Networking and Communication Assignment - Management IT, Fall 2019
VerifiedAdded on 2022/10/31
|7
|1522
|154
Homework Assignment
AI Summary
This document presents a comprehensive solution to a Management IT assignment focused on networking and communication. The assignment addresses key concepts including the OSI model and the TCP/IP protocol suite, outlining their layers and correlations. It explores network and user support layers within the TCP/IP model, and explains data encapsulation. The solution details the responsibilities of the Data Link, Network, and Transport layers, and clarifies the differences between network and transport layer delivery. The document also discusses the necessity of error detection mechanisms at the transport layer, the distinctions between logical, physical, and port addresses, and the services provided by the Application layer. Finally, it examines the advantages of combining the Session, Presentation, and Application layers in the TCP/IP model. The solution is well-structured and includes relevant references to support the answers.

Running Head: NETWORKING
0
Networking
IT NETWORKING AND COMMUNICATION
(Student Details: )
9/20/2019
0
Networking
IT NETWORKING AND COMMUNICATION
(Student Details: )
9/20/2019
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Management
1
Answer 1
There are 7, 4 layers in the OSI model and TCI/IP protocol suite i.e. the internet model. The
seven layers of OSI model are as follows:
Physical layer
Data link layer
Network layer
Transport layer
Session layer
Presentation layer
Application layer
On the other hand, 4 layers of the TCP/IP model are:
Network access which is known as Ethernet
IP protocol layer
Transport layer
Application layer (Goralski, 2017).
Answer 2
The layers of the OSI model are the part of theoretical framework, whereas TCP/IP protocol
suite which is often known as internet model is a practical framework that uses different
protocols for connectivity of several work-stations (Goralski, 2017).
1
Answer 1
There are 7, 4 layers in the OSI model and TCI/IP protocol suite i.e. the internet model. The
seven layers of OSI model are as follows:
Physical layer
Data link layer
Network layer
Transport layer
Session layer
Presentation layer
Application layer
On the other hand, 4 layers of the TCP/IP model are:
Network access which is known as Ethernet
IP protocol layer
Transport layer
Application layer (Goralski, 2017).
Answer 2
The layers of the OSI model are the part of theoretical framework, whereas TCP/IP protocol
suite which is often known as internet model is a practical framework that uses different
protocols for connectivity of several work-stations (Goralski, 2017).

Management
2
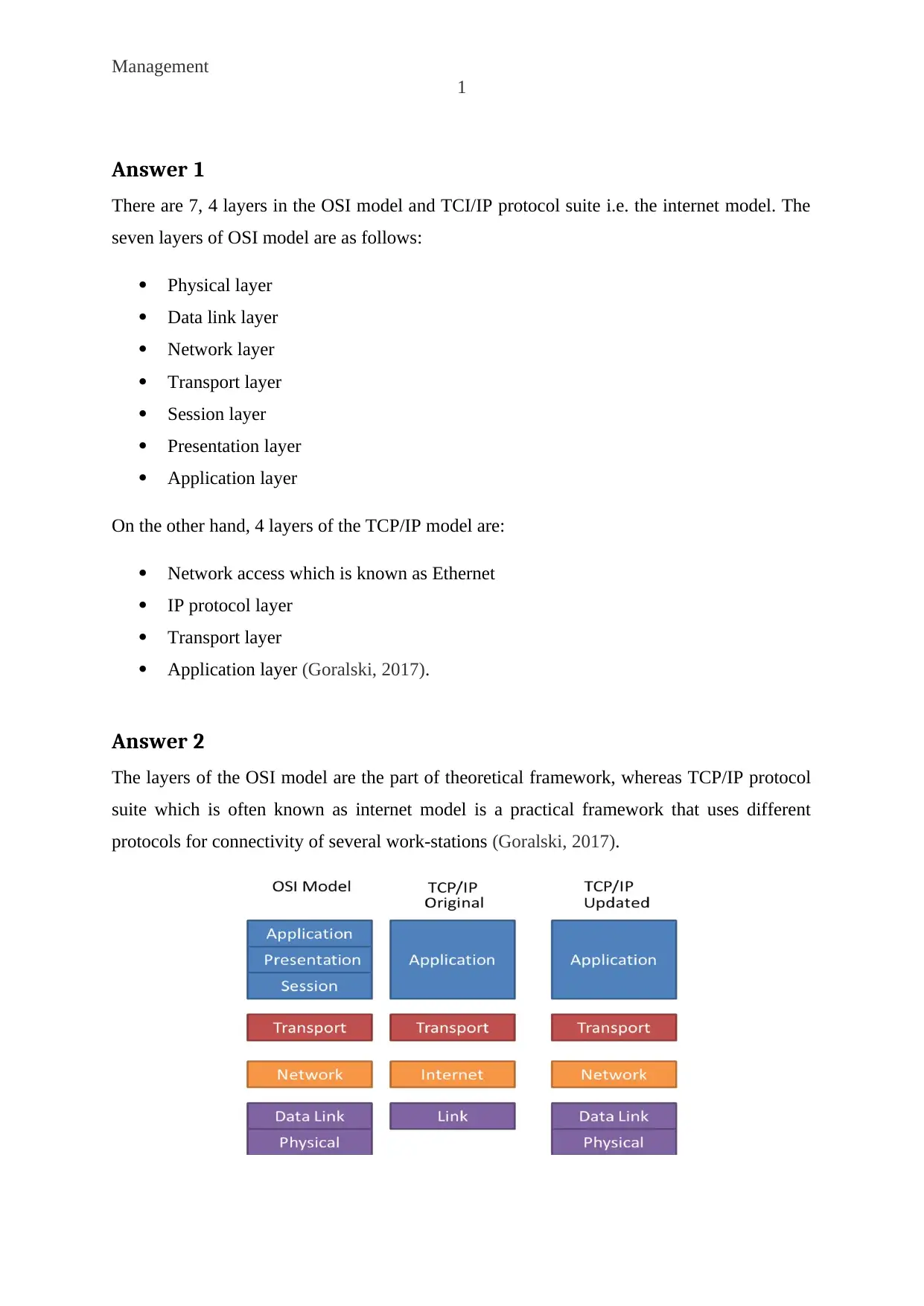
In this context, as mentioned in the above figure the three layers of OSI model include
presentation, application, and session forms the application protocol of the TCP/IP model.
Besides, transport layer of OSI model acts as the transport protocol of TCP/IP. The network
layer of the OSI model works as the internet protocol in TCP/IP model. Lastly, the two layers
of OSI model combine as a link protocol in TCP/IP protocol suite (Goralski, 2017).
Answer 3
In the context of the TCP/IP model, both the internet layer and link layers are network
support layers while application layer of the TCP/IP protocol suite is the user support layer.
The application layer is the user support layer because it allows interoperability among
unrelated software systems. In addition to that, network support layer deals with electrical
specifications, transport timing, physical connection, as well as reliability factor of system
(Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 4
The data encapsulation is often termed as data hiding. Data hiding is the process where the
application details of any class are typically kept encrypted from the users. In this context,
users can only perform a defined set of operations. In the context of TCP/IP model and OSI
model, whenever a protocol from the sending end adds data into the packet header, then this
whole procedure is recognized as data encapsulation. It has been found that every layer is
having a distinct term for the reformed packet (Tiwana & Konsynski, 2010).
Answer 5
The data-link layer is highly responsible for media access control, logical link control,
hardware addressing, as well as error detection while handling and defining
physical layer standards largely. It has been found that the data link layer offers
reliable transfer of data with transmitting packets. The data link layer usually performed all of
the above-mentioned tasks with the required synchronization, flow control as well as error
control. Apart from this, some major responsibilities of data-link layer are:
Framing
Flow and error control
Physical addressing
2
In this context, as mentioned in the above figure the three layers of OSI model include
presentation, application, and session forms the application protocol of the TCP/IP model.
Besides, transport layer of OSI model acts as the transport protocol of TCP/IP. The network
layer of the OSI model works as the internet protocol in TCP/IP model. Lastly, the two layers
of OSI model combine as a link protocol in TCP/IP protocol suite (Goralski, 2017).
Answer 3
In the context of the TCP/IP model, both the internet layer and link layers are network
support layers while application layer of the TCP/IP protocol suite is the user support layer.
The application layer is the user support layer because it allows interoperability among
unrelated software systems. In addition to that, network support layer deals with electrical
specifications, transport timing, physical connection, as well as reliability factor of system
(Stallings, Brown, Bauer, & Bhattacharjee, 2012).
Answer 4
The data encapsulation is often termed as data hiding. Data hiding is the process where the
application details of any class are typically kept encrypted from the users. In this context,
users can only perform a defined set of operations. In the context of TCP/IP model and OSI
model, whenever a protocol from the sending end adds data into the packet header, then this
whole procedure is recognized as data encapsulation. It has been found that every layer is
having a distinct term for the reformed packet (Tiwana & Konsynski, 2010).
Answer 5
The data-link layer is highly responsible for media access control, logical link control,
hardware addressing, as well as error detection while handling and defining
physical layer standards largely. It has been found that the data link layer offers
reliable transfer of data with transmitting packets. The data link layer usually performed all of
the above-mentioned tasks with the required synchronization, flow control as well as error
control. Apart from this, some major responsibilities of data-link layer are:
Framing
Flow and error control
Physical addressing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Management
3
Access control (Vacca, 2012).
Answer 6
It has been found that the transport layer is generally responsible for the process-to-
process delivery of the message. On the other hand, the network layer supervises host-to-
host delivery of single packets. In this context, it can be said that multi-level bed distribution
logically communicates amid vacation spot to origin. Moreover, transport layer delivery is
responsible for source to destination delivery. Besides, the layers offer strong connection
services, while covering network layer error control as well as flow control along with packet
sequence control (Datta, Bonnet, & Nikaein, 2012).
Answer 7
When the data link layer can easily detect errors among different hops, we also need another
mechanism at the transport layer because this layer helps to gather chunks of data. The data is
received from many sockets and the transport layer encapsulates them with its transport
headers (Vacca, 2012). Here, the transport layer mechanism is needed because it performs
multiplexing and de-multiplexing which is responsible for passing such resulting error
segments to the network layer of the TCP/IP protocol suite. Moreover, the transport layer also
provides the reverse process that is transferring data to the particular socket which is known
as de-multiplexing (Tiwana & Konsynski, 2010).
Answer 8
The major accountabilities of the network layer are segmented into two key parts include
routing and logical addressing. In the context of logical addressing, responsibilities of the
network layer can be:
The network layer usually adds a header towards the packet which is approaching from an
upper layer known as the transport layer. The network layer contains the logical addresses of
the receiver as well as sender.
On the other hand, in case of routing whenever an independent network or link is connected
with each other for creating an internetwork, the linked devices route the packets towards
3
Access control (Vacca, 2012).
Answer 6
It has been found that the transport layer is generally responsible for the process-to-
process delivery of the message. On the other hand, the network layer supervises host-to-
host delivery of single packets. In this context, it can be said that multi-level bed distribution
logically communicates amid vacation spot to origin. Moreover, transport layer delivery is
responsible for source to destination delivery. Besides, the layers offer strong connection
services, while covering network layer error control as well as flow control along with packet
sequence control (Datta, Bonnet, & Nikaein, 2012).
Answer 7
When the data link layer can easily detect errors among different hops, we also need another
mechanism at the transport layer because this layer helps to gather chunks of data. The data is
received from many sockets and the transport layer encapsulates them with its transport
headers (Vacca, 2012). Here, the transport layer mechanism is needed because it performs
multiplexing and de-multiplexing which is responsible for passing such resulting error
segments to the network layer of the TCP/IP protocol suite. Moreover, the transport layer also
provides the reverse process that is transferring data to the particular socket which is known
as de-multiplexing (Tiwana & Konsynski, 2010).
Answer 8
The major accountabilities of the network layer are segmented into two key parts include
routing and logical addressing. In the context of logical addressing, responsibilities of the
network layer can be:
The network layer usually adds a header towards the packet which is approaching from an
upper layer known as the transport layer. The network layer contains the logical addresses of
the receiver as well as sender.
On the other hand, in case of routing whenever an independent network or link is connected
with each other for creating an internetwork, the linked devices route the packets towards
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Management
4
their final position with the help of network layer addresses present in every packet
(Gollmann, 2010).
Answer 9
The responsibilities of the transport layer can be explained as follows:
The layer usually creates a process-to-process communication with the help of port
numbers (Goralski, 2017).
The layer offers a flow-and-error controlling mechanism at the level of the transport
layer
The transport layer provides a linking mechanism for the distinct processes like
sending data streams to the transport layer effectively
The layer is responsible for building the connection, breaking the whole data stream
into transportable units while numbering them as well as sending them one-by-one
(Comer, 2018).
Answer 10
There are some basic differences amid logical, physical and port addresses. The differences
can be seen as follows:
Logical Address
This is an IP address of the
entire system which is a
combination of Host ID and
Net ID. Such an address is
utilised by the network layer
for identifying a specific
network from the rest
networks (Vacca, 2012).
Physical Address
This address of NIC is also
called as mac address. The
address is specified with the
manufacturer's firm of the
chosen card. Besides, the
physical address is typically
utilised by the data link layer.
Port Address
The different applications
which are running on a
computer usually run with a
port number that is known as
port address. In this context,
the port address for different
apps is usually decided with
the Kernel of the operating
system.
4
their final position with the help of network layer addresses present in every packet
(Gollmann, 2010).
Answer 9
The responsibilities of the transport layer can be explained as follows:
The layer usually creates a process-to-process communication with the help of port
numbers (Goralski, 2017).
The layer offers a flow-and-error controlling mechanism at the level of the transport
layer
The transport layer provides a linking mechanism for the distinct processes like
sending data streams to the transport layer effectively
The layer is responsible for building the connection, breaking the whole data stream
into transportable units while numbering them as well as sending them one-by-one
(Comer, 2018).
Answer 10
There are some basic differences amid logical, physical and port addresses. The differences
can be seen as follows:
Logical Address
This is an IP address of the
entire system which is a
combination of Host ID and
Net ID. Such an address is
utilised by the network layer
for identifying a specific
network from the rest
networks (Vacca, 2012).
Physical Address
This address of NIC is also
called as mac address. The
address is specified with the
manufacturer's firm of the
chosen card. Besides, the
physical address is typically
utilised by the data link layer.
Port Address
The different applications
which are running on a
computer usually run with a
port number that is known as
port address. In this context,
the port address for different
apps is usually decided with
the Kernel of the operating
system.

Management
5
Answer 11
There are specific services offered by the application layer within the internet model as
follows:
File transfer
Email services
Remote access (Dillon, Wu, & Chang, 2010).
Shared database management
Answer 12
It has been found that the primary advantage of combining session, presentation and
application layers into a single layer in TCP/IP model is less queuing. Combining process
offers additional latency, as well as uses more memory. In addition to that, when three layers
are combined in single layer then the data exchange between every layer is controlled with
the application layer which ultimately makes it easier to tune (Stallings, Brown, Bauer, &
Bhattacharjee, 2012). However, less reusability and harder to maintain will be counted as
disadvantages of the combining process.
5
Answer 11
There are specific services offered by the application layer within the internet model as
follows:
File transfer
Email services
Remote access (Dillon, Wu, & Chang, 2010).
Shared database management
Answer 12
It has been found that the primary advantage of combining session, presentation and
application layers into a single layer in TCP/IP model is less queuing. Combining process
offers additional latency, as well as uses more memory. In addition to that, when three layers
are combined in single layer then the data exchange between every layer is controlled with
the application layer which ultimately makes it easier to tune (Stallings, Brown, Bauer, &
Bhattacharjee, 2012). However, less reusability and harder to maintain will be counted as
disadvantages of the combining process.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Management
6
References
Comer, D. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. New York: Chapman and Hall/CRC.
Datta, S., Bonnet, C., & Nikaein, N. (2012). Android power management: Current and future
trends. Enabling Technologies for Smartphone and Internet of Things, 1, 48-53.
Dillon, T., Wu, C., & Chang, E. (2010). Cloud computing: issues and challenges. Advanced
Information Networking and Applications (AINA), 2010 24th IEEE International
Conference, IEEE, 27-33.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network.
London: Morgan Kaufmann.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
6
References
Comer, D. (2018). The Internet book: everything you need to know about computer
networking and how the Internet works. New York: Chapman and Hall/CRC.
Datta, S., Bonnet, C., & Nikaein, N. (2012). Android power management: Current and future
trends. Enabling Technologies for Smartphone and Internet of Things, 1, 48-53.
Dillon, T., Wu, C., & Chang, E. (2010). Cloud computing: issues and challenges. Advanced
Information Networking and Applications (AINA), 2010 24th IEEE International
Conference, IEEE, 27-33.
Gollmann, D. (2010). Computer Security. Wiley Interdisciplinary Reviews: Computational
Statistics, 2(5), 544-554.
Goralski, W. (2017). The illustrated network: how TCP/IP works in a modern network.
London: Morgan Kaufmann.
Stallings, W., Brown, L., Bauer, M., & Bhattacharjee, A. (2012). Computer security:
principles and practice. NJ: Pearson Education.
Tiwana, A., & Konsynski, B. (2010). Complementarities between organizational IT
architecture and governance structure. Information Systems Research, 21(2), 288-304.
Vacca, J. (2012). Computer and information security handbook. London: Newnes.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


