Comprehensive Report on HNC Unit 2 Networking: Principles and Devices
VerifiedAdded on 2024/05/13
|17
|3337
|326
Report
AI Summary
This report delves into networking principles and protocols, examining various network types such as PAN, LAN, MAN, WAN, and SAN, highlighting their benefits and constraints. It explains the impact of network topology, communication methods, and bandwidth requirements on network performance. The report also compares common networking principles and discusses how protocols enhance the effectiveness of networked systems. Furthermore, it explores the operating principles of networking devices like bridges, modems, hubs, switches, routers, and gateways, along with different server types. The interdependence of workstation hardware and networking software is also discussed, culminating in a justification for server selection based on cost and performance optimization. This document is available on Desklib, a platform offering AI-based study tools and solved assignments for students.

Unit 02
Networking
Networking
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction................................................................................................................................3
LO1 Examine networking principles and their protocols..........................................................4
P1 Discuss the benefits and constraints of different network types and standards................4
P2 Explain the impact of network topology, communication and bandwidth requirements. 9
M1 Compare common networking principles and how protocols enable the effectiveness of
networked system.................................................................................................................10
LO2 Explain networking devices and operations....................................................................11
P3 Discuss the operating principles of networking devices and server types......................11
P4 Discuss the inter-dependence of workstation hardware with relevant networking
software................................................................................................................................13
M2 Explore a range of server types and justify the selection of a server, considering a
given scenario regarding cost and performance optimisation..............................................14
Conclusion................................................................................................................................15
References................................................................................................................................16
List of Figures
Figure 1. Personal area network.................................................................................................4
Figure 2. Local area network.....................................................................................................5
Figure 3 Metropolitan area network...........................................................................................6
Figure 4 Wide area network.......................................................................................................7
Figure 5 Storage area network...................................................................................................8
Figure 6: IEEE 802 Standards....................................................................................................8
Figure 7 Network topology........................................................................................................9
Introduction................................................................................................................................3
LO1 Examine networking principles and their protocols..........................................................4
P1 Discuss the benefits and constraints of different network types and standards................4
P2 Explain the impact of network topology, communication and bandwidth requirements. 9
M1 Compare common networking principles and how protocols enable the effectiveness of
networked system.................................................................................................................10
LO2 Explain networking devices and operations....................................................................11
P3 Discuss the operating principles of networking devices and server types......................11
P4 Discuss the inter-dependence of workstation hardware with relevant networking
software................................................................................................................................13
M2 Explore a range of server types and justify the selection of a server, considering a
given scenario regarding cost and performance optimisation..............................................14
Conclusion................................................................................................................................15
References................................................................................................................................16
List of Figures
Figure 1. Personal area network.................................................................................................4
Figure 2. Local area network.....................................................................................................5
Figure 3 Metropolitan area network...........................................................................................6
Figure 4 Wide area network.......................................................................................................7
Figure 5 Storage area network...................................................................................................8
Figure 6: IEEE 802 Standards....................................................................................................8
Figure 7 Network topology........................................................................................................9

Introduction
The networking is a data communication between the two networks using different protocols
for changing the way business and the daily work. The computer networks are capable of
sending and receiving the data from one node to another node using network devices which
connects from the communication channel.
The computer network is a telecommunication channel which the user uses it for connecting
the device to the same network and is also known as a data network. The network must meet
certain criteria’s such as:-
Performance of the system
Reliability of the data on the network
Scalability of the network.
The computer network measures a performance time like transit time and response time
which check whether the performance is accurate. The properties of a good network depend
on the following:-
Interpersonal communication when we communicate with each other it should be
efficient and easy so that the person communicating with us can understand and all these
are possible because of a computer network.
Resources can be shared as it is available on the network which can be accessed by
anyone in the network.
Sharing files and data only the authorised user will be allowed to share the file on the
network.
Based on this thing the above report is divided into two section. In first section, the
discussion is done regarding the protocols and the principles that are associated with the
network. In the first section different standards and types of network is done.
In the second section, the discussion is done regarding the operations of the networking
devices. Also in this section, the discussion of the interdependence is done in between the
networking hardware and software.
The networking is a data communication between the two networks using different protocols
for changing the way business and the daily work. The computer networks are capable of
sending and receiving the data from one node to another node using network devices which
connects from the communication channel.
The computer network is a telecommunication channel which the user uses it for connecting
the device to the same network and is also known as a data network. The network must meet
certain criteria’s such as:-
Performance of the system
Reliability of the data on the network
Scalability of the network.
The computer network measures a performance time like transit time and response time
which check whether the performance is accurate. The properties of a good network depend
on the following:-
Interpersonal communication when we communicate with each other it should be
efficient and easy so that the person communicating with us can understand and all these
are possible because of a computer network.
Resources can be shared as it is available on the network which can be accessed by
anyone in the network.
Sharing files and data only the authorised user will be allowed to share the file on the
network.
Based on this thing the above report is divided into two section. In first section, the
discussion is done regarding the protocols and the principles that are associated with the
network. In the first section different standards and types of network is done.
In the second section, the discussion is done regarding the operations of the networking
devices. Also in this section, the discussion of the interdependence is done in between the
networking hardware and software.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LO1 Examine networking principles and their protocols.
P1 Discuss the benefits and constraints of different network types and standards.
Networking is the process through which we can communicate from one source to other.
Networking can be classified into different types such as:-
1. PAN (Personal area network)- it is the smallest wireless type of networking which is
used as modem, phone, tablets etc. and rotate around a single person in one building.
These types of network are found a small organisation and house which is managed by
only one person.
Figure 1. Personal area network
Source-(Dhola, 2015)
Benefits of PAN:
It is very cost effective, we don’t need any extra wire for establishing the communication.
It is very easy to and there is no advanced setup.
It is very reliable and can connect data within the range of 10m from your network.
It is secure as only the authorized person can share the data.
Constraints of PAN:
It is costly as we need digital devices for communicating such as smartphone, laptops etc.
The infrared signals travel in a straight line.
2. LAN (local area network) - It is also designed for a small area like a factory, small office
or organisation. LANs are also used for troubleshooting because it is easily designed and
P1 Discuss the benefits and constraints of different network types and standards.
Networking is the process through which we can communicate from one source to other.
Networking can be classified into different types such as:-
1. PAN (Personal area network)- it is the smallest wireless type of networking which is
used as modem, phone, tablets etc. and rotate around a single person in one building.
These types of network are found a small organisation and house which is managed by
only one person.
Figure 1. Personal area network
Source-(Dhola, 2015)
Benefits of PAN:
It is very cost effective, we don’t need any extra wire for establishing the communication.
It is very easy to and there is no advanced setup.
It is very reliable and can connect data within the range of 10m from your network.
It is secure as only the authorized person can share the data.
Constraints of PAN:
It is costly as we need digital devices for communicating such as smartphone, laptops etc.
The infrared signals travel in a straight line.
2. LAN (local area network) - It is also designed for a small area like a factory, small office
or organisation. LANs are also used for troubleshooting because it is easily designed and
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
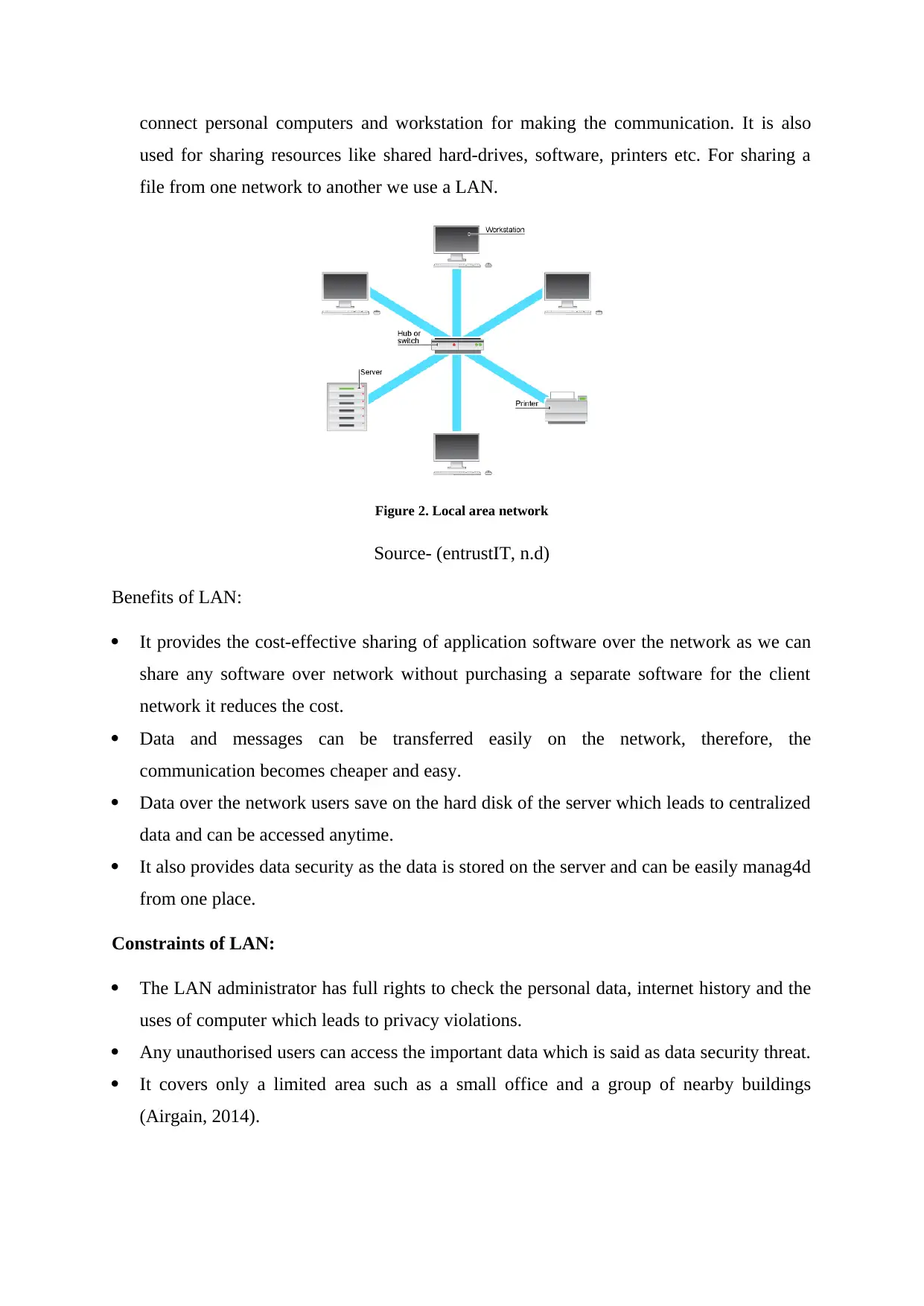
connect personal computers and workstation for making the communication. It is also
used for sharing resources like shared hard-drives, software, printers etc. For sharing a
file from one network to another we use a LAN.
Figure 2. Local area network
Source- (entrustIT, n.d)
Benefits of LAN:
It provides the cost-effective sharing of application software over the network as we can
share any software over network without purchasing a separate software for the client
network it reduces the cost.
Data and messages can be transferred easily on the network, therefore, the
communication becomes cheaper and easy.
Data over the network users save on the hard disk of the server which leads to centralized
data and can be accessed anytime.
It also provides data security as the data is stored on the server and can be easily manag4d
from one place.
Constraints of LAN:
The LAN administrator has full rights to check the personal data, internet history and the
uses of computer which leads to privacy violations.
Any unauthorised users can access the important data which is said as data security threat.
It covers only a limited area such as a small office and a group of nearby buildings
(Airgain, 2014).
used for sharing resources like shared hard-drives, software, printers etc. For sharing a
file from one network to another we use a LAN.
Figure 2. Local area network
Source- (entrustIT, n.d)
Benefits of LAN:
It provides the cost-effective sharing of application software over the network as we can
share any software over network without purchasing a separate software for the client
network it reduces the cost.
Data and messages can be transferred easily on the network, therefore, the
communication becomes cheaper and easy.
Data over the network users save on the hard disk of the server which leads to centralized
data and can be accessed anytime.
It also provides data security as the data is stored on the server and can be easily manag4d
from one place.
Constraints of LAN:
The LAN administrator has full rights to check the personal data, internet history and the
uses of computer which leads to privacy violations.
Any unauthorised users can access the important data which is said as data security threat.
It covers only a limited area such as a small office and a group of nearby buildings
(Airgain, 2014).
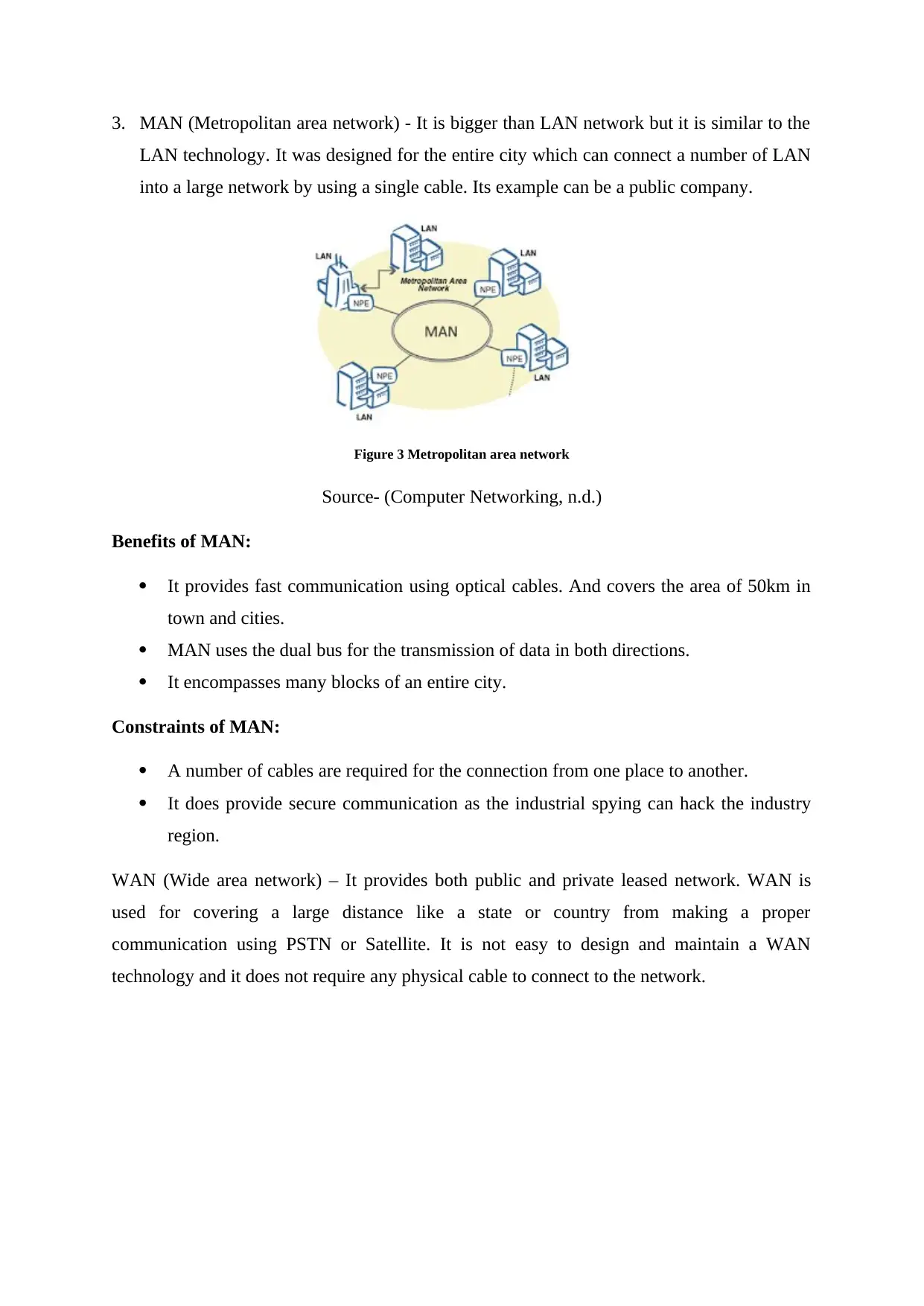
3. MAN (Metropolitan area network) - It is bigger than LAN network but it is similar to the
LAN technology. It was designed for the entire city which can connect a number of LAN
into a large network by using a single cable. Its example can be a public company.
Figure 3 Metropolitan area network
Source- (Computer Networking, n.d.)
Benefits of MAN:
It provides fast communication using optical cables. And covers the area of 50km in
town and cities.
MAN uses the dual bus for the transmission of data in both directions.
It encompasses many blocks of an entire city.
Constraints of MAN:
A number of cables are required for the connection from one place to another.
It does provide secure communication as the industrial spying can hack the industry
region.
WAN (Wide area network) – It provides both public and private leased network. WAN is
used for covering a large distance like a state or country from making a proper
communication using PSTN or Satellite. It is not easy to design and maintain a WAN
technology and it does not require any physical cable to connect to the network.
LAN technology. It was designed for the entire city which can connect a number of LAN
into a large network by using a single cable. Its example can be a public company.
Figure 3 Metropolitan area network
Source- (Computer Networking, n.d.)
Benefits of MAN:
It provides fast communication using optical cables. And covers the area of 50km in
town and cities.
MAN uses the dual bus for the transmission of data in both directions.
It encompasses many blocks of an entire city.
Constraints of MAN:
A number of cables are required for the connection from one place to another.
It does provide secure communication as the industrial spying can hack the industry
region.
WAN (Wide area network) – It provides both public and private leased network. WAN is
used for covering a large distance like a state or country from making a proper
communication using PSTN or Satellite. It is not easy to design and maintain a WAN
technology and it does not require any physical cable to connect to the network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
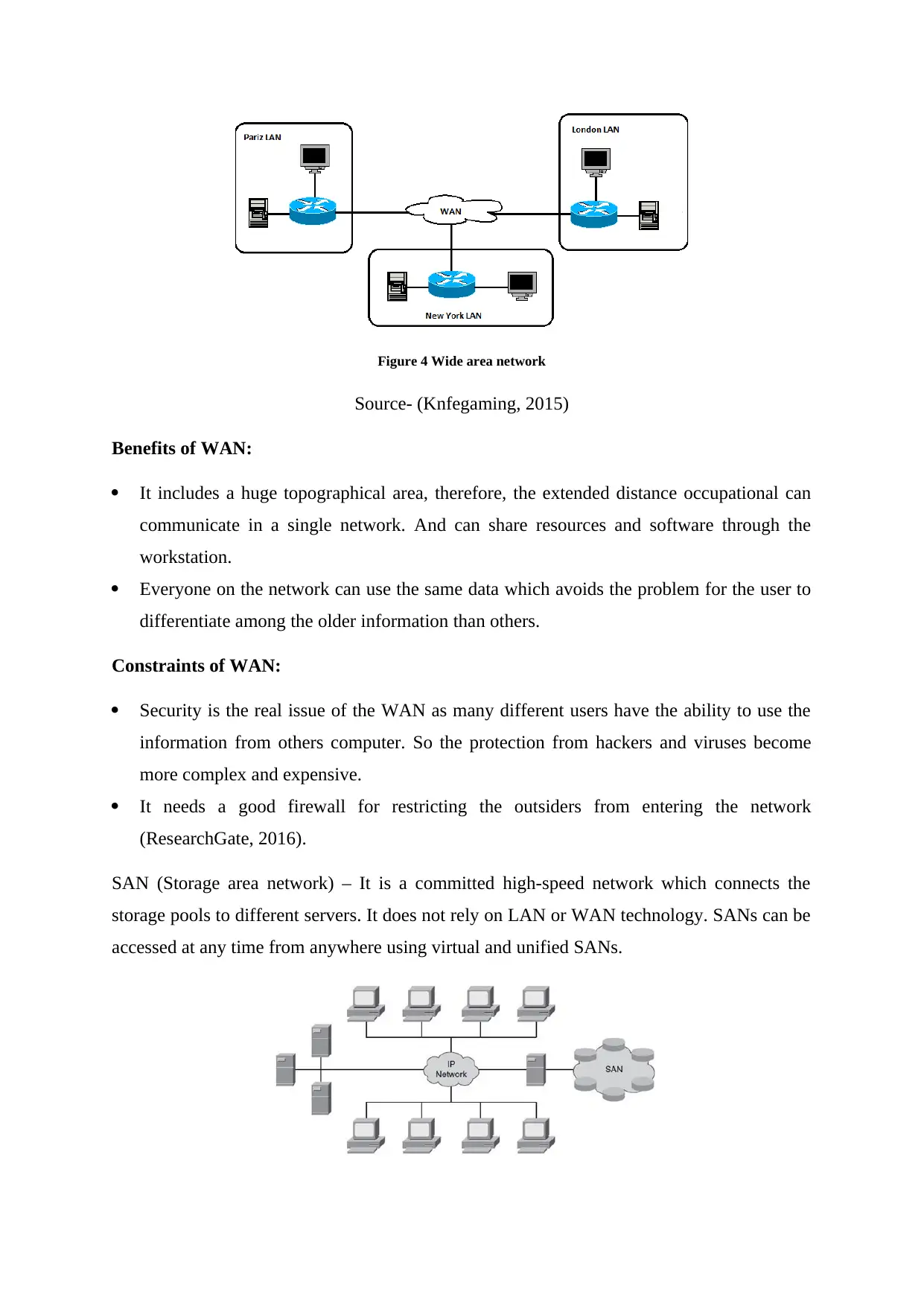
Figure 4 Wide area network
Source- (Knfegaming, 2015)
Benefits of WAN:
It includes a huge topographical area, therefore, the extended distance occupational can
communicate in a single network. And can share resources and software through the
workstation.
Everyone on the network can use the same data which avoids the problem for the user to
differentiate among the older information than others.
Constraints of WAN:
Security is the real issue of the WAN as many different users have the ability to use the
information from others computer. So the protection from hackers and viruses become
more complex and expensive.
It needs a good firewall for restricting the outsiders from entering the network
(ResearchGate, 2016).
SAN (Storage area network) – It is a committed high-speed network which connects the
storage pools to different servers. It does not rely on LAN or WAN technology. SANs can be
accessed at any time from anywhere using virtual and unified SANs.
Source- (Knfegaming, 2015)
Benefits of WAN:
It includes a huge topographical area, therefore, the extended distance occupational can
communicate in a single network. And can share resources and software through the
workstation.
Everyone on the network can use the same data which avoids the problem for the user to
differentiate among the older information than others.
Constraints of WAN:
Security is the real issue of the WAN as many different users have the ability to use the
information from others computer. So the protection from hackers and viruses become
more complex and expensive.
It needs a good firewall for restricting the outsiders from entering the network
(ResearchGate, 2016).
SAN (Storage area network) – It is a committed high-speed network which connects the
storage pools to different servers. It does not rely on LAN or WAN technology. SANs can be
accessed at any time from anywhere using virtual and unified SANs.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Figure 5 Storage area network
Source- (Siemon, n.d)
Benefits of SAN:
The SAN provides high-speed disk technology for storing data at a speed which exceed 5
Gbps.
It also provides a centralized backup by storing the stored data on local disk.
Constraints of SAN:
It is costly to set up a SAN technology.
It is complex and difficult to manage the SAN technology.
By taking the help of the standards the development of the network can be done in a
fundamental manner. Also through this thing, the compatibility of the product can be
increased through these standards. Different standards which are issued by IEEE which and
can be used in the network are shown below:
Figure 6: IEEE 802 Standards
Source- (Siemon, n.d)
Benefits of SAN:
The SAN provides high-speed disk technology for storing data at a speed which exceed 5
Gbps.
It also provides a centralized backup by storing the stored data on local disk.
Constraints of SAN:
It is costly to set up a SAN technology.
It is complex and difficult to manage the SAN technology.
By taking the help of the standards the development of the network can be done in a
fundamental manner. Also through this thing, the compatibility of the product can be
increased through these standards. Different standards which are issued by IEEE which and
can be used in the network are shown below:
Figure 6: IEEE 802 Standards
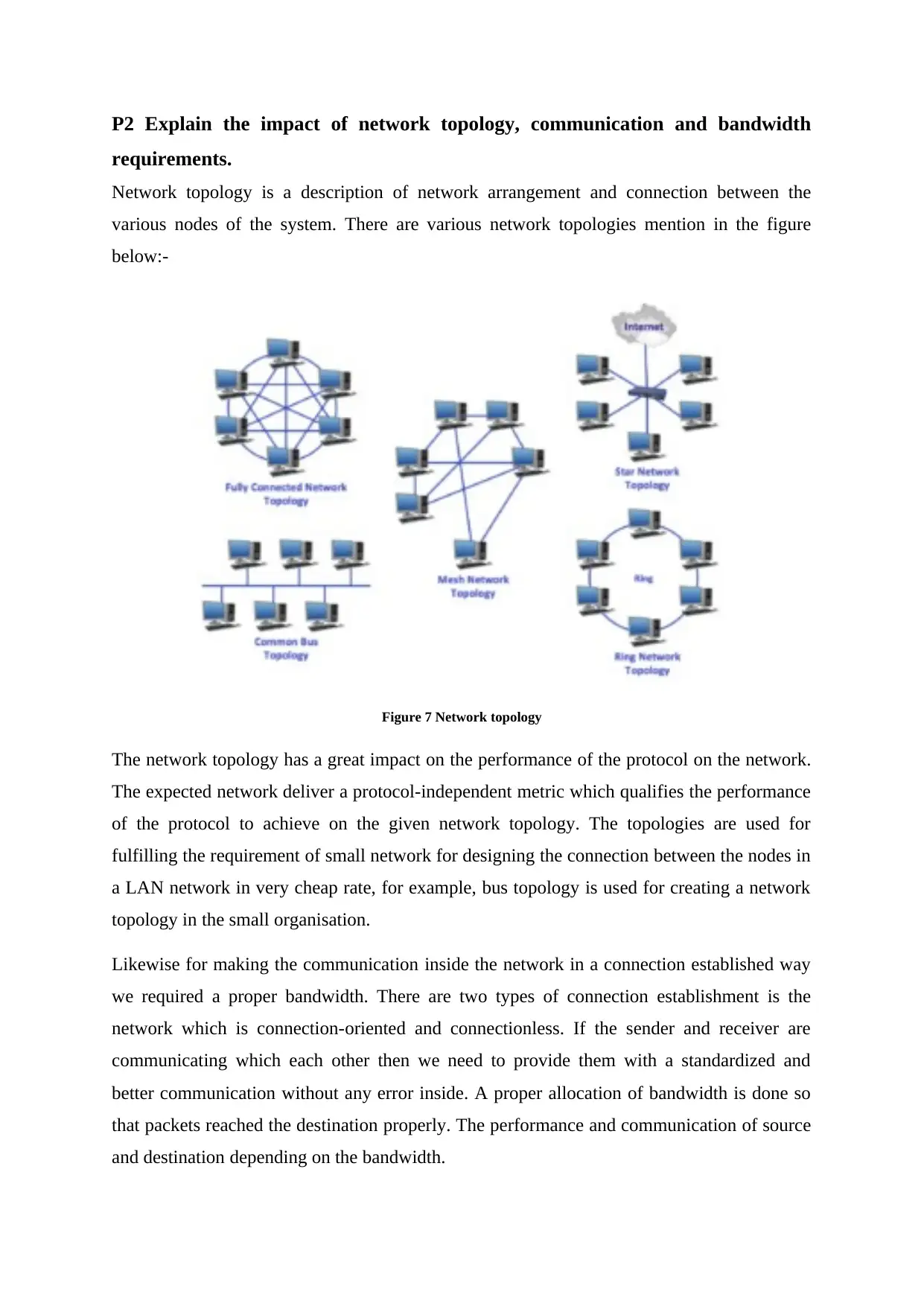
P2 Explain the impact of network topology, communication and bandwidth
requirements.
Network topology is a description of network arrangement and connection between the
various nodes of the system. There are various network topologies mention in the figure
below:-
Figure 7 Network topology
The network topology has a great impact on the performance of the protocol on the network.
The expected network deliver a protocol-independent metric which qualifies the performance
of the protocol to achieve on the given network topology. The topologies are used for
fulfilling the requirement of small network for designing the connection between the nodes in
a LAN network in very cheap rate, for example, bus topology is used for creating a network
topology in the small organisation.
Likewise for making the communication inside the network in a connection established way
we required a proper bandwidth. There are two types of connection establishment is the
network which is connection-oriented and connectionless. If the sender and receiver are
communicating which each other then we need to provide them with a standardized and
better communication without any error inside. A proper allocation of bandwidth is done so
that packets reached the destination properly. The performance and communication of source
and destination depending on the bandwidth.
requirements.
Network topology is a description of network arrangement and connection between the
various nodes of the system. There are various network topologies mention in the figure
below:-
Figure 7 Network topology
The network topology has a great impact on the performance of the protocol on the network.
The expected network deliver a protocol-independent metric which qualifies the performance
of the protocol to achieve on the given network topology. The topologies are used for
fulfilling the requirement of small network for designing the connection between the nodes in
a LAN network in very cheap rate, for example, bus topology is used for creating a network
topology in the small organisation.
Likewise for making the communication inside the network in a connection established way
we required a proper bandwidth. There are two types of connection establishment is the
network which is connection-oriented and connectionless. If the sender and receiver are
communicating which each other then we need to provide them with a standardized and
better communication without any error inside. A proper allocation of bandwidth is done so
that packets reached the destination properly. The performance and communication of source
and destination depending on the bandwidth.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

M1 Compare common networking principles and how protocols enable the
effectiveness of networked system.
The network principles are Packet Transmission which transmits the packets between the
source and the destination by using the asynchronous transmission protocols. Other is Data
streaming which is used for multimedia data streaming at higher bandwidth and frequency
with continuous flow rate. Example network: ATM, IPv6, resource reverse protocol etc
(NetworkLessons, 2017).
In switching method, there are four kinds of method which the network used:-
Broadcasting the packets
Circuit switching for interconnecting the circuit segments.
Packet switching for developing the advanced processors and storage spaces.
Frame relay for streaming small packets.
Protocol is implemented for specifying the sequences of a message transmitted and in which
format. The protocol communicates in peer-to-peer transmission across encapsulated method
over the physical medium. Each protocol includes the protocol stack while receiving the
packets. The networking principles rotate on the OSI protocol which has a layered
architecture such as:-
Application layer
Presentation layer
Session layer
Transport layer
Network layer
Data link layer
Physical layer
The basic networking principle is: - understanding the user need and designing the network
for a roaming user base. It also accessed a wider service for the department.
effectiveness of networked system.
The network principles are Packet Transmission which transmits the packets between the
source and the destination by using the asynchronous transmission protocols. Other is Data
streaming which is used for multimedia data streaming at higher bandwidth and frequency
with continuous flow rate. Example network: ATM, IPv6, resource reverse protocol etc
(NetworkLessons, 2017).
In switching method, there are four kinds of method which the network used:-
Broadcasting the packets
Circuit switching for interconnecting the circuit segments.
Packet switching for developing the advanced processors and storage spaces.
Frame relay for streaming small packets.
Protocol is implemented for specifying the sequences of a message transmitted and in which
format. The protocol communicates in peer-to-peer transmission across encapsulated method
over the physical medium. Each protocol includes the protocol stack while receiving the
packets. The networking principles rotate on the OSI protocol which has a layered
architecture such as:-
Application layer
Presentation layer
Session layer
Transport layer
Network layer
Data link layer
Physical layer
The basic networking principle is: - understanding the user need and designing the network
for a roaming user base. It also accessed a wider service for the department.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO2 Explain networking devices and operations
P3 Discuss the operating principles of networking devices and server types.
Networking devices are those devices which are used in networking. Combination of various
networking devices and computer system makes a network infrastructure. List of the
commonly used networking devices is given below:
Bridge: it is used to connect two different types of subnetworks. It works at data link
layer.
Modem: it is a combination of modulator and demodulator.
Hub: It is used to connect hosts and transfer data. It acts as a multiport repeater. Hub
doesn’t have collision domain so, it sends a message to all connected ports. Thus, it is
considered less secure and slower.
Switch: Switch is more secure than a hub because it filters the packets based on the MAC
address and forwards accordingly to only the intended receiver. It acts as a multiport
bridge. It works at data link layer. It also performs error checking. It has multiple
collision domains but only a single broadcast domain.
Repeater: It is used to strengthen the signal by regenerating it. It works at physical layer.
It is used to send a signal to a long distance without reducing its quality.
Router: It is a layer 3 device. It is used to connect devices between different network. It
performs filtering on the basis of IP address. It uses different routing protocols to route
the packets between source and destination.
Gateways: It is a way to connect networks. It acts as a messenger agent. It is considered
as complex networking device (Shekhar, 2018).
Whereas as the name suggests server is used to provides some set of services to clients. There
are different types of servers such as a print server, mail server, file server etc. These devices
have high processing power and high capabilities. Client makes a request for a particular
service and server provide that.
There are different types of servers in networking:
Print server: It is used to manage the printer requests and queues. It processes printer
related jobs. It receives the printing requests and sends them to a suitable printer.
P3 Discuss the operating principles of networking devices and server types.
Networking devices are those devices which are used in networking. Combination of various
networking devices and computer system makes a network infrastructure. List of the
commonly used networking devices is given below:
Bridge: it is used to connect two different types of subnetworks. It works at data link
layer.
Modem: it is a combination of modulator and demodulator.
Hub: It is used to connect hosts and transfer data. It acts as a multiport repeater. Hub
doesn’t have collision domain so, it sends a message to all connected ports. Thus, it is
considered less secure and slower.
Switch: Switch is more secure than a hub because it filters the packets based on the MAC
address and forwards accordingly to only the intended receiver. It acts as a multiport
bridge. It works at data link layer. It also performs error checking. It has multiple
collision domains but only a single broadcast domain.
Repeater: It is used to strengthen the signal by regenerating it. It works at physical layer.
It is used to send a signal to a long distance without reducing its quality.
Router: It is a layer 3 device. It is used to connect devices between different network. It
performs filtering on the basis of IP address. It uses different routing protocols to route
the packets between source and destination.
Gateways: It is a way to connect networks. It acts as a messenger agent. It is considered
as complex networking device (Shekhar, 2018).
Whereas as the name suggests server is used to provides some set of services to clients. There
are different types of servers such as a print server, mail server, file server etc. These devices
have high processing power and high capabilities. Client makes a request for a particular
service and server provide that.
There are different types of servers in networking:
Print server: It is used to manage the printer requests and queues. It processes printer
related jobs. It receives the printing requests and sends them to a suitable printer.

Proxy server: It is used to filter the incoming requests and helps to increase the
performance. It works between web browser and external server.
Mail server: Mail server provides mail services to clients. It uses DHCP, POP3 and IMAP
protocols. It is used to share and store the mails
DNS server: it acts as a database to store domain names and corresponding IP. It helps to
convert domain name into IP and vice-versa.
File server. It is used to securely transfer files between computers. It acts as a centralized
server for all the connected computers.
Web server: it is used to download and upload the files from the internet. It uses HTTP
and HTTPS protocol.
A server uses an operating system which manages it. It acts as a layer between hardware and
software of the server. These OS particularly designed for the servers. For example windows
server 2008/2012/1016, Linux, RHEL etc.
performance. It works between web browser and external server.
Mail server: Mail server provides mail services to clients. It uses DHCP, POP3 and IMAP
protocols. It is used to share and store the mails
DNS server: it acts as a database to store domain names and corresponding IP. It helps to
convert domain name into IP and vice-versa.
File server. It is used to securely transfer files between computers. It acts as a centralized
server for all the connected computers.
Web server: it is used to download and upload the files from the internet. It uses HTTP
and HTTPS protocol.
A server uses an operating system which manages it. It acts as a layer between hardware and
software of the server. These OS particularly designed for the servers. For example windows
server 2008/2012/1016, Linux, RHEL etc.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



