Networking Infrastructure: Network Types, Topologies, and Protocols
VerifiedAdded on 2021/06/30
|26
|8992
|888
Report
AI Summary
This report delves into the fundamentals of networking infrastructure, exploring various network types like LAN, MAN, and WAN, along with their respective benefits and limitations. It examines network protocols such as TCP/IP, FTP, HTTP, and DNS, highlighting their roles in data transmission and communication. The report also analyzes different network topologies, including bus, ring, star, mesh, tree, and hybrid, discussing their structures and impacts on network performance. Furthermore, it covers the operating principles of networking devices such as routers and switches, and server types, as well as the interdependence of workstation hardware and networking software. The document provides a comprehensive overview of networking concepts, essential for understanding the complexities of modern network systems.
ASSIGNMENT 1 FRONT SHEET
Qualification BTEC Level 5 HND Diploma in Computing
Unit number and title Unit 2: Networking Infrastructure
Submission date Date Received 1st submission
Re-submission Date Date Received 2nd submission
Student Name Đoàn Nhật Quang Student ID GCD18518
Class GCD0901 Assessor name Đặng Quan
Student declaration
I certify that the assignment submission is entirely my own work and I fully understand the consequences of plag
making a false declaration is a form of malpractice.
Student’s signature
Grading grid
P1 P2 P3 P4 M1 M2 D1
Qualification BTEC Level 5 HND Diploma in Computing
Unit number and title Unit 2: Networking Infrastructure
Submission date Date Received 1st submission
Re-submission Date Date Received 2nd submission
Student Name Đoàn Nhật Quang Student ID GCD18518
Class GCD0901 Assessor name Đặng Quan
Student declaration
I certify that the assignment submission is entirely my own work and I fully understand the consequences of plag
making a false declaration is a form of malpractice.
Student’s signature
Grading grid
P1 P2 P3 P4 M1 M2 D1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
❒ Summative Feedback: ❒ Resubmission Feedback:
Grade: Assessor Signature: Date:
Lecturer Signature:
Grade: Assessor Signature: Date:
Lecturer Signature:

Contents
I. Discuss the benefits and constraints of different network types and standards ............................................ 3
1. Network ............................................................................................................................................................ 3
2. Network types .................................................................................................................................................. 3
3. Network protocol ............................................................................................................................................. 5
4. International standard organizations ............................................................................................................ 8
II. Explain the impact of network topology, communication and bandwidth requirements. ........................ 9
1. Network topology............................................................................................................................................. 9
2. Physical topology ........................................................................................................................................... 10
3. Logical topology ............................................................................................................................................. 10
4. The difference between physical topology and logical topology ................................................................ 10
5. Examples of popular topologies ................................................................................................................... 11
6. Network communication ............................................................................................................................... 17
III. Discuss the operating principles of networking devices and server types ................................................ 20
1. Network devices ............................................................................................................................................. 20
2. Servers ............................................................................................................................................................ 23
IV. Discuss the inter-dependence of workstation hardware with relevant networking software. ................ 23
References ................................................................................................................................................................... 25
Figures
Figure 1 Working model of LAN .................................................................................................................................. 3
Figure 2 Network connection MAN .............................................................................................................................. 4
Figure 3 WAN connection............................................................................................................................................. 5
Figure 4 Bus Topology ................................................................................................................................................ 11
Figure 5 Ring Topology .............................................................................................................................................. 13
Figure 6 Star Topology ................................................................................................................................................ 14
Figure 7 Mesh Topology ............................................................................................................................................. 15
Figure 8 Tree Topology .............................................................................................................................................. 16
Figure 9 Hybrid Topology ........................................................................................................................................... 17
Figure 10 the model in the net shop ............................................................................................................................ 24
I. Discuss the benefits and constraints of different network types and standards ............................................ 3
1. Network ............................................................................................................................................................ 3
2. Network types .................................................................................................................................................. 3
3. Network protocol ............................................................................................................................................. 5
4. International standard organizations ............................................................................................................ 8
II. Explain the impact of network topology, communication and bandwidth requirements. ........................ 9
1. Network topology............................................................................................................................................. 9
2. Physical topology ........................................................................................................................................... 10
3. Logical topology ............................................................................................................................................. 10
4. The difference between physical topology and logical topology ................................................................ 10
5. Examples of popular topologies ................................................................................................................... 11
6. Network communication ............................................................................................................................... 17
III. Discuss the operating principles of networking devices and server types ................................................ 20
1. Network devices ............................................................................................................................................. 20
2. Servers ............................................................................................................................................................ 23
IV. Discuss the inter-dependence of workstation hardware with relevant networking software. ................ 23
References ................................................................................................................................................................... 25
Figures
Figure 1 Working model of LAN .................................................................................................................................. 3
Figure 2 Network connection MAN .............................................................................................................................. 4
Figure 3 WAN connection............................................................................................................................................. 5
Figure 4 Bus Topology ................................................................................................................................................ 11
Figure 5 Ring Topology .............................................................................................................................................. 13
Figure 6 Star Topology ................................................................................................................................................ 14
Figure 7 Mesh Topology ............................................................................................................................................. 15
Figure 8 Tree Topology .............................................................................................................................................. 16
Figure 9 Hybrid Topology ........................................................................................................................................... 17
Figure 10 the model in the net shop ............................................................................................................................ 24
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
I. Discuss the benefits and constraints of different network types and
standards
1. Network
In information technology, a network is defined as the connection of at least two computer systems, either
by cable or wireless connection. The simplest network is a combination of two computers connected by
cable. This type of network is called a peer-to-peer network. There is no hierarchy in this network; both
participants have the same privileges. Each computer has access to the other's data and can share resources
like disk space, applications, or peripherals (printers, etc.).
Networks today tend to be a bit more complex and consist of more than just two computers. Systems with
more than ten participants typically use a client-server network. In these networks, a central computer
(server) provides resources to other participants in the network (client).
2. Network types
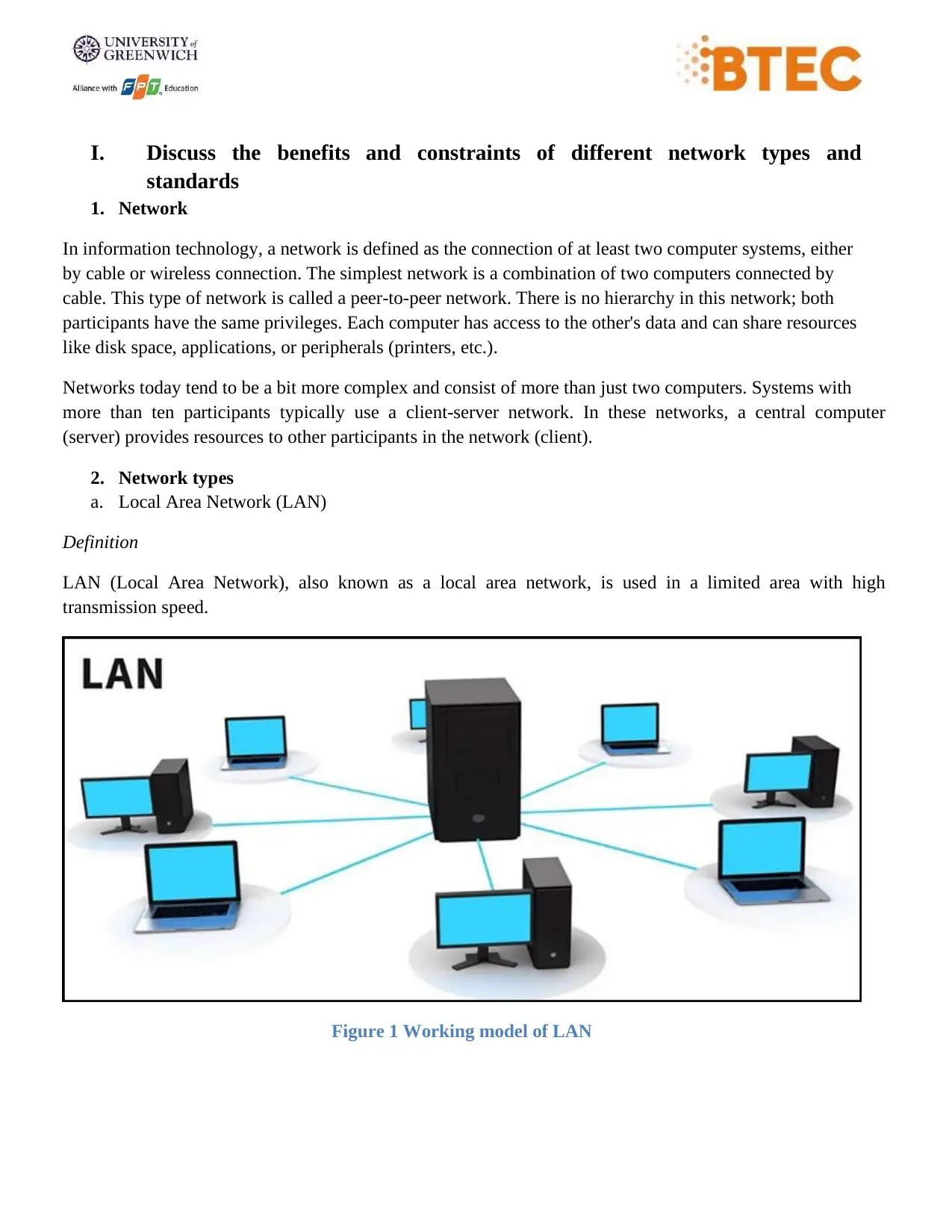
a. Local Area Network (LAN)
Definition
LAN (Local Area Network), also known as a local area network, is used in a limited area with high
transmission speed.
Figure 1 Working model of LAN
standards
1. Network
In information technology, a network is defined as the connection of at least two computer systems, either
by cable or wireless connection. The simplest network is a combination of two computers connected by
cable. This type of network is called a peer-to-peer network. There is no hierarchy in this network; both
participants have the same privileges. Each computer has access to the other's data and can share resources
like disk space, applications, or peripherals (printers, etc.).
Networks today tend to be a bit more complex and consist of more than just two computers. Systems with
more than ten participants typically use a client-server network. In these networks, a central computer
(server) provides resources to other participants in the network (client).
2. Network types
a. Local Area Network (LAN)
Definition
LAN (Local Area Network), also known as a local area network, is used in a limited area with high
transmission speed.
Figure 1 Working model of LAN
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Devices using LAN can share resources with each other, typically sharing files, printers, ... and some other
devices.
Advantages
High transmission speed, support to connect many devices quickly. Although limited in connection range,
it costs less, uses less wires, and is easy to administer.
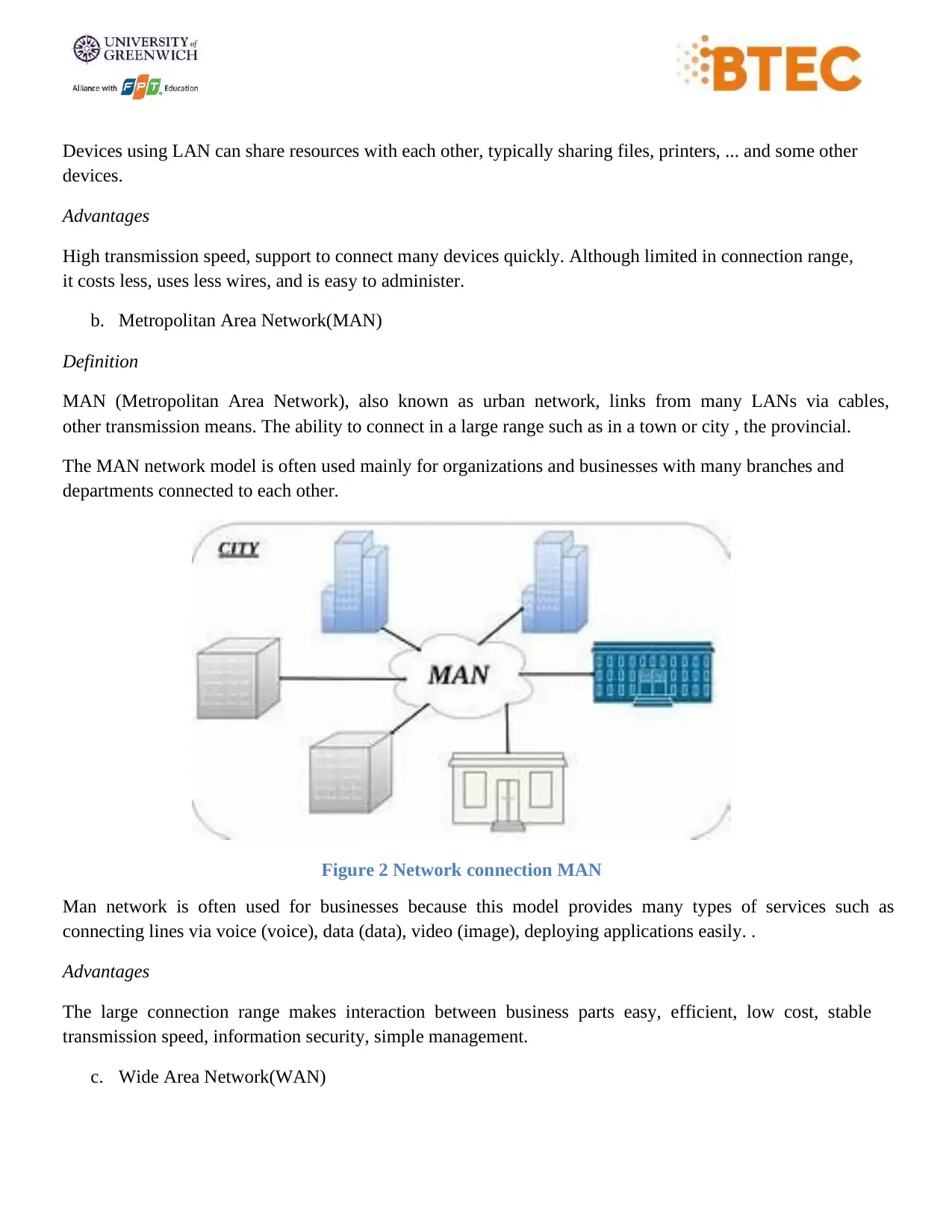
b. Metropolitan Area Network(MAN)
Definition
MAN (Metropolitan Area Network), also known as urban network, links from many LANs via cables,
other transmission means. The ability to connect in a large range such as in a town or city , the provincial.
The MAN network model is often used mainly for organizations and businesses with many branches and
departments connected to each other.
Figure 2 Network connection MAN
Man network is often used for businesses because this model provides many types of services such as
connecting lines via voice (voice), data (data), video (image), deploying applications easily. .
Advantages
The large connection range makes interaction between business parts easy, efficient, low cost, stable
transmission speed, information security, simple management.
c. Wide Area Network(WAN)
devices.
Advantages
High transmission speed, support to connect many devices quickly. Although limited in connection range,
it costs less, uses less wires, and is easy to administer.
b. Metropolitan Area Network(MAN)
Definition
MAN (Metropolitan Area Network), also known as urban network, links from many LANs via cables,
other transmission means. The ability to connect in a large range such as in a town or city , the provincial.
The MAN network model is often used mainly for organizations and businesses with many branches and
departments connected to each other.
Figure 2 Network connection MAN
Man network is often used for businesses because this model provides many types of services such as
connecting lines via voice (voice), data (data), video (image), deploying applications easily. .
Advantages
The large connection range makes interaction between business parts easy, efficient, low cost, stable
transmission speed, information security, simple management.
c. Wide Area Network(WAN)
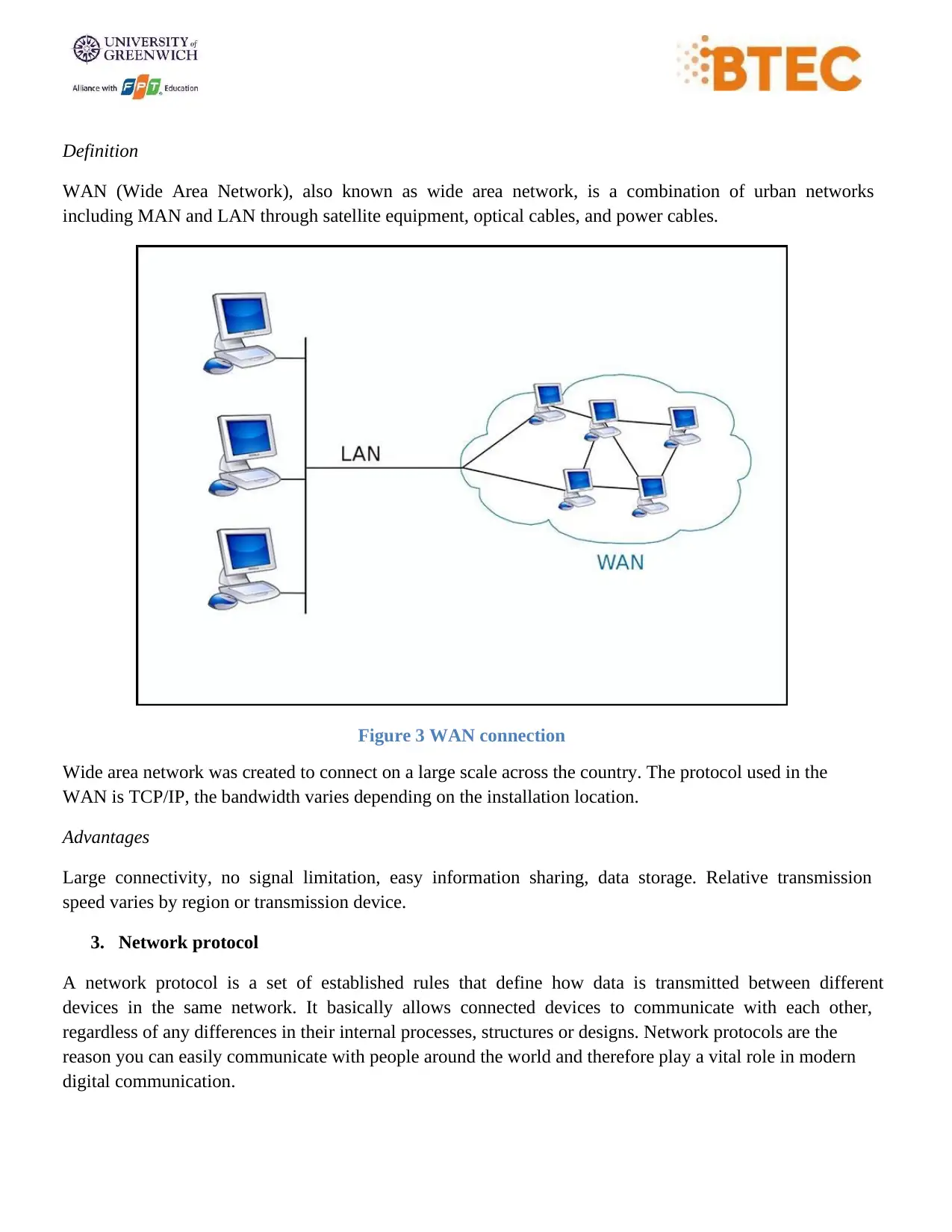
Definition
WAN (Wide Area Network), also known as wide area network, is a combination of urban networks
including MAN and LAN through satellite equipment, optical cables, and power cables.
Figure 3 WAN connection
Wide area network was created to connect on a large scale across the country. The protocol used in the
WAN is TCP/IP, the bandwidth varies depending on the installation location.
Advantages
Large connectivity, no signal limitation, easy information sharing, data storage. Relative transmission
speed varies by region or transmission device.
3. Network protocol
A network protocol is a set of established rules that define how data is transmitted between different
devices in the same network. It basically allows connected devices to communicate with each other,
regardless of any differences in their internal processes, structures or designs. Network protocols are the
reason you can easily communicate with people around the world and therefore play a vital role in modern
digital communication.
WAN (Wide Area Network), also known as wide area network, is a combination of urban networks
including MAN and LAN through satellite equipment, optical cables, and power cables.
Figure 3 WAN connection
Wide area network was created to connect on a large scale across the country. The protocol used in the
WAN is TCP/IP, the bandwidth varies depending on the installation location.
Advantages
Large connectivity, no signal limitation, easy information sharing, data storage. Relative transmission
speed varies by region or transmission device.
3. Network protocol
A network protocol is a set of established rules that define how data is transmitted between different
devices in the same network. It basically allows connected devices to communicate with each other,
regardless of any differences in their internal processes, structures or designs. Network protocols are the
reason you can easily communicate with people around the world and therefore play a vital role in modern
digital communication.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Similar to how speaking the same language simplifies communication between two people, network
protocols make it possible for devices to interact with each other due to predefined rules built into the
device's software and hardware suffer. Neither a local area network (LAN) nor a wide area network
(WAN) could function as it does today without the use of network protocols.
a. List common protocol
1. Internet Protocol: IP works similarly to a postal service. When users send and receive data from their
devices, the data is concatenated into packets, like messages with two IP addresses: one for the sender and
one for the recipient. After the packet leaves the sender, it goes to a port, like a post office, directing it in
the appropriate direction. Packets continue to move through the ports until they reach their destination.
IP is often paired with TCP to form TCP/IP, the overall set of internet protocols. Together, IP sends
packets to their destination and TCP arranges the packets in the correct order, as IP sometimes sends
packets out of order to ensure packets go the fastest way.
2. Transmission control protocol: TCP is the other half of TCP/IP and puts packets in order so that IP can
deliver them. specifically, TCP numbers individual packets because IP can send packets to their
destination through different routes and make them out of order, so TCP modifies this before IP delivers
packets .
TCP also detects errors during sending - including the lack of any packets based on TCP's numbering
system - and asks IP to retransmit those packets before IP delivers the data to its destination. Through this
process, the TCP/IP suite controls the communication on the internet
3. File Transfer Protocol: FTP is a client-server protocol, with which a client requests a file and the server
supplies it. FTP runs over TCP/IP -- a suite of communications protocols -- and requires a command
channel and a data channel to communicate and exchange files, respectively. Clients request files through
the command channel and receive access to download, edit and copy the file, among other actions,
through the data channel.
FTP has grown less popular as most systems began to use HTTP for file sharing. However, FTP is a
common network protocol for more private file sharing, such as in banking.
4. Hypertext Transfer Protocol: Like FTP, HTTP is a file sharing protocol that runs over TCP/IP, although
HTTP's superiority works across web browsers and is generally recognizable to most users. When a user
visits a website domain and wants to access that domain, HTTP provides access. HTTP connects to the
domain's server and requests the web page's HTML, which is the code that structures and displays the
design of the page.
protocols make it possible for devices to interact with each other due to predefined rules built into the
device's software and hardware suffer. Neither a local area network (LAN) nor a wide area network
(WAN) could function as it does today without the use of network protocols.
a. List common protocol
1. Internet Protocol: IP works similarly to a postal service. When users send and receive data from their
devices, the data is concatenated into packets, like messages with two IP addresses: one for the sender and
one for the recipient. After the packet leaves the sender, it goes to a port, like a post office, directing it in
the appropriate direction. Packets continue to move through the ports until they reach their destination.
IP is often paired with TCP to form TCP/IP, the overall set of internet protocols. Together, IP sends
packets to their destination and TCP arranges the packets in the correct order, as IP sometimes sends
packets out of order to ensure packets go the fastest way.
2. Transmission control protocol: TCP is the other half of TCP/IP and puts packets in order so that IP can
deliver them. specifically, TCP numbers individual packets because IP can send packets to their
destination through different routes and make them out of order, so TCP modifies this before IP delivers
packets .
TCP also detects errors during sending - including the lack of any packets based on TCP's numbering
system - and asks IP to retransmit those packets before IP delivers the data to its destination. Through this
process, the TCP/IP suite controls the communication on the internet
3. File Transfer Protocol: FTP is a client-server protocol, with which a client requests a file and the server
supplies it. FTP runs over TCP/IP -- a suite of communications protocols -- and requires a command
channel and a data channel to communicate and exchange files, respectively. Clients request files through
the command channel and receive access to download, edit and copy the file, among other actions,
through the data channel.
FTP has grown less popular as most systems began to use HTTP for file sharing. However, FTP is a
common network protocol for more private file sharing, such as in banking.
4. Hypertext Transfer Protocol: Like FTP, HTTP is a file sharing protocol that runs over TCP/IP, although
HTTP's superiority works across web browsers and is generally recognizable to most users. When a user
visits a website domain and wants to access that domain, HTTP provides access. HTTP connects to the
domain's server and requests the web page's HTML, which is the code that structures and displays the
design of the page.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Another form of HTTP is HTTPS, which stands for HTTP over Secure Sockets Layer or HTTP Secure.
HTTPS can encrypt user web pages and HTTP requests. This provides greater security for users and can
prevent common cybersecurity threats, such as man-in-the-middle attacks.
5. Domain name system: DNS is a database that includes a website's domain name, which people use to
access the website, and its corresponding IP addresses, which devices use to locate the website. DNS
translates the domain name into IP addresses, and these translations are included within the DNS. Servers
can cache DNS data, which is required to access the websites. DNS also includes the DNS protocol, which
is within the IP suite and details the specifications DNS uses to translate and communicate.
DNS is important because it can quickly provide users with information, as well as access to remote hosts
and resources across the internet.
6. Dynamic Host Configuration Protocol: DHCP assigns IP addresses to network endpoints so they can
communicate with other network endpoints over IP. Whenever a device joins a network with a DHCP
server for the first time, DHCP automatically assigns it a new IP address and continues to do so each time
a device moves locations on the network.
When a device connects to a network, a DHCP handshake takes place, where the device and DHCP server
communicate. The device establishes a connection; the server receives it and provides available IP
addresses; the device requests an IP address; and the server confirm it to complete the process
7. Simple mail transfer protocol: SMTP is the most common email protocol that is part of the TCP/IP suite
and controls how an email client sends a user's email messages. The email server uses SMTP to send
email messages from the client to the email server to the receiving email server. However, SMTP doesn't
control how the email client receives mail - just how the client sends it.
That said, SMTP requires other protocols to ensure email is sent and received properly. SMTP can work
with Post Office Protocol 3 or Internet Mail Access Protocol, which controls how email servers receive
email messages.
8. User Datagram Protocol: UDP is an alternative to TCP and also works with IP to transmit time-sensitive
data. UDP enables low-latency data transmissions between internet applications, so this protocol is ideal
for voice over IP or other audio and video requirements. Unlike TCP, UDP doesn't wait for all packets to
arrive or organize the packets. Instead, UDP transmits all packets even if some haven't arrived.
UDP only transmits packets, while TCP transmits, organizes and ensures the packets arrive. While UDP
works more quickly than TCP, it's also less reliable.
9. OSPF Routing Protocol: OSPF works with IP in sending packets to their destination. IP aims to send
packets over the road as quickly as possible, which OSPF is designed to do. OSPF opens the shortest or
HTTPS can encrypt user web pages and HTTP requests. This provides greater security for users and can
prevent common cybersecurity threats, such as man-in-the-middle attacks.
5. Domain name system: DNS is a database that includes a website's domain name, which people use to
access the website, and its corresponding IP addresses, which devices use to locate the website. DNS
translates the domain name into IP addresses, and these translations are included within the DNS. Servers
can cache DNS data, which is required to access the websites. DNS also includes the DNS protocol, which
is within the IP suite and details the specifications DNS uses to translate and communicate.
DNS is important because it can quickly provide users with information, as well as access to remote hosts
and resources across the internet.
6. Dynamic Host Configuration Protocol: DHCP assigns IP addresses to network endpoints so they can
communicate with other network endpoints over IP. Whenever a device joins a network with a DHCP
server for the first time, DHCP automatically assigns it a new IP address and continues to do so each time
a device moves locations on the network.
When a device connects to a network, a DHCP handshake takes place, where the device and DHCP server
communicate. The device establishes a connection; the server receives it and provides available IP
addresses; the device requests an IP address; and the server confirm it to complete the process
7. Simple mail transfer protocol: SMTP is the most common email protocol that is part of the TCP/IP suite
and controls how an email client sends a user's email messages. The email server uses SMTP to send
email messages from the client to the email server to the receiving email server. However, SMTP doesn't
control how the email client receives mail - just how the client sends it.
That said, SMTP requires other protocols to ensure email is sent and received properly. SMTP can work
with Post Office Protocol 3 or Internet Mail Access Protocol, which controls how email servers receive
email messages.
8. User Datagram Protocol: UDP is an alternative to TCP and also works with IP to transmit time-sensitive
data. UDP enables low-latency data transmissions between internet applications, so this protocol is ideal
for voice over IP or other audio and video requirements. Unlike TCP, UDP doesn't wait for all packets to
arrive or organize the packets. Instead, UDP transmits all packets even if some haven't arrived.
UDP only transmits packets, while TCP transmits, organizes and ensures the packets arrive. While UDP
works more quickly than TCP, it's also less reliable.
9. OSPF Routing Protocol: OSPF works with IP in sending packets to their destination. IP aims to send
packets over the road as quickly as possible, which OSPF is designed to do. OSPF opens the shortest or

fastest path first for packets. It also updates the routing tables - a set of rules that control where packets
travel - and alerts routers about changes to the routing table or the network when a change occurs.
OSPF is similar to and supports the Routing Information Protocol - which directs traffic based on the
number of hops it has to make on a route - and it has also replaced RIP in many networks. OSPF was
developed as a more affordable and scalable alternative to RIP. For example, RIP sends updated routing
tables out every 30 seconds, while OSPF sends updates only when necessary and performs updates for the
specific part of the table where the change occurred.
10. Telnet: Telnet is designed for remote connectivity, and it establishes connections between a remote
endpoint and a host machine to enable a remote session. Telnet prompts the user at the remote endpoint to
log on and, once authenticated, gives the endpoint access to network resources and data at the host
computer.
Telnet has existed since the 1960s and was arguably the first draft of the modern internet. However, Telnet
lacks sophisticated security protections required for modern communications and technology, so it isn't
commonly used anymore.
4. International standard organizations
Some international standards organizations:
IEC - International Electrotechnical Commission
IEEE - Institute of Electric and Electronic Engineers
IETF - Internet Engineering Task Force
ISO - International Organization for Standardization
ITU - The International Telecommunication Union
ITU-R - ITU Radiocommunications Sector (CCIR)
ITU-T - ITU Telecommunications Sector (CCITT)
IUPAC - International Union of Pure and Applied Chemistry
OASIS - Organization for the Advancement of Structured Information Standards
SI - Systéme International d'Unit's (International System of Units)
W3C - World Wide Web Consortium
Accellera - Accellera Organization
The names of the standards used in networking:
International Organization for Standardization (ISO): Probably the largest standards organization
in the world, ISO is actually a confederation of standards organizations from dozens of countries.
In the networking world, ISO is best known for its OSI Reference Model.
travel - and alerts routers about changes to the routing table or the network when a change occurs.
OSPF is similar to and supports the Routing Information Protocol - which directs traffic based on the
number of hops it has to make on a route - and it has also replaced RIP in many networks. OSPF was
developed as a more affordable and scalable alternative to RIP. For example, RIP sends updated routing
tables out every 30 seconds, while OSPF sends updates only when necessary and performs updates for the
specific part of the table where the change occurred.
10. Telnet: Telnet is designed for remote connectivity, and it establishes connections between a remote
endpoint and a host machine to enable a remote session. Telnet prompts the user at the remote endpoint to
log on and, once authenticated, gives the endpoint access to network resources and data at the host
computer.
Telnet has existed since the 1960s and was arguably the first draft of the modern internet. However, Telnet
lacks sophisticated security protections required for modern communications and technology, so it isn't
commonly used anymore.
4. International standard organizations
Some international standards organizations:
IEC - International Electrotechnical Commission
IEEE - Institute of Electric and Electronic Engineers
IETF - Internet Engineering Task Force
ISO - International Organization for Standardization
ITU - The International Telecommunication Union
ITU-R - ITU Radiocommunications Sector (CCIR)
ITU-T - ITU Telecommunications Sector (CCITT)
IUPAC - International Union of Pure and Applied Chemistry
OASIS - Organization for the Advancement of Structured Information Standards
SI - Systéme International d'Unit's (International System of Units)
W3C - World Wide Web Consortium
Accellera - Accellera Organization
The names of the standards used in networking:
International Organization for Standardization (ISO): Probably the largest standards organization
in the world, ISO is actually a confederation of standards organizations from dozens of countries.
In the networking world, ISO is best known for its OSI Reference Model.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

American National Standards Institute (ANSI): ANSI is the primary organization responsible for
coordinating and publishing computer and information technology standards in the United States.
While they are often thought of as developing and maintaining standards, they are not. Instead,
they oversee and accredit the organizations that actually create the standards, referring to them as
the Standards Development Organization or SDO. ANSI also publishes standards documents
created by SDOs and serves as the US representative for ISO.
Information Technology Industry Council (ITIC): ITIC is a group of several dozen companies in
the information technology (computer) industry. ITIC is an ANSI approved SDO for developing
and handling standards related to a variety of computer-related topics. It was formerly known as
the Computer and Business Equipment Manufacturers Association (CBEMA).
National Committee on Information Technology (NCITS): A committee established by ITIC to
develop and maintain standards relevant to the world of information technology. NCITS was
formerly known as the X3 Accredited Standards Committee, Information Technology, or more
commonly, just X3. It maintains several subcommittees that develop and maintain standards for
various technical topics.
The Institute of Electrical and Electronics Engineers (IEEE): IEEE (pronounced “eye-triple-ee”) is
a well-known professional organization for people working in the electrical or electronic field,
including computers. computer and network. IEEE's main claim to fame in the networking industry
is the IEEE 802 Project, which covers many popular networking technologies including Ethernet.
Electronics Industry Alliance (EIA): EIA is the international industry association best known for
publishing standards for electrical wiring and transmission.
Telecommunication Industry Association (TIA): TIA is the communications sector of the EIA, and
is responsible for developing communications standards. Because communications, wiring, and
transmission lines are all involved, and because the TIA and EIA organizations are also involved,
standards issued by the EIA or TIA are often labeled with the prefixes combining ““ EIA/TIA” or
“TIA/EIA”.
International Telecommunication Union - Telecommunications Standardization Field (ITU-T):
ITU-T is another large international organization that develops standards for the
telecommunications industry. ITU-T was formerly known as the International Telephone and
Telephone Advisory Committee or CCITT.
European Telecommunications Standards Institute (ETSI): An organization with members from
dozens of countries both inside and outside Europe that develops telecommunications standards for
the European (and elsewhere) market. ETSI is known for regulating the use of radio bandwidth in
Europe and developing standards like HiperLAN.
II. Explain the impact of network topology, communication and bandwidth
requirements.
1. Network topology
coordinating and publishing computer and information technology standards in the United States.
While they are often thought of as developing and maintaining standards, they are not. Instead,
they oversee and accredit the organizations that actually create the standards, referring to them as
the Standards Development Organization or SDO. ANSI also publishes standards documents
created by SDOs and serves as the US representative for ISO.
Information Technology Industry Council (ITIC): ITIC is a group of several dozen companies in
the information technology (computer) industry. ITIC is an ANSI approved SDO for developing
and handling standards related to a variety of computer-related topics. It was formerly known as
the Computer and Business Equipment Manufacturers Association (CBEMA).
National Committee on Information Technology (NCITS): A committee established by ITIC to
develop and maintain standards relevant to the world of information technology. NCITS was
formerly known as the X3 Accredited Standards Committee, Information Technology, or more
commonly, just X3. It maintains several subcommittees that develop and maintain standards for
various technical topics.
The Institute of Electrical and Electronics Engineers (IEEE): IEEE (pronounced “eye-triple-ee”) is
a well-known professional organization for people working in the electrical or electronic field,
including computers. computer and network. IEEE's main claim to fame in the networking industry
is the IEEE 802 Project, which covers many popular networking technologies including Ethernet.
Electronics Industry Alliance (EIA): EIA is the international industry association best known for
publishing standards for electrical wiring and transmission.
Telecommunication Industry Association (TIA): TIA is the communications sector of the EIA, and
is responsible for developing communications standards. Because communications, wiring, and
transmission lines are all involved, and because the TIA and EIA organizations are also involved,
standards issued by the EIA or TIA are often labeled with the prefixes combining ““ EIA/TIA” or
“TIA/EIA”.
International Telecommunication Union - Telecommunications Standardization Field (ITU-T):
ITU-T is another large international organization that develops standards for the
telecommunications industry. ITU-T was formerly known as the International Telephone and
Telephone Advisory Committee or CCITT.
European Telecommunications Standards Institute (ETSI): An organization with members from
dozens of countries both inside and outside Europe that develops telecommunications standards for
the European (and elsewhere) market. ETSI is known for regulating the use of radio bandwidth in
Europe and developing standards like HiperLAN.
II. Explain the impact of network topology, communication and bandwidth
requirements.
1. Network topology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network topology is used to describe the physical and logical structure of a network. It maps the way
different nodes on a network--including switches and routers--are placed and connected, as well as how
data flows. Diagramming the locations of endpoints and service requirements helps determine the best
placement for each node to optimize traffic flows.
2. Physical topology
Physical topology can be considered as a layout of the network media that shows the interconnections of
the devices on the network. It specifies which geometric shape the linked devices form with each other.
The physical topology does not give much comprehensive detail about the type of devices, the mechanism
used for interacting with other devices in the network, and how data is transferred from one device to
another.
Therefore, it gives essential details of the network and network devices broadly, neglecting the higher
level details like device type, addressing schemes, connectivity, and so on.
The factors that affect communication of devices on a network based on the physical topology selected
are:
CostScalability
Bandwidth capacity
Ease of installation
Ease of troubleshooting
3. Logical topology
Unlike the physical topology, the logical topology emphasizes the manner in which data is transmitted
between network nodes rather than the physical layout of the path the data follows. An important fact
regarding these topologies is that both the physical and logical topologies are independent of a network,
no matter what shape and size it may be.
Such a logical topology is a signal path that traverses a physical topology. It handles -
Line discipline
Delivery frame according to order
Error message
Optimal flow control.
4. The difference between physical topology and logical topology
Key difference between physical and logical topology
different nodes on a network--including switches and routers--are placed and connected, as well as how
data flows. Diagramming the locations of endpoints and service requirements helps determine the best
placement for each node to optimize traffic flows.
2. Physical topology
Physical topology can be considered as a layout of the network media that shows the interconnections of
the devices on the network. It specifies which geometric shape the linked devices form with each other.
The physical topology does not give much comprehensive detail about the type of devices, the mechanism
used for interacting with other devices in the network, and how data is transferred from one device to
another.
Therefore, it gives essential details of the network and network devices broadly, neglecting the higher
level details like device type, addressing schemes, connectivity, and so on.
The factors that affect communication of devices on a network based on the physical topology selected
are:
CostScalability
Bandwidth capacity
Ease of installation
Ease of troubleshooting
3. Logical topology
Unlike the physical topology, the logical topology emphasizes the manner in which data is transmitted
between network nodes rather than the physical layout of the path the data follows. An important fact
regarding these topologies is that both the physical and logical topologies are independent of a network,
no matter what shape and size it may be.
Such a logical topology is a signal path that traverses a physical topology. It handles -
Line discipline
Delivery frame according to order
Error message
Optimal flow control.
4. The difference between physical topology and logical topology
Key difference between physical and logical topology
The physical topology is basically the physical layout of the network media. In contrast, logical
topology refers to how, how data is transmitted throughout the network.
The physical topology will not impede the transfer of data from one device to the other according
to the logical topology.
Logical topology is invisible in nature while physical topology can be customized.
5. Examples of popular topologies
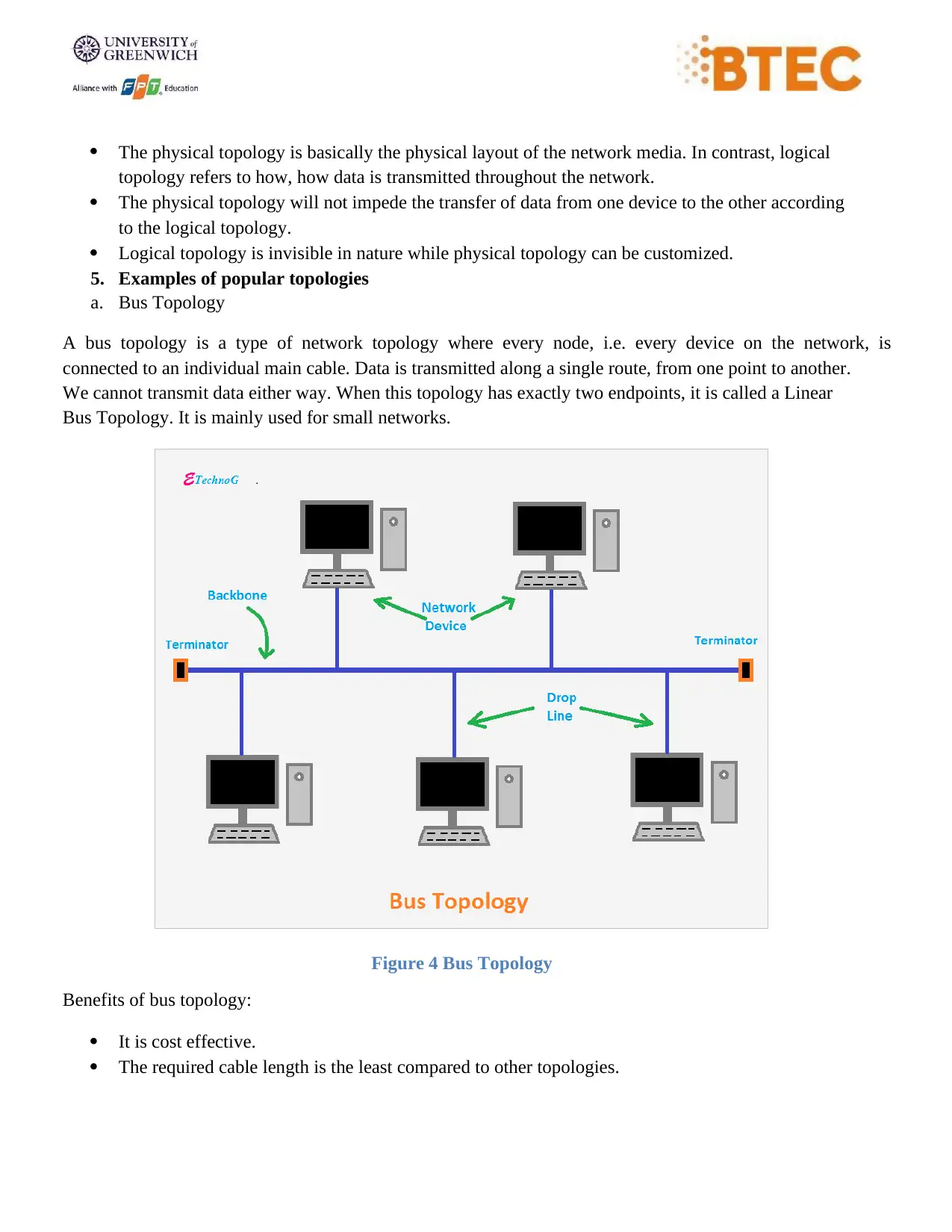
a. Bus Topology
A bus topology is a type of network topology where every node, i.e. every device on the network, is
connected to an individual main cable. Data is transmitted along a single route, from one point to another.
We cannot transmit data either way. When this topology has exactly two endpoints, it is called a Linear
Bus Topology. It is mainly used for small networks.
Figure 4 Bus Topology
Benefits of bus topology:
It is cost effective.
The required cable length is the least compared to other topologies.
topology refers to how, how data is transmitted throughout the network.
The physical topology will not impede the transfer of data from one device to the other according
to the logical topology.
Logical topology is invisible in nature while physical topology can be customized.
5. Examples of popular topologies
a. Bus Topology
A bus topology is a type of network topology where every node, i.e. every device on the network, is
connected to an individual main cable. Data is transmitted along a single route, from one point to another.
We cannot transmit data either way. When this topology has exactly two endpoints, it is called a Linear
Bus Topology. It is mainly used for small networks.
Figure 4 Bus Topology
Benefits of bus topology:
It is cost effective.
The required cable length is the least compared to other topologies.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 26
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





