Comprehensive Review of Networking Protocols and Concepts Task
VerifiedAdded on 2023/04/23
|8
|1390
|97
Homework Assignment
AI Summary
This assignment delves into fundamental networking concepts and protocols, beginning with an explanation of the 'traceroute' command and its utility in discovering network routes. It covers IPv4 addressing, detailing its structure and subnet masks. The assignment further explores advanced features of network switches, such as port security and VLANs, and emphasizes the importance of physical security for networking devices. Data encryption methods, including IPsec and Kerberos, are discussed as crucial for network security. The document also contrasts circuit switching and packet switching methods, using POTS and ISDN as examples of circuit-switched networks. Finally, it explains the role of hypervisors in managing virtual machines and provides an overview of operating systems, highlighting their core components like file systems and kernels. Desklib provides access to this and other solved assignments to aid students in their studies.
Running Head: NETWORKING 0
Networking
Individual task
Student name
Networking
Individual task
Student name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking 1
Table of Contents
Week -1............................................................................................................................................2
Answer – 1:......................................................................................................................................2
Week -2............................................................................................................................................3
Answer – 2:......................................................................................................................................3
Week -3............................................................................................................................................4
Answer – 3:......................................................................................................................................4
Week - 4...........................................................................................................................................4
Answer – 4:......................................................................................................................................4
Week - 5...........................................................................................................................................5
Answer – 5:......................................................................................................................................5
References........................................................................................................................................6
Table of Contents
Week -1............................................................................................................................................2
Answer – 1:......................................................................................................................................2
Week -2............................................................................................................................................3
Answer – 2:......................................................................................................................................3
Week -3............................................................................................................................................4
Answer – 3:......................................................................................................................................4
Week - 4...........................................................................................................................................4
Answer – 4:......................................................................................................................................4
Week - 5...........................................................................................................................................5
Answer – 5:......................................................................................................................................5
References........................................................................................................................................6

Networking 2
Week -1
Answer – 1:
Trace route is a windows command and it is used for discover the routes, which is selected by
packet for reaching at destination. The networking device or computer systems send out a
sequence of UDP data grams at the remote host. It sends three datagrams; each datagram is
having a Time-To-Live field, which is set to one. It does this by sending Internet Control
Message Protocol (ICMP) Echo Request messages to the destination (Cowley, 2012).
Every router sends an ICMP Time Exceeded Message (TEM). Each time TTL increased by 1 and
it is easier to scan all the router for that destination. However, in the end, maximum value of
TTL means packet is not valid and it will discard by the router, which reduce the traffic in the
network (Dye, et al., 2007).
This command has different options for specific purpose, such as –d is used for prevents tracert
from resolving IP to host names.
In figure, www.google.com.au is tracing by tracert command over a maximum of 30 hops. It is
showing different 15 routes, which are connected with this hostname. There are five fields, first
is showing number of routes, second, third, and fourth field is used for TTL and fifth field is
showing the IP addresses of different hosts. 172.217.25.131 is Google IP address from one of
the Google IP’s (Forouzan, 2007).
Question: What is IPv4 addressing?
Answer: IP addresses are used 32 bits for providing a number to the network device. It is divided
in four octets; each octet is having 8 bits, which is having a value from 0 to 255. It is having a
subnet masks, which is describing about network ID, and host ID for a specific network. As an
example 192.168.10.250 is a IP and it have subnet mast, which is 255.255.255.0.
Week -1
Answer – 1:
Trace route is a windows command and it is used for discover the routes, which is selected by
packet for reaching at destination. The networking device or computer systems send out a
sequence of UDP data grams at the remote host. It sends three datagrams; each datagram is
having a Time-To-Live field, which is set to one. It does this by sending Internet Control
Message Protocol (ICMP) Echo Request messages to the destination (Cowley, 2012).
Every router sends an ICMP Time Exceeded Message (TEM). Each time TTL increased by 1 and
it is easier to scan all the router for that destination. However, in the end, maximum value of
TTL means packet is not valid and it will discard by the router, which reduce the traffic in the
network (Dye, et al., 2007).
This command has different options for specific purpose, such as –d is used for prevents tracert
from resolving IP to host names.
In figure, www.google.com.au is tracing by tracert command over a maximum of 30 hops. It is
showing different 15 routes, which are connected with this hostname. There are five fields, first
is showing number of routes, second, third, and fourth field is used for TTL and fifth field is
showing the IP addresses of different hosts. 172.217.25.131 is Google IP address from one of
the Google IP’s (Forouzan, 2007).
Question: What is IPv4 addressing?
Answer: IP addresses are used 32 bits for providing a number to the network device. It is divided
in four octets; each octet is having 8 bits, which is having a value from 0 to 255. It is having a
subnet masks, which is describing about network ID, and host ID for a specific network. As an
example 192.168.10.250 is a IP and it have subnet mast, which is 255.255.255.0.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking 3
Week -2
Answer – 2:
MAC Address Port #
00-25-2A-00-01-B3 4
00-25-2A-00-10-3F 3
00-25-2A-00-AA-2B 2
00-25-2A-00-11-1D 5
00-25-2A-00-10-1B 5
Switch – 1
Question: Explain about advanced features of network switches?
Answer: Smart switches are used for making network more reliable and it makes network more
efficient (Ghosekar, et al., 2010). Smart switches are also known as high-speed switches. They
are having these features:
1. Port security
2. Spanning tree protocol
3. Virtual local area networks
4. Multicast processing
Week -2
Answer – 2:
MAC Address Port #
00-25-2A-00-01-B3 4
00-25-2A-00-10-3F 3
00-25-2A-00-AA-2B 2
00-25-2A-00-11-1D 5
00-25-2A-00-10-1B 5
Switch – 1
Question: Explain about advanced features of network switches?
Answer: Smart switches are used for making network more reliable and it makes network more
efficient (Ghosekar, et al., 2010). Smart switches are also known as high-speed switches. They
are having these features:
1. Port security
2. Spanning tree protocol
3. Virtual local area networks
4. Multicast processing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking 4
Week -3
Answer – 3:
Physical security is also necessary for the networking devices, such as switches, wireless access
points and wiring for networking. They are so important for any network. Physical locations
should have EMI-free environment, locks, Adequate-cooling measures, and adequate power
supply (Techdonut, 2018). Locking cabinets are also helpful for providing security to the
network devices. Wiring should be inaccessible to eavesdropping equipment. All the devices
should have recovery from disasters, such as floods (Kenneth C. Mansfield & Antonakos, 2009).
Question: How can secure the data in the network through encryption?
Answer: Encryption is beneficial for securing data through prevention, such as prevents people
from using packet sniffer to capture data. It is also provide security to the data, if some can have
physical access of computer system. IP security (IPsec) is highly used for encrypting data for
transmission in the network. Kerberos is a good example of encryption technology (Lammle,
2011).
Week - 4
Answer – 4:
Circuit switching is creating a temporary connection between sender and receiver for data
transmission. Circuit switched network are available everywhere easily. They are pronging
dedicated bandwidth to the sender and receiver for their data transmission. It is having low cost
for implementation. As an example, POTS and ISDN are best example of circuit switched
networks, which are used by WAN connection (Mitchell, 2018).
Packet switched method is providing virtual circuits for data transfer. It takes charge for
providing bandwidth only by the clients. In this method, bandwidth is shared with other users,
which is a security issue (Mukherjee, et al., 2014).
Week -3
Answer – 3:
Physical security is also necessary for the networking devices, such as switches, wireless access
points and wiring for networking. They are so important for any network. Physical locations
should have EMI-free environment, locks, Adequate-cooling measures, and adequate power
supply (Techdonut, 2018). Locking cabinets are also helpful for providing security to the
network devices. Wiring should be inaccessible to eavesdropping equipment. All the devices
should have recovery from disasters, such as floods (Kenneth C. Mansfield & Antonakos, 2009).
Question: How can secure the data in the network through encryption?
Answer: Encryption is beneficial for securing data through prevention, such as prevents people
from using packet sniffer to capture data. It is also provide security to the data, if some can have
physical access of computer system. IP security (IPsec) is highly used for encrypting data for
transmission in the network. Kerberos is a good example of encryption technology (Lammle,
2011).
Week - 4
Answer – 4:
Circuit switching is creating a temporary connection between sender and receiver for data
transmission. Circuit switched network are available everywhere easily. They are pronging
dedicated bandwidth to the sender and receiver for their data transmission. It is having low cost
for implementation. As an example, POTS and ISDN are best example of circuit switched
networks, which are used by WAN connection (Mitchell, 2018).
Packet switched method is providing virtual circuits for data transfer. It takes charge for
providing bandwidth only by the clients. In this method, bandwidth is shared with other users,
which is a security issue (Mukherjee, et al., 2014).
Networking 5
Question: explain about leased line connection.
Answer: it is a dedicated connection, which is provided by the service provider. It is permanent
link for data transfer. SONET is an example of leased line connection. It is secure and reliable
connection. It is so expensive (Sunshine, 2013).
Week - 5
Answer – 5:
Hypervisor are providing a monitoring facility for hardware equipment. It allows multiple virtual
machines to share physical hardware resources. It is having two types, which are type-1, and
type-2.
Type – 1 is run directly on the host computer’s hardware and controls. It is used for monitor
guest operating system. It is also called bare-metal virtualization.
Type – 2 is installed in installed in a host machine and it will allow accessing the host hardware
on behalf of guest operating system.
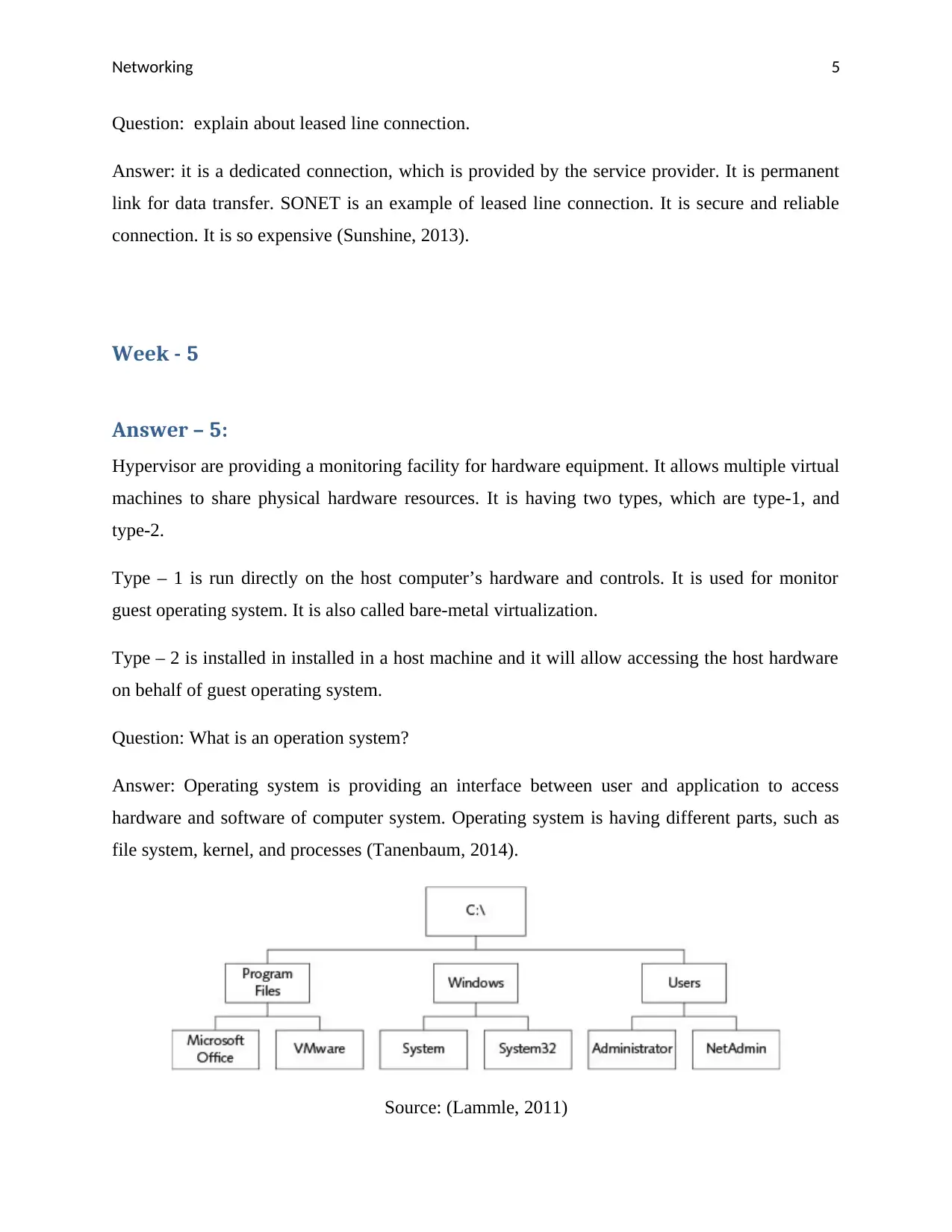
Question: What is an operation system?
Answer: Operating system is providing an interface between user and application to access
hardware and software of computer system. Operating system is having different parts, such as
file system, kernel, and processes (Tanenbaum, 2014).
Source: (Lammle, 2011)
Question: explain about leased line connection.
Answer: it is a dedicated connection, which is provided by the service provider. It is permanent
link for data transfer. SONET is an example of leased line connection. It is secure and reliable
connection. It is so expensive (Sunshine, 2013).
Week - 5
Answer – 5:
Hypervisor are providing a monitoring facility for hardware equipment. It allows multiple virtual
machines to share physical hardware resources. It is having two types, which are type-1, and
type-2.
Type – 1 is run directly on the host computer’s hardware and controls. It is used for monitor
guest operating system. It is also called bare-metal virtualization.
Type – 2 is installed in installed in a host machine and it will allow accessing the host hardware
on behalf of guest operating system.
Question: What is an operation system?
Answer: Operating system is providing an interface between user and application to access
hardware and software of computer system. Operating system is having different parts, such as
file system, kernel, and processes (Tanenbaum, 2014).
Source: (Lammle, 2011)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Networking 6
File system is having a hierarchy, which are shows in above diagram.
References
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Ghosekar, P., Katkar, G. & Ghorpade, P., 2010. Mobile ad hoc networking: imperatives and
challenges. IJCA Special issue on MANETs, Volume 3, pp. 153-158.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana: John
Wiley & Sons.
Mitchell, B., 2018. What Is Computer Networking?. [Online]
Available at: https://www.lifewire.com/what-is-computer-networking-816249
[Accessed 16 January 2019].
Mukherjee, . A., Fakoorian, S. A. A., Huang, J. & Swindlehurst, A. L., 2014. Principles of
physical layer security in multiuser wireless networks: A survey. A survey. IEEE
Communications Surveys & Tutorials, 16(3), pp. 1550-1576.
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
Techdonut, 2018. Network management tasks. [Online]
Available at: https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
File system is having a hierarchy, which are shows in above diagram.
References
Cowley, J., 2012. Communications and Networking. 2 ed. kingswinford: Springer Science &
Business Media.
Dye, M., McDonald, R. & Rufi, A., 2007. Network Fundamentals, CCNA Exploration
Companion Guide. Indianapolis: Cisco press..
Forouzan, A. B., 2007. Data communications & networking. 8th ed. New Delhi: Tata McGraw-
Hill Education.
Ghosekar, P., Katkar, G. & Ghorpade, P., 2010. Mobile ad hoc networking: imperatives and
challenges. IJCA Special issue on MANETs, Volume 3, pp. 153-158.
Kenneth C. Mansfield, J. & Antonakos, J. L., 2009. Computer Networking for LANS to WANS:
Hardware, Software and Security. 1 ed. Bostan(MA): Cengage Learning.
Lammle, T., 2011. CCNA Cisco Certified Network Associate Deluxe Study Guide. indiana: John
Wiley & Sons.
Mitchell, B., 2018. What Is Computer Networking?. [Online]
Available at: https://www.lifewire.com/what-is-computer-networking-816249
[Accessed 16 January 2019].
Mukherjee, . A., Fakoorian, S. A. A., Huang, J. & Swindlehurst, A. L., 2014. Principles of
physical layer security in multiuser wireless networks: A survey. A survey. IEEE
Communications Surveys & Tutorials, 16(3), pp. 1550-1576.
Sunshine, C. A., 2013. Computer network architectures and protocols. New Jersy: Springer
Science & Business Media.
Tanenbaum, A. S., 2014. Computer networks. Harlow, Essex: Pearson.
Techdonut, 2018. Network management tasks. [Online]
Available at: https://www.techdonut.co.uk/buy-and-manage-it/regular-it-maintenance/network-
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Networking 7
management-tasks
[Accessed 29 08 2018].
management-tasks
[Accessed 29 08 2018].
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





