University Networking and Security: Content Analysis Report ITECH1102
VerifiedAdded on 2022/08/21
|12
|2406
|27
Report
AI Summary
This report provides a detailed content analysis of networking and security concepts, covering topics from number systems (binary, decimal, octal, hexadecimal) to network models (OSI and TCP/IP) and protocols. The analysis explores various network devices such as hubs, switches, and routers, along with their functions and operational layers. It delves into IP addressing, including IPv4 and IPv6, subnetting, and the Domain Name System (DNS). The report also examines transport layer protocols like UDP and TCP, discussing 3-way handshakes and sockets. Furthermore, it covers the physical layer, including multiplexing techniques (TDM, FDM) and transmission media (guided and unguided), comparing their speed, cost, and security aspects. The report references key concepts from the provided lecture material and related articles, offering a comprehensive overview of networking and security fundamentals. This report is a student contribution to Desklib, a platform offering AI-based study tools.

Running head: NETWORKING AND SECURITY
NETWORKING AND SECURITY
Name of the Student
Name of the University
Author Note:
NETWORKING AND SECURITY
Name of the Student
Name of the University
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING AND SECURITY
1. Number System
In the field of computer science number system the numbers are represents in difference
way. There are basically 4 ways by which the numbers can be represented. Those includes the
Binary representation, Decimal representation, Octal representation and the Hexadecimal
representation (Ino et al., 2017).
Number
System
Base Value Digits
Binary
Representatio
n
2 0 and 1
Decimal
Representatio
n
10 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
Octal
Representatio
n
8 0, 1, 2, 3, 4, 5, 6, 7
Hexadecimal
Representatio
n
16 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F
a) Binary to Decimal, octal and hexadecimal:
While converting Binary numbers to hexadecimal representation the binary number will be
divided with 4bit binary word. Where the binary number 101010 will be 2A16 in
Hexadecimal and 528 will be in octal representation.
Whereas, the conversion of binary to decimal will be done similar to the below example:-
12^4 02^312^212^1 02^0
= 1 × 16 + 0 × 8 + 1 × 4 + 1 × 2 + 0 × 1
= 16 + 4 + 2
= 22
1. Number System
In the field of computer science number system the numbers are represents in difference
way. There are basically 4 ways by which the numbers can be represented. Those includes the
Binary representation, Decimal representation, Octal representation and the Hexadecimal
representation (Ino et al., 2017).
Number
System
Base Value Digits
Binary
Representatio
n
2 0 and 1
Decimal
Representatio
n
10 0, 1, 2, 3, 4, 5, 6, 7, 8, 9
Octal
Representatio
n
8 0, 1, 2, 3, 4, 5, 6, 7
Hexadecimal
Representatio
n
16 0, 1, 2, 3, 4, 5, 6, 7, 8, 9, A, B, C, D, E, F
a) Binary to Decimal, octal and hexadecimal:
While converting Binary numbers to hexadecimal representation the binary number will be
divided with 4bit binary word. Where the binary number 101010 will be 2A16 in
Hexadecimal and 528 will be in octal representation.
Whereas, the conversion of binary to decimal will be done similar to the below example:-
12^4 02^312^212^1 02^0
= 1 × 16 + 0 × 8 + 1 × 4 + 1 × 2 + 0 × 1
= 16 + 4 + 2
= 22
2NETWORKING AND SECURITY
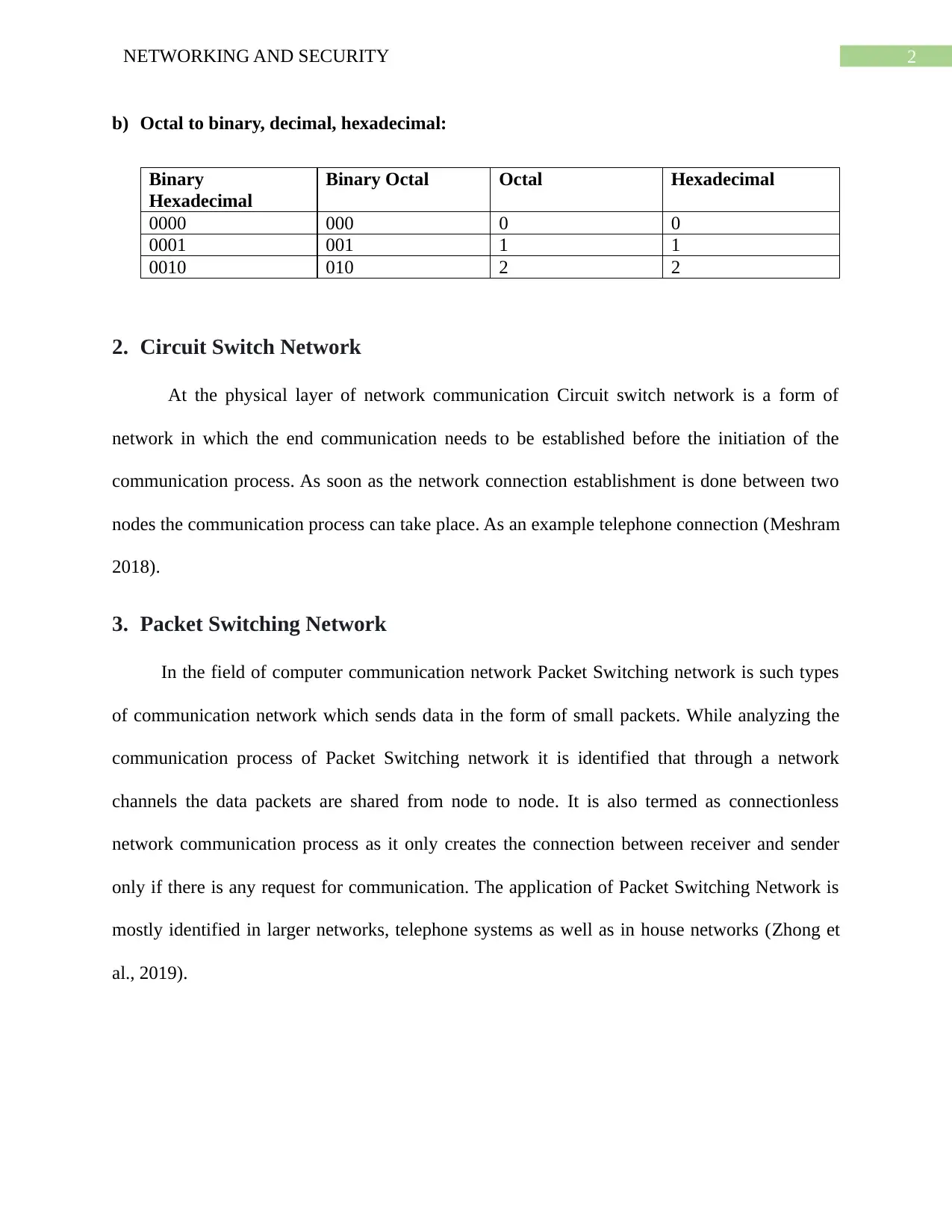
b) Octal to binary, decimal, hexadecimal:
Binary
Hexadecimal
Binary Octal Octal Hexadecimal
0000 000 0 0
0001 001 1 1
0010 010 2 2
2. Circuit Switch Network
At the physical layer of network communication Circuit switch network is a form of
network in which the end communication needs to be established before the initiation of the
communication process. As soon as the network connection establishment is done between two
nodes the communication process can take place. As an example telephone connection (Meshram
2018).
3. Packet Switching Network
In the field of computer communication network Packet Switching network is such types
of communication network which sends data in the form of small packets. While analyzing the
communication process of Packet Switching network it is identified that through a network
channels the data packets are shared from node to node. It is also termed as connectionless
network communication process as it only creates the connection between receiver and sender
only if there is any request for communication. The application of Packet Switching Network is
mostly identified in larger networks, telephone systems as well as in house networks (Zhong et
al., 2019).
b) Octal to binary, decimal, hexadecimal:
Binary
Hexadecimal
Binary Octal Octal Hexadecimal
0000 000 0 0
0001 001 1 1
0010 010 2 2
2. Circuit Switch Network
At the physical layer of network communication Circuit switch network is a form of
network in which the end communication needs to be established before the initiation of the
communication process. As soon as the network connection establishment is done between two
nodes the communication process can take place. As an example telephone connection (Meshram
2018).
3. Packet Switching Network
In the field of computer communication network Packet Switching network is such types
of communication network which sends data in the form of small packets. While analyzing the
communication process of Packet Switching network it is identified that through a network
channels the data packets are shared from node to node. It is also termed as connectionless
network communication process as it only creates the connection between receiver and sender
only if there is any request for communication. The application of Packet Switching Network is
mostly identified in larger networks, telephone systems as well as in house networks (Zhong et
al., 2019).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3NETWORKING AND SECURITY
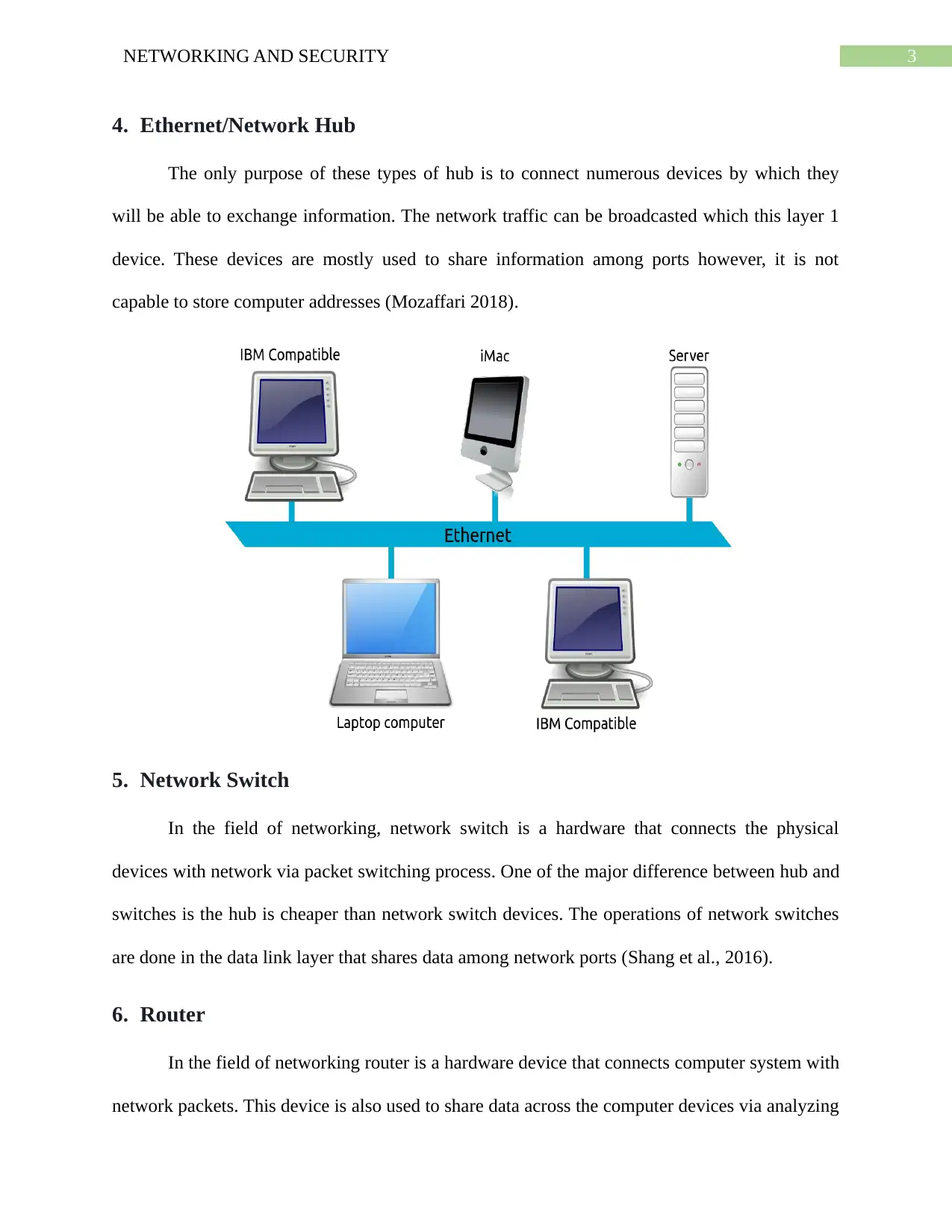
4. Ethernet/Network Hub
The only purpose of these types of hub is to connect numerous devices by which they
will be able to exchange information. The network traffic can be broadcasted which this layer 1
device. These devices are mostly used to share information among ports however, it is not
capable to store computer addresses (Mozaffari 2018).
5. Network Switch
In the field of networking, network switch is a hardware that connects the physical
devices with network via packet switching process. One of the major difference between hub and
switches is the hub is cheaper than network switch devices. The operations of network switches
are done in the data link layer that shares data among network ports (Shang et al., 2016).
6. Router
In the field of networking router is a hardware device that connects computer system with
network packets. This device is also used to share data across the computer devices via analyzing
4. Ethernet/Network Hub
The only purpose of these types of hub is to connect numerous devices by which they
will be able to exchange information. The network traffic can be broadcasted which this layer 1
device. These devices are mostly used to share information among ports however, it is not
capable to store computer addresses (Mozaffari 2018).
5. Network Switch
In the field of networking, network switch is a hardware that connects the physical
devices with network via packet switching process. One of the major difference between hub and
switches is the hub is cheaper than network switch devices. The operations of network switches
are done in the data link layer that shares data among network ports (Shang et al., 2016).
6. Router
In the field of networking router is a hardware device that connects computer system with
network packets. This device is also used to share data across the computer devices via analyzing
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4NETWORKING AND SECURITY
the IP address of the receiver. Router works similar to gateway application and the operations of
this device is performed in layer 3 which the network layer (Mejías et al., 2017).
7. The Internet Models
In the field of networking there are two popular models which includes the TCP/IP and OSI
model. These models helps to get a detail idea about the working of networking. While analyzing
this aspect it is identified that OSI model has 7 significant layers and TCP/IP model has 5
significant layer. The layers of OSI includes Application layer, Presentation layer, session layer,
transport layer, network layer, data link layer and the physical layer. TCP/IP layers includes the
Application layer, Transport Layer, network Layer, data link Layer and the physical layer
(Katsikeas et al., 2017). Each layers of these two models have their own purpose. In the below
section a detail elaboration of TCP/IP layers are mentioned:-
7.1. Application Layer
Application layer works with FTP and HTTP protocols. This layer helps the user to get
the access of their preferred services. Followed by an analysis on it operations it is
identified that there are four types of interface present which helps to provide the
services to its users (Edeline et al., 2016).
a) Client/Server architecture:
According to the architecture of this model the user will send request to the server
and then server will analyze request and then it responds based of the verification results.
b) Peer to peer architecture:
In this scenario the roles of server has been replaced by the peers present in the
network.
c) Host based architecture:
the IP address of the receiver. Router works similar to gateway application and the operations of
this device is performed in layer 3 which the network layer (Mejías et al., 2017).
7. The Internet Models
In the field of networking there are two popular models which includes the TCP/IP and OSI
model. These models helps to get a detail idea about the working of networking. While analyzing
this aspect it is identified that OSI model has 7 significant layers and TCP/IP model has 5
significant layer. The layers of OSI includes Application layer, Presentation layer, session layer,
transport layer, network layer, data link layer and the physical layer. TCP/IP layers includes the
Application layer, Transport Layer, network Layer, data link Layer and the physical layer
(Katsikeas et al., 2017). Each layers of these two models have their own purpose. In the below
section a detail elaboration of TCP/IP layers are mentioned:-
7.1. Application Layer
Application layer works with FTP and HTTP protocols. This layer helps the user to get
the access of their preferred services. Followed by an analysis on it operations it is
identified that there are four types of interface present which helps to provide the
services to its users (Edeline et al., 2016).
a) Client/Server architecture:
According to the architecture of this model the user will send request to the server
and then server will analyze request and then it responds based of the verification results.
b) Peer to peer architecture:
In this scenario the roles of server has been replaced by the peers present in the
network.
c) Host based architecture:

5NETWORKING AND SECURITY
Using this interface the communication will be establish by using the features of
mainframe and connecting it with the client’s terminals.
d) Cloud based architecture:
Cloud based architecture provides the IaaS, SaaS and PaaS services in order to
deliver an effective computing platforms to its clients.
7.2. Data Link Layer
These layers primary does the communication between the local devices.
7.2.1. Network Interface Card
The primary objective of NIC to establish a connection between network
and devices. These 48 bits cards has mostly two parts, one is the OUI 24 bits and
the second one is the unique 24 bits. Network filtering is one of the operations of
NIC
7.2.2. Cyclic Redundancy Check (CRC)
In this process the accuracy of NIC is checked where it will decide
whether the network packets will be kept on rejected.
7.2.3. CSMA/CD & CSMA/CA
These are the types of access controls in which the CSMA/CD will detect
whether any collision has occurred during the transmission process or not. Whereas,
CSMA/CA will avoid the occurred collision to complete the transmission (Zhao et
al., 2018).
7.2.4. Address Resolution Protocol (ARP)
Using this interface the communication will be establish by using the features of
mainframe and connecting it with the client’s terminals.
d) Cloud based architecture:
Cloud based architecture provides the IaaS, SaaS and PaaS services in order to
deliver an effective computing platforms to its clients.
7.2. Data Link Layer
These layers primary does the communication between the local devices.
7.2.1. Network Interface Card
The primary objective of NIC to establish a connection between network
and devices. These 48 bits cards has mostly two parts, one is the OUI 24 bits and
the second one is the unique 24 bits. Network filtering is one of the operations of
NIC
7.2.2. Cyclic Redundancy Check (CRC)
In this process the accuracy of NIC is checked where it will decide
whether the network packets will be kept on rejected.
7.2.3. CSMA/CD & CSMA/CA
These are the types of access controls in which the CSMA/CD will detect
whether any collision has occurred during the transmission process or not. Whereas,
CSMA/CA will avoid the occurred collision to complete the transmission (Zhao et
al., 2018).
7.2.4. Address Resolution Protocol (ARP)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORKING AND SECURITY
In the field of networking this protocol is used to detect and store the IP
address and the MAC address. Then it will retrieve those addresses via the
machines in case of any query.
7.3. Internet (Network) layer/IP layer (Layer 3)
This layer uses the ARP and IP transmission protocol with the purpose to
share network traffics between hosts.
7.3.1. IP addressing
There are two types of IP address IPv4 and IPv6. Where IPv6 addresses
are 32 bits 128 bits longer. And the IPv4 addresses are 32 bits longer.
IPv4: 1.160.10.240
IPv6: 3ffe:1900:4545:3:200:f8ff:fe21:67cf.
7.3.2. How to get an IP address?
IP addresses of the operating system has the features to operate manually
and automatically. While configuring is automatically it needs to user dynamic
host sever protocol to get IP settings of a machine. And in case of manual
configuration it needs the IP settings of the operating system only (Zhao et al.,
2018).
7.3.3. Subnet mask
This is used to get the idea about the numbers of bits that has been
occupied by the node and the network. In order to calculate it binary 1 represents
network and 0 represents node.
7.3.4. CIDR
In the field of networking this protocol is used to detect and store the IP
address and the MAC address. Then it will retrieve those addresses via the
machines in case of any query.
7.3. Internet (Network) layer/IP layer (Layer 3)
This layer uses the ARP and IP transmission protocol with the purpose to
share network traffics between hosts.
7.3.1. IP addressing
There are two types of IP address IPv4 and IPv6. Where IPv6 addresses
are 32 bits 128 bits longer. And the IPv4 addresses are 32 bits longer.
IPv4: 1.160.10.240
IPv6: 3ffe:1900:4545:3:200:f8ff:fe21:67cf.
7.3.2. How to get an IP address?
IP addresses of the operating system has the features to operate manually
and automatically. While configuring is automatically it needs to user dynamic
host sever protocol to get IP settings of a machine. And in case of manual
configuration it needs the IP settings of the operating system only (Zhao et al.,
2018).
7.3.3. Subnet mask
This is used to get the idea about the numbers of bits that has been
occupied by the node and the network. In order to calculate it binary 1 represents
network and 0 represents node.
7.3.4. CIDR
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7NETWORKING AND SECURITY
CIDR is used to signify the portion of bits occupied by an IP addresses. As
an example 1.160.10.240/16. Which indicates that this IP address has occupied 16
bits of network address (Iskander et al., 2016).
7.3.5. Domain name system (DNS)
In this process the domain name is interpreted into IP addresses.
7.4. Transport Layer
In this layer it uses the UDP and TCP protocols to perform its activities. This layer
make sure that each of applications has prominent connection with the network as well.
7.4.1. Sockets
Socket is a mixture of port no. and IP addresses. In transport layer each on the
application is assigned with a port number and those ports are the primary identity of
those applications into the transport layer. And in the ending and receiving point of the
network nodes are sockets which helps to transfer data among nodes.
7.4.2. UDP
In the transport layer UDP is a stateless protocol that transfers data. Since, after
completion of the transmission the connection gets destroyed thus after transmission it is
very difficult to understand the statues of the transferred data (Zhao et al., 2018).
7.4.3. TCP
TCP is also one of the protocol that transfers data. However, as compared to
UDP, TCP is slower is case of delivering large files. It is more reliable the UDP as in
TCP it provides assurance of the delivered data.
7.4.4. 3-way Handshake
CIDR is used to signify the portion of bits occupied by an IP addresses. As
an example 1.160.10.240/16. Which indicates that this IP address has occupied 16
bits of network address (Iskander et al., 2016).
7.3.5. Domain name system (DNS)
In this process the domain name is interpreted into IP addresses.
7.4. Transport Layer
In this layer it uses the UDP and TCP protocols to perform its activities. This layer
make sure that each of applications has prominent connection with the network as well.
7.4.1. Sockets
Socket is a mixture of port no. and IP addresses. In transport layer each on the
application is assigned with a port number and those ports are the primary identity of
those applications into the transport layer. And in the ending and receiving point of the
network nodes are sockets which helps to transfer data among nodes.
7.4.2. UDP
In the transport layer UDP is a stateless protocol that transfers data. Since, after
completion of the transmission the connection gets destroyed thus after transmission it is
very difficult to understand the statues of the transferred data (Zhao et al., 2018).
7.4.3. TCP
TCP is also one of the protocol that transfers data. However, as compared to
UDP, TCP is slower is case of delivering large files. It is more reliable the UDP as in
TCP it provides assurance of the delivered data.
7.4.4. 3-way Handshake

8NETWORKING AND SECURITY
This is also one of the data transferring process which consists three basic
steps.
Step 1- client will send request.
Step 2- server will acknowledge the request and the send it back to the client.
Step 3- client will receive it with an acknowledgement.
This is one of the most reliable data transferring process within transport layer.
7.5. Physical Layer
This layer performs the connection establishment between the network and
computer devices and communicate via digital or analog data.
7.5.1. Multiplexing
In this process the communication channel can perform multiple communications at
a time.
a) Time Division multiplexing (TDM):
This will divide the communication process in different time slots.
b) Frequency Division multiplexing (FDM):
This will differentiate the frequencies of the data transmission.
c) Wavelength Division multiplexing:
In this process the wavelength transmittable data gets divided.
7.5.2. Transmission media
There are two types of transmission media, one is the guided media and
another one is the unguided media. Guided media includes the coaxial cable, optical
fiber and twisted cable. And the unguided media consists of microwaves, radio waves
and infrared.
This is also one of the data transferring process which consists three basic
steps.
Step 1- client will send request.
Step 2- server will acknowledge the request and the send it back to the client.
Step 3- client will receive it with an acknowledgement.
This is one of the most reliable data transferring process within transport layer.
7.5. Physical Layer
This layer performs the connection establishment between the network and
computer devices and communicate via digital or analog data.
7.5.1. Multiplexing
In this process the communication channel can perform multiple communications at
a time.
a) Time Division multiplexing (TDM):
This will divide the communication process in different time slots.
b) Frequency Division multiplexing (FDM):
This will differentiate the frequencies of the data transmission.
c) Wavelength Division multiplexing:
In this process the wavelength transmittable data gets divided.
7.5.2. Transmission media
There are two types of transmission media, one is the guided media and
another one is the unguided media. Guided media includes the coaxial cable, optical
fiber and twisted cable. And the unguided media consists of microwaves, radio waves
and infrared.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9NETWORKING AND SECURITY
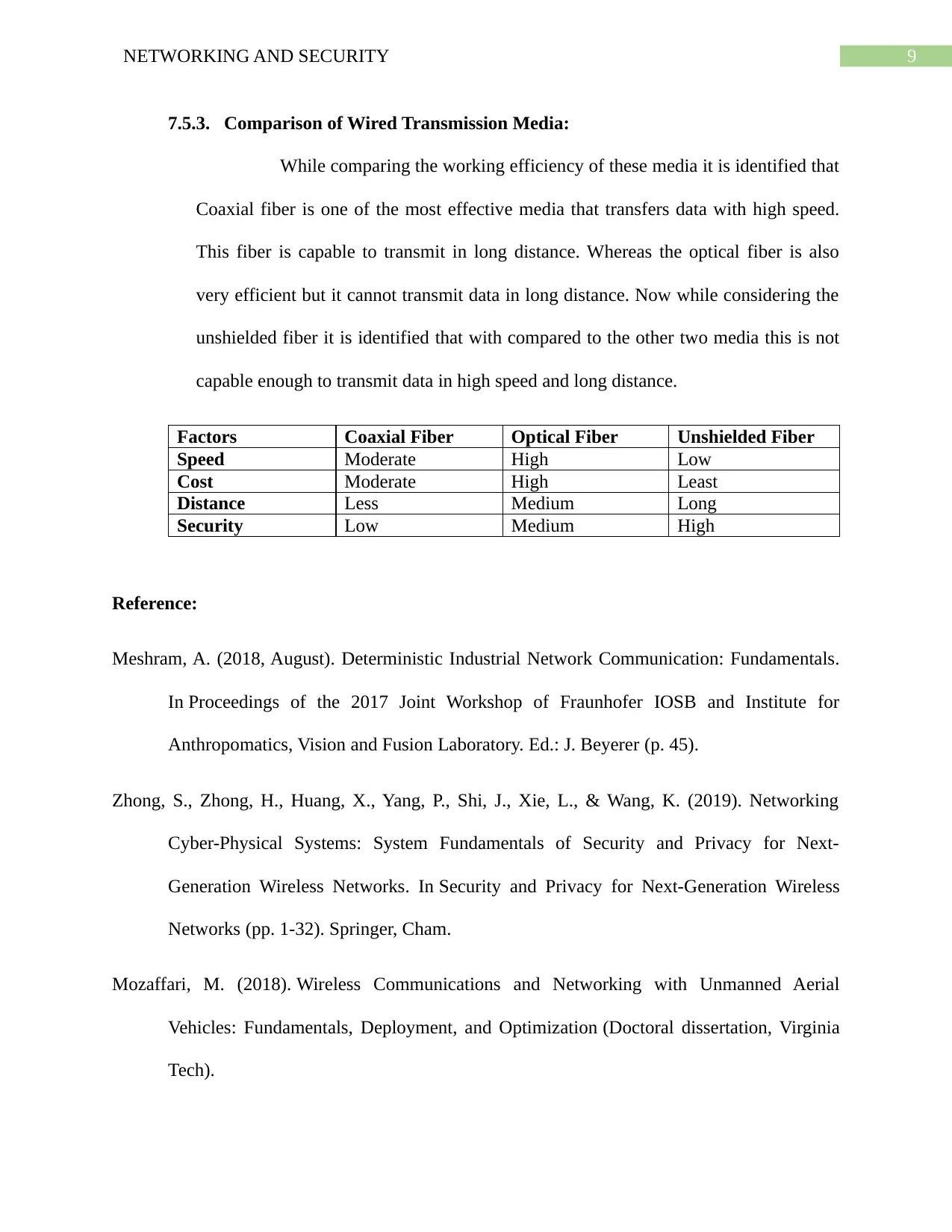
7.5.3. Comparison of Wired Transmission Media:
While comparing the working efficiency of these media it is identified that
Coaxial fiber is one of the most effective media that transfers data with high speed.
This fiber is capable to transmit in long distance. Whereas the optical fiber is also
very efficient but it cannot transmit data in long distance. Now while considering the
unshielded fiber it is identified that with compared to the other two media this is not
capable enough to transmit data in high speed and long distance.
Factors Coaxial Fiber Optical Fiber Unshielded Fiber
Speed Moderate High Low
Cost Moderate High Least
Distance Less Medium Long
Security Low Medium High
Reference:
Meshram, A. (2018, August). Deterministic Industrial Network Communication: Fundamentals.
In Proceedings of the 2017 Joint Workshop of Fraunhofer IOSB and Institute for
Anthropomatics, Vision and Fusion Laboratory. Ed.: J. Beyerer (p. 45).
Zhong, S., Zhong, H., Huang, X., Yang, P., Shi, J., Xie, L., & Wang, K. (2019). Networking
Cyber-Physical Systems: System Fundamentals of Security and Privacy for Next-
Generation Wireless Networks. In Security and Privacy for Next-Generation Wireless
Networks (pp. 1-32). Springer, Cham.
Mozaffari, M. (2018). Wireless Communications and Networking with Unmanned Aerial
Vehicles: Fundamentals, Deployment, and Optimization (Doctoral dissertation, Virginia
Tech).
7.5.3. Comparison of Wired Transmission Media:
While comparing the working efficiency of these media it is identified that
Coaxial fiber is one of the most effective media that transfers data with high speed.
This fiber is capable to transmit in long distance. Whereas the optical fiber is also
very efficient but it cannot transmit data in long distance. Now while considering the
unshielded fiber it is identified that with compared to the other two media this is not
capable enough to transmit data in high speed and long distance.
Factors Coaxial Fiber Optical Fiber Unshielded Fiber
Speed Moderate High Low
Cost Moderate High Least
Distance Less Medium Long
Security Low Medium High
Reference:
Meshram, A. (2018, August). Deterministic Industrial Network Communication: Fundamentals.
In Proceedings of the 2017 Joint Workshop of Fraunhofer IOSB and Institute for
Anthropomatics, Vision and Fusion Laboratory. Ed.: J. Beyerer (p. 45).
Zhong, S., Zhong, H., Huang, X., Yang, P., Shi, J., Xie, L., & Wang, K. (2019). Networking
Cyber-Physical Systems: System Fundamentals of Security and Privacy for Next-
Generation Wireless Networks. In Security and Privacy for Next-Generation Wireless
Networks (pp. 1-32). Springer, Cham.
Mozaffari, M. (2018). Wireless Communications and Networking with Unmanned Aerial
Vehicles: Fundamentals, Deployment, and Optimization (Doctoral dissertation, Virginia
Tech).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10NETWORKING AND SECURITY
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Mejías, A., Herrera, R. S., Márquez, M. A., Calderón, A. J., González, I., & Andújar, J. M.
(2017). Easy handling of sensors and actuators over TCP/IP networks by open source
hardware/software. Sensors, 17(1), 94.
Katsikeas, S., Fysarakis, K., Miaoudakis, A., Van Bemten, A., Askoxylakis, I., Papaefstathiou, I.,
& Plemenos, A. (2017, July). Lightweight & secure industrial IoT communications via
the MQ telemetry transport protocol. In 2017 IEEE Symposium on Computers and
Communications (ISCC) (pp. 1193-1200). IEEE.
Edeline, K., Kühlewind, M., Trammell, B., Aben, E., & Donnet, B. (2016). Using UDP for
internet transport evolution. arXiv preprint arXiv:1612.07816.
Zhao, J., Bai, J., Zhang, Q., Yang, F., Li, Z., Zhang, X., ... & Bai, R. (2018, December). The
Discussion about Mechanism of Data Transmission in the OSI Model. In 2018
International Conference on Transportation & Logistics, Information & Communication,
Smart City (TLICSC 2018). Atlantis Press.
Iskander, M. F., Yun, Z., Qazi, F. A., Sasaki, G., & Das, A. (2016, November). Physical layer
based approach for advanced directional networking. In MILCOM 2016-2016 IEEE
Military Communications Conference (pp. 424-429). IEEE.
Ino, K., Kanno, Y., Yamada, Y., Shiku, H., & Matsue, T. (2017). Binary-number-based digital
electrochemical detection using a single working electrode with multiple
sensors. Electrochemistry Communications, 77, 76-80.
Shang, W., Yu, Y., Droms, R., & Zhang, L. (2016). Challenges in IoT networking via TCP/IP
architecture. Technical Report NDN-0038. NDN Project.
Mejías, A., Herrera, R. S., Márquez, M. A., Calderón, A. J., González, I., & Andújar, J. M.
(2017). Easy handling of sensors and actuators over TCP/IP networks by open source
hardware/software. Sensors, 17(1), 94.
Katsikeas, S., Fysarakis, K., Miaoudakis, A., Van Bemten, A., Askoxylakis, I., Papaefstathiou, I.,
& Plemenos, A. (2017, July). Lightweight & secure industrial IoT communications via
the MQ telemetry transport protocol. In 2017 IEEE Symposium on Computers and
Communications (ISCC) (pp. 1193-1200). IEEE.
Edeline, K., Kühlewind, M., Trammell, B., Aben, E., & Donnet, B. (2016). Using UDP for
internet transport evolution. arXiv preprint arXiv:1612.07816.
Zhao, J., Bai, J., Zhang, Q., Yang, F., Li, Z., Zhang, X., ... & Bai, R. (2018, December). The
Discussion about Mechanism of Data Transmission in the OSI Model. In 2018
International Conference on Transportation & Logistics, Information & Communication,
Smart City (TLICSC 2018). Atlantis Press.
Iskander, M. F., Yun, Z., Qazi, F. A., Sasaki, G., & Das, A. (2016, November). Physical layer
based approach for advanced directional networking. In MILCOM 2016-2016 IEEE
Military Communications Conference (pp. 424-429). IEEE.
Ino, K., Kanno, Y., Yamada, Y., Shiku, H., & Matsue, T. (2017). Binary-number-based digital
electrochemical detection using a single working electrode with multiple
sensors. Electrochemistry Communications, 77, 76-80.

11NETWORKING AND SECURITY
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



