University Networking Assignment: IPv4, IPv6, P2P, and HTTP Protocols
VerifiedAdded on 2020/04/07
|9
|2070
|48
Homework Assignment
AI Summary
This assignment solution addresses key networking concepts. It begins by discussing the depletion of IPv4 addresses and the increasing adoption of IPv6, highlighting its advantages such as more addresses, efficient routing, and improved security. The solution then explains the transition process from IPv4 to IPv6, emphasizing the importance of IP Address Management (IPAM) tools. It compares centralized and decentralized P2P networks, outlining their advantages and disadvantages. The role and properties of Distributed Hash Tables (DHT) within P2P networks are also explored, along with an example of how DHTs facilitate data routing. Furthermore, the client-server architecture is explained, distinguishing the roles of servers and clients. Finally, the solution differentiates between persistent and non-persistent HTTP connections, detailing their characteristics and advantages. The assignment references several academic sources to support its claims.

Running head: NETWORKING
Networking
Name of the Student:
Name of the University:
Author Note
Networking
Name of the Student:
Name of the University:
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
NETWORKING
Answer to question 1
The IPv4 IP addresses have been depleting at a huge rate. The rate of depletion has been
increase at a great rate and as a result the use of the IPv6 has been increasing at a great rate.
Many of the major organizations have been migrating their IP addresses form the IPv4 to the IP6
addresses. According to the reports by the IANA it has been known 18 percent of the IP
addresses have been unassigned (Goyal & Arora, 2017). The RIRs have also reported that 68%
of their IP addresses have either been unassigned or has been migrated to IPv6. One of the main
reasons for this being that forth fifth of the addresses that are being used by the IPv4 system have
already being exhausted and only one-fifth of the remaining addresses are useful.
In addition to all this, the IPv6 Addresses provide various type of advantages over the
IPv4 addresses. The IPv6 provides various options to allocate more addresses to the systems and
by the time the IPv6 addresses would be fully exhausted other option such as the NAT
technologies would be fully implemented and hence the shortage of the IP addresses would not
be persistent over the web. In addition to this the IPv6 provides more efficient routing for the
addresses. They also provide very efficient packet processing. They support direct data flow and
also have a simplified network configuration. They support the new services and provided an
improved security. But this transition is taking a long time as the IPv6 cannot communicate
directly with the IPv4 host.
Answer to question 2
For the migration from IPv4 to IPv6 it is very important to have knowledge of the IPv4
and IPv6 version. The IPv4 version of the internet protocol is the primitive version that supports
the primitive addresses. In addition to this, the IPv6 version of the protocol is the next generation
NETWORKING
Answer to question 1
The IPv4 IP addresses have been depleting at a huge rate. The rate of depletion has been
increase at a great rate and as a result the use of the IPv6 has been increasing at a great rate.
Many of the major organizations have been migrating their IP addresses form the IPv4 to the IP6
addresses. According to the reports by the IANA it has been known 18 percent of the IP
addresses have been unassigned (Goyal & Arora, 2017). The RIRs have also reported that 68%
of their IP addresses have either been unassigned or has been migrated to IPv6. One of the main
reasons for this being that forth fifth of the addresses that are being used by the IPv4 system have
already being exhausted and only one-fifth of the remaining addresses are useful.
In addition to all this, the IPv6 Addresses provide various type of advantages over the
IPv4 addresses. The IPv6 provides various options to allocate more addresses to the systems and
by the time the IPv6 addresses would be fully exhausted other option such as the NAT
technologies would be fully implemented and hence the shortage of the IP addresses would not
be persistent over the web. In addition to this the IPv6 provides more efficient routing for the
addresses. They also provide very efficient packet processing. They support direct data flow and
also have a simplified network configuration. They support the new services and provided an
improved security. But this transition is taking a long time as the IPv6 cannot communicate
directly with the IPv4 host.
Answer to question 2
For the migration from IPv4 to IPv6 it is very important to have knowledge of the IPv4
and IPv6 version. The IPv4 version of the internet protocol is the primitive version that supports
the primitive addresses. In addition to this, the IPv6 version of the protocol is the next generation

2
NETWORKING
addresses. The protocol is a successor to the IPv4 and the IPv4 were of 32 bits that were to be
replaced by the 128 bit addresses. Although the adoption of the IPv6 version is a slow process
the depletion of the IPv4 versions have already improved the adoption rate of the IPv6 addresses
(Suzuki et al., 2013). The process of the replacement of the addresses does not mean that the IP
addresses are actually replaced but it means that the IPv6 addresses are enabled in addition to the
IPv4 addresses. The versions are not compatible to each other and the devices supporting IPv4
would not be supporting the IPv6 addresses. The migration processes involve a very transparent
and solid process. The procedures have to be managed by the IP Address Management or the
IMAP tools. In addition to this it should be known that The Men & Mice IP Address
Management Module is Free of charge tool that helps the process of migrating from the IPv4 to
the IPv6 processes. For the deployment of the IPv6 addresses the Men and Mice has introduced
the whitepaper outlining stepwise for the processes. The process is also supported by the IPv6
Migration Screencast.
Answer to question 3
The Centralized P2P is basically a distributed network with a central server and the
decentralized P2P is network where the location of the server is not central (Tran & Ha, 2016).
The table provided below shows the comparison of the advantages and the disadvantages of the
centralized P2P and the Decentralized P2P:
Centralized P2P Decentralized P2P
Advantages
The Centralized P2P network is easier
to set up and hence incur less cost.
This network is also very cost
The network prioritizes the efficiency
The network is highly scalable
Data in between the components is
NETWORKING
addresses. The protocol is a successor to the IPv4 and the IPv4 were of 32 bits that were to be
replaced by the 128 bit addresses. Although the adoption of the IPv6 version is a slow process
the depletion of the IPv4 versions have already improved the adoption rate of the IPv6 addresses
(Suzuki et al., 2013). The process of the replacement of the addresses does not mean that the IP
addresses are actually replaced but it means that the IPv6 addresses are enabled in addition to the
IPv4 addresses. The versions are not compatible to each other and the devices supporting IPv4
would not be supporting the IPv6 addresses. The migration processes involve a very transparent
and solid process. The procedures have to be managed by the IP Address Management or the
IMAP tools. In addition to this it should be known that The Men & Mice IP Address
Management Module is Free of charge tool that helps the process of migrating from the IPv4 to
the IPv6 processes. For the deployment of the IPv6 addresses the Men and Mice has introduced
the whitepaper outlining stepwise for the processes. The process is also supported by the IPv6
Migration Screencast.
Answer to question 3
The Centralized P2P is basically a distributed network with a central server and the
decentralized P2P is network where the location of the server is not central (Tran & Ha, 2016).
The table provided below shows the comparison of the advantages and the disadvantages of the
centralized P2P and the Decentralized P2P:
Centralized P2P Decentralized P2P
Advantages
The Centralized P2P network is easier
to set up and hence incur less cost.
This network is also very cost
The network prioritizes the efficiency
The network is highly scalable
Data in between the components is
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
NETWORKING
effective network.
The network prioritizes robustness
Data transmission is organized by this
type of network.
The network is implemented using the
hybrid approach that can support a
variety of information
done by handshaking approach
Disadvantages
The network scalability is low
The efficiency of the network is low
The data sharing is not organized in
the centralized system.
The joining of network involves a
simplified method for this type of
networks.
The robustness in the network is very
unconvincing
The variety of information in
centralized P2P network is not
available in the network
The implementation of the network is
not possible using a hybrid network
design.
The set up process of the network
involves very complex processes.
The joining procedures involve very
complex procedures for the network.
Answer to question 4
NETWORKING
effective network.
The network prioritizes robustness
Data transmission is organized by this
type of network.
The network is implemented using the
hybrid approach that can support a
variety of information
done by handshaking approach
Disadvantages
The network scalability is low
The efficiency of the network is low
The data sharing is not organized in
the centralized system.
The joining of network involves a
simplified method for this type of
networks.
The robustness in the network is very
unconvincing
The variety of information in
centralized P2P network is not
available in the network
The implementation of the network is
not possible using a hybrid network
design.
The set up process of the network
involves very complex processes.
The joining procedures involve very
complex procedures for the network.
Answer to question 4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
NETWORKING
The DHT or the Distributed Hash Table is a part of the P2P network (Li et al., 2013). The
DHT consists of the following properties:
In a network any type of data can be founded provided that there is an existence of the
data in the network.
All the nodes require very limited knowledge about the neighbouring nodes or the nodes
that are existing in the network.
The process that is involved for finding the data in the network is very limited.
The DHT can very easily tolerate the failure of the crashes.
They can also handle the incoming and the outgoing nodes within the network.
The DHT is very useful in the P2P networks:
The Hash tables provides the mapping for the keys to the values of the network.
Good functions perform the distribution of the values in the network evenly.
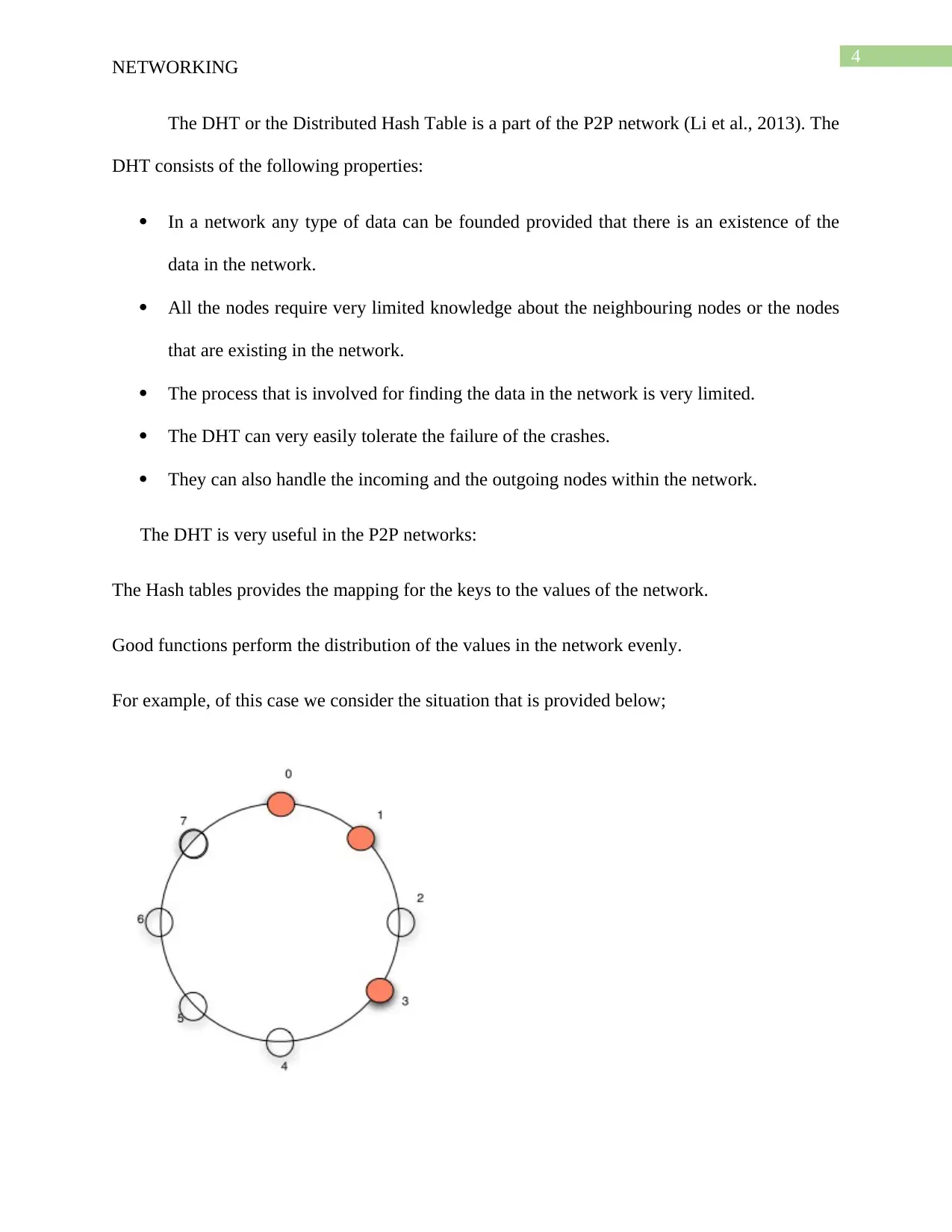
For example, of this case we consider the situation that is provided below;
NETWORKING
The DHT or the Distributed Hash Table is a part of the P2P network (Li et al., 2013). The
DHT consists of the following properties:
In a network any type of data can be founded provided that there is an existence of the
data in the network.
All the nodes require very limited knowledge about the neighbouring nodes or the nodes
that are existing in the network.
The process that is involved for finding the data in the network is very limited.
The DHT can very easily tolerate the failure of the crashes.
They can also handle the incoming and the outgoing nodes within the network.
The DHT is very useful in the P2P networks:
The Hash tables provides the mapping for the keys to the values of the network.
Good functions perform the distribution of the values in the network evenly.
For example, of this case we consider the situation that is provided below;

5
NETWORKING
In provided example the node that are to be worked with are 0,1,3. 0 is responsible for
data that hashes to 0. For the data that would be hashed to 1 or 2 node number 1 would be
responsible. Node number 3 is responsible for data that hashes to 3-7. For simpler routing of the
chord each node should be keeping track of the neighboring node and most probably the
successor node. For a piece of data, a node can very easily ask for the data from its successor. All
the nodes in the ring would be queried. For n number of nodes in the chord ith node is the first
entry and that is followed by 2^(i-1) modulo n. This contains the Chord identifier and the actual
IP address of the nodes. In the example the node the looks for the predecessor in the node. The
predecessor of 5 is 3 in the provided network. It is assumed that node 3 is looking for node 2 so
that the data can be available. It is known that the successor of node 7 is 0, then query 0 to find
that 2 is stored by node 1. This chord would get the data in O(logN) time.
Answer to question 5
In the client server architecture, the server is the node that provides the service in the
network to all the nodes. In addition to this the client side machines are those that receive the
services in the network. The server conducts the network and performs the function of
connecting all the nodes in the network (Bibinagar & Kim, 2013). The server provides the data
and also performs all the requirement of the network such as authentication and security
processes. The server is the node that should be active all the time in the network. The server is
the most important node in the network and performs all the functionality in the network. It can
be easily said that the network would become unresponsive if the server is down. The client
machines on the other hand is useful for the user only. The network can be fairly active without
the client machine in the network. The user can use the client machine to get online on the
network and hence, the client machine can have uptime only on the requirement of the users.
NETWORKING
In provided example the node that are to be worked with are 0,1,3. 0 is responsible for
data that hashes to 0. For the data that would be hashed to 1 or 2 node number 1 would be
responsible. Node number 3 is responsible for data that hashes to 3-7. For simpler routing of the
chord each node should be keeping track of the neighboring node and most probably the
successor node. For a piece of data, a node can very easily ask for the data from its successor. All
the nodes in the ring would be queried. For n number of nodes in the chord ith node is the first
entry and that is followed by 2^(i-1) modulo n. This contains the Chord identifier and the actual
IP address of the nodes. In the example the node the looks for the predecessor in the node. The
predecessor of 5 is 3 in the provided network. It is assumed that node 3 is looking for node 2 so
that the data can be available. It is known that the successor of node 7 is 0, then query 0 to find
that 2 is stored by node 1. This chord would get the data in O(logN) time.
Answer to question 5
In the client server architecture, the server is the node that provides the service in the
network to all the nodes. In addition to this the client side machines are those that receive the
services in the network. The server conducts the network and performs the function of
connecting all the nodes in the network (Bibinagar & Kim, 2013). The server provides the data
and also performs all the requirement of the network such as authentication and security
processes. The server is the node that should be active all the time in the network. The server is
the most important node in the network and performs all the functionality in the network. It can
be easily said that the network would become unresponsive if the server is down. The client
machines on the other hand is useful for the user only. The network can be fairly active without
the client machine in the network. The user can use the client machine to get online on the
network and hence, the client machine can have uptime only on the requirement of the users.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
NETWORKING
Answer to question 6
There are two types of HTTP connection in the client server paradigm. The persistent
HTTP connection leaves the connections open after the request is sent (Lilly et al., 2014). In
addition to this, subsequent HTTP messages between the same client that are sent over the open
connections in the network are known as persistent connections. The client sends the request on
the reception of referenced object and also for all the referenced object only one RTT would be
available.
On the other hand, the Non persistent connection requires 2 RTTs per object and an
overhead for each of the TCP connection is required in this protocol for the client server
architecture. Very often parallel TCP connections are requiring by the referenced objects to be
fetched.
There are two types of persistent connections and they are Pipelined and Non-pipelined
connections. On the other hand, the two type of connections that are present for the Non-
persistent connections are Parallel connection and non-parallel connections.
The advantages of the persistent connection over the non-persistent connections are that
they demand lower amount of CPU performance as because less number of connections are
being used in this network. Additionally, they also reduce the latency in the network. The errors
in the network can also be reported without closing the connection.
NETWORKING
Answer to question 6
There are two types of HTTP connection in the client server paradigm. The persistent
HTTP connection leaves the connections open after the request is sent (Lilly et al., 2014). In
addition to this, subsequent HTTP messages between the same client that are sent over the open
connections in the network are known as persistent connections. The client sends the request on
the reception of referenced object and also for all the referenced object only one RTT would be
available.
On the other hand, the Non persistent connection requires 2 RTTs per object and an
overhead for each of the TCP connection is required in this protocol for the client server
architecture. Very often parallel TCP connections are requiring by the referenced objects to be
fetched.
There are two types of persistent connections and they are Pipelined and Non-pipelined
connections. On the other hand, the two type of connections that are present for the Non-
persistent connections are Parallel connection and non-parallel connections.
The advantages of the persistent connection over the non-persistent connections are that
they demand lower amount of CPU performance as because less number of connections are
being used in this network. Additionally, they also reduce the latency in the network. The errors
in the network can also be reported without closing the connection.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
NETWORKING
References
Bibinagar, N., & Kim, W. J. (2013). Switched Ethernet-based real-time networked control
system with multiple-client–server architecture. IEEE/ASME transactions on
Mechatronics, 18(1), 104-112.
Cui, Y., Chen, Y., Liu, J., Lee, Y. L., Wu, J., & Wang, X. (2015). State management in IPv4 to
IPv6 transition. IEEE Network, 29(6), 48-53.
Goyal, V., & Arora, G. (2017). Implementation of Enhanced Interior Gateway Routing Protocol
(EIGRP) in IPv6 Network. Research Journal of Advanced Engineering and Science, 2(1),
90-95.
Li, T., Zhou, X., Brandstatter, K., Zhao, D., Wang, K., Rajendran, A., ... & Raicu, I. (2013,
May). ZHT: A light-weight reliable persistent dynamic scalable zero-hop distributed hash
table. In Parallel & distributed processing (IPDPS), 2013 IEEE 27th international
symposium on (pp. 775-787). IEEE.
Lilly, S. M., Mortensen, E. M., Frei, C. R., Pugh, M. J., & Mansi, I. A. (2014). Comparison of
the risk of psychological and cognitive disorders between persistent and nonpersistent
statin users. The American journal of cardiology, 114(7), 1035-1039.
Sha, F., Chen, X., Ye, R., Wu, M., Zhang, Z., & Cai, W. (2017, May). A communication method
between IPv4 server and IPv6 network in virtual machine environment. In Computer and
Information Science (ICIS), 2017 IEEE/ACIS 16th International Conference on (pp. 885-
888). IEEE.
NETWORKING
References
Bibinagar, N., & Kim, W. J. (2013). Switched Ethernet-based real-time networked control
system with multiple-client–server architecture. IEEE/ASME transactions on
Mechatronics, 18(1), 104-112.
Cui, Y., Chen, Y., Liu, J., Lee, Y. L., Wu, J., & Wang, X. (2015). State management in IPv4 to
IPv6 transition. IEEE Network, 29(6), 48-53.
Goyal, V., & Arora, G. (2017). Implementation of Enhanced Interior Gateway Routing Protocol
(EIGRP) in IPv6 Network. Research Journal of Advanced Engineering and Science, 2(1),
90-95.
Li, T., Zhou, X., Brandstatter, K., Zhao, D., Wang, K., Rajendran, A., ... & Raicu, I. (2013,
May). ZHT: A light-weight reliable persistent dynamic scalable zero-hop distributed hash
table. In Parallel & distributed processing (IPDPS), 2013 IEEE 27th international
symposium on (pp. 775-787). IEEE.
Lilly, S. M., Mortensen, E. M., Frei, C. R., Pugh, M. J., & Mansi, I. A. (2014). Comparison of
the risk of psychological and cognitive disorders between persistent and nonpersistent
statin users. The American journal of cardiology, 114(7), 1035-1039.
Sha, F., Chen, X., Ye, R., Wu, M., Zhang, Z., & Cai, W. (2017, May). A communication method
between IPv4 server and IPv6 network in virtual machine environment. In Computer and
Information Science (ICIS), 2017 IEEE/ACIS 16th International Conference on (pp. 885-
888). IEEE.

8
NETWORKING
Suzuki, H., Naito, K., Kamienoo, K., Hirose, T., & Watanabe, A. (2013, September). Ntmobile:
New end-to-end communication architecture in ipv4 and ipv6 networks. In Proceedings
of the 19th annual international conference on Mobile computing & networking (pp. 171-
174). ACM.
Tran, M. H., & Ha, S. V. U. (2016). Decentralized Online Social Network Using Peer-to-Peer
Technology. REV Journal on Electronics and Communications, 5(1-2).
NETWORKING
Suzuki, H., Naito, K., Kamienoo, K., Hirose, T., & Watanabe, A. (2013, September). Ntmobile:
New end-to-end communication architecture in ipv4 and ipv6 networks. In Proceedings
of the 19th annual international conference on Mobile computing & networking (pp. 171-
174). ACM.
Tran, M. H., & Ha, S. V. U. (2016). Decentralized Online Social Network Using Peer-to-Peer
Technology. REV Journal on Electronics and Communications, 5(1-2).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




