Networking Technologies: DHCP, DNS Zones, Classful vs Classless IP
VerifiedAdded on 2023/04/11
|7
|1031
|483
Homework Assignment
AI Summary
This assignment provides a comprehensive overview of several key networking technologies. It begins by detailing the benefits of using DHCP for dynamic IP address assignment, including centralized network client configuration and support for both BOOTP clients and large networks. The assignment then explains the use of DNS zones in managing DNS domains, highlighting their role in differentiating managed areas and enabling granular control. Furthermore, it contrasts classful and classless IP addressing, explaining the reasons for the transition to CIDR and providing an example of subnetting. Finally, the reflection exercise summarizes the student's learning experience, acknowledging newly acquired knowledge and identifying areas for further exploration, specifically the database functionalities of DHCP and the DNS zone file structure. Desklib offers a wealth of similar solved assignments and past papers to aid students in their studies.

Running head: NETWORKING TECHNOLOGIES
Networking Technologies
Name of the Student
Name of the University
Author Note
Networking Technologies
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1NETWORKING TECHNOLOGIES
Benefits of DHCP in IP assignment
The DHCP protocol is used by internet service providers (ISP) for dynamically
assigning IP addresses every time the router is restarted thus eliminating duplication of IP
addresses (Lemon and Mrugalski 2016). The dynamic addresses obtained are cheaper
compared to static addresses while also providing greater privacy. Dynamic IP addresses are
also very useful for one way Virtual Private Networks (VPN). Other benefits than IP
assignment are:
Centralized configuration of network clients: Custom configurations for specific
clients can be created. Information related to configuration is stored in a particular
place called DHCP data store. Client specific changes can easily be implemented by
merely editing their information contained in the data store.
BOOTP client support: All DHCP servers respond to the requests from clients of
BOOTP as well as DHCP. These clients of BOOTP receive booting and IP addresses
related information from servers.
Support for clients both remote and local: BOOTP messages are relayed among the
networks. DHCP makes use of the relay feature of BOOTP in multiple ways (Shen
and Chen 2018). Almost all network routers are configurable for working as relay
agents of BOOTP for passing requests to the servers which are not present on the
network of the client.
Support for Large networks: DHCP servers use multithreading for processing millions
of client requests at the same time. Possess support for data stores optimized for
handling large amounts of data.
Benefits of DHCP in IP assignment
The DHCP protocol is used by internet service providers (ISP) for dynamically
assigning IP addresses every time the router is restarted thus eliminating duplication of IP
addresses (Lemon and Mrugalski 2016). The dynamic addresses obtained are cheaper
compared to static addresses while also providing greater privacy. Dynamic IP addresses are
also very useful for one way Virtual Private Networks (VPN). Other benefits than IP
assignment are:
Centralized configuration of network clients: Custom configurations for specific
clients can be created. Information related to configuration is stored in a particular
place called DHCP data store. Client specific changes can easily be implemented by
merely editing their information contained in the data store.
BOOTP client support: All DHCP servers respond to the requests from clients of
BOOTP as well as DHCP. These clients of BOOTP receive booting and IP addresses
related information from servers.
Support for clients both remote and local: BOOTP messages are relayed among the
networks. DHCP makes use of the relay feature of BOOTP in multiple ways (Shen
and Chen 2018). Almost all network routers are configurable for working as relay
agents of BOOTP for passing requests to the servers which are not present on the
network of the client.
Support for Large networks: DHCP servers use multithreading for processing millions
of client requests at the same time. Possess support for data stores optimized for
handling large amounts of data.

2NETWORKING TECHNOLOGIES
DNS domain zones
The DNS can be broken into multiple zones. The zones are used for differentiating
between distinctly managed areas in DNS namespaces which are managed by administrators
or organizations. They allow more granular control of the DNS components like authoritative
name servers. DNS zones can have several subdomains and zones which may exist on that
server only. DNS zones are not physically separated from each other and specifically used to
delegate control (Afanasyev et al. 2017). Domain name spaces work as hierarchical trees
having DNS root domains on top. DNS zones start at domains within the trees while also able
to extend into subdomains so multiple of them are manageable by a single entity. The domain
administrator is the one who is with creating the DNS zones. DNS zones can be comprised of
multiple domains or even subdomains. Multiple DNS zones may also be existing on one or
the same server. Information specific to DNS zones are stored within text files called the
DNS zone file (Lee, Jeong and Park 2016).
Classful IP addressing vs Classless IP addressing
IPv4 addresses have a length of 32 bits. Every 8-bit field or octet, is represented through
decimal numbers within 0 and 255 (like 172.168.121.24). IPv4 addresses identify networks
(network numbers) as well as unique interfaces on the network like host number.
Here the network portion of IP addresses was identified with using absolute values for
particular addresses (leading bits) with the following. In other words, classful addresses
encode netmask within the IP addresses:
DNS domain zones
The DNS can be broken into multiple zones. The zones are used for differentiating
between distinctly managed areas in DNS namespaces which are managed by administrators
or organizations. They allow more granular control of the DNS components like authoritative
name servers. DNS zones can have several subdomains and zones which may exist on that
server only. DNS zones are not physically separated from each other and specifically used to
delegate control (Afanasyev et al. 2017). Domain name spaces work as hierarchical trees
having DNS root domains on top. DNS zones start at domains within the trees while also able
to extend into subdomains so multiple of them are manageable by a single entity. The domain
administrator is the one who is with creating the DNS zones. DNS zones can be comprised of
multiple domains or even subdomains. Multiple DNS zones may also be existing on one or
the same server. Information specific to DNS zones are stored within text files called the
DNS zone file (Lee, Jeong and Park 2016).
Classful IP addressing vs Classless IP addressing
IPv4 addresses have a length of 32 bits. Every 8-bit field or octet, is represented through
decimal numbers within 0 and 255 (like 172.168.121.24). IPv4 addresses identify networks
(network numbers) as well as unique interfaces on the network like host number.
Here the network portion of IP addresses was identified with using absolute values for
particular addresses (leading bits) with the following. In other words, classful addresses
encode netmask within the IP addresses:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
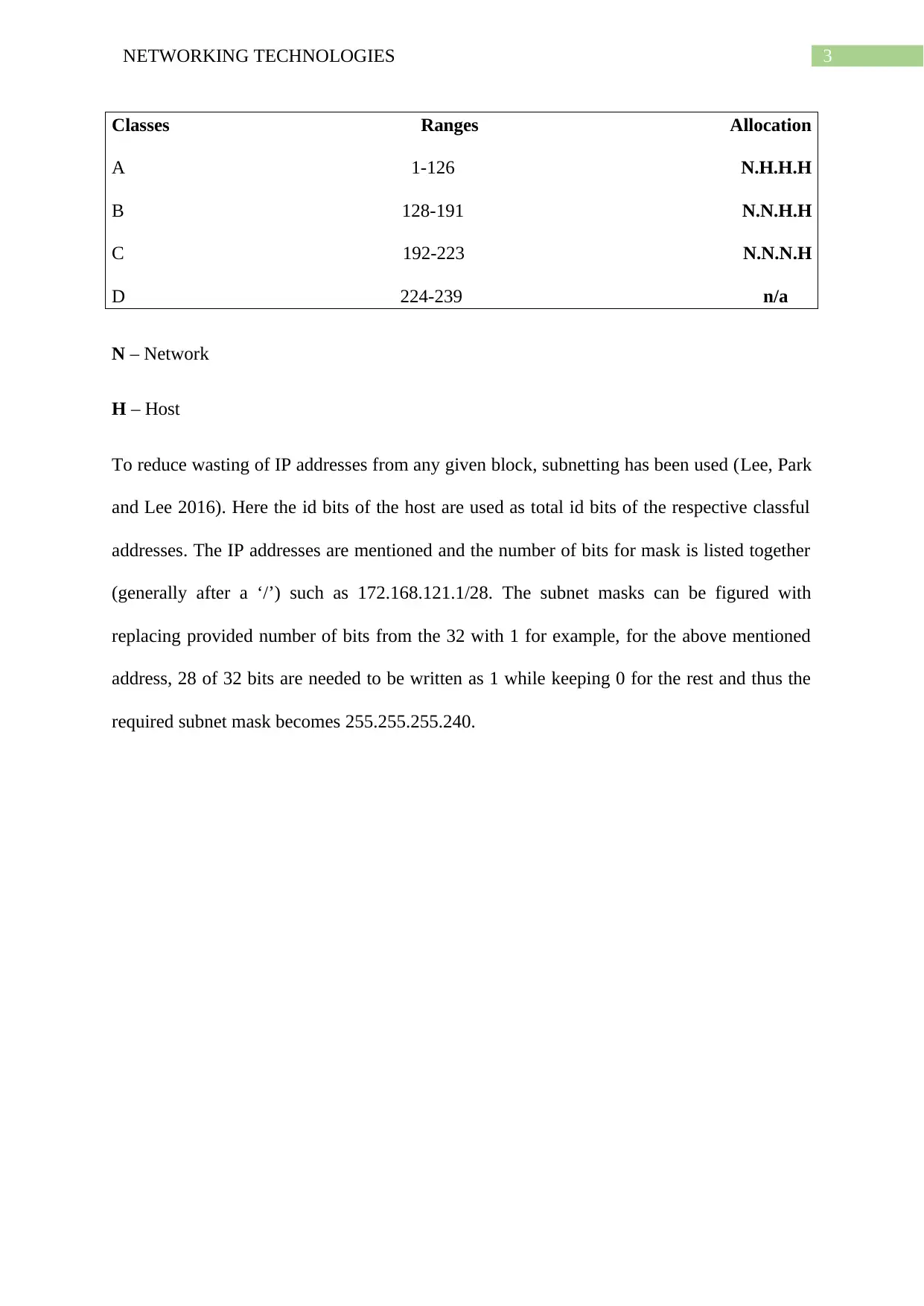
3NETWORKING TECHNOLOGIES
Classes Ranges Allocation
A 1-126 N.H.H.H
B 128-191 N.N.H.H
C 192-223 N.N.N.H
D 224-239 n/a
N – Network
H – Host
To reduce wasting of IP addresses from any given block, subnetting has been used (Lee, Park
and Lee 2016). Here the id bits of the host are used as total id bits of the respective classful
addresses. The IP addresses are mentioned and the number of bits for mask is listed together
(generally after a ‘/’) such as 172.168.121.1/28. The subnet masks can be figured with
replacing provided number of bits from the 32 with 1 for example, for the above mentioned
address, 28 of 32 bits are needed to be written as 1 while keeping 0 for the rest and thus the
required subnet mask becomes 255.255.255.240.
Classes Ranges Allocation
A 1-126 N.H.H.H
B 128-191 N.N.H.H
C 192-223 N.N.N.H
D 224-239 n/a
N – Network
H – Host
To reduce wasting of IP addresses from any given block, subnetting has been used (Lee, Park
and Lee 2016). Here the id bits of the host are used as total id bits of the respective classful
addresses. The IP addresses are mentioned and the number of bits for mask is listed together
(generally after a ‘/’) such as 172.168.121.1/28. The subnet masks can be figured with
replacing provided number of bits from the 32 with 1 for example, for the above mentioned
address, 28 of 32 bits are needed to be written as 1 while keeping 0 for the rest and thus the
required subnet mask becomes 255.255.255.240.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
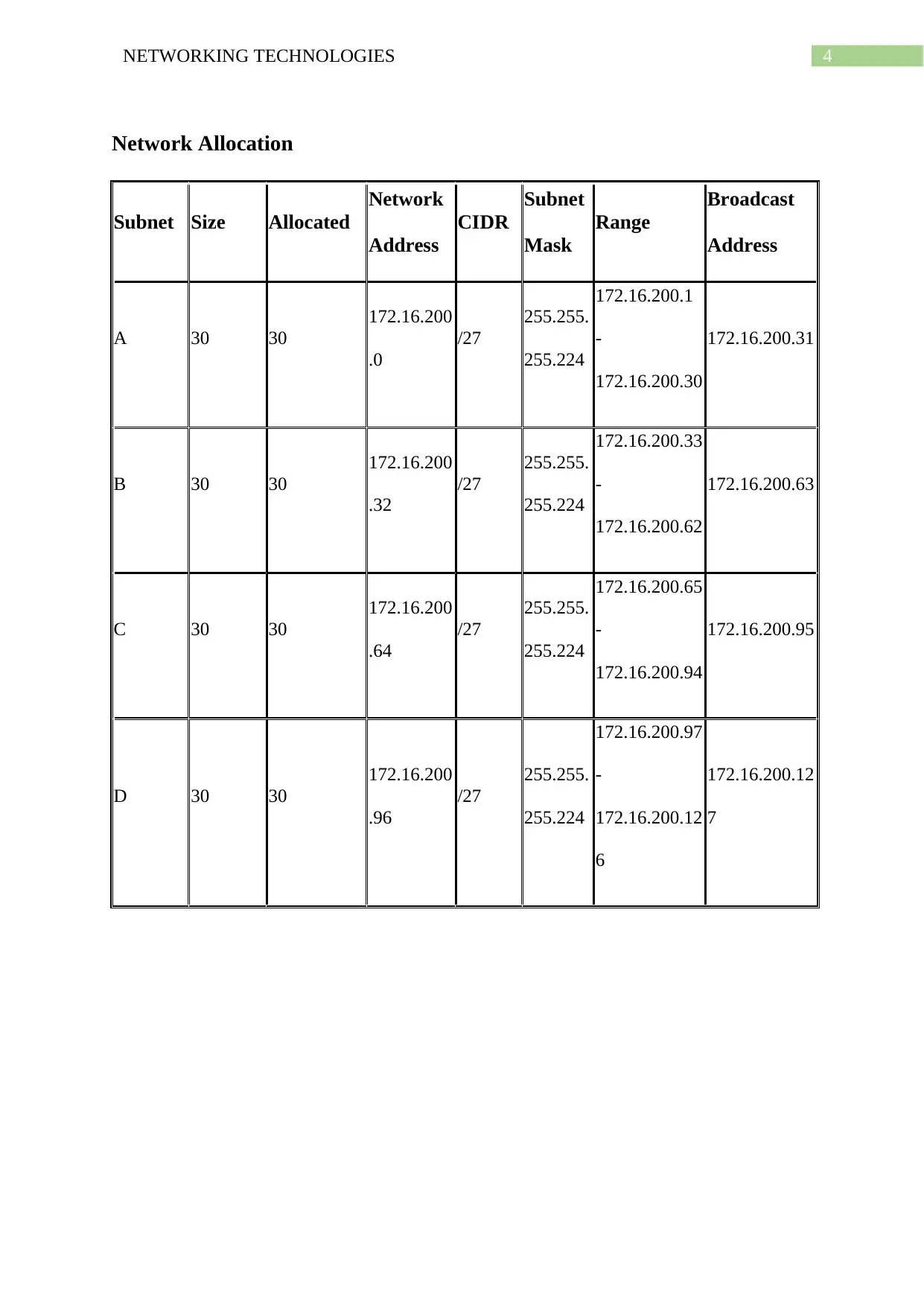
4NETWORKING TECHNOLOGIES
Network Allocation
Subnet Size Allocated
Network
Address
CIDR
Subnet
Mask
Range
Broadcast
Address
A 30 30
172.16.200
.0
/27
255.255.
255.224
172.16.200.1
-
172.16.200.30
172.16.200.31
B 30 30
172.16.200
.32
/27
255.255.
255.224
172.16.200.33
-
172.16.200.62
172.16.200.63
C 30 30
172.16.200
.64
/27
255.255.
255.224
172.16.200.65
-
172.16.200.94
172.16.200.95
D 30 30
172.16.200
.96
/27
255.255.
255.224
172.16.200.97
-
172.16.200.12
6
172.16.200.12
7
Network Allocation
Subnet Size Allocated
Network
Address
CIDR
Subnet
Mask
Range
Broadcast
Address
A 30 30
172.16.200
.0
/27
255.255.
255.224
172.16.200.1
-
172.16.200.30
172.16.200.31
B 30 30
172.16.200
.32
/27
255.255.
255.224
172.16.200.33
-
172.16.200.62
172.16.200.63
C 30 30
172.16.200
.64
/27
255.255.
255.224
172.16.200.65
-
172.16.200.94
172.16.200.95
D 30 30
172.16.200
.96
/27
255.255.
255.224
172.16.200.97
-
172.16.200.12
6
172.16.200.12
7

5NETWORKING TECHNOLOGIES
Reflection
a)
From the first three modules, by answering the questions I can comfortably say that I
gained thorough theoretical as well as technical knowledge regarding the protocols used in
networking for assigning IP addresses, mainly DHCP. The learning experience includes
benefits of using the DHCP protocol and where it should be used. The concept of DNS zones
is relatively new for me and all the definitions and statements relating to DNS zones were
pretty refreshing. Lastly by distinguishing between classful and classless IP addressing
techniques some of my key doubts got resolved.
b)
Although we discussed the topics of DHCP protocol and DNS zones at great depths, I
still think there is much more to learn specifically about these topics. To be more specific I
would like to explore further on the database related functionalities of DHCP and for DNS
zones, I think we did not dig deeper into the DNS zone file, the different sections of the DNS
zone file and how the contents may vary for different use cases (Hoffman 2018).
Reflection
a)
From the first three modules, by answering the questions I can comfortably say that I
gained thorough theoretical as well as technical knowledge regarding the protocols used in
networking for assigning IP addresses, mainly DHCP. The learning experience includes
benefits of using the DHCP protocol and where it should be used. The concept of DNS zones
is relatively new for me and all the definitions and statements relating to DNS zones were
pretty refreshing. Lastly by distinguishing between classful and classless IP addressing
techniques some of my key doubts got resolved.
b)
Although we discussed the topics of DHCP protocol and DNS zones at great depths, I
still think there is much more to learn specifically about these topics. To be more specific I
would like to explore further on the database related functionalities of DHCP and for DNS
zones, I think we did not dig deeper into the DNS zone file, the different sections of the DNS
zone file and how the contents may vary for different use cases (Hoffman 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6NETWORKING TECHNOLOGIES
References
Afanasyev, A., Jiang, X., Yu, Y., Tan, J., Xia, Y., Mankin, A. and Zhang, L., 2017, July.
NDNS: A DNS-like name service for NDN. In 2017 26th International Conference on
Computer Communication and Networks (ICCCN) (pp. 1-9). IEEE.
Hoffman, P., 2018. Representing DNS Messages in JSON (No. RFC 8427).
Lee, S., Jeong, J.P. and Park, J.S., 2016, January. DNSNA: DNS name autoconfiguration for
Internet of Things devices. In 2016 18th International Conference on Advanced
Communication Technology (ICACT) (pp. 410-416). IEEE.
Lee, Y., Park, H. and Lee, Y., 2016. Ip geolocation with a crowd-sourcing broadband
performance tool. ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20.
Lemon, T. and Mrugalski, T., 2016. Customizing DHCP Configuration on the Basis of
Network Topology (No. RFC 7969).
Shen, N. and Chen, E., 2018. Generalized UDP Source Port for DHCP Relay (No. RFC
8357).
References
Afanasyev, A., Jiang, X., Yu, Y., Tan, J., Xia, Y., Mankin, A. and Zhang, L., 2017, July.
NDNS: A DNS-like name service for NDN. In 2017 26th International Conference on
Computer Communication and Networks (ICCCN) (pp. 1-9). IEEE.
Hoffman, P., 2018. Representing DNS Messages in JSON (No. RFC 8427).
Lee, S., Jeong, J.P. and Park, J.S., 2016, January. DNSNA: DNS name autoconfiguration for
Internet of Things devices. In 2016 18th International Conference on Advanced
Communication Technology (ICACT) (pp. 410-416). IEEE.
Lee, Y., Park, H. and Lee, Y., 2016. Ip geolocation with a crowd-sourcing broadband
performance tool. ACM SIGCOMM Computer Communication Review, 46(1), pp.12-20.
Lemon, T. and Mrugalski, T., 2016. Customizing DHCP Configuration on the Basis of
Network Topology (No. RFC 7969).
Shen, N. and Chen, E., 2018. Generalized UDP Source Port for DHCP Relay (No. RFC
8357).
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




