Networking Fundamentals Report: OSI Layers, Protocols, and Media Types
VerifiedAdded on 2022/12/05
|12
|2509
|449
Report
AI Summary
This report delves into the fundamentals of networking, focusing on the OSI and TCP/IP models. It provides a detailed explanation of the seven layers of the OSI model, including their functions and associated protocols. The report also compares the OSI and TCP/IP protocol suites, highlighting their similarities and differences. Furthermore, it covers various protocols used at each layer of the OSI model, along with a discussion of different media types, including wired and wireless connections, and their suitability for different network scenarios. The report concludes with a proposed network topology diagram for a business, outlining the use of VLANs and the integration of wired and wireless connections. The report emphasizes the importance of network design and the selection of appropriate protocols for establishing reliable communication, and it also touches on the application of these concepts in a real-world business environment.

Running head: NETWORKING FUNDAMENTALS
Networking Fundamentals
Name of the Student
Name of the University
Author’s note:
Networking Fundamentals
Name of the Student
Name of the University
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING FUNDAMENTALS
Table of Contents
Introduction:....................................................................................................................................2
1. OSI layered architecture:.............................................................................................................2
2. Comparison of the OSI Protocol Suite with the TCP/IP Protocol Suite:....................................4
3. Protocols of OSI Model Layers:..................................................................................................6
4. Media Types:...............................................................................................................................7
5. Topology Diagram of the Overall Networking:..........................................................................8
Conclusion:......................................................................................................................................9
References:....................................................................................................................................10
Table of Contents
Introduction:....................................................................................................................................2
1. OSI layered architecture:.............................................................................................................2
2. Comparison of the OSI Protocol Suite with the TCP/IP Protocol Suite:....................................4
3. Protocols of OSI Model Layers:..................................................................................................6
4. Media Types:...............................................................................................................................7
5. Topology Diagram of the Overall Networking:..........................................................................8
Conclusion:......................................................................................................................................9
References:....................................................................................................................................10

2NETWORKING FUNDAMENTALS
Introduction:
The network can be referred to as the digital communication between the devices
connected to each other using wire or wireless medium. Internet is the largest network that
connects all the devices connected to it to other devices [1]. The small networks in the office
buildings are LAN network. The LAN refers to the Local Area Network which connects devices
located in a small geographical locations.
This report is created based on the information available about the SUREINSURE. The
organization wants to develop new network. This network will be established in newly bought
two buildings. The LAN network is proposed for creating the network. Each building has three
floors. The customers will be waiting in the ground floor of first buildings. They will access the
network using Wi-Fi connection. The network will have printers for customer service
department. The network will be connected to an ISP so that each device can connect to internet.
Devices in two buildings can communicate with each other without internet connection.
1. OSI layered architecture:
OSI is the abbreviation of Open Systems Interconnection. This model was created in the
year of 1974 by International Organization of Standardization. This model has seven layers
which works together for transmitting data from one device to another.
Physical Layer: The physical layer is referred as the bottom layer in the OSI reference
model and it is associated with the connections that are established physically among the
network components. Bits is used by the devices of physical layer for storing the data. The
physical connection sends data in the form of 0 and 1 [3]. It is responsible for synchronization of
bit, rate control of bit, transmission mode and physical topologies.
Introduction:
The network can be referred to as the digital communication between the devices
connected to each other using wire or wireless medium. Internet is the largest network that
connects all the devices connected to it to other devices [1]. The small networks in the office
buildings are LAN network. The LAN refers to the Local Area Network which connects devices
located in a small geographical locations.
This report is created based on the information available about the SUREINSURE. The
organization wants to develop new network. This network will be established in newly bought
two buildings. The LAN network is proposed for creating the network. Each building has three
floors. The customers will be waiting in the ground floor of first buildings. They will access the
network using Wi-Fi connection. The network will have printers for customer service
department. The network will be connected to an ISP so that each device can connect to internet.
Devices in two buildings can communicate with each other without internet connection.
1. OSI layered architecture:
OSI is the abbreviation of Open Systems Interconnection. This model was created in the
year of 1974 by International Organization of Standardization. This model has seven layers
which works together for transmitting data from one device to another.
Physical Layer: The physical layer is referred as the bottom layer in the OSI reference
model and it is associated with the connections that are established physically among the
network components. Bits is used by the devices of physical layer for storing the data. The
physical connection sends data in the form of 0 and 1 [3]. It is responsible for synchronization of
bit, rate control of bit, transmission mode and physical topologies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3NETWORKING FUNDAMENTALS
Data Link Layer: This OSI reference layer has function named framing which allows a
sender to transfer a collection of bits which is understandable by the receiver. Another function is
physical addressing. This function adds an address of the device, named MAC, to the frame. In
order to re-transfer the damaged or lost frames, the data link layer user error control function.
Network Layer: This layer handles data transmission from sending node to the receiver
which is located in different network. The network layer has a function named routing which
determines the best route for transmitting a packet/message from the sender to destination node.
This layer must identify uniquely every device that is linked to the network. For doing that this
layer has an addressing scheme [5]. This scheme is about putting the IP of the receiver and
sender within the header of the packet. The network layer function is called Logical Addressing.
Transport Layer: This layer is used to provide services to application layer along with
receive service from the network layer. The main function of the transport layer is Segmentation
and Reassembly. The segmentation is breaking the messages accepted from the session layer.
Reassembly is the process of re-joining this segments at the receivers to create the actual
message [9]. The second function is Service Point Addressing. The transport layer ads a port
address or service point address to the segment so that message can be delivered to the correct
process.
Session Layer: This layer maintain sessions and establishes connection, authentication
and also overhead security. Session establishment, maintenance and termination is the first
function of the session layer. Using this function, two processes can establish and end
connection. Synchronization is the second function in the session layer. This function allows
putting synchronization points into the data by adding checkpoints [5]. The last function is
Data Link Layer: This OSI reference layer has function named framing which allows a
sender to transfer a collection of bits which is understandable by the receiver. Another function is
physical addressing. This function adds an address of the device, named MAC, to the frame. In
order to re-transfer the damaged or lost frames, the data link layer user error control function.
Network Layer: This layer handles data transmission from sending node to the receiver
which is located in different network. The network layer has a function named routing which
determines the best route for transmitting a packet/message from the sender to destination node.
This layer must identify uniquely every device that is linked to the network. For doing that this
layer has an addressing scheme [5]. This scheme is about putting the IP of the receiver and
sender within the header of the packet. The network layer function is called Logical Addressing.
Transport Layer: This layer is used to provide services to application layer along with
receive service from the network layer. The main function of the transport layer is Segmentation
and Reassembly. The segmentation is breaking the messages accepted from the session layer.
Reassembly is the process of re-joining this segments at the receivers to create the actual
message [9]. The second function is Service Point Addressing. The transport layer ads a port
address or service point address to the segment so that message can be delivered to the correct
process.
Session Layer: This layer maintain sessions and establishes connection, authentication
and also overhead security. Session establishment, maintenance and termination is the first
function of the session layer. Using this function, two processes can establish and end
connection. Synchronization is the second function in the session layer. This function allows
putting synchronization points into the data by adding checkpoints [5]. The last function is
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4NETWORKING FUNDAMENTALS
Dialog Controller. This function is responsible for allowing two systems to establish
communication among them in full-duplex or half-duplex.
Presentation Layer: The most important function of this layer is translation. It can
translate ASCII to EBCDIC. The Encryption/ Decryption function refers to data Encryption/
Decryption. This function converts the raw and original data into another form of code which is
not understandable any device but the desired receiver. This layers does the job of encrypting
and decrypting data [9]. Compression is the last function of this layer. This compression function
makes the bits quantity lesser. This way the message consumes less data and travels faster
through network.
Application Layer: This layer is the highest layer in the OSI reference Model. The
application layer produce the information which is to be transmitted through the route. This layer
can also be referred to as the way of accessing and managing the network [3]. The application
layer has the following functions Network Virtual Terminal, FTAM-File transfer access and
management, Mail Services and Directory Services.
2. Comparison of the OSI Protocol Suite with the TCP/IP Protocol Suite:
Basis for
Comparison
OSI MODEL TCP/IP MODEL
Abbreviation
of
Open system Interconnect Transmission Control Protocol/
Internet Protocol [12]
Refers to A theoretical model that can be
utilized regarding computing
systems
A client/server model that can be
utilized for transmitting data over a
network
Dialog Controller. This function is responsible for allowing two systems to establish
communication among them in full-duplex or half-duplex.
Presentation Layer: The most important function of this layer is translation. It can
translate ASCII to EBCDIC. The Encryption/ Decryption function refers to data Encryption/
Decryption. This function converts the raw and original data into another form of code which is
not understandable any device but the desired receiver. This layers does the job of encrypting
and decrypting data [9]. Compression is the last function of this layer. This compression function
makes the bits quantity lesser. This way the message consumes less data and travels faster
through network.
Application Layer: This layer is the highest layer in the OSI reference Model. The
application layer produce the information which is to be transmitted through the route. This layer
can also be referred to as the way of accessing and managing the network [3]. The application
layer has the following functions Network Virtual Terminal, FTAM-File transfer access and
management, Mail Services and Directory Services.
2. Comparison of the OSI Protocol Suite with the TCP/IP Protocol Suite:
Basis for
Comparison
OSI MODEL TCP/IP MODEL
Abbreviation
of
Open system Interconnect Transmission Control Protocol/
Internet Protocol [12]
Refers to A theoretical model that can be
utilized regarding computing
systems
A client/server model that can be
utilized for transmitting data over a
network
5NETWORKING FUNDAMENTALS
Layers It has seven layers
Physical Layer, Data Link Layer,
Network Layer, Transport Layer,
Session Layer, Presentation Layer
and Application Layer
It has four layers
Network Interface Layer, Internet
Layer, Transport Layer and
Application Layer.
Creator International Standard Organization DoD or Department of Defense
Tangible No Yes
Utilization Never used In most cases
Definition The OSI is a model that was created
on the concept of layers which are
positioned horizontally [2].
TCP/IP is the protocol that allows
nodes in a network to communicate
with each other and is considered as a
standard model in computer
networking
Working
Function
The working is based on concepts of
networking
Client request for service and host
provide the service
Layer Model Physical Layer, Data Link Layer and
Network Layer are in Media Layers.
Transport Layer, Session Layer,
Presentation Layer and Application
Layer are in Host Layer.
Network Interface Layer and Internet
Layer are in Media Layers.
Transport Layer and Application
Layer are in Host Layer
Layers It has seven layers
Physical Layer, Data Link Layer,
Network Layer, Transport Layer,
Session Layer, Presentation Layer
and Application Layer
It has four layers
Network Interface Layer, Internet
Layer, Transport Layer and
Application Layer.
Creator International Standard Organization DoD or Department of Defense
Tangible No Yes
Utilization Never used In most cases
Definition The OSI is a model that was created
on the concept of layers which are
positioned horizontally [2].
TCP/IP is the protocol that allows
nodes in a network to communicate
with each other and is considered as a
standard model in computer
networking
Working
Function
The working is based on concepts of
networking
Client request for service and host
provide the service
Layer Model Physical Layer, Data Link Layer and
Network Layer are in Media Layers.
Transport Layer, Session Layer,
Presentation Layer and Application
Layer are in Host Layer.
Network Interface Layer and Internet
Layer are in Media Layers.
Transport Layer and Application
Layer are in Host Layer
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORKING FUNDAMENTALS
3. Protocols of OSI Model Layers:
The first layer of the OSI Model is the physical layer. The cabling is managed within the
layer along with the other hardware resources. IEEE.802.11, DSL, OTN,
PON, Bluetooth, IEEE.802.3, L431 and TIA 449 are the major protocols that are included within
this layer [6].
The second layer of OSI model is the data link layer. This layer is responsible for
receiving data from the physical layer and converting that data into the frame. ARP, CSLIP,
HDLC, IEEE.802.3, PPP, X-25, SLIP, ATM, SDLS and PLIP are the major protocols that are
being used by the Data Link Layer.
The third layer in the OSI model is the Network Layer. This layer can be considered as
the most significant among all the OSI layers. This layer is capable of conducting real-time
process of data along with transmitting the data from sender to receiver. The layer three routers
and switches are the devices used in this layer. Internet Protocol (IPv4), Internet Protocol (IPv6),
IPX, AppleTalk, ICMP, IPSec and IGMP are the major protocls used in this layer.
The fourth layer is the transport layer. The transport layer can work in either connection
or connectionless mode. This layer is responsible for transmitting data from the source node to
the destination node. This layer will be using the TCP for establishing connection between the
devices. The standardizing body of TCP is Transmission Control Protocol. The TCP can be
considered as the most important protocol in the network. The function of the TCP is to create a
communication between two nodes so that these two nodes can communicate with each other
[7]. The TCP uses acknowledgement from the receiver to ensure delivery of data and delivering
the packets same way transmission were meant to be.
3. Protocols of OSI Model Layers:
The first layer of the OSI Model is the physical layer. The cabling is managed within the
layer along with the other hardware resources. IEEE.802.11, DSL, OTN,
PON, Bluetooth, IEEE.802.3, L431 and TIA 449 are the major protocols that are included within
this layer [6].
The second layer of OSI model is the data link layer. This layer is responsible for
receiving data from the physical layer and converting that data into the frame. ARP, CSLIP,
HDLC, IEEE.802.3, PPP, X-25, SLIP, ATM, SDLS and PLIP are the major protocols that are
being used by the Data Link Layer.
The third layer in the OSI model is the Network Layer. This layer can be considered as
the most significant among all the OSI layers. This layer is capable of conducting real-time
process of data along with transmitting the data from sender to receiver. The layer three routers
and switches are the devices used in this layer. Internet Protocol (IPv4), Internet Protocol (IPv6),
IPX, AppleTalk, ICMP, IPSec and IGMP are the major protocls used in this layer.
The fourth layer is the transport layer. The transport layer can work in either connection
or connectionless mode. This layer is responsible for transmitting data from the source node to
the destination node. This layer will be using the TCP for establishing connection between the
devices. The standardizing body of TCP is Transmission Control Protocol. The TCP can be
considered as the most important protocol in the network. The function of the TCP is to create a
communication between two nodes so that these two nodes can communicate with each other
[7]. The TCP uses acknowledgement from the receiver to ensure delivery of data and delivering
the packets same way transmission were meant to be.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING FUNDAMENTALS
The fifth layer in the OSI model is the session layer. The session layer will be using the
PPTP protocol. The standardizing body of PPTP is The Point-to-Point Tunneling Protocol [10].
The PPTP has the function of developing the virtual private network.
The sixth layer in the OSI model is the presentation layer. This layer will be using the
protocol named SSL. The SSL has standardizing body Secure Sockets Layer. The SSL has the
function of creating a secure connection between the nodes. It has one private key and one public
key. This protocol uses these two keys to encrypt messages.
The last, seventh, layer in the OSI model is the application layer. This layer will be using
the SNMP protocol. The SNMP has the standardizing body Simple Network Management
Protocol. This protocol has the function of gathering and maintaining data regarding the
managed devices within IP networks. It also updates the information for changing the device
behavior.
4. Media Types:
Both the Wired and Wireless media types will be considered in this network design. The
wired connections are more secure, fast and reliable. On the other hand, the wireless connections
are more scalable and easy to manage. In a room where a lot of temporary devices will be
connected to the network, the wireless connection is suitable [8]. The wireless also allows the
network to connect mobile devices. That is why customer waiting room will have wireless
connection and other office devices will be connected to router using wire.
The fifth layer in the OSI model is the session layer. The session layer will be using the
PPTP protocol. The standardizing body of PPTP is The Point-to-Point Tunneling Protocol [10].
The PPTP has the function of developing the virtual private network.
The sixth layer in the OSI model is the presentation layer. This layer will be using the
protocol named SSL. The SSL has standardizing body Secure Sockets Layer. The SSL has the
function of creating a secure connection between the nodes. It has one private key and one public
key. This protocol uses these two keys to encrypt messages.
The last, seventh, layer in the OSI model is the application layer. This layer will be using
the SNMP protocol. The SNMP has the standardizing body Simple Network Management
Protocol. This protocol has the function of gathering and maintaining data regarding the
managed devices within IP networks. It also updates the information for changing the device
behavior.
4. Media Types:
Both the Wired and Wireless media types will be considered in this network design. The
wired connections are more secure, fast and reliable. On the other hand, the wireless connections
are more scalable and easy to manage. In a room where a lot of temporary devices will be
connected to the network, the wireless connection is suitable [8]. The wireless also allows the
network to connect mobile devices. That is why customer waiting room will have wireless
connection and other office devices will be connected to router using wire.
8NETWORKING FUNDAMENTALS
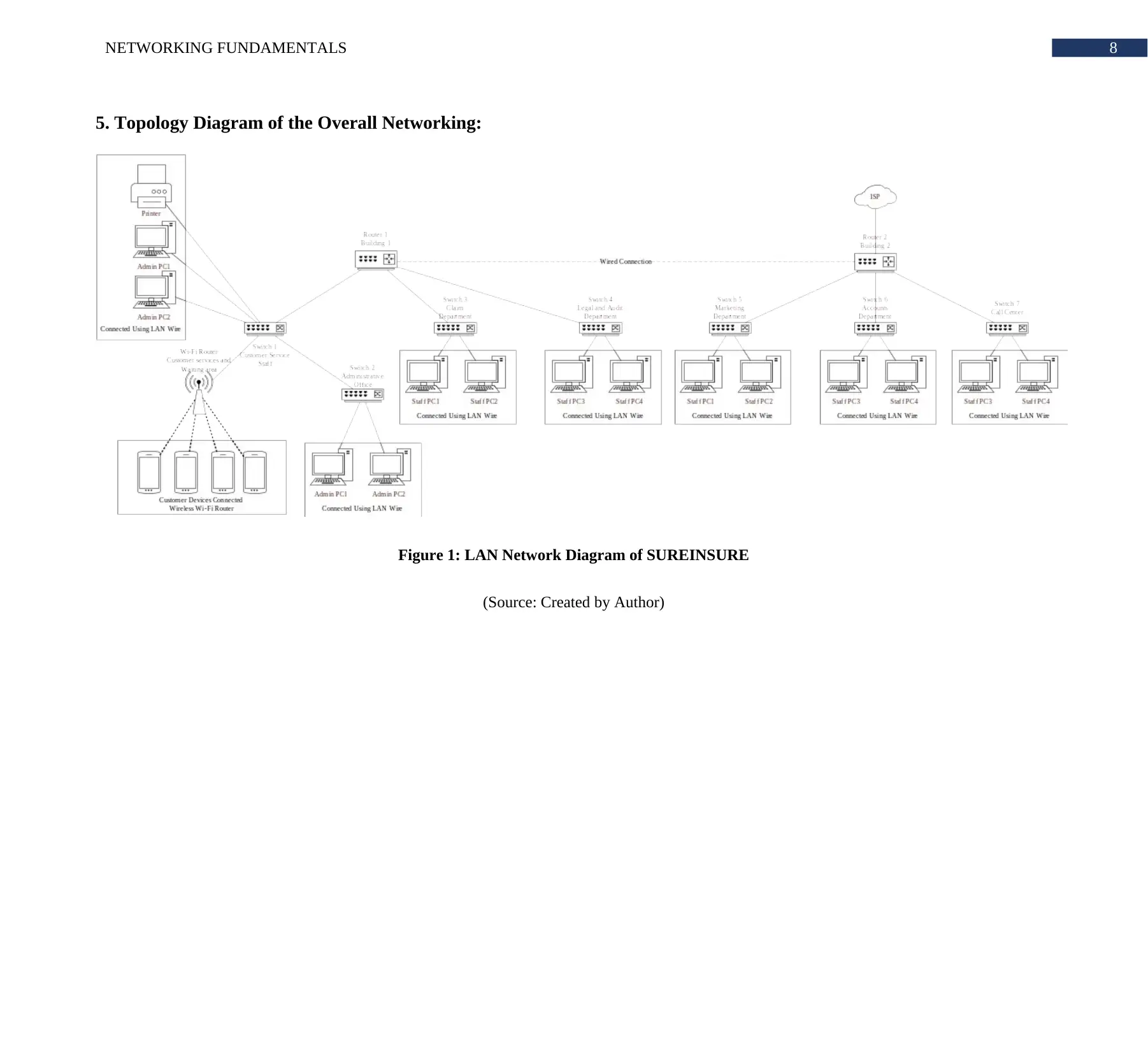
5. Topology Diagram of the Overall Networking:
Figure 1: LAN Network Diagram of SUREINSURE
(Source: Created by Author)
5. Topology Diagram of the Overall Networking:
Figure 1: LAN Network Diagram of SUREINSURE
(Source: Created by Author)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9NETWORKING FUNDAMENTALS
Conclusion:
The above study concludes that the proposed network diagram is very suitable for the
organization. All the details provided within the report is very descriptive and accurate. The
network diagram proposes that the network of SUREINSURE has to use VLAN to connect all
the nodes together. The protocols used for each layer of OSI model perfectly describes how the
network going to establish flawless communication.
Conclusion:
The above study concludes that the proposed network diagram is very suitable for the
organization. All the details provided within the report is very descriptive and accurate. The
network diagram proposes that the network of SUREINSURE has to use VLAN to connect all
the nodes together. The protocols used for each layer of OSI model perfectly describes how the
network going to establish flawless communication.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORKING FUNDAMENTALS
References:
[1] Hasan, S.M., Sahib, M.A. and Namel, A.T., “Bandwidth Utilization Prediction in LAN
Network Using Time Series Modeling,” IRAQI JOURNAL OF COMPUTERS,
COMMUNICATION AND CONTROL & SYSTEMS ENGINEERING, 19(2), pp.78-89, 2019.
[2] Huang, J. and Cai, L., “Research on TCP/IP network communication based on Node. Js,”
In AIP Conference Proceedings (Vol. 1955, No. 1, p. 040115). AIP Publishing, April 2018.
[3] Radhakrishnan, R., Edmonson, W.W., Afghah, F., Rodriguez-Osorio, R.M., Pinto, F. and
Burleigh, S.C., “Survey of inter-satellite communication for small satellite systems: Physical
layer to network layer view,” IEEE Communications Surveys & Tutorials, 18(4), pp.2442-2473,
2016.
[4] Theoleyre, F., Watteyne, T., Bianchi, G., Tuna, G., Gungor, V.C. and Pang, A.C.,
“Networking and communications for smart cities special issue editorial,” Computer
Communications, 58(0), pp.1-3, 2015.
[5] Chandra, A. and Thakur, S., “Qualitative analysis of hybrid routing protocols against network
layer attacks in MANET,” Apoorva Chandra et al, International Journal of Computer Science
and Mobile Computing, 4(6), pp.538-543, 2015.
[6] Bellalta, B., “IEEE 802.11 ax: High-efficiency WLANs,” IEEE Wireless
Communications, 23(1), pp.38-46, 2016.
[7] Cui, Y., Wang, L., Wang, X., Wang, H. and Wang, Y., “FMTCP: A fountain code-based
multipath transmission control protocol,” IEEE/ACM Transactions on Networking (ToN), 23(2),
pp.465-478, 2015.
References:
[1] Hasan, S.M., Sahib, M.A. and Namel, A.T., “Bandwidth Utilization Prediction in LAN
Network Using Time Series Modeling,” IRAQI JOURNAL OF COMPUTERS,
COMMUNICATION AND CONTROL & SYSTEMS ENGINEERING, 19(2), pp.78-89, 2019.
[2] Huang, J. and Cai, L., “Research on TCP/IP network communication based on Node. Js,”
In AIP Conference Proceedings (Vol. 1955, No. 1, p. 040115). AIP Publishing, April 2018.
[3] Radhakrishnan, R., Edmonson, W.W., Afghah, F., Rodriguez-Osorio, R.M., Pinto, F. and
Burleigh, S.C., “Survey of inter-satellite communication for small satellite systems: Physical
layer to network layer view,” IEEE Communications Surveys & Tutorials, 18(4), pp.2442-2473,
2016.
[4] Theoleyre, F., Watteyne, T., Bianchi, G., Tuna, G., Gungor, V.C. and Pang, A.C.,
“Networking and communications for smart cities special issue editorial,” Computer
Communications, 58(0), pp.1-3, 2015.
[5] Chandra, A. and Thakur, S., “Qualitative analysis of hybrid routing protocols against network
layer attacks in MANET,” Apoorva Chandra et al, International Journal of Computer Science
and Mobile Computing, 4(6), pp.538-543, 2015.
[6] Bellalta, B., “IEEE 802.11 ax: High-efficiency WLANs,” IEEE Wireless
Communications, 23(1), pp.38-46, 2016.
[7] Cui, Y., Wang, L., Wang, X., Wang, H. and Wang, Y., “FMTCP: A fountain code-based
multipath transmission control protocol,” IEEE/ACM Transactions on Networking (ToN), 23(2),
pp.465-478, 2015.

11NETWORKING FUNDAMENTALS
[8] Mendes, T., Godina, R., Rodrigues, E., Matias, J. and Catalão, J., “Smart home
communication technologies and applications: Wireless protocol assessment for home area
network resources,” Energies, 8(7), pp.7279-7311, 2015.
[9] Nath, P.B. and Uddin, M.M., “TCP-IP Model in Data Communication and
Networking,” American Journal of Engineering Research, 4(10), pp.102-107, 2015.
[10] Narayan, S., Ishrar, S., Kumar, A., Gupta, R. and Khan, Z., “Performance analysis of 4to6
and 6to4 transition mechanisms over point to point and IPSec VPN protocols,” In 2016
Thirteenth International Conference on Wireless and Optical Communications Networks
(WOCN) (pp. 1-7). IEEE, July 2016.
[11] Cui, Y., Wu, J., Xu, M., Metz, C. and Yang, S., “IPv4 Multicast over an IPv6 Multicast in
Softwire Mesh Network,” 2018.
[12] Huang, J. and Cai, L., “Research on TCP/IP network communication based on Node. Js,”
In AIP Conference Proceedings (Vol. 1955, No. 1, p. 040115). AIP Publishing, April 2018.
[8] Mendes, T., Godina, R., Rodrigues, E., Matias, J. and Catalão, J., “Smart home
communication technologies and applications: Wireless protocol assessment for home area
network resources,” Energies, 8(7), pp.7279-7311, 2015.
[9] Nath, P.B. and Uddin, M.M., “TCP-IP Model in Data Communication and
Networking,” American Journal of Engineering Research, 4(10), pp.102-107, 2015.
[10] Narayan, S., Ishrar, S., Kumar, A., Gupta, R. and Khan, Z., “Performance analysis of 4to6
and 6to4 transition mechanisms over point to point and IPSec VPN protocols,” In 2016
Thirteenth International Conference on Wireless and Optical Communications Networks
(WOCN) (pp. 1-7). IEEE, July 2016.
[11] Cui, Y., Wu, J., Xu, M., Metz, C. and Yang, S., “IPv4 Multicast over an IPv6 Multicast in
Softwire Mesh Network,” 2018.
[12] Huang, J. and Cai, L., “Research on TCP/IP network communication based on Node. Js,”
In AIP Conference Proceedings (Vol. 1955, No. 1, p. 040115). AIP Publishing, April 2018.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




