Networking and Security: Principles, Protocols, and Cloud
VerifiedAdded on 2023/06/05
|9
|2034
|244
Report
AI Summary
This report delves into the critical aspects of networking and security, providing a comprehensive overview of network connectivity, communication principles, and cloud computing. It explores the vital role of network connectivity in modern computing, emphasizing the importance of secure and efficient data sharing. The report details the principles of communication in networks, including protocols, senders, messages, transmission mediums, and receivers. It examines the functionality of hardware entities like gateways, routers, switches, and repeaters, along with software entities that facilitate user and file management. Furthermore, the report discusses the Open System Interconnection (OSI) model, outlining the seven layers and their respective protocols, such as HTTP, TCP, and IP. It also covers the fundamental aspects of cloud computing, including on-demand access, broad network access, resource pooling, and elasticity. Finally, the report addresses networking needs for businesses, emphasizing the importance of scalable network architecture, security, and the assessment of existing network components to meet business demands.

Running head: NETWORKING AND SECURITY 1
Networking and Security
Name
Tutor
Course
Date
Networking and Security
Name
Tutor
Course
Date
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING AND SECURITY 2
Networking and Security
Due to the need for a faster and secure means to share files, resources, and information,
computer networking has proved to be vital since it allows interconnection of multiple computers
to facilitate all these essentials. There is more consideration on the side of security in the current
computing world so that risks that come with networks such as unauthorized access with
malicious intentions are avoided by all means. Factor like administration, geographical span,
architecture, and inter-connectivity determines how a particular network can be classified. For
instance, in the current computing, there are a number of attributes which are as a result of a
well-established network connectivity as discussed below.
The Role and Function of Network Connectivity Currently
When numerous parts of a network are connected to one another extensively by means of
switches, gateways, routers among others, it is in simple terms called network connectivity. It is
a well laid matric resulting to well-connected network parts. In the current computing, there is a
greater realization from institutions and communication companies of a vibrant role played by a
noble network connectivity in operations that are both internally and towards their clients
(Hoffmann & Triesch, 2017). There is a surety of effective communication no matter the
distance by means of radio, wireless network and telephone.
Network connectivity emphasizes on optimal utilization of both software and hardware
components which can result in extreme business performance to an organization. In particular,
cables that are fiber-optic are mostly used currently due to their ability to be bundled and
flexibility hence common is data transmissions that are long-haul. Therefore, for a good
connectivity has to carry both data, video, and voice in a way that is reliable and secure. It is
consequently a fact that network connectivity is the mainstay of organizations in the current
Networking and Security
Due to the need for a faster and secure means to share files, resources, and information,
computer networking has proved to be vital since it allows interconnection of multiple computers
to facilitate all these essentials. There is more consideration on the side of security in the current
computing world so that risks that come with networks such as unauthorized access with
malicious intentions are avoided by all means. Factor like administration, geographical span,
architecture, and inter-connectivity determines how a particular network can be classified. For
instance, in the current computing, there are a number of attributes which are as a result of a
well-established network connectivity as discussed below.
The Role and Function of Network Connectivity Currently
When numerous parts of a network are connected to one another extensively by means of
switches, gateways, routers among others, it is in simple terms called network connectivity. It is
a well laid matric resulting to well-connected network parts. In the current computing, there is a
greater realization from institutions and communication companies of a vibrant role played by a
noble network connectivity in operations that are both internally and towards their clients
(Hoffmann & Triesch, 2017). There is a surety of effective communication no matter the
distance by means of radio, wireless network and telephone.
Network connectivity emphasizes on optimal utilization of both software and hardware
components which can result in extreme business performance to an organization. In particular,
cables that are fiber-optic are mostly used currently due to their ability to be bundled and
flexibility hence common is data transmissions that are long-haul. Therefore, for a good
connectivity has to carry both data, video, and voice in a way that is reliable and secure. It is
consequently a fact that network connectivity is the mainstay of organizations in the current
NETWORKING AND SECURITY 3
world whereby they need to implement a virtuous connectivity in order to run their businesses
smoothly and without unnecessary catastrophes besides staying ahead of their competitors
(Gopinath et al., 2015).
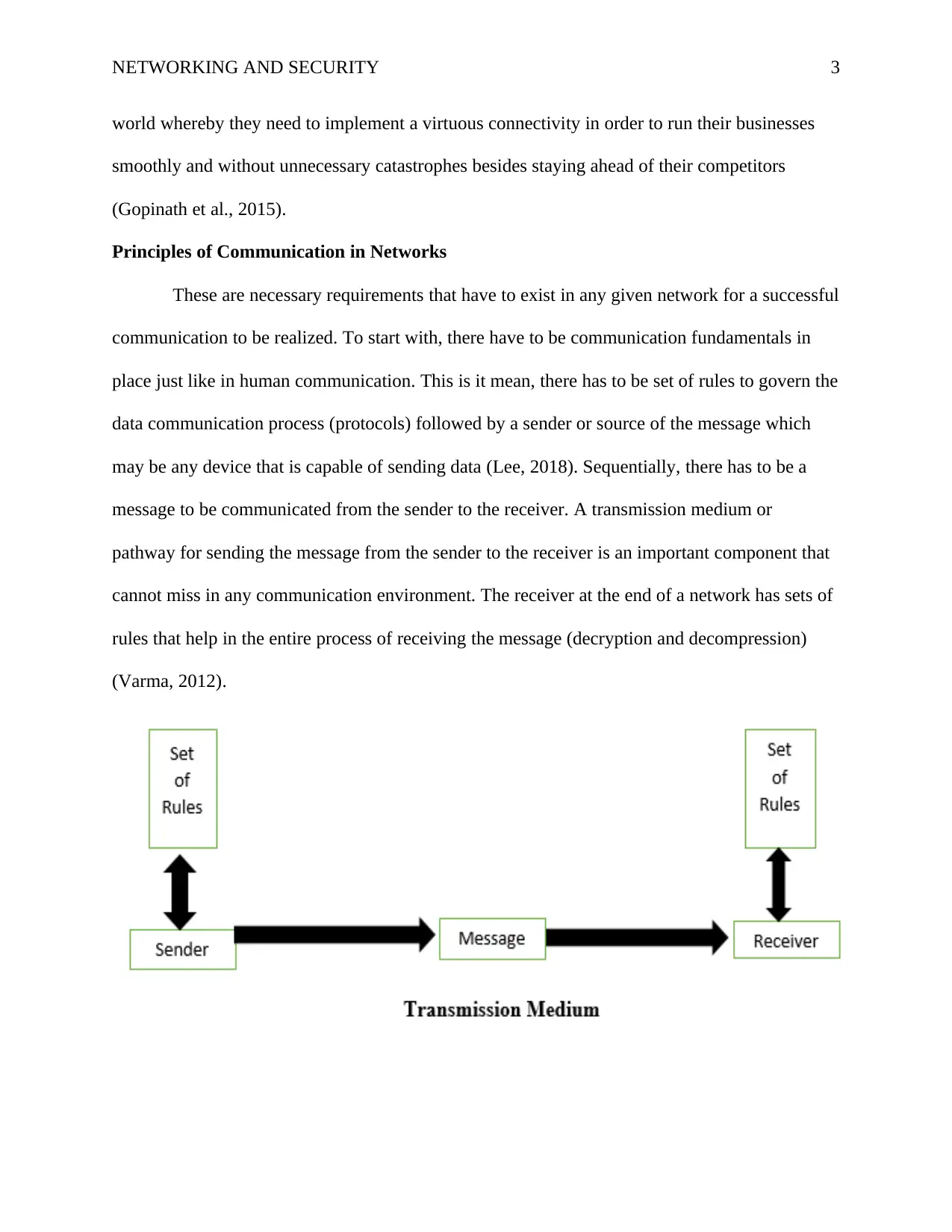
Principles of Communication in Networks
These are necessary requirements that have to exist in any given network for a successful
communication to be realized. To start with, there have to be communication fundamentals in
place just like in human communication. This is it mean, there has to be set of rules to govern the
data communication process (protocols) followed by a sender or source of the message which
may be any device that is capable of sending data (Lee, 2018). Sequentially, there has to be a
message to be communicated from the sender to the receiver. A transmission medium or
pathway for sending the message from the sender to the receiver is an important component that
cannot miss in any communication environment. The receiver at the end of a network has sets of
rules that help in the entire process of receiving the message (decryption and decompression)
(Varma, 2012).
world whereby they need to implement a virtuous connectivity in order to run their businesses
smoothly and without unnecessary catastrophes besides staying ahead of their competitors
(Gopinath et al., 2015).
Principles of Communication in Networks
These are necessary requirements that have to exist in any given network for a successful
communication to be realized. To start with, there have to be communication fundamentals in
place just like in human communication. This is it mean, there has to be set of rules to govern the
data communication process (protocols) followed by a sender or source of the message which
may be any device that is capable of sending data (Lee, 2018). Sequentially, there has to be a
message to be communicated from the sender to the receiver. A transmission medium or
pathway for sending the message from the sender to the receiver is an important component that
cannot miss in any communication environment. The receiver at the end of a network has sets of
rules that help in the entire process of receiving the message (decryption and decompression)
(Varma, 2012).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORKING AND SECURITY 4
Functionality and Role of Software and Hardware Entities that Contribute to
Communication in Networks
Hardware entities. To start with, a gateway supports the existence of compatibility amid
networks in converting protocols, codes, transmission speed or even security measures. On the
other hand, a router that resides on OSI layer three transmits data between multiple segments of a
network (LAN) or to another router when a network setup is of the internet (WAN). A switch
that resides on OSI layer two is also another hardware device that connects multiple devices
together on a network forming a LAN and forwards data to a specific device. Unlike a router, a
bridge links two divergent parts of LAN making them work as a single LAN. The existence of
repeaters is to help in retransmitting signals with a higher power over a channel so that it can
cover a longer distance (Wang, Qiao & Yu, 2014).
Software entities. Through networking software, the inner working mechanism
of a network is exposed to an administrator. They are known to facilitate the access given to
users to help them access network resources. The roles of software include user management and
file management. Talking about functionality, the interconnection of multiple devices on a
network or even over the internet is allowed by the networking software. On the functionality
aspect, administrators are able to add or and remove users from a network apart from being able
to define how users can store and access data (WANG & LÜ, 2014).
Protocols Known to Implement Network Communication
The interactions among the communicating entries are specified by protocols which are
sets of rules used during communication by both end points. They bring to light the design and
the entire activities that involve how data is sent and received over a particular network. Packet
Functionality and Role of Software and Hardware Entities that Contribute to
Communication in Networks
Hardware entities. To start with, a gateway supports the existence of compatibility amid
networks in converting protocols, codes, transmission speed or even security measures. On the
other hand, a router that resides on OSI layer three transmits data between multiple segments of a
network (LAN) or to another router when a network setup is of the internet (WAN). A switch
that resides on OSI layer two is also another hardware device that connects multiple devices
together on a network forming a LAN and forwards data to a specific device. Unlike a router, a
bridge links two divergent parts of LAN making them work as a single LAN. The existence of
repeaters is to help in retransmitting signals with a higher power over a channel so that it can
cover a longer distance (Wang, Qiao & Yu, 2014).
Software entities. Through networking software, the inner working mechanism
of a network is exposed to an administrator. They are known to facilitate the access given to
users to help them access network resources. The roles of software include user management and
file management. Talking about functionality, the interconnection of multiple devices on a
network or even over the internet is allowed by the networking software. On the functionality
aspect, administrators are able to add or and remove users from a network apart from being able
to define how users can store and access data (WANG & LÜ, 2014).
Protocols Known to Implement Network Communication
The interactions among the communicating entries are specified by protocols which are
sets of rules used during communication by both end points. They bring to light the design and
the entire activities that involve how data is sent and received over a particular network. Packet
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
NETWORKING AND SECURITY 5
switching is a technique used by protocols in the entire processes of sending and receiving of
packets.
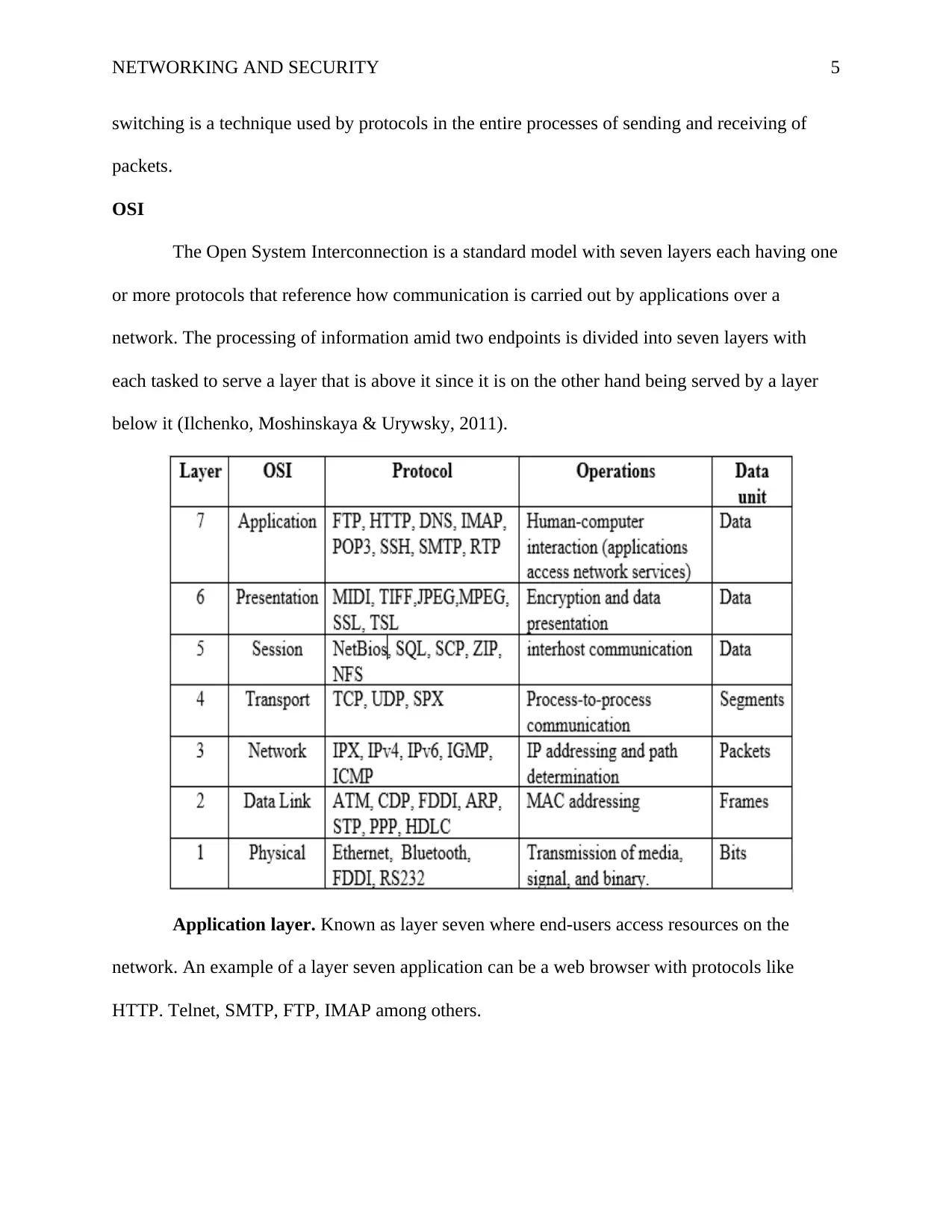
OSI
The Open System Interconnection is a standard model with seven layers each having one
or more protocols that reference how communication is carried out by applications over a
network. The processing of information amid two endpoints is divided into seven layers with
each tasked to serve a layer that is above it since it is on the other hand being served by a layer
below it (Ilchenko, Moshinskaya & Urywsky, 2011).
Application layer. Known as layer seven where end-users access resources on the
network. An example of a layer seven application can be a web browser with protocols like
HTTP. Telnet, SMTP, FTP, IMAP among others.
switching is a technique used by protocols in the entire processes of sending and receiving of
packets.
OSI
The Open System Interconnection is a standard model with seven layers each having one
or more protocols that reference how communication is carried out by applications over a
network. The processing of information amid two endpoints is divided into seven layers with
each tasked to serve a layer that is above it since it is on the other hand being served by a layer
below it (Ilchenko, Moshinskaya & Urywsky, 2011).
Application layer. Known as layer seven where end-users access resources on the
network. An example of a layer seven application can be a web browser with protocols like
HTTP. Telnet, SMTP, FTP, IMAP among others.

NETWORKING AND SECURITY 6
Presentation layer. Layer six where data is put in a form to be transmitted. Data
compression, data encryption, and protocol conversion are done here. However, decompression
and decryption are done at the destination host for easy understanding.
Session layer. Is in layer five where communication sessions between the two end points
are managed. Connections are shared and also terminated at this layer. Protocols like RPC,
NetBIOS, SQL, and NFS operates here.
Transport layer. Layer four where process-to-process or service-to-service
communication happens. Segmentation and port addressing are also done here hence protocols
like UDP, SPX, and TCP are located here.
Network layer. Is in layer three where source to destination packet delivery happens. IP
addressing is also done here alongside packetization, error control, and also flow control.
Protocols like TCP/IP, ICMP, and IPX resides here.
Data Link layer. It is in layer two where point-to-point delivery of frames is done. It is
where switches operate and MAC address is used at this point. CSMA/CD access method is used
in this layer while packets are being sent node-to-node.
Physical layer. Also termed as layer one where physical transmission of bits is carried
out. Media connectors and entire physical topology of a network are defined here. Protocols like
Ethernet, RS232, FDDI, and ATM work in this layer (Silva et al., 2015).
Fundamental Aspects of Cloud Computing
Cloud computing is a model that permits on-demand and appropriate network access to a
pool of shared resources which are released without interaction with the service provider. Having
defined so, for a service to be categorized into cloud computing, it has to an on-demand self-
service allowing a customer to do all the computing minus human interaction. Cloud computing
Presentation layer. Layer six where data is put in a form to be transmitted. Data
compression, data encryption, and protocol conversion are done here. However, decompression
and decryption are done at the destination host for easy understanding.
Session layer. Is in layer five where communication sessions between the two end points
are managed. Connections are shared and also terminated at this layer. Protocols like RPC,
NetBIOS, SQL, and NFS operates here.
Transport layer. Layer four where process-to-process or service-to-service
communication happens. Segmentation and port addressing are also done here hence protocols
like UDP, SPX, and TCP are located here.
Network layer. Is in layer three where source to destination packet delivery happens. IP
addressing is also done here alongside packetization, error control, and also flow control.
Protocols like TCP/IP, ICMP, and IPX resides here.
Data Link layer. It is in layer two where point-to-point delivery of frames is done. It is
where switches operate and MAC address is used at this point. CSMA/CD access method is used
in this layer while packets are being sent node-to-node.
Physical layer. Also termed as layer one where physical transmission of bits is carried
out. Media connectors and entire physical topology of a network are defined here. Protocols like
Ethernet, RS232, FDDI, and ATM work in this layer (Silva et al., 2015).
Fundamental Aspects of Cloud Computing
Cloud computing is a model that permits on-demand and appropriate network access to a
pool of shared resources which are released without interaction with the service provider. Having
defined so, for a service to be categorized into cloud computing, it has to an on-demand self-
service allowing a customer to do all the computing minus human interaction. Cloud computing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

NETWORKING AND SECURITY 7
has to contain a network access that is broad, reachable and with multiple platform preferences.
There is also an aspect of multi-tenant and resource pooling in a way that data can be accessed at
any time, simultaneously and anywhere. Based on policy, cloud computing has to support quick
elasticity being able to grow and shrink without interfering with the users or applications. All in
all, services offered in cloud computing have to be measured or metered allowing customers to
pay for what they use (Linthicum, 2018).
Networking needs for Business in Relation to Networking Architecture
While setting up a network, the consideration of a network that can meet the needs of a
business is vital. The requirements have to be expressed in business terms by considering the
amount of data to be transmitted, expectations of the new network, and if efficiency will be
realized from the new network. To start with, a business has to consider the number of people
that will have to use the network (customers, suppliers, and staff). If a business has future
development plans, it has to come up with a scalable network which will give room for
expansion when the need arises. The existing network in a business has to be assessed to
determine whether to upgrade the existing components or to purchase new ones. Furthermore,
security in the business system has to be prioritized in terms of who will use the network,
necessary access controls, and the backup to be used in the business (Kirkpatrick, 2013). This
will show some sense of preparedness in the business hence gain more trust from customers.
has to contain a network access that is broad, reachable and with multiple platform preferences.
There is also an aspect of multi-tenant and resource pooling in a way that data can be accessed at
any time, simultaneously and anywhere. Based on policy, cloud computing has to support quick
elasticity being able to grow and shrink without interfering with the users or applications. All in
all, services offered in cloud computing have to be measured or metered allowing customers to
pay for what they use (Linthicum, 2018).
Networking needs for Business in Relation to Networking Architecture
While setting up a network, the consideration of a network that can meet the needs of a
business is vital. The requirements have to be expressed in business terms by considering the
amount of data to be transmitted, expectations of the new network, and if efficiency will be
realized from the new network. To start with, a business has to consider the number of people
that will have to use the network (customers, suppliers, and staff). If a business has future
development plans, it has to come up with a scalable network which will give room for
expansion when the need arises. The existing network in a business has to be assessed to
determine whether to upgrade the existing components or to purchase new ones. Furthermore,
security in the business system has to be prioritized in terms of who will use the network,
necessary access controls, and the backup to be used in the business (Kirkpatrick, 2013). This
will show some sense of preparedness in the business hence gain more trust from customers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

NETWORKING AND SECURITY 8
References
Gopinath, K., Krishnamurthy, V., Cabanban, R., & Crosson, B. (2015). Hubs of Anticorrelation
in High-Resolution Resting-State Functional Connectivity Network Architecture. Brain
Connectivity, 5(5), 267-275. doi: 10.1089/brain.2014.0323
Hoffmann, F., & Triesch, J. (2017). Nonrandom network connectivity comes in pairs. Network
Neuroscience, 1(1), 31-41. doi: 10.1162/netn_a_00004
Ilchenko, M., Moshinskaya, A., & Urywsky, L. (2011). Levels separation and merging in the
OSI reference model for information–telecommunication systems. Cybernetics and
Systems Analysis, 47(4), 598-605. doi: 10.1007/s10559-011-9340-4
Kirkpatrick, K. (2013). Software-defined networking. Communications of the ACM, 56(9), 16-
19.
Lee, B. (2018). Reviewer Acknowledgements for Network and Communication Technologies
Vol. 3, No. 1. Network And Communication Technologies, 3(1), 45. doi:
10.5539/nct.v3n1p45
Linthicum, D. (2018). Approaching Cloud Computing Performance. IEEE Cloud
Computing, 5(2), 33-36. doi: 10.1109/mcc.2018.022171665
Silva, B. M., Rodrigues, J. J., de la Torre Díez, I., López-Coronado, M., & Saleem, K. (2015).
Mobile-health: A review of current state in 2015. Journal of biomedical informatics, 56,
265-272.
Varma, A. (2012). Data Link Control in Data Communication. IOSR Journal Of Electronics And
Communication Engineering, 4(1), 39-47. doi: 10.9790/2834-0413947
Wang, J., Qiao, C., & Yu, H. (2014). Resilient virtual infrastructure design and recovery. Optical
Switching and Networking, 11, 153. doi: 10.1016/j.osn.2013.11.002
References
Gopinath, K., Krishnamurthy, V., Cabanban, R., & Crosson, B. (2015). Hubs of Anticorrelation
in High-Resolution Resting-State Functional Connectivity Network Architecture. Brain
Connectivity, 5(5), 267-275. doi: 10.1089/brain.2014.0323
Hoffmann, F., & Triesch, J. (2017). Nonrandom network connectivity comes in pairs. Network
Neuroscience, 1(1), 31-41. doi: 10.1162/netn_a_00004
Ilchenko, M., Moshinskaya, A., & Urywsky, L. (2011). Levels separation and merging in the
OSI reference model for information–telecommunication systems. Cybernetics and
Systems Analysis, 47(4), 598-605. doi: 10.1007/s10559-011-9340-4
Kirkpatrick, K. (2013). Software-defined networking. Communications of the ACM, 56(9), 16-
19.
Lee, B. (2018). Reviewer Acknowledgements for Network and Communication Technologies
Vol. 3, No. 1. Network And Communication Technologies, 3(1), 45. doi:
10.5539/nct.v3n1p45
Linthicum, D. (2018). Approaching Cloud Computing Performance. IEEE Cloud
Computing, 5(2), 33-36. doi: 10.1109/mcc.2018.022171665
Silva, B. M., Rodrigues, J. J., de la Torre Díez, I., López-Coronado, M., & Saleem, K. (2015).
Mobile-health: A review of current state in 2015. Journal of biomedical informatics, 56,
265-272.
Varma, A. (2012). Data Link Control in Data Communication. IOSR Journal Of Electronics And
Communication Engineering, 4(1), 39-47. doi: 10.9790/2834-0413947
Wang, J., Qiao, C., & Yu, H. (2014). Resilient virtual infrastructure design and recovery. Optical
Switching and Networking, 11, 153. doi: 10.1016/j.osn.2013.11.002

NETWORKING AND SECURITY 9
WANG, B., & LÜ, J. (2014). Software Networks Nodes Impact Analysis of Complex Software
Systems. Journal Of Software, 24(12), 2814-2829. doi: 10.3724/sp.j.1001.2013.04397
WANG, B., & LÜ, J. (2014). Software Networks Nodes Impact Analysis of Complex Software
Systems. Journal Of Software, 24(12), 2814-2829. doi: 10.3724/sp.j.1001.2013.04397
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





