Networking Fundamentals 2: LAN and WAN Design for Arr Company
VerifiedAdded on 2020/05/16
|10
|2116
|316
Report
AI Summary
This report provides a detailed analysis of network design, focusing on Wide Area Network (WAN) and Local Area Network (LAN) implementations for Arr Company. It explores potential concerns related to network connections, including electromagnetic interference, redundancy, and security vulnerabilities. The report outlines the design of a LAN, discussing cabling plans (twisted pair, fiber optics) and network topologies (peer-to-peer, client-server, star topology). Floor plans for the company's head office are presented, detailing the layout of each floor and the placement of workstations and servers. The design incorporates VLANs for improved security and efficiency. The report concludes with a summary of the network solution, emphasizing the importance of security and efficient network management. The network is designed using Cisco Packet Tracer and floor plans are created in Microsoft Visio.

Running Head: NETWORKING FUNDAMENTALS
Networking Fundamentals
Name of the Student
Name of the University
Author’s Note
Networking Fundamentals
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKING FUNDAMENTALS
Table of Contents
1. Introduction................................................................................................................................2
2. Wide Area Network Design.........................................................................................................2
2.1. Potential Concerns related with the connections................................................................2
3. Local Area Network Design.........................................................................................................4
4. Discussion on the local area wiring.............................................................................................4
5. Discussion on the type of local area network topology..............................................................5
6. Floor Plan for the company’s head office...................................................................................6
6.1. Floor plan for the First floor:................................................................................................6
6.2. Floor plan for the Second floor:...........................................................................................7
6.3. Floor plan for the Third floor:..............................................................................................7
7. Conclusion..................................................................................................................................8
Bibliography....................................................................................................................................9
NETWORKING FUNDAMENTALS
Table of Contents
1. Introduction................................................................................................................................2
2. Wide Area Network Design.........................................................................................................2
2.1. Potential Concerns related with the connections................................................................2
3. Local Area Network Design.........................................................................................................4
4. Discussion on the local area wiring.............................................................................................4
5. Discussion on the type of local area network topology..............................................................5
6. Floor Plan for the company’s head office...................................................................................6
6.1. Floor plan for the First floor:................................................................................................6
6.2. Floor plan for the Second floor:...........................................................................................7
6.3. Floor plan for the Third floor:..............................................................................................7
7. Conclusion..................................................................................................................................8
Bibliography....................................................................................................................................9
2
NETWORKING FUNDAMENTALS
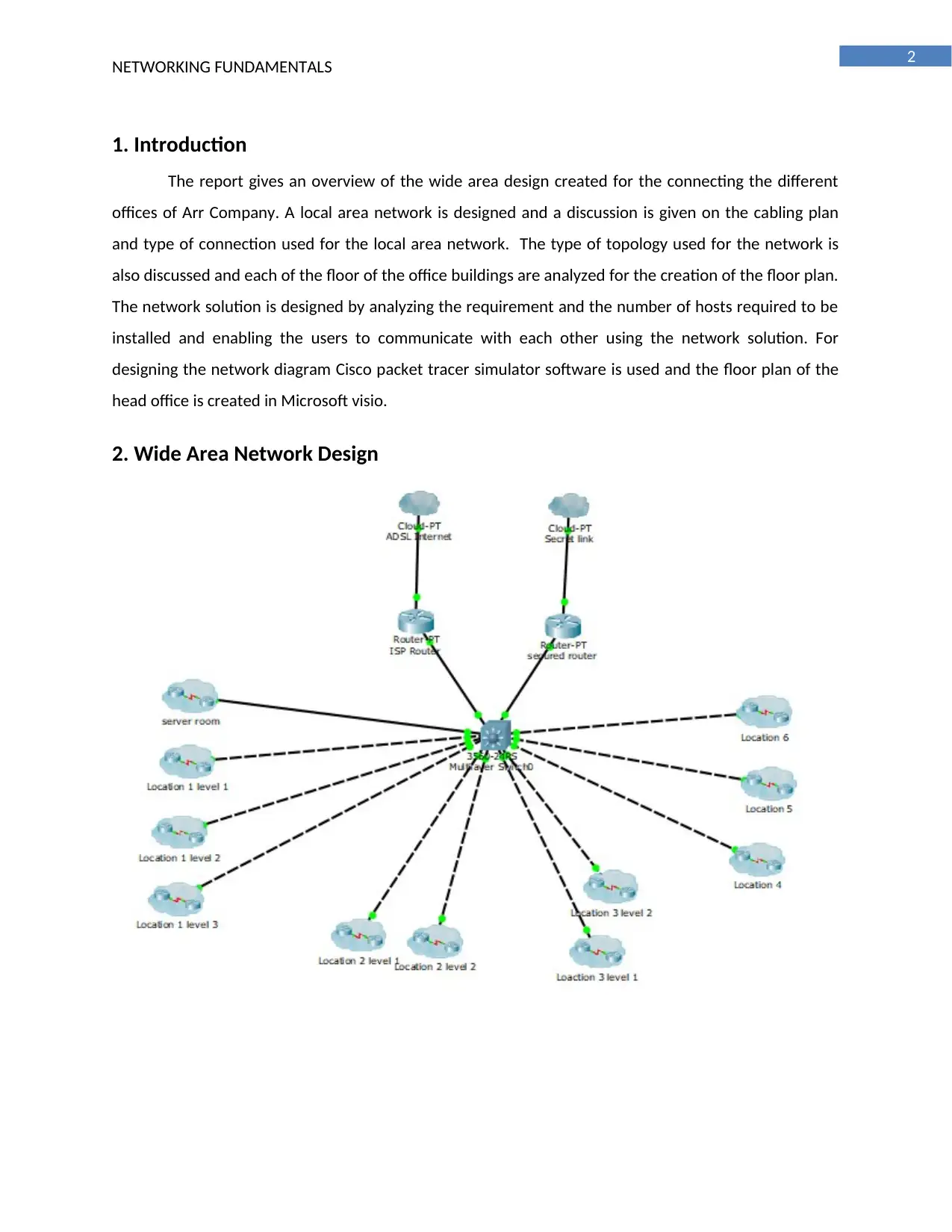
1. Introduction
The report gives an overview of the wide area design created for the connecting the different
offices of Arr Company. A local area network is designed and a discussion is given on the cabling plan
and type of connection used for the local area network. The type of topology used for the network is
also discussed and each of the floor of the office buildings are analyzed for the creation of the floor plan.
The network solution is designed by analyzing the requirement and the number of hosts required to be
installed and enabling the users to communicate with each other using the network solution. For
designing the network diagram Cisco packet tracer simulator software is used and the floor plan of the
head office is created in Microsoft visio.
2. Wide Area Network Design
NETWORKING FUNDAMENTALS
1. Introduction
The report gives an overview of the wide area design created for the connecting the different
offices of Arr Company. A local area network is designed and a discussion is given on the cabling plan
and type of connection used for the local area network. The type of topology used for the network is
also discussed and each of the floor of the office buildings are analyzed for the creation of the floor plan.
The network solution is designed by analyzing the requirement and the number of hosts required to be
installed and enabling the users to communicate with each other using the network solution. For
designing the network diagram Cisco packet tracer simulator software is used and the floor plan of the
head office is created in Microsoft visio.
2. Wide Area Network Design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKING FUNDAMENTALS
2.1. Potential Concerns related with the connections
There are different potential concerned that should be analyzed for increasing the efficiency of
the network design and reduce the response time of the proposed network solution. The installation of
the network device near the power lines, motors and other sources can cause electromagnetic
interferences and thus degrade the quality of the signals and cause error in the transmission. The
network should be designed with redundant links such that if a link is broken the secondary link can be
used for backup for transmitting the data packets in the network. There are many security related issues
that needs to be resolved for securing the network and restrict the access of the unauthorized users to
connect with the core components of the network. The network administrator may face difficulty while
management of the network resources distributed in different location of the network. There are other
potential concerns that can affect the network such as cost, administrative time and the failure of the
file server installed in the network. The network is designed to remove the complexity such that it can
save the effort of the technician to resolve any problem associated with the maintenance of the
network.
The connection between the offices should be secured and some encryption algorithm, must be
applied such that if it is accessed by any third party agents it would not be recovered and thus cannot
use for illegal activity. The wireless access point installed in the network should have proper protection
such that it cannot be access by unauthorized users. The servers connected in the network should be
configured to group the users and manage the printing jobs for better management of the users and the
network resources. A network monitoring tool should be used for the analysis of the flow of data
packets and protect the network from distributed denial of service attacks.
NETWORKING FUNDAMENTALS
2.1. Potential Concerns related with the connections
There are different potential concerned that should be analyzed for increasing the efficiency of
the network design and reduce the response time of the proposed network solution. The installation of
the network device near the power lines, motors and other sources can cause electromagnetic
interferences and thus degrade the quality of the signals and cause error in the transmission. The
network should be designed with redundant links such that if a link is broken the secondary link can be
used for backup for transmitting the data packets in the network. There are many security related issues
that needs to be resolved for securing the network and restrict the access of the unauthorized users to
connect with the core components of the network. The network administrator may face difficulty while
management of the network resources distributed in different location of the network. There are other
potential concerns that can affect the network such as cost, administrative time and the failure of the
file server installed in the network. The network is designed to remove the complexity such that it can
save the effort of the technician to resolve any problem associated with the maintenance of the
network.
The connection between the offices should be secured and some encryption algorithm, must be
applied such that if it is accessed by any third party agents it would not be recovered and thus cannot
use for illegal activity. The wireless access point installed in the network should have proper protection
such that it cannot be access by unauthorized users. The servers connected in the network should be
configured to group the users and manage the printing jobs for better management of the users and the
network resources. A network monitoring tool should be used for the analysis of the flow of data
packets and protect the network from distributed denial of service attacks.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORKING FUNDAMENTALS
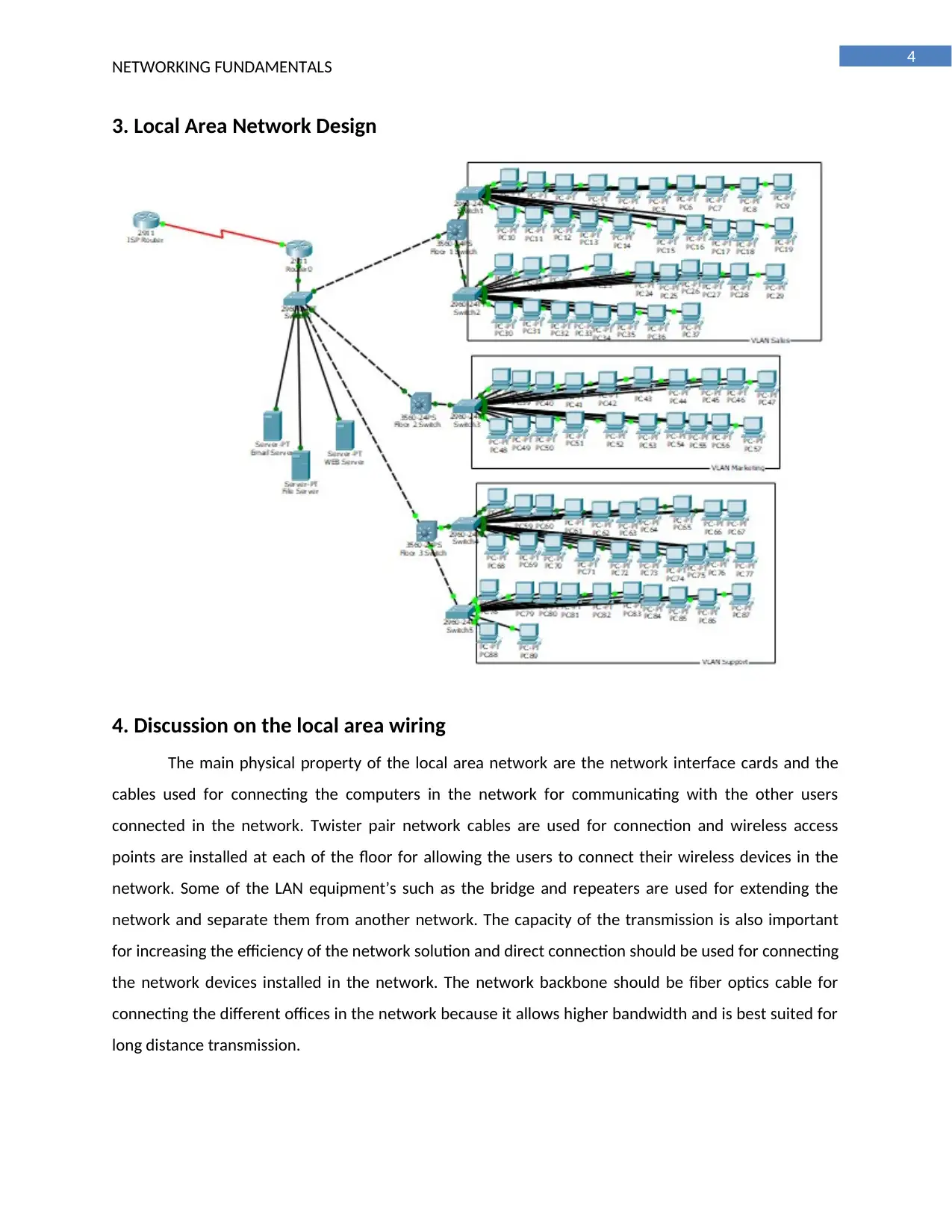
3. Local Area Network Design
4. Discussion on the local area wiring
The main physical property of the local area network are the network interface cards and the
cables used for connecting the computers in the network for communicating with the other users
connected in the network. Twister pair network cables are used for connection and wireless access
points are installed at each of the floor for allowing the users to connect their wireless devices in the
network. Some of the LAN equipment’s such as the bridge and repeaters are used for extending the
network and separate them from another network. The capacity of the transmission is also important
for increasing the efficiency of the network solution and direct connection should be used for connecting
the network devices installed in the network. The network backbone should be fiber optics cable for
connecting the different offices in the network because it allows higher bandwidth and is best suited for
long distance transmission.
NETWORKING FUNDAMENTALS
3. Local Area Network Design
4. Discussion on the local area wiring
The main physical property of the local area network are the network interface cards and the
cables used for connecting the computers in the network for communicating with the other users
connected in the network. Twister pair network cables are used for connection and wireless access
points are installed at each of the floor for allowing the users to connect their wireless devices in the
network. Some of the LAN equipment’s such as the bridge and repeaters are used for extending the
network and separate them from another network. The capacity of the transmission is also important
for increasing the efficiency of the network solution and direct connection should be used for connecting
the network devices installed in the network. The network backbone should be fiber optics cable for
connecting the different offices in the network because it allows higher bandwidth and is best suited for
long distance transmission.

5
NETWORKING FUNDAMENTALS
Different types of cables are used for interconnecting the routers, switches and the nodes
connected in the network. There are different types of cables such as unshielded twisted pair, shielded
twisted pair, multi-mode fiber and single mode fiber for local wiring. The interconnection between the
routers are done using the serial cables and cat 6a cables are used for connecting the layer 2 switch with
the router and for local distribution purpose the cat 6 cable is applied. The cat 6a cables operates in the
frequency of 500 Mhz and has the support for 1000 Mbps Ethernet and 10 Gbps Ethernet connections.
The cat 6 cable is used for reducing the cost of cabling because its price is less when compared with the
cat 6a cables.
5. Discussion on the type of local area network topology
Two types of network configuration are applied for designing the network solution for Arr
Company, such as peer to peer network and client server network. The peer to peer network is designed
for each of the departments that have less number of users and where security is not the main aspect.
Each of the users connected in the peer to peer network can share their files and documents easily
without any restriction acting on them. The client server network is used for the management of the
wide area network where a central server is installed in the network for storing the files in the server
and controlling the access of the other users. High level of security can be implemented and the server
should have high end configuration for supporting the virtualization and balancing the load of the
network. The local area network is designed following the star topology and a central router is used for
each of the department for connecting the nodes installed in different location of the office building.
The star topology is selected because different medium can be used for transmission of data packets in
the star topology. Separate cables are used for establishment of connection between the device and the
central switch and thus if a device fails it does not affects the performance of the network. A backup
plan should be available for the central device because it is the main element of the network, if it fails
the whole network would stop working.
Each of the department of the organization are connected using a separate VLAN configured on
the switch used for providing connection to the users. Since it is a large organization many data are
generated in the network and there is a risk of collision between the data packets in the network and
the data may get lost. Thus the creation of the VLAN would help to create separate channels for
transmission of the data packets in the network and increase the efficiency of the network.
NETWORKING FUNDAMENTALS
Different types of cables are used for interconnecting the routers, switches and the nodes
connected in the network. There are different types of cables such as unshielded twisted pair, shielded
twisted pair, multi-mode fiber and single mode fiber for local wiring. The interconnection between the
routers are done using the serial cables and cat 6a cables are used for connecting the layer 2 switch with
the router and for local distribution purpose the cat 6 cable is applied. The cat 6a cables operates in the
frequency of 500 Mhz and has the support for 1000 Mbps Ethernet and 10 Gbps Ethernet connections.
The cat 6 cable is used for reducing the cost of cabling because its price is less when compared with the
cat 6a cables.
5. Discussion on the type of local area network topology
Two types of network configuration are applied for designing the network solution for Arr
Company, such as peer to peer network and client server network. The peer to peer network is designed
for each of the departments that have less number of users and where security is not the main aspect.
Each of the users connected in the peer to peer network can share their files and documents easily
without any restriction acting on them. The client server network is used for the management of the
wide area network where a central server is installed in the network for storing the files in the server
and controlling the access of the other users. High level of security can be implemented and the server
should have high end configuration for supporting the virtualization and balancing the load of the
network. The local area network is designed following the star topology and a central router is used for
each of the department for connecting the nodes installed in different location of the office building.
The star topology is selected because different medium can be used for transmission of data packets in
the star topology. Separate cables are used for establishment of connection between the device and the
central switch and thus if a device fails it does not affects the performance of the network. A backup
plan should be available for the central device because it is the main element of the network, if it fails
the whole network would stop working.
Each of the department of the organization are connected using a separate VLAN configured on
the switch used for providing connection to the users. Since it is a large organization many data are
generated in the network and there is a risk of collision between the data packets in the network and
the data may get lost. Thus the creation of the VLAN would help to create separate channels for
transmission of the data packets in the network and increase the efficiency of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKING FUNDAMENTALS
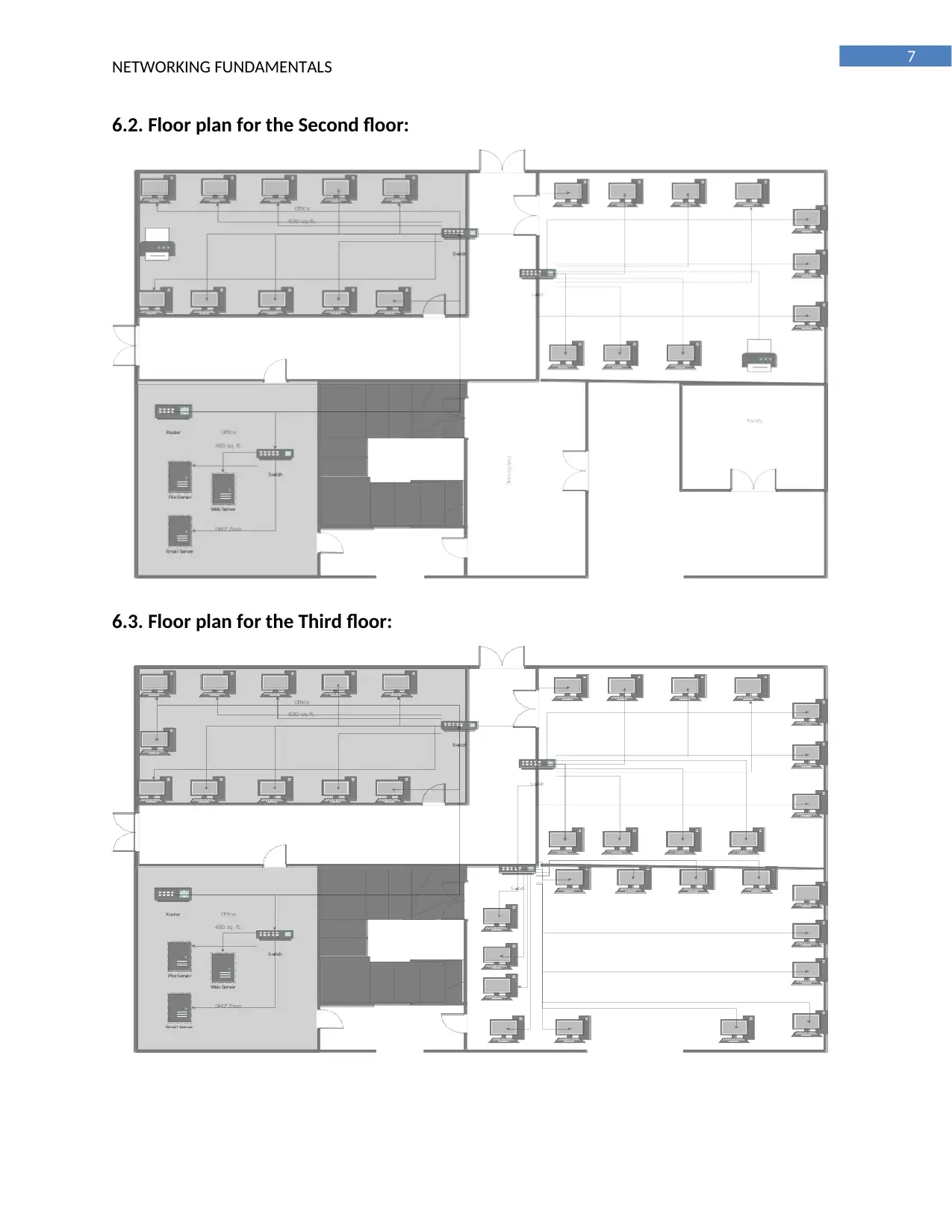
6. Floor Plan for the company’s head office
The office buildings of Arr Company is located in different location of the suburb and a wide area
network connection should be used for the connecting the offices. Local server are installed in each of
the building for serving the needs of the users. The head office of the company is located in Melbourne
CBD in the top three floor of a building for three departments namely: general support, sales and
marketing. The first floor needs a LAN for connecting the 32 workstations, the second floor needs LAN
for connecting the 20 workstations and the third floor needs the local area network for connecting the
38 workstations. Each of the LAN should be configured with IP address and subnetted for reducing the
wastage of the IP address. A central router should be installed in the network for connecting all the
three departments and configured with IP route for enabling communication with the other offices. A
layer 3 switch should be connected with the router for creation of VLAN and minimize the impact of the
potential problems identified for the development of the network solution. A same layout is followed for
each of the floor for the development of the network solution. The head office of the company should
be connected with a strong backbone and the network servers should be installed in the DMZ zone and
the physical access should be restricted.
6.1. Floor plan for the First floor:
NETWORKING FUNDAMENTALS
6. Floor Plan for the company’s head office
The office buildings of Arr Company is located in different location of the suburb and a wide area
network connection should be used for the connecting the offices. Local server are installed in each of
the building for serving the needs of the users. The head office of the company is located in Melbourne
CBD in the top three floor of a building for three departments namely: general support, sales and
marketing. The first floor needs a LAN for connecting the 32 workstations, the second floor needs LAN
for connecting the 20 workstations and the third floor needs the local area network for connecting the
38 workstations. Each of the LAN should be configured with IP address and subnetted for reducing the
wastage of the IP address. A central router should be installed in the network for connecting all the
three departments and configured with IP route for enabling communication with the other offices. A
layer 3 switch should be connected with the router for creation of VLAN and minimize the impact of the
potential problems identified for the development of the network solution. A same layout is followed for
each of the floor for the development of the network solution. The head office of the company should
be connected with a strong backbone and the network servers should be installed in the DMZ zone and
the physical access should be restricted.
6.1. Floor plan for the First floor:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
NETWORKING FUNDAMENTALS
6.2. Floor plan for the Second floor:
6.3. Floor plan for the Third floor:
NETWORKING FUNDAMENTALS
6.2. Floor plan for the Second floor:
6.3. Floor plan for the Third floor:

8
NETWORKING FUNDAMENTALS
7. Conclusion
From the above report it can be concluded that for the development of the network solution
and analysis is made on the structure of the building, floor plans and the number of workstations and
servers required for each of the department. For the preparation of the network solution a wide area
network and a local area network is designed. There are some potential concerns related with the
connection between each of the departments and they are also discussed in the report. The wide area
network is designed for connecting the different offices located in different location of the suburbs and
the local area network is designed for connecting each of the departments in the office. For designing
the wide area network for the company separate cluster is used different VLANs are allocated for each
of the cluster for increasing the security of the network.
NETWORKING FUNDAMENTALS
7. Conclusion
From the above report it can be concluded that for the development of the network solution
and analysis is made on the structure of the building, floor plans and the number of workstations and
servers required for each of the department. For the preparation of the network solution a wide area
network and a local area network is designed. There are some potential concerns related with the
connection between each of the departments and they are also discussed in the report. The wide area
network is designed for connecting the different offices located in different location of the suburbs and
the local area network is designed for connecting each of the departments in the office. For designing
the wide area network for the company separate cluster is used different VLANs are allocated for each
of the cluster for increasing the security of the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
NETWORKING FUNDAMENTALS
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol. 2014,
no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp. 463-
464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design in
Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4, 2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network design
model to bus rapid transit network design: case study Isfahan metropolitan area", Transport,
vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based genetic/simulated
annealing algorithm for a closed-loop logistics network design problem", International Journal of
Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-844,
2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
NETWORKING FUNDAMENTALS
Bibliography
[1]. R. Brewer, "Advanced persistent threats: minimising the damage", Network Security, vol. 2014,
no. 4, pp. 5-9, 2014.
[2]. "IEEE/ACM Transactions on Networking society information", IEEE/ACM Transactions on
Networking, vol. 24, no. 5, pp. C3-C3, 2016.
[3]. D. Langenhan, VMware View Security Essentials. Packt Publishing, 2013.
[4]. "Optical Switching and Networking", Optical Switching and Networking, vol. 10, no. 4, pp. 463-
464, 2013.
[5]. S. Subramaniam, M. Brandt-Pearce, P. Demeester and C. Vijaya Saradhi, Cross-Layer Design in
Optical Networks. Boston, MA: Springer US, 2013.
[6]. "Introduction to Information Security", Network Security, vol. 2013, no. 12, p. 4, 2013.
[7]. "The Practice of Network Security Monitoring", Network Security, vol. 2014, no. 10, p. 4, 2014.
[8]. J. Wang, "The Design of Improved Elman Network Intrusion Detection Algorithm in Digital
Campus Network", Advanced Materials Research, vol. 1049-1050, pp. 2096-2099, 2014.
[9]. S. Kermanshahi, Y. Shafahi and M. Bagherian, "Application of a new rapid transit network design
model to bus rapid transit network design: case study Isfahan metropolitan area", Transport,
vol. 30, no. 1, pp. 93-102, 2013.
[10]. E. Yadegari, M. Zandieh and H. Najmi, "A hybrid spanning tree-based genetic/simulated
annealing algorithm for a closed-loop logistics network design problem", International Journal of
Applied Decision Sciences, vol. 8, no. 4, p. 400, 2015.
[11]. F. Liu and W. Qu, "Design of Campus Network Database Access Based on
Encryption", Applied Mechanics and Materials, vol. 608-609, pp. 331-335, 2014.
A. Hosapujari and A. Verma, "Development of a Hub and Spoke Model for Bus Transit
Route Network Design", Procedia - Social and Behavioral Sciences, vol. 104, pp. 835-844,
2013.
[12]. "The Comprehensive Evaluation Research of Campus Network Security Based on the
Analytic Hierarchy Process (AHP)", INTERNATIONAL JOURNAL ON Advances in Information
Sciences and Service Sciences, vol. 5, no. 7, pp. 809-816, 2013.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





