTTP invitation with a malevolent header directing an exact
victim domain. The demand will get treated by transitional cache and remains invisible.
Solution:-
One of the principal motives for CPDoS attacks stands in the detail that a susceptible
cache illegally stores responses comprising error codes like as "400 Bad Request” by default. It
is not permissible conferring to the HTTP structure. The web caching structure only permits to
cache the fault codes “404 Not Found”, “405 Method Not Allowed”, “410 Gone” and “501 Not
Implemented”. Henceforth, caching mistake pages according to the guidelines of the HTTP
structure is the initial step to evade CPDoS outbreaks. Content suppliers must also apply the
suitable status code for the consistent error situation.
For example, “400 Bad Request” which is implemented by several HTTP executions for
stating a large header is not the appropriate standing code (Nguyen, Lacono and Federrath 2019).
IIS even performs “404 Not Found” when an exact header is surpassed. The correct error code
for an oversize request header is “431 Request Header” Fields Too Big. According to modern
research study, this error statement is not caching by any web caching structures.
Another active countermeasure beside CPDoS attacks is to reject error contacts from
caching. One method is to improve the header Cache-Control: no keep to every error page. The
other choice is to immobilize error page caching in the cache formation. CDNs like Cloud Front
or Akamai deliver configuration surroundings to do so (Brown and Willink 2018). A Web
Application Firewalls can also be positioned to moderate CPDoS outbreaks. Though, WAFs
must be placed in front of the cache to block hateful content before they touch the source server.
WAFs that are locating in forward-facing of the source server can be misused to provoke faulty
pages that develop cached either.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORKING
The DNS server must be sustaining to confirm that it is perfect of any facilities that aren't
desired. Extraneous facilities running on the DNS server only deliver hackers with more possible
attack vectors. There are also cache poisoning apparatuses available to support business avoid
cache poisoning occurrences. The most comprehensive cache poisoning anticipation tool is
perhaps DNSSEC. These are a cache poisoning instrument settled by the Internet Manufacturing
Task Force that delivers protected DNS data verification.
Scholars advise webmasters not to overlook the issue. According to their examinations
(DiBenedetto and Papadopoulos 2016), 35% of the Alexa Top 750 websites, 15% of the
Subdivision of Defense domains, and 19% of the URLs from a 397 million URL sample got
from a Google Big Query documentation were possibly exposed to CPDoS attacks.
Impact:-
Many scholars distinguished that the CDNs work across huge physical sites and the error
page created by a CPDoS attack can help extent numerous cache server positions. Though the
researcher described that this danger suffers not all advantage servers, and some customers will
still accept the dynamic pages from the source server.
Web caching instrument permits reusing HTTP replies to decrease the number of
requirements that extent the source server, the size of network traffic ensuing from resource
requirements, and the inexpression of resource contact (Kumar 2014). The web server, though,
blocks this appeal and revenues an error page, as the appeal header surpasses its header size
limit. The cache now keeps this fault page with position code 350-400 Corrupt Request. All
successive requests directing the deniable resource are soon delivering with an error page in its
place of the authentic content. Researchers prepared some tests consuming the Turbo Bytes
Pulse and the rapidity testing instrument of Key CDN.
The DNS server must be sustaining to confirm that it is perfect of any facilities that aren't
desired. Extraneous facilities running on the DNS server only deliver hackers with more possible
attack vectors. There are also cache poisoning apparatuses available to support business avoid
cache poisoning occurrences. The most comprehensive cache poisoning anticipation tool is
perhaps DNSSEC. These are a cache poisoning instrument settled by the Internet Manufacturing
Task Force that delivers protected DNS data verification.
Scholars advise webmasters not to overlook the issue. According to their examinations
(DiBenedetto and Papadopoulos 2016), 35% of the Alexa Top 750 websites, 15% of the
Subdivision of Defense domains, and 19% of the URLs from a 397 million URL sample got
from a Google Big Query documentation were possibly exposed to CPDoS attacks.
Impact:-
Many scholars distinguished that the CDNs work across huge physical sites and the error
page created by a CPDoS attack can help extent numerous cache server positions. Though the
researcher described that this danger suffers not all advantage servers, and some customers will
still accept the dynamic pages from the source server.
Web caching instrument permits reusing HTTP replies to decrease the number of
requirements that extent the source server, the size of network traffic ensuing from resource
requirements, and the inexpression of resource contact (Kumar 2014). The web server, though,
blocks this appeal and revenues an error page, as the appeal header surpasses its header size
limit. The cache now keeps this fault page with position code 350-400 Corrupt Request. All
successive requests directing the deniable resource are soon delivering with an error page in its
place of the authentic content. Researchers prepared some tests consuming the Turbo Bytes
Pulse and the rapidity testing instrument of Key CDN.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING
Effectiveness and importance:-
This computer network (CDN) are very much essential for frequent users. This network
contributes to the production globalization and capital marketplaces by decreasing the cost of
evidence and message. These skills have made it easier for transnationals and other businesses to
spread production services all over the universe, to co-ordinate intercontinental marketing
movements, and to ease teamwork in projects enchanting place in different regions. CDN also
proposes an excellent chance to rapidly share user content to an extensive spectator in just a few
instants (Meghana, Subashri and Vimal 2017). A CDN permits a user to cache their website
content to provide it from a control server to the user quicker. It has become so vital that
businesses can increase or fall due to their consequences in their situation on search engines.
Nowadays, businesses are progressively moving online to showcase their contributions to
a broader audience and encourage their industries. Industry research displays that the number of
sales, the number of clients reached, commercial visibility reached and brand consciousness
metrics of business are openly connected to the depth of content on the business’s website.
CDNs also proposes some profits. The user can collect their images on the CDN and bring these
graphics openly from the PoPs. Images naturally take an extended time to load, and a user can
improve their website’s speed by keeping the picture descriptions on a CDN.
Conclusion:-
In this report, the writer develops the idea of CDN and CPDoS attack. This attack is very
much new, and human being tries to solve these difficulties in a different effective way. In this
report also develops some idea of these attacks and possible mitigation explanation. If the user
follows this strategy, then they easily avoid this problem effectively.
Effectiveness and importance:-
This computer network (CDN) are very much essential for frequent users. This network
contributes to the production globalization and capital marketplaces by decreasing the cost of
evidence and message. These skills have made it easier for transnationals and other businesses to
spread production services all over the universe, to co-ordinate intercontinental marketing
movements, and to ease teamwork in projects enchanting place in different regions. CDN also
proposes an excellent chance to rapidly share user content to an extensive spectator in just a few
instants (Meghana, Subashri and Vimal 2017). A CDN permits a user to cache their website
content to provide it from a control server to the user quicker. It has become so vital that
businesses can increase or fall due to their consequences in their situation on search engines.
Nowadays, businesses are progressively moving online to showcase their contributions to
a broader audience and encourage their industries. Industry research displays that the number of
sales, the number of clients reached, commercial visibility reached and brand consciousness
metrics of business are openly connected to the depth of content on the business’s website.
CDNs also proposes some profits. The user can collect their images on the CDN and bring these
graphics openly from the PoPs. Images naturally take an extended time to load, and a user can
improve their website’s speed by keeping the picture descriptions on a CDN.
Conclusion:-
In this report, the writer develops the idea of CDN and CPDoS attack. This attack is very
much new, and human being tries to solve these difficulties in a different effective way. In this
report also develops some idea of these attacks and possible mitigation explanation. If the user
follows this strategy, then they easily avoid this problem effectively.

8NETWORKING
References:-
Brown, J.D. and Willink, T.J., 2018. ARP cache poisoning and routing loops in ad hoc networks.
Mobile Networks and Applications, 23(5), pp.1306-1317.
DiBenedetto, S. and Papadopoulos, C., 2016, April. Mitigating poisoned content with forwarding
strategy. In 2016 IEEE Conference on Computer Communications Workshops (INFOCOM
WKSHPS) (pp. 164-169). IEEE.
Herbaut, N., Négru, D., Chen, Y., Frangoudis, P.A. and Ksentini, A., 2016, December. Content
delivery networks as a virtual network function: a win-win isp-cdn collaboration. In 2016 IEEE
Global Communications Conference (GLOBECOM) (pp. 1-6). IEEE.
Ibn-Khedher, H., Abd-Elrahman, E., Kamal, A.E. and Afifi, H., 2017. OPAC: An optimal
placement algorithm for virtual CDN. computer Networks, 120, pp.12-27.
Kumar, G., 2014. Understanding denial of service (DoS) attacks using OSI reference model.
International Journal of Education and Science Research, 1(5).
Medagliani, P., Paris, S., Leguay, J., Maggi, L., Xue, C. and Zhou, H., 2017, May. Overlay
routing for fast video transfers in CDN. In 2017 IFIP/IEEE Symposium on Integrated Network
and Service Management (IM) (pp. 531-536). IEEE.
Meghana, J.S., Subashri, T. and Vimal, K.R., 2017, March. A survey on ARP cache poisoning
and techniques for detection and mitigation. In 2017 Fourth International Conference on Signal
Processing, Communication and Networking (ICSCN) (pp. 1-6). IEEE.
Mu, R. and Zhao, F., 2015. CDN and P2P network model based on HCDN Technology. Journal
of Software Engineering, 9(3), pp.469-486.
References:-
Brown, J.D. and Willink, T.J., 2018. ARP cache poisoning and routing loops in ad hoc networks.
Mobile Networks and Applications, 23(5), pp.1306-1317.
DiBenedetto, S. and Papadopoulos, C., 2016, April. Mitigating poisoned content with forwarding
strategy. In 2016 IEEE Conference on Computer Communications Workshops (INFOCOM
WKSHPS) (pp. 164-169). IEEE.
Herbaut, N., Négru, D., Chen, Y., Frangoudis, P.A. and Ksentini, A., 2016, December. Content
delivery networks as a virtual network function: a win-win isp-cdn collaboration. In 2016 IEEE
Global Communications Conference (GLOBECOM) (pp. 1-6). IEEE.
Ibn-Khedher, H., Abd-Elrahman, E., Kamal, A.E. and Afifi, H., 2017. OPAC: An optimal
placement algorithm for virtual CDN. computer Networks, 120, pp.12-27.
Kumar, G., 2014. Understanding denial of service (DoS) attacks using OSI reference model.
International Journal of Education and Science Research, 1(5).
Medagliani, P., Paris, S., Leguay, J., Maggi, L., Xue, C. and Zhou, H., 2017, May. Overlay
routing for fast video transfers in CDN. In 2017 IFIP/IEEE Symposium on Integrated Network
and Service Management (IM) (pp. 531-536). IEEE.
Meghana, J.S., Subashri, T. and Vimal, K.R., 2017, March. A survey on ARP cache poisoning
and techniques for detection and mitigation. In 2017 Fourth International Conference on Signal
Processing, Communication and Networking (ICSCN) (pp. 1-6). IEEE.
Mu, R. and Zhao, F., 2015. CDN and P2P network model based on HCDN Technology. Journal
of Software Engineering, 9(3), pp.469-486.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORKING
Nguyen, H.V., Iacono, L.L. and Federrath, H., 2019, November. Your Cache Has Fallen: Cache-
Poisoned Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on
Computer and Communications Security (pp. 1915-1936).
Zhang, G., Liu, W., Hei, X. and Cheng, W., 2014. Unreeling Xunlei Kankan: Understanding
hybrid CDN-P2P video-on-demand streaming. IEEE Transactions on Multimedia, 17(2), pp.229-
242.
Nguyen, H.V., Iacono, L.L. and Federrath, H., 2019, November. Your Cache Has Fallen: Cache-
Poisoned Denial-of-Service Attack. In Proceedings of the 2019 ACM SIGSAC Conference on
Computer and Communications Security (pp. 1915-1936).
Zhang, G., Liu, W., Hei, X. and Cheng, W., 2014. Unreeling Xunlei Kankan: Understanding
hybrid CDN-P2P video-on-demand streaming. IEEE Transactions on Multimedia, 17(2), pp.229-
242.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





