ITECH1102: Data Link, Transport Layer, Cloud Computing Report
VerifiedAdded on 2023/04/24
|7
|1457
|220
Report
AI Summary
This report provides an overview of the data link layer, transport layer, and cloud computing. The data link layer focuses on data flow and framing, ensuring secure communication between devices on the same network. The transport layer manages server applications and allows multiplexing, using protocols like TCP and UDP to ensure reliable data delivery. Cloud computing, defined as delivering services over the internet, offers benefits such as self-service resources and cost reduction, using public, private, and hybrid networks, and is divided into IaaS, PaaS, and SaaS models. The report examines the functionality, issues, and importance of each concept in the context of networking and modern computing.

Networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1 | P a g e
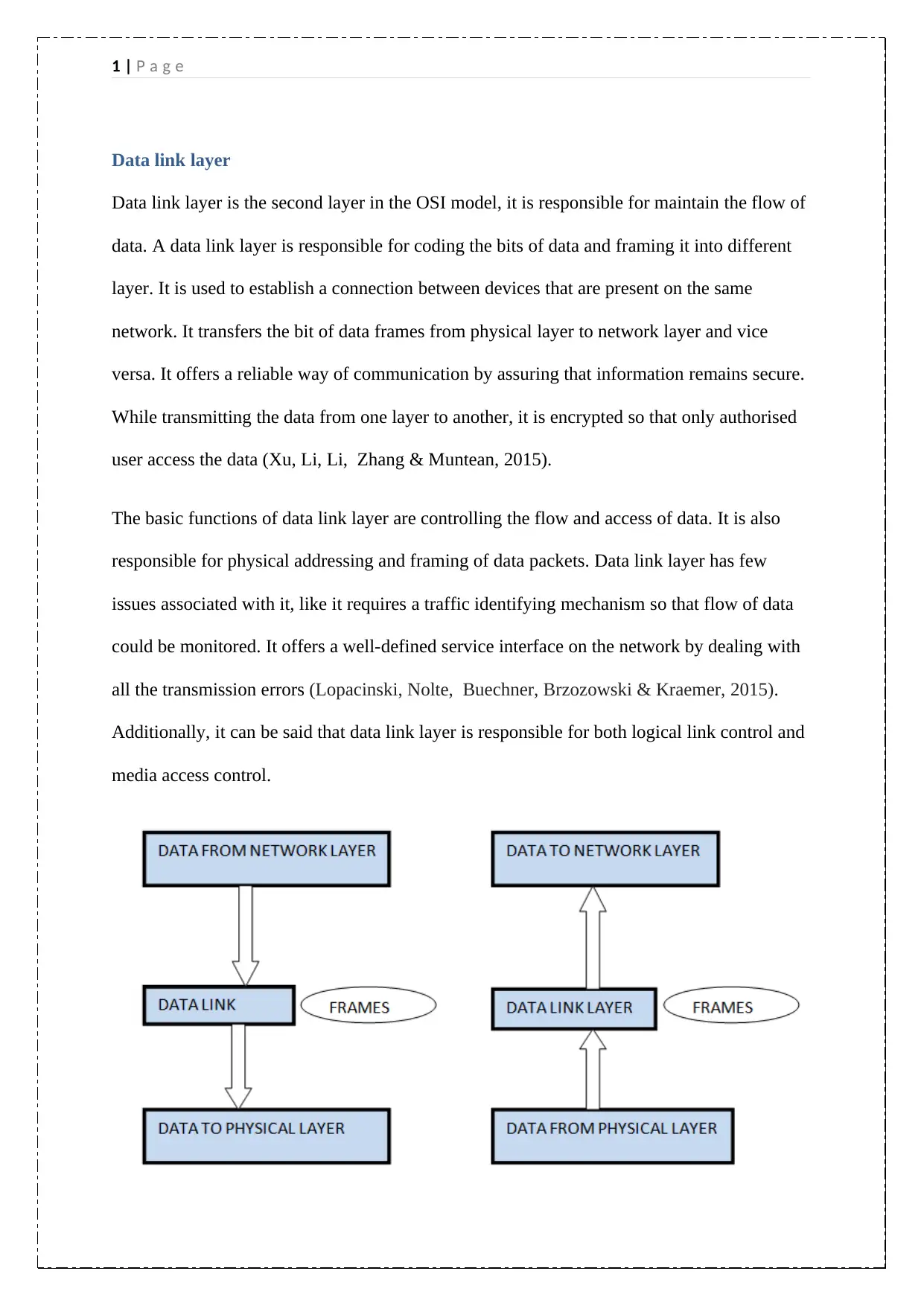
Data link layer
Data link layer is the second layer in the OSI model, it is responsible for maintain the flow of
data. A data link layer is responsible for coding the bits of data and framing it into different
layer. It is used to establish a connection between devices that are present on the same
network. It transfers the bit of data frames from physical layer to network layer and vice
versa. It offers a reliable way of communication by assuring that information remains secure.
While transmitting the data from one layer to another, it is encrypted so that only authorised
user access the data (Xu, Li, Li, Zhang & Muntean, 2015).
The basic functions of data link layer are controlling the flow and access of data. It is also
responsible for physical addressing and framing of data packets. Data link layer has few
issues associated with it, like it requires a traffic identifying mechanism so that flow of data
could be monitored. It offers a well-defined service interface on the network by dealing with
all the transmission errors (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer, 2015).
Additionally, it can be said that data link layer is responsible for both logical link control and
media access control.
Data link layer
Data link layer is the second layer in the OSI model, it is responsible for maintain the flow of
data. A data link layer is responsible for coding the bits of data and framing it into different
layer. It is used to establish a connection between devices that are present on the same
network. It transfers the bit of data frames from physical layer to network layer and vice
versa. It offers a reliable way of communication by assuring that information remains secure.
While transmitting the data from one layer to another, it is encrypted so that only authorised
user access the data (Xu, Li, Li, Zhang & Muntean, 2015).
The basic functions of data link layer are controlling the flow and access of data. It is also
responsible for physical addressing and framing of data packets. Data link layer has few
issues associated with it, like it requires a traffic identifying mechanism so that flow of data
could be monitored. It offers a well-defined service interface on the network by dealing with
all the transmission errors (Lopacinski, Nolte, Buechner, Brzozowski & Kraemer, 2015).
Additionally, it can be said that data link layer is responsible for both logical link control and
media access control.

2 | P a g e
(Source : https://masror.com/data-link-layer-osi-model/)
This layer is responsible for packing the data by encapsulating it into the frames. It also
maintains the synchronization of data at times of data transfer. Data link layer ensures flow
control by enabling the machines to exchange the information at high speed. Data link layers
transfers the frames from one layer to another it also prevent traffic jam.
Transport layer
Transport layer is used for server applications and allow access to information to user. It also
grants the access of multiplexing by allowing multiple users to access the information at the
same time (Rescorla, 2018). The service of transport layer is gained using datagram protocol.
The UDP packet of transport layer covers the address of source and destination. The UDP
packet also covers the checksum bit that is used to check whether the data is securely
transferred or not (Zhao, Sexton Park, Baure, Nino & So, 2015). If the checksum bit does not
match it can be found that some bugs have hit the system. Some of the functions that are
offered by transport layer are that it offers connection oriented communication by using
internet protocol and datagram protocol. In case of transport layer packets are not lost as they
are checked by using checksum bit that keeps an idea about arrival of packets from sender
and receiver.
(Source : https://masror.com/data-link-layer-osi-model/)
This layer is responsible for packing the data by encapsulating it into the frames. It also
maintains the synchronization of data at times of data transfer. Data link layer ensures flow
control by enabling the machines to exchange the information at high speed. Data link layers
transfers the frames from one layer to another it also prevent traffic jam.
Transport layer
Transport layer is used for server applications and allow access to information to user. It also
grants the access of multiplexing by allowing multiple users to access the information at the
same time (Rescorla, 2018). The service of transport layer is gained using datagram protocol.
The UDP packet of transport layer covers the address of source and destination. The UDP
packet also covers the checksum bit that is used to check whether the data is securely
transferred or not (Zhao, Sexton Park, Baure, Nino & So, 2015). If the checksum bit does not
match it can be found that some bugs have hit the system. Some of the functions that are
offered by transport layer are that it offers connection oriented communication by using
internet protocol and datagram protocol. In case of transport layer packets are not lost as they
are checked by using checksum bit that keeps an idea about arrival of packets from sender
and receiver.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3 | P a g e
(Source: http://fiberbit.com.tw/transport-layer-in-osi-networking-model-system-2/)
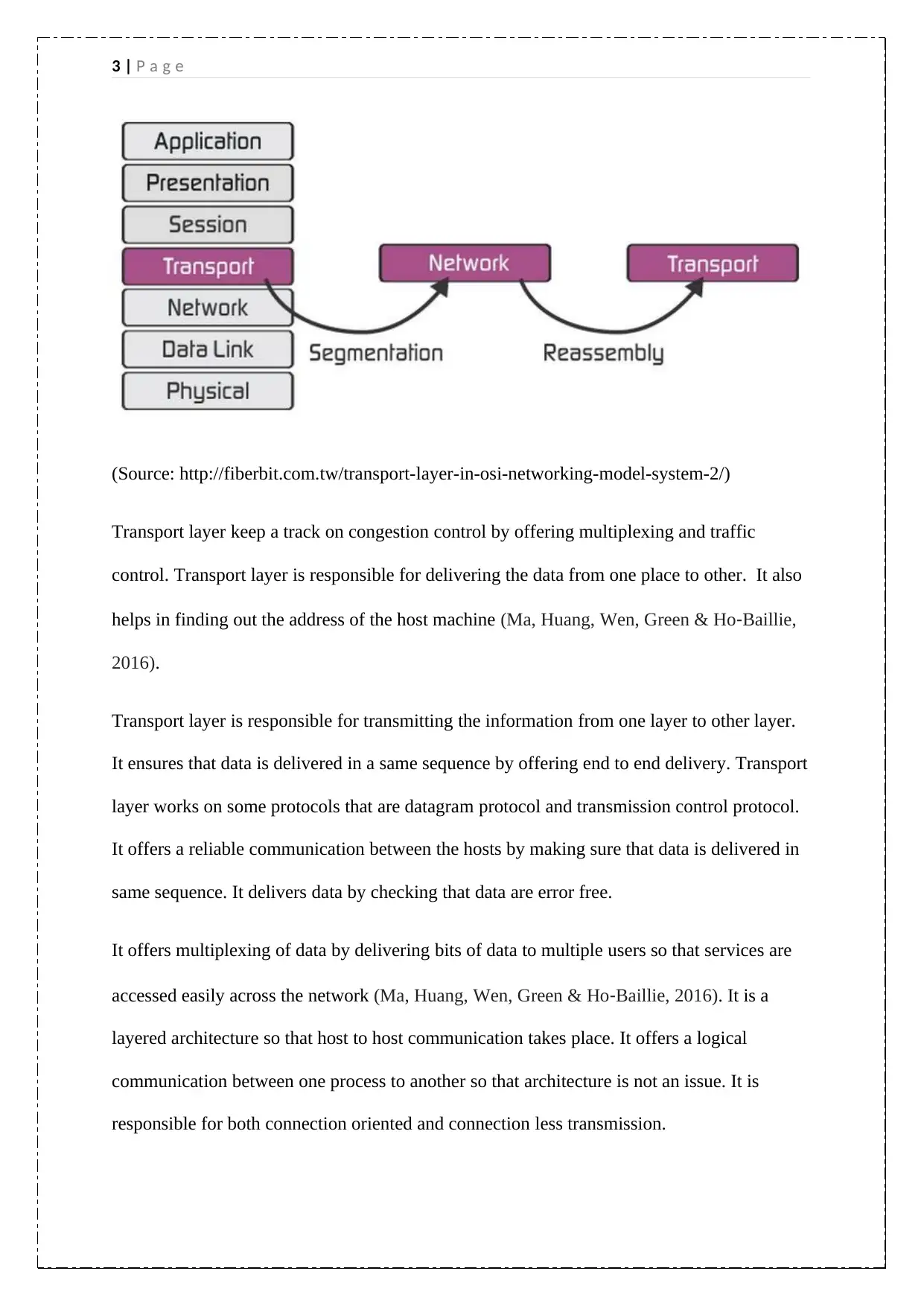
Transport layer keep a track on congestion control by offering multiplexing and traffic
control. Transport layer is responsible for delivering the data from one place to other. It also
helps in finding out the address of the host machine (Ma, Huang, Wen, Green & Ho‐Baillie,
2016).
Transport layer is responsible for transmitting the information from one layer to other layer.
It ensures that data is delivered in a same sequence by offering end to end delivery. Transport
layer works on some protocols that are datagram protocol and transmission control protocol.
It offers a reliable communication between the hosts by making sure that data is delivered in
same sequence. It delivers data by checking that data are error free.
It offers multiplexing of data by delivering bits of data to multiple users so that services are
accessed easily across the network (Ma, Huang, Wen, Green & Ho‐Baillie, 2016). It is a
layered architecture so that host to host communication takes place. It offers a logical
communication between one process to another so that architecture is not an issue. It is
responsible for both connection oriented and connection less transmission.
(Source: http://fiberbit.com.tw/transport-layer-in-osi-networking-model-system-2/)
Transport layer keep a track on congestion control by offering multiplexing and traffic
control. Transport layer is responsible for delivering the data from one place to other. It also
helps in finding out the address of the host machine (Ma, Huang, Wen, Green & Ho‐Baillie,
2016).
Transport layer is responsible for transmitting the information from one layer to other layer.
It ensures that data is delivered in a same sequence by offering end to end delivery. Transport
layer works on some protocols that are datagram protocol and transmission control protocol.
It offers a reliable communication between the hosts by making sure that data is delivered in
same sequence. It delivers data by checking that data are error free.
It offers multiplexing of data by delivering bits of data to multiple users so that services are
accessed easily across the network (Ma, Huang, Wen, Green & Ho‐Baillie, 2016). It is a
layered architecture so that host to host communication takes place. It offers a logical
communication between one process to another so that architecture is not an issue. It is
responsible for both connection oriented and connection less transmission.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4 | P a g e
Cloud computing and mobile
Cloud computing is a general term that is used for delivering services over the internet. It
allows company to consume resources by using virtual machine. Cloud computing offer
various benefits like it offer self-service resources to manage the workload. It also eliminates
the need of IT provisions to manage the resources (Ali, Khan & Vasilakos, 2015). It helps in
increasing the elasticity by improving the demand. The resources are used pay per use by
enabling users to manage the workloads (Botta, De Donato, Persico & Pescapé, 2016).
Cloud computing make the resources available by the third party and it reduces the capital
cost and expenses of infrastructure. It increases the overall speed as resources are accessed by
a single click. The other benefit of using cloud computing is that requires less power and
poor storage. It allows user to access he resources from any geographical location. It has
eliminated the need of IT team as it allow easy access so that business goals can be received.
There are different cloud networks that are public, private and hybrid. Public networks are
handled by third party user and there is no fixed control of a single individual. Private
networks are handled by a particular person that is used to store personal data. Hybrid
network on the other hand is the combination of both public as well as private network and it
is handled by government authority (Almorsy, Grundy & Müller, 2016). Cloud computing
offers various advantage like monitoring of applications, collaboration of content,
communication, storage, finance and other queries. The working operations of multinational
organisations have shifted from traditional networks to cloud based networks. The cloud
based services are divided into three forms that are IaaS, PaaS and Saas. It allows easy ways
to expand the services so that storage instances get increased. Cloud computing saves the
overall time and cost by offering them resources that could be used without actually
downloading them on the system. Security remains the only concern for businesses while
storing files over the network (Botta, De Donato, Persico & Pescapé, 2016). From the
Cloud computing and mobile
Cloud computing is a general term that is used for delivering services over the internet. It
allows company to consume resources by using virtual machine. Cloud computing offer
various benefits like it offer self-service resources to manage the workload. It also eliminates
the need of IT provisions to manage the resources (Ali, Khan & Vasilakos, 2015). It helps in
increasing the elasticity by improving the demand. The resources are used pay per use by
enabling users to manage the workloads (Botta, De Donato, Persico & Pescapé, 2016).
Cloud computing make the resources available by the third party and it reduces the capital
cost and expenses of infrastructure. It increases the overall speed as resources are accessed by
a single click. The other benefit of using cloud computing is that requires less power and
poor storage. It allows user to access he resources from any geographical location. It has
eliminated the need of IT team as it allow easy access so that business goals can be received.
There are different cloud networks that are public, private and hybrid. Public networks are
handled by third party user and there is no fixed control of a single individual. Private
networks are handled by a particular person that is used to store personal data. Hybrid
network on the other hand is the combination of both public as well as private network and it
is handled by government authority (Almorsy, Grundy & Müller, 2016). Cloud computing
offers various advantage like monitoring of applications, collaboration of content,
communication, storage, finance and other queries. The working operations of multinational
organisations have shifted from traditional networks to cloud based networks. The cloud
based services are divided into three forms that are IaaS, PaaS and Saas. It allows easy ways
to expand the services so that storage instances get increased. Cloud computing saves the
overall time and cost by offering them resources that could be used without actually
downloading them on the system. Security remains the only concern for businesses while
storing files over the network (Botta, De Donato, Persico & Pescapé, 2016). From the

5 | P a g e
research, it is found that cloud infrastructure relies on virtualization that means it offers
virtual software so that hardware’s can run over it.
research, it is found that cloud infrastructure relies on virtualization that means it offers
virtual software so that hardware’s can run over it.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6 | P a g e
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Lopacinski, L., Nolte, J., Buechner, S., Brzozowski, M., & Kraemer, R. (2015). 100 Gbps
wireless–data link layer VHDL implementation. Measurement Automation
Monitoring, 61.
Ma, Q., Huang, S., Wen, X., Green, M. A., & Ho‐Baillie, A. W. (2016). Hole transport layer
free inorganic CsPbIBr2 perovskite solar cell by dual source thermal
evaporation. Advanced Energy Materials, 6(7), 1502202.
Rescorla, E. (2018). The transport layer security (TLS) protocol version 1.3 (No. RFC 8446)
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Zhao, D., Sexton, M., Park, H. Y., Baure, G., Nino, J. C., & So, F. (2015). High‐Efficiency
Solution‐Processed Planar Perovskite Solar Cells with a Polymer Hole Transport
Layer. Advanced Energy Materials, 5(6), 1401855.
References
Ali, M., Khan, S. U., & Vasilakos, A. V. (2015). Security in cloud computing: Opportunities
and challenges. Information sciences, 305, 357-383.
Almorsy, M., Grundy, J., & Müller, I. (2016). An analysis of the cloud computing security
problem. arXiv preprint arXiv:1609.01107.
Botta, A., De Donato, W., Persico, V., & Pescapé, A. (2016). Integration of cloud computing
and internet of things: a survey. Future Generation Computer Systems, 56, 684-700.
Lopacinski, L., Nolte, J., Buechner, S., Brzozowski, M., & Kraemer, R. (2015). 100 Gbps
wireless–data link layer VHDL implementation. Measurement Automation
Monitoring, 61.
Ma, Q., Huang, S., Wen, X., Green, M. A., & Ho‐Baillie, A. W. (2016). Hole transport layer
free inorganic CsPbIBr2 perovskite solar cell by dual source thermal
evaporation. Advanced Energy Materials, 6(7), 1502202.
Rescorla, E. (2018). The transport layer security (TLS) protocol version 1.3 (No. RFC 8446)
Xu, C., Li, Z., Li, J., Zhang, H., & Muntean, G. M. (2015). Cross-layer fairness-driven
concurrent multipath video delivery over heterogeneous wireless networks. IEEE
Transactions on Circuits and Systems for Video Technology, 25(7), 1175-1189.
Zhao, D., Sexton, M., Park, H. Y., Baure, G., Nino, J. C., & So, F. (2015). High‐Efficiency
Solution‐Processed Planar Perovskite Solar Cells with a Polymer Hole Transport
Layer. Advanced Energy Materials, 5(6), 1401855.
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





