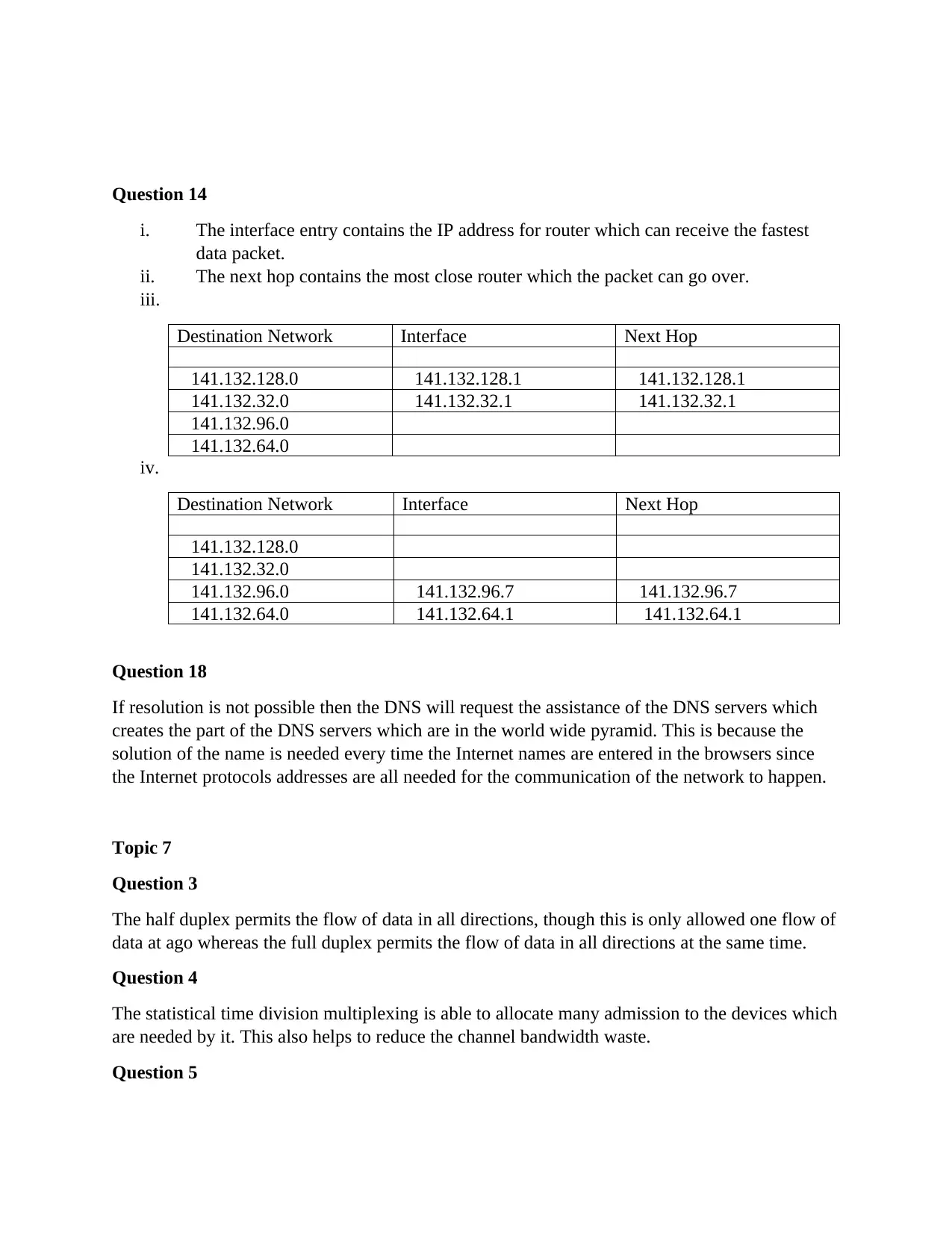
ITECH1102: Analysis of Networking Security Concepts and Protocols
VerifiedAdded on 2021/05/31
|5
|829
|27
Homework Assignment
AI Summary
This assignment solution addresses various networking security concepts and protocols. It begins by comparing peer-to-peer networks to larger networks, highlighting their administration differences. The solution then dissects the ITECH1102 application client program protocol, detailing its structure, including flags, addresses, control, information, and FCS. It explains how the ping program functions using the TCP/IP protocol to determine network delays and the use of MAC addresses in the data link layer for accurate communication. Furthermore, the assignment includes examples of IP and MAC addresses. It explains the role of DNS servers and the process of resolution, followed by a comparison of half and full duplex communication. The solution also touches upon statistical time division multiplexing and Manchester encoding, explaining how they improve bandwidth utilization and data transmission. Finally, the solution discusses the application of terrestrial microwave links.
1 out of 5











![[object Object]](/_next/static/media/star-bottom.7253800d.svg)